Ultimate Resource On Trezor Hardware Wallets (#GotBitcoin)
Be careful, buy only from Trezor Shop or authorized resellers. Ultimate Resource On Trezor Hardware Wallets (#GotBitcoin)

Related:
Ultimate Resource On Ledger Hardware Wallet (#GotBitcoin?)
Next Bitcoin Core Release To Finally Connect Hardware Wallets To Full Nodes
Ultimate Resource On Crypto Hardware (And Other) Wallets
Wallets Are Over. Your Phone Is Your Everything Now
Survey Shows Many BTC Holders Use Hardware Wallet, Have Backup Keys
What Are Lightning Wallets Doing To Help Onboard New Users?
Introducing BTCPay Vault – Use Any Hardware Wallet With BTCPay And Its Full Node
Inheritance Planning For Cryptocurrencies
How To Securely Transfer Crypto To Your Heirs
However, in recent weeks, we have discovered something more startling. A one-to-one copy of Trezor One. In other words, a fake Trezor device, manufactured by a different, unknown vendor.
While Trezor clones are marketed under a different name, manufactured by (legitimate) legal companies, allowing you to distinguish them from the original, a fake Trezor tries to replicate the original to the bone.
It seeks to be as indistinguishable from the original as possible. It is not dissimilar to counterfeit brand clothing.
Similarly to clothing fakes, a fake Trezor One is often sold at a steep discount. This should act as the first red flag. Others will be described below.
More importantly though, let’s have a look at why fake Trezor devices can be a severe threat to your security. As we did not manufacture the device, we cannot guarantee its function. These fake devices are thus unsuitable for secure storage of cryptocurrencies and other digital assets.
You would not entrust your money to somebody who has already cheated you by selling you a different product than you thought you were buying.
We, therefore, recommend not to use this device and report it to us, which would help us fight these scams and provide you with a legitimate device.
As soon as we learned about the existence of Trezor fakes, we have started to fervently pursue a number of legal and other steps to prevent those fakes from being produced and distributed, in order to protect you, our customers.
How to check if your device is genuine.
The Hologram
We are warning our customers about the hologram when logging for the first to the wallet.trezor.io.
If you suspect you have bought a fake Trezor One device, do not use the device and contact our support immediately.
Original Trezor One holographic seal (above) in contrast with fake holographic seal (below)


How to shop for a genuine Trezor One device.
The simplest way to procure your genuine Trezor One is to buy it at the official Trezor shop, official Amazon shop or from official resellers. Be very cautious when buying on other marketplaces, such as eBay, Taobao, AliExpress, unknown Amazon resellers or other places. If you are not sure about the authenticity of the seller or the channel, always proceed with the official channels. You can find more information about the security elements both for Trezor One and Trezor Model T on our Wiki.
When It Comes To Your Coins, Keep It Quiet
Have you ever heard the saying “Silence is golden”? In the context of cryptocurrencies, being quiet about your funds will not bring you gold, but it might just save your coins.
Beware of stranger danger.
Let’s suppose that you have invested a lot of money in cryptocurrencies, or that your investments have paid off and your cryptocurrency funds have multiplied.
Obviously, you are pleased about it, and you want to share your success story with other people, so you post a comment about it on Facebook or Reddit.
A random reader of your post might then decide that he or she really wants your riches and starts using a variety of malicious tactics to get them. These might include cyber attacks or even physical violence. (You would be surprised how much information can be mined from your social media, including your physical location.)
Use Common Sense
In the offline face-to-face world, a bit of restraint might come in handy as well.
It is easy to have a few beers and start to be a bit more talkative. Making friends is great, but the contents of your Trezor wallet might not be the best topic to begin with, just like you wouldn’t talk to everyone about your regular bank account balance or your salary.
Don’t Be An Easy Target
Trezor hardware wallet, One or Model T, is a perfectly safe, cryptographically protected place for your coins and keys.
However, keeping a low profile will protect you from other people even trying to steal your funds or harm you. Physical violence or blackmail are things even Trezor cannot protect you from.
What to avoid?
While publicly advocating the benefits of crypto is perfectly fine, boasting about how much you actually own might not be a good idea.
Avoid talking about your account balances with people you do not trust. (Sometimes, you should keep quiet even with people you trust.)
Avoid posting about your personal funds on social media and on internet forums.
Never ever post your recovery seed online or show it to anybody else.
Use a fresh receiving address for your incoming transactions. If not careful, your address may be used to track your balance and transaction history.
Phishing Attacks Used To Steal Your Coins
Ever since the dawn of the internet, there has been a type of malicious activity almost immune to technological advancement in cybersecurity — social engineering. Nowadays, the target of these practices can be even you and your cryptocurrencies.
Phishing is a type of attack which relies on the fallibility of human judgment and perception. Phishing, the most widespread form of attack, is regularly used to extract sensitive data such as credit card numbers, SSN, passwords, and other confidential information from unknowing users online by letting them submit this information directly to the attacker.
Trust Your Device
Your internet browser and software wallets are often susceptible to malware and tricks implemented to mislead you or lure out information which should never get online. Your Trezor device, however, stays offline and is isolated from these attempts to misdirect you. The fundamental purpose of your Trezor device is to keep your recovery seed isolated. You should always look at your device for confirmation of all operations, especially when working with your recovery seed. Your computer should never require the use of your seed without the device knowing it.
Moreover, if you ever need to use the recovery seed to access your accounts, the device will always instruct you to enter the words in a shuffled order. We recommend entering the words of your seed directly on the device to maximize the safety of this operation.
There is a variety of phishing techniques which could be used to carry out an attack. In this article, we offer you some basic knowledge and tips on how to protect yourself against these kinds of malicious attempts.
The Impersonation technique is one of the fastest to carry out and technologically simplest to implement. The attacker usually impersonates a Customer Service agent or Sales representative and tries to lure sensitive information from an unaware user using emails, phone communication or a spoofed website.
Trezor (SatoshiLabs) representatives will never ever ask for your recovery seed (in any form) or a credit card number.
If you ever have a problem with your device or have some questions about Trezor-related issues, be sure to reach out to us only by submitting a ticket in our Support Center.
We do not provide phone call or live technical support. Do not call numbers who claim to be associated with the Trezor Support team.
Many phishing techniques aim to get you to a fraudulent site where all inputs are collected and controlled by the attacker. Similarly to the impersonation techniques, these are also designed to rob you of your private keys.
DNS poisoning technique takes advantage of how the Domain Name System works and sends the visitor off in the wrong direction, making the site appear to be offline or even redirecting users to a server the attacker controls. On the other hand, BGP hijacking is a process of taking control of a group of IP prefixes assigned to a potential victim. Both methods can be identified by an invalid SSL certificate, but users can skip the warning very quickly, leading them to the malicious site. It is, therefore, crucial to be wary of all signs, especially when working with something as important as cryptocurrencies.
The Unicode domain phishing attack, also known as IDN homograph attack, relies on the fact that the affected browsers show Unicode characters used in domain names as ordinary characters, making them virtually impossible to separate from legitimate domains. If an attacker can register a domain that is visually indistinguishable from a legitimate one, he can trick users into trusting the site.
Cybersquatting refers to illegal domain name registration or use. It can have many different forms, but its primary purpose is to steal or misspell a domain name. Cybersquatting can also include advertisers who mimic domain names that are similar to famous, highly trafficked websites.
Never enter your recovery seed online in a straight sequence and never disclose the order of the words.
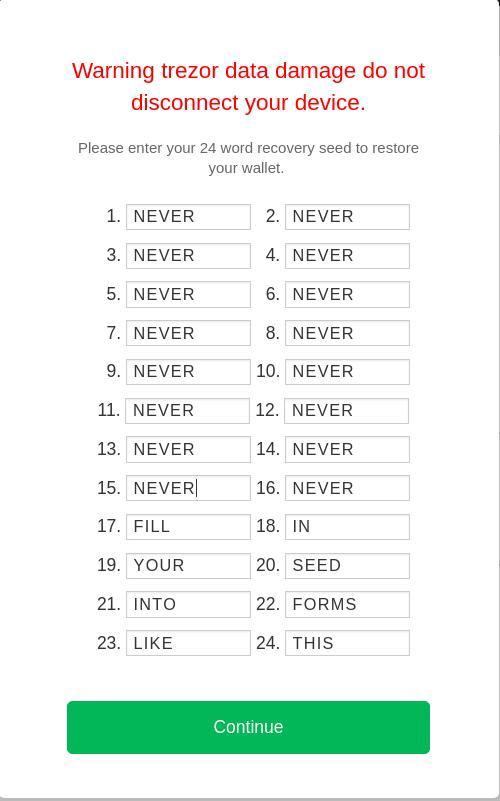
Trust your device. Look for confirmation on the screen, especially when it involves transactions or your recovery seed.
Make sure the URL is exactly: https://wallet.trezor.io (or https://beta-wallet.trezor.io). Although the “Secure” https lock may not be a guarantee of the authenticity of the website, be alarmed if it is missing.
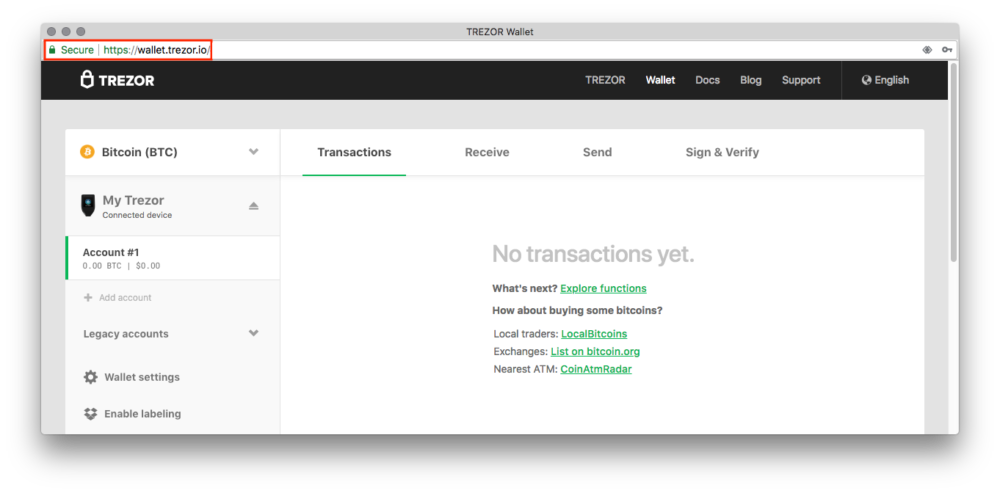
* Carefully Observe The Website Addresses And Watch Out For Any Misspellings Or Odd Characters.
* Bookmark The https://wallet.trezor.io To Avoid Misspelling It In The Address Bar Of Your Browser.
* Use Updated Security Software, Install Security Patches And Updates As They Are Made Available.
* Avoid Clicking On Links In An Email Or Social Media Unless You Are Absolutely Sure That It Is Authentic. (Hover Above The Links To See The Url Before Clicking On It And Then Enter The Url By Yourself.).
* Pay Particularly Close Attention To Shortened Links, Especially On Social Media.
* Be Vigilant. Do Some Research First Before You Decide To Trust A Third-Party Service With Your Sensitive Information (Even Your Xpub).
Updated: 9-16-2019
SatoshiLabs Rolls Out Bitcoin-Only Firmware for Trezor Wallets
SatoshiLabs, the Prague-based manufacturer of hardware cryptocurrency wallets Trezor, released a beta version of its new firmware that supports Bitcoin (BTC) exclusively.
“Orange Coin Good!”
According to the blog post published on Sept. 9, SatoshiLabs’ new BTC firmware is now available to download for both Trezor One and Trezor Model T.
The company also noted that it aims to introduce a “stable version” of Bitcoin-only firmware in the next month’s release, adding:
“From now on, we will be producing four different versions of firmware — regular (full altcoin support + U2F/WebAuthn) and Bitcoin-only, for both Trezor One and Model T. […] We have created a customized version of both our firmware and Wallet designed for everyone who supports the idea of Bitcoin. Every Bitcoin maximalist can now enjoy the Wallet interface with nothing else but Bitcoin.”
Firmware For Bitcoin Maximalists
Per the announcement, to install the new firmware, users will require Trezor Model T (version 2.1.0 or newer) or Trezor One, access to Trezor Beta Wallet or trezorctl, and a correct firmware installation file.
As Cointelegraph reported on March 11, Trezor’s direct competitor — major hardware crypto wallets manufacturer Ledger — disclosed five reported vulnerabilities in Trezor One and Trezor Model T.
In response, Trezor later claimed that none of the weaknesses revealed by Ledger are “critical” for hardware wallets. It was stated that none of them can be exploited remotely, as the attacks described require “physical access to the device, specialized equipment, time, and technical expertise.”
Updated: 2-1-2020
Trezor Wallets Can Be Hacked, Kraken Reveals
Kraken Security Labs revealed on Jan 31. that Trezor hardware wallets and their derivatives can be hacked to extract private keys. Though the procedure is quite involved, Kraken claims that it “requires just 15 minutes of physical access to the device.”
The attack requires a physical intervention on the Trezor wallet by either extracting its chip and placing it on a special device or soldering a couple of critical connectors.
The Trezor chip must then be connected to a “glitcher device” that would send it signals at specific moments. These break the built-in protection that prevents the chip’s memory from being read by external devices.
The trick allows the attacker to read critical wallet parameters, including the private key seed.
Though the seed is encrypted with a PIN-generated key, the researchers were able to brute force the combination in just two minutes.
The vulnerability is caused by the specific hardware used by Trezor, meaning that the company cannot easily fix it. It would need to completely redesign the wallet and recall all existing models.
In the meantime, Kraken urged Trezor and KeepKey users to not allow anyone to physically access the wallet.
In a coordinated response published by Trezor, the team minimized the impact of the vulnerability. The company argued that the attack would show visible signs of tampering due to the need to open the device, while also noting that the attack requires extremely specialized hardware to perform.
Finally, the team suggested users activate the wallet’s passphrase feature to protect from such attacks. The password is never stored on the device as it is added to the seed to generate the private key on the fly. Kraken also noted that this is a viable alternative, though researchers referred to it as “a bit clunky to use in practice.”
The feature also adds significant responsibility to each user. The passphrase needs to be complex enough to not be easily brute forced as well, and forgetting it would completely lock users out of their money.
Cointelegraph reached out to Kraken for additional details, but had not received a response as of press time. The article will be updated as more information becomes available.
Updated: 2-14-2020
Ledger Reignites Trezor Beef With ‘Dishonest’ Report on Crypto Wallet Hardware
Cryptocurrency hardware wallet manufacturer Ledger has reignited an old feud with competitor Trezor, in a blog post dated Feb. 13 highlighting the claimed benefits of its internal Secure Element chips. Trezor co-founder and CEO of SatoshiLabs, Marek “Slush” Palatinus, hit straight back, in a tweet accusing the post of being “dishonest” and not telling the “whole story.”
The Ledger post compared the three internal chip types common to hardware wallet devices: Microcontroller Units (MCU), Safe Memory chips and its own Secure Elements.
It claimed that the MCUs found in Trezor wallets were intended for general devices such as microwaves and TV remotes, and had no embedded countermeasures against physical security attacks.
Furthermore, it stated that Safe Memory chips, used in certain other manufacturers’ hardware wallets, were not third-party tested, and were vulnerable to side-channel attacks as the private keys were passed to the MCU.
Only part of the story
Palatinus retweeted the post, claiming that Ledger was being “dishonest” and “point[ing] out only part of the whole story.”
A non-disclosure agreement (NDA) for Secure Elements chip vendors prevents wallet manufacturers from discussing security issues, according to the tweet:
“Trezor is using nonNDA chips so we can be fully transparent and act in your best interest.”
Palatinus promised to talk more about the implications of NDAs to end-user security at the Bitcoin 2020 conference in March.
Bad Blood
Ledger previously clashed with Trezor last March, when it published a report disclosing five supposed vulnerabilities in Trezor hardware wallets.
As Cointelegraph reported, Trezor was quick to respond, pointing out that none of the vulnerabilities were critical for hardware wallets. Furthermore, none of the weaknesses could be exploited remotely, with all requiring physical access to the device.
Things seemed to have calmed down since then, but with this latest post, Ledger may well have reignited an old beef.
Public Service Announcement. Non-genuine,Public Service Announcement. Non-genuine,Public Service Announcement. Non-genuine,Public Service Announcement. Non-genuine,Public Service Announcement. Non-genuine,Public Service Announcement. Non-genuine,Public Service Announcement. Non-genuine,Public Service Announcement. Non-genuine,
Updated: 10-14-2020
Trezor Claims New “Phishing Proof” Desktop Wallet
The desktop app reportedly provides “more robust protection” than Trezor’s browser-based wallet.
Crypto wallet provider Trezor has launched a new desktop app called Trezor Suite for its hardware wallet.
According to an Oct. 14 blog post, Trezor’s parent company Satoshi Labs claimed its desktop app provides “more robust protection” than its browser-based wallet, and said they have eliminated the risk of phishing attacks that often target crypto users.
“People have the right to privacy and security online but few know how to achieve it,” stated the Trezor blog. “Using Trezor Suite should help everyone take full advantage of Bitcoin more easily and open the door to a more privacy-aware, crypto-competent, and self-sovereign society.”
Hardware wallets — despite being commonly used as a cold storage method — aren’t exempt from data breaches. In January, Kraken Security Labs showed that hackers could extract private keys from a Trezor hardware wallet with just 15 minutes of physical access to the device.
There has been fierce competition among major cryptocurrency wallet providers, with data security often at the forefront of the discussion. Cointelegraph reported in September that hackers had been targeting users on Electrum — a Bitcoin hot wallet — in phishing scams resulting in the loss of millions of dollars. Ledger, another hardware wallet provider, confirmed a data breach in June that compromised more than one million user email addresses.
Trezor noted that its desktop app would be in public beta until January, at which time its old browser-based Trezor Wallet would be deprecated.
Updated: 10-12-2020
Spanish Lawmakers Get Cryptocurrency In A Bid To Promote Industry
All 350 members of Spain’s lower house got 1 euro equivalent in cryptocurrency, and it’s not a donation.
Members of Spain’s lower house of Congress saw a surprise in their inboxes, the equivalent of 1 euro in crypto.
As reported by Spanish news outfit ABC, the plan is spearheaded by Tutellus, a decentralized platform looking to tokenize education technology, and the Blockchain Observatory. The project aims to promote the use of cryptocurrencies in the country.
All 350 members of Spain’s lower house, or the Congress of Deputies, received the equivalent of 1 euro in cryptocurrency in their emails. Miguel Caballero, Tutellus founder, said the goal is to raise awareness about the future role of cryptocurrencies in society:
“We have explained to your honorable members that we are in a time of profound change in the use of money, in addition to highlighting the important role that cryptocurrencies have today.”
Caballero said the cryptocurrency “is not a donation” and acknowledged that some congress members might be more familiar with crypto. But for those who no experience with cryptocurrencies yet, Caballero said, this is an opportunity to learn more.
Spain is not the first country to send cryptocurrencies to lawmakers. The political action committee (PAC) of the Chamber of Digital Commerce sent $50 worth of Bitcoin to all 541 members of Congress in early October, reported Decrypt.
Spanish banks have been more interested in cryptocurrencies and blockchain in the past few years. Santander partnered with Ripple for a blockchain-based payments platform while the Banco Bilbao Vizcaya Argentaria (BBVA) launched a study to explore zero-knowledge proofs and other cryptographic techniques.
The European Central Bank also announced it would look into a digital euro by 2021 and released a report diving into its possible impact on the retail market.
Updated: 1-19-2021
Trezor Crypto Wallet Warns Users Of Doppelgänger Scam App On Google Play
The fake Trezor app has been downloaded by at least 1,000 people on the Android’s app store Google Play.
Trezor, a major hardware cryptocurrency wallet supplier, has warned its users about a fake Trezor application on Google Play.
According to Trezor, the fake app is malicious and has no relation to Trezor or SatoshiLabs, a company that created the Trezor wallet. Announcing the news on Jan. 18, Trezor asked its clients to not install the malicious application, reminding users that they should never share their seed phrase with anyone.
This app is malicious and has no relation to Trezor or SatoshiLabs. Please, don’t install it.
Remember that you should never share your seed with anyone until your Trezor device asks you to do it! pic.twitter.com/6C3iKfPDnR
— Trezor (@Trezor) January 18, 2021
Trezor also provided its users with a short manual on using Trezor wallet with Android. In the manual, the company listed major third-party Trezor apps including Mycelium, Sentinel or Walleth.
At publishing time, the malicious app is still available on Google Play. As of Jan. 18, the app was reportedly downloaded more than 1,000 times. The doppelgänger app also has about 200 reviews on the app store, with the majority warning that it is a scam. “This app is a scam. Never enter your recovery phrase in anything except an official hardware Trezor. Anyone that asks for this phrase (besides a physical Trezor) is trying to scam you),” one supposed user wrote.
Trezor did not immediately respond to Cointelegraph’s request for comment.
This is not the first time that a fake app has been listed on Google Play. In May 2019, Cointelegraph reported on a malicious Google Play app imitating Trezor wallet. The app was found by ESET antivirus researchers, who said that they expect more crypto scam apps to enter the Android store as the crypto market grows.
Online scammers have been targeting other popular crypto companies to impersonate their apps on Google and steal money from users. In May 2020, a cybersecurity researcher discovered 22 malicious Google Chrome extensions imitating crypto services like Trezor’s rival Ledger and major Ether (ETH) wallet MetaMask.
Updated: 1-26-2022
Engineer Hacks Trezor Wallet, Recovers $2M In ‘Lost’ Crypto
Hacker helps Trezor One owner who forgot his wallet passcode and seed phrase to recover cryptocurrency funds valued over $2 million.
A computer engineer and hardware hacker has revealed how he managed to crack a Trezor One hardware wallet containing more than $2 million in funds.
Joe Grand — who is based in Portland and is also known by his hacker alias, Kingpin — uploaded a Youtube video explaining how he pulled off the ingenious hack.
After unsuccessfully trying to guess the security PIN 12 times, they decided to quit before the wallet automatically wiped itself after 16 incorrect guesses.
But with their investment growing to $2 million this year, they redoubled their efforts to access the funds.
Without their wallet’s seed phrase or PIN, the only way to retrieve the tokens was through hacking.
They reached out to Grand who spent 12 weeks of trial and error but eventually found a way to recover the lost PIN.
The key to this hack was that during a firmware update, the Trezor One wallets temporarily move the PIN and key to RAM, only to later move them back to flash once the firmware is installed.
Grand found that in the version of firmware installed on Reich’s wallet, this information was not moved but copied to the RAM, which means that if the hack fails and the RAM is erased, the information about the PIN and key would still be stored in flash.
After using a fault injection attack — a technique that alters the voltage going to the chip — Grand was able to surpass the security the microcontrollers have to prevent hackers from reading RAM, and obtained the PIN needed to access the wallet and the funds. Grand explained:
“We are basically causing misbehavior on the silicon chip inside the device in order to defeat security. And what ended up happening is that I was sitting here watching the computer screen and saw that I was able to defeat the security, the private information, the recovery seed, and the pin that I was going after popped up on the screen.”
According to a recent tweet from Trezor, this vulnerability, which allows the pin to be read from the wallet’s RAM, is an older one that has already been fixed for newer devices. But unless changes are made to the microcontroller, fault injection attacks still can pose a risk.
Updated: 1-28-2022
Trezor Removes Controversial Address Verification Protocol, Other Wallets Follow Suit
One week after introducing the Address Ownership Proof Protocol, or AOPP, the hardware wallet company backtracked on its decision due to customer privacy concerns.
Since 2019, Swiss financial crypto intermediaries have required proof of ownership of an external wallet’s address for Bitcoin withdrawals and deposits to their customers’ non-custodial wallets. One automated mechanism used for this is the Address Ownership Proof Protocol, or AOPP.
The Trezor hardware wallet introduced AOPP signing as part of its latest January update last week, allowing users to generate signatures that conform to the AOPP standard used in certain jurisdictions. On Jan. 28, Trezor announced that it will remove this protocol in the next Trezor Suite update “after careful consideration of recent feedback.”
Recent feedback refers to Reddit and Twitter users who were concerned that the use of AOPP signaled Trezor’s support for greater regulation and a disregard for a potential loss of privacy.
We will remove AOPP in our next Trezor Suite update in February.
More on our decision: https://t.co/hMDenbdjcg
— Trezor (@Trezor) January 28, 2022
In a blog post explaining the removal, Trezor admitted it “underestimated how this feature would be received,” but that the company “welcomes public scrutiny.” The fact that it listened to its users and reacted so quickly demonstrates the power of social media sentiment.
The hardware wallet maker claimed it is against the regulations that concern AOPP, namely the data leak risks associated with using a stringent identification process like Know Your Customer, or KYC, to buy Bitcoin. The company clarified its intent:
“Our sole aim was to make withdrawal to self-custody easier for users in countries with strict regulation, but we acknowledge that more harm than good could be done in the end if this were viewed as proactive compliance with regulations we do not agree with.”
Other hardware wallets such as Sparrow Wallet, Samourai Wallet and BlueWallet have also decided to follow Trezor and remove the automated protocol.
✅ @SparrowWallet – Removing AOPP next release
✅ @bluewalletio – Removing AOPP next release
✅ @Trezor – Removing AOPP next releaseCongrats to these projects for strength & resolve to listen to the community. Congrats to the community who successfully made their desires known https://t.co/RuqnxgbJfu
— Samourai Wallet (@SamouraiWallet) January 28, 2022
While the AOPP protocol may not directly or negatively impact users of non-custodial wallets, decentralization and freedom are central tenets to the crypto community who values privacy. The main concern is that the implementation of AOPP may set a precedent for increased government influence and surveillance.
Updated: 4-3-2022
Trezor Investigates Potential Data Breach As Users Cite Phishing Attacks
Numerous users on Twitter alarmed Trezor of an ongoing email phishing campaign specifically targeting Trezor users via their registered email addresses.
Cryptocurrency hardware wallet provider Trezor has begun investigating a possible data breach that may have compromised users’ email addresses and other personal information.
Earlier on Sunday, several users from the Crypto Twitter community warned about an ongoing email phishing campaign specifically targeting Trezor users via their registered email addresses.
Hey trezor, are you aware of a phishing campaign going on? I just received this email with my actual email on it. It looked very legit. pic.twitter.com/GF0Od6llr2
— josearkaos ⚡️ (@josearkanos) April 3, 2022
In the ongoing attack, several Trezor users have been contacted by unauthorized actors posing as the company — with the ultimate intention to steal funds by misleading unwary investors. As part of the attack, users received an email about downloading an application from the “trezor.us” domain, which is different from the official Trezor domain name, “trezor.io.”
We are investigating a potential data breach of an opt-in newsletter hosted on MailChimp.
A scam email warning of a data breach is circulating. Do not open any email originating from noreply@trezor.us, it is a phishing domain.
— Trezor (@Trezor) April 3, 2022
Trezor initially suspected that the compromised email addresses belong to a list of users who opted-in for newsletters, which was hosted on an American email marketing service provider Mailchimp.
Wow, @Trezor, this is the best phishing attempt I have seen in the last few years. I am really lucky I don’t have Trezor, because if I had, I would probably actually download that update. pic.twitter.com/DaBN2Oix11
— Tomáš Kafka (@keff85) April 2, 2022
Through Further Investigation, Trezor Announced:
“MailChimp have confirmed that their service has been compromised by an insider targeting crypto companies.”
While Trezor officially investigates to identify the total number of stolen email addresses, users are advised not to click on links coming from unofficial sources until further notice.
On March 19, New Jersey-based crypto financial institution BlockFi proactively confirmed a data breach to warn investors about the possibility of phishing attacks.
Regarding recent third-party data incident: pic.twitter.com/50z7IrQ1za
— BlockFi (@BlockFi) March 19, 2022
As Cointelegraph reported, hackers gained access to BlockFi’s client data that was hosted on Hubspot, a client relationship management platform. According to BlockFi:
“Hubspot has confirmed that an unauthorized third-party gained access to certain BlockFi client data housed on their platform.”
While specifics on the breached data are yet to be identified and revealed, BlockFi reassured users by highlighting that personal data — including passwords, government-issued IDs and social security numbers — “were never stored on Hubspot.”
Updated: 4-21-2022
Noncustodial Bitcoin Wallets Unbannable, Says Exec Behind Trezor Wallets
There are a few ways for regulators to limit the usage of noncustodial wallets, but there is no way to ban it completely, SatoshiLabs CFO said.
As regulators grow increasingly concerned about investors moving their cryptocurrency out of centralized exchanges, one industry exec has assessed the probability of a potential ban of noncustodial wallets.
Stepan Uherik, the chief financial officer of SatoshiLabs, the firm behind the Trezor hardware wallet, is confident that it’s highly unlikely that governments around the world could one day ban the use of noncustodial wallets.
“It’s very improbable that all the countries would ban noncustodial wallets, or any other aspect of Bitcoin’s peer-to-peer network for that matter,” the chief financial officer told Cointelegraph.
Uherik said that potential efforts to ban noncustodial wallets would likely be similar to certain countries banning things like cryptography or torrents in the past.
“The adoption of these technologies continued unabated. In some sense, governments’ attempts at banning certain technology are good marketing for said technology,” he noted.
Also known as self-custodial wallets, noncustodial cryptocurrency wallets are designed to grant the user full control of the owned crypto.
In contrast to custodial wallets, noncustodial wallets remove the need to rely on a third party that could recover, freeze or seize the user’s crypto assets. This makes the user solely responsible for storing the private keys.
As noncustodial wallets essentially enable users to “be their own bank,” many financial regulators and banking institutions became worried about the potential risks behind such tools.
Earlier this week, a major bank association in Russia proposed to criminalize certain use cases of noncustodial wallets due to the complexity of seizing crypto assets held in these wallets, among other reasons.
Previously, a European Parliament committee approved a regulatory update that could potentially interfere with the ability of exchanges to deal with noncustodial crypto wallets.
There are apparently a few ways for governments to limit the usage of noncustodial wallets but there is no possibility of a complete ban, according to the SatoshiLabs chief financial officer.
Governments could try to ban certain noncustodial wallets through mobile app stores as there are only two dominant mainstream mobile app providers, Google and Apple, Uherik suggested, adding:
“Such a ban would be easy to enact, but it would cover only a portion of noncustodial wallets and would likely motivate users to look beyond the popular app stores. Hardware and desktop wallets would be unaffected.”
Any efforts to ban noncustodial wallets would also lead to a strong backlash from consumer protection non-governmental organizations because such censorship “has no place in civilized countries,” he said.
Uherik also stated that open-sourced hardware wallets are resistant to any ban, while hardware wallet makers are in a better situation than most other Bitcoin firms regulatory-wise, because they don’t offer custodial solutions or financial services. He concluded:
“Governments can slow the adoption of Bitcoin, but Bitcoin will prevail in the end. Bitcoin is an idea whose time has come, and nobody can fight that.”
Updated: 5-22-2022
Intuit Sued Over Hack That Led To Theft Of Cryptocurrencies
* Trezor Users Fell Victim To Phishing Attack, According To Suit
* Illinois Man Claims He Lost $87,000 Worth Of Cryptocurrencies
Intuit Inc. was sued for failing to secure its email marketing service, which allegedly allowed hackers to steal cryptocurrencies from Trezor users.
Using a sophisticated phishing attack, hackers were earlier this month able to access cryptocurrency wallets sold by the Czech company Trezor, according to the lawsuit, filed Friday in federal court in San Jose.
Intuit’s Mailchimp email marketing service revealed on April 4 that hackers had penetrated its servers and harvested the “audience data” from 102 of its clients, including Trezor, according to the suit.
Using the data, the hackers sent phishing emails to Trezor users, warning them — falsely — that their accounts had been compromised and advising them to download a new version of what they claimed was the Trezor app, according to the suit. The phony app prompted users for their passwords and recovery codes, which the hackers used to clear out their digital wallets.
Intuit declined to comment on the lawsuit.
Alan Levinson, an Illinois man who filed the suit, said the hackers took cryptocurrencies worth $87,000 from his account.
The proposed class-action suit faults Intuit and its subsidiary Rocket Science Group LLC, which operates Mailchimp, but not Trezor. Intuit is accused of disregarding the rights of Trezor account holders by “failing to take adequate and reasonable measures to ensure that its data systems were protected.”
The hackers reportedly gained access to Mailchimp’s email accounts when one of its employees clicked on a malicious link in an email, according to the suit.
“Defendants fell victim to one of the oldest cybertricks in the book,” Levinson claims in the lawsuit.
The suit is Levinson v. Intuit, Inc., 22-cv-02477, in U.S. District Court, Northern District of California (San Jose.)
Updated: 5-5-2022
TurboTax Owner Intuit To Pay $141 Million Over ‘Deceptive’ Marketing Allegations
Software company to send check to nearly 4.4 million users; Intuit didn’t admit to wrongdoing in settlement.
Intuit Inc. agreed to pay $141 million to settle allegations its TurboTax software deceived low-income Americans into paying to file their taxes when they actually qualified to file for free.
As part of the settlement agreement, which was signed Wednesday by attorneys general in all 50 states and Washington, D.C., Intuit will send checks to nearly 4.4 million users who were affected. They will receive about $30 for each year they paid for services from 2016 to 2018. Customers who were affected will automatically receive notices in the mail.
Intuit said in a blog post Wednesday that it didn’t admit to wrongdoing and agreed to pay $141 million to put the matter behind it.
Shares of Intuit fell 2.6% to $419.54 Wednesday morning.
New York Attorney General Letitia James said her office opened an investigation into Intuit after a ProPublica story reported that the company was using deceptive digital tactics to steer low-income tax filers away from the federal free services they qualified for and toward TurboTax’s paid services.
The investigation led by Ms. James found that Intuit paid for online search ads that confused customers, sending those searching for the Internal Revenue Service’s free filing service toward TurboTax’s paid service. It also said TurboTax’s website never displayed or recommended the free filing program from the IRS, even though it promised to find them the right solution. Ms. James said 70% of taxpayers qualify for free filing through the IRS.
“Intuit cheated millions of low-income Americans out of free tax filing services they were entitled to,” said Ms. James. “This agreement should serve as a reminder to companies large and small that engaging in these deceptive marketing ploys is illegal.”
As part of the settlement, the Mountain View, Calif.-based software company was also ordered to pull its “free, free, free” advertising campaign, which allegedly promises free tax preparation services to customers only to later charge the majority of them after they have already inputted their personal and financial information.
The Federal Trade Commission also sued the company in March for misleading advertising. The agency asked a U.S. district court to stop Intuit from advertising that TurboTax users can file their taxes for free, saying that in many cases people don’t qualify for TurboTax’s free filing and are instead pushed to pay for services. Intuit said at the time that the FTC’s allegations weren’t credible.
Intuit said at the time that the FTC’s allegations weren’t credible and that it would challenge the complaint.
U.S. District Judge Charles Breyer last month denied the FTC’s request to stop the ads, saying Intuit had already stopped airing some of the ads.
Updated: 6-14-2022
What Happens If You Lose Or Break Your Hardware Crypto Wallet?
The safety of the recovery phrase is way more important than keeping the hardware wallet safe, according to executives at Ledger and Trezor.
Hardware cryptocurrency wallets are known for granting users full control of their crypto and providing more security, but such wallets are prone to risks such as theft, destruction or loss.
Does that mean that all your Bitcoin is lost forever if your hardware wallet is lost, burned or stolen? Not at all.
There are a number of options to restore cryptocurrency for someone who has lost access to their hardware wallet. The only requirement to recover crypto assets, in that case, would be maintaining access to the private keys.
A private key is a cryptographic string of letters and numbers that allows users to access crypto assets as well as to complete transactions and receive crypto.
Most crypto wallets usually provide a private key in the mnemonic form of a recovery phrase, which contains a human-readable backup allowing users to recover private keys.
The mnemonic form is typically enabled through BIP39, the most common standard used for generating seed phrases for crypto wallets.
Also referred to as a seed phrase, a BIP39 recovery phrase is basically a password consisting of 12 or 24 random words that are used to recover a cryptocurrency wallet.
Crypto wallet platforms typically generate a seed phrase at the very beginning of setting up a wallet, instructing users to write it down on paper.
Not Your Keys, Not Your Coins
According to executives at major hardware crypto wallet firms Ledger and Trezor, the safety of the recovery phrase is way more important than keeping the hardware wallet safe.
Keeping a private key safe is a guiding principle for the crypto community, embodied in the phrase: “Not your keys, not your coins.” The principle means that users are not really in control of their coins if they don’t own their private keys.
Both Ledger and Trezor wallets allow users to recover access to their wallets through a seed phrase by simply using another hardware wallet.
“A user could recover their wallet and funds on any of the other new Ledger wallets. Alternatively, they could also recover on a Trezor, SafePal or another hardware wallet device,” Ledger chief technology officer Charles Guillemet told Cointelegraph.
Users can also turn to software wallets to access their funds in case the hardware wallet was lost, stolen or destroyed.
“If you lost your Trezor, but you still have your recovery seed, you can recover your funds through many hardware wallets and software wallets in the market,” Trezor chief information security officer Jan Andraščík said.
According to the Ledger and Trezor executives, the list of compatible software wallets includes platforms such as Electrum, Exodus, MetaMask, Samourai, Wasabi, Spot and others.
Threats To A Backup Phrase
As the safety of the recovery phrase is the top priority in maintaining access to a crypto wallet, one may be wondering how to best protect the seed phrase.
“Preserving the seed is one of the most crucial topics in Bitcoin security,” Andraščík told Cointelegraph. He pointed out three main threats when it comes to BIP39 passwords: those caused by the user themselves, any type of natural or human-made disasters, or theft.
Loss of a recovery phase is very common: A wallet user could accidentally throw it out or just not understand the importance of it at the very beginning of setting up the wallet.
Users could also choose the wrong place to keep their recovery phrase, with one common mistake of simply putting the phrase online.
Crypto wallet users should never digitize their seed phrases in order to avoid unfortunate events such as hacking, Ledger’s Guillemet said, adding:
“It is paramount for users to secure the recovery phrase. It should be stored in a safe place and should not be digitized — in other words, don’t put your words in an email or a text file and don’t take photos.”
As such, most crypto wallets recommend their users simply write the seed phrase down on a piece of paper and store it in a safe place.
Tips To Protect The Recovery Phrase
In order to ensure reliable protection for the recovery phrase, one may go further than just writing it down on paper.
Ledger and Trezor executives provide a number of recommendations for crypto wallet users to boost the protection of their seed phrases, including using fire-proof storing capsules or steel plates to engrave the recovery phrase.
Other sophisticated methods to protect a seed phrase also include distributing backups between several groups of people and locations such as family, a safe box at the bank, or a secret spot in the garden.
One such method is known as Shamir Backup, allowing users to distribute their private keys into several parts that, together, are needed to recover the wallet.
While hardware wallet providers do their best to help users recover their assets in case they lose their wallets, there’s still nothing much they can do about losing a recovery phrase.
That is because the private key is designed to be held solely by the user of a noncustodial wallet, Trezor’s Andraščík said. He noted that the principle of noncustody and its security implications are completely against the idea of having some kind of “backup,” adding:
“If anyone has an opportunity to recover your Bitcoin, it means they have access to your Bitcoin, and you need to trust that these actors will always treat you with goodwill. We are getting rid of the need to trust, and rather, we encourage them to verify.”
“Ledger is also working to improve the user experience generally, removing the pain points without compromising security. That said, self-custody remains the DNA of blockchain and the DNA of Ledger. Users always remain in control,” Guillemet stated.
Updated: 7-6-2022
Hardware Crypto Wallet Sales Increase As Centralized Exchanges Scramble
Hardware wallet providers are seeing increases in revenue in this bear market as crypto investors withdraw assets off centralized exchanges.
Blockchain analysis firm Glassnode recently characterized the 2022 bear market as the worst on record. This seems to be the case due to events such as the war in Ukraine and rising inflation, coupled with serious problems among centralized crypto exchanges.
Yet, the bear market hasn’t negatively impacted all players in the crypto ecosystem. Hardware wallet providers seem to be benefiting from the massive amount of crypto withdrawals from centralized exchanges.
Pascal Gauthier, CEO of hardware wallet crypto firm Ledger, told Cointelegraph that the company’s revenue dropped about 90% during the 2018 crypto winter, but this hasn’t been the case this year. He said:
“Every quarter we are doing as much revenue as the whole of 2020, which was a very good year for Ledger. Right now year-on-year we are still up, which tells us that this bear market is different. It’s not a real bear market, but rather a bear market for centralized value propositions.”
To put this in perspective, Gauthier shared that the company shipped the most units of Ledger hardware wallets to date following Coinbase’s declaration of losses, which further suggested that users are not protected in the case of bankruptcy.
“We did $2 million a day in revenue following the release of this report, but it was just a peak because nothing bad actually happened to Coinbase. People just realized that their crypto wasn’t safe,” he said.
Gauthier elaborated that once Celsius froze users’ funds and rumors began circulating that BlockFi may do the same, Ledger, yet again, saw a major boost in business.
“People were rushing to our products to move funds to somewhere secure. We have now been seeing about six-times an increase in revenue week-on-week,” said Gauthier.
Ariel Wengroff, head of global communications and marketing at Ledger, further told Cointelegraph that the company recently formed a partnership with Best Buy, allowing consumers to buy Ledger products directly in-store, which has also increased sales. “We are launching in 256 more stores this July,” she said.
Ledger isn’t the only hardware wallet provider witnessing revenue gains in this bear market. Josef Tětek, Bitcoin analyst at Trezor, told Cointelegraph that the firm has also seen a significant surge of interest in Trezor devices.
“People are finding out that keeping their coins on exchanges and with custodians can be very risky, so they are naturally looking for self-custody options,” he said.
Tětek added that Trezor believes the liquidation cascade centralized lenders and exchanges are undergoing hasn’t fully played out yet.
In turn, he noted that Trezor is urging clients of exchanges and custodians to consider withdrawing their coins into their own wallets, at least for the time being. He added:
“As Warren Buffett famously said, we don’t know who’s swimming naked until the tide goes out — and the outflow has only just begun.”
Hardware wallet provider GridPlus has also seen an uptick in sales, which is mainly being generated by the nonfungible token (NFT) community.
Justin Leroux, CEO of hardware wallet GridPlus, told Cointelegraph that the firm has struggled to meet consumer demand recently, noting that they are ramping up production. He explained:
“The NFT community has been the largest sustained source of growth for us: New users drawn to crypto’s application layer need to immediately jump into self-custody to participate in NFT markets since centralized options are not readily available.”
Risks To Consider
According to findings from the research firm Mordor Intelligence, the global hardware wallet market was valued at $202.40 million in 2020.
This market is expected to be valued at $877.69 million by 2026, but today’s increasing demand for hardware wallets may influence this amount to equate to more.
While it’s noteable to see the hardware wallet market thriving during a bear cycle, it’s also important to mention that these products are not foolproof.
Alejandro Munoz-McDonald, a smart contract engineer at Immunefi — a bug bounty platform for Web3 products — told Cointelegraph that holding funds in a hardware wallet does not mean they are 100% safe. He said:
“A user can still fall victim to a phishing attack. They sign some transaction thinking it will do something else and then they get their NFT or tokens stolen.
Another attack vector could be through an infinite approval a user made to a contract that turns out to have a critical vulnerability. If a compromised contract has permission to transfer your funds, they’re as good as gone.”
Munoz-McDonald pointed out that Ledger and Trezor do a relatively good job of preventing attacks on surfacing a user’s private key. However, he noted that hardware wallets are still vulnerable to physical attacks.
“If an attacker gains physical access to your hardware wallet, it’s game over,” he said.
Moreover, hardware wallets are also vulnerable to data breaches, allowing attackers to access user information. Ledger witnessed a data breach on June 17, 2020, which prompted competing popular hardware wallet provider Trezor to issue the coupon code for consumers looking to move funds from Ledger to Trezor.
Munoz-McDonald still encourages users to self-custody their funds, noting that a hardware wallet is the best way to do so. “But, they also need to be educated on phishing schemes and have general online awareness,” he said.
Gauthier added that users must understand how Web3 works in order to securely self-custody their crypto assets. “Web3 gives ownership to users, whereas Web2 doesn’t. Decentralization may seem harder, but there is a price to pay for self-sovereignty,” he said.
Shedding light on this, Gauthier explained that while some crypto investors may find it easier to purchase and hold cryptocurrency through centralized exchanges, there could be fake underlying sentiments that are hard to initially catch.
“No one reads the fine print associated with these exchanges, therefore no one understood the Celsius business model to begin with. Scams are generally easy to use, so users need to do more due diligence,” he said.
Fortunately, as more crypto investors migrate to hardware wallets, a number of providers have started putting a large emphasis on user education.
Adam Lowe, creator of Arculus — a cold storage wallet solution — told Cointelegraph that it’s become clear that there are strong tailwinds driving the need for hardware wallets.
Given this, he believes that first-time crypto users should evaluate hardware wallets based on best-in-class security features and ease of use.
“If it looks too complicated to use, you will either stop using it or worse, lose access to your crypto,” he said.
In order to help users navigate this, Lowe mentioned that Arculus features an extensive FAQ page, along with how-to-videos to help users get started.
Leroux also stated that the most important security tool is education. According to Leroux, common attack vectors for hardware wallet users are social engineering and phishing attempts rather than sophisticated technical approaches.
“While we have seen browser extension scripts that hijack user wallets, it’s far more common to see users lose funds through fundamental missteps like improperly storing their seed phrase or being tricked into sharing it,” he said.
While much of this may sound daunting, it’s important to point out that many providers offer 24/7 support centers in addition to educational content.
It’s also noteworthy that both Ledger and Trezor wallets allow users to recover access to their wallets through a seed phrase by using another hardware wallet.
This feature can be extremely helpful if a user loses or has their wallet stolen. If this were to happen, a user could recover their funds on another Ledger, Trezor or SafePal hardware wallet.
Veronica Wong, CEO of SafePal, told Cointelegraph that the firm stresses the importance of keeping private keys safe and has seen an obvious growth curve in the last 30-days due to the troubles at the centralized crypto firm. She added:
“As crypto penetration and user base continue to grow, decentralized wallets will become the most important blockchain entrance to new users.
In the long run, wallets could even become an on-chain identity manager, protecting all your on-chain data and authorizations.”
Accommodating New Growth
Risks aside, the phrase “Not your keys, not your coins” has become more apparent to the crypto community than ever before. “The current challenges of accessing crypto on exchanges highlight the need for secure ownership of your private keys,” Lowe emphasized.
As a result, hardware wallet providers are preparing to accommodate a sudden surge in users. In order to do so, many are developing new products while ensuring that existing features meet market demands.
For example, Lowe shared that Arculus recently announced NFT support and WalletConnect integration, allowing consumers the ability to browse NFTs and DApps all within the Arculus ecosystem.
Gauthier also explained that Ledger has been focused on evolving its products for Web3, noting that the company just announced “clear signing” technology for NFTs.
While the Ledger Nano S Plus was designed with NFT collectors in mind, Gauthier explained that the clear signing functionality was officially implemented during “Ledger Op3n,” an event that took place on June 22 this year in New York.
“No one is doing clear signing for NFTs – everyone is just sending NFTs blindly left and right, which is a terrible thing to do,” he commented. Clear signing aims to provide all the details on a transaction.
In turn, Gauthier added that hardware wallet providers must focus on certain features moving forward such as bigger screens, more memory, and additional connectivity.
While accommodating NFT growth is critical, Tětek mentioned that Trezor is exploring options to implement Lighting Network capabilities for its users, which will help make Bitcoin transactions faster and cheaper.
According to a Trezor blog post, this will ultimately make Bitcoin more convenient to use as a means of payment.
This all boils down to the urgency for crypto investors to take personal security more seriously. “Self-custody is a fundamental requirement for both financial self-sovereignty and using permissionless decentralized systems.
If you’re using centralized exchanges exclusively, you’re not using crypto, you’re just spot trading IOUs on a company’s database,” Leroux remarked.
Updated: 8-31-2022
Hardware Wallet Trezor Enables Direct Crypto Purchases With MoonPay
The new integration with MoonPay and SatoshiLabs-founded Invity platform provides buy, sell and exchange features directly in the Trezor wallet.
Hardware walletcompany Trezor is moving to enable direct crypto purchases with a new partnership with the crypto fintech startup MoonPay.
Trezor, Czech Republic-based hardware wallet provider, has partnered with MoonPay to allow its customers to buy crypto directly in their hardware wallet, according to an announcement on Wednesday.
Backed by major industry investors including Tiger Global and Coatue, MoonPay is a crypto payment service that allows users to buy and sell cryptocurrencies and nonfungible tokens (NFTs) using debit cards, credit cards and other payment methods. In April 2022, the firm raised $87 million from investors like Justin Bieber and Snoop Dogg to focus on NFTs and Web3.
The collaboration with MoonPay builds on Trezor’s previous partnership with Invity, a crypto exchange comparison tool integrated directly into the wallet.
Like Trezor, Invity is a startup operating under the parent firm, SatoshiLabs. The platform connects clients with trusted partner exchanges to provide direct-to-custody trades with various payment methods. Combined, the three platforms provide buy, sell and exchange features directly in the Trezor wallet.
The new integration allows customers to buy and sell a wide number of cryptocurrencies through a noncustodial crypto wallet, helping users to better protect their funds.
At the time of writing, Trezor supports more than 1,000 cryptocurrencies, including Bitcoin and others.
“For users that have used MoonPay through their network of partners, they will have their account already created and payment methods saved, so will be able to transact in a few seconds,” Invity CEO Stepan Uherik told Cointelegraph.
For first time users of MoonPay, they require basic Know Your Customer checks based on transaction amount to comply with regulations prior to executing the first transactions, he added.
Uherik also noted that the buy feature is immediately available on Trezor via MoonPay, while the sell option is coming at a later date.
The latest news is yet another milestone for crypto purchases on Trezor, as the hardware wallet has been previously supporting crypto buys on its native app Trezor Suite via an in-app Trade feature.
The option has been available through the crypto exchange comparison tool created by Invity since at least late 2020, Trezor said in one of its blog posts.
“By allowing Trezor owners to buy crypto directly from their wallet, we’re tapping into a committed cohort of cryptocurrency users who take security very seriously,” MoonPay senior business development manager Antonio Talledo said.
“Through this partnership with MoonPay, we’re taking the lead to bring secure, borderless and easy financial freedom to billions,” Uherik noted.
Updated: 11-15-2022
Trezor Reports 300% Surge In Sales Revenue Due To FTX Contagion
The hardware wallet firm is certain that the latest uptick in demand is a result of investors rescuing their funds in the aftermath of the FTX failure.
Amid growing concerns over centralized cryptocurrency exchanges in the wake of the FTX crisis, investors are increasingly moving to hardware crypto wallets.
A major hardware wallet provider, Trezor, has recorded a major uptick in wallet sales in the aftermath of the FTX contagion, the firm’s brand ambassador Josef Tetek told Cointelegraph on Nov. 15.
Trezor saw its sales revenue surge 300% week-on-week and it’s still growing, Tetek reported, adding that the current sales are higher than a year ago when Bitcoin reached its all-time highs at $68,000. Trezor has also recorded a significant spike in its website traffic, which increased 350% over the same period, the exec noted.
According to Tetek, Trezor is quite certain that the uptick in new wallet users was a result of issues with FTX, a crypto exchange at the center of the latest industry scandal involving the misappropriation of user funds. The spike in demand for Trezor wallets started early last week, exactly when “rumors of the FTX insolvency started circulating,” Tetek reported.
Trezor expects further growth in new users in the near future as the failure of middlemen in crypto would only continue to unfold, Tetek suggested, stating:
“We expect this trend to continue in the short to mid term, as the contagion of FTX failure continues to unwind and Bitcoin or cryptocurrency holders lose trust in custodians and finally start to explore their options to self-custody their digital assets.”
According to the executive, Trezor is able to satisfy current levels of demand in the short to medium term. “Even if sales continue at this elevated rate, we are confident there would be a limited impact on our stock in the longer term, as we were already planning for an uptick in sales,” Tetek said.
He also noted that Trezor doesn’t plan to increase the prices for its hardware wallets in line with its vision to make “self-custody accessible to all.”
Despite the spike in demand and the associated increase in support requests, Trezor isn’t planning to expand its hiring. “We did not have to downscale as we were prepared for a prolonged and deep bear market,” Tetek stated, adding that Trezor currently employs a total of 100 people working in multiple locations, with the majority based in Prague.
Cryptocurrency investors have been increasingly moving to self-custody with software and hardware wallets, with exchange outflows nearing all-time highs by mid-November 2022.
Ledger, a major rival hardware wallet supplier, has recorded a significant surge in demand for its devices recently as well. The French cold wallet firm saw one of its highest traffic days ever shortly after FTX stopped all crypto withdrawals last week, triggering inventors to offload their funds from exchanges to cold storage as soon as possible.
Amid the ongoing FTX contagion, even some of the biggest crypto exchanges started promoting the need for self-custody. Binance CEO Changpeng Zhao admitted on Nov. 14 that centralized exchanges may no longer be necessary as investors would shift to self-custodial solutions like hardware or software wallets.
“If we can have a way to allow people to hold their own assets in their own custody securely and easily, that 99% of the general population can do it, centralized exchanges will not exist or probably don’t need to exist, which is great,” the CEO said.
Updated: 4-19-2023
Trezor Wallet Betrays Customers By Implementing CoinJoin
Wasabi coordinator zkSNACKs has been using a chain surveillance company to screen incoming UTXOs for their coinjoin for over a year. This is an unnecessary and disturbing practice for a supposedly privacy-focused company to be involved in.
By choosing Wasabi as its coinjoin partner, Trezor has destroyed all trust in its company. If you can’t trust a company with your privacy, why would you trust their hardware wallets or firmware?
Doing a coinjoin will not erase records of your purchase of KYC Bitcoin, but it can provide good forward privacy (sending, spending) if used properly.
Meanwhile Trezor’s version: Trezor Model T users can now hide their transaction history and balance while purchasing, donating and making other transactions with Bitcoin.
Cryptocurrency hardware wallet firm Trezor is expanding the privacy of Bitcoin transactions through collaboration with the privacy-focused Wasabi Wallet.
Trezor has rolled out the privacy-enabling CoinJoin feature on its hardware wallets, allowing users to enhance the privacy and security of Bitcoin transactions.
In the announcement on April 19, Trezor noted that the new function is immediately live on the company’s Trezor Model T wallet.
The company plans to enable the CoinJoin option for its first hardware wallet, the Model One, in the near future.
CoinJoin is a process used to anonymize Bitcoin transactions that enables users to send their BTC as part of a large collaborative transfer and obfuscate transaction history.
The method was introduced by former Bitcoin core developer Gregory Maxwell in August 2013, providing an option to send BTC transactions more privately.
Trezor’s new collaboration with Wasabi enables the CoinJoin option on its wallets and allows users to hide their transactions and balances while purchasing, donating and making other transactions with Bitcoin.
In order to enable CoinJoin, users need to open a new CoinJoin account on the main Trezor menu. The selection of the new CoinJoin feature is available alongside other account types, including Segregated Witness (SegWit) and Bitcoin Taproot accounts.
To enable maximum privacy, the CoinJoin feature on Trezor also prompts users to allow the anonymous communication protocol, Tor.
“Coinjoin in Trezor is optional, and users must first send their coins to a specific CoinJoin account if they wish to use this function. If users choose not to use CoinJoin, nothing changes for them,” Trezor’s Bitcoin analyst Josef Tetek told Cointelegraph.
As Coinjoin enables more privacy, coinjoined transactions are somewhat more costly, as they require users to pay a coordinator fee, Tetek said, noting:
“When entering a CoinJoin, users also pay a 0.3% coordinator fee and the mining fee. Remixes — further CoinJoin rounds — have no coordinator fee. There is no additional fee when spending coinjoined outputs.”
Unlike the coordinator fee, mining fees are charged with any other Bitcoin transactions. As such, users must pay a mining fee for each round for CoinJoin.
Apart from fees, the CoinJoin function is also associated with longer transaction times. Setting up a conjoin account discovery alone may take significantly longer than regular account discovery due to downloading whole blocks and using a slower connection on Tor.
“The CoinJoin process itself can take up to several hours. Afterward, the outputs can be spent in the same fashion as any other Bitcoin outputs,” Tetek stated.
Trezor CEO Matěj Žák emphasized that Trezor values privacy as the most important asset of individuals. “Consequently, we’re delighted that we’ve found a way for our community to keep their Bitcoin history private,” he noted.
According to the firm, Trezor is the first hardware wallet to implement CoinJoin, following in the footsteps of software wallets like Wasabi.
Updated: 4-20-2023
Censorship Concerns Grow As Trezor Integrates ‘CoinJoin’
Trezor is hiding comments that highlights the censorship concerns of its integration of CoinJoin — a Bitcoin privacy technology.
Trezor’s integration of CoinJoin is driving the community wild with concerns about the hardware wallet company censoring Bitcoin (BTC) transactions.
Trezor Implements CoinJoin
On April 19, the hardware wallet manufacturer announced implementing CoinJoin in collaboration with Wasabi Wallet.
Trezor said the new feature would improve users’ transactions’ security and privacy. The firm said the new function is available on its Trezor Model T wallet — adding that it would be integrated to Model One later.
CoinJoin usually combines multiple transactions to obfuscate users’ transactions to enhance privacy.
This makes it difficult to trace these transactions to a specific individual, as numerous users are pulled into one transaction.
Trezor said the CoinJoin feature would be available to users by clicking the “Anonymize” button. The degree of privacy is determined by the number of CoinJoin rounds the user prefers.
The firm added that the rest of the process is automated and requires no active participation from the user. The feature attracts a 0.3% fee of the amount that the user wants to obfuscate,
Community Highlights Censorship Concerns
The crypto community criticized Trezor’s new feature — many citing the censorship concerns that come with it.
The host of the Proof of Decentralization Podcast Chris Blec highlighted this concern, saying “the terms of service of Wasabi Wallet (zkSNACKs), which will be providing Trezor’s new CoinJoin feature gives” room for censorship.
Blec Said:
“Wasabi’s tool is a total capitulation to government censorship. It blocks BTC transactions that are for things like buying guns & ammo, sexual content, alleged copyright violations, credit repair services & much more. It also states that they are under no obligation to tell you why you’re blocked.”
A rival privacy firm Samourai Wallet also highlighted this concern in several tweets. According to the firm, Trezor’s new integration is a pipeline to surveillance.
Meanwhile, the hidden reply on Trezor’s CoinJoin announcement showed it hid all the responses that expressed these censorship concerns.
Trezor has yet to respond to our request for comment as of press time.
Related Articles:
Bitcoin Information & Resources (#GotBitcoin?)
How HBCUs Are Prepping Black Students For Blockchain Careers
Why Every US Congressman Just Got Sent Some ‘American’ Bitcoin
CME Sounding Out Crypto Traders To Gauge Market Demand For Ether Futures, Options
Bitcoin Drops To $10,446.83 As CFTC Charges BitMex With Illegally Operating Derivatives Exchange
BitcoinACKs Lets You Track Bitcoin Development And Pay Coders For Their Work
One Of Hal Finney’s Lost Contributions To Bitcoin Core To Be ‘Resurrected’ (#GotBitcoin?)
Cross-chain Money Markets, Latest Attempt To Bring Liquidity To DeFi
Memes Mean Mad Money. Those Silly Defi Memes, They’re Really Important (#GotBitcoin?)
Bennie Overton’s Story About Our Corrupt U.S. Judicial, Global Financial Monetary System And Bitcoin
Stop Fucking Around With Public Token Airdrops In The United States (#GotBitcoin?)
Mad Money’s Jim Cramer Will Invest 1% Of Net Worth In Bitcoin Says, “Gold Is Dangerous”
State-by-state Licensing For Crypto And Payments Firms In The Us Just Got Much Easier (#GotBitcoin?)
Bitcoin (BTC) Ranks As World 6Th Largest Currency
Pomp Claims He Convinced Jim Cramer To Buy Bitcoin
Traditional Investors View Bitcoin As If It Were A Technology Stock
Mastercard Releases Platform Enabling Central Banks To Test Digital Currencies (#GotBitcoin?)
Being Black On Wall Street. Top Black Executives Speak Out About Racism (#GotBitcoin?)
Tesla And Bitcoin Are The Most Popular Assets On TradingView (#GotBitcoin?)
From COVID Generation To Crypto Generation (#GotBitcoin?)
Right-Winger Tucker Carlson Causes Grayscale Investments To Pull Bitcoin Ads
Bitcoin Has Lost Its Way: Here’s How To Return To Crypto’s Subversive Roots
Cross Chain Is Here: NEO, ONT, Cosmos And NEAR Launch Interoperability Protocols (#GotBitcoin?)
Crypto Trading Products Enter The Mainstream With A Number Of Inherent Advantages (#GotBitcoin?)
Crypto Goes Mainstream With TV, Newspaper Ads (#GotBitcoin?)
A Guarded Generation: How Millennials View Money And Investing (#GotBitcoin?)
Blockchain-Backed Social Media Brings More Choice For Users
California Moves Forward With Digital Asset Bill (#GotBitcoin?)
Walmart Adds Crypto Cashback Through Shopping Loyalty Platform StormX (#GotBitcoin?)
Congressman Tom Emmer To Lead First-Ever Crypto Town Hall (#GotBitcoin?)
Why It’s Time To Pay Attention To Mexico’s Booming Crypto Market (#GotBitcoin?)
Bitcoin Developer Amir Taaki, “We Can Crash National Economies” (#GotBitcoin?)
Veteran Crypto And Stocks Trader Shares 6 Ways To Invest And Get Rich
Is Chainlink Blazing A Trail Independent Of Bitcoin?
Nearly $10 Billion In BTC Is Held In Wallets Of 8 Crypto Exchanges (#GotBitcoin?)
SEC Enters Settlement Talks With Alleged Fraudulent Firm Veritaseum (#GotBitcoin?)
Blockstream’s Samson Mow: Bitcoin’s Block Size Already ‘Too Big’
Attorneys Seek Bank Of Ireland Execs’ Testimony Against OneCoin Scammer (#GotBitcoin?)
OpenLibra Plans To Launch Permissionless Fork Of Facebook’s Stablecoin (#GotBitcoin?)
Tiny $217 Options Trade On Bitcoin Blockchain Could Be Wall Street’s Death Knell (#GotBitcoin?)
Class Action Accuses Tether And Bitfinex Of Market Manipulation (#GotBitcoin?)
Sharia Goldbugs: How ISIS Created A Currency For World Domination (#GotBitcoin?)
Bitcoin Eyes Demand As Hong Kong Protestors Announce Bank Run (#GotBitcoin?)
How To Securely Transfer Crypto To Your Heirs
‘Gold-Backed’ Crypto Token Promoter Karatbars Investigated By Florida Regulators (#GotBitcoin?)
Crypto News From The Spanish-Speaking World (#GotBitcoin?)
Financial Services Giant Morningstar To Offer Ratings For Crypto Assets (#GotBitcoin?)
‘Gold-Backed’ Crypto Token Promoter Karatbars Investigated By Florida Regulators (#GotBitcoin?)
The Original Sins Of Cryptocurrencies (#GotBitcoin?)
Bitcoin Is The Fraud? JPMorgan Metals Desk Fixed Gold Prices For Years (#GotBitcoin?)
Israeli Startup That Allows Offline Crypto Transactions Secures $4M (#GotBitcoin?)
[PSA] Non-genuine Trezor One Devices Spotted (#GotBitcoin?)
Bitcoin Stronger Than Ever But No One Seems To Care: Google Trends (#GotBitcoin?)
First-Ever SEC-Qualified Token Offering In US Raises $23 Million (#GotBitcoin?)
You Can Now Prove A Whole Blockchain With One Math Problem – Really
Crypto Mining Supply Fails To Meet Market Demand In Q2: TokenInsight
$2 Billion Lost In Mt. Gox Bitcoin Hack Can Be Recovered, Lawyer Claims (#GotBitcoin?)
Fed Chair Says Agency Monitoring Crypto But Not Developing Its Own (#GotBitcoin?)
Wesley Snipes Is Launching A Tokenized $25 Million Movie Fund (#GotBitcoin?)
Mystery 94K BTC Transaction Becomes Richest Non-Exchange Address (#GotBitcoin?)
A Crypto Fix For A Broken International Monetary System (#GotBitcoin?)
Four Out Of Five Top Bitcoin QR Code Generators Are Scams: Report (#GotBitcoin?)
Waves Platform And The Abyss To Jointly Launch Blockchain-Based Games Marketplace (#GotBitcoin?)
Bitmain Ramps Up Power And Efficiency With New Bitcoin Mining Machine (#GotBitcoin?)
Ledger Live Now Supports Over 1,250 Ethereum-Based ERC-20 Tokens (#GotBitcoin?)
Miss Finland: Bitcoin’s Risk Keeps Most Women Away From Cryptocurrency (#GotBitcoin?)
Artist Akon Loves BTC And Says, “It’s Controlled By The People” (#GotBitcoin?)
Ledger Live Now Supports Over 1,250 Ethereum-Based ERC-20 Tokens (#GotBitcoin?)
Co-Founder Of LinkedIn Presents Crypto Rap Video: Hamilton Vs. Satoshi (#GotBitcoin?)
Crypto Insurance Market To Grow, Lloyd’s Of London And Aon To Lead (#GotBitcoin?)
No ‘AltSeason’ Until Bitcoin Breaks $20K, Says Hedge Fund Manager (#GotBitcoin?)
NSA Working To Develop Quantum-Resistant Cryptocurrency: Report (#GotBitcoin?)
Custody Provider Legacy Trust Launches Crypto Pension Plan (#GotBitcoin?)
Vaneck, SolidX To Offer Limited Bitcoin ETF For Institutions Via Exemption (#GotBitcoin?)
Russell Okung: From NFL Superstar To Bitcoin Educator In 2 Years (#GotBitcoin?)
Bitcoin Miners Made $14 Billion To Date Securing The Network (#GotBitcoin?)
Why Does Amazon Want To Hire Blockchain Experts For Its Ads Division?
Argentina’s Economy Is In A Technical Default (#GotBitcoin?)
Blockchain-Based Fractional Ownership Used To Sell High-End Art (#GotBitcoin?)
Portugal Tax Authority: Bitcoin Trading And Payments Are Tax-Free (#GotBitcoin?)
Bitcoin ‘Failed Safe Haven Test’ After 7% Drop, Peter Schiff Gloats (#GotBitcoin?)
Bitcoin Dev Reveals Multisig UI Teaser For Hardware Wallets, Full Nodes (#GotBitcoin?)
Bitcoin Price: $10K Holds For Now As 50% Of CME Futures Set To Expire (#GotBitcoin?)
Bitcoin Realized Market Cap Hits $100 Billion For The First Time (#GotBitcoin?)
Stablecoins Begin To Look Beyond The Dollar (#GotBitcoin?)
Bank Of England Governor: Libra-Like Currency Could Replace US Dollar (#GotBitcoin?)
Binance Reveals ‘Venus’ — Its Own Project To Rival Facebook’s Libra (#GotBitcoin?)
The Real Benefits Of Blockchain Are Here. They’re Being Ignored (#GotBitcoin?)
CommBank Develops Blockchain Market To Boost Biodiversity (#GotBitcoin?)
SEC Approves Blockchain Tech Startup Securitize To Record Stock Transfers (#GotBitcoin?)
SegWit Creator Introduces New Language For Bitcoin Smart Contracts (#GotBitcoin?)
You Can Now Earn Bitcoin Rewards For Postmates Purchases (#GotBitcoin?)
Bitcoin Price ‘Will Struggle’ In Big Financial Crisis, Says Investor (#GotBitcoin?)
Fidelity Charitable Received Over $100M In Crypto Donations Since 2015 (#GotBitcoin?)
Would Blockchain Better Protect User Data Than FaceApp? Experts Answer (#GotBitcoin?)
Just The Existence Of Bitcoin Impacts Monetary Policy (#GotBitcoin?)
What Are The Biggest Alleged Crypto Heists And How Much Was Stolen? (#GotBitcoin?)
IRS To Cryptocurrency Owners: Come Clean, Or Else!
Coinbase Accidentally Saves Unencrypted Passwords Of 3,420 Customers (#GotBitcoin?)
Bitcoin Is A ‘Chaos Hedge, Or Schmuck Insurance‘ (#GotBitcoin?)
Bakkt Announces September 23 Launch Of Futures And Custody
Coinbase CEO: Institutions Depositing $200-400M Into Crypto Per Week (#GotBitcoin?)
Researchers Find Monero Mining Malware That Hides From Task Manager (#GotBitcoin?)
Crypto Dusting Attack Affects Nearly 300,000 Addresses (#GotBitcoin?)
A Case For Bitcoin As Recession Hedge In A Diversified Investment Portfolio (#GotBitcoin?)
SEC Guidance Gives Ammo To Lawsuit Claiming XRP Is Unregistered Security (#GotBitcoin?)
15 Countries To Develop Crypto Transaction Tracking System: Report (#GotBitcoin?)
US Department Of Commerce Offering 6-Figure Salary To Crypto Expert (#GotBitcoin?)
Mastercard Is Building A Team To Develop Crypto, Wallet Projects (#GotBitcoin?)
Canadian Bitcoin Educator Scams The Scammer And Donates Proceeds (#GotBitcoin?)
Amazon Wants To Build A Blockchain For Ads, New Job Listing Shows (#GotBitcoin?)
Shield Bitcoin Wallets From Theft Via Time Delay (#GotBitcoin?)
Blockstream Launches Bitcoin Mining Farm With Fidelity As Early Customer (#GotBitcoin?)
Commerzbank Tests Blockchain Machine To Machine Payments With Daimler (#GotBitcoin?)
Man Takes Bitcoin Miner Seller To Tribunal Over Electricity Bill And Wins (#GotBitcoin?)
Bitcoin’s Computing Power Sets Record As Over 100K New Miners Go Online (#GotBitcoin?)
Walmart Coin And Libra Perform Major Public Relations For Bitcoin (#GotBitcoin?)
Judge Says Buying Bitcoin Via Credit Card Not Necessarily A Cash Advance (#GotBitcoin?)
Poll: If You’re A Stockowner Or Crypto-Currency Holder. What Will You Do When The Recession Comes?
1 In 5 Crypto Holders Are Women, New Report Reveals (#GotBitcoin?)
Beating Bakkt, Ledgerx Is First To Launch ‘Physical’ Bitcoin Futures In Us (#GotBitcoin?)
Facebook Warns Investors That Libra Stablecoin May Never Launch (#GotBitcoin?)
Government Money Printing Is ‘Rocket Fuel’ For Bitcoin (#GotBitcoin?)
Bitcoin-Friendly Square Cash App Stock Price Up 56% In 2019 (#GotBitcoin?)
Safeway Shoppers Can Now Get Bitcoin Back As Change At 894 US Stores (#GotBitcoin?)
TD Ameritrade CEO: There’s ‘Heightened Interest Again’ With Bitcoin (#GotBitcoin?)
Venezuela Sets New Bitcoin Volume Record Thanks To 10,000,000% Inflation (#GotBitcoin?)
Newegg Adds Bitcoin Payment Option To 73 More Countries (#GotBitcoin?)
China’s Schizophrenic Relationship With Bitcoin (#GotBitcoin?)
More Companies Build Products Around Crypto Hardware Wallets (#GotBitcoin?)
Bakkt Is Scheduled To Start Testing Its Bitcoin Futures Contracts Today (#GotBitcoin?)
Bitcoin Network Now 8 Times More Powerful Than It Was At $20K Price (#GotBitcoin?)
Crypto Exchange BitMEX Under Investigation By CFTC: Bloomberg (#GotBitcoin?)
“Bitcoin An ‘Unstoppable Force,” Says US Congressman At Crypto Hearing (#GotBitcoin?)
Bitcoin Network Is Moving $3 Billion Daily, Up 210% Since April (#GotBitcoin?)
Cryptocurrency Startups Get Partial Green Light From Washington
Fundstrat’s Tom Lee: Bitcoin Pullback Is Healthy, Fewer Searches Аre Good (#GotBitcoin?)
Bitcoin Lightning Nodes Are Snatching Funds From Bad Actors (#GotBitcoin?)
The Provident Bank Now Offers Deposit Services For Crypto-Related Entities (#GotBitcoin?)
Bitcoin Could Help Stop News Censorship From Space (#GotBitcoin?)
US Sanctions On Iran Crypto Mining — Inevitable Or Impossible? (#GotBitcoin?)
US Lawmaker Reintroduces ‘Safe Harbor’ Crypto Tax Bill In Congress (#GotBitcoin?)
EU Central Bank Won’t Add Bitcoin To Reserves — Says It’s Not A Currency (#GotBitcoin?)
The Miami Dolphins Now Accept Bitcoin And Litecoin Crypt-Currency Payments (#GotBitcoin?)
Trump Bashes Bitcoin And Alt-Right Is Mad As Hell (#GotBitcoin?)
Goldman Sachs Ramps Up Development Of New Secret Crypto Project (#GotBitcoin?)
Blockchain And AI Bond, Explained (#GotBitcoin?)
Grayscale Bitcoin Trust Outperformed Indexes In First Half Of 2019 (#GotBitcoin?)
XRP Is The Worst Performing Major Crypto Of 2019 (GotBitcoin?)
Bitcoin Back Near $12K As BTC Shorters Lose $44 Million In One Morning (#GotBitcoin?)
As Deutsche Bank Axes 18K Jobs, Bitcoin Offers A ‘Plan ฿”: VanEck Exec (#GotBitcoin?)
Argentina Drives Global LocalBitcoins Volume To Highest Since November (#GotBitcoin?)
‘I Would Buy’ Bitcoin If Growth Continues — Investment Legend Mobius (#GotBitcoin?)
Lawmakers Push For New Bitcoin Rules (#GotBitcoin?)
Facebook’s Libra Is Bad For African Americans (#GotBitcoin?)
Crypto Firm Charity Announces Alliance To Support Feminine Health (#GotBitcoin?)
Canadian Startup Wants To Upgrade Millions Of ATMs To Sell Bitcoin (#GotBitcoin?)
Trump Says US ‘Should Match’ China’s Money Printing Game (#GotBitcoin?)
Casa Launches Lightning Node Mobile App For Bitcoin Newbies (#GotBitcoin?)
Bitcoin Rally Fuels Market In Crypto Derivatives (#GotBitcoin?)
World’s First Zero-Fiat ‘Bitcoin Bond’ Now Available On Bloomberg Terminal (#GotBitcoin?)
Buying Bitcoin Has Been Profitable 98.2% Of The Days Since Creation (#GotBitcoin?)
Another Crypto Exchange Receives License For Crypto Futures
From ‘Ponzi’ To ‘We’re Working On It’ — BIS Chief Reverses Stance On Crypto (#GotBitcoin?)
These Are The Cities Googling ‘Bitcoin’ As Interest Hits 17-Month High (#GotBitcoin?)
Venezuelan Explains How Bitcoin Saves His Family (#GotBitcoin?)
Quantum Computing Vs. Blockchain: Impact On Cryptography
This Fund Is Riding Bitcoin To Top (#GotBitcoin?)
Bitcoin’s Surge Leaves Smaller Digital Currencies In The Dust (#GotBitcoin?)
Bitcoin Exchange Hits $1 Trillion In Trading Volume (#GotBitcoin?)
Bitcoin Breaks $200 Billion Market Cap For The First Time In 17 Months (#GotBitcoin?)
You Can Now Make State Tax Payments In Bitcoin (#GotBitcoin?)
Religious Organizations Make Ideal Places To Mine Bitcoin (#GotBitcoin?)
Goldman Sacs And JP Morgan Chase Finally Concede To Crypto-Currencies (#GotBitcoin?)
Bitcoin Heading For Fifth Month Of Gains Despite Price Correction (#GotBitcoin?)
Breez Reveals Lightning-Powered Bitcoin Payments App For IPhone (#GotBitcoin?)
Big Four Auditing Firm PwC Releases Cryptocurrency Auditing Software (#GotBitcoin?)
Amazon-Owned Twitch Quietly Brings Back Bitcoin Payments (#GotBitcoin?)
JPMorgan Will Pilot ‘JPM Coin’ Stablecoin By End Of 2019: Report (#GotBitcoin?)
Is There A Big Short In Bitcoin? (#GotBitcoin?)
Coinbase Hit With Outage As Bitcoin Price Drops $1.8K In 15 Minutes
Samourai Wallet Releases Privacy-Enhancing CoinJoin Feature (#GotBitcoin?)
There Are Now More Than 5,000 Bitcoin ATMs Around The World (#GotBitcoin?)
You Can Now Get Bitcoin Rewards When Booking At Hotels.Com (#GotBitcoin?)
North America’s Largest Solar Bitcoin Mining Farm Coming To California (#GotBitcoin?)
Bitcoin On Track For Best Second Quarter Price Gain On Record (#GotBitcoin?)
Bitcoin Hash Rate Climbs To New Record High Boosting Network Security (#GotBitcoin?)
Bitcoin Exceeds 1Million Active Addresses While Coinbase Custodies $1.3B In Assets
Why Bitcoin’s Price Suddenly Surged Back $5K (#GotBitcoin?)
Zebpay Becomes First Exchange To Add Lightning Payments For All Users (#GotBitcoin?)
Coinbase’s New Customer Incentive: Interest Payments, With A Crypto Twist (#GotBitcoin?)
The Best Bitcoin Debit (Cashback) Cards Of 2019 (#GotBitcoin?)
Real Estate Brokerages Now Accepting Bitcoin (#GotBitcoin?)
Ernst & Young Introduces Tax Tool For Reporting Cryptocurrencies (#GotBitcoin?)
Recession Is Looming, or Not. Here’s How To Know (#GotBitcoin?)
How Will Bitcoin Behave During A Recession? (#GotBitcoin?)
Many U.S. Financial Officers Think a Recession Will Hit Next Year (#GotBitcoin?)
Definite Signs of An Imminent Recession (#GotBitcoin?)
What A Recession Could Mean for Women’s Unemployment (#GotBitcoin?)
Investors Run Out of Options As Bitcoin, Stocks, Bonds, Oil Cave To Recession Fears (#GotBitcoin?)
Goldman Is Looking To Reduce “Marcus” Lending Goal On Credit (Recession) Caution (#GotBitcoin?)


Leave a Reply
You must be logged in to post a comment.