What Are The Biggest Crypto Heists, Rug Pulls And Exit Scams And How Much Was Stolen? (#GotBitcoin)
As the appeal of cryptocurrency has grown, so has the opportunity for scammers to part naive investors from their money. 2020 has been no exception, with cryptocurrency and blockchain forensics company Ciphertrace dubbing it “the year of the exit scam.” What Are The Biggest Crypto Heists And How Much Was Stolen? (#GotBitcoin)
Exit scams are not a new phenomenon, with a 2018 report conducted by Statis Group revealing over 80% of initial coin offerings (ICOs) in that year to have been fraudulent. Here, we explain exit scams and how to spot them, as well as a look at some of the biggest scams that have been discovered by various researchers.
What Are Exit Scams?
The premise of cryptocurrency is simple, a new ICO launches, claiming to offer lucrative returns for investors. Investors can’t believe their luck and clamor to buy in. The business runs for some time on the back of the invested capital, but, sooner or later, disaster strikes and the company shuts down, often with no explanation.
After a while, it becomes obvious that the company is gone for good, along with the invested funds. The poisoned chalice of crypto’s decentralized nature often means that investors are left in the dark when trying to recoup or trace their pilfered funds.
How To Spot An Exit Scam
Many exit scams have tell-tale signs that investors should look out for. The financial content site Investopedia has a handy list of key characteristics.
First, exit scams often have inconsistent or misleading information about the team behind the project. When scouting potential investment opportunities, investors should scour for information on key members of any ICO.
It’s important to remember that online credibility can be faked by purchasing likes, profiles and followers on social media. Celebrity endorsements with verified accounts could also ring alarm bells for investors. A fake Twitter account purporting to be Elon Musk, with a supposedly verified twitter account, raised over $155,000 as part of a 2018 Bitcoin scam.
Investors should verify the credentials of backers, team leaders and promoters of cryptocurrency projects. Although individuals may seem to be legitimate at first glance, brand new social media profiles and few followers or connections should raise eyebrows.
The most significant characteristic unifying exit scams in cryptocurrency is the promise of a huge return on investment (ROI) — chances are that it’s probably too good to be true.
Investors should always look through even the smallest details of what they are required to invest and what the company purports to be able to give back to them.
ICOs usually come with a white paper, setting out the design details of the project along with a business plan and other information. Investors should pursue all available information for ICOs, as any vagueness in the white papers should signal a big red flag.
When investing in an ICO, it’s vital to get an understanding of the business model. Investopdia writes that anything powered by concept alone should be a warning to anyone tempted to buy in. Although cryptocurrency projects can and do launch off the back of technological advances, investors should be wary of projects looking to gather millions of dollars before taking a sober look at the project’s ability to return the investment from the published information.
Heavy promotion of an upcoming ICO can also be a sign of an exit scam. Past scams have employed bloggers to promote via numerous forums. Ads both online and in print media could also be suspicious.
$2.9 Billion Plustoken Scam Could Be Largest Exit Scam Ever
A 2019 report shared with Cointelegraph by the cryptocurrency and blockchain forensics company Ciphertrace dubbed 2019 the year of the exit scam and highlighted the billions of dollars stolen in multiple scams this year alone.
The report shines a light on what, if confirmed, could be the biggest crypto scam ever, with an estimated loss of around $2.9 billion after Chinese police uncovered an alleged Ponzi scheme involving the South Korean wallet provider and exchange PlusToken. Although more is being uncovered about PlusToken, mystery still surrounds the key events.
Ciphertrace reports that the platform has enshrouded several Chinese nationals, the government of Vanuatu, the Chinese police and the company’s co-founders — a South Korean man operating under the alias of “Kim Jung Un” and a Russian known only as “Leo.” The alleged PlusToken scam centers around an app with which the wallet provider claimed investors could invest in PlusToken (PLUS).
According to the report, the firm claimed that the token, based on the Ethereum blockchain, was developed by a major technology company. PlusToken is also said to have falsely stated that it could deliver wallet holders an ROI of between 8% and 16% per month, with a minimum deposit of $500 in crypto assets.
Ciphertrace also reported that no verifiable source of revenue existed other than the proceeds from new membership. Those were onboarded per the traditional method of a Ponzi scheme, which require a constant stream of new investment in order to support its semblance of growth.
Investors were incentivized to recommend new users with an invitation, which was the only way to join.
Although this was enough for some members to dismiss the legitimacy of the project outright, Leo, the company’s co-founder, published a press release that claimed he had met with Prince Charles, the future head of the English royal family, providing photos as proof. Ciphertrust reported that it had contacted the Prince Charles Foundation, which confirmed that Leo had indeed attended the event, but would not provide other information about the individual due to European Union General Data Protection Regulation, or GDPR.
PlusToken’s fate was seemingly sealed on June 28, after members of the Chinese police touched down in Vanuatu, detained six people involved with the project and extradited them back to mainland China. Ciphertrace reported that the so-called “PlusToken Six” were either Vanuatu citizens or applying for citizenship at the time of their arrest.
Soon after, PlusToken members found that they were unable to withdraw funds from their accounts. Customers were informed that withdrawals via the app were frozen due to “technical difficulties.” By June 20, the PlusToken app had ceased operations due to purported system maintenance.
For investors, there seems to be no secure lead on the final resting place of the allegedly billions of dollars of stolen funds. The Chinese government has yet to comment. A July 12 post from PlusToken stated that the six Chinese individuals were simply service users and not actually involved with the running of the company itself, stating that users should ignore the rumors and not try to log in until they receive confirmation that the servers are back online.
Updated: 11-27-2019
PlusToken Scam Selling Could Dump BTC Price For the Next Two Months
This year has yielded significant price action for Bitcoin (BTC), both to the upside and to the downside. Bitcoin’s price recently fell to around $6,500 as selling pressure continues to plague the market.
Recent data from crypto-Twitter analyst Ergo shows such selling is possibly due to further liquidation of 200,000 BTC in funds from the alleged PlusToken ponzi scheme.
Ergo Said In A Tweetstorm:
“If my numbers are correct, the 200k BTC estimates reported earlier this year were correct, and market impacts will continue for some time.”
Back in August, Cointelegraph reported on some of the funds thought to be associated with the PlusToken operation — a total movement of 22,923 BTC on August 17.
The alleged PlusToken scam is said to be one of the most sizeable exit scams the crypto space has seen thus far, Cointelegraph said in a separate report.
Crypto researcher Ergo conducted fairly extensive research on the subject, looking at various wallets thought to be associated with the alleged scam. Confirming the amount of BTC funds the scam controls might give an idea of how many Bitcoin the PlusToken crew could dump (or have dumped) on the open crypto markets, possibly accounting for past and future price action.
The analyst noted 200,000 BTC as the commonly stated amount the alleged scam might have originally controlled, citing three specific wallet addresses thought to be part of the operation.
Linking to a past article on the subject, the analyst pointed toward PlusToken’s use of Wasabi Mixer, a method of mixing coins to make tracking them more difficult, as well as a method Ergo referred to as “self-shuffling.”
“My current totals are around 187,000 BTC. This analysis is not complete yet, but roughly confirms the previous 200,000 BTC estimates.”
That tweet includes a helpful chart breaking down the numbers. Following the trail, Ergo concluded that 1,100 BTC have likely been sold each day so far in November.
“Assuming all of the mixed coins (129,000 BTC) accounted for so far have been sold over a period from early August through today will give an average of around 1,300 BTC sold per day,” the analyst said.
“Going forward we can use the daily sell estimates and the ~58,000 BTC unmixed total to estimate the duration of the remaining selling at between 1.5 and 2 months.”
But Bitcoin’s bearish pressure might instead be attributed to a lack of new retail money entering Bitcoin over the past two years, as stated by Tone Vays, or simply the ebbs and flows of the ever-volatile crypto market.
Updated: 7-30-2020
27 Key Execs At PlusToken Scam Are Reportedly Arrested
PlusToken, one of the greatest exit scams in history, defrauded investors of nearly $6 billion, according to latest reports.
The story of PlusToken, one of the largest scams in the cryptocurrency industry, takes another twist as dozens of major suspects have been arrested.
As many as 27 core PlusToken team members have been arrested by Chinese police, according to a July 30 report by local industry publication ChainNews.
According to the report, the total amount of investor losses in the PlusToken scam is estimated at 40 billion Chinese yuan or $5.7 billion.
The report also mentions that investigators have also arrested another 82 core members of the scheme.
Dovey Wan, founding partner of blockchain-based investment company Primitive Ventures, tweeted that the owner key is already burned so technically it will not be able to commit fraud.
She said, “I sincerely hope this attempt can be a good learning experience for the Chinese community to start an effective DAO [Decentralized Autonomous Organization], a bottom up governance, a real movement from the people that’s for the people.”
As reported, the PlusToken scheme has emerged as one of the largest scams in the history of crypto. The project was initially presented as a South Korea-based exchange offering high investor returns.
Eventually, the entire operation was exposed as a scam after several million participants found they were unable to withdraw their investment. As previously reported, the scam scheme was estimated to defraud investors of about $5 billion in total.
Updated: 12-17-2019
‘Anonymity Vouchers’ Could Bring Limited Privacy To CBDCs: ECB Report
The European Central Bank (ECB) is thinking through the logistics of a hypothetical central bank digital currency (CBDC).
Revealed Tuesday in an ECB report, Europe’s central bankers have developed an “anonymity voucher” to give prospective CBDC users limited privacy in their retail transactions.
The ECB’s “novel new concept” aims to bridge two clashing forces in the digitized payments landscape: Europeans’ desire for private transactions and regulators’ demand for anti-money-laundering (AML) enforcement.
“The ongoing digitalisation of the economy represents a major challenge for the payments ecosystem, requiring that a balance be struck between allowing a certain degree of privacy in electronic payments and ensuring compliance with regulations aimed at tackling money laundering and the financing of terrorism (AML/CFT regulations),” the report’s executive summary said.
The anonymity vouchers, issued to all account holders at a “regular interval” regardless of their account balances, could be redeemed on a one-to-one basis to shield their transactions, the report states.
Under the proposed system, if Alice wants to anonymously send CBDC tokens to Bob, Alice must hold the equivalent number of anonymity vouchers. The anonymized transactions would skip reviews from the ECB’s proposed AML Authority, the intermediary reviewing all transactions.
Pincoin
On April 9, 2018, two ICOs — iFan and Pincoin — operating under the umbrella of company Modern Tech based in Vietnam, went silent after reports outed them as scams that had scalped 32,000 investors out of an alleged $660 million in tokens, according to Tuoi Tre News.
Victims claim that the damages amount to roughly 15 trillion Vietnamese dong ($660 million) in token sales. Angered investors held a demonstration outside Modern Tech’s Ho Chi Minh City headquarters on April 8.
One of the initial characteristics that could have alarmed investors was the fact that Pincoin offered service users bonuses for successfully bringing other people on board. Pincoin did initially pay out cash until January 2018, when the company switched to iFan tokens, TechCrunch reported.
The owner of Modern Tech’s office building said that the company left its offices in March and that no one knew their current whereabouts. The firm left behind only an incomplete website that is now inactive. Modern Tech initially tried to pass itself off as a mere representative of both coins in Vietnam, prior to media reports confirming that seven of its Vietnamese executives were in fact behind the projects.
TechCrunch reported that the ambiguous mission statement from the then-functional site is typical of the vague and jargon-filled copy used by exit scammers:
“The PIN Project is about building an online collaborative consumption platform for global community, base on principles of Sharing Economy, Blockchain Technology, and Crypto Currency”
Financial scam directory Behindmlm released a report in February 2018 that found its buy-in method was typical of an ROI Ponzi scheme. Pincoin’s website is currently down, though iFan’s is still online.
QuadrigaCX — Regulators Catch On
The death of 30-year old Gerald Cotten shook the crypto world — not only because Cotten was the co-founder and CEO of Canada’s largest cryptocurrency exchange, QuadrigaCX, but also because his control of the passwords and keys to accounts rendered all the assets on the exchange forever inaccessible after his death. Cotten took over $195 million of stolen cryptocurrency with him to the grave.
Commenting on the May 9 Ernst & Young report, Ciphertrace said Cotten had played fast and loose with customer funds for many years in order to support a lavish lifestyle for both himself and his wife. Cotten allegedly exercised complete control over the exchange and used his position to perform “unsupported deposits” — i.e., fabricated transactions not represented by either fiat or cryptocurrency.
Cotten also used significant volumes of customers’ cryptocurrency via transfers from the platform into other exchanges he controlled. As per the EY report, Cotten shifted significant amounts of fiat and cryptocurrency between alias accounts, although less than 1% of these transfers was supported by documentation. Ciphertrace notes that as the admin, Cotten was in a perfect position to hide his fraudulent activities.
In a pattern that may now seem familiar, Cotten used customer funds to pay for QuadrigaCX operating costs after the company suffered liquidity issues due to his reported fraudulent use of user deposits. As QuadrigaCX began to struggle to stay afloat, EY reported that Cotten gambled customer funds in off-platform margin accounts to meet margin calls.
The report also states that Cotten traded unsupported deposits for legitimate funds thereby generating artificial trading markets, abused his position to override Know Your Customer requirements and hoarded all passwords:
“The Monitor understands passwords were held by a single individual, Mr. Cotten and it appears that Quadriga failed to ensure adequate safeguard procedures were in place to transfer passwords and other critical operating data to other Quadriga representatives should a critical event materialize (such as the death of key management personnel).”
As of April 12, EY estimated that Quadriga held around $20.8 million in assets and around $160 million in liabilities. The debts and assets are spread over three subsidiary companies, 0984750 B.C. LTD. (the “Quadriga Estate”), Quadriga Fintech Solutions and Whiteside Capital Corporation. On July 31, the Supreme Court of Nova Scotia approved over $1.6 million in fees for parties seeking remuneration from the exchange, according to court documents seen by Cointelegraph.
CFTC Action Launched After $147 Million BTC Scheme
On June 18, 2019, the United States Commodity Futures Trading Commission (CFTC) initiated a civil enforcement action against now-defunct Control-Finance Limited for a scheme involving $147 million worth in Bitcoin.
It is alleged that Control-Finance Ltd. defrauded over 1,000 investors by laundering around 22,858 Bitcoin. In mid-September 2017, its website was abruptly taken offline, payments to clients were suspended and advertising content from social media accounts was deleted.
The firm initially said that it would reimburse customers by late 2017. However, the company allegedly began transferring laundered Bitcoin by using the crypto wallet service CoinPayments. According to Ciphertrace’s Q2 2019 Anti-Money Laundering (AML) report, the CFTC complaint charges the company and its founder Benjamin Reynolds with:
“Exploiting public enthusiasm for crypto assets by fraudulently obtaining and misappropriating at least 22,858.22 Bitcoin from more than 1,000 customers through a classic high-yield investment (HYIP) Ponzi scheme called the Control-Finance Affiliate Program.”
Per the CFTC, the company claimed that investors who buy Bitcoin through the firm would be guaranteed daily profits thanks to their team of expert cryptocurrency traders. The complaint also stated that the firm falsely claimed market volatility would ensure funds invested through Control-Finance would result in profit.
The CFTC also alleged that Control-Finance misleadingly promised that it could earn customers a 1.5% ROI daily and 45% monthly. Control-Finance is also reported to have sent partial amounts of new clients’ BTC deposits to other customers, which were disguised as profit from trading, a tactic typical of Ponzi schemes. The legal action seeking civil monetary penalties and permanent trading bans continues.
Co-Owner Of Bitmarket Found Shot Dead After Alleged Exit Scam
On July 8, the Poland-based exchange Bitmarket shut down, citing liquidity issues. According to Ciphertrace’s Q2 2019 AML report, the shutdown cost users around 2,300 Bitcoin, approximately $23 million. Users attempting to log on to the site were met with the following message:
“We regret to inform you that due to the loss of liquidity, since 08/07/2019, Bitmarket.pl/net was forced to cease its operations. We will inform you about further steps.”
Ciphertrace reports that Bitmarket had a history of partners pulling out. In 2015, the firm lost payment processors CashBill and BlueMedia after the companies’ banks requested they end their working relationship with Bitmarket. PKO Bank Polski, Bitmarket’s own bank, also terminated its relationship with the firm only six months after Bank BPH had done so earlier in 2015.
Bitmarket’s two founders, Marcin Aszkiełowicz and Tobiasz Niemiro, have contradicting accounts about the misplaced user funds. Aszkiełowicz claimed that the exchange had been hacked for 600 BTC in 2015, an incident from which the company was unable to recover.
Niemiro, however, claimed that he was not responsible for activities on the exchange. Niemiro also purported to have been told that the company was purchased with a deficit of 600 BTC, which he allegedly repaid with his own money. Niemiro said he could not confirm that his partners had indeed used the money to purchase the 600 BTC.
Two weeks after the interview, Niemiro was found dead in a forest near his home with a gunshot wound to the head, which the police deemed to be self-inflicted. The District Attorney’s Office stated that it is not looking into the involvement of third parties in Niemiro’s death, but are still actively investigating the misappropriation of funds.
Binance: Funds ‘SAFU’ After Amazon Web Services Error Stops Withdrawals
Cryptocurrency exchange Binance has confirmed user funds are not at risk after a reported technical problem began affecting withdrawals.
According to CEO Changpeng Zhao, also known as CZ, the situation was being resolved on Aug. 23, while funds security was not compromised.
“Funds are #safu,” he wrote on Twitter, employing a now well-known catchphrase he had previously inadvertently created while confirming there was no danger to cryptocurrency holdings.
“Funds Are Safu” After AWS Error Busts Withdrawals
The issue, he explained, centered on Amazon Web Services (AWS). Problems with caching were producing error messages for a portion of Binance traders, with withdrawals also impacted.
“AWS is having an issue, mostly with caching services, affecting some users globally. We are working with them and monitoring the situation closely,” CZ wrote, adding:
“It’s causing some 500 error messages on APIs and affecting some withdrawal processing.”
Binance Shrugs Off Alleged KYC Data Leak
Binance had just recovered from a publicity scare which involved a self-proclaimed hacker alleging he had access to users’ Know Your Customer, or KYC, data.
Prior to that, a hack saw funds worth $41 million leave the platform due to a security issue — something which sparked a weeklong maintenance shutdown and payouts to affected users.
This week, Binance announced it was working on a new cryptocurrency project, Venus, as an answer to Facebook’s controversial Libra digital currency.
Updated: 11-27-2019
Crypto Exchange Upbit Confirms Theft of 342,000 Ether — $50M
Major South Korean cryptocurrency exchange — run by a subsidiary of Korean tech giant Kakao — has notified users of the theft of 342,000 Ether (ETH) from its hot wallet.
The incident was confirmed in an official statement written by Lee Seok-woo, the CEO of Upbit’s operator, Dunamu, on Nov. 27.
Upbit will use corporate funds to protect user assets
In His Statement, Lee Seok-Woo Revealed That:
“At 1:06 PM on November 27, 2019, 342,000 ETH (approximately 58 billion won) were transferred from the Upbeat Ethereum Hot Wallet to an unknown wallet. Unknown wallet address is 0xa09871AEadF4994Ca12f5c0b6056BBd1d343c029.”
Apologizing to users for any “inconvenience” caused, the CEO outlined measures by the exchange taken after it detected the incident while stopping short of calling it a “hack.”
The exchange has pledged to protect user assets, stating that the 342,000 ETH (roughly $50 million by press time) will be covered by corporate assets. It has already moved all crypto assets held in its hot wallet to cold storage.
Deposits and withdrawals will take at least two weeks to resume, with Lee Seok-woo promising to inform users as soon as they reopen.
The CEO further indicated that all other recent large-scale transfers were not abnormal, but were related to the exchange moving assets between hot and storage facilities.
Active Threats
In March of this year, Upbit and local cybersecurity firm East Security alleged that a phishing scam targeting its users had been perpetrated by hackers from North Korea.
In January 2018, South Korea’s four largest crypto exchanges — Bithumb, Upbit, Coinone and Korbit — created a hotline for major exchanges to ensure suspicious transactions could be detected and frozen immediately after being disclosed.
Bithumb has to date suffered three major security breaches, most recently in March of this year.
Signs Point To Inside Job In Upbit Crypto Exchange Hack, Says Commentator
Following the theft of 342,000 Ether (ETH) ($50 million) from major South Korean crypto exchange Upbit, some commentators have suggested that the hack was actually an inside job.
As Cointelegraph contributor Joseph Young tweeted on Nov. 27:
“The ‘hacker’ timed when UPbit was making crypto transfers to its cold wallet (other alts like TRON, etc.). Hence, I think the probability of it being an inside job is higher than external breach.”
Hacker’s Timing Was Advantageous
As Cointelegraph reported, the incident was confirmed in an official statement published earlier today, which read:
“At 1:06 PM on November 27, 2019, 342,000 ETH (approximately 58 billion won) were transferred from the Upbeat Ethereum Hot Wallet to an unknown wallet. Unknown wallet address is 0xa09871AEadF4994Ca12f5c0b6056BBd1d343c029.”
In its statement, the exchange emphasized that it deemed the 342,000 ETH transaction to be the only irregular transaction on the ledger, alluding to a number of other large-scale transfers that it said were related to the exchange moving assets between hot and cold storage wallets.
As data published by large-scale crypto transaction tracker Whale Alert has revealed, the 342,000 ETH transaction was followed by a series of major transfers of Tron (TRX) and BitTorrent (BTT) tokens.
While the ETH, TRX and BTT transactions were transferred to an unknown wallet, subsequent Stellar (XLM), OMG and EOS transfers were made from Upbit to crypto exchange Bittrex.
aking Upbit’s statement about cold storage transfers at face value, Young has argued for the strong possibility than an exchange employee took advantage of the timing of the storage transfers to perpetrate the theft.
Upbit today pledged to cover all user assets with corporate funds and exchange deposits and withdrawals will reportedly take at least two weeks to resume.
Markets React To Exchange Hack
Cryptocurrency markets have seemingly reacted to news of the incident, with Bitcoin (BTC) falling below $7,000 once again in an already fragile market climate.
Huge kudos to law enforcement on this one. Many of us never thought the stolen coins would be recovered. This is a testament to the transparency of blockchains, and what savvy law enforcement can do in this new universe.
— Emin Gün Sirer (@el33th4xor) February 8, 2022
Binance CEO Changpeng Zhao has tweeted that the exchange will “work with Upbit and other industry players to ensure any hacked funds that may make their way to Binance are immediately frozen.”
As Cointelegraph previously reported, the theft of 14 billion won ($13 million) in cryptocurrency from major South Korean cryptocurrency exchange Bithumb was believed by executives to be the work of an insider.
Updated: 11-28-2019
Upbit Promises Swift Reimbursement, Theories Over Missing Funds Swell
On Nov. 27, major South Korean cryptocurrency exchange Upbit announced that 342,000 Ether (ETH), accounting for roughly $50 million, were stolen from its hot wallet earlier that day. Details remain vague, and some users are suggesting an inside job, although experts are skeptical of the theory after analyzing the incident.
The platform’s operator has promised to compensate all stolen funds shortly. UpBit is the second “Big Four” exchange in the country to experience a major security breach this year.
Upbit Brief
Upbit is one of the largest cryptocurrency exchanges in South Korea (alongside Korbit, Bithumb and Coinone) and the only major domestic platform to post a profit in 2018. It was launched in October 2017 by Dunamu Inc. — a fintech firm backed by local internet giant Kakao — after it signed “an exclusive partnership agreement” with United States cryptocurrency exchange Bittrex.
As part of the collaboration, Upbit had a shared order book arrangement, with Bittrex orders visible in its bid windows. However, in September, the South Korean trading platform ostensibly broke off its partnership with Bittrex to reorganize its ETH, Bitcoin (BTC) and Tether (USDT) markets.
Upbit has been widely considered a safe and compliant exchange overall. Recently, it was put on par with industry juggernauts like Kraken and Coinbase as one of the space’s cleanest platforms in the Blockchain Transparency Institute’s latest market surveillance report, which verifies cryptocurrency exchange volumes.
Indeed, Upbit has seemingly put a lot of effort into security measures. Last year, it reportedly became the first crypto exchange to obtain an information security management system license from the Korea Internet and Security Agency.
Further, Upbit has been following guidelines set out by the intergovernmental Anti-Money Laundering-focused body, the Financial Action Task Force. Specifically, in September this year, Upbit ceased trading support for six cryptocurrencies, including some privacy coins.
Upbit is a member of the Korean Blockchain Association — a domestic alliance comprised of 14 crypto trading platforms — which published a self-regulatory framework for its members to boost trading transparency in April 2018. It contained five key requirements, including managing clients’ coins separately from their own, holding a minimum equity of 2 billion won ($1.8 million), and publishing regular audit and financial reports.
Finally, in January 2018, Upbit partook in creating a special hotline for domestic exchanges that aims to ensure suspicious transactions being detected and frozen immediately after disclosure.
The Attack And Upbit’s Initial Response
Upbit was relatively quick to confirm the loss. Around 3 p.m. local time, the first media reports surfaced, stating that the platform had halted all trading after a large amount of cryptocurrencies was withdrawn to an anonymous wallet.
On social media, users were already discussing a number of large-scale transactions from Upbit’s wallet that had been spotted by WhaleAlert, a service dedicated to tracking sizable cryptocurrency transactions.
There was a 342,000 ETH transaction to an unknown wallet, followed by 10 identical transactions totaling 100,000,000 TRX incoming from the exchange’s vault. At around 6 p.m. local time, Lee Sirgoo, the CEO of Upbit, published an official statement on the matter:
“At 1:06 PM on November 27, 2019, 342,000 ETH (approximately 58 billion won) were transferred from the Upbeat Ethereum Hot Wallet to an unknown wallet. Unknown wallet address is 0xa09871AEadF4994Ca12f5c0b6056BBd1d343c029.”
Apologizing to users for any inconvenience caused, Lee Sirgoo outlined the measures taken by the exchange after it detected the incident. The exchange has pledged to protect user assets, stating that the 342,000 ETH (or roughly $50 million) will be covered using corporate assets.
It had already moved all crypto assets held in its hot wallet to cold storage by the time the announcement was published, the CEO stated. Some of the funds may have been moved to Bittrex’s wallets, as data provided by WhaleAlert suggests.
Deposits and withdrawals will take at least two weeks to resume, Sirgoo added, promising to inform users as soon as they reopen. The CEO also clarified that all other recent, large-scale transfers were not abnormal, but were related to the exchange moving assets between hot and cold storage facilities.
Inside Job?
Some Experts Are Skeptical
Notably, Lee Sirgoo avoided using the word “hack” in his statement, which prompted some commentators on social media to suggest that the incident was actually an inside job. As Cointelegraph contributor Joseph Young tweeted:
“The ‘hacker’ timed when UPbit was making crypto transfers to its cold wallet (other alts like TRON, etc.). Hence, I think the probability of it being an inside job is higher than external breach.”
However, Taylor Monahan, the founder and CEO of noncustodial wallet MyCrypto, analyzed the incident in detail by studying the nature of transactions and is hesitant to confirm the theory. “Anything is possible, of course,” she told Cointelegraph. “But a lot of people are jumping to conclusions without real supporting evidence.” Monahan then elaborated:
“The biggest thing that points to it not being an inside job is how the transactions were generated and signed. UPbit seems to follow a certain method with their programmatic transactions, and the ‘hack’ transaction in question used a different method. In addition, UPbit manually signed a transaction to secure their remaining ETH, after discovering the hack, and this too was generated differently than the ‘hack’ transaction.”
If it were an inside job or a breach of Upbit’s backend systems, it would align with the exchange’s typical behavior, she added, while the way that the ETH transaction was generated “points to someone who knows very little about the Ethereum network.”
Monahan also commended Upbit on how they have been handling the aftermath, but criticized the exchange’s languid use of cold storage, “If Upbit utilized cold storage more regularly and limited the value held by their hot wallet, the loss could have been minimized.”
Upbit Is Collaborating With KISA And Police
Upbit’s CEO Lee Sirgoo Told Cointelegraph That They Are Currently Cooperating With Kisa And The National Police Agency Cyber Bureau On The Matter:
“We will be able to provide you with more information once the investigation is complete.”
Nevertheless, Sirgoo was able to answer some specific questions through email upon request by Cointelegraph. For instance, he confirmed that the exchange has contacted all major trading platforms and asked to blacklist the attacker’s wallet address, and that the cryptocurrency community “has been extremely cooperative.”
In addition, he confirmed that Dunamu and Upbit have enough funds to reimburse the lost amount. “It should be completed shortly,” Sirgoo told Cointelegraph.
Exchanges Continue To Get Hacked In 2019
2019 has witnessed a number of high-profile crypto exchange hacks, including the $42 million Binance security breach, $19 million Bithumb heist and $28 Million Bitpoint break-in, which confirms that security is still an industry-wide problem. So what could finally stop centralized exchanges from getting hacked?
Hartej Sawhney, co-founder and CEO at Zokyo cybersecurity agency, suggests that compliance standards could improve the situation. “Centralized crypto exchanges are web services, not that different from an online banking applications,” Sawhney told Cointelegraph, continuing:
“Most companies respect security either because of regulation or they already faced a security breach. The cryptocurrency industry could benefit from compliance standards such as PCI-DSS or HIPAA.”
Further, Sawhney listed a number of concrete measures that exchanges should follow to achieve higher security, including establishment of adequate infrastructure, processes, tools, security testing and education on how to avoid cyber attacks, adding that, “Regular third-party offensive security testing needs to become standard and transparent.”
Upbit has promised to keep Cointelegraph updated once it have more information. KISA has not returned Cointelegraph’s request for comment.
Updated: 12-5-2019
Crypto Exchange UpBit’s Operator Launches Custody Service With Ledger
DXM, a financial services subsidiary of South Korean fintech firm Dunamu, has worked with crypto cybersecurity firm Ledger to launch an institutional crypto asset custody service.
The Partnership And The New Custodian
Industry news outlet TheBlock reported on Dec. 4 that DXM plans to launch the custodian under the name Upbit Safe and that Ledger Vault, Ledger’s custody arm, will support the initiative with its technology. Upbit safe will reportedly use Ledger’s hardware security technology to make trading more efficient and safer for its institutional clients.
Ledger’s Head of Asia-Pacific region Glenn Woo explained that Ledger Vault offers solutions that allow institutions to customize their custody rules to better fit their needs. DXM Chief Strategy Officer Eric Yoo told the outlet that the firm plans to target UpBit’s customers first. Yoo explained the new enterprise’s outlook:
“We are a subsidiary of the largest exchange in Korea and have an advantage over our peers given that we already have a lot of assets we can bring into our custody. […] The combination of the Upbit brand, Ledger Vault’s security technology, and DXM’s own technology will give DXM an edge in the Korean market.”
Lack Of Regulation Hinders Crypto Growth
Still, Yoo admitted that institutional participation in the crypto space in South Korea is largely hampered by unclear regulation. Still, he believes that clarity should improve as soon as next year, bringing new money to the local crypto industry:
“The biggest regulatory risk in Korea is uncertainty and lack of regulations. […] It’s quite a wild wild west out there. […] Once regulations become clearer, it’d be easier for us to engage with institutional money and not take the risks from uncertainties.”
Woo also explained that Ledger Vault is still a new service in the space and is still trying to penetrate the market. He hopes that with his company’s help, DXM will be able to help his firm scale its operations:
“DMX has a reputation of being very secure… With the track record that they have in Korea, they can definitely help us scale.”
The number of custody services aiming to secure the crypto assets of institutions is steadily increasing as regulation is making the space more suitable for institutional investors. One of the last examples is the custody feature launched by institutional Bitcoin (BTC) trading platform Bakkt for its entire client base after obtaining regulatory approval in the first half of November.
Updated: 12-12-2019
US SEC Charges Shopin Founder With Orchestrating Fraudulent $42 Million ICO
The United States Securities and Exchange Commission (SEC) has charged Eran Eyal, the founder Shopin, with orchestrating a fraudulent initial coin offering (ICO).
In a press release on Dec. 11, the SEC alleged that the businessman and his company defrauded hundreds of investors in an ICO that raised more than $42 million from August 2017 to April 2018. According to the SEC, Shopin’s actions constituted an unregistered securities offering of Shopin Tokens.
Eyal told investors he would use the funds from the token sale to create blockchain-based shopper profiles. These profiles would then track customer purchase histories across online retailers and recommend products based on this information. However, Eyal never created a functional platform. Marc P. Berger, Director of the SEC’s New York Regional Office said:
“As alleged in today’s action, the SEC seeks to hold Eyal and Shopin responsible for scamming innocent investors with false claims about relationships and contracts they had secured in support of a blockchain-based universal shopper profile […] Retail investors considering an investment in a digital asset that meets the definition of a security must be afforded the same truthful disclosures as in any traditional securities offering.”
Furthermore, Eyal allegedly lied about having forged partnerships with established retail outlets when in fact no such partnerships existed.
The SEC also claims that Eyal misappropriated investor funds to pay for personal expenses. From the SEC complaint:
“Eyal used over $500,000 of investor funds for expenses such as his rent, retail shopping, entertainment, tickets to philanthropic events, and a dating service, but omitted to disclose to investors that he would use any proceeds for his own benefit.”
The commission has charged Eyal and Shopin with violating the anti-fraud and registration provisions of the federal securities laws, and is seeking injunctive relief, disgorgement with prejudgment interest and civil money penalties. The SEC also seeks a bar against Eyal and Shopin prohibiting them from participating in any future securitized token offerings.
Eyal had previously been charged with defrauding investors for $600,000 by misrepresenting the staff and clients of his previous startup, Springleap.
Updated: 12-13-2019
VeChain Loses $6.6M In VET Tokens To Hacker In Attack On Buyback Wallet
VeChain Foundation’s wallet has been compromised in a hacker attack targeting funds earmarked for the foundation’s buyback program.
Per a VeChain Foundation announcement on Dec. 13, an unknown hacker has redirected 1.1 billion VET tokens — valued at approximately $6,600,000 at press time — from the VeChain Foundation’s buyback wallet to a personal wallet address.
Security Breach Is Likely A Result Of Internal Misconduct Unnoticed Due To Human Error
In the initial update on the incident, VeChain Foundation noted that the hack is in “no way related” to the operations of the actual standard procedure or VeChain’s hardware wallet solutions.
A member of Cointelegraph Consulting also indicated that VeChain enterprise products will not be affected.
According to the statement, the VeChain’s security breach was likely due to misconduct of one of its staff members in the finance team. Specifically, the person has allegedly created the buyback account partly violating the standard procedure approved by the Foundation. The auditing team did not pick up the misconduct due to human error, the announcement notes.
Measures To Mitigate The Situation And Add More Clarity
In the same announcement, the Foundation has listed a number of measures designed to mitigate the incident and get more clarity. As such, the firm provided a link with the hacker’s address tagged on VeChainStats in order to instantly trace other addresses interacting with the hacker’s address.
As part of their efforts, the company notified all exchanges to monitor, blacklist and freeze all funds coming from the attacker as well as withdrawals from the corresponding exchanging wallets.
Additionally, VeChain has launched a security investigation on other crypto assets that are subject to the custody of the Foundation to prevent further breach. The Singapore-based firm also reported on the incident to law enforcement in Singapore and will keep monitoring the situation and working with cybersecurity and law enforcement professionals to add more clarity, the statement notes.
VET Token Slides Over 4% Amid The Hack
VeChain is a major cryptocurrency and blockchain platform designed to enhance supply chain management and business processes. VET token is ranked the 28th largest crypto asset by market capitalization of $325 million at the time of this writing. Following the news, the token dipped over 4% with the market cap dropping to a low of $320 million. The altcoin is seeing a slight recovery at press time, according to Coin360.
VeChain, which is known for providing its blockchain Thor blockchain for Walmart China’s blockchain platform, has recently partnered with Cointelegraph Consulting, a division of Cointelegraph aiming to contribute to the global adoption of blockchain technology.
Updated: 12-13-2019
Alleged Bitcoin Ponzi Scheme Assets Frozen As US Judge Grants Injunction
A United States court has granted regulators a preliminary injunction against an alleged Bitcoin (BTC) Ponzi scheme which reportedly defrauded investors of $11 million.
In a filing with the United States District Court in Nevada dated Dec. 6, Judge Jennifer A. Dorsey ruled in favor of the Commodity Futures Trading Commission (CFTC) and against Circle Society, along with its operator, David Saffron.
CFTC Wins Injunction Against CIrcle Society
“…I find that this is a proper case for granting a preliminary injunction and other equitable relief to preserve the status quo, protect customers from further loss and damage, and enable the Commission to fulfill its statutory duties,” Dorsey wrote.
Circle will now see its assets frozen, and the CFTC will be able to inspect its financial records prior to any further legal action.
The CFTC originally charged Circle Society and Saffron in late September, after investors complained that the latter fraudulently maintained an $11 million Bitcoin binary options offering. At the time, the regulator likened the company’s activities to a Ponzi scheme, stating in an October press release:
“According to the complaint, the defendants fraudulently solicited funds from at least fourteen members of the public to participate in a pool operated by Circle Society, an entity Saffron created and used to perpetrate his fraud, by making false claims of Saffron’s trading expertise and guaranteeing rates of return up to 300%.”
U.S. Goes After Crypto Sales
The events underscore the increasingly persistent line taken by both the CFTC and its fellow financial regulator, the Securities and Exchange Commission (SEC), regarding cryptocurrency activities that do not conform to the law.
As Cointelegraph previously reported, enforcement action continues to impact even legitimate companies, with regulators specifically eyeing practices related to sales of tokens via initial coin offerings, or ICOs.
These include Canadian messaging firm Kik, which almost shut down after a lengthy legal battle with the SEC over its 2017 sale.
Updated: 12-13-2019
Shopin Founder Pleads Guilty to Orchestrating Fraudulent $42 Million ICO
The New York Attorney General (NYAG) Letitia James announced the conviction of Shopin founder Eran Eyal for orchestrating a fraudulent initial coin offering (ICO) following his guilty plea.
As the NYAG announced on Dec. 12, the former CEO of Shopin pleaded guilty to felony charges for running a fraudulent initial coin offering that raised more than $42 million between August 2017 and April 2018. Eyal also pleaded guilty to defrauding investors of $600,000 by misrepresenting the staff and clients of his previous startup, Springleap.
Quick Turnaround In Court
Yesterday, the United States Securities and Exchange Commission (SEC) charged Eyal for defrauding hundreds of investors in a scam ICO. According to the SEC, Eyal’s actions constituted an unregistered securities offering of Shopin Tokens. The SEC further claimed that Eyal also misappropriated investor funds to pay for personal expenses. Attorney General James commented on the conviction:
“My office won’t allow white collar criminals to get away with their schemes to defraud innocent victims, no matter how complex […] This one individual created company after company after company just to continue cheating investors out of hundreds of thousands of dollars. Using fake product trials and nonexistent contracts with major retailers he was able to lure victims to invest in his technology schemes, including his very own cryptocurrency. We will use every available resource at our disposal to pursue all who attempt to abuse and manipulate the system, because no one is above the law.”
Despite the Attorney General’s tough talk, the court seems not to have proscribed any jail time. The court ordered Eyal to pay $125,000 in restitution and $475,000 in judgments to investors, and to surrender the remaining $450,000 in cryptocurrency to the AG’s Office. The Brooklyn resident is further required to step down as CEO of Shopin, and is banned from raising capital or serving as an officer in a business in New York for three years.
SEC Seeks To Reopen Case Against Bitcoin Fraudster
Cointelegraph recently reported that the SEC has filed to reopen a case against Bitcoin (BTC) fraudster Renwick Haddow as he has not resolved the regulator’s claims for monetary relief against him. Last year, the SEC accused Haddow of defrauding Bitcoin investors for more than $37 million. The court found him guilty in June of 2019.
Updated: 12-14-2019
QuadrigaCX Victims Request Proof of Gerald Cotten’s Death by Exhuming Body
Canadian law firm Miller Thomson has made a request to the Royal Canadian Mounted Police (RCMP) to conduct an exhumation and post-mortem autopsy on the body of Gerald Cotten, the deceased owner of the now-defunct Canadian crypto exchange QuadrigaCX.
On Dec. 13, the Miller Thomson lawyers explained in a letter to the RCMP that the request to exhume and examine Cotten’s body was appropriate given the “questionable circumstances surrounding Mr. Cotten’s death and the significant losses” sustained by users of the cryptocurrency exchange.
Victims Need Clarity On Whether Gerald Cotten Is In Fact Deceased
The law firm further points to publicly available information about the debacle surrounding the Canadian crypto exchange, which, in the firm’s view, further highlights “the need for certainty around the question of whether Mr. Cotten is in fact deceased.”
Over the past year, the exchange has been engaged in a lengthy court case with the exchange’s creditors, some of whom have speculated wildly as to the fate of the lost cryptocurrency, and with some seemingly convinced that Cotton could have faked his own death.
Cotton reportedly died in India from a fatal disease in December 2018, taking with him the private keys and password to crypto wallets, resulting in users losing about $190 million.
Widow Of Gerald Cotten Hands Over $9 Million In Assets To Disgruntled Users
In October, the widow of Gerald Cotten, Jennifer Robertson, handed over $9 million in assets to the users of the QuadrigaCX crypto exchange. Robertson announced in a personal statement, that she would be transferring the vast majority of estate assets to EY Canada, the Big Four audit firm that acted as the bankruptcy trustee of QuadrigaCX during its insolvency hearings. She said at the time:
“I have now entered into a voluntary settlement agreement where the vast majority of my assets and all of the Estate’s assets are being returned to QCX to benefit the Affected Users.”
Updated: 12-17-2019
HitBTC Scammers Face Two Years In Jail For $140K Bitcoin Twitter Fraud
Two Canadian men who defrauded a Bitcoin (BTC) investor out of $140,000 by impersonating exchange HitBTC may serve two years in prison.
According to court records on Dec. 16, brothers Jagroop Singh Khatkar and Karanjit Singh Khatkhar pled guilty to charges of conspiracy to commit wire fraud over a scam carried out via Twitter in July 2018.
HitBTC Victim: “I Feel Sorry For Them”
The case originally came to light in July this year, as per documents filed with the United States District Court in Portland, Oregon.
Posing as the support service for HitBTC, the pair convinced a user, an unnamed 63-year-old woman, to reveal the email address attached to her trading account. They then hacked into the account, stealing 23 BTC, worth around $140,000 at the time.
As per the documents, the Singh Khatkhars “did unlawfully, knowingly, and intentionally transfer, possess, and use, without lawful authority, a means of identification of another, knowing that the means of identification belonged to a real person.”
At a plea hearing on Monday, the victim took pity on the defendants, having learned she would likely win back possession of the lost funds.
“I feel sorry for them. I have a son that’s 27. I hope they can turn their smarts into something more beneficial,” she reportedly said.
The Singh Khatkhars will return for sentencing next March.
Bitcoin Scams Continue To Surface
The case highlights the persisting trend of bad actors cashing in on cryptocurrency’s increasing mainstream appeal.
As Cointelegraph reported, the previous few months alone have seen multiple instances of crime associated with the theft of assets, some of which dwarf the Singh Khatkhars’ $140,000 haul.
Earlier in December, police in New Jersey arrested three men associated with an alleged cryptocurrency Ponzi scheme which collected a whopping $722 million.
Suspicions have also surfaced over new market entrants, notably in connection with the setup and profit potential touted by the founder of altcoin HEX, which launched at the start of this month.
Updated: 12-18-2019
Bitcoin Scammers ‘Tired’ of Crypto as Focus Switches to Prepaid Cards
Bitcoin (BTC) scammers may be abandoning the cryptocurrency to focus on extorting money via prepaid debit cards, a new study suggests.
Revealing its findings in a blog post on Dec. 16, cybersecurity company Kaspersky Lab highlighted a growing trend in Brazil as an example of hackers’ growing taste for prepaid cards.
Prepaid Cards’ International Appeal
Specifically, a so-called “sextortion” scam — demanding a victim pay money to avoid compromising information about his or her private life going public — targets Acesso cards in the country.
“The debit cards in this particular sextortion scheme — Acesso cards — are sold in Brazil and work with the Mastercard system,” Kaspersky explains. As such, money gleaned from cards can be spent anywhere Mastercard is accepted, the post continues:
“One of the features of these cards is that they are usable not only in Brazil, but internationally as well. Perhaps that’s the feature that the cybercriminals in question are particularly interested in.”
Two Photos To Steal Funds
The Acesso scam works by hackers sending fake emails en masse, which tell recipients to purchase a prepaid card in a store, load it with funds and photograph both sides. Armed with a visual representation of the card, the hackers can then spend the funds.
Whether the trend could ultimately lead to a complete loss of interest in using Bitcoin among scammers, however, is open to interpretation.
“It is still too early to say if prepaid debit cards will supplant bitcoin as the new ransom currency of choice, or whether such messages are the exception rather than the rule,” Kaspersky adds.
Meanwhile, cryptocurrency-related crime remains a major threat to internet users. In its latest annual summary of new threats, Kaspersky identified a total of over 2.2 million devices targeted by mining malware alone since November 2018.
Updated: 12-29-2019
Is PlusToken Scam About to Dump ETH? $105M Moves to Unknown Wallet
Ether (ETH) price faced fresh selling pressure on Dec. 19 as a giant transaction associated with the PlusToken ponzi scheme worried traders.
Data from Twitter-based monitoring resource Whale Alert, a single movement of 789,525 ETH ($105.1 million) between a known PlusToken wallet and an unknown recipient occurred early Thursday.
Giant Transaction Turns Traders Bearish On ETH
PlusToken, which hit a high of near $350 before crashing, has earned the infamous title of being one of the world’s biggest ponzi schemes. While still operational, its Chinese operators received an estimated $3 billion in Bitcoin (BTC) and ETH from unwitting investors purchasing PlusToken coins.
Despite several arrests, subsequent activity has shown one or more individuals still have access to the scheme’s wallets.
Noting the ETH move, trader and analyst Alex Krueger warned the consequences for the Ether price could be severe.
“Heads up,” he told Twitter followers.
As Cointelegraph previously noted, suspicions had already surfaced about PlusToken’s impact on Bitcoin. In a report last month, research firm Chainalysis suggested scammers may be using over-the-counter (OTC) off-ramps to sell BTC en masse, driving down the price.
Specifically, they eyed exchange Huobi’s OTC offering as a potential venue for the illicit transactions.
“Unfortunately, because it’s not possible to distinguish between trades made by OTC brokers in possession of PlusToken funds and all other trades made on Huobi, we can’t say for sure that PlusToken cashouts caused Bitcoin’s price to drop,” the report stated.
Chainalysis Concluded:
“However, we can say that those cashouts cause increased volatility in Bitcoin’s price, and that they correlate significantly with Bitcoin price drops.”
Cointelegraph has approached Huobi for comment. A representative said the exchange was examining the situation but had not responded as of press time.
Wertheimer: Ethereum Has “Reached The Absurd”
While both BTC/USD and ETH/USD have fallen significantly in recent weeks, Ether faces added difficulties as slow progress and controversial decisions by Ethereum developers take their toll on sentiment.
This week, critics came out against a decision to implement a second hard fork on Ethereum in under a month, which they said would disillusion nodes, which could easily be jettisoned from the network.
“When your ‘decentralized’ network moves to a non-emergency schedule of one hard fork every 3 weeks, you’ve reached the absurd,” pro-Bitcoin commentator Udi Wertheimer summarized on Monday.
Wertheimer Concluded:
“You jumped the shark. There’s really no excuse to this and people should be talking about it.”
Updated: 12-23-2019
Hackers Grab Nearly $480K From Blockchain Platform Nuls
Blockchain platform Nuls has lost almost $480,000 worth of NULS tokens due to a hack, according to a security update tweeted on Dec. 22.
In its tweet, Nuls said it had detected that 2 million tokens had been transferred, of which 548,354 tokens — worth roughly $131, 600 — had entered the trading market and were now untraceable.
Mandatory hard fork upgrade to be released ASAP
In response to the theft, Nuls has decided to hard fork the blockchain at block height 87,800:
“After the hard fork, the remaining 1451645.65303905 NULS that has not entered the trading market will be destroyed in a permanent freeze to prevent continued flow into the market.”
The action should help to prevent losses to community members, the team claims. The hard fork will be released as soon as possible, with the team notifying node owners that an upgrade is mandatory and should be complied with ASAP.
Nuls revealed that hackers exploited a security vulnerability in the Nuls 2.2. version, which it says has now been fixed. It also notes that all relevant cryptocurrency exchanges have been contacted and are actively cooperating with the Nuls team.
Post-hack, Nuls token sees only mild losses
The stolen tokens represent only 2% of the circulating supply of over 73 million. The hack has seemed to have little effect on NUL’s price movement. At press time, NULS has lost 1% on the day and is trading at $0.238.
With offices in southwestern China, Singapore and teams in the United States, Australia and South Korea, Nuls is an open-source, enterprise-grade blockchain platform that provides customizable, modular blockchain infrastructure for a variety of business requirements.
The company was ranked 4th in the latest crypto rankings report from China’s Center for Information and Industry Development.
Updated: 1-5-2020
Most Significant Hacks of 2019 — New Record of Twelve in One Year
Twelve major cryptocurrency exchange hacks occurred in 2019. Of these, 11 hacks resulted in the theft of cryptocurrency while one only involved stolen customer data. In total, $292,665,886 worth of cryptocurrency and 510,000 user logins were stolen from crypto exchanges in 2019. Cryptocurrency exchanges experienced more hacks last year than in 2018, when only nine cryptocurrency exchanges fell victim to security breaches.
As time goes on, you might think that cryptocurrency exchanges would become more secure. The reality, however, is that more hacks on cryptocurrency exchange are taking place year after year. In general, crypto exchanges remain unregulated, and it’s still unclear which regulatory agency has jurisdiction over the crypto markets.
Although there are no established rules regarding how cryptocurrency exchanges should safeguard customer funds, there are crypto-friendly countries and states. Canada, Malta and the American state of Wyoming have created crypto-friendly legislation that makes it easier for businesses to operate and gives them guidelines regarding security practices.
Sadly, not all countries have created guidelines or laws that help crypto businesses operate and reduce the risk for consumers. The way cryptocurrency exchanges store and protect their customer’s wealth differs from exchange to exchange; unfortunately, this makes cryptocurrency exchanges a hotbed for hacks that result in the theft of cryptocurrency or customer data. Let’s take a closer look at the cryptocurrency exchange hacks of 2019 and how much cryptocurrency, fiat and customer data was stolen in each incident.
Updated: 1-7-2020
CFTC Cannot Locate Man Responsible For Over $140 Million Crypto Ponzi
The United States Commodity Futures Trading Commission (CFTC) is having trouble locating Benjamin Reynolds, who is allegedly responsible for a cryptocurrency Ponzi scheme worth over $140 million.
Financial news outlet FinanceFeeds reported on Jan. 6 that the CFTC has filed a motion with the New York Southern District Court. More precisely, the regulator filed for the service of process on Reynolds by publication on The Daily Telegraph and extending for sixty days the time limit by which the service must be effected on him and his firm.
A Major Bitcoin Ponzi Scheme
In mid-June, the CFTC launched action against the company over an alleged $147 million Bitcoin (BTC) Ponzi. The CFTC filed against the Reynolds with the aforementioned court for allegedly defrauding over a thousand investors of at least 22,858 Bitcoin.
In a memorandum accompanying the motion, the regulator reportedly explains that it attempted to serve Reynolds at the address listed as his “service address” in the incorporation papers of Control Finance, the firm that managed the scheme. When the process server arrived at the address, he discovered that it does not actually exist.
The CFTC also tried to email Reynolds at the only known email address associated with him and his company, but got back an error message indicating that the message could not be delivered. The regulator learned from affected investors that the Ulsan District Prosecutors’ Office in South Korea is also investigating the scheme, but had similarly failed to contact Reynolds.
Cryptocurrency Scams
Scammers have long been using the speculative enthusiasm surrounding cryptocurrencies to lure in and defraud unsuspecting investors. As Cointelegraph reported, Bitcoin scam ads featuring the likeness of Martin Lewis have continued to appear on social media despite Lewis’ previous efforts to prevent such illegal practices.
One particularly famous cryptocurrency-related scam is OneCoin, which was a $4 billion pyramid scheme. The scam was first discovered in May 2015. However, proceedings are still ongoing, and OneCoin’s website shut down only at the beginning of December last year.
Updated: 1-29-2020
Lawyers Ramp Up Pressure To Exhume Quadriga CEO’s Body
Lawyers representing the former users of the QuadrigaCX platform are doubling down on a formal request to exhume the exchange’s founder’s body.
Miller Thomson, the court-appointed representative counsel for Quadriga’s former users, contacted Bill Blair, the public official responsible for overseeing the Royal Canadian Mounted Police, asking him to clarify whether the law enforcement agency investigating Quadriga’s 2019 collapse would exhume founder Gerald Cotten’s body in a letter emailed to creditors and posted to the law firm’s website Tuesday.
The law firm first requested the RCMP exhume and autopsy last month, asking the agency to both confirm Cotten’s body is indeed in his grave, as well as determine the cause of death. Cotten’s demise precipitated the exchange’s eventual transition into bankruptcy.
“Today, Representative Counsel issued a letter to the Honorable Bill Blair, Canadian Minister of Public Safety and Emergency Preparedness, requesting an update on whether the RCMP will conduct an exhumation and postmortem autopsy on the alleged body of Gerald Cotten prior to Spring 2020,” the letter reads.
The document notes users can contact the minister directly via email “if they have further questions about the RCMP’s management of this file,” while also suggesting they can contact their Members of Parliament for possible answers.
An email sent to Blair was not immediately returned.
‘Law Enforcement Activities’
Tuesday’s letter follows an update from Ernst & Young (EY), the bankruptcy trustee for Quadriga. The company, which was appointed by the Nova Scotia Supreme Court last year to consolidate Quadriga’s crypto holdings, said Monday it was requesting a court approve nearly $640,000 CAD ($484,000 USD) in expenses for cooperating with multiple federal agencies.
According to the report, EY spent $188,939 CAD between June 24, 2019, and Dec. 31, 2019, “in connection with the Law Enforcement Activities.” In addition, Stikeman Elliott and Lenczner Slaght, law firms representing EY, charged $133,618 CAD and $314,599 CAD, respectively, over the same time period.
According to EY, much of this billing comes from analyzing 750,000 documents the company compiled into an “EDiscovery Database,” which was then used to determine which documents met production demands from the various law enforcement agencies involved.
“During the process, the Trustee made various efforts to minimize costs and to streamline wherever possible the accumulation, review and production of documents,” the report said. “This included utilizing the services of contract lawyers specialized in privilege review and available at a significantly lower billing rate than other professionals managing the overall Law Enforcement Activities.”
However, the sheer volume of documents meant that “significant” effort on EY and its counsel’s part were still required, the report claimed.
A nearly 80-page breakdown details how the expenses were accrued. The report did not provide any information on how many claims were filed by creditors or how much each creditor might expect to receive.
Updated: 1-30-2020
Alleged Launderer Of $4B In BTC Vinnik Charged In France After Extradition
French authorities have charged former operator of now-shuttered crypto exchange BTC-e and Russian national Alexander Vinnik.
Bloomberg reported on Jan. 28 that Vinnik’s lawyers said that he will remain in France to face his charges following his recent extradition from Greece. According to an unspecified official at the prosecutor’s office, Vinnik was charged with extortion, aggravated money laundering, conspiracy and harming automatic data-processing systems.
The Legal Shuttle
One of his lawyers said that after his trial in France has run its course, authorities are expected to send him back to Greece so he can be extradited to the United States. After the U.S. prosecution is over, he would be finally sent to Russia. The French investigation is ongoing and no trial has been ordered. Ariane Zimra, a French lawyer for Vinnik said:
“There is no causal link between what Alexander Vinnik is being accused of and Alexander Vinnik.”
Vinnik is currently in a French hospital after going on a hunger strike for 40 days to protest his detention. Vinnik’s lawyers also recently filed a complaint that alleges a violation of his rights on behalf of his children.
Zoi Konstantopoulou, one of his lawyers, suggested that he is being persecuted because he is a blockchain genius and is seen as a threat to the banking system. He said:
“Alexander’s crime is to be Russian and a person with extraordinary technological knowledge that could liberate people economically. […] The Greek Minister of Justice has in essence decided that this person is going to spend his life being extradited, judged and then re-extradited, re-judged and yet again re-extradited and re-judged.”
An Overview Of Vinnik’s Case
Vinnik is believed to be involved in the hack of Bitcoin exchange Mt. Gox since the 300,000 BTC stolen there were allegedly not only laundered through BTC-e but were also on his personal wallet. Given those suspicions, the Mt. Gox trustee contacted the U.S. Department of Justice and requested information about him.
Vinnik was first indicted by the U.S. in July 2017. A Greek Court later ruled for his extradition to Russia in September 2018. In July 2018, however, local authorities ruled to extradite him to France, where he is now.
The matter of Vinnik’s extradition is a major diplomatic ordeal with multiple countries trying to obtain his extradition. Russia, for instance, filed multiple requests and asked for help from the United Nations High Commissioner for Human Rights in an attempt to bring him under its jurisdiction.
Updated: 2-8-2020
Alexander Vinnik Claims Injustice While Now Fighting Charges In France
After spending 30 months in detention, Greek authorities have finally extradited the Russian national and alleged Bitcoin (BTC) money launderer Alexander Vinnik to France. Prosecutors in France are charging Vinnik, operator of the defunct BTC-e crypto exchange, with multiple counts of money laundering, extortion and conspiracy.
Vinnik also has pending extradition requests from both Russia and the United States. The alleged Bitcoin criminal has previously stated his preference for extradition to his native homeland, which Greek officials have turned down.
Thus, after the conclusion of his trial in France, Vinnik will return to Greece to face another extradition to the U.S. The U.S. State Department reportedly wants to question Vinnik in connection with the Mt. Gox hack and subsequent theft of 300,000 BTC allegedly traced to Vinnik’s personal crypto wallet. Reports also suggest that Russian state agents funneled money through BTC-e to fund interference in the U.S. 2016 presidential elections.
Amid the three-way diplomatic tussle, Vinnik’s legal team said that its client has been subjected to gross human rights abuses. Vinnik’s lawyers have also accused prosecutors of working to keep their client in detention without charges or a trial while preventing him from having any contact with members of his family.
Vinnik’s defense lawyers also allude to the prosecution being sponsored by political and business interests based on their client’s involvement in crypto and blockchain technology. The former BTC-e chief is one of a few crypto personalities to have run-ins with the law, much like Silk Road creator Ross Ulbricht, who is currently serving a double life sentence for running a darknet drug market.
Alleged Human Rights Abuses Amid Vinnik’s Two-Year Detention
In a phone call with Cointelegraph, Zoe Konstantopoulou, one of Vinnik’s lawyers, leveled allegations of human rights abuses against the Greek authorities. Commenting on the scale of these infringements, Konstantopoulou revealed:
“Alexander has been subject to arbitrary detention for 30 months, which is prohibited by the Greek constitution. During this period, he has been made to suffer cruel and inhuman treatment from the authorities.”
According to Konstantopoulou, Vinnik is being held without trial or charges and in the absence of any court orders. Konstantopoulou has also claimed that the case against Vinnik has some political undertones with vested interests in Greece, France and the U.S. looking to punish the former BTC-e operator.
When asked about the effect of these alleged maltreatments on Vinnik’s health, Konstantopoulou revealed that the health status of the Russian national continues to deteriorate. “Alexander is currently on the 44th day of his hunger strike in protest of the gross human rights violations suffered at the hands of the authorities in Greece,” she revealed during a call with Cointelegraph.
Apart from the alleged maltreatment, Vinnik’s lawyer also revealed that Greek law enforcement was preventing any contact between the former BTC-e operator and his family. According to Konstantopoulou:
“Greek law enforcement isn’t allowing Alexander to see his family, even his wife who has been diagnosed with brain cancer.”
In a private note to Cointelegraph on the Vinnik case, Yusaku Senga, CEO of cross-blockchain swap platform Swingby, said crypto personalities accused of wrongdoing usually suffer harsher punishments than their counterparts in mainstream finance. According to Senga:
“If we look at the prosecution of Charlie Shrem and compare it level of prosecution brought against Goldman Sachs and its senior directors for their involvement in the huge scale of money laundering and embezzlement in the 1MDB scandal in Malaysia, it’s hard not to argue that crypto advocates and entrepreneurs are being much more harshly persecuted.”
Like Vinnik, Charlie Shrem was also associated with another crypto exchange, BitInstant. U.S. authorities arrested Shrem in 2014, charged him with money laundering and sentenced him to two years in prison.
Timeline Of Vinnik’s Prosecution
In July 2017, Greek police arrested Vinnik while on vacation with his family in the tourist village of Ouranoupoli. Thus began the over two-year legal battle that has kept the Russian national behind bars while three different nations jostle for Vinnik’s extradition so he can face criminal charges.
Shortly after his arrest, the U.S. filed an extradition request and seemed to be successful in pushing for Vinnik’s transfer stateside. By September, officials in Moscow also requested Vinnik’s extradition to Russia.
By 2018, France entered the fray, turning the case into a diplomatic three-way tussle. Greek police also revealed an assassination plot with suspected Russian criminals reportedly intent on stopping Vinnik’s return to the country.
In mid-December 2019, Greek judicial authorities finally moved to extradite Vinnik to France to await trial. At the beginning of the year, Vinnik’s case entered a new phase with his extradition to France. Authorities in the country have already leveled money laundering and conspiracy charges against him.
Vinnik’s legal troubles stem from his alleged involvement in the BTC-e crypto exchange. Launched in 2011, the defunct platform saw little in the way of crypto trading activity until Mt. Gox — the market leader at the time — fell into financial trouble following one of the biggest Bitcoin exchange hacks in history.
With Mt. Gox out of the way, BTC-e grew exponentially, accounting for about 15% of all U.S. dollar-denominated Bitcoin trading activity by late 2016. Despite being a major player in the crypto trading space at the time, BTC-e had little in the way of Know Your Customer and anti-money laundering protocols.
Thus, the platform reportedly became a popular channel for funneling “dirty money.” Mt. Gox hackers allegedly used the exchange to launder 300,000 BTC, the exact amount of which was also found in Vinnik’s wallet.
Apart from the money laundering, several law enforcement authorities say BTC-e replaced Silk Road as the channel for illicit deals with many users of the platform engaging in drug trafficking and sales of other banned or regulated goods.
Concerning Bitcoin And Criminal Activities
Crypto critics usually espouse the same rhetoric of digital currencies as being channels for online criminal activities. Many financial regulators and governments opposed to or keen on strictly regulating the cryptocurrency industry usually tout the same refrain of digital currencies enabling tax evasion, money laundering and terrorist financing, to mention a few.
The counter-argument offered by crypto proponents is that Bitcoin and other cryptocurrencies only account for a small portion of global financial crimes. A January 2020 report by blockchain analytics firm Chainalysis revealed that crypto payments on the darknet accounted for 0.08% of all digital currency transactions in 2019.
Updated: 2-8-2020
Cryptocurrency Scams Took In More Than $4 Billion In 2019
Ponzi schemes are the latest form of bitcoin fraud, with big platforms like one called PlusToken drawing the most money.
Seo Jin-ho, a travel-agency operator in South Korea, wasn’t interested in exotic investments when a colleague first introduced him to PlusToken, a platform that traded bitcoin and other cryptocurrencies. But the colleague was persistent.
“You won’t regret this,” she said, according to Mr. Seo. She visited him several times early in 2019, telling him he could earn 10% a month. Finally, his skepticism gave way, and he bought $860 of cryptocurrency on the PlusToken platform.
His investment grew at a dazzling rate. He invested more—a lot more. In less than five months, he bought $86,000 of cryptocurrencies, cashing out only $500.
“I was thinking, what’s the point of keeping money in the bank?” said Mr. Seo, who is in his late 40s. He went to PlusToken conferences. He told his friends about it. He became a convert.
In June 2019, all that changed. Chinese authorities concluded PlusToken was a scam and arrested six Chinese citizens allegedly running the platform out of the Pacific island nation of Vanuatu. The site stopped working. People couldn’t get their money out. Mr. Seo, and myriad others like him, lost access to everything.
Big Year For Crypto Fraud
Bitcoin-based frauds raised more money in 2019 than in 2017 and 2018 combined.
Authorities in China declined to comment. Authorities in Vanuatu couldn’t be reached. In October, a man called Leo, who said he was the PlusToken chief executive, said “everything is OK” in a YouTube video. Attempts to contact representatives of PlusToken weren’t successful.
PlusToken was a Ponzi scheme. That was the conclusion by Chainalysis, a New York-based firm that designs software that can analyze cryptocurrency data and help track illicit transactions.
Its clients include the Federal Bureau of Investigation, the Drug Enforcement Administration and the Internal Revenue Service. PlusToken drew investors mainly in South Korea and China in 2018 and the first half of 2019. It netted at least $2 billion, Chainalysis said.
Cryptocrime is expanding. Ponzi schemes and other frauds involving bitcoin and cryptocurrencies lured at least $4.3 billion from investors in 2019, according to Chainalysis. That was a bigger haul than the combined $3 billion in 2017 and 2018.
After a boom in dubious initial coin offerings in 2017 and a number of hacks in 2018, Ponzi schemes have become among the most popular vehicles for fraud. The biggest ones have been prolific: Just six well-orchestrated scams were responsible for about 90% of the funds stolen last year, Chainalysis said.
“There’s been huge growth in ones that mimic investing opportunities,” said Kim Grauer, head of research at Chainalysis. They are becoming more sophisticated, larger in size and they reach into the mainstream, victimizing naive investors, she said.
Cryptocurrencies have struggled to find acceptance in the 11 years since bitcoin launched. At its height in 2017, bitcoin’s price neared $20,000, and it attracted a passionate following among some investors who predicted it would upend global finance and replace the dollar.
But the hype ran ahead of the fundamentals, and the bubble burst the next year. The number of average daily transactions in 2019, about 325,000, was up about 13% from 2017’s 288,000. But the dollar value of those transactions was flat. It totaled about $3.8 trillion in 2019, according to research firm TradeBlock, versus $3.7 trillion in 2017.
Still, there are plenty of inexperienced investors who have heard stories of bitcoin riches and think they can get rich, too. Fraudsters use that naiveté against them, said Christopher Janczewski, a special agent at the Internal Revenue Service who has led criminal investigations that involved cryptocurrencies.
“A lot of it is just traditional crime dressed up,” he said. “They’re still always driven by fear, or confusion, of missing the next boom.”
Federal law-enforcement agencies including the IRS, the Securities and Exchange Commission and the Justice Department have all been involved in different investigations into cryptocurrency-based illicit activities. The IRS declined to discuss any open investigations. The Justice Department couldn’t be reached for comment.
PlusToken had a futuristic slant in the materials that the group published, including a “white paper,” but operated like a classic Ponzi, according to Chainalysis and interviews with alleged victims. People opened accounts on the PlusToken platform, investing in cryptocurrencies like bitcoin and ethereum. The platform was supposedly trading on their behalf. Users were promised dazzling returns.
The alleged perpetrators organized meetups and elaborate conferences. They introduced a blond-haired Russian known only as Leo as chief executive and attempted to market him as a celebrity. Mr. Seo said he was told Leo had been an artificial-intelligence developer at Alphabet Inc.’s Google and had secured hundreds of millions of dollars of investment from the British royal family.
To bolster that claim, a group calling itself the PlusToken Alliance posted a photo on its Facebook page that appeared to show Leo at a charity reception with Prince Charles in London in 2019. It is unclear who maintained the page.
Without more information about his identity, a spokeswoman for Alphabet said she couldn’t confirm whether Leo had ever worked for the company. The Prince Charles Foundation, which represents Prince Charles, couldn’t be reached for comment.
The aggressive marketing paid off. Chainalysis tracked about 180,000 bitcoin, 6.4 million ether and 110,000 tether that went through PlusToken wallets. Calculating the prices at the various times investors deposited funds, those investments added up to $2 billion.
Some of that money appears to have been paid out to early investors, but Chainalysis said much of it was transferred to wallets likely controlled by the operators themselves.
Although big projects like PlusToken have drawn the most money, smaller operators trawl the internet as well. Gary Condry said he was victim of one of them in November.
Mr. Condry, a 70-year-old Army veteran in Wooster, Ohio, said he started texting with a man calling himself Jason Hanley whom he found on social media. Mr. Hanley maintained pages on Instagram and Facebook, where he promoted an investment website called cryptoinvestments247 and promised weekly payouts.
“I had never really invested in anything,” said Mr. Condry, who was already in debt. “Bitcoin sounded like the quickest way to make money,” he added.
Text messages between Gary Condry and a man calling himself Jason Hanley, who promised exponential profit for trading small amounts of bitcoin.
In late November, he gave Mr. Hanley $200, followed by an additional $700 in early December. Within weeks, he was told, his account had risen to nearly $17,000.
There was a catch, though. Mr. Hanley demanded an additional $1,700 before he would pay out Mr. Condry’s “profits,” according to text messages from Mr. Hanley that were reviewed by The Wall Street Journal. This wasn’t part of their agreement, Mr. Condry said. After a number of angry text messages, he said he gave up trying to cash out his profits, or to even recoup his original investment.
“I already lost it,” Mr. Condry said. “I didn’t see it.” Mr. Condry said he called the Ohio attorney general to report the events. The attorney general’s office couldn’t be reached for comment.
When reached by the Journal, Mr. Hanley declined to discuss Mr. Condry’s investment or cryptoinvestments247.
“I’m busy, man,” he texted later. “Got no time for everything.” An hour later, the Facebook account was deleted. Soon after, the Instagram account was gone, too.
In August, Mr. Seo was among some 200 PlusToken investors who filed a complaint with prosecutors in Seoul to kick-start an investigation into the alleged scam. Others in the group are still hoping their PlusToken wallets will start working again, he said.
“That false hope is killing people,” he said.
Updated: 2-11-2020
PlusToken Scam Moves $123M In Bitcoin Just As BTC Price Regains $10K
As Bitcoin (BTC) and Ether (ETH) price rallied to new 2020 highs on Feb. 11, a large transaction totaling nearly 12,000 BTC was moved from a wallet associated with the PlusToken Ponzi scheme.
Twitter-based crypto transaction bot, WhaleAlert, noted that “12,000 #BTC (118,852,619 USD) transferred from unknown wallet to unknown wallet.” This transaction was later followed by a second transaction splitting the 12,000 BTC into smaller sums.
According to PeckShield Inc. co-founder and VP of research, Chiachih Wu, a total of 12,423 BTC ($123 million) was moved into what Wu says appear to be cold wallet addresses.
Meanwhile, Twitter users Sue Zhu and ErgoBTC allege that the group behind the PlusToken scam is covertly moving a significant amount of Bitcoin from wallet addresses associated with the group. Zhu noted:
“Plus Token coins are on the move again, but more importantly, are now being split into smaller amounts vs the single output transfers from a few hours ago.”
As previously reported by Cointelegraph, the PlusToken Ponzi scheme was one of the largest scams in existence to rock the crypto sector. Initially, the project was presented as a South Korea-based exchange offering a high-yield return on investment but eventually, the entire operation was exposed as a scam after several million participants found they were unable to withdraw their investment.
In the past, such movements were followed by suspected massive open market sales on cryptocurrency exchanges which led to sharp corrections in Bitcoin, Ether and many other altcoin prices.
In 2019, Crypto Twitter researcher Ergo estimated that a major market sell-off was possibly driven by the PlusToken scammers liquidating 200,000 BTC on the open market. Ergo explained in November:
“If my numbers are correct, the 200k BTC estimates reported earlier this year were correct, and market impacts will continue for some time.”
Many analysts also believe that PlusToken sales are one of the primary catalysts for the 7-month long market downtrend that began after Bitcoin price reached $13,800 on June 26, 2019.
Given that Bitcoin has not long escaped this 7-month downtrend when bears completely controlled the price, investors casting a wary gaze at today’s transfers are not overreacting as the move could eventually culminate with a repeat of previous bulk crypto sales.
Adding further explanation to today’s transfers, Chiachih Wu said, “it seems a programmed transaction since all 7 new utxos are split into smaller parts (100-400 BTC) in the same block…will be gone soon.”
Considering that in 2020 Bitcoin price is up by 42.9% and Ether has gained 82.89%, now seems like an opportune moment for the PlusToken scammers to capitalize on their ill-gotten gains.
At the time of writing, both transactions have been confirmed and as the event gains traction in crypto media it will be interesting to see how investors and the price react to the possibility of some or all of the $123 million in Bitcoin being sold at market rate on cryptocurrency exchanges.
Updated: 2-13-2020
Coin Ninja CEO Arrested For Allegedly Laundering $311M With Bitcoin Privacy Tools
Larry Harmon, the CEO of Bitcoin media site Coin Ninja and founder of crypto wallet provider DropBit, is facing federal charges related to his use of Bitcoin privacy tools.
United States federal prosecutors are charging Harmon with conspiracy to launder money and operating a money transmitting business without a FinCEN license.
According to an arrest warrant filed earlier this month, Harmon allegedly laundered over 354,468 Bitcoins (BTC) (worth $311 million at the time of the transactions), allowing the users of a privacy tool named Helix, and a darknet search engine named Grams, to make transactions on AlphaBay, a known dark market that was shut down in 2017.
Helix allowed users to mix the coins before spending through a CoinJoin transaction. The mixing of coins has been associated with money laundering and other illicit activities.
Harmon is facing a 30-year prison sentence for these alleged crimes.
Harmon Denied Bail
Journalist and podcaster Peter McCormack reportedly spoke to Harmon’s brother, Gary Harmon, who said that Coin Ninja’s assets have been frozen and that the FBI has removed $4,000 in Bitcoin from its Lightning Network node.
According to McGormack, Larry has been denied release on bail bond because he was deemed a flight risk, “even though they have confiscated all his assets.”
The state attorney’s motion to detain Harmon shows that the state believes that Harmon will not reasonably appear in court if permitted a release on bail as he has “significant family ties outside the United States” and is “subject to a lengthy period of incarceration if convicted.
DropBit has gained some attention among Bitcoiners, particularly because it allows the users to send BTC on-chain and over the Lightning Network using Twitter handles or phone numbers. Since DropBit’s funds have been frozen, Gary Harmon and its developers are personally funding the wallet’s operations, according to McCormack.
Updated: 2-17-2020
New Email Extortion Scam Targets Google’s AdSense, Demands Bitcoin
A new extortion scam targeting website owners serving banner ads through Google’s AdSense program has begun circulating the Internet. The malicious scheme demands Bitcoin (BTC) in exchange for preventing an attack, which would purportedly lead to the users’ AdSense account suspension.
The email-based extortion scheme was reported by security news and investigation blog KrebsOnSecurity, on Feb. 17. The blog post detailed that some site owners received a message as their site had been spotted by the malicious program as one seeking revenue from publishing an ad. The message ostensibly read:
“Very soon the warning notice from above will appear at the dashboard of your AdSense account undoubtedly! This will happen due to the fact that we’re about to flood your site with huge amount of direct bot generated web traffic with 100% bounce ratio and thousands of IP’s in rotation — a nightmare for every AdSense publisher.
More also we’ll adjust our sophisticated bots to open, in endless cycle with different time duration, every AdSense banner which runs on your site.”
The message appears as a warning, wherein the cybercriminals demand $5,000 worth of BTC to deter the attack.
The user who shared the message with KrebsOnSecurity said that their recent AdSense traffic statistics had detected a substantially increased invalid traffic. Google ostensibly called the scam a classic threat sabotage, where a fraudster tries to trigger an enforcement action against a publisher by sending invalid traffic to their inventory.
Google’s Strict Policy Toward Ads
The news came on the heels of Google’s new policy regarding its ads, wherein the team behind AdSense said that it will stop showing ads before invalid clicks happen. “This year, we’re enhancing our defenses even more by improving the systems that identify potentially invalid traffic or high risk activities before ads are served.
These defenses allow us to limit ad serving as needed to further protect our advertisers and users,” Google explained.
Previously, Google took a hard line on decentralization and cryptocurrency. The most prominent example of hostility from Google occurred in June 2018, when the company announced that it would ban all crypto-related advertising in accordance with an update to its Financial Services policy.
Most recently, Google blacklisted keywords mentioning Ethereum (ETH) on its advertising platform, Google Ads. Google confirmed that “Ethereum” had been blacklisted as a keyword “regardless of the nature of the service that is being promoted.”
Criminals Increasingly Demand Bitcoin
The leading cryptocurrency has been gaining popularity among criminals around the world. Earlier in February, two letter bombs exploded in the Netherlands and an anonymous criminal asked for a Bitcoin payment to prevent future attacks.
In Thailand, Singaporean Mark Cheng was kidnapped and tortured for a $740,000 ransom in BTC. After transferring all his available funds of $46,000, he allegedly made a daring escape as his captors prepared to murder him.
Updated: 2-18-2020
Decentralized Lending Protocol bZx Hacked Twice In A Matter Of Days
Decentralized finance (DeFi) proponents are taking a hard hit after decentralized lending protocol bZx saw two successful hacks just days apart with losses totalling around $954,000.
According to bZx’s report, the protocol was compromised for the first time on Feb. 14, when the team was at the ETHDenver industry event. The second attack, according to industry news outlet The Block, took place on Feb. 18.
The First Attack’s Procedure
The attacker used multiple DeFi protocols to lend and swap significant quantities of Ether and wrapped Bitcoin (WBTC) — a token on the Ethereum blockchain that tracks the price of Bitcoin (BTC) — in a way that allowed him to manipulate the prices and profit off of a decentralized leveraged trade.
The attacker first took loaned 10,000 Ether (ETH) from decentralized lending protocol dYdX, then used 5,500 ETH ($1.46 million) to collateralize a 112 wrapped Bitcoin (WBTC) loan (over $1 million) on DeFi protocol Compound.
At this point, the attacker sent 1,300 ETH (over $372,000) to decentralized margin trading ETH to open a 5x leveraged position on the ETH/BTC pair on bZx’s Fulcrum trading platform and borrowed 5,637 ETH through Kyber’s Uniswap and swapped them for 51 WBTC, causing large slippage.
This, in turn, allowed the attacker to profit from swapping the 112 WBTC from Compound to 6,671 ETH, resulting in a profit of 1,193 ETH (nearly $318,000). The hacker finally paid back the 10,000 ETH loan on dYdX that he took before.
According to an in-depth analysis of the attack, the transaction with which the attacker opened the leveraged trade should have been prevented by safety checks, but those checks did not fire due to a bug in bZx’s smart contract. The team behind the protocol has announced that the bug has been patched.
The Second Attack
The nature of the second attack is still largely unclear, but a message from the project’s CVO and operations lead Kyle Kistner in the official bZx Telegram group suggests that it was an oracle manipulation attack. Oracles are usually centralized components that provide external data to on-chain applications.
The Block estimates the loss to be 2,388 ETH (nearly $636,000). Kistner said that the team can neutralize the hack and prevent the loss of user funds like they did for the first hack. Furthermore, he promised that bZx developers will switch to oracles based on the Chainlink protocol, seemingly suggesting that it would make the system safer.
Cointelegraph will update this article with further information once it is forthcoming.
The Prevalence Of Crypto In Hacks
The non-reversibility of transactions is a basic property of most cryptocurrency, or at least is strived for by most projects. While desirable for many reasons, this feature is also appreciated by cybercriminals who get to keep funds if they manage to steal them, while wire transfers could instead be reversed.
Hacker groups are also saying ahead of the curve by updating their methods. Cybersecurity firm TrendMicro recently discovered that hacking group Outlaw has been updating its toolkit for stealing enterprises’ data for nearly half a year.
Earlier this month, Cointelegraph reported that hackers compromised five United States law firms and demanded two 100 Bitcoin ransoms from each firm: one to restore access to data, and one to delete the hacker’s copy instead of selling it.
Updated: 2-18-2020
Chinese Exchange FCoin Closes Down, Still Owes Users $125 Million
Zhang Jian, founder of Chinese crypto exchange Fcoin, revealed in a post earlier today that FCoin may not be able to pay the 7,000-13,000 BTC (that’s $67 million to $125 million) that it owes users.
According to Zhang, the exchange hasn’t been hacked and isn’t an exit scam. But evidence suggests it might be exactly that.
Zhang claims that the shutdown is the result of a series of internal data errors and decisions that are too complicated to explain:
“This is a problem that is a little too complicated to be explained in a single sentence, the time span is also large, and the two story development lines are advancing and affecting each other at the same time, leading to the final outcome.”
The Beginning Of A Nightmare
After FCoin’s launch in May, the exchange’s reported trading volumes became some of the biggest in the world overnight with a new business model called “transaction mining.” Later it was reported by one Redditor that this volume was actually fake. The FCoin order book appears to be crawling with bots. “The price of FT is constantly manipulated,” wrote one Redditor, who also described the exchange as a scam.
The business model was suspicious from the get-go. There was no airdrop nor ICO at launch. FCoin distributed 51% of its native tokens to users for reimbursing transaction fees. Users were incentivized to transact as frequently as possible, since the platform reimbursed 100% of the transaction fees they paid in FT tokens. 80% of the exchange’s daily revenue from transaction fees were then paid back to users.
Binance’s CEO Changpeng Zhao has called FCoina Ponzi scheme since the middle of 2018. He also commented on Zhang’s post in a tweet:
“I rarely called out anyone, with exceptions. On Chinese social media, I called FCoin a pyramid scheme in mid-2018. Their founder calls his own plan a “better invention than #Bitcoin”. That did it for me. Who would say such a thing? About themselves? Except scammers.”
Zhang said there had been errors detected in the FCoin system ever since 2018 but did not explain why FCoin had failed to address such problems before it’s too late:
‘With the deepening of the investigation, we found a large number of existing data problems of dividends and mining returns, and these problems have existed for many days. As a result, a large number of users have already been through operations such as buying and selling various currencies and withdrawing cash, causing the pollution of assets.”
The platform was suspended a few days ago by its own account for risk-control. This caused a great deal of speculation that the project was shutting down and its operators were using it as an excuse vanish.
The Final Struggle
In the last few sentences on his blog post, Zhang claimed he would handle the users’ email requests for withdrawals personally. He also mentioned that he will compensate FCoin user losses with the profits he would make from his other projects. But then again, he did not mention what specific project he has been working on or when would he be able to pay back the money he owes to the users.
Some Chinese sites have reported that with Zhangjian’s admitting he owes users $125million debts, he might face potential civil lawsuits in the near future. Yet given that the exchange is registered overseas and Zhang has also moved out of China, it may be difficult for the FCoin case to see a domestic legal solution.
Updated: 2-22-2020
FCoin Blames Poor Auditing For Shutdown, But Others Suspect Exit Scam
Less than two years after bursting onto the scene, Chinese crypto exchange FCoin has shut down its operations. The platform, founded by Zhang Jian, also says it may be unable to pay the 7,000 to 13,000 Bitcoin (BTC) — about $67 million to $125 million — that is owed to its customers.
Jian, the former chief technology officer of Huobi, tried to explain the reasons for the platform’s insolvency, identifying poor auditing practices. Crypto pundits, however, say there is a more sinister aspect to FCoin’s demise — one that involves a cleverly orchestrated exit scam by the platform’s hierarchy.
An examination ofFCoin’s cold wallet shows numerous transfers to other cryptocurrency exchanges. The platform also destroyed a large cache of its eponymous native token, worth about $75 million.
With the platform’s crypto shortfall, it appears users will face significant difficulties in receiving their compensation from FCoin. Jian could also face legal troubles, especially seeing as authorities in Beijing are keen on extending the crypto trading ban to exchanges domiciled overseas but still providing services to Chinese citizens.
Jian’s Tell-All
In a post published by Jian on Feb. 18, 2020, the FCoin founder attempted to set the record straight concerning the platform shutting down. As previously reported by Cointelegraph, Jian revealed that in addition to going out of business, the platform may not be able to pay back as much as 13,000 BTC owed to its customers. An excerpt from Jian’s tell-all reads:
“The internal problems and technical difficulties we face are the result of financial difficulties. It is expected that the scale of non-payment is between 7,000–13,000 BTC.”
According to Jian, FCoin’s demise was neither due to a hack or an attempted exit scam. Instead, the former Huobi CTO blamed a series of data and decision errors — specifically concerning proper auditing of the payouts of the platform’s transaction mining model.
The FCoin founder’s statement revealed that several months of the platform’s operations went by before the exchange began implementing any significant checks and balances in its back-end. This operational failure eventually led to catastrophic consequences for the crypto exchange.
A Little Bit Of History
In May 2018, FCoin entered the crypto exchange scene with a novel business model called “trans-fee mining.” This new development took the concept of exchange tokens to another level by reimbursing users with a percentage of the transaction fees received by the platform.
In FCoin’s case, this reimbursement was 100% of the trading fee for each transaction. Thus, for every crypto trade on its platform, FCoin would pay back the user the full amount of the transaction in its native FCoin Token (FT).
Data from the report at the time showed that platforms using the same model as FCoin had been accounting for 12% of the total crypto spot trading market. Traders looking to enjoy what was essentially cost-free transactions were rushing to FCoin and the likes to trade their tokens. Beyond reimbursing users with 100% of their trading fees in FT, FCoin added another layer to its trans-fee mining model by paying its users 80% of its daily revenue.
This meant users were incentivized to trade on platforms that make use of the trans-free mining model, which ultimately led to an explosion of activity. According to CryptoCompare’s December 2018 review of cryptocurrency exchanges, platforms running the trans-fee mining model were beginning to pull-in significant trading volumes.
By 2019, FCoin adjusted its trans-fee mining model, canceling the 100% FT reimbursement, deciding instead to payback transaction fees with the cryptocurrency in which the trader executed the trade. The Chinese crypto exchange also reduced its daily revenue payback to 20%, with the remaining 80% held for one year and still allowing FT holders to earn interest during the holding period.
These adjustments, made at the end of April 2019, were supposed to help the platform move toward a more sustainable operating model. However, as the narrative below will show, the move came too late to salvage what was already a crypto exchange in dire straits.
FCoin’s Trans-Fee Mining Bubble
In theory, trans-fee mining ought to incentivize users to trade frequently, thereby increasing the exchange’s transaction volume. In reality, the model encouraged dishonest activities — an influx of bots, spoofing, wash trading, etc. To earn more money per trade, rogue actors would collude to create fake transaction volumes, propping up the trading activities on these platforms.
In 2019, several reports emerged showing that the majority of volume data provided by crypto trading metrics providers such as CoinMarketCap was from wash trading. Most of the platforms singled out in a Bitwise report were running some form of a trans-fee mining protocol.
It didn’t take long after the emergence of FCoin and trans-fee mining for some crypto pundits and other stakeholders to issue multiple warnings about the model. Back in 2018, Binance CEO Changpeng Zhao called trans-fee mining a reverse initial coin offering. At the time, Zhao remarked:
“You use BTC or ETH to pay for the transaction fee to the exchange, where it pays you back 100% via the exchange tokens. Isn’t it the same with using BTC or ETH to buy the exchange tokens?”
While FCoin was pulling in large transaction volumes, the back-end architecture that ought to prevent any abuse of the system was not yet in place. With the increasing transaction volume came a spike in the price of FT.
Buoyed on by the upward trajectory of FT’s price action, platform users were increasing their transactions on the platform, earning valuable FCoin tokens that were likely sold for other cryptocurrencies like Bitcoin.
Meanwhile, poor back-end controls on the exchange meant that some users were receiving fee reimbursements in excess of the stipulated amounts prescribed by the model. Then came the crash of FT, with the price falling by about 95%.
FCoin Price Crash On Aug. 30, 2019
According to Jian, this decline and the discovery of irregular FT payments forced the team to use the exchange’s resources to buy a significant portion of the tokens back in a bid to create scarcity and engineer a return to upward price action. However, the FT buybacks ultimately failed to rescue FCoin. Instead, there seems to have been a steady outflow of funds from the platform’s Bitcoin wallets right up until the announcement of the exchange’s shutdown.
Following The Money
The flow of funds from FCoin Bitcoin wallets also provides further insight into how the trans-fee mining bubble caused the demise of the crypto exchange. Crypto forensic startup PeckShield published a report detailing cryptocurrency transfers from the platform’s wallets.
Balance of FCoin’s cold wallet, April 2018 to February 2020
According to the report, FCoin’s cold wallet held 13,272 BTC in mid-July 2018. This figure is the largest Bitcoin cache held by the exchange, and it signaled the prosperous early months of the platform’s operations.
However, over the following six weeks, FCoin’s holdings dropped 10,000 BTC, as just 3,505 BTC was left in the cold wallet by August 2019. This period — from mid-July 2019 to the end of August 2019 — lines up perfectly with the first discovery of irregular reimbursements and other data errors alluded to by Jian in his statement earlier this week. An excerpt from PeckShield’s report translated from Chinese reads:
“We speculate that FCoin’s cash flow problem may already have emerged in July 2018. Pandora’s box may have been opened at that time when it was in the limelight.”
In summary, FCoin’s cold wallet saw two major outflow streams — totaling 8,009 BTC and 11,107 BTC — and a third, smaller transfer of 55 BTC. These outgoing transactions occurred over a period spanning from June 13, 2018, and Feb. 17, 2020 — the day before Jian’s public statement.
From these two major streams, smaller BTC amounts were funneled to major crypto exchanges such as Huobi, Coinbase, Bitstamp and OKEx, to mention a few. In total, PeckShield estimates that more than 19,100 BTC was transferred out of the FCoin cold wallet. Another translated excerpt from the report reads:
“We have statistically summarized all FCoin-related address balances and found that there are about 477 BTC remaining.”
Unanswered Questions
With events still unfolding, unanswered questions persist about the nature of FCoin’s demise. For one, why was there an increasing amount of net BTC outflows from the platform’s cold wallet while the price of FT was tumbling?
These outflows do not appear to be user withdrawals, given their non-random nature. Data from on-chain analysis shows that the transaction amounts were always nice, round digits such as 100 BTC or 150 BTC. Dovey Wan, a founding partner at blockchain investment firm Primitive Ventures, argued that the orderly distribution of the net outflows is proof that those transactions were not user withdrawals.
In a separate analysis by white hat crypto transaction analyst ErgoBTC, there is evidence that shows every outbound transaction from FCoin’s cold wallet is followed by a 100 BTC or 150 BTC deposit on an exchange such as Huobi or OKEx.
Another puzzling question from the FCoin debacle shows up in the absence of net outflows between April 2019 and August 2019. Why would a crypto exchange’s cold wallet, which had seen drastic changes in its balance over a period of almost one year, suddenly come to a standstill for four months?
Exit Scam, Ineptitude Or Both?
As for the question of whether FCoin’s demise was an exit scam or the product of ineptitude on the part of the platform’s hierarchy, Josh Lawler, a partner at Zuber Lawler and Del Duca LLP, told Cointelegraph:
“The story of FCoin, intentional or otherwise, is that of a Ponzi scheme. The facts and circumstances would be violations of any number of regulatory laws designed to prevent exposure of the investing public to fraud and incompetence. At best, FCoin’s story is a combination of the two. In the digital asset space, it is a cautionary tale as to what happens when undercapitalized and over-exuberant entrepreneurs try to become instant unicorns.”
In his statement, Jian promised to pay back affected users, revealing that he was personally overseeing email withdrawal requests from users of the platform. According to Jian, this process could take between one and three months, with the FCoin founder stating that profits from his next venture will also be used to compensate the victims of the crypto exchange’s insolvency.
FCoin published a statement on Feb. 20 that stated it was considering reopening the exchange. According to the letter: “At present, the social committee and Zhang Jian are discussing the restart plan, and the follow-up will be gradually disclosed to the community according to the process.”
Justin Sun, the CEO of Tron (TRX), has also pledged to help affected FCoin users, promising 1,000 BitTorrent tokens (BTT) to each FCoin customer who moves to the Poloniex exchange. Back in November 2019, Sun was reportedly part of a team of investors that acquired Poloniex from Goldman Sachs-backed fintech firm Circle.
Updated: 2-22-2020
Bitcoin Cash Faces ‘Slow Death’ After Alleged $30M Hack — Commentator
Altcoin Bitcoin Cash (BCH) has become the subject of intense speculation after a major investor claimed he lost $30 million in a wallet hack.
In a now-deleted Reddit post from Feb. 22, the investor, who appears to be Dreamhost founder Josh Jones, said the attacker also stole 1,500 Bitcoin (BTC) worth $14.4 million.
Hacker Steals Reported $45M
The hack came in the form of Jones’ SIM card being compromised. So far, he has not confirmed whether this was a so-called “SIM swap,” or whether the funds were commandeered by other means.
In the deleted post, Jones appealed to BCH miners not to validate the transactions. He wrote:
“It’s only had 3 confirmations, if any miners/the community can help somehow, I’ve got the private keys. Help help help.. Big reward obviously.”
Commenting on the events, Dovey Wan, founding partner at crypto asset fund Primitive Ventures, warned that the impact would go far beyond Jones himself.
In a series of tweets, Wan reproduced the Reddit post, criticizing Jones for keeping such a large amount of cryptocurrency in a wallet accessible simply from his smartphone. She described the attack as “really brutal.”
Wan: BCH Drama Will Result In “Slow Death”
Subsequently, Wan added that the hacker was splitting up the stolen funds, likely in an attempt to conceal their origin and make them easier to sell on exchanges.
“RIP BCH .. only a double-spent can help this poor guy now,” she wrote, continuing that Bitcoin Cash as a cryptocurrency faced a significant threat:
“No matter what, this 60000 $BCH hack, the dispute among BCH camp between Ver and Jihan, all these will mark a slow death of it.”
As Cointelegraph reported, Bitcoin Cash has seen various contentious events throughout its lifespan, including a hard fork in 2018 which resulted in the creation of another altcoin, Bitcoin SV (BSV).
It is unclear which other problems Wan was referencing when she mentioned two of its leading figures — Bitmain executive Jihan Wu and Bitcoin.com founder Roger Ver.
At press time, BCH/USD had barely reacted to the hack, slipping just 1% on the day to trade at $373. Year to date, the pair is still up over 80%.
Updated: 2-26-2020
Ex-Microsoft Employee Convicted of 18 Felonies In Digital Currency Scheme
A former employee at Microsoft has been found guilty of 18 federal felonies in connection with a complex scheme to embezzle $10 million using cryptocurrency.
The man — a 25-year old Ukrainian national, Volodymyr Kvashuk — worked as a full-time software engineer at the firm from August 2016, before being fired in June 2018.
Kvashuk was convicted in the United States District Court in Seattle, the Department of Justice revealed on Feb. 25.
“A House of Lies”
The multi-count conviction reveals the complexity of Kvashuk’s scheme, in which he hid behind accounts tied to his fellow employees and resorted to extensive fraud and cryptocurrency mixing services to cover his tracks.
The 18 felonies thus span five counts of wire fraud, six counts of money laundering, two counts of aggravated identity theft, two counts of filing false tax returns, and one count each of mail fraud, access device fraud, and access to a protected computer in furtherance of fraud.
In his role at Microsoft, Kvashuk was involved in testing the corporation’s online retail sales platform. He exploited his testing access to steal “currency stored value,” such as crypto gift cards, which he then resold at a profit on the web.
Beginning with small amounts of $12,000 in value using his own account access, Kvashuk turned to using test email accounts linked to other employees as the magnitude of his thefts escalated to millions of dollars.
To further obscure his connection to the scheme, Kvashuk used a Bitcoin mixing service to muddy the digital source of the funds that ultimately were cashed into his bank account.
Over a seventh month period, roughly $2.8 million in Bitcoin was transferred into Kvashuk’s account. He also used the ill-gotten proceeds to buy luxury goods, including a $160,000 Tesla car and a $1.7 million lakefront home.
Kvashuk falsified tax return forms, falsely claiming he had received the Bitcoin as a gift from family. Assistant U.S. Attorney Siddharth Velamoor told the court Kvashuk’s “crime of greed” dripped “fraud and deceit every step of the way.”
During the five-day trial, Kvashuk claimed he had been working on a special project for Microsoft’s benefit, rather than intending to defraud the firm. Velamoor’s colleague, assistant attorney Michael Dion, characterized the testimony as “a house of lies on top of a previous house of lies.”
For his crimes, Kvashuk faces up to 20 years in prison.
The crimes were reportedly thwarted by the U.S. tax agency IRS-CI Cyber Crimes Unit. Pointing to Kvashuk’s theft from both Microsoft and the federal government, IRS-CI special agent in charge Ryan L. Korner said:
“Criminals who think they can avoid detection by using cryptocurrency and laundering through mixers are put on notice […] you will be caught and you will be held accountable.”
Strengthening Investigative Powers
Earlier this month, U.S. President Donal Trump’s proposed budget laid out a tough stance against crypto-associated financial crimes.
It included a proposal to reconsolidate the Secret Service with the Department of the Treasury to improve the efficiency of cyber and financial crime investigations.
The administration also revealed it intends to continue to invest in tools that can help the government to combat new threats, such as the use of crypto in money laundering and terrorist financing.
Updated: 2-28-2020
Crypto Exchanges OKEx and Bitfinex Suffer Simultaneous DDoS Attacks
Cryptocurrency exchanges OKEx and Bitfinex are suffering multiple denial of service attacks. It is unclear as of now if the attacks are connected, though OKEx CEO blamed competitors on his personal Weibo page.
OKEx first suffered a distributed denial of service (DDoS) attack on Feb. 27 at approximately 11:30 AM EST. CEO Jay Hao posted on his personal Weibo page as the attack was unfolding, blaming unnamed competitors in the attack. The attack routed as much as 200 gigabytes per second of traffic, which put strain on OKEx systems.
At approximately 4:30 AM EST on Feb. 28, the denial of service attacks resumed. This time Bitfinex was hit as well, as announced by the exchange’s Twitter account.
The Bitfinex status page shows that the attack lasted for an hour until 5:30 AM, severely crippling the exchange’s activity during that period as throughput fell close to zero.
In the same timeframe, OKEx was attacked again with another DDoS attack, as tweeted by Hao. The new denial attack reportedly routed 400 gigabytes per second of traffic, twice as much as the previous one.
An OKEx representative told Cointelegraph that the denials of service were “properly handled within a short period of time and no overseas client is impacted.”
The attack was conducted shortly after “temporary system maintenance” was completed, which had options and futures trading disabled during the maintenance period. The representative stated that the two events are completely unrelated.
Bitfinex representatives stated that the team implemented a “stricter protection level” as normal activity was resumed.
Bitfinex CTO Paolo Ardoino shared more information about the attack with Cointelegraph. He explained:
“The attacker tried to exploit concurrently several platform features to increase load in the infrastructure. While we use many different DDoS prevention mechanisms, the huge number of different IP addresses used and the sophisticated crafting of the requests towards our API v1 exploited an internal inefficiency in one of our non-core process queues.”
While he says that the platform was not affected in its core services and could resist the attack, he decided to enter maintenance to “quickly bring in the countermeasures and patch for all similar attacks.”
What could be the culprit?
Bitfinex CTO, Paolo Ardoino, revealed in a tweet that the attack was “very sophisticated,” with the team having “worked hard to completely annihilate it in a short period of time.”
In a follow-up tweet, he revealed that he was not aware of the OKEx attacks, but was “interested to understand similarities.” He added:
“We’ve seen a level of sophistication that means a deep preparation from the attacker. Good news: this family of attacks won’t work again against Bitfinex.”
While Hao had initially blamed competitors, this was before the next attacks. It is unclear if they are connected with each other. While DDoS attacks are highly disruptive, their short duration is unlikely to alter the competitive landscape between exchanges.
Updated: 3-2-2020
Whistleblower Outs ‘Wolf of Kyiv’ For $70 Million Bitcoin Scam
A whistleblower has revealed the existence of a 200-employee Ukrainian Bitcoin (BTC) trading scam that netted $70 million in 2019.
The whistleblower outed the scam by providing footage and internal company documents to Swedish newspaper Dagens Nyheter, which reported the news on March 1.
The scam predominantly targets investors based in Australia, New Zealand and the United Kingdom by using fake news articles advertised on Facebook and some mobile game platforms.
The stories feature interviews with celebrities who purportedly made a killing by investing in crypto — including Gordon Ramsey, Hugh Jackman and Martin Lewis.
Ukrainian Company Milton Group Accused Of Operating Scam
The whistleblower claims that the scam is being perpetrated by Ukrainian company Milton Group from two floors of an office building in Kyiv. The offices are kitted with professional telephone and client management systems.
After responding to the ads, victims would be contacted by call-center workers promising extraordinary returns from cryptocurrencies, foreign currencies and commodities. Fake account statements detailing profits are used to entice further investment from the scam’s victims.
Jacob Keselman, the CEO of Milton Group stated that the allegations against it are “incorrect” in a phone interview with Dagens Nyheter. Keselman describes himself as “the wolf of Kyiv” on his Instagram profile.
Scammers Encourage Victims To Borrow To Invest
The whistleblower claims to have been a part of the scams “retention” team, where he was expected to make 300 calls each day.
He was tasked with “squeez[ing] the money” from clients until their “last cent,” and was remunerated on a commission basis.
The operation reportedly poses under many different business titles, including contacting victims under the guise of offering scam recovery services after they have already been duped. If receptive, victims are encouraged to install software on their computer that allegedly steals their online banking information.
The scam also impersonates national tax authorities, posting letters demanding that prospective victims settle fabricated tax debts.
Some Victims Have Lost Everything
The organization reportedly netted $70 million in 2019, and Dagens Nyheter noted that many victims have been duped out of their life savings.
Internal documents reportedly show employees gleefully recounting having “f***ed” investors, including a note on a customers’ account that states, “Getting f***ed every month for at least 1,000 EUR. Gets pension on the 20th/works every Tuesday.”
The Guardian contacted 16 British victims of the scam, who recounted receiving an onslaught of phone calls after responding to ads. A victim identified as Teresa stated:
“You get bombarded by all of these different companies. I don’t know if any of them are the same. They were calling all day, every day, all through the weekends […] Sometimes you’re on the phone to one company and the phone is buzzing with a call from another.”
Dagens Nyheter spoke to one 67-year-old Swedish victim who claimed that she can no longer pay her rent or buy food. Internal documents revealed her file, which contained a note stating, “Sold her home to pay, no money, crying.”
Crypto Threat Landscape Evolves
February saw cybersecurity firm ThreatFabric identify several sophisticated Remote Access Trojans (RATs) targeting cryptocurrency wallets and exchanges.
The RATs include ‘Cerberus’, which targets Coinbase users by stealing 2-Factor Authentication (2FA) codes for the Google Authenticator app.
Updated: 3-2-2020
US Treasury Department Blacklists 20 Bitcoin Addresses Tied To Alleged North Korean Hackers
The U.S. Treasury Department’s Office of Foreign Asset Control has added 20 new bitcoin (BTC) addresses associated with two individuals to its list of sanctioned individuals.
According to an update to OFAC’s “Specially Designated Nationals” (SDN) list, Jiadong Li and Yinyin Tian are accused of being linked to the Lazarus Group, a cybercrime group possibly affiliated with the North Korean government.
The group has been accused of stealing more than half a billion dollars in crypto as far back as 2018, when cybersecurity vendor Group-IB claimed it had targeted 14 different exchange in two years. Monday’s action specifically stems from the hack of an unnamed exchange in April 2018, according to a press release by the Treasury Department.
According to a grand jury indictment unsealed Monday and flagged by George Washington University’s Seamus Hughes, the two are charged with conspiracy to launder monetary instruments and operating an unlicensed money transmission business.
A separate in rem forfeiture document unsealed Monday shows the U.S. government is trying to seize the crypto held in 113 different addresses, alleging that the two defendants (who are explicitly named on page 21) laundered “a bulk of the stolen BTC.”
According to the forfeiture document, a total of $234 million in crypto was actually stolen, including bitcoin, ether (ETH), zcash (ZEC), dogecoin (DOGE), XRP (XRP), litecoin (LTC) and ethereum classic (ETC).
Most of the proceeds from the hack were laundered through the use of “peel chains,” a term the U.S. government is using to describe the act of sending crypto from one address to another, with some portion of the funds moving to a different address than the bulk in each transaction.
The litecoin was not properly laundered, and appears to remain at the address it was sent to.
The defendants sold some of the crypto to U.S. customers and used a U.S.-based exchange for some transactions, according to the forfeiture document. A South Korean exchange is also implicated in the document.
The Agency Listed 12 Addresses Associated With Jiadong Li:
XBT 1EfMVkxQQuZfBdocpJu6RUsCJvenQWbQyE
XBT 17UVSMegvrzfobKC82dHXpZLtLcqzW9stF
XBT 39eboeqYNFe2VoLC3mUGx4dh6GNhLB3D2q
XBT 39fhoB2DohisGBbHvvfmkdPdShT75CNHdX
XBT 3E6rY4dSCDW6y2bzJNwrjvTtdmMQjB6yeh
XBT 3EeR8FbcPbkcGj77D6ttneJxmsr3Nu7KGV
XBT 3HQRveQzPifZorZLDXHernc5zjoZax8U9f
XBT 3JXKQ81JzBqVbB8VHdV9Jtd7auWokkdPgY
XBT 3KHfXU24Bt3YD5Ef4J7uNp2buCuhrxfGen
XBT 3LbDu1rUXHNyiz4i8eb3KwkSSBMf7C583D
XBT 3MN8nYo1tt5hLxMwMbxDkXWd7Xu522hb9P
XBT 3N6WeZ6i34taX8Ditser6LKWBcXmt2XXL4
OFAC Listed Eight Addresses Affiliated With Yinyin Tian:
XBT 134r8iHv69xdT6p5qVKTsHrcUEuBVZAYak
XBT 15YK647qtoZQDzNrvY6HJL6QwXduLHfT28
XBT 1PfwHNxUnkpfkK9MKjMqzR3Xq3KCtq9u17
XBT 14kqryJUxM3a7aEi117KX9hoLUw592WsMR
XBT 1F2Gdug9ib9NQMhKMGGJczzMk5SuENoqrp
XBT 3F2sZ4jbhvDKQdGbHYPC6ZxFXEau2m5Lqj
XBT 1AXUTu9y3H8w4wYx4BjyFWgRhZKDhmcMrn
XBT 1Hn9ErTCPRP6j5UDBeuXPGuq5RtRjFJxJQ
While thousands of bitcoin appear to have flowed through the listed addresses, the majority appeared to hold no bitcoin as of press time.
Monday’s move is the third time OFAC has listed cryptocurrency addresses on its sanctions list. In 2018, the agency tied bitcoin addresses to a pair of Iranian nationals it accused of facilitating financial transactions related to ransomware. Last year, the agency also listed a litecoin address and additional bitcoin addresses affiliated with three Chinese nationals it charged with violating money laundering and drug smuggling laws.
According to the Treasury Department’s press release, “North Korea’s malicious cyber activity is a key revenue generator” for the nation. The country uses peer-to-peer marketplaces and exchanges with “negligible” know-your-customer controls, and crypto stolen by the nation can be used in a variety of ways.
“Given the illicit finance risk that cryptocurrency and other digital assets pose, in June 2019 the Financial Action Task Force (FATF) amended its standards to require all countries to regulate and supervise such service providers, including exchangers, and to mitigate against such risks when engaging in cryptocurrency transactions,” the press release said.
“The United States is particularly concerned about platforms that provide anonymous payment and storage functionality without transaction monitoring, suspicious activity reporting, or customer due diligence, among other obligations.”
OFAC also deleted a number of Russian entities linked to the Independent Petroleum Company from its sanctions list in Monday’s action.
Updated: 3-3-2020
How To Stop The Next Quadriga: Make Exchanges Prove Their Reserves
CoinDesk columnist Nic Carter is partner at Castle Island Ventures, a public blockchain-focused venture fund based in Cambridge, Mass. He is also the cofounder of Coin Metrics, a blockchain analytics startup.
What differentiates bitcoin from its analog cousin, gold? You might respond ‘divisibility’ or ‘portability.’ You would be correct. But what really differentiates it? The answer, of course, is auditability.
Consider the set of things you can prove about a lump of gold. If you use it as a settlement medium, with the help of an XRF Spectrometer (available for sale for $13,500), you can prove that this inbound fleck of gold is genuine. Now what can I prove about your gold? Well, nothing. I have to take your word for it that it is in fact gold.
This isn’t an issue, unless you’re holding the gold on my behalf. Now I have a problem: I’ve entrusted you with my gold — perhaps you’ve issued me an IOU that represents a claim on that gold — but I have no ability to determine that you have the gold you claim you have on deposit. I cannot audit your gold from afar.
Perhaps I choose to trust you. But if you don’t go to the effort of re-verifying all the gold you receive, then you need to prove to me, your depositor, that all of your counterparties in the gold supply chain are honest. And they need to prove that their counterparties — miners, refiners, jewelers, recyclers, custodians — are honest, too. The outcome is a fully permissioned supply chain in which a single body holds each entity to account with a convoluted ruleset.
One such walled garden is governed by the London Bullion Market Association, which manages $400 billion worth of gold sitting in vaults in London. Because it’s so costly to administer a gold supply chain, link by link, and ensure that not only is the gold, well, gold, but that it’s gold stamped by the right people, LBMA gold rarely strays outside those confines.
And this is the best case scenario, believe it or not. The other outcome is that the government (or really, a single government) holds everyone’s gold and then refuses to give it back when the time comes.
So costly verification leads to concentration. The more expensive it is to verify the integrity of a monetary good, the more taking delivery of it is difficult for smaller holders, and the more it lends itself towards capture.
“One potential solution is to demand that exchanges issue periodic proofs that they actually have dominion over assets owed to depositors.”
Take bitcoin (BTC), on the other hand. How do you verify the validity of some inbound bitcoin you are receiving? For the paranoid: run a full node. Using the beefiest providers, it’ll set you back $150 per month, or you can build your own with a $35 Raspberry Pi. What about verifying the integrity of all the bitcoin ever mined?
Your full node does that by default, simply by following consensus rules. For each block, it checks that there was a sufficient cost exerted to create those new bitcoins, and that they were mined according to the predefined schedule (50 BTC per block for four years, then 25, and so on). To obtain a summary, run the gettxoutsetinfo RPC command on your full node.
Now what about you proving to me that you truly own some bitcoin that you claim you own? Thanks to public-key cryptography, this is trivial. The most convenient way in bitcoin is to use the signmessage RPC command present in software like Bitcoin Core or Electrum.
I provide you with a string of text, and you pair it with your private key to create a proof that you own some given UTXOs. This is quite powerful: trusting only cryptography, I can know for a fact that you control a specific quantity of bitcoin at a moment in time.
Some bitcoiners believe bitcoin’s auditability advantages over gold will allow it to escape the dismal fate suffered by the shiny rock. President Nixon had an easy time voiding the gold standard in 1971 because most of the relevant gold was already held in U.S.’s government vaults. Bitcoin is held by millions of people. And I count myself among those who are optimistic that bitcoin’s properties as highly auditable collateral will yield a monetary base asset which is held mostly by end users, rather than a tiny handful of intermediaries.
Despite the ease of taking ownership of one’s bitcoins, the reality is that, by my count, at least 20 percent of outstanding supply is held by intermediaries. Although those in the Rothbardian school would disagree with me, I don’t believe that fractional reserve banking is inherently fraudulent.
The fraud occurs when exchanges represent themselves as fully reserved when they are not. In theory, bitcoin’s qualities lend themselves to mitigating this risk. Even in a custodial setting, the auditable nature of bitcoin means that savers can independently verify that the liabilities of depository institutions match their assets. The problem is that some of the most prominent bitcoiners don’t share my enthusiasm for the idea. Problematically, this group includes the CEOs of the bitcoin banks, today referred to as exchanges.
These bitcoin banks are the prime beneficiaries of the existence of bitcoin. They are the largest businesses in the industry. The public has an insatiable demand for intermediated bitcoin, and has paid dearly for the privilege. Exchanges store a wonderfully auditable asset, but for the most part, they simply ask depositors to trust them not to misbehave by establishing covert fractional reserves. And the history of bitcoin banks is full of breaches of that trust.
The list is long and painful: Mt. Gox, Quadriga, FCoin, Cryptopia, Bitfinex, Cryptsy and Bitcoinica, among many others, have all suffered major hacks or insolvencies. Exchanges simply have too lousy a track record to get a pass.
Exchanges are meant, in theory, to distinguish operating capital from user deposits, and to hold those deposits equivalent on a 1:1 basis to liabilities. In practice, either through malice or incompetence, some exchanges never develop sufficiently strong controls, fail to mitigate key man risk, or simply lose track of their coins. Since redemptions rarely come all at once, these insolvencies can go undetected for years. Unknown to the unwitting buyer, Mt. Gox was most likely already insolvent when it was sold to Mark Karpeles in 2011.
For sure, depositors can find some assurances in laws and regulation: if an exchange has a Bitlicense or a license to operate Limited Purpose Trust Company in New York, it is likely subject to reasonable scrutiny over its deposit-taking activity. Even better: registering as a Wyoming Special Purpose Depository Institution. The Wyoming law stipulates specific requirements for deposit-taking “crypto banks” designed to give depositors confidence – although no institutions have received the charter just yet.
Generally speaking however, exchanges are not forthcoming with the details of the audits they may undergo, when they do exist. And many exchanges are lightly- or entirely un-regulated. Some of the deepest pools of liquidity in the crypto industry – Binance, BitMEX, Derebit, Bitfinex, among others – are not meaningfully regulated in any sense. Now bitcoiners should demand not more regulation, but rather seek to head off future regulatory power grabs by holding exchanges to a higher standard in the first place.
One potential solution is to demand that exchanges issue periodic proofs that they actually have dominion over assets owed to depositors. These “Proofs of Reserve” (PoR), if done properly, leverage bitcoin’s neat cryptographic properties and give depositors reasonably sound assurances that the exchange is not misrepresenting their solvency.
Such PoR ceremonies purport to prove that deposit-taking institutions have sufficient BTC in reserve to satisfy all liabilities owed to depositors. After a brief period of enthusiasm for the public audits in the wake of Mt. Gox in 2014, today only one exchange routinely carries out these attestations — the London-based Coinfloor.
I envision a robust, periodic PoR program not as a panacea, but as a complement to regulation in onshore exchanges, and an (inferior) substitute offshore. If some operations, formerly reliant on contracts and trust, can be formalized and expressed as code, we should embrace them.
Now the set of engagements in which software and cryptography outperform the standard trust-manufacturing processes is rather small. But proving custody of a digital asset is one case where signmessage is more convenient, and perhaps cheaper, than an auditor’s report. While implementations vary, the process as it is currently carried out entails posting an anonymized list of user deposits as well as an attestation to BTC held in the vault.
Proof of Reserve and other solvency attestations are not without their drawbacks, and exchanges have managed to trick assessors implementing the process in the past, but we shouldn’t forget the broader objective here. If we are unable to take advantage of the innate cryptographic verifiability of bitcoin, then we have scarcely innovated relative to gold. One wonders – what are we doing here, again?
Updated: 3-4-2020
YouTuber Sentenced To 50 Years For Kidnapping And Bitcoin Ransom
25-year-old Mexican YouTuber Germán Abraham Loera Acosta has been sentenced to 50 years in prison for masterminding a woman’s kidnapping in February 2018 in Chihuahua, Mexico.
Acosta is one of six men convicted for the kidnapping. The group demanded $100,000 in Bitcoin (BTC) in exchange for the release of 33-year-old lawyer Tania Denisse.
Jassiel Omar Molina Ceballos, Jesús Adrián Mendoza Pérez, Edgar René Subías Rubalcaba, Jesús Arnulfo Ochoa Martínez and Juan Alfonso Puerta Holguín were sentenced alongside Acosta.
Digital Footprint Used To Trace Kidnappers
Acosta rented a house that was used to hold the victim captive while they established communications with authorities over the internet to demand a ransom of 2 million Mexican pesos (roughly $103,000).
At the time, authorities described Acosta as “very experienced” in using internet communications anonymously. Despite his technological savvy, authorities emphasized that they were able to track the Bitcoins that were sent to the kidnappers.
All Ransom Money Was Retrieved By Authorities
After receiving the ransom, Acosta used Twitter to reach out to the founders of Mexican cryptocurrency exchange Bitso, writing: “I’d like to speak to you. We are the heads of marketing for the biggest bitcoin casinos in the world.” Bitso did not respond to the message.
Forty-eight hours after establishing communication with Acosta, the Anti-Kidnap Unit of the Chihuahua Prosecutor’s Office rescued Denisse. The kidnappers were located by the state’s cybercrime department.
All ransom money was fully recovered by law enforcement during the kidnappers’ arrest. Three vehicles, a handgun and the mobile phones used to negotiate the ransom were also seized in the operation.
Acosta is a former YouTuber with an audience of tens of thousands who claimed to be the director of a marketing company. He also reportedly participated in the World Congress of Young Leaders for Peace in Mexico during June 2017.
Updated: 3-4-2020
Swedish Foreign Minister Urges Ukraine To Investigate $70 Million Bitcoin Fraud
The Swedish government is reacting to an alleged Bitcoin fraud scheme that targeted vulnerable people in Sweden, Australia, New Zealand and the U.K.
Ukrainian officials were informed of the allegations in a meeting on March 2, according to an Organized Crime and Corruption Reporting report published on March 3.
Foreign Policy Consequences Of The Fraud
Swedish Minister of Foreign Affairs Ann Linde championed an investigation published by national newspaper Dagens Nyheter (DN). The article alleges that the Ukraine-based Milton Group, ostensibly an IT support company, defrauded victims in developed countries by proposing fake Bitcoin (BTC) investment schemes.
The group reportedly scammed victims for over $70 million, with several examples of elderly people losing their life’s savings. Milton Group operates mainly out of Kyiv, Ukraine’s capital.
Linde shared the findings with unnamed Ukrainian officials, expressing her outrage at the findings. She said:
“It is really upsetting to see how they bluff Swedish retirees who have to leave their homes and live on a minimum subsistence level. And then they sit there, laughing.”
The minister urged the Ukrainian government to take decisive action in response to the media report, adding:
“The most important thing is that [the allegations] get attention. I don’t know if this information exists in Ukrainian, otherwise it is up to DN to make sure it does.”
Government officials also criticized the lack of oversight by Facebook, which allowed Milton Group’s ads to circulate.
Details Of The Alleged Fraud
The investigation was made possible by an unidentified whistleblower who reported on the inner workings of the operation. He claims to have been part of a “retention” team and was expected to make 300 calls each day. The victims were initially hooked via Facebook ads that targeted people interested in cryptocurrency.
The callers also frequently changed their presented identities to continue “squeezing the money” from clients. After selling a victim on a phony investment scheme, they would pose as lawyers and financial advisors promising to return the money that the victim invested — for a fee.
Some victims reportedly transferred over $1,000 every month to the group, while one elderly citizen was defrauded for as much as $200,000.
The whistleblower also revealed that the “sales” staff received different commissions based on payment method. Transfers via credit card and transmission services like Moneygram were valued at 4% and 6% respectively. Transfers in cryptocurrencies compensated the “salesman” with as much as 9%.
Updated: 3-5-2020
Co-Founders of Alleged $9 Million Crypto Ponzi Scheme Plead Not Guilty
Zachary Salter, the co-founder of Zima Digital Assets alongside 28-year-old John Caruso, has pleaded not guilty to charges of money laundering and conspiracy to commit wire fraud in his arraignment in Arizona on March 4.
The criminal indictment alleges that the pair ran a purported cryptocurrency investment scheme that was used to defraud their customers of more than $9 million in a classic Ponzi scheme.
Approximately $1.9 million in deposits were cycled back to early investors as supposed investment returns. The purported profits served to validate the scheme, contributing to a further wave of deposits.
The remaining $7 million was spent lavishly — on vacations, luxury car rentals, private jets, and casino gambling. Despite flaunting their lavish lifestyle on social media, the pair claimed no taxable income.
The pair defrauded more than 90 investors, including elderly citizens and former-professional baseball players. They were arrested on Jan. 30.
Both Co-Founders Plead Not Guilty
The indictment includes allegations of false statements in investor contracts and misrepresentations in direct messages to clients.
Caruso also pleaded not guilty during his arraignment on Feb. 26. Caruso has a criminal record and was last released from prison during 2017.
Both men will now face a jury trial on July 4, 2020. If convicted of either charge, Salter and Caruso will have to forfeit all property derived through the criminal scheme.
Scammers Lose $830,000 In Investor Funds At Casinos
Following a hearing in early February, the prosecution alleged that “there is no evidence any of the investment funds that have been provided to Caruso and Salter have gone to any cryptocurrency/digital asset investment, or to any investment of any kind, as fraudulently misrepresented by both Caruso and Salter.”
It was heard that the pair used investors’ funds to rack up $830,000 in gambling losses, $670,000 in credit card expenses, $540,000 in private jet and luxury vehicle rentals, and $150,000 in rent for a 20,000-square-foot mansion.
At the time of the February hearing, Zima Digital Assets was still actively receiving investor funds.
Updated: 3-5-2020
Crypto Investment Fund Suffers Hack Exposing Data of 266,000 Users: Report
In the latest privacy breach to hit the cryptocurrency space, Malta-based Trident Crypto Fund has suffered a major data leak, Russian newspaper Izvestia reports on Thursday.
Ashot Oganesyan, chief technology officer of cybersecurity firm DeviceLock, told the publication the personal data of about 266,000 people registered with the fund was posted on a number of file-sharing websites following the breach.
The stolen database, including email addresses, cellphone numbers, encrypted passwords and IP addresses, was posted online around Feb. 20, along with the description of the website vulnerability that made the breach possible, Oganesyan said. On March 3, the unknown hackers decrypted and published a dataset of 120,000 passwords, he added.
Izvestia reached out to one of the individuals on the database who confirmed a connection to Trident Crypto Fund, though he’d only registered for a seminar hosted by the firm and didn’t invest.
The fund does not list its team members on the website and has no presence in LinkedIn. It’s unclear where the fund is registered or physically located. According to Crypto Fund Research, the fund is based in Malta. It offers clients investment in a “top 10 crypto” index calculated by the fund itself.
Updated: 3-6-2020
Ledger Wallet Warns of Fake Google Chrome Extension Stealing Crypto
Major cryptocurrency hardware wallet supplier Ledger has warned its users about another phishing attack trying to steal their crypto — this one using a Google Chrome extension.
In a March 5 tweet, the French crypto company specified that there is a fake extension on Google Chrome browser that attempts to steal users’ crypto by asking them to enter their 24-word recovery phrase to access their wallet.
Ledger Live Gets Removed From The Chrome Web Store
The phishing attack was reported by Catalin Cimpanu, a cybersecurity reporter at business technology news website ZDNet on March 4. According to Cimpanu, the malicious Chrome extension was first discovered by Harry Denley, director of security at blockchain interface platform MyCrypto.
According to the report, the fake Chrome extension is called Ledger Live. It tries to mimic the real mobile and desktop application Ledger Live that allows Ledger wallet users to approve transactions by syncing their hardware wallet with a trusted device.
As of press time, the fake Ledger Live extension had apparently been removed from the Chrome Web Store. According to the report, the phishing extension was downloaded at least 120 times before it was taken down.
Fake Extension Was Advertised By Google Ads
As reported by ZDNet, the malicious extension was trying to mislead users into thinking that it represented the Chrome version of the original Ledger Live app, which would allow them to check balances and approve transactions via Chrome. Users were apparently offered to install the extension and connect their Ledger wallet to it by entering the wallet’s seed phrase — a backup phrase or word seed used to get access to their wallets.
MyCrypto exec Denley, who first uncovered the phishing attack, reportedly ridiculed the malicious extension by claiming that it makes no sense to install and use such an extension with a hardware wallet that is meant to protect funds by storing cryptocurrency offline.
However, Denley still admitted that he would not be surprised if the fake extension has tricked people, adding that it’s a “big problem in the cryptocurrency area, to teach people their private keys/mnemonics should stay offline.” The malicious extension could apparently have misled some users, taking into account the fact that it was advertised by Google’s online advertising platform Google Ads, as reported by Denley.
In the warning announcement, Ledger emphasized that the platform would never ask its users for their recovery phrase, urging that to never share the 24-word seed phrase or enter it into any device connected to the Internet. This is, however, not the first time that Ledger users encountered a fake Chrome extension. As reported by Cointelegraph in early January, another malicious Chrome extension stole about $16,000 in privacy-focused cryptocurrency Zcash (ZEC).
There have been no official announcements of the data breach on the fund’s website or in its Telegram group as of Thursday morning European time – when the news was first published.
Trident has not yet responded CoinDesk’s requests for comment via email, Telegram and Facebook.
Last week, decentralized derivatives exchange Digitex also suffered a leak of user data, though it said probably only email addresses had been lost in a theft attributed to an ex-employee.
Binance, the largest crypto exchange by trading volume, also saw verification details of possibly 60,000 users allegedly made public last summer. The firm said the know-your-customer data did not match its own, however, and suggested it was not the source of the breach.
Updated: 3-6-2020
Reginald Fowler Pleads Not Guilty To New Crypto Capital Charges
Reginald Fowler has pleaded not guilty to a new charge of wire fraud during a March 6 hearing at the United States District Court for the Southern District of New York.
On Feb. 20, the U.S. government filed a superseding indictment against Fowler, adding wire fraud to existing charges of bank fraud, illegal money transfer and conspiracy stemming from Crypto Capital alleged shadow banking practices.
James McGovern, Fowler’s attorney, criticized the fresh indictment, asserting that he has “no idea what [Fowler has] been charged with,” such as when and how the alleged wire fraud took place.
“I’ve never really seen a superseding indictment when it provides less information than the one before,” McGovern told the court.
Fowler was previously offered a plea deal, with reports claiming that he had “appeared ready to plead guilty” to a single count on Jan. 15. However, by Jan. 31, the U.S. government announced that Fowler had rejected the offer, which it subsequently withdrew.
Fowler To Face Trial In January
In light of the rejected offer, U.S. attorney Jessica Fender indicated that the government wished to go to trial during April.
Fowler’s representation pushed back against the prospect of an April trial, stating: “The case is just changed dramatically by the inclusion of this new count.” McGovern claimed that there are 30,000 documents-worth of discovery that he has not yet received that require review before going to trial.
Judge Andrew Carter Jr. ruled in favor of Fowler, pushing the trial back until Jan. 11, 2021. The trial is expected to last between four and five weeks.
Crypto Capital Provided Shadow Banking Services To Cryptocurrency Exchanges
The former NFL team owner is accused of acting as an unlicensed money transmitter and deceiving financial institutions as to the purpose of his accounts held with them. Through Crypto Capital, he allegedly provided shadow banking services to numerous cryptocurrency exchanges, including Bitfinex, Binance, Cex.io, Coinapult and QuadrigaCX.
Crypto Capital reportedly began providing bank services to Bitfinex when the exchange was kicked out of Taiwan in 2017. For two years, Bitfinex customers were allegedly instructed to deposit funds to accounts held in the name of various Crypto Capital subsidiaries at financial institutions all over the world.
In October 2019, Crypto Capital executive Ivan Lee was arrested in Poland, with reports tying him to $350 million in funds that were seized by authorities from a Crypto Capital subsidiary during April 2018. The seized funds allegedly included money that the firm was laundering for a Colombian narcotics cartel.
Crypto Capital remains a centerpiece to the ongoing investigation by the New York State Office into Bitfinex’s failure to disclose the loss of $880 million customer funds and a subsequent loan from sister-company Tether.
Bitfinex and Tether claim that the funds are not lost, rather have been seized alongside the accounts of various Crypto Capital subsidiaries.
Updated: 3-8-2020
Crex24 Exchange Accused of Hiding Hack From Customers
Users are accusing Estonian cryptocurrency exchange, Crex24, of hiding the scale of a hack from its users after suspending trade for several altcoin pairings.
Crex24’s members claim that the exchange has not given an explanation for its suspension of more than sixty altcoins. The exchange has also frozen withdrawal and deposit services for many of the platform’s coins.
Despite the apparent disruption to services and calls for answers on Twitter, the exchange’s social media posts suggest that it has been more interested in trying to drum up support for new listings than addressing the concerns of its users.
Accusation Mount Over Suspicious Htmlcoin Activity
A report published by Brazilian crypto press Livecoin on March 6 cites an anonymous Crex24 user who claims to have identified suspicious movements of the alternative cryptocurrency Htmlcoin, and may suggest foul play on the part of the exchange.
The user claims that the exchange froze his funds in mid-February, leading to a loss of approximately $32,000 of cryptocurrency.
Crex would later announce that 200 million Htmlcoins, worth $11,200, were stolen from its wallets and that it would be working with the Htmlcoin team to reimburse investors.
1.3 Billion Htmlcoin Transferred From Crex24 To Hitbtc
However, the anonymous source claims to have identified 1.3 billion Htmlcoins being withdrawn from Crex’s wallet, worth $72,800, on Feb. 12. The funds were sent to cryptocurrency exchange Hitbtc.
Htmlcoin, which reportedly has a large Brazilian user base, was added to the exchange during January of this year. Less than two months later, its pairings are now offline.
Crex24 has also reportedly increased its know-your-customer verification requirements for processing withdrawals since accusations began to swirl — further inhibiting their customers’ ability to remove funds from the platform.
According to Coin360, Crex24 hosted roughly $2.62 million in trade over the past 24 hours — ranking it 137th by daily volume at the time of writing.
At press time, Crex24 had not responded to Cointelegraph’s attempts to obtain a statement regarding the accusations.
Updated: 3-9-2020
Belgian Gov’t Will Sell $125K of Seized Bitcoin In Irish Public Auction
Major United Kingdom and Ireland-based auction house Wilsons Auctions is putting $125,000 worth of Bitcoin (BTC) under the hammer later this month.
In an announcement on March 6, Wilsons revealed the auction will be hosted by Wilsons Auctions Dublin on March 24.
The Bitcoin is being sold on behalf of the Belgian Federal government, which seized the cryptocurrency in criminal cases and is now cooperating with Wilsons’ Asset Recovery Department to dispose of the Bitcoin.
The auction will be unreserved, i.e. without a minimum price set for the winning bid.
First Public Online Auction In Ireland
While Wilsons has previously sold off cryptocurrency in other auction formats, this month’s sale represents the first public online auction of crypto in Ireland.
Mark Woods, an asset recovery executive at Wilsons, said of the auction:
“The format has proven popular with our customers, who are able to bid online and purchase cryptocurrency from an established and trusted auction house instead of utilizing online exchanges, which can be a risky and daunting process.”
He added that Wilsons offers guidance to cryptocurrency novices, with the aim of enabling all investors to “participate on a level playing field.”
Woods struck a positive tone about the auction house’s recent collaborations with international experts, law enforcement and government agencies in the cryptocurrency field, noting that the strategy allows the auction house to remain “at the forefront” of developments.
1-2-3 Sold!
Wilsons has revealed that bidders from over 90 countries world-wide participated in its auction involving crypto-assets seized by the Belgian government earlier this year.
The auction house also held a Monero (XMR) auction in January, selling off XMR seized by United Kingdom law enforcement, as well as multi-crypto asset auctions in fall of last year.
As reported, auctions have become a common means for governments and law enforcement agencies to dispose of seized crypto, as with the United States’ use of the format for assets from the Silk Road darknet marketplace.
Updated: 3-11-2020
New PlusToken Report Shows KYC May Be Smoke And Mirrors
A new report on the PlusToken Ponzi scheme shows regulated exchanges are being used to dump coins, despite stringent Know Your Customer (KYC) identify verification rules.
Investigative company OXT Research has released a second edition of their in-depth blockchain analysis on the PlusToken scam.
The report explained PlusToken funds generally moved from unmixed allotments and locations, to mixers. After mixers, the funds saw consolidation, and then finally distribution. OXT’s report said:
“Approximately 80% of coins entering mixing have been distributed while up to 33,872 BTC remain in the mixer and 3,853 BTC are in the distribution process, resulting in a total of 37,725 BTC that have entered mixing, but not yet been distributed.”
Around $1.3 billion worth has been sold off in the past seven months with the report noting that distribution increases into market strength and “pauses” with market weakness.
OXT found that nearly 70% of the total hoard has been distributed to date meaning that “most of PlusToken’s market effects have largely passed.”
A large amount of coins ended up on OKEx. “OKEx is a newly labeled and significant coin destination having received nearly 50% of February distributions,” the report stated, adding that Huobi also remains one of the most significant coin destinations.
The PlusToken Coins Were Offloaded On Regulated Exchanges
ErgoBTC, an analyst closely following developments, pointed to an important aspect of the report — the usage of regulated exchanges for offloading BTC profits, as opposed to over-the-counter (OTC) selling. ErgoBTC tweeted:
“Regulated KYC’d exchanges have been the main destination of these coins throughout the post-shutdown period. Despite the ‘right narratives’ constructed by vested business interests, ‘OTC’ has not been the preferred destination of these coins.”
Governing bodies across the globe have pushed KYC and Anti-Money Laundering (AML) requirements for years, expressing the laws as a method of fraud prevention.
OKEx requires KYC to withdraw funds from the platform and so does Huobi.
PlusToken Has Been At It For Almost A Year
For many months crypto markets have experienced the effects of the unravelling of one of the largest alleged scams in the industry’s history. The operation reportedly began in 2018, ammassing 10 million participants by 2019.
Authorities apprehended several of the scheme’s operators in June 2019, although it is uncertain how many involved parties still remain at large. Some headlines note a potential correlation between Bitcoin’s 2019 downtrend — which started around the same time as the PlusToken arrests — and apparent PlusToken dumping.
PlusToken Moved More BTC On March 6
Data from several days ago shows a significant amount of funds were moved from wallets thought to be associated with PlusToken.
ErgoBTC noted that roughly 13,000 Bitcoin were transferred to a coin mixer, according to a March 6 tweet.
Less than 24 hours later, Bitcoin’s price fell from $9,200 down to $8,850. Bitcoin’s price continued further descent, down to a press time price of $7,930.
However other experts see more of a correlation to declining mainstream markets, explaining that investors are flocking to more stable assets.
Updated: 3-11-2020
Two Japanese Men Arrested For ‘Fencing’ NEM From Coincheck Hack
Tokyo police arrested two men in connection to the Coincheck hack on March 11. The men are accused of purchasing stolen NEM (XEM) through a dark web market, in violation of a law designed to tackle organized crime.
As reported by Japan Times on March 11, Tokyo’s Metropolitan Police Department arrested a doctor from Hokkaido and a company executive from the Osaka Prefecture.
According to the police, the suspects knew the origin of the funds. They reportedly purchased the XEM at a sizeable discount in February and March 2018 from a dark web website.
The suspects were allegedly apprehended through inquiries to a cryptocurrency exchange that some of the NEM was sent to. How the police were able to pinpoint the destination of the funds is unspecified. Blockchain tracking tools were most likely employed as well.
Chasing The NEM Trail
The Coincheck hack is one of the largest in the history of cryptocurrency exchange thefts. Hackers stole over $534 million worth of XEM in January 2018, with the trail allegedly leading to Russia-based attackers. Tokyo police allocated approximately 100 investigators to the case. Authorities are continuing investigations on other alleged buyers of the stolen NEM.
The stolen tokens were reportedly exchanged for Bitcoin (BTC) or Litecoin (LTC) and dispersed over 13,000 wallets. It is unclear if the hackers were able to fully cash out their proceeds, as many exchanges have increased their security and monitoring efforts since then.
Investigators appear to have shifted their focus now as they target those who purchased the tokens. The practice of buying stolen goods to resell them at a profit is called fencing and is considered a crime in most jurisdictions.
Advocates of privacy coins often believe that “transparent” coins such as Bitcoin or NEM lack fungibility, which could result in users unwittingly becoming “fencers” of stolen coins.
Coincheck History
After a tumultuous 2018 where it saw revenue drop by 66% over a single quarter, the exchange eventually rebounded under its new owner Monex Group, who purchased Coincheck in April 2018. In early 2019 it was one of several Japanese exchanges to be granted a license from Japan’s Financial Services Agency.
In May 2018 the exchange dropped all coins with privacy features from its offering, while in November of the same year it resumed NEM trading.
Updated: 3-11-2020
LocalBitcoins Seller Charged After Undercover ‘Human Trafficking’ Sting
A Washington state resident has been charged with money laundering after selling Bitcoin for $140,000 in cash to undercover agents.
Bothell’s Kenneth Warren Rhule, 26, met with agents from Homeland Security Investigations on numerous occasions between April to December 2018, often in Seattle-area Starbucks cafes.
According to the unsealed complaint Rhule — who traded on localbitcoins.com under the name Gimacut9 — allegedly closed at least seven deals with agents “posing as criminals” who wanted to buy untraceable Bitcoin with the proceeds of their operations.
They told Rhule they were bringing Ukranian women to the U.S. for the purposes of prostitution.
Special Agent Victor Morales From The Drug Enforcement Agency Said In The Complaint:
“Rhule conducted these transactions even after the undercover agent explained that at least a portion of the cash involved represented proceeds of human trafficking.”
Rhule made an appearance before the US District Court of Seattle on Tuesday. He was charged with conducting an unlicensed money transmitting business and five counts of laundering monetary instruments. The complaint noted that he failed to conduct any Know Your Customer ID verification checks.
The money laundering charges are punishable by up to 20 years in prison, while the marijuana charges are punishable with a minimum of five years in prison, and a maximum of 40 years.
Rhule Allegedly Boasts Of Drug Operations
On one occasion while waiting for confirmations the Bitcoin had been successfully deposited, Rhule allegedly boasted about doing “5,10 or 20,000 kilo” CBD (Cannabidiol) orders. The investigation found he was running an unlicensed marijuana products business manufacturing items including hash oil.
He documented his sophisticated growing operations with photographs uploaded to his Google, iCloud and Instagram accounts — including pictures of Rhule posing with crops of marijuana.
He was also charged with conspiracy to manufacture and distribute marijuana.
Bitcoin Dealer Extols The Virtues Of Monero
Rhule also advised the undercover agents that Bitcoin was only pseudo-anonymous and extolled the virtues of Monero which he said was a “100% anonymous cryptocurrency”:
“Rhule explained to UCA-1 that Monero operated under the same concept as any cryptocurrency and was verifiable on the blockchain with one important caveat: wallet addresses could not be tracked.”
The ‘Gimacut9’ LocalBitcoins account last made a deal on July 1 2019 and was banned from November 2019 onwards. LocalBitcoins no longer offers a cash for crypto trading option.
Updated: 3-12-2020
Alleged Deer.io Black Market Kingpin Arrested by FBI
Kirill Victorovich Firsov, the alleged owner of Russian-based anonymous marketplace Deer.io, was arrested on March 7 by Federal Bureau of Investigation (FBI) officials at John F. Kennedy Airport in New York.
Court documents allege that Firsov is the mastermind behind Deer.io — a site that offered darknet-style services in exchange for Bitcoin on the normal web. The FBI estimates it has facilitated more than $17 million worth of sales.
Firsov will be arraigned in New York court later this week, where he is expected to face charges for trafficking stolen information, and aiding and abetting trafficking.
Deer.io Hosted $17 Million In Black Market Sales Since 2013
Since 2013, Deer.io has hosted 24,000 active stores specializing in stolen information, offering a simple ‘turn-key’ solution for black-market entrepreneurs.
Vendors would pay roughly 800 Russian rubles ($12.50) to operate on Deer.io each month, with hosting offered on private Russian servers out of the reach of U.S. authorities. Fees were paid to Firsov in Bitcoin (BTC) or via the Russian payments platform WebMoney.
Of the 250 Deer.io shops reviewed by the FBI so far, not a single business dealt in legitimate wares. Items for sale on the platform included user passwords, fake social media accounts and sensitive identity data such as birth certificates and tax returns.
Troves Of Personal Data Sold Openly On Deer
During its investigations, the FBI made several purchases using the Deer platform including 999 documents containing Personally-Identifying Information (PII) from one vendor for $170 in Bitcoin, and $522 in Bitcoin for a stash of 2,650 documents from another.
For $20 worth of crypto, the FBI was able to pick up the usernames and passwords for 1,100 compromised gaming accounts.
Deer.io rose to prominence as an underground marketplace specializing in stolen goods during 2016 after infamous hacker Tessa88 used the platform to sell sensitive data hacked from social media networks LinkedIn and MySpace.
Updated: 3-12-2020
US Charges Dutch National With Running Crypto-Funded Child Porn Site
U.S. prosecutors indicated a Dutch national Thursday for allegedly spearheading a rape and child pornography website that’s made over $1.6 million worth of bitcoin selling videos since 2012.
Known as “Michael R.M.,” and “Mr. Dark,” the man allegedly ran a site called “DarkScandals” that operated on the darknet, which requires special software to access, and on the public clearnet. He allegedly sold over 2,000 videos and had ties to 303 virtual currency accounts, according to a press release from the U.S. Attorney’s Office for the District of Columbia.
Bitcoin (BTC) and ether (ETH) funded the bulk of the operation, according to the complaint against the man filed in the U.S. District Court for the District of Columbia.
Customers allegedly sent the cryptocurrencies as payment for videos or could upload their own. Their video submissions had to follow “specific rules,” though. As detailed extensively in the complaint, the videos had to be explicitly “obscene.”
“The types of crimes described in this indictment are the most disgusting I’ve encountered in 30 years of law enforcement,” said Don Fort, chief of the Internal Revenue Service’s Criminal Investigation team (IRS-CI), in a press release. “It is a special kind of evil to prey on and profit from the pain of others.”
Federal agents discovered DarkScandals while investigating the Welcome to Video case last year. That operation led to hundreds of arrests, the seizure of hundreds of thousands of videos and the dismantling of what was deemed the “largest darknet child pornography website” by investigators at the time.
It also led investigators straight to DarkScandals, the complaint said. “A subsequent review of a Washington, D.C.-based ‘Welcome to Video’ customer’s virtual currency records lead to the discovery of the DarkScandals sites.”
The case serves as another reminder that cryptocurrencies are a double-edged sword for criminals. On the one hand, transactions cannot be blocked by a regulated third party like a bank or payment processor; on the other hand, they leave a trail of crumbs for investigators that is difficult to obscure.
Agents with IRS and Homeland Security Investigations traced 303 digital currency transactions in the course of this latest investigation. The IRS used Chainalysis’ transaction tracing software in that investigation; a spokesperson for Chainalysis did not immediately respond to requests for comment.
“If you thought you were anonymous, think again,” Fort said.
U.S. investigators worked in partnership with the Dutch National Police, Europol and the German Federal Criminal Police in parallel investigations, according to DOJ.
Prosecutors are seeking to charge the man on nine counts and seize the operation’s digital currency holdings. It was not immediately clear if he is in custody. A spokesperson for the U.S Attorney’s office did not immediately respond to a request for comment.
Updatd: 2-18-2020
Two Canadians Sentenced To Prison Time In US For Bitcoin Theft
Two Canadian nationals have been sentenced to two years in a United States federal prison for stealing 23.2 Bitcoin (BTC) through a scam on Twitter in 2017.
According to the U.S. Department of Justice, on March 17, 23-year-old Karanjit Khatar and 24-year-olds Jagroop Khatkar were formally sentenced to 24 months in prison and three years supervised release for money laundering and conspiracy to commit wire fraud.
Scammers Impersonate HitBTC Support Staff On Twitter
Beginning in October 2017, the British Columbia-residents were found to have impersonated customer service representatives from the Hong Kong-based cryptocurrency exchange HitBTC.
Acting under the handle “@HitBTCAssist,” the pair responded to a request posted to the real HitBTC’s Twitter account concerning cryptocurrency withdrawal processes.
The Khatkars were able to convince the Oregon resident to forward sensitive information relating to their email, HitBTC, and Kraken accounts — which the scammers used to transfer 23.2 Bitcoins to Karanjit’s wallet.
Worth $119,000 today, the stolen Bitcoin had a value of roughly $130,000 at the time of the theft.
Stolen Proceeds Spent On A Lavish Lifestyle
The scammers divided the stolen proceeds equally, quickly selling the Bitcoins to fund an exorbitant lifestyle including casino gambling and luxury vehicles.
Within two days of the theft, Karanjit Khatkar purchased a Mercedes-Benz for nearly $40,000. He also gambled with tens of thousands of dollars while visiting high-end casinos in Las Vegas.
Karanjit was arrested at the McCarran International Airport in Las Vegas on July 18, 2019, while Jagroop later appeared at his arraignment voluntarily.
The pair pleaded guilty on Dec. 16, 2019, and were ordered to pay total restitution of $184,511.
Crypto Scams Capitalize On Coronavirus Panic
A number of government regulators have warned of a recent uptick of scams seeking to capitalize on the widespread fears relating to COVID-19.
On March 11, the United Kingdom Financial Conduct Authority warned that coronavirus scams may “take many forms and could be about insurance policies, pensions transfers or high-return investment opportunities, including investments in cryptoassets.”
Earlier this month, cybersecurity threat researcher DomainTools identified the coronavirus-themed ransomware “CovidLock.” DomainTools found that the website coronavirusapp.site installs ransomware on a users’ device under the guise of providing a thermal map showing the spread of the coronavirus nearby.
Once granted permission to access a device’s screen settings, the ransomware changes the lock screen password and demands $100 in Bitcoin in exchange for restored access to the phone.
Updated: 3-20-2020
Woman Arrested For Stealing $480,000 From Crypto Exchange She Co-Founded
A woman was arrested in Bengaluru, India on March 17 for allegedly stealing 63.5 Bitcoins (BTC) from Bitcipher Labs — a cryptocurrency exchange that she had previously co-founded.
The thefts took place on January 11 and March 11 respectively, resulting in $480,000 worth of BTC being stolen from Bitcipher.
Bitcipher Co-Founder Steals $480,000 In BTC
Ayushi Jain, the 26-year-old former-employee, was found to have stolen 63.5 BTC from hardware wallets owned by the exchange.
Indian police acted in response to a complaint filed by Bitcipher Labs’ CEO, Ashish Singhal, who had identified the two unauthorized transactions.
The Bengaluru Investigation Department stated that an “investigation revealed the complainant had hardware wallets in which Bitcoins were stored, and a 24-word passphrase (password) was written on a piece of paper.”
Police suspected that the thief was “someone proficient in using this technology, and who was closely associated with the firm”, due to the fact that the culprit was able to operate a cryptocurrency hardware wallet and access the funds using the wallet’s corresponding passphrase.
Stolen Funds Were Recovered
After preparing a list of the exchange’s former employees, Ayushi was identified as a likely suspect, as she had quit the company on Dec. 16, 2019, despite having co-founded the firm alongside Singhal in 2017.
After being detained, Ayushi confessed to the theft. The stolen funds were recovered by police. A senior police officer stated:
“On Wednesday, we took Ayushi into custody and searched her house. We seized a laptop which contained the history, showing how Ayushi used the passphrase and stole money in installments between January and March. She confessed to the crime. By Thursday afternoon, we recovered the entire amount.”
Police seized Ayushi’s laptop, and all stolen funds have been returned to the exchange.
Crypto Exchanges Rush To Enter Indian Market
India has become a renewed focus of the cryptocurrency community. Recently, the Supreme Court reversed the Reserve Bank of India’s ban on financial institutions, and are now providing services to businesses operating with cryptocurrencies.
Despite several cryptocurrencies rushing to enter the Indian market, a recent parliamentary investigation has revealed that only two cryptocurrency exchanges are licensed with the country’s Ministry of Corporate Affairs.
Updated: 3-23-2020
SEC Charges Former State Senator Over Digital Asset ‘Scam’
The Securities and Exchange Commission (SEC) has pressed charges against a former state senator for his role in a $4.3 million token sale that promised outlandishly high returns.
The SEC confirmed Friday it had filed a complaint against David Schmidt, a former Republican state senator for Washington State, as well as two other people for their role promoting the sale of “Meta 1 Coins.”
Filed in the Western District of Texas on March 16, the complaint accuses Robert Dunlap and Nicole Bowdler, as well as Schmidt, of violating antifraud and securities regulations when promising investors returns of nearly 225,000 percent. They also claimed the coin was risk-free and would never lose value.
The SEC said defendants made “numerous false and misleading statements,” including that Meta 1 Coin was backed by an art collection valued at $1 billion, or a gold deposit valued at $2 billion, that was regularly audited by an accounting firm.
“The defendants made audacious claims about the Meta 1 Coin and would say almost anything to separate investors from their money,” said David Peavler, the SEC’s regional director at the Fort Worth Regional Office. “Investors should always look skeptically at promoters who claim that their investment cannot lose value or that investors will receive massive returns.”
In total, Meta 1 Coin raised $4.3 million from around 150 investors, some based in the U.S. The digital assets were never distributed to investors, however. Some of the proceeds were funneled to a Chicago-based fund, Pramana Capital, as well as to another individual, Peter Shamoun. The SEC claims defendants used investors’ money to fund lavish lifestyles, including the purchase of a $215,000 Ferrari.
Launched in 2018, Meta 1 Coin’s website doesn’t include a description of what the purpose of the coin is. Its Twitter page is filled with pictures and short clips of physical Meta 1 Coins, talking about the disruptive potential of blockchain technology.
Its Terms Of Use Also Include Some Pretty Weird Statements, Including:
“The only participants of META 1 Coin Trust and the named websites are for Live Natural Man and Women, flesh-and-blood Almighty God-created private Humans sui juris sentient being; and an Ambassador of God Almighty Domiciled in the ARIZONA Republic and on religious sojourn through the UNITED STATES.”
Schmidt, a moderate Republican, was initially elected as a representative for Washington State back in 1994. After serving four terms, he became a state senator in 2002, before losing his re-election bid in 2006. Now based in Arizona, he works as a consultant, writer and radio program host, according to his LinkedIn page.
In 2012, Washington’s electoral watchdog, the Public Disclosure Commission (PDC), fined Schmidt $10,000 for improperly using more than $41,000 in donations to reimburse himself for lost wages between 2003-2006, as well as mortgage repayments and personal travel costs.
Schmidt denied misusing campaign dollars, claiming in 2011 that campaign funding rules were “very open to interpretation.”
Schmidt could not be reached for comment on the SEC complaint.
The SEC is seeking civil penalties and permanent injunctions against Schmidt and the other two defendants, as well as for investors to be refunded. The regulator also wants Pramana Capital and Shamoun to hand over any funds received from the Meta 1 Coin Trust sale.
CoinDesk reached out to both Meta 1 Coin Trust and Pramana Capital for comment, but had not received a response by press time.
Updated: 3-24-2020
YouTube Scam Impersonates Ripple CEO Garlinghouse For Fake XRP Airdrop
Despite YouTube’s many aggressive actions against cryptocurrency-related content, the world’s most popular video-hosting website is apparently having trouble discovering a major scam account involving crypto.
On March 23, the crypto community spotted a bogus YouTube account impersonating Brad Garlinghouse, CEO of major blockchain company Ripple, in order to promote a fake airdrop scam.
Video Containing Fake XRP Airdrop Description Was Uploaded On Youtube On March 19
The apparent scam account has around 277,000 subscribers and contains only one video, which promotes a fake giveaway in the third-biggest cryptocurrency, XRP. Uploaded on YouTube on March 19, the video description promotes a nonexistent airdrop of 50 million XRP tokens and has amassed over 85,000 views as of press time.
While the video itself is not fake and is a real interview that Garlinghouse gave in February 2020, the scam lies in the video description. The Ripple exec hasn’t yet reacted to the scam alert on Twitter so far despite reports mentioning him.
Specifically, the video description presents users with a bogus airdrop contest taking place from March 20 till March 25, according to the video description. The YouTube scammer asks users to send between 2,000 XRP to 500,000 XRP in order to “participate” in exchange for immediate airdrop of 20,000 to 5 million XRP. For example, the fraudster promises to send 2.5 million XRP back in exchange for sending 250,000 XRP ($40,000) to his/her crypto address. As of press time, the address has 5,135 XRP ($800).
Scammers Purchasing Youtube Channels With Large Numbers Of Subscribers Could Be A Reason
A co-founder of crypto podcast SPQR Media, who first reported on the YouTube scam on his Twitter account on March 23, emphasized in a recent tweet that the scam channel is still up and running and is receiving funding for promotion on YouTube. Twitter user @Andy_SPQR told Cointelegraph that he noticed the scam page last night as an ad popped up on his YouTube feed.
The SPQR co-founder highlighted that he immediately tweeted to report on the apparent scam as the YouTube account had a “huge number of subs but only one video,” while the description promised a free XRP airdrop scam. According to the executive, the reason for the scam is that YouTube allows users to purchase channels from each other. He said:
“In my opinion I think what’s happening is these scammers are purchasing YouTube channels with large numbers of subscribers and then deleting all content and uploading that video. I think that’s how they are able to maintain a presence on YouTube.”
YouTube Started An Apparent Crypto War In Late 2019
The news comes on the heels of YouTube continuing its apparent war against crypto content makers on the platform.
As Cointelegraph reported on March 10, YouTube deleted another batch of crypto-related videos from two separate crypto channels. In late 2019, YouTube was also aggressively deleting crypto content from some of the biggest players in the industry. As reported by Cointelegraph, YouTube subsequently admitted that some of its deletions were a mistake, while a lot of crypto YouTubers expressed intention to move to blockchain-based video hosting platforms to share their content.
Updated: 3-25-2020
Fake Ledger Live Chrome Extension Stole 1.4M XRP, Researchers Claim
A fraudulent Google Chrome extension has allegedly stolen as much 1.4 million XRP from users this month alone.
In a series of tweets published on March 24, the research team “xrplorer forensics” claimed that fake Ledger Live extensions are being used to collect user backup passphrases:
“They are advertised in Google searches and use Google Docs for collecting data. Accounts are being emptied and we have seen more than 200K XRP being stolen the past month alone.”
Revising this initial figure, xrplorer forensics later amended its estimate to “close to 1.4M.”
The Fraudulent Extension Is Still Available On Google Store
According to the researchers, most of the stolen XRP appears to still be held in accounts, with a proportion cashed out via the crypto exchange HitBTC.
Sharing a screenshot of a post request from the alleged scam, xrplorer forensics warned the community against downloading tools for their hardware wallets from any developer other than the vendor directly — in this case, French crypto hardware wallet manufacturer, Ledger.
As of press time, two “Ledger Live” extensions appear on the Google store for the Chrome browser, both of which include multiple user reviews that appear to corroborate xrplorer forensics’ warnings against the scam.
Exchanges Should Be On The Alert
In a series of parallel tweets between March 20 and March 25, xrplorer forensics claimed that close to 300 million XRP currently residing in XRP accounts is flagged as fraudulent.
The vast majority of it, they claim, comes from the PlusToken exit scam. 13 million XRP is, in their estimation, derived from other thefts and scams.
In a tweet today addressed to crypto exchange bithunter.io, the researchers asked why AML (anti-money-laundering) alerts were not observed for a series of large and allegedly suspicious transactions. They contend that one-third of all XRP bithunter has received is from suspect accounts on their advisory list.
As of March 20, the researchers said they had been noticing a “consolidation of funds from various scams happening right now,” appealing to exchanges to stay alert to the nature of incoming payments.
Repeat Warnings
At the start of this month, Ledger had itself cautioned its users against the fake Ledger Live extension — first discovered by Harry Denley, director of security at blockchain interface platform MyCrypto. Denley, like xrplorer forensics, had identified that the fake extension was being propagated by a GoogleAds campaign.
Updated: 3-29-2020
Network of Fake Bitcoin QR Code Generators Stole $45,000 In March
A network of malicious QR code generators has stolen more than $40,000 from Bitcoin (BTC) users in one month.
At least nine fake Bitcoin-to-QR code generators have been spotted in recent weeks, with security researcher, Harry Denley, first tweeting that he had identified two domains hosting fake QR code applications on March 22.
Denley later identified seven other domains sharing the same interface — suggesting that they are all created by the same developer.
Fake Bitcoin QR Code Generators Steal Over 7 BTC
The malicious programs promise to convert a user’s Bitcoin address into a QR code, claiming to eliminate the risk of the user losing their funds as a result of typos when entering or sharing their address — a service offered by every popular block explorer and most mobile wallet applications.
However, the QR code generated by the programs is always the same address — diverting the victims’ funds to the malicious program’s developers. The supposed QR generators correspond to five different wallets, which have absorbed more than seven BTC, likely from the apps’ victims.
The malicious websites are bitcoin-barcode-generator.com, bitcoinaddresstoqrcode.com, bitcoins-qr-code.com, btc-to-qr.com, create-bitcoin-qr-code.com, free-bitcoin-qr-codes.com, freebitcoinqrcodes.com, qr-code-bitcoin.com, and qrcodebtc.com.
‘Bitcoin Transaction Accelerators’ Accumulate 17.6 BTC
The websites are hosted by three different servers that collectively host roughly 450 other websites that appear sketchy — with the sites featuring keywords related to coronavirus, Gmail, and various cryptocurrencies.
Among the sites are several purported “Bitcoin transaction accelerators,” which claim to speed up BTC transfers in exchange for a 0.001 BTC. The BTC addresses associated with the supposed ‘accelerators’ have absorbed more than 17.6 BTC — taking in nearly $110,000.
Crypto Scams Capitalize On Coronavirus Fears
Opportunistic scammers have sought to capitalize on the COVID-19 pandemic — with UK county regulators, the Texas State Securities Board, and the US Commodity Futures Trade Commission issuing warnings about the proliferation of coronavirus crypto scams over the past week.
Recent scams have also impersonated the World Health Organization in an attempt to siphon donations, and taken the form of apps purporting to track the spread of coronavirus.
Updated: 4-4-2020
CFTC Requests Default After Failing To Find $147M Bitcoin Ponzi Operator
The United States Commodity Futures Trading Commission (CFTC) has requested that the alleged founder of the crypto $147 million Ponzi scheme Control-Finance be declared a default.
On April 3, the CFTC filed for a ruling of default after Control-Finance’s alleged founder and director, Benjamin Reynolds, did not respond to the regulator’s complaint.
CFTC Unable To Locate Reynolds After 10 Months
The CFTC’s complaint was filed during June 2019 — alleging that Reynolds misappropriated at least 22,858 BTC from more than 1,000 customers from May 1, 2017.
In January 2020, the SEC requested additional time to locate Reynolds amid an ongoing investigation in South Korea.
During July 2019 the regulator had attempted to serve Reynolds at two addresses associated with the scheme’s director, later learning from Control-Finance investors that the accused may be situated in Korea.
The CFTC simultaneously filed a notice of voluntary dismissal without prejudice against Control-Finance.
Ponzi Scheme Does Away With $147 Million
The CFTC’s complaint alleges that Control-Finance claimed to divert customer funds to the trading operations of its expert employees while diverting new depositors’ funds to the scheme’s previous investors to create the illusion of profits and build hype.
The firm constructed a pyramid scheme around a purported affiliate program, which was promoted on Twitter, Facebook, and YouTube. In September 2017, Control-Finance removed its website, ceased making affiliate payouts, and deleted advertising content from social media.
While claiming that customer funds would be returned during the following two months, the pair were the scheme was liquidating the 22,858 BTC in its possession for roughly $147 million.
Control-Finance sought to launder the funds through thousands of transactions, with the BTC ultimately arriving at wallets held with Canadian crypto exchange CoinPayments.
Updated: 4-6-2020
Q3 Crypto Ponzi Victims File Class Action Lawsuit Against Wells Fargo
Q3 Investment Recovery Vehicle (Q3IRV), an entity representing the more than 100 victims of the alleged $35 million Q3 Ponzi scheme, has filed a class-action lawsuit against Wells Fargo Advisors.
The suit accuses Wells Fargo of failing to inquire into the activities of an employee accused of co-masterminding the scam.
The plaintiffs assert that the Wells Fargo subsidiary failed to make appropriate inquiries into its financial advisor James Seijas — as per the firm’s policy mandating employees to regularly report activities relating to outside interests.
Crypto Ponzi Victims Sue Wells Fargo For Vicarious Liability
Q3IRV is seeking damages and interest for vicarious liability for the actions and omissions of Seijas.
The plaintiffs assert that Wells Fargo did not inquire into Siejas’ role at Q3 while he operated the scheme, despite the firm’s policies for employees:
“Wells Fargo Advisors’s policies and procedure required employees to regularly report to Wells Fargo Advisors concerning work they did outside the scope of their employment…”
The lawsuit emphasizes that as Seijas touted himself as an investor working on behalf of Wells Fargo while he was an employee of the firm, “the acts and omissions described herein were committed in his capacity as an agent for Wells Fargo Advisors.”
The lawsuit also names Wells Fargo Advisors in counts of unjust enrichment, negligence and fraud.
Seijas Worked At Wells Fargo Advisors For Five Years
The lawsuit alleges that Siejas, alongside fellow co-founders Quan Tran — a certified general surgeon, and Michael Ackerman — a former UBS securities employee, formed the Q3 Trading Club in 2017.
Q3 purported to pool investors funds to trade crypto assets using a proprietary algorithm, promoting the scheme to physicians on social media, including a Facebook group called “Physicians Dads’ Group.”
The suit alleged that, after raising upwards of $1 million, Q3 became a limited partnership and expanded to take in $33 million from 150 investors across the United States.
Q3IRV claims that only $10 million the funds raised were invested in virtual currencies, with over $10 million being diverted to the trio:
“Despite Defendants’ representation to potential and existing Q3 Investors that their virtual currency trading was highly successful and that Q3 Investors were free to withdraw the profits earned in their accounts after one year, Defendants did not trade virtual currencies successfully and most of Q3 Investors’ money was misappropriated or lost in trading.”
Q3’s operators also diverted $4 million in purported licensing fees for access to their proprietary algorithm into their personal bank accounts, according to the plaintiffs.
Updated: 12-10-2019
Camarillo Man And Two Others Arrested In Alleged $722-Million Cryptocurrency Fraud Scheme
Three men, including one from Camarillo, have been arrested in connection with an alleged cryptocurrency mining scheme that authorities say defrauded investors out of hundreds of millions of dollars from April 2014 through December 2019. The Department of Justice announced charges Tuesday.
Matthew Brent Goettsche, 37, of Lafayette, Colo.; Jobadiah Sinclair Weeks, 38, of Arvada, Colo.; and Joseph Frank Abel, 49, of Camarillo, were indicted on charges of conspiracy to offer and sell unregistered securities. Goettsche and Weeks were also charged with conspiracy to commit wire fraud.
U.S. Atty. Craig Carpenito described the alleged fraud as a “modern, high-tech Ponzi scheme” that amounted to $722 million. Two other suspects remain at large.
“Those arrested today are accused of deploying elaborate tactics to lure thousands of victims with promises of large returns on their investments in a bitcoin mining pool, an advanced method of profiting on cryptocurrency,” said Paul Delacourt, the assistant director in charge of the FBI’s Los Angeles Field Office. “The defendants allegedly made hundreds of millions of dollars by continuing to recruit new investors over several years while spending victims’ money lavishly.”
The defendants operated BitClub Network, providing false and misleading figures that investors were told were “bitcoin mining earnings” in exchange for money, Carpenito said.
According to court documents, officials said that Goettsche referred to investors as “dumb” and said he was “building this whole model on the backs of idiots.” On at least three occasions, the illegality of the alleged scheme was referenced to Goettsche. Additionally, he, Weeks, Abel, and others conspired to sell BitClub Network shares when they were unregistered securities, authorities said.
The maximum penalty for wire fraud conspiracy is 20 years in prison and a fine of up to $250,000. Conspiracy to sell unregistered securities carrie a maximum penalty of five years in prison and a fine up to $250,000.
Updated: 4-8-2020
High Court Delivers Judgement On User Assets At Hacked Exchange Cryptopia
Hacked cryptocurrency exchange Cryptopia today informed its users that the High Court of New Zealand has delivered its judgment on the status of their compromised assets.
In a tweet thread published on April 8, the exchange shared the 74-page court document detailing the judgment, summarizing:
“Today, 8 April 2020, Justice Gendall delivered his judgment finding firstly, cryptocurrencies are “property” […] and secondly, that account holders’ cryptocurrency were held on multiple trusts, separated by individual crypto-asset type. This means that the cryptocurrencies are beneficially owned by the account holders and are not assets of the company.”
Some Creditors To Get Less Than 50% Of Claims
As previously reported, the now-defunct Cryptopia was the target of a security breach in January 2019, which continued for two weeks after its detection until the exchange managed to regain control of its wallets.
In today’s judgment, Justice Grendall revealed that users’ assets on the exchange had been held in multiple trusts, each of which grouped together account holders holding a particular type of digital asset.
The result is that account holders within each specific group are treated as the co-beneficiaries of the same trust.
As to whether crypto assets qualify under New Zealand’s trust law, Justice Grendall firmly concluded that crypto is “a species of intangible personal property and clearly an identifiable thing of value.”
As property, crypto assets are therefore, “without question […] capable of being the subject matter of a trust.” Should the liquidators succeed to recover the stolen assets, the judgment therefore holds that:
“They are to be dealt with pro rata within each specific trust for the digital asset concerned according to the amounts recovered assessed against the amounts stolen.”
While account holders will be reimbursed, Justice Grendall determined that the pool of liquidated assets available to creditors is likely to be around NZD 5.4 million [$3.22 million].
This amounts to less than 50% of the value of their claims, given that the total value of all creditors’ claims is an estimated NZD 12.7 million [$7.57 million], NZD 5 million ($2.9 million) of which is being sought by the tax authorities.
Identity Troubles
A further detail in the judgment refers to cases where the assigned liquidator, Grant Thornton, might be unable to ascertain the identity of a particular account holder. In such instances, the affected digital assets are to be dealt with pursuant to New Zealand’s Trustee Act.
This is particularly relevant in light of a revelation from Grant Thornton in August 2019. The firm then explained that some Cryptopia customers did not have individual wallets and their funds were pooled together, as the exchange kept details of customer holdings in its database.
As a consequence, the firm said it was impossible to determine individual ownership by relying on wallet keys.
At the time, Grant Thornton assured users that it was working to “reconcile the accounts of over 900,000 customers, many holding multiple crypto-assets, millions of transactions and over 400 different crypto-assets […] one-by-one.”
In December, Grant Thornton revealed it had recovered almost $11 million and disbursed $2.46 million to certain preferential creditors. However, the firm said it was still “not practicable to estimate a completion date for the liquidation,” adding that “no detailed reconciliation” process between customer databases and crypto assets held in wallets “had ever been completed.”
Updated: 4-8-2020
US State Regulators Order ‘Fraudulent’ Crypto Mining Scheme To Shut Down
The Texas State Securities Board (TSSB) and Alabama Securities Commission (ASC) ordered Ultra Mining to cease and desist, alleging it promised to double investments in a cloud mining scheme.
The state securities regulators filed an emergency action against Ultra BTC Mining and Laura Branch on Wednesday, alleging the firm promised to double investors’ funds, touted a massive bitcoin price rise, offered affiliate and partner programs and claimed to donate to COVID-19 charity efforts without proof.
Ultra Mining allegedly raised $18 million.
According to the order, the investments in hash power appear to be securities. The TSSB is alleging that the respondents failed to register before selling these securities, and “are engaging in fraud” by making misleading statements about the returns.
“The company is promising eye-opening returns. According to the order, they are telling potential investors that a $10,000 investment in computing power will return nearly $10,500 per year. A $50,000 investment will return nearly $52,000 per year,” a press release said.
The respondents claim that “bitcoin is still in a bull market,” and expect the price to reach nearly $23,000, and letting investors who deposit at least $10,000 receive a greater share of the mining power, the order said.
Ultra Mining’s website describes it as a “cryptocurrency bitcoin cloud mining company.”
“The company provides modern, high-efficiency platform rental services for Bitcoin mining.
We guarantee an instant connection, access 24/7, operation without any interruptions, real-time mining monitoring, easy-to-use and secure platform as well daily mining outputs,” the company’s website reads.
While the website links a Facebook page, the Twitter and Telegram icons on the site link to Twitter.com and Telegram.com, rather than actual social media profiles. (Note: Telegram.com is the local newspaper for Worcester, Mass., while Telegram.org leads to the messaging app.)
Ultra Mining is also claiming to have donated at least $100,000 to Unicef to fight COVID-19, and claims it will donate again.
However, “respondents … are expressly refusing to provide any information that verifies the donation, that potential investors can rely upon to independently verify the donation or that demonstrates their financial ability to donate the money,” the order said.
Ultra Mining did not immediately return a request for comment.
Updated: 4-9-2020
Bitcoin Trading Scam Claims To Involve Prince Harry And Meghan Markle
A Bitcoin (BTC) trading scam has claimed the involvement of the Duke and Duchess of Sussex Prince Harry Charles Albert David and his wife Meghan Markle.
According to an April 9 report by the Mirror, the royal couple was featured in a fake BBC article where they praised a Bitcoin trading scheme.
The fake news piece claimed that the pair talked during a television show about a “wealth loophole” that can “transform anyone into a millionaire within three to four months.”
According to the fake article, the scheme would play a role in the couple’s very real intentions to step back as senior Royal Family members and become financially independent. The report praises the well-known Bitcoin scam Bitcoin Evolution:
“What’s made us successful is jumping into new opportunities quickly and without hesitation, and right now our number one money-make is a new cryptocurrency auto-trading program called Bitcoin Evolution. […] It’s the single biggest opportunity we’ve seen in our entire lifetimes to build a small fortune fast. […] We urge everyone to check this out before the banks shut it down.”
Too Good To Be True
The article leads potential victims to the scam’s website, which features a red banner and a countdown clock, warning that registration will close soon because of high demand. As the Mirror explains, this is a strategy meant to motivate potential investors to fall for the scam. The website also claimed that members usually earn at least $1,300 daily while working an average of 20 minutes per day, adding:
“Your profits are unlimited within The Bitcoin Evolution. Some members earned their first million within just 61 days.”
Bitcoin Scam Impersonations
In order to gain credibility, promoters of cryptocurrency scams often claim to involve well-known public figures. As Cointelegraph reported in late March, Janet Jackson’s billionaire ex-husband, Wissam Al Mana, was also featured in such a scam promotion on Facebook. He later demanded that the social media platform reveal the identity of the promoter.
Also in March, the cryptocurrency community spotted a bogus YouTube account impersonating Brad Garlinghouse, the CEO of the firm behind XRP Ripple.
Updated: 4-11-2020
$2M Crypto Scam Allegedly Funded Man’s Lavish Lifestyle
A trust has sued businessman, Brock Flagstad, over allegedly misappropriating over $2 million in funds that were purportedly designated for cryptocurrency trading.
Despite Flagstad soliciting the funds for the purpose of digital asset trading, the James Streibich Revocable Trust accuses the businessman of siphoning money from the investment to fuel an exorbitant lifestyle involving private jets and luxury vehicles.
Businessman Accused Of Misappropriating Over $2M
The complaint has been brought against both Flagstad individually, and against seven companies operated by the businessman — levying allegations of fraud, theft, conspiracy, breach of contract, and breach of fiduciary duty.
The trust asserts that Flagstad reached out to its trustee, James Streibich, in May 2018 to pitch an investment that would be used by his firm Folding Light’s “proprietary financial trading platform.”
In exchange for a $2 million investment, Streibich claims the trust was assured a preferred interest in Folding Light and informed by Flagstad’s attorney that the funds would exclusively be used for trading.
However, the trust claims that within just weeks of its investment, Flagstad began “siphoning trading capital the trust invested with Folding Light to outside banking accounts and his other ventures.”
Flagstad Allegedly Requested $200K Loan And Fled To Georgia
After Folding Light’s trading team left the firm in 2018 to start a new company, the trust states it accepted a request from Flagstad for a $200,000 line of credit.
In the Summer of 2019, the trust claims that Flagstad stopped making interest payments on the loan, moved to the state of Georgia, and became “increasingly unavailable.”
Flagstad allegedly operates 17 companies from the same address in Chicago, with the plaintiffs accusing him of perpetrating similar schemes targeting other Chicago-based investors.
“Flagstad has solicited millions of dollars in private equity funds for Flagstad companies from numerous prominent Chicago-area investors,” the complaint reads.
Investment Capital Possibly Used To Fund Lavish Lifestyle
Streibich claims to possess banking documents showing at least $849,000 that had been wired from Folding Light to his personal bank account.
The trust insinuates that some of the funds it invested may have been used to support exorbitant purchases, with the claim asserting that “Flagstad has a rapacious personal need for cash to support his lavish lifestyle of private jets and expensive cars.”
The trust is seeking injunctive relief and compensation for damages.
Flagstad Denies Allegations
The businessman’s attorney, Stan Sneeringer, told Law360 that the allegations against Flagstad are false and they intend to defend the case “vigorously.”
“Anyone can allege anything they want in a complaint, particularly where, as here, the allegations are made ‘on information and belief.’ It is another matter to prove those allegations in a court of law,” he added.
Updated: 4-14-2020
The Federal Bureau Of Investigations (Fbi) Expects A Rise In The Number Of Crypto Scams Related To The Coronavirus Pandemic
In a April 13 press release, the FBI warned that the increase of “cryptocurrency-related fraud schemes” would only be facilitated by more people getting on board with crypto. The elderly are particularly vulnerable, but the agency is reporting people of all ages could be victimized by such scams.
“There are not only numerous virtual asset service providers online but also thousands of cryptocurrency kiosks located throughout the world which are exploited by criminals to facilitate their schemes. Many traditional financial crimes and money laundering schemes are now orchestrated via cryptocurrencies.”
In particular, the agency warned Americans to be on the lookout for blackmail attempts, work from home scams, fake COVID-19 treatments or preventative measures, and somewhat more traditional investment scams.
Among the more egregious scams the FBI mentions is an email or letter in which the author threatens to infect the victim or their family with the coronavirus unless a payment is made to a provided Bitcoin wallet address.
How To Spot A Fake Charity
As reported by Cointelegraph, some online perpetrators have even attempted to steal cryptocurrency by misleading people into thinking they are sending Bitcoin donations to the World Health Organization (WHO) to fight the COVID-19 pandemic.
According to the FBI, anyone who suspects they are being targeted by a scammer should verify that such charities are legitimate and accept crypto for donations. Even if the organization is legitimate, “pressure to use a virtual currency should be considered a significant red flag.”
Scams In The Time Of Coronavirus
The FBI warning is consistent with the data published on April 10 by blockchain forensics firm Chainalysis. The firm noted while the average value of transactions received by the wallets of known scammers fell 30% during March, the number of scams involving blackmail and fake email narratives have surged.
Updated: 4-20-2020
DForce Hacker Attempts To Negotiate After Allegedly Leaking His Identity
The hacker behind the recent theft of $25 million from DeFi platform Lendf.me has leaked important data about himself, and is already signaling for peace.
The world of decentralized finance (DeFi) suffered yet another incident on April 19 as Chinese lending platform Lendf.me, part of the dForce network, was drained of almost all of its funds.
The hack is shaping up to be different from others, as the hacker seems to be negotiating with the founders of the protocol.
As reported by Cointelegraph yesterday, the attack occurred at 8:45 AM Chinese time on April 19, which corresponds to 8:45 PM Eastern time on April 18. The attacker leveraged a well-known vulnerability in the expanded ERC-777 token standard called reentrancy attack.
How Did The Hack Work?
The hacker used the imBTC token as the Trojan horse of the attack. It is one of many Ethereum (ETH) wrappers for Bitcoin (BTC), which was written according to ERC-777 specification. This is considered a more advanced but also more vulnerable version of the common ERC-20 standard — especially when used in a DeFi context.
The hack exploited this by combining it with a crucial flaw in Lendf.me’s contracts and how they updated the user’s balance.
As an analyst going by the pseudonym of Frank Topbottom explained on Twitter, the hacker executed many iterations of a simple attack.
In every single transaction, the hacker deposited imBTC on the Lendf.me platform, which was registered on his account’s balance. A second deposit from the same transaction would add a minuscule amount of imBTC, which would allow using a “reentrancy” to withdraw the previously deposited tokens.
Crucially, the contract failed to update the hacker’s balance when withdrawing money. He was thus free to deposit the BTC again, doubling his balance each time.
Eventually, the hacker siphoned almost the entirety of the imBTC present on the platform, amounting to some 291 imBTC ($2 million), according to the analyst.
He then continued to perform the same attack, which at this point simply inflated his balance until its value covered the entirety of the funds held by the protocol.
Finally, he used the fake balance as collateral to borrow almost every single token available on the Lendf.me platform, carrying off about $25 million in various cryptocurrencies and stablecoins.
The Hacker Already Got Partially Busted
Shortly after the attack, an interesting exchange of on-chain messages occurred.
The hacker sent three transactions of PAX tokens summing up to $250,000 to 1inch.exchange, ParaSwap and an account identified as “Lendf.me admin.” This is most likely a symbolic gesture, as pax means “peace” in Latin.
Lendf.me replied with an email address to contact and then signaled that it had responded to the hacker’s inquiry. Later he returned Huobi-issued assets to Lendf.me, worth about $2.6 million.
Lendf.me finally sent a message with a mildly threatening tone, saying “Contact us, for your better future.”
Sergej Kunz, the CEO of 1inch.exchange — a decentralized exchange aggregator that the hacker used to exchange some of the funds — explained to Cointelegraph that the cybercriminal leaked important metadata about himself by directly using its web-based content delivery network, instead of the IPFS-based frontend.
Specifically, all three exchange requests came from a single Chinese IP address, which suggests that the hacker did not use a decentralized network like Tor. Kunz theorized that this is a VPN or a proxy server, which may be liable to subpoenas.
The hacker is also known to have been using a Mac, revealing his screen’s resolution and system language, which was set to “en-us.”
It is worth noting that this data is trivial to obfuscate, but the high amount of uncommon details in this metadata suggested to 1inch that it was simply an oversight. He concluded:
“He seems to be a good programmer, but an inexperienced hacker.”
As police investigations are already underway, according to Kunz, it appears likely that the hacker will be forced to return the money in hopes of lenient treatment.
Updated: 4-20-2020
Crypto Staking Wallet Offers 1.5% Daily Returns: Ponzi In Progress?
A cryptocurrency staking app which offers 1.5% daily returns might be a Ponzi scheme related to one that exit-scammed two years ago.
A cryptocurrency staking wallet that offers users as much as 1.5% daily returns is bearing striking resemblance to a Ponzi scheme.
That’s according to a Medium article published on April 19 by Jan Kowalski which warns readers to steer clear of an app known as StakedWallet. The website offers Proof-of-Stake “investment opportunities” wherein the user’s daily payout increases the longer they keep their funds staked.
Staking payouts begin at 0.6% per day, and increase to 1.5% after nine months. Seemingly effortless daily returns such as these have been a hallmark of almost all well-known cryptocurrency scams in the past, including the infamous BitConnect.
At first glance the app appears to have overwhelmingly positive reviews on both Google Play and the App Store, as well as Trustpilot. However, closer inspection of the reviews shows them to be either incredibly vague, or lacking in logic.
One Gabriel Cătălin Baltac wrote on Trustpilot on April 19 that he had already made “millions of bitcoins” using the app:
“Great app i’ve made millions of bitcoins using this thank you!”
As of press time, total supply of BTC is roughly 18.34 million.
Return of Westland Storage?
Of the 945 reviews left on Trustpilot, just 4% fall under the ‘bad’ category, while 93% are either ‘excellent’ or ‘great’. However, many of the bad reviews echo a similar sentiment – and they also make mention of ‘Westland Storage’:
“All of you should be arrested. I am following and you will see the result. I will see all of you under arrest. Only way is you refund me. Pay my money back scammer. You thieves from westland storage and now stakedwallet.io have rubbed my 10 LTC. Pay it back…”
Kowalski’s article also mentions Westland Storage — a defunct cryptocurrency Ponzi scheme that exit-scammed in late 2018. Indeed, Kowalski claims that the operators of Westland Storage are the same people running StakedWallet today.
His article draws attention to similarities between StakedWallet’s website and that of Westland Storage, seen below. Kowalksi also notes similarities in the user interface of both mobile apps, while the in-app token, SWL, is a slight rearrangement of Westland Storage’s WSL token.
Kowalski — a victim of Westland Storage’s exit-scam two years ago — is well-placed to compare the two projects. He says he registered for StakedWallet and noticed the similarities straight-away:
“I knew what it is. Same bounty system, suspiciously similar in-app currency called SWL (Westland Storage had WLS), literally the same part of UI in StakedWallet as in Westland Storage mobile app. The similarities are just too huge.”
The StakedWallet website links to documents displaying the project’s status as a legally registered company in Australia, however, as Kowalski notes, Westland Storage was also a registered company.
The website’s traffic jumped from 72 clicks per month, to 437,000 clicks, within the last three months, according to data from a free SEO plugin tool. No ownership information is present on the website. Attempts were made to reach the site owners, but no reply has been forthcoming thus far.
Updated: 4-22-2020
Chinese Cosmic Cryptocurrency Ponzi Absorbs $11 Million in Three Weeks
A new Chinese Bitcoin Ponzi scheme has absorbed roughly $11 million in Bitcoin in less than one month of operating.
Antimatter Kingdom (AK), a new Chinese crypto Ponzi scheme, appears to have netted $11 million worth of Bitcoin (BTC) in less than one month of operating.
Upon launching at the start of April, AntiMatter Kingdom described itself as “a super mining application group” operating on the CXC chain.
The press release boasts that AK reduces its supply by 18% every 90 days, urging investors to capitalize on the “huge opportunity.”
CXC claims to comprise a “revolutionary blockchain business structure” allowing it to “compete with the cruel cosmic entropy law and make the development of commercial civilization lasting and orderly.”
Investors are supposedly allowed to tap into AK’s cosmic capabilities through a variety of cloud mining schemes in exchange for BTC — promising exponential returns in the form of “continuously transmit[ting] the growth force for the source ecology.”
AK Garners Eight-Figures In Three Weeks
While AK claims to have absorbed 180,000 Bitcoins, it appears that the scheme has netted closer to $11 million in BTC — with a wallet that blockchain analysis Ergo has associated with the scheme having received 1,607 Bitcoins as of this writing.
The scheme follows the enormous PlusToken scam, which absorbed $1.4 billion in Bitcoin during 2019.
PlusToken reached heights unprecedented by a crypto scam, sponging 200,000 or approximately 1% of Bitcoin’s total supply.
As a consequence of its success, blockchain forensics firm Chainalysis believes that attempts from PlusToken’s operators to liquidate their stash impacts the price of Bitcoin.
Updated: 4-22-2020
Judge Orders Arrest of Former GOP State Senator Involved with Crypto Scam
A Texas federal judge issued a bench warrant in response to a contempt motion brought by the SEC against former Rep. Senator David Schmidt.
A Texas federal judge issued warrants for the arrest of an ex-Washington state senator and the leaders behind an alleged cryptocurrency scam involving the Meta 1 coin.
At an April 21 hearing with the U.S. Securities and Exchange Commission, Judge Robert Pitman ordered bench warrants for former Republican senator David Schmidt and cohort Robert Dunlap after they failed to appear. This was despite the fact the proceedings were being convened over video conference in light of COVID-19 prevention measures.
Nicole Bowdler, the third defendant named in the judge’s ruling, was not targeted in a bench warrant, but given one final opportunity to comply by April 24.
SEC Motion Targeting Crypto Scammers
The arrest warrants are part of an ongoing case from the SEC regarding the Meta 1 coin, an alleged crypto scam backed by Schmidt that promised investors the coins were backed with “$1 billion in fine art or $2 billion of gold holdings” without having any actual tokens. The SEC froze the cryptocurrency’s assets on March 16 and charged the firm’s operators with fraud.
However, that apparently did not stop Schmidt and Dunlap from continuing to tout Meta 1. According to the SEC’s contempt motion, the three defendants had already raised over $4.3 million from Meta 1 “investors” and were continuing to sell the tokens.
Arrests Over Fines
Judge Pitman chose an arrest warrant for Schmidt and Dunlap over a fine, citing that the latter would “neither be especially burdensome nor particularly effective” in light of the assets at their disposal:
“If incarcerated, Dunlap and Schmidt will be unable to continue Meta 1’s operations, create marketing videos, or email their putative investors.”
The bench warrant to be carried out by the U.S. Marshals Service will have the crypto scammers delivered into federal custody in the Western District of Texas.
Republican Senator And “Earth Angel” Scammers
None of the defendants in the SEC case is a stranger to controversy. Schmidt lost a re-election campaign for his seat in Washington in 2006, after which he faced investigation for misspending over $40,000 in campaign funds. He subsequently paid a $10,000 fine.
However, despite his propensity for illicit activities, Schmidt wasn’t the origin of the purported crypto scam. That honor goes to Dunlap, who launched the Meta 1 token with Bowdler in April 2018.
Bowdler is considered to have played a lesser role in the scheme, which may explain why Judge Pitman did not issue an arrest warrant for her like Schmidt and Dunlap. In one of the SEC’s March filings, the commission said she used some rather unique methods to attract investors in the cryptocurrency:
“Bowdler claims to use her ‘psychic expertise’ to provide investment guidance to listeners who share her beliefs, encouraging them to invest in Meta1. In particular, Bowdler claims to be an ‘Earth Angel incarnated to help humanity,’ and purports to regularly channel and commune with angels, including the mythical angel, Metatron, who frequently teaches her about ‘the realities of our world.'”
Updated: 4-22-2020
Miners Trick Stablecoin Protocol PegNet, Turning $11 Into Almost $7M Hoard
Rogue miners submitted phony price data that tricked decentralized stablecoin network PegNet into turning a small wallet balance into a $6.7 million stash.
At approximately 05:00 UTC Tuesday morning, four mining entities – which together comprised as much as 70 percent of the PegNet hashrate – submitted data that artificially inflated the price of a “pJPY,” a stablecoin pegged to the price of Japanese yen, according to a core developer going by the username “WhoSoup.”
Beginning initially with a wallet balance of $11, the group pushed the price of pJPY up to $6.7 million and then transferred it into pUSD – PegNet’s USD-linked stablecoin. They then tried (unsuccessfully) to liquidate as much as possible on spot exchanges and distribute the remainder in hundreds of different wallet addresses.
PegNet is a decentralized network, built on top of the Factom protocol, where users can trade stablecoins pegged to 42 assets. Besides fiat currencies, there are also digital assets pegged to commodities, such as gold, and other cryptocurrencies including bitcoin and ether.
The network relies on miners to submit price data collected from a series of oracles and APIs to keep stablecoin prices pegged to their fiat equivalents. Each block requires up to 50 data points, and the protocol discards the 25 submissions furthest away from the total average. Most use the third to fourth default sources, but miners are also able to submit their own arbitrary values.
“WhoSoup” told CoinDesk this isn’t normally a problem as the system works to incentivize miners – with a block reward – to submit price data in line with those of other submissions.
Over Discord, the developer explained the miners essentially performed a form of 51 percent attack by submitting 35 of the top 50 price submissions, skewing the average in their favor and meaning that the remaining 15 price submissions were discarded as outliers.
With the fake exchange rate, the miners converted the inflated pJPY into pUSD so the overall wallet balance rose from $11 worth of pJPY tokens to well over 6.7 million pUSD which, assuming accurate price data, should be worth $6.7 million.
Tuesday’s attack lasted about 20 minutes and apparently did not affect other users’ funds.
David Johnston, who as well as being Factom Inc. chairman is also one of the main figures behind PegNet, told CoinDesk that group had no control over transactions and conversion of other users, but could only confirm price data. “This attacker seems to have only affected their own wallet,” he said.
Johnston added that the attacker had not been able to transfer much of the pUSD into the PegNET’s native PEG cryptocurrency, as the protocol’s software doesn’t allow quick conversions. “This person was able to generate a bunch of pAssets, but not able to convert them into PEG and dump on the market,” he said.
The way PegNet is configured means the identity of individuals controlling the mining entities cannot be known. While there were four mining entities that worked in unison, it isn’t clear whether these were all controlled by the same person or whether this was the work of a group.
But there are still some unanswered questions. The attacker has since reached out to PegNet and claimed they were only trying to “pentest [penetration test] the network and code logic,” to identify potential vulnerabilities and notify core developers.
They have also destroyed all the stablecoins in question, sending them all to the PegNet burn address at roughly 14:00 UTC Tuesday.
Both Who and Johnston refused to be drawn on the motives behind the attack. “I can’t speak to intent of this person just their actions,” Johnston said. “Their actions were to generate the pAssets and then destroy those pAssets. [It] seems like more of a stunt than an attack given the short time it lasted and their actions since.”
The attacker’s decision to burn the assets seems to mirror the actions of the hacker who drained dForce of $25 million at the weekend and then handed back stolen assets after learning Singaporean authorities had their IP address.
Johnston said PegNet would now review some of its oracle mechanisms, to ensure they are robust enough to withstand these sorts of attacks again in the future.
“I fully expect more sophisticated attacks over time. As values in DeFi networks rise there is ever more reason to attack them,” he said. “The key is building systems like PegNet where individual users are not affected by the actions of others in the system. So because PegNet has no reserve or collateral held in a pool, there were no common user funds to drain.”
PegNet isn’t certain yet whether the miners were able to offload any of the pUSD on to cryptocurrency exchanges.
Updated: 4-22-2020
Crypto Sextortion Scams Prove to Be Alarmingly Successful
An investigation provided in-depth info regarding how sextortion scams remain profitable for cybercriminals.
A study carried out by SophosLabs in conjunction with cryptocurrency intelligence company, CipherTrace, revealed that sextortion scams are a profitable business. Between September 1, 2019, and January 31, 2020, nearly $500,000 in profits we gained by cybercriminals engaging in sextortion.
According to the report, the modus operandi is that the scammers told victims through email that their computers were hacked and that they allegedly obtained information on their history of visits to pornographic pages.
They then proceeded to extort the recipient of the message, asking for $800 worth of Bitcoin (BTC) as payment.
Bigger Criminal Enterprises Could Be Behind The Sextortion Scams
The investigation revealed that many of the cybercriminals behind these scams are connected to a large and organized network. The wallets investigated by SophosLabs and CipherTrace were found to be connected to other criminal enterprises.
SophosLabs Highlighted The Following In The Report Regarding Such Wallets:
“Tracking where physically in the world the money went from these sextortion scams is a difficult endeavor. Out of the 328 addresses provided, CipherTrace determined that 20 of the addresses had IP data associated with them, but those addresses were connected to VPNs or Tor exit nodes — so they were not useful in geo-locating their owners.”
Some of the wallets traced back to dark web markets such as WallStreetMarket, Hydra Market, and FeShop.
The Study Also Revealed The Following:
“As with many spam campaigns, the sextortion messages were launched from botnets using compromised personal computers all around the world, with PCs in Vietnam providing the greatest single share (7%). Some of the messages demonstrated some new methods being used by sophisticated spammers to evade filtering software.”
Compared to the revenue earned by ransomware attacks, SophosLabs claims that the profits from spam sextortion are relatively small. Even so, they still represent a significant source of revenue for cybercriminals.
Overall Growth In Crypto-Related Scams Amid The Coronavirus Pandemic
Amid the COVID-19 crisis, the number of crypto scams has increased, as reported by Cointelegraph, citing an FBI press release published on April 13. These include (but are not limited to) fake charities and work from home scams.
Updated: 4-25-2020
US Authorities Freeze COVID-19 Website Alleged Scammer Tried To Sell For Bitcoin
The U.S. Departments of Justice (DOJ) and Homeland Security (DHS) have seized coronaprevention.org, alleging its owner tried to sell the domain for bitcoin after posting about it in a “hacker’s forum.”
Announced late Friday, the unidentified owner of the site tried to sell the domain to an undercover agent with the Department of Homeland Security’s Criminal Investigations unit, who said they wanted to use the site to sell fake COVID-19 testing kits, a plan the owner reportedly said was “genius.”
According to a warrant attached to the press release, the owner of coronaprevention.org, referred to as “Subject A,” listed the domain for sale on a forum “known to focus on content related to, and populated by users interested in, hacking and hijacking online accounts” a day after U.S. President Donald Trump declared a national emergency due to the virus.
The undercover agent reached out, and Subject A allegedly said they were charging $500 payable in bitcoin for the domain (according to the warrant, such domains are usually closer to $20). The agent ultimately sent a partial payment to an undisclosed bitcoin address.
The news comes on the heels of the DOJ’s announcement that it had “disrupted” hundreds of domains that were being used to shill scams related to COVID-19.
A list of the domains seized was not available, and it is unclear whether Friday’s seizure was related. However, earlier this week a DOJ spokesperson told CoinDesk, “The department is aware of the reported increase in COVID-19-related fraud involving various virtual payment platforms and appreciates the proactive assistance of many in the cryptocurrency community to thwart those schemes.”
The spokesperson did not respond to a follow up question about which entities it was working with.
Updated: 4-30-2020
Google Keeps Promoting Crypto Scams Despite Strict Crypto Policies
CoinCorner reports that Google Ads is running a phishing ad despite the firm being unable to use its service.
While Google’s subsidiary, YouTube, is facing a lawsuit for promoting cryptocurrency scams, Google’s advertising platform continues to display fraudulent crypto ads through its advertising network.
According to a report by Bitcoin (BTC) crypto exchange, CoinCorner, Google Ads was running an ad for CoinCorner’s phishing clone website, CoinCornerr.com. The issue was reported by CoinCorner’s marketing manager, Molly Spiers, on April 30.
Google Ads Promotes A Crypto Scam But Doesn’t Want To Promote A Real Firm
Spiers told Cointelegraph that CoinCorner’s team first noticed the fraudulent ad on Thursday morning after searching for “CoinCorner” on Google.com and Google.co.uk. According to the executive, the phishing ad was promoted by Google.
CoinCorner has struggled to place ads on Google Ads for years.
The Isle of Man-based crypto exchange has been restricted from advertising on Google Ads since Google put a blanket ban on crypto ads back in 2018, Spiers said. Although Google subsequently announced a partial reverse of the ban, CoinCorner is still among the crypto firms that are not allowed to use Google Ads. Prior to 2018, CoinCorner was a loyal user of Google Ads.
Spiers Said:
“We have previously had full access to the GoogleAds platform – we were loyal customers for 4 years, from when we launched CoinCorner in June 2014 to when Google updated their Financial Services policy in June 2018 […] We have contacted Google a number of times to ask for updates on the UK, but to date, GoogleAds is still not available to us.”
The fraudulent CoinCornerr.com website is currently unavailable. Its Google Ad has purportedly been taken down at the time of publication. According to domain registration data, the fraudulent domain was created on April 29.
Does Google Actually Allow Crypto Ads?
According to Google’s advertising policies, the platform does allow some crypto ads. Specifically, Google Ads service accepts ads for crypto hardware products and crypto exchanges.
However, crypto exchanges are subject to specific requirements and purportedly only allowed to be promoted in the United States and Japan to date. Cointelegraph tried to reach out to Google for comment and will update if we hear back.
According to Spiers, the fraudulent website successfully bypassed Google Ads’ restrictions by not mentioning Bitcoin or cryptocurrency in their advert at all. The executive elaborated that any adverts that contain crypto-related keywords, like Bitcoin or crypto, are automatically disapproved. “They’ve used the same text as us but removed any mention of Bitcoin, which, at a quick glance, could easily be mistaken for our site,” Spiers explained.
Crypto Scam Issues Intensify On Google And Youtube
CoinCorner’s case is not the first time users have caught Google advertising a crypto scam. In March 2020, Google Ads was promoting a fake Ledger Wallet extension designed to steal crypto from users. To Google’s credit, we reported in mid-April that the company removed 49 Google Chrome web browser extensions after receiving reports of phishing activity.
Meanwhile, Google’s video giant subsidiary, YouTube, has also been burdened with crypto scams. On April 21, Ripple Labs and its CEO, Brad Garlinghouse, filed a lawsuit against YouTube after the platform promoted a fake airdrop from an account impersonating Garlinghouse. Less than a week later, Ripple CTO, David Schwartz, had his YouTube channel suspended on April 29.
Updated: 5-8-2020
Belgium Losing $3.2M To Crypto Fraud In 2019 Is ‘Tip of the Iceberg’
Belgium’s economic inspectorate reported $3.2 million in losses due to cryptocurrency fraud in 2019.
Global losses from cryptocurrency fraud and theft surged massively in 2019, doubling from 2018. Despite multiple efforts to tackle fraudulent crypto schemes, countries like Belgium continued to suffer losses to crypto fraudsters.
According to a May 8 report by Belgian newspaper De Tijd, Belgium’s economic inspectorate reported 2.94 million euros ($3.2 million) in losses due to cryptocurrency fraud in 2019.
Figures Continue To Grow, But Real Numbers Are Apparently Unreported
The recent figures show that the number of crypto fraud cases in Belgium has been growing in recent years. In 2018, Belgian’s Federal Public Service, known as FPS Economy, reported $2.5 million losses to crypto scams in the country.
What’s more, these growing numbers are apparently “just the tip of the iceberg” as the majority of fraud cases remain unreported.
Nathalie Muylle, Belgium’s minister of economy and consumer affairs, said that real losses were apparently higher than $3.2 million.
“The amounts are not always communicated by reporters,” Muylle noted.
As previously reported, Belgian authorities estimate that local investors lose more than $150 million to scam schemes each year.
Belgium Has Taken Multiple Preventive Measures To Tackle Crypto Scams
According to Muylle, Belgium has mainly taken a preventive approach to fight crypto scams so far while prosecution measures are still undecided. In 2019, the economic inspectorate reportedly sent a related query to the public prosecutor’s office for fraud and is still waiting for a decision.
Belgian authorities have indeed taken multiple preventive measures to tackle the problem in recent years. In February 2020, Belgium’s Financial Services and Markets Authority, or FSMA, blacklisted a bunch of crypto-related fraudulent websites.
Previously, FPS Economy rolled out a website to raise awareness of the risks associated with investments in crypto.
Meanwhile, the cryptocurrency industry apparently remains largely unregulated in Belgium to date. In February 2020, FSMA chairman Jean-Paul Servais urged the Senate to establish a “legal framework for the sale, purchase, and use of virtual currencies and all related financial products.” The official pointed out that fraudulent activities in the market will continue to impact investors if the industry remains unregulated.
Updated: 5-13-2020
17,000 Creditors Hope To Recover Assets Lost To Defunct Exchange QuadrigaCX
QuadrigaCX trustee Ernst & Young has received close to 17,000 proofs of claim from creditors, denominated in various fiat and cryptocurrencies.
Close to 17,000 creditors of the now-shuttered Canadian crypto exchange QuadrigaCX have filed to reclaim their lost assets.
Details of the claims were revealed in an interim status report published on May 12 by Ernst & Young (EY), the trustee for QuadrigaCX’s ongoing bankruptcy proceedings.
Details Of Submitted Claims So Far
The report reveals that as of May 6, EY had received 16,959 proofs of claim denominated in various fiat and cryptocurrencies, many of which included multiple currency components. The currencies span United States dollars and Canadian dollars, as well as Bitcoin (BTC), Bitcoin SV (BSV), Bitcoin Cash (BCH), Bitcoin Gold (BTG), Litecoin (LTC) and Ether (ETH).
The report indicates that the trustee anticipates that all claims will be converted to Canadian dollars, although respective currency conversion rates have not yet been decided upon.
Neither has EY yet finalized its review of all proofs of claim. The firm has, however, already found a number of proofs that contain technical deficiencies, such as being unsigned. In other cases, it is following up with certain claimants whose submitted proofs diverge from the amounts recorded in QuadrigaCX’s records.
EY has overridden a previous deadline of August 31, 2019 for claimants to submit their proofs and continues to process new submissions, although the report notes that the volume of new claim submissions has “slowed considerably.”
QuadrigaCX’s Corporate Tax Liabilities
EY lastly notes that QuadrigaCX failed to file its tax returns in the ordinary course of business prior to the onset of bankruptcy proceedings and that, therefore, the outstanding amount of its corporate tax liabilities is currently unknown.
Resolving outstanding liabilities with the Canadian tax authorities will be “necessary prior to the Trustee declaring any distribution to Affected Users or creditors generally as tax claims rank [on equal footing] with the unsecured claims of Affected Users,” EY indicates.
Crypto Users Doubt The Official Story Of QuadrigaCX’s Demise
As Cointelegraph reported yesterday, a new survey of cryptocurrency users has revealed the depths of suspicion surrounding the history of QuadrigaCX’s closure. The exchange’s founder and CEO Gerald Cotten — purportedly the sole individual with access to the exchange’s wallets and keys — was reported to have died while doing volunteer work at an orphanage in India.
Some 60% of respondents to the new survey believe Cotten is definitely still alive, while 90% agree that the body reported to be his should be exhumed and autopsied.
Last year, an EY report indicated that QuadrigaCX had around $20.8 million in assets, and around $160 million in liabilities as of April 12, 2019.
Updated: 5-13-2020
Crypto Scams Targeting Pacific Communities On The Rise, Say New Zealand Regulators
Cryptocurrency-related investment scams targeting Pacific communities are on the increase, New Zealand’s Financial Markets Authority (FMA) and Commerce Commission have warned.
Concerns over various crypto-related frauds alongside coronavirus-related scams have prompted the two regulators to launch an awareness campaign aimed at keeping communities safe from criminal schemes.
According to the FMA, there has been a “steady increase in complaints” relating to a variety of different frauds since March. Social media bitcoin scams that fake celebrity endorsements and news articles were identified as being the most widely reported among the different types.
The FMA’s director of regulation, Liam Mason, warned in a press release that some scams have been aimed specifically at Pacific communities. New Zealand has sizable populations of Pacific Island ethnic groups living in cities including Auckland and Wellington.
“We saw the OneCoin pyramid scheme proliferate through Pacific social and community groups. Last year the FMA also reiterated its warning that Skyway Group (or SWIG) may be involved in a scam and was targeting Pacific groups,” Mason said.
“At the very least, check if they [investment firms] are on the online Financial Services Providers Register, which by law they should be,” Mason said. “Or check if they’re named on the FMA’s Warnings webpage.”
The awareness campaign includes bilingual webpages and resources as well as radio ads that will play on popular Pacific radio stations in the Samoan and Tongan languages, the two most widely spoken Pacific languages in the region.
“Our advice is pretty simple: Don’t just trust, check it out. Even if someone you love and trust tells you a money-making scheme is OK, don’t just trust. There are lots of resources you can use for simple research, like Netsafe and the Scamwatch website,” said Joseph Liava’a, associate commissioner at the Commerce Commission, the consumer and competition watchdog.
OneCoin was called a multi-billion dollar pyramid scheme based on “lies” by U.S. prosecutors in March of last year when they indicted its leaders, Ruja Ignatova and Konstantin Ignatov. The central bank of Samoa launched an investigation into the alleged fraud in 2018 after reports promoters had been targeting local investors on the islands.
Updated: 5-14-2020
Upbit Hack’s $50M Funds Continue Moving After Hitting Binance
Millions of dollars in ETH stolen from Upbit in 2019 continues to move on unknown wallets, OKEx, and a little-known exchange.
Crypto funds associated with Upbit’s $50 million hack in November 2019 have continued to move. Soon after hitting the world’s biggest crypto exchange, Binance, large sums of the stolen funds continued to be transferred to a little-known crypto exchange as well as major exchanges like OKEx.
On May 14, Whale Alert — a service dedicated to tracking major crypto transactions — reported on a series of new transactions involving funds from Upbit’s 2019 hack. According to Whale Alert, a large portion of the stolen Ether (ETH) has also hit a number of unknown wallets.
Addresses Of Little-Known Exchange Byex.Com Receive Over $100,000 Worth Of Stolen ETH
In a series of May 14 tweets, Whale Alert reported on at least six transactions moving Upbit’s stolen ETH to Byex.com exchange. The transactions involved batches from around $15,000 to $30,000, with Whale Alert marking them as “stolen funds transferred from Upbit Hack Nov 2019 to BYEX.”
The New Transactions Came Some Time After Whale Alert First Reported In A May 13 Tweet:
“We were able to confirm just now that a significant portion of the #Upbit hacks are being deposited into an exchange called #BYEX.”
Whale Alert confirmed to Cointelegraph that the funds were transferred to the exchange with the domain Byex.com. “We are certain that we have the correct hotwallet for that exchange,” Whale Alert noted.
Byex.com Exchange Claims They Didn’t Receive The Funds Reported By Whale Alert
Byex.com exchange subsequently specified on their Telegram channel that the platform has not been able to detect the reported transactions. “I have checked on the backend and did not see such transactions in any of BYEX accounts,” Byex.com’s project manager told Cointelegraph.
The Byex rep also pointed out that the funds were apparently moved to addresses originating from another exchange, Byex.io, which is now defunct. The project manager said:
“Whale Alert traces the “old” byex.io address which led to such confusion. We did come across BYEX’s previous news when we bought the .com domain but did not pay much attention to it. We do not know any of the byex.io team. We are a new team who just started last year around September. I would like to distinguish our official name as with our domain — Byex.com.”
Over $3 Million Worth Of Stolen Ether Was Moved In Recent Days
Byex.com’s transactions came alongside a number of other transfers involving Upbit’s $50 million hack. On May 14, Whale Alert reported that over $1.3 million worth of ETH was moved to unknown wallets in a series of transactions. Previously, at least 9,000 ETH ($1.8 million) deriving from Upbit’s $50 million hack were sent to unknown wallets in three 3,000 ETH batches, Whale Alert tweeted on May 13.
Whale Alert also reported on a $55,000 batch being deposited onto major crypto exchange, OKEx, on May 14. Cointelegraph reached out to OKEx for comment, but did not receive an immediate response. This story will be updated should they respond.
On May 13, Binance exchange froze $27,000 worth of stolen Ether on its platform immediately after Whale Alert reported on the suspicious transaction.
Updated: 5-14-2020
COVID-19 Defense Fails Once More For Co-Founder Of Alleged $9M Crypto Ponzi
In the case against an alleged crypto Ponzi scheme founder, judges are not convinced that the risk of COVID-19 is enough to allow posting a bail bond for release.
One of the persons behind an alleged cryptocurrency Ponzi scheme has once again been denied bail. The accused, John Caruso, continues to be considered an extreme flight risk despite pleading not guilty earlier in 2020.
As filed by Judge John Tuchi on May 14, Caruso requested another emergency motion asking to be released from prison, after a similar request was denied in April by Judge Michelle Burns.
Caruso’s legal team attempted a COVID-19 defense, arguing that the spread of the virus puts the defendant at risk of infection while he stays in prison.
Both of the judges reviewing the motion did not cede to this tactic, stating that the spread of COVID-19 has no effect on Caruso’s flight risk.
In the earlier denial, Judge Michelle Burns had also noted that the 28-year-old Caruso is in excellent health condition and is unlikely to be strongly affected by the coronavirus. Furthermore, Judge Tuchi argued that Caruso would be potentially more at risk of infection in the outside world, summarizing that the issues of flight risk and personal health “are apples and oranges.”
The judges appear to be adamant in their wish to detain Caruso due to his troubled history, which includes seven prior felony convictions and multiple counts of violated probation. He was released from prison in November 2017, while the alleged Ponzi scheme was launched in June 2018.
A compounding factor is that investigators appear to have been unable to trace the location of all proceeds from the scheme, leading them to believe that he could use the money to disappear.
Previous History
John Caruso is accused, together with his partner Zachary Salter, of creating Zima Digital Assets, a cryptocurrency investment scheme that failed to invest the funds it received into cryptocurrency.
Instead, the pair are believed to have used customer funds, amounting to approximately $9 million, to finance their lavish lifestyle.
The pair was rumored to have racked up $830,000 in gambling losses following 30 trips to Las Vegas, in addition to accumulating $670,000 in credit card expenses, $540,000 in private jet and luxury vehicle rentals, and $150,000 in rent for a 20,000-square-foot mansion.
Of the $9 million collected, about $1.9 million seems to have been paid out to early participants to make the scheme appear more trustworthy.
Caruso’s trial is scheduled for July 2020, facing charges that could result in five years in prison.
Updated: 5-16-2020
PlusToken Scammer Implicated In China’s Second Ten-Figure Crypto Ponzi
Local police have busted Wotoken, China’s second ten-figure crypto Ponzi.
The scam, Wotoken, took in roughly $1 billion worth of crypto at current prices from over 715,000 victims.
One of the scam’s core operators is purportedly linked to PlusToken — a multi-billion Ponzi that is believed to have impacted the price trajectory of Bitcoin (BTC) on numerous occasions throughout 2019.
China’s Second Ten-Figure Ponzi Busted
Earlier today, Chinese media outlet, Qianba, reported that a case surrounding “super large MLM network” Wotoken had opened for trial on May 14 in Yancheng City.
The scam claimed to generate returns for users through employing algorithmic trading bots, offering referral commissions to affiliates. However, as with most MLM scams, the advertised proprietary trading software did not exist.
In total, 715,249 registered users fell for the scam, resulting in Wotoken accumulating 46,000 BTC, over 2 million Ethereum (ETH), 292,000 Litecoin (LTC), 56,000 Bitcoin Cash (BCH), and 684,00 Eos (EOS) — worth nearly $1 billion at the time of the arrest.
Wotoken was active from July 2018 through October 2019.
Wotoken Operator Associated With PlusToken
Six defendants faced trial for operating Wotoken, including one individual with ties to the notorious PlusToken Ponzi.
All six defendants pleaded guilty, with the court recommending prison terms of between six months and 11 years.
Updated: 5-19-2020
US FinCEN Awards Secret Service For Seizing $22 M In Crypto
An investigation that involved several U.S. federal agencies led to the bust of the darknet operators and seizure of $22M in cryptocurrency.
May 19, the Financial Crimes Enforcement Network (FinCEN) awarded several federal agencies in the United States, whose joint probe led to the seizure of $22 million worth of cryptocurrency from the darkenet operators.
12-16% Cashout Fee
This is an annual award whereby FinCEN recognizes law enforcement agencies for using Bank Secrecy Act reporting to successfully pursue and prosecute criminal investigations. The investigation involved Immigration and Customs Enforcement-Homeland Security Investigations, United States Postal Inspection Service, and United States Secret Service:
“Investigative results identified dark web vendors sending illicitly earned Bitcoin with a physical receiving address via an encrypted email to conduct this cash-out scheme. This cash-out vendor charged anywhere from 12-16 percent depending on the amount of digital currency being cashed out.”
Everything Is Big In Texas
The investigators used the information they subpoenaed from a “well-known cryptocurrency exchanger.” This massive joint investigation effort:
“Concluded after the arrest of 42 individuals, the seizure of $22 million in various digital currencies, $3.5 million in cash, 120 firearms, 15 pill press machines, and a wide range of controlled substances. The United States Attorney’s Office, Northern District of Texas prosecuted this case.”
Cryptocurrency-related crime is a multibillion dollar industry, although only a small percentage of crypto transactions involve illicit activity.
Updated: 5-19-2020
BlockFi’s Data Breach May Allow Criminals To Extort Rich Clients
BlockFi disclosed a data breach that potentially leaked the physical addresses and account activity of its customers, highlighting the risks of KYC finance platforms.
Crypto lending provider BlockFi reported on Tuesday that it suffered a data breach that may put some of its clients in physical danger.
According to its incident report, some of the company’s client data was breached through a SIM card swap attack performed on one of its employees.
The attackers successfully stole the email account and phone number used for the employee’s account verification procedure, which allowed them to access BlockFi’s records.
SIM swapping attacks are the result of network operator vulnerabilities and are usually performed through co-conspirators with access to the phone network’s equipment — though external intrusion techniques are also possible. This type of attack was the culprit behind several high-profile exchange thefts, but they usually target the clients themselves.
The attackers allegedly attempted to withdraw customer funds directly, but the attempts were unsuccessful, BlockFi says.
Nevertheless, the attackers had full access to customer data used as part of BlockFi’s marketing efforts.
The company stressed that no “non-public identification information” was leaked, which would include bank account numbers, passwords or social security numbers.
However, the hackers did obtain access to the customers’ full names, email addresses, dates of birth and notably, activity information and physical addresses.
Can The Victims Be Physically Extorted?
BlockFi asserts that no threat to customers’ BlockFi funds exists, writing, “Due to the nature of the information that was leaked, we do not believe there is any immediate risk to BlockFi clients or company funds.”
However, home address and activity data may expose the affected users to extortion and physical theft.
BlockFi did not disclose what kind of activity data was included in these databases and has declined to answer Cointelegraph’s query on the subject, referring to the incident report for all information.
An unnamed spokesperson only added that “we have not received further indications that the unauthorized third party has tampered with the information that was accessed at this time.”
Nevertheless, it is easy to believe that simply reading the activity data would allow attackers to know the size of the client’s account and collateral pledges. This kind of data is crucial for any directed marketing campaign.
Furthermore, BlockFi’s Privacy Policy Explicitly States That This Information Is Available For Marketing Usage:
“We may use your personal information and information about how your use our services to send promotional and other information to you. We also may use your personal information to conduct analysis regarding your usage of our services and products and the effectiveness of our marketing initiatives.”
The connection between the home address, the customers’ activity on the platform and their identification data could allow criminals to precisely target the victims of this attack to extort them out of their cryptocurrency.
This kind of theft is not unheard of, as a Singaporean man was reportedly kidnapped in January and forced to transfer the cryptocurrency in his possession.
Similar cases were reported in 2017, notably the kidnapping of the director of the crypto exchange Exmo in Ukraine. India was also reported to have several such cases that year.
The Case For Anonymous Finance
An Ethereum core developer used the occasion to praise the anonymity of blockchain-based decentralized finance, saying “will naysayers finally start to understand the point of DeFi on Ethereum?”
While DeFi carries a different set of risks, the consequences of data breaches on centralized platforms that hold Know Your Customer data could be catastrophic.
Updated: 5-19-2020
BlockFi Says Hacker SIM-Swapped Employee’s Phone, No Funds Were Lost
BlockFi said an attacker got hold of users’ data by compromising an employee’s phone and taking control of the person’s phone number through a SIM swap attack.
The New York-based crypto lending platform announced in a memo to users on Tuesday that a hacker – whose identity remains unknown – gained access to some of its retail marketing systems for just over an hour early on May 14.
“On May 14, there was a data incident at BlockFi that exposed certain client account information for a brief period of time. While no information was accessed that would enable the intruder to access your account or your funds, we believe it is in the interest of transparency to share the following details with you, and all of our other clients who were potentially affected,” reads the memo, which was shared with CoinDesk.
BlockFi said the hacker accessed confidential data, such as names, dates of birth, postal addresses and activity histories. Other sensitive account information including bank account details, social security and tax identification numbers, passport and driver’s license numbers and photo scans, were not affected in the data breach, the company said.
User funds were also not affected.
In an incident report, also published Tuesday, BlockFi said the hacker had accessed through an employee’s phone. By tricking the mobile phone operator into activating the employee’s phone number on another device, the hacker was able to access some parts of the company’s internal systems.
“A BlockFi employee’s phone number was breached and utilized by an unauthorized third party to access a portion of BlockFi’s encrypted back-office system,” the incident report reads. “The unauthorized third party was able to access BlockFi client information typically used by BlockFi for retail marketing purposes throughout the duration of this incident.”
The report adds the hacker tried, unsuccessfully, to make withdrawals of user funds, before BlockFi was finally able to remove them from the internal system.
In a statement, a BlockFi spokesperson said: “A sole intruder gained minimal access for a short period of time to select internal marketing systems. The BlockFi team immediately mitigated the impact of the breach through a number of standing policies and safeguards in place to protect client assets and data.”
“The issue has since been resolved and BlockFi’s products and services are fully operational and secure,” the spokesperson added.
The spokesperson did not specify which mobile network the employee used.
Updated: 5-19-2020
Ukraine Arrests Hacker Accused of Selling Personal Data, Crypto Wallet Info
A national law enforcement agency in Ukraine has detained a hacker it claims is responsible for the country’s largest known theft of personal data, cryptocurrency wallets and other information.
The Security Service of Ukraine (SSU) reported detaining a hacker, known as Sanix, allegedly for selling a database with 773 million email addresses and 21 million unique passwords on various online forums in recent years.
In addition to email logins and passwords, the database contained “PIN codes for bank cards, e-wallets of cryptocurrencies, PayPal accounts, information about computers hacked for further use in botnets and for organizing DDoS attacks,” the SSU said in its press release. The stolen data belonged to people from different countries, including the European Union and the U.S., the agency claimed.
The agency seized “computer equipment with two terabytes of stolen information, phones with evidence of illegal activities and cash from illegal transactions,” including about $10,000 in Ukrainian hryvnias and U.S. dollars, the release said.
The seizures happened after SSU received a tip that Sanix is “probably a Ukrainian, a resident of [the] Ivano-Frankivsk region” and searched his home.
Sanix now faces criminal charges for unauthorized interference with computers and unauthorized sale or dissemination of information with limited access. According to the Ukrainian criminal code, a combination of these two can lead up to eight years of prison time.
The breach was first reported in January 2019 by cybersecurity researcher Troy Hunt. Wired called it “a breach of breaches,” saying the 87-gigabyte database “claims to aggregate over 2,000 leaked databases that contain passwords whose protective hashing has been cracked.”
The first batch of stolen data had been followed by several more “collections,” offered by Sanix as well as another hacker named Oxa, Forbes wrote at the time. The hackers offered “lifetime” access to the databases for modest amounts from $45 to $65.
Updated: 5-20-2020
Hackers Target Enterprise Blockchains
Private blockchains that have been specifically designed for enterprise use could be highly desirable targets for hackers’ attacks.
When blockchain technology was first brought to the public’s attention, it was lauded on many fronts as “unhackable.” While there are many benefits to blockchain worth noting already, we probably still haven’t seen what its ultimate potential will be. One thing is certain though: It is not unhackable. That reality has been illustrated with increasing clarity to the tune of around $2 billion in cryptocurrency stolen by hackers since 2017.
Recent attacks have seen a shift in focus from public networks, such as the Bitcoin and Ethereum blockchains, to private networks built for the use of large corporations. In theory, the latter should be a more difficult target for a hacker due to their nature as smaller ecosystems where everyone knows one another and intruders have a harder time hiding.
The reality has been a different matter. As more private enterprise blockchain networks come online, cybercriminals have focused intently on proving that the technology is, in fact, quite hackable. Here’s what they’re doing and how to keep them from getting into yours.
Blockchain Basics
Before we dive into the particulars of recent attacks on private blockchain networks, let’s make sure our terminology is straight. A blockchain simply means a decentralized cryptographic database that exists on linked computers called nodes. Each node keeps an up-to-date copy of the entire database. All nodes have to verify and approve a transaction before it is added to the database.
Thanks to a design based on cryptography, economics and game theory, node owners have a financial incentive through a process called mining to play a straight game rather than try to subvert the system. A correctly designed blockchain database is easy to verify and add transactions to but hard and, more importantly, expensive in computing resources to defraud.
Companies engaged in a variety of activities such as cross-border transactions, digital record storage, and tracking goods and information have had their eye on blockchain for a while now. Blockchain application-building has been a high priority project for some truly massive operations, such as Fidelity Investments and the New York Stock Exchange to name a couple.
What sometimes goes overlooked in the rush to take advantage of the allure of blockchain security and ease of use is that they are essentially trying to tame a Wild West technology and make it play nice in the most corporate of environments.
Easing into the real world
While it is true that one would be hard pressed to recall a single private blockchain network hack that resulted in a real loss, there are reasons for this, and these reasons are in the process of changing. First of all, enterprise-level blockchain apps have been under feverish development the past few years, and only now are a few starting to be rolled out for public use.
In some cases, blockchain has allowed developers to put a new twist on an old idea. The Ethereum-backed security app called Orchid is in the process of taking the traditional idea of a virtual private network, throwing it on top of a blockchain and presto, you’re looking at the next generation of privacy technology.
Expect to see an increasing pace of familiar products and services receiving a similar blockchain boost.
To the average hacker, there was previously nothing on these networks worth stealing, but that is changing. New apps are moving from the research and development stage into production, which means there is now a profit motive. Like detestable flies, hackers are attracted to this new prey. They see it as both a challenge to their skills and an opportunity for easy money.
As time has passed, a few strategies have arisen that allow the unhackable blockchain protocol to be penetrated.
Control 51% and you control the game
The 51% Rule is an inherent drawback to most blockchain networks. The feature that allows this kind of attack is based on the proof-of-work concept in which a transaction must be approved by a majority of nodes, or 51%, in order to be approved and added to the database. If a single entity, in this case an entity with a propensity toward fraud, could somehow summon the computing resources that gave it control of 51% of the nodes, then it’s simply a matter of sending payments and then creating an alternate version of the database in which the payments did not happen.
This type of divergence is called a “fork” in blockchain terminology. Continuing with our assumption that a single hacker controls a majority of the nodes, they could designate the fork as the legitimate database version and continue to spend the same cryptocurrency again and again. As mentioned, collecting together the computing power needed to take over a major currency such as Bitcoin (BTC) or Ether (ETC) works out to a cost of thousands of dollars per hour, according to the site Crypto51.
However, if a hacker decides to go after a smaller, more lightly traded coin, the cost to take over the network drops considerably.
Corporate Insider Attacks
When it comes to private networks of the kind currently being deployed by major corporations, the most severe danger posed is from those already within the system. In other words, employees, vendors or others that have been invited to the network immediately have access to all the confidential data stored there. This is one design flaw when compared with public networks that needs to change.
On the public side, such as with Bitcoin, developers deploy zero-trust and other security tools to keep sensitive data from falling into the wrong hands and often off the chain entirely. As with traditional private networks, too many companies delving into their first blockchain project think that the main threat is from the outside. Their energy and focus go toward keeping outsiders on the outside, forgetting that insiders can be a threat too.
Philosophical action tip for blockchain design: Trust no one, especially those on the inside. A disgruntled ex-employee with an ax to grind and knowledge of where the nodes are could sell out your network to the highest dark web bidder. One denial-of-service attack and it’s all over. Design for safety from the outside and inside.
Final thoughts
Perhaps the biggest danger posed to private blockchain networks is the fact that they don’t have a dedicated community full of members from all over the world that spend their days and nights testing, tweaking and improving the network. By its very nature of being smaller and private, there is no equivalent process in place for vigorous testing. There’s no easy solution here. It’s hard for a single company to generate the same kind of enthusiasm and support as a massively popular cryptocurrency such as Bitcoin.
One current approach is to take advantage of a company such as Kaspersky, which has developed a process for conducting blockchain security audits. Since Kaspersky is Russian-owned, some companies are understandably cautious about letting it take a look behind the curtain, but the idea is still sound. As time goes on and more corporate blockchains come online, expect the auditing and support industry to become more robust.
Updated: 5-22-2020
Plus Token Leadership Faces Criminal Prosecution In China
PlusToken main criminal suspect is facing public prosecution.
One of the ringleaders of Plus Token is now facing criminal charges in China. Plus Token is one of the largest apparent scams in the cryptocurrency industry’s history.
According to local media, Zhou will face public prosecutors in the Court of Jianhu County, Yancheng City, Jiangsu Province. As the local government only supplied Zhou’s family name, at press time we can’t confirm exactly which Zhou this refers to.
Zhou reportedly publicized and promoted the PlusToken wallet App, a so-called crypto currency financial management application, through Wechat and other avenues over the internet.
By registering four different accounts with SIM cards in the wallet, he allegedly lured more than 1.9 million people into the pyramid scam.
A Pyramid Ponzi Scheme
According to local authorities, the PlusToken wallet disguises itself as a cryptocurrency financial management app, but allows criminals to recruit members by promising high returns baked on the amount of other investors they can pull in.
Local Police Said That They Received Reports From The Public Regarding The Scam As Early As Last Year, Explaining:
“In the name of providing a cryptocurrency appreciation service, the platform falsely claims that it has the function of mining cryptos, and requires members to pay certain value of cryptocurrencies such as Bitcoin, Ethereum, EOS, etc., so as to obtain high static income.”
Other Criminals Involved
As Cointelegraph reported previously, members of the Chinese police touched down in Vanuatu and detained six people involved with the PlusToken project and extradited them back to mainland China last year. It could be the biggest crypto scam ever, with an estimated loss of around $2.9 billion.
Updated: 5-24-2020
Hacker Sells Tens of Thousands of Ledger, Trezor, And Keepkey Users’ Info
The customer databases of Trezor, Ledger, and Keepkay have allegedly been listed for sale by the perpetrating hacker.
The hacker that breached the Ethereum.org forum is allegedly selling the databases for the three most-popular crypto hard wallets — Ledger, Trezor, and KeepKey.
The Ethereum forum hacker is now selling the databases of @Trezor and @Ledger.
Both of which obtained from a @Shopify exploit.
(suggesting there are many more underground leaks).The hacker also claims he has the full SQL database of famous investing site @BankToTheFuture. pic.twitter.com/4M3f2bQKvB
— Under the Breach (@underthebreach) May 24, 2020
The three databases contain the name, address, phone number, and email for more than 80,000 users combined, however, they do not contain passwords for the accounts.
The hacker has also recently listed the SQL database for online investment platform, BnkToTheFuture.
Ledger And Trezor Databases Reportedly Compromised
On May 24, cyber crime monitoring website, Under the Breach, spotted the hacker’s new listings for the databases of the top hardware wallet providers.
The hacker claims to be in possession of account information corresponding to nearly 41,500 Ledger users, over 27,100 Trezor users, and KeepKey’s 14,000 customers.
Chat logs posted to Twitter indicate that the data was stolen through exploiting a vulnerability to the popular e-commerce website platform Shopify.
Trezor and Ledger Denies Data Breach
Following the release of the information, both Ledger and Trezor have published an update in denial of the data breach, albeit revealing that their respective teams are still investigating the situation.
Rumors pretend our Shopify database has been hacked through a Shopify exploit. Our ecommerce team is currently checking these allegations by analyzing the so-called hacked db, and so far it doesn’t match our real db. We continue investigations and are taking the matter seriously.
— Ledger (@Ledger) May 24, 2020
There are rumors spreading that our eshop database has been hacked thru a Shopify exploit. Our eshop does not use Shopify, but we are nonetheless investigating the situation. We’ve been also routinely purging old customer records from the database to minimize the possible impact.
— Trezor (@Trezor) May 24, 2020
Ledger uses Shopify for its eCommerce sales, and although Trezor doesn’t, any of its large resellers using the eCommerce solution may as well leave users to the possibility of data theft.
In a similar recent development, Coinfomania reported an email address leak that affected traders on popular cryptocurrency derivatives exchange, BitMEX.
Hacker Adds To Bazaar Of Crypto Account Info
The hacker is now advertising the databases of 18 virtual currency exchanges and forums, in addition to the email lists of two crypto tax platforms.
The databases include the full SQL for Korean exchange Korbit spanning 4,500 users, three databases for Mexcican trading platform Bitso, and the complete account information including passwords for blockchain platforms Blockcypher, Nimirum, and Plutus.
The hacker specifies he is only interested in premium bids, stating: “Don’t offer me low dolar, only big money allowed.”
KYC Platforms Comprise Honeypot For Hackers
Last week, BlockFi reported a data breach resulting from a Sim-swap attack. Customers’ full names, email address, date of birth, and physical addresses were leaked. Client funds were not impacted.
At the end of April, Etana, a custody firm that provides services to Kraken, also suffered a data breach that did not see any customer funds lost.
Updated: 5-25-2020
Stolen Trezor, Ledger and KeepKey Databases Are a ‘Scam,’ Says SatoshiLabs
What if this scammer is just pretending to be a hacker?
The hacker claiming to be selling user databases from top hardware wallet manufacturers Ledger, Trezor, and KeepKey appears to actually be peddling bunk, according to SatoshiLabs.
On May 24, cybercrime monitoring blog Under the Breach reported that a hacker had begun advertising the customer databases of popular hardware wallet companies for sale. The data purportedly included the full names and physical addresses for over 80,000 user accounts.
Under the Breach tweeted screenshots suggesting that the hacker obtained the databases by exploiting a vulnerability of popular e-commerce platform Shopify.
“Don’t offer me low dolar, only big money allowed,” the hacker warns prospective bidders.
Trezor Refutes Hacker’s Claims
SatoshiLabs is the team behind Trezor, and a company rep told Cointelegraph that Trezor had gotten ahold of sample data for the supposed database and found “no Trezor customer data included in the offered database.”
Trezor’s initial investigation concluded that “the content and structure of the leaked data does not correspond to the data from the Trezor e-shop and looks more likely to be fabricated.” The spokesperson added that “the whole incident seems like a scam.”
Slush, the pseudonymous chief executive of SatoshiLabs, said, “We take data privacy very seriously at SatoshiLabs. By anonymizing the data in our e-shop after 90 days, we minimize the impact of such a breach. I would like to assure our customers that their data is being treated as highly sensitive.“
A spokesperson for Shopify also told Cointelegraph that an investigation into the purported vulnerability found “no evidence of any compromise of Shopify’s systems.”
Scammer Poses As Hacker
After adding the popular hardware wallets to his advertisement for stolen data, the hacker now claims to offer customer databases of 18 total virtual currency firms, having first posted the ad on May 17.
But based on investigations carried out by the companies whose databases are supposedly available for purchase, the hacker’s entire bazaar of stolen account information is probably fabricated.
Mexican crypto trading platform Bitso, one of the companies previously named in the hacker’s list, has also refuted the validity of the cybercriminal’s claims, asserting that its investigations “have not found evidence that a third party has sufficient information to access our customers’ accounts.”
Updated: 5-26-2020
Trezor E-Shop Breach Is A Hoax
An unknown hacker listed supposedly leaked data of customers from the Trezor e-shop for bidding recently. We have thoroughly analyzed the data sample and we can confirm that it does not match our customer records from the e-shop. We can also assure our Trezor Wallet users, that their data has not been affected. We have evaluated the information as a hoax mainly due to the following facts:
* The content and structure of the leaked data does not correspond to the data from the Trezor e-shop and looks fabricated.
* Trezor has strong protocols on data protection that include anonymization of the e-shop data after a period of 90 days from the purchase.
* Trezor e-shop is not and was historically not running on the Shopify platform, which was mentioned as a source of the leaked data.
How Does The Trezor Anonymization Protocol Work?
The Trezor e-shop collects solely the necessary data needed for the delivery of the product. This data is used for logistic purposes only. After collecting the data, we treat it as highly sensitive. We know that, in the bitcoin industry, data privacy is extremely important. After 90 days of placing your order, we remove all the sensitive data from our online systems. This minimizes the impact of potential breaches.
Pro Tips For Data Privacy Handling
Even though this information is a hoax, there is always something to learn from it. We treat your data with the utmost privacy.
Ideally we would like not having your real personal information at all. But we understand your parcel has to be delivered somewhere, so here are some tips on how you can minimize the data leakage also on your side:
* If possible order your goods using the address of the company you are working for and have it delivered there.
* You can even tell your reception desk that you will be using a pseudonym.
* If you can not have goods delivered to your office, consider using a P.O. box.
* Always use a special purpose email in which you avoid your real name.
* If you really need to share your phone number, share the work one preferably.
Updated: 5-27-2020
Ledger, Trezor And Others: Hack Allegations Are Baseless, Lack Proof
Representatives of companies that were allegedly hacked strongly deny the allegations, stating that the exploit had been fixed years ago.
According to a report by an online monitoring web portal, Under the Breach, a hacker was able to penetrate the privacy protocols of major firms such as Trezor, Ledger and Bnktothefuture on May 24 and walk away with a host of sensitive customer data, including email addresses, home addresses and phone numbers.
The documents posted by Under the Breach claimed that the hacker was in possession of three large databases that allegedly contained the details of more than 80,000 customers. In this regard, it was also rumored that the hacker was able to procure the above-stated information via an exploit that was linked to Shopify, an e-commerce firm that provides its services to a number of major crypto firms.
It now appears as though this so-called data breach has been a major false-flag, since many of the companies linked with the hack have come forth to say that Under the Breach’s claims are not grounded in any factual evidence. For example, a spokesperson for Shopify told Cointelegraph: “We have investigated these claims and found no evidence to substantiate them, and no evidence of any compromise of Shopify’s systems.”
Similarly, Ledger’s security team moved to allay customer fears that their funds may potentially be in jeopardy. The firm released a detailed blog post stating that the rumor about the leaked customer data being from Ledger’s e-shop was a hoax and that the company’s security team had investigated the sample data and confirmed that it did not match its native client information.
Lastly, in addressing concerns regarding the hacker’s claim that they were able to gain access to Ledger’s client database through a 2016 Shopify exploit, the hardware wallet manufacturer’s security team stated that while Ledger currently employs Shopify as a third-party provider for its e-commerce operations, the same was not the case back in 2016.
Companies debunk the breach
To get a better overview of all that transpired since the hacking rumor went viral online, Cointelegraph reached out to Matthieu Riou, chief technical officer and co-founder of BlockCypher, a cloud-optimized platform powering blockchain applications that allegedly had its data compromised. Riou claimed that after performing a thorough analysis of the matter, his team reached a conclusion that the leak in question was more than four years old and is simply being recirculated. He further clarified:
“For example the number of records as reported by the hacker (2358 users) is particularly telling. We thankfully now have quite a few more users than that. But this number is consistent with a March 2016 data leak we had on an older system and acknowledged at the time.”
Not only that, Riou also pointed out that since the 2016 leak, his firm’s developer team has completely rewritten its user and API token management web application from scratch — as a result of which, users have had to re-register on the new platform with a different password. He added: “We’ve now been running on the new improved platform for several years and have had no issues. We can’t speak as to the severity or recentness of the data dumps originating from other firms.”
This sentiment was echoed by Peter Vecchiarelli, operations manager for Augur, a decentralized betting protocol that the hacker claimed to have compromised and stolen customer data from. Vecchiarelli stated that the “leaked” list associated with Augur was the same one allegedly acquired by hackers back in 2016. He pointed out that upon conducting a cross-reference test, his team found that the leaked list did not match any of Augur’s private email lists for marketing or crowd sale, and was merely a downloaded list of all the individuals who had set their email addresses to “publicly viewable” from a previous Slack channel operated by the company.
Lastly, Marek Palatinus, CEO of SatoshiLabs — the company behind Trezor’s various hardware wallets — told Cointelegraph that it is important for people to understand that the “data breach is not legit” and consists primarily of information that is fabricated. For example, he pointed out that Trezor’s e-shop does not run on Shopify and that the firm makes use of a niche anonymization protocol to minimize the impact of potential data breaches such as this one. Furthermore, Palantus stated:
“Even if the data was leaked from any of the mentioned party e-shops, the hardware wallet secret keys were not exposed, therefore the hacker or any other potential person that gets hold of the database won’t get access to your secret keys stored on a hardware wallet. Trezor does not collect any data from your hardware wallet or Trezor Wallet app.”
Crypto Exchanges’ Rubbish Hack Claims
Another aspect of this recent data breach is that the hacker claimed to have obtained a host of customer information from prominent crypto exchanges and investment platforms such as Coinigy, BitSo and Plutus.
Cointelegraph spoke with Coinigy co-founder William Kehl, who stated that one of Coinigy’s third-party Stripe accounts was compromised back in 2016, and as a result, an attacker was able to access info related to more than 500 customers. This data included the last four digits of customers’ credit card numbers, their names and their addresses along with associated emails. However, as part of the above-stated breach, Kehl maintains that none of Coinigy’s internal databases — including user accounts, passwords or API keys — were compromised. He added:
“We were immediately alerted to the incident when it occurred, and we immediately locked these accounts and our entire platform down, required all users to perform a complete security audit including but not limited to new passwords and API keys before they were able to log back into the platform. Again, what you see offered by the ‘hacker’ was not acquired from our database, but through gaining momentary access to some third party services we used.”
Similarly, addressing the rumors surrounding the hack, a spokesperson for Mexican cryptocurrency exchange Bitso told Cointelegraph that having investigated this alleged threat, the company’s security team has not found anything out of the ordinary. He added:
“We activated the pre-established protocols to review this potential event, and we will be informing users. At this time, we have not found evidence that a third party has sufficient information to access our customers’ accounts.”
The same thoughts were mirrored by David Morrison, community manager for Plutus, a crypto-fintech firm. Morrison stated that after having investigated several possible attack vectors, his company’s security team was not able to find any evidence of a hacking attempt. He said, “So far we have not found any solid evidence of successful hacking attempts. Regardless, we are taking all precautions possible and informing our customers appropriately.”
Jumping The Gun
On May 19, BlockFi reported a data breach that arose due to a sim-swap attack, resulting in compromised customer data held by the company, such as full names, email addresses, date of birth and physical addresses. Similarly, Etana, a custody firm that services the crypto exchange Kraken, also fell victim to a similar data breach last month.
While customer funds were reportedly not affected in any way throughout the aforementioned cases, whenever a story about some platform being compromised, people tend to jump to the worst conclusion right away.
Updated: 5-25-2020
Analyst Is ‘Surprised’ There Hasn’t Been A Large-Scale Attack On Bitcoin Cash Yet
A cryptocurrency analyst recently said that he is surprised that Bitcoin Cash did not yet fall victim to an attack, given the fall in its hashrate.
Yassine Elmandjra, a crypto asset analyst at ARK Invest, said in a May 24 tweet that the Bitcoin Cash (BCH) hashrate fell by 30% since its halving event, and only accounts for about 2% of the SHA-256 hashrate. Elmandjra now thinks it’s only a question of time before somebody takes advantage of the network:
“Surprised we haven’t seen a large scale attack yet.”
According to data from BitInfoCharts, the Bitcoin Cash average daily hashrate fell by nearly 25.6% since its April 8 halving. Still, Elmandjra presumably did his calculations based on May 23 data, where the hashrate was down by about 33.52%. It is worth noting that the hashrate is currently much higher than where it initially was, after falling by over 61%.
As Cointelegraph reported earlier this month, Bitcoin’s hashrate has shed around 25%-40%, new blocks are generated remarkably slowly speed and fees significantly higher since the halving.
Hayden Otto is a Bitcoin Cash event organizer and founder of BitcoinBCH, a BCH-based development firm. Otto argues that Elmandjra was misled by the Bitcoin (BTC) narrative that Bitcoin Cash can be easily hacked by a 51% attack.
According to Otto, “the formulas they use to determine the cost of a 51% attack does not consider important factors such as the incentives of miners.” He believes that such an attack could not be executed as easily as many suggest, and this is why no such attack took place on the Bitcoin Cash network.
Attacking Bitcoin Cash Is Easier Said Than Done
Otto added that Bitcoin Cash’s hashrate is currently about 3.5% of Bitcoin’s and has remained there for years. According to Cointelegraph’s calculations using CoinMetrics hashrate comparison chart data, BCH’s hashrate is currently equivalent to 3% of BTC’s. Furthermore, BCH’s hashrate was equivalent to about 4% on May 20, 2019. This data seems to generally back Otto’s point of view. He claims that an attack on Bitcoin Cash isn’t realistic:
“Bitcoin Cash is currently about 3.5% of BTC’s hashrate and has been around this level for more than a year. Despite this there has been no attack because miners are profit-seeking and there is no incentive to attack. Any attacker will be challenged by honest miners defending the chain, and the 10-block reorg protection neuters any attempt to secretly mine a longer chain. The risk of losing money far outweighs any potential reward, which ultimately makes any attempt to 51% attack Bitcoin Cash unviable.”
Still, as Otto himself pointed out Bitcoin Cash’s hash rate is usually just about 3.5% of what Bitcoin’s hashrate is. Because of this, BCH arguably needs such block reorganization prevention measures more than Bitcoin, where the computing power needed to attempt such an attack would be prohibitively expensive.
Updated: 6-1-2020
Hacker Steals Database of the Largest Hosting Provider on the Dark Web
Sensitive data from darknet websites hosted in Daniel’s Hosting have been leaked by a hacker who claims ties to Anonymous.
Reports emerged on May 31 about a hacker that stole and leaked the database of Daniel’s Hosting (DH), the largest free web hosting provider in the darknet, and the home of several crypto-related forums and stores.
The hacker —under the pseudonym “KingNull”— also claims to be part of the Anonymous collective and reportedly got the information after the second hacking suffered by DH on March 10, which resulted in 7,600 dark websites taken down.
The fact forced the hosting provider to shut down its service and urged the users to migrate their sites to new ones on the dark web.
Leaked Info Could Help To Trace The ID Of People Running Illegal Darknet Sites
According to reports, the leaked data includes 3,671 email addresses, 7,205 passwords, and 8,850 private keys of the domains attached to the dark web sites.
Threat intelligence firm, Under the Beach, confirmed this finding to ZDNet and commented on the following:
“This information could substantially help law enforcement track the individuals running or taking part in illegal activities on these darknet sites.”
DH warned its affected users that they should immediately change the password that the hacker leaked, as they could be used to hijack new accounts that site owners create with other providers.
Although DH is reportedly the home of illegal cybercrime-related sites, it also hosts many owners of dissident and political sites, who could have their identity revealed to the authorities, according to the hosting provider.
Hacker’s Alleged Ties With Anonymous
The report clarifies that the suspected hacker did not steal the IP addresses. For now, Daniel Winzen, head of DH, said there is no set date for relaunching the service.
The fact that the hacker is allegedly related to Anonymous would not be a surprise. The collective launched an anti-child pornography “Operation Darknet” against Freedom Hosting in 2013, which was the largest Tor web hosting at that time.
Recent figures unveiled by Crystal Blockchain Analytics showed that the total USD value of Bitcoin (BTC) transferred on the dark web rose by 65% in Q1 2020, drawing authorities’ attention to illicit transactions through the darknet.
Updated: 6-2-2020
$1.4B in Crypto Stolen In First Five Months of 2020, Says CipherTrace
Researchers say 2020 is on track to become a record-breaking year for cryptocurrency-related thefts, hacks and fraud.
Digital asset intelligence firm CipherTrace released a report on Tuesday revealing that in the first five months of this year so far, the value of ill-gotten funds siphoned through cryptocurrency crimes has reached almost $1.4 billion.
This makes it possible that the amount of funds lost to bad actors in 2020 will outstrip the $4.5 billion lost in 2019, which CipherTrace then attributed to an uptick of “insider jobs” at businesses such as crypto exchanges.
This year, CipherTrace notes that criminals are capitalizing on the coronavirus crisis to target more victims and are propagating new crypto-related phishing campaigns, ransomware and darknet marketplace fraud.
The COVID-19 Crypto Crime Scene In 2020
CipherTrace has identified multiple scams this year involving email campaigns that impersonate coronavirus-related official groups in order to solicit personal information and/or payments in cryptocurrency.
Mimicked entities have included the World Health Organization, the Red Cross and the Centers for Disease Control and Prevention.
Other COVID-19-related applications and sites include purported virus trackers for smartphones, which enable criminals to spy on users or to install ransomware and later demand payment in cryptocurrency to decrypt users’ files.
New darknet markets have also emerged requesting payment in crypto for COVID-19 diagnostic tests, ostensible vaccines and “cures,” or sought-after personal protective equipment.
Of the $1.36 billion in crypto stolen so far this year, 98% of the total value ($1.3 billion) was accounted for by fraud and misappropriation, rather than by hacks and direct thefts.
Money Laundering Risks Remain
CipherTrace notes that evolving Anti-Money Laundering measures have proved reasonably effective, causing the global average of illicit funds received by exchanges to drop by 47% in 2019.
Challenges remain, however, with “regulatory arbitrage” — i.e., high-risk crypto firms relocating to less regulated jurisdictions. This, the report claims, is still prevalent ahead of the forthcoming enforcement of the Financial Action Task Force’s travel rule in June.
CipherTrace indicates that 74% of the Bitcoin (BTC) moved in exchange-to-exchange transactions was cross-border, a fact that points to the urgency of establishing global AML and counterterrorism standards such as those set out by the FATF.
The report further points to the amplifying effect of the global public health and economic crisis, noting that “in the rush to institute government programs, there will inevitably be corruption and misallocated funds, creating a ripe environment for money laundering.”
Looking Ahead
Another striking finding in the report involves the “exponential” rise of funds being sent to high-risk exchanges from United States Bitcoin ATMs in 2019 rather than to lower-risk entities, prompting CipherTrace to predict that ATMs could be the next target for financial regulators.
Updated: 6-7-2020
Crypto Crime On The Rise — Good Odds Of 2020 Becoming A Record-Breaker
Experts believe that a more holistic crypto ecosystem, especially one that is more AML-centric, is needed to help prevent the spread of crypto scams in 2020.
Per a new report released by digital-asset intelligence firm CipherTrace on June 2, the value of ill-gotten funds siphoned through cryptocurrency crimes over the first five months of the year stands at a whopping $1.4 billion, thus making 2020 a potentially active year in regard to cryptocurrency-related thefts, hacks and fraud.
The report goes on to state that if things continue at the same rate, the total volume of stolen crypto for 2020 has the potential to get close to reaching the $4.5-billion mark set in 2019. Criminals appear to be capitalizing on the ongoing COVID-19 pandemic to target unsuspecting individuals by luring them in via a variety of crypto-related phishing campaigns, ransomware and darknet marketplace fraud.
Additionally, out of the multiple scams that have been accounted for this year, many of them have reportedly made use of email campaigns impersonating various coronavirus-related official groups — such as the World Health Organization, the Red Cross and the Centers for Disease Control and Prevention — to solicit payments and donations in the form of cryptocurrency.
Lastly, CipherTrace officials claim that of the $1.36 billion in crypto stolen so far this year, 98% of the total value — nearly $1.3 billion — can be attributed to fraud and misappropriation rather than to hacks and direct thefts.
Scammers Have Continued To Evolve Their Methodologies
To gain a better understanding of where the market seems to be heading in the coming months and years, particularly when it comes to crypto crime, Cointelegraph spoke to John Jefferies, the chief marketing officer and chief financial analyst at CipherTrace.
In his view, while it is nearly impossible to predict with any certainty how trends related to cryptocurrency theft and fraud will evolve this year, it is possible that by the time the year comes to a close, the amount of funds netted by criminals may exceed the expectations of the report, betting 2019’s $4.5 billion figure.
Further elaborating on the subject, Jefferies stated that the largest contributor to this year’s crypto crime total has been Wotoken’s alleged billion-dollar Ponzi scheme that emerged from China. Furthermore, he is concerned in the coming months about exit scams by smaller virtual asset service providers, or VASPs, that that are struggling financially, adding:
“Retail investors should be wary of any company that uses hyperbolic statements and promises of extraordinary returns to lure them into participating. If WoToken had been required by regulatory agencies to provide detailed investment prospectus and audited financial statements, they wouldn’t have been able to launch their scheme and fool more than 700,000 victims. Many VASPs have dramatically improved their security posture, making it harder for hackers to steal from the platforms themselves.”
An even bleaker picture was painted by Pawel Aleksander, the co-founder and chief information officer of CoinFirm — a blockchain analytics company. He told Cointelegraph that as per his company’s own research and analysis, the volume of crypto funds stolen within the first quarter of 2020 may actually be closer to the $2 billion mark, highlighting:
“Knowing the amounts related to the various fraud happening as a whole has its importance but the most important aspect is addressing how to solve them and providing entities with the tools and solutions to do so.”
The Pandemic Has Made Things Worse
As a result of the ongoing coronavirus situation, an increasing number of people have started to spend more time in front of their computer and smartphone screens. Naturally, scammers have recognized this fact and are trying to seize this opportunity by devising novel ploys — promising high returns on various crypto-related offerings such as binary options, trust trading, etc. — to lure in unsuspecting individuals.
Commenting on the issue of how companies can best limit the spread of crypto-related scams, Aleksander stated that despite most social media platforms and messengers attempting to come down more seriously and limit such nefarious schemes, there are still many challenges that have yet to be tackled successfully. In his view, a balanced ecosystem is required, in which Anti-Money Laundering procedures can be democratized and users are given a voice:
“This can happen by achieving a synergy between AML, fraud investigations and an open data ecosystem that takes the security of crypto financial markets to a level never seen before or even thought possible in traditional finance.”
In this regard, he believes that a threefold solution is needed — i.e., one that is based on an AML technological platform that enables institutions to verify the risk of blockchain transaction counterparties and meet their regulatory obligations.
Not only that, but the platform should also have the capability to facilitate end-to-end investigations in cases where funds are reported missing as well as incentivize the reporting of suspicious activities. Aleksander closed out by saying: “If the industry collectively adopts such solutions and processes, the capability of such scams of not only being successful but being able to take advantage of the stolen funds will become severely limited.”
A similar point of view is shared by Jefferies, who also believes that banks, VASPs and other money service businesses can safeguard themselves against bad actors that are utilizing their platforms and payment networks to launder money as well as engage in other illegal activities by deploying effective AML measures.
How Do Bitcoin ATMs Fit Into All Of This?
A striking aspect of CipherTrace’s above-mentioned report involves the “exponential” rise of funds being sent to high-risk exchanges from United States-based Bitcoin ATMs rather than lower-risk entities such as established crypto exchanges. This has prompted experts to believe that BATMs may be at a greater risk of being used to launder money, especially given the preponderance of funds sent from them overseas, potentially to jurisdictions with lax AML and Know Your Customer policies.
Providing his insights on the matter, Jefferies stated that part of the reason for the increasing use of BATMs by money launderers, such as in the Kunal Kalra case, is their increasing ubiquity across the U.S. He added:
“Even in spite of the growing availability of privacy coins like Monero and Zcash, criminals continue to use Bitcoin because of the abundance of Bitcoin-to-fiat offramps. Banks and money service businesses should pay attention to high-risk transactions originating from BATMs that lack proper AML compliance.”
Bitcoin Cleaner Than Fiat?
Even though the crypto sector is still routinely maligned by members of the mainstream media that claim that digital currencies are still, by and large, being used by bad actors for nefarious reasons — such as terrorist financing, drug trade, etc. — Jefferies told Cointelegraph that as per his company’s latest research, cryptocurrencies are considerably cleaner than their reputation would suggest:
“The reality is that criminal use of Bitcoin and other cryptocurrencies is very low, less than 0.2% of the funds accepted by exchanges is directly from criminal sources.”
Updated: 6-8-2020
Law Enforcement Is Starting to Make Criminals Doubt the Dark Web
Trend Micro reveals dwindling confidence among darknet users in marketplaces due to security concerns.
A new study revealed that the dark web marketplace users are starting to lose trust due to the authorities’ crackdown and “current volatility” within the landscape, which results in instability for the darknet sites to establish a fixed presence.
According to cybersecurity company Trend Micro on June 7, crackdowns on marketplaces Dream Market, Wall Street Market, Valhalla and DeepDotweb have generated uncertainty among users regarding the unstable security infrastructure that dark web sites have been providing.
Fears Of “Exit Scams”
The report detailed that after March 2019, when law enforcement shut down darknet sites, sales activity experienced a considerable slowdown.
Doubts began to increase among users about their anonymity when making transactions as well as a surge in exit scams — sites that shut down suddenly and steal money from the customers — and undercover actions by the authorities within the marketplaces.
Lack of confidence in the darknet marketplaces led to the creation of a site called DarkNet Trust, which was created to verify vendors’ reputations by searching through usernames and PGP fingerprints.
Darknet Marketplaces Shifting To Additional Security Measures
Administrators of dark web marketplaces were also forced to add new security features like walletless markets, multi signatures on Bitcoin (BTC), and Monero (XMR) and no-javascript policies.
Trend Micro explains that a walletless market is a method where payment is directly made between the buyer to the vendor, with the marketplace getting a monthly commission as opposed to transaction fees.
The report also notes that new encrypted email services like Sonar and Elude “suddenly” emerged, as users accused Protonmail of helping law enforcement.
Recent months have, consequently, seen increased all-around user skepticism.
Cointelegraph reported on May 31 that a hacker stole and leaked the database of Daniel’s Hosting (DH), the largest free web hosting provider on the darknet and the home of several crypto-related forums and stores.
Updated: 6-10-2020
Bitcoin Options Open Interest Rises 50% In A Month To Hit $1.5 Billion
Just over a month since open interest in Bitcoin options hit a record high of $1 billion, the latest figures show that it has increased 50% to break $1.5 billion.
According to the latest data from market analysis company Skew, total open interest in Bitcoin (BTC) options passed $1.5 billion on June 9. This comes barely a month after open interest crossed $1 billion for the first time, marking a 50% increase in just 33 days.
50% Rise In A Month Led By Two Players
Total Bitcoin options open interest hit $1 billion for the first time ever on May 7. Just over a month later, Deribit alone has open interest of $1.1 billion, and the total open interest has broken through $1.5 billion.
Deribit’s 20% increase from $903 million over the course of the month has not been the biggest story though.
Chicago Mercantile Exchange (CME) has increased its Bitcoin options open interest by over 850% in this time. On May 7 this stood at $38 million, but by June 9 CME recorded $368 million of open interest.
CME Aiming For The Options Crown?
As Cointelegraph reported, in the first half of May alone, open interest on CME Bitcoin options soared a massive 1,000% from $12 million to $142 million.
While unable to sustain quite that level of growth, the latest figures show that CME’s options momentum is far from running out of steam.
Of the other major players in the BTC options market, LedgerX open interest remained roughly the same since May 7 at $52 million while OKEx saw a 15% fall to $65 million.
An outlier in the field, Bakkt also saw a fall in open interest, from $80,000 to $68,000.
Despite this, the performance of both Deribit and CME shows that Bitcoin options is a rapidly growing market sector.
Updated: 6-11-2020
Deceased Quadriga Founder Committed Fraud
The Ontario Securities Commission says that the Vancouver-based crypto exchange was a fraud.
The Ontario Securities Commission, or OSC, claims that the crypto exchange Quadriga collapsed in 2018 because of fraud committed by its late founder, Gerald Cotten, who passed away on his honeymoon in India.
The report released on June 11, revealed by CBC Canada, says Cotten opened several accounts under aliases and credited himself with “fictitious currency,”. He traded this currency with unsuspecting clients of his Vancouver-based crypto exchange.
The deceased Quadriga founder was unable to meet his client’s withdrawal requests when the price of crypto assets fell. He then created a Ponzi scheme, covering the demand using funds from other Quadriga clients.
As detailed by the OSC, the organization attributed about $115 million of the $169 million clients lost to Cotten’s fraudulent trading, which helped him finance his millionaire lifestyle.
Due to Cotten’s death, the OSC says it will not seek to bring legal action against Quadriga, as “it’s not practical.”
Updated: 6-11-2020
Japanese Judge Upholds Charges Against Mt Gox’s Mark Karpeles
A Japanese judge ruled in support of the data tampering charges moved against the CEO of now-defunct crypto exchange Mt. Gox.
A Japanese judge ruled in support of data tampering charges moved against Mark Karpeles — the CEO of now-defunct crypto exchange, Mt. Gox.
At the end of March, Karpeles appealed his conviction on charges of having tampered with financial record data to harm his clients. Now, local news outlet Nikkei reported on June 11 that Tokyo District Court Judge Mariko Goto decided to uphold the previous ruling.
Karpeles Sentenced To Over 2 Years In Jail
The previous ruling sentenced Karpeles to two and a half years in jail for tampering with Mt. Gox data for February-September 2013 and depositing $33.5 million into his account. He will not have to serve this sentence unless he commits another offense within four years.
Karpeles claimed that increasing his account’s balance was not a crime. The Judge, on the other hand, ruled that this action violated the terms and conditions of the firm and added that the account balance was doctored in order to conceal fake Bitcoin (BTC) by the firm.
Mt. Gox was once the largest and most successful cryptocurrency exchange in the world. At the time of its closure, it was the biggest cryptocurrency exchange to disappear following a hack. In February 2014, the firm stated that almost 750,000 of its customers’ Bitcoins, as well as 100,000 of the firm’s own Bitcoins were stolen.
Updated: 6-11-2020
500 Estonian Crypto Companies Lose Permits After $220B Scandal
Estonia is withdrawing permits from hundreds of crypto companies following Europe’s biggest money laundering scandal.
Estonia, one of the European Union’s most crypto-friendly countries, is cracking down on hundreds of licensed crypto companies in response to a $220 billion money laundering scandal, according to Bloomberg.
Estonia was among the first EU countries to license crypto companies but has been forced to clamp down after hundreds of billions of dollars of dirty money was detected in the Estonian unit of Denmark’s largest lender Danske Bank A/S. It’s put the country at the center of Europe’s biggest money laundering scandal.
License To Ill
Madis Reimand, Head of the Baltic country’s Financial Intelligence Unit revealed that regulators suspect that licensed crypto firms are abusing their Estonian credentials to commit fraud elsewhere.
Hence, more than 500 companies — about a third of the total — which had failed to start operations in Estonia within six months of being licensed, have seen their permits withdrawn. He explained that:
“This is a first step in tidying up the market, allowing us to take care of the most urgent issues by permitting operations only for companies that can be subjected to Estonian supervision and coercive measures.”
The Purge Isn’t Over
Reimand indicated that more strict licensing measures will come. More than a half of the country’s remaining crypto companies may also lose their licenses as they too have no operations in Estonia and their managers are outside the country.
Updated: 6-12-2020
15 People Plead Guilty In Bitcoin-Powered Fake Auctions Case
The U.S. Department of Justice received two more guilty pleas from Romanian nationals involved in a crypto-fuelled transnational cyber fraud ring on June 11.
Fifteen people have pleaded guilty to involvement in an international syndicate that used fraudulent online auctions to dupe victims out of Bitcoin (BTC) according to the United States Department of Justice (DoJ).
From at least December 2013, the syndicate used listings for non-existent goods on auction and sales websites to defraud victims, with the group laundering the funds through a Romanian crypto exchange Coinflux in recent years.
According to the DoJ’s announcement, four of the guilty pleas were made by Romanian nationals in the past 24 days before U.S. Magistrate Judge Matthew A. Stinnett, with two taking place in the last 24 hours.
International Cyber Fraud Ring Busted
On June 11, 30-year-old Bogdan-Stefan Popescu and 34-year-old Liviu-Sorin Nedelcu entered guilty pleas for one count of RICO conspiracy each.
The complaint states that Nedelcu collaborated with other fraudsters to post advertisements on auction websites for goods that did not exist, most commonly vehicles. “Upon receiving payment, Nedelcu and his co-conspirators engaged in a sophisticated money laundering scheme to convert the victim payment into Bitcoin,” said the DoJ.
The DoJ asserts that Popescu oversaw “an operation whereby he knowingly negotiated fraudulently obtained Bitcoin” through online fraud, in addition to providing money laundering services and distributing tools used to defraud U.S.-based victims.
Romanian Exchange Coinflux Laundered Funds
The funds generated by the syndicate were laundered through the Romanian cryptocurrency exchange Coinflux.
33-year-old Vlad-Călin Nistor, the founder and operator Coinflux, pleaded guilty to one count of RICO conspiracy on May 19. Nistor would convert the criminals’ crypto assets into local fiat currency on behalf of Romanian-members of the group.“
The DoJ asserts that Nistor laundered the funds despite “knowing that the Bitcoin represented the proceeds of illegal activity,” with plea documents noting that Nistor exchanged over $1.8 million worth of Bitcoin for Popescu.
30-year-old Beniamin-Filip Ologeanu also pleaded guilty to RICO conspiracy on May 19, having worked in conjunction with the syndicate to post fraudulent ads on auction and sales websites. Olegeanu also purchased the fraudulent proceeds from his co-conspirators in the form of prepaid debit cards to be laundered in the United States.
“Through the use of digital currencies and trans-border organizational strategies, this criminal syndicate believed they were beyond the reach of law enforcement,” said U.S. Secret Service assistant director Michael D’Ambrosio.
“However, as this successful investigation clearly illustrates, with sustained, international cooperation, we can effectively hold cyber criminals accountable for their actions, no matter where they reside.”
Coinflux Founder Arrested In 2018
In December 2018, Romanian media reported that Nistor had been arrested in Romania at the behest of U.S-based prosecutors for alleged money laundering and fraudulent activity. Less than one month later, it was announced that Nistor would be extradited to the United States.
Updated: 6-12-2020
South Korean Police On The Hunt For Ethereum Crime Ring Masterminds
The Seoul Metropolitan Police seize two unnamed local crypto exchanges in an effort to dismantle an ETH-related crime ring.
The Seoul Metropolitan Police Agency launched a criminal investigation on June 12, leading to the search and seizure of two unnamed cryptocurrency exchanges. These efforts were enacted with the hope of dismantling an Ethereum (ETH) crime ring worth $41.5M.
According to Joongang Ilbo, the alleged crime network promoted its business model as a multi-level marketing scheme, or MLM. More than 1,500 people are believed to have sent their crypto assets to the scammers.
“Huge Returns” Promised With ETH Investments
Reports indicate that the company’s CEO, identified by the name “Mr. Shin,” was investigated and received a court order prohibiting him from leaving the country while authorities conduct their investigation. Police indicate Mr. Shin is one of at least 100 individuals being watched by authorities.
Another suspect, known as “Mr. A,” is also being monitored. As an executive of one of the exchanges, he allegedly promised “huge returns” for ETH investments.
Number Of Victims May Exceed 1,500
As of press time, 433 investors have filed complaints with the police, alleging that they were unable to withdraw their funds from the scheme. Attorneys speaking on behalf of the victims have said that there could be 1,000 more individuals who have yet to approach the police.
Cointelegraph reported on June 2 that the value of ill-gotten funds siphoned through cryptocurrency crimes over the first five months of the year stands at a whopping $1.4 billion.
Updated: 6-12-2020
Examining the Status of Stablecoin Minting and Burning Activities
We selectively analyzed six stablecoins — USDT, GUSD, HUSD, PAX, TUSD and USDC — to uncover their minting and burning activities so far in 2020.
As of June 4, six stablecoins — Tether (USDT), Gemini Dollar (GUSD), HUSD (HUSD), PAX Gold (PAXG), TrueUSD (TUSD) and USD Coin (USDC) — have had a total of more than 10,000 minting transactions so far in 2020, totaling $8 billion, with USDT issued on the Ethereum blockchain dominating the stablecoin landscape. The major stablecoin began to explode in early March and drove the market cap of the entire stablecoin market higher. By the end of the April, it was ranked third in size behind Bitcoin (BTC) and Ether (ETH). Its current market capitalization accounts for about 85% of the total stablecoin market capitalization.
During the most volatile session, in March 2020, the number of minting and burning activities was at a peak, and the dollar value of newly issued tokens also reached its highest point.
In terms of burning activities, there have been nearly 5,600 burning events reported so far in 2020, with the total value of destruction exceeding $3 billion.
We looked at the quarterly stablecoin minting and burning records from early 2017. The dollar value of burning and minting in the third quarter of 2019 was at a historical high, and the volume of burning and minting activities reached a historical high in the first quarter of 2020.
Based on the data, we believe that if the trend continues, the number of minting and burning activities for Q2 2020 will be at least equal to the number in Q1 2020.
Stablecoins Minting And Burning Historical Record
Significant Differences In The Number Of Minting Activities
The following figure shows the number of minting activities and the dollar value of stablecoins minted in the first five months of 2020.
Total Value Of Stablecoins Minted And Minting Transaction Volume
Among the stablecoins shown, HUSD initiated 5,280 minting transactions, increasing the overall market value by about $101 million, with an average of $200,000 per minting transaction. USDT only initiated 74 minting transactions, but the overall market value increased by approximately $5.5 billion as a result, with an average of $74 million per minting transaction — 370 times the average value of HUSD minting per transaction.
We also looked at data around stablecoin minting in dollar value and transaction activities. Minting activity reached its peak in March, which was also the month with the largest dollar value minted so far in 2020.
In addition, We found that the dollar value of different stablecoins being minted varies. As shown in the figure below, there are significant differences in the number of minting activities for different stablecoins.
Up to the $10 million range, there are 1,800 minting activities per month on average in 2020 so far, while for larger values, there are less than 30 minting activities on average per month.
HUSD is the most frequently issued stablecoin in the $10 million section, followed by TUSD.
USDT is vastly different from the other five stablecoins and is the one that has minted more than $40 million in a single transaction, these transactions have also mostly concentrated in the $40 million bucket with a total of more than 56 minting transactions so far in 2020. There were only six minting transactions in total in the $10 million to $40 million bucket.
Stablecoin Burning Transactions Rarely Occur In Significant Value And Is Mostly Concentrated Within The $10 Million Range
The data on the number of burning transactions and the total dollar value of destruction of each stablecoin are shown in the following figure. HUSD ranks first in the number of burning transactions and the dollar value of destruction. In addition, although USDT has the least number of burning transactions, the value of destruction ranks second.
In addition, we have observed that if we exclude the USDT data, the frequency and dollar value of stablecoin destruction per month are relatively average, around 1,000 times and $500 million, respectively.
USDT destruction is characterized by a lower frequency of burning transactions but each being high in value. The value of USDT destruction reached 50% of the total burn value during February 2020.
The destruction events are concentrated in the $10 million range and was rarely of high value. Only USDT and USDC made the cut to being greater than or equal to the $40 million bucket per burning transaction.
It is worth noting that burning activities in March only capped at $10 million per transaction, with the highest number of burning transactions occurring so far in 2020.
The rise of stablecoins is inevitable. The sector creates endless possibilities in this volatile parallel financial universe. They are not only bringing liquidity to the ecosystem but also driving significant innovations and creating many other use cases to drive the cryptocurrency industry further. However, the industry has much to address, such as the risks and issues in the stablecoin sector. It is without a doubt that the crypto industry will see continued strong growth of the stablecoin sector, thereby driving meaningful adoption.
Updated: 6-12-2020
Karpeles Says Mt Gox Verdict May Set ‘Dangerous’ Precedent
A day after a Tokyo court upheld charges against him, Mark Karpeles, the former owner and CEO of Mt. Gox, spoke to Cointelegraph.
A day after a Tokyo court upheld charges against him, Mark Karpeles, the former owner and CEO of the now-defunct exchange Mt. Gox, spoke to Cointelegraph regarding the verdict.
On June 11, Tokyo District Court Judge Mariko Goto struck down Karpeles’ appeal to a previous charge of tampering with financial data. Karpeles was first convicted in March 2019 and received a two-and-a-half year jail sentence. He began the appeals process that same month. The former CEO will have to serve time should he commit another offense within four years.
Speaking to Cointelegraph, Karpeles said he hadn’t decided whether to appeal again and was currently consulting with his legal counsel on how to proceed:
“The verdict, in this case, relies on the concept brought by the prosecution that the company has its own ‘will’ that can differ from management’s and/or shareholders’. I believe this can be dangerous as it means when a company fails management can be later prosecuted for taking actions that go against what the prosecution decided was the company’s will at a given time.”
On June 11, Judge Goto explained the reason for the charge as “an action that goes against terms of services which the company indicated as its own will.”
Tokyo-based Mt. Gox was the biggest exchange in the world where nearly 70% of all BItcoin (BTC) transactions were conducted at one point. In February 2014, the company lost track of almost 750,000 BTC belonging to the customers and 100,000 BTC of its own.
Mt. Gox entered bankruptcy proceedings in 2014 but has since undergone civil rehabilitation processes to enable it to pay back creditors.
The rehabilitation plan is set to be submitted by July 1.
Updated: 6-13-2020
Five Wanted For Indian Crypto Scam Operating Since 2017
Five individuals have been identified by Indian police as likely involved with a crypto investment scam that has operated since 2017.
Indian police have registered a case against five individuals suspected of involvement in a cryptocurrency scam that has defrauded investors since 2017.
Despite operating for several years, the scammers are only believed to have made away with a modest bounty of roughly $34,200.
The group is believed to have solely operated in the Maharashtra state’s district of Palghar.
Indian Police Target Multi-Year Scam
On June 13, media outlet New Indian Express reported that five people had been booked for allegedly defrauding investors under the guise of cryptocurrency investment.
The group promised exorbitant returns to those who invested in crypto assets from them, soliciting payments in the form of cash and cheques. However, after the funds were received, the scammers became increasingly evasive in their interactions with investors, local police said.
None of the accused fraudsters have been arrested so far.
Last month, the case concerning Amrit Bhardwaj and Vivek Bhardwaj — two brothers who operated India’s notorious multi-level marketing crypto scam GainBitcoin — was transferred from the Cyber Cell to local police’s Crime Branch.
India Ramps Up Darknet Crackdown
Indian police have recently expanded efforts to crack down on darknet crime, recently announcing plans to build an AI-powered web portal for deep web policing, and teaming up with international regulators to bust anonymous free market vendors peddling unlicensed pharmaceuticals or narcotics.
Perceptions that crypto assets may comprise a tool for illicit activities could prove highly damaging for India’s digital asset sector, with the Indian Ministry of Finance proposing a new ban on cryptocurrencies on June 12 — only three months after the Supreme Court’s ruling that lifted the country’s prohibition on banks providing financial services to firms operating with crypto.
Updated: 6-15-2020
Fraudulent Site Impersonates Encrypted Messaging Service To Steal Bitcoins
A new Bitcoin-related scam emerged through a phishing site that impersonates a self-destructing encrypted notes service.
Cybercriminals have reportedly created a fake site version of the legitimate encrypted self-destructing notes service privnote.com. The fake version can be shared with other users to steal Bitcoin.
According to a June 14 report from KrebsOnSecurity, the creators of the encrypted notes service complained about a fake clone site, privnotes.com, whose scam scheme consists of the following:
“Any messages containing Bitcoin addresses will be automatically altered to include a different Bitcoin address, as long as the Internet addresses of the sender and receiver of the message are not the same.”
Privnote.com said in the report that the phishing site does not apply encryption systems. Instead, the cybercriminals can read and/or modify all messages sent by users, in addition to using an automated script that scours messages for Bitcoin (BTC) addresses, and replaces them with scammers’ wallet address.
A ”Smart” Scam
On the fake site, Allison Nixon, chief research officer at cybersecurity firm Unit 221B, said the scam is “pretty smart,” explaining:
“Because of the design of the site, the sender won’t be able to view the message because it self destructs after one open, and the type of people using privnote aren’t the type of people who are going to send that bitcoin wallet any other way for verification purposes.”
One of the factors that alert the company is the fact that because both URLs are similar, when doing a Google search with the term “privnotes,” the user will see the first shot of a Google’s paid aid, which is the phishing site. The second result is the legit website.
Recent Bitcoin-Related Scams
In May, Harry Denley, a crypto-security researcher, discovered almost 22 Google Chrome web browser extensions built to steal their users’ cryptocurrencies. The extensions he found impersonated well-known crypto firms such as Ledger, KeepKey, MetaMask, and Jaxx.
Cointelegraph reached out to privnote.com but received no reply as of press time. This article will be updated should a response come in.
Updated: 6-16-2020
SIM Swap Hackers Target Crypto Investors — Cell Services Not Available
Civil lawsuits against telecom providers such as AT&T are becoming commonplace as the number of SIM swap hacking scandals rises.
On June 11, it came to light that California resident Richard Yuan Li had been charged with conspiracy to commit wire fraud for his role in a number of SIM swap attacks that targeted at least 20 individuals. Not only that, but as part of his elaborate money swindling scheme he also attempted to extort 100 Bitcoin (BTC) from an unknown physician in exchange for keeping their private, sensitive information from being released online.
According to numerous reports, Li’s nefarious deeds can be traced all the way back to 2018 — and lasting until around mid-2019 — when he along with a group of co-conspirators tried to defraud many unsuspecting individuals of their hard-earned savings using SIM swap attacks. In this regard, a SIM swapping involves the rerouting of a person’s SIM card to a phone that is in possession of a hacker, thus allowing them to gain access to an individual’s personal information such as emails, bank account details, cryptocurrency wallet, etc.
Furthermore, over the course of the past few years, SIM swap attacks have seen a dramatic spike. For example, back in May 2018, crypto investor Michael Terpin fell victim to a $23.8 million SIM swap attack that was perpetrated by 18-year-old Ellis Pinsky of Irvington, New York. Similarly, investor and two-time Emmy award winner Seth Shapiro filed a lawsuit against American telecom giant AT&T, alleging that the firm’s employees had masterminded a nefarious SIM swap scheme that resulted in him losing $1.8 million in various crypto assets.
Sim Swapping Due To Poor ID Verification Protocols?
SIM swapping has become a significant threat for users of major networks in the United States, especially as more and more individuals are starting to rely on their mobile devices to work remotely. In this regard, a large number of Americans are having their lifetime savings and invaluable data stolen from under their eyes solely because mobile operators are seemingly failing to take reasonable steps to prevent their employees from repeatedly conspiring with criminal hackers.
In this regard, John Pierce, a trial lawyer and the global managing partner of Pierce Bainbridge, told Cointelegraph that while criminal prosecutions are starting to take place, accountability in civil cases is absolutely crucial to deter this kind of misconduct. Not only that, he also believes that a major reform in data security practices is needed from the side of most cellphone service providers.
To gain a more in-depth understanding of why SIM-swap-related incidents have been increasing sharply over the past three to four years, Cointelegraph reached out to Mark Grabowski, an associate professor of cyberlaw at Adelphi University as well as a regular columnist for the Washington Examiner. In his view, the reason is that people are now using their smartphones to facilitate their everyday digital activities rather than personal computers, which are considerably more secure. He added:
“In addition to infecting smartphones with malware, criminals are illegally spoofing users’ phone numbers (faking the number that an incoming call is from), porting their numbers (moving the number from a user’s phone to another phone controlled by the criminal) and even cloning SIM cards, the computer chips that identify a phone, to access users’ data and steal money.”
While the federal Wireless Telephone Protection Act of 1998 protects customers from their personal data being shared with third-party sources, Grabowski opined that the lax ID verification protocols that are being used by most cell phone carriers these days make customers vulnerable to a variety of different hack attempts.
Earlier this year, several members of Congress sent a letter to the Federal Communications Commission urging it to mandate that wireless carriers provide stronger protections for customers to truly lock down their accounts, such as requiring an in-person visit to a store before a phone number can be ported to another device or carrier.
Cell Phone Providers Should Step Up?
Cybersecurity is an ever-evolving domain wherein attackers continually seek to modify their gameplans in order to keep up with the latest trends. For example, hackers at one point were using SMS messages to gain access to people’s cell phones by attacking the Signaling System No. 7, or SS7, communications protocol. Now, hackers have become more sophisticated in their ways and have learned how to crack passwords using a variety of different means. As a result, many companies have responded by adding two-factor authentication protocols to bolster their security.
Talking about how easy it is for miscreants to carry out a SIM swap attack, Mark Herschberg, an instructor at the Massachusetts Institute of Technology as well as chief technology officer of cybersecurity company Averon, told Cointelegraph that while initiating such an attack is certainly not easy, if the wallet has enough value in it then it’s worth it for the hackers, adding: “Attackers are very efficient in finding the optimal effort to reward approaches.”
Additionally, talking about ways in which this rising issue can be combated successfully, Herschberg pointed out that there are newer technologies that allow for silent 2FA authentication to take place with no action on the part of the user. In his view, this method is more secure and can help detect SIM swaps more efficiently — thus allowing a transaction to be flagged by a network operator if one’s SIM has been changed recently.
Battle With AT&T Rages On
In perhaps one of the most widely covered SIM swap court cases, a U.S. district judge released an order on May 20 rejecting AT&T’s bid to dismiss Shapiro’s lawsuit in which he claims that the company acted in an extremely negligent manner and failed to prevent miscreants from making their way with $1.8 million worth of crypto. In a conversation with Cointelegraph, Shapiro stated:
“We’re not simply alleging that AT&T employees were involved in my theft: they were named in an indictment by the Department of Justice, from a case built by the Department of Homeland Security (US v Freeman). So the federal government has already proven that AT&T employees are stealing from its customers.”
Furthermore, it is worth mentioning that in the past, AT&T has been handed a number of major defeats in cases quite similar to Shapiro’s. Back in 2018, for example, California resident Robert Ross lost $1 million worth of crypto after a hacker was able to gain control of his AT&T phone. Similarly, North Carolina resident Jason Williams was also at the receiving end of a major SIM swap attack in which he lost a bulk of his crypto savings.
Elaborating on how network operators have been trying to deflect responsibility when it comes to such SIM swap incidents, Shapiro added that for years, big-name players such as AT&T have allowed its employees to destroy the lives of its customers — subjecting them to theft, extortion and other major crimes — instead of taking action to solve such problems: “The Department of Justice indicted two AT&T employees in my case. In that month alone, one of those AT&T employees committed 29 illegal SIM swaps; the other committed at least 12 and AT&T did nothing to stop them.”
Commenting on the subject, Pierce said that AT&T has sought to focus the blame on the hackers that collaborated with AT&T employees to carry out attacks and downplay the relationship between the control of a victim’s cellphone number and the ability to gain access to the victim’s accounts through two-factor authentication:
“AT&T’s motion to dismiss Mr. Shapiro’s lawsuit argued that Mr. Shapiro’s allegations did not meet various technical legal requirements to establish legally cognizable claims against it — most of which the court resolutely rejected. Mr. Shapiro’s court now joins a growing chorus of other federal courts that have allowed civil lawsuits by SIM swap victims to proceed against AT&T.”
Making The Call
While some suggest that this recent increase in SIM swapping incidents could be directly linked with the desire of the masses to adopt cryptocurrencies, it appears as though there is not enough evidence available to support this correlation. For example, as with ransomware attacks, SIM swapping simply provides hackers with another avenue to strike a large payday.
However, what should be understood is that in order to prevent SIM swap attacks from becoming commonplace, cellphone users need to become more technically savvy and adopt privacy protocols such as “offline two-factor codes” that can allow users to perform verification checks without them having to rely on their cell phone carrier. An even better alternative could be making use of a physical security key, which would make it nearly impossible for miscreants to gain access to an individual’s personal data.
Updated: 6-16-2020
Cybercrime Up 75% During COVID-19, Congressional Hearing Details
A recent U.S. government hearing showed a significant uptick in online crime since COVID-19 took over in 2020.
Giving the opening remarks during a U.S. House meeting on illegal digital activities, Representative and subcommittee chair Emanuel Cleaver (D-MO) noted a major jump for online crime in 2020.
“We are seeing a 75% spike in daily cybercrimes, reported by the FBI since the start of the pandemic,” Cleavor said in his opening statements of the June 16 virtual hearing before the Subcommittee on National Security, International Development, and Monetary Policy.
Speaker Dials Into Specific Attacks And Sectors
After COVID-19 prevention measures caused business closures and shelter-in-place orders in mid-March, many companies looked to remote work. As droves of people increased their web activity, hackers saw more opportunities. Amid newfound need for online meetings, for example, popular video meeting platform Zoom suffered widespread data leaks.
Called on for comment as a witness in the meeting, VMware’s head of cybersecurity strategy, Tom Kellermann, singled out the finance industry, noting a 238% uptick in related digital crime between January and May 2020. “This is compounded by the 900% increase in ransomware attacks,” he added.
Kellermann Mentions A Crypto Connection
After noting a number of ways nefarious parties have preyed on victims, Kellerman mentioned an uptick in crypto exchange hacks and leaks. He also explained that parties use these venues as a means of laundering money, in tandem with the dark web and anonymous digital assets.
“Dark web forums enabled by anonymous virtual currencies have created a bazaar for criminals and organized crime to reach a global market,” Kellerman said, also mentioning “extremist organizations.”
The VMware Cybersecurity Head Added:
“Many of these payment systems and cryptocurrencies offer true or relative anonymity. This raises the necessity of increased regulation of digital money.”
In combination with a number of other points, Kellermann posited increased regulation as a possible solution, mentioning several proposed regulatory actions.
Bitcoin maintains a level of pseudonymity, depending on its purchase origin. In most cases, however, the public can track Bitcoin more easily than cash. Although Kellermann called out digital assets for their anonymity, many assets yield traceability. Anonymous coins, such as Monero and Zcash, tout additional privacy-focused features, but are often misunderstood. Recent research shows criminals’ lack of proper anonymous usage.
Updated: 6-17-2020
Alleged Ponzi Scheme Sent The $5 Million In Ether Gas Fees
The origin of the abnormal Ether transactions that paid more than $5 million in gas fees seems to be Korean “exchange” GoodCycle.
After a week of searches, it appears that the culprit behind at least two of the anomalous high fee transactions on Ether (ETH) was found.
As reported by Chinese blockchain analytics company PeckShield on June 16, the originating address appears to be coming from Korean platform GoodCycle, a recently launched peer-to-peer exchange that provides “investment” opportunities to its users.
According to PeckShield, this platform shows all the signs of a Ponzi scheme, which would explain its rapid rise in popularity.
The analysts conducted a thorough blockchain analysis and found that a wallet beginning with “0xcdd6a2b” was the origin of the first two transactions. The team was able to make a deposit on the GoodCycle platform and conclusively proved that it went to that address.
Ransomware Theory More Likely
The analysts argue that due to GoodCycle relying on a pyramid scheme, it makes sense why it has not come forward to claim the money, as that would erode trust in the platform from its users and subsequently collapse the venture.
Jeff Liu, a co-founder of PeckShield, told Cointelegraph that GoodCycle is likely to be the victim of an attack, though he added that “there are still other possibilities, such [as] internal operation errors.”
The report from PeckShield notes that the exchange does not even use the encrypted HTTPS protocol, which would make it trivial to hack the exchange through “man-in-the-middle” attacks.
A communication from GoodCycle itself seems to confirm that the platform is suffering a hack, subsequently blocking withdrawals and performing a “security upgrade.”
Victim Got In Contact With The Mining Pools
Two transactions sent today to SparkPool and Ethermine from the wallet that was identified as GoodCycle’s are signed with a message stating “I am the sender.”
It appears likely that the team finally regained control back, as it is unlikely that the hackers would have been able to make the transaction.
When asked why the exchange did not move sooner in shutting itself down, which was one of the criticisms of the blackmail theory, Liu replied:
“In my opinion, they are not very experienced exchange operators, and may need some professional help on how to deal with these operation issues.”
However, Ethermine has already decided to distribute the funds to miners, while SparkPool pledged to begin the process today as well.
The PlusToken Connection
Anonymous researcher Frank Topbottom was able to identify that several addresses connected to the massive PlusToken Ponzi scheme were interacting with the address later associated with GoodCycle. Specifically, funds from a known PlusToken sent ETH to the same deposit address used for some transactions on the GoodCycle address.
It is unclear whether the association runs deeper. It is possible that GoodCycle was simply another venue used by the scammers to launder their proceeds.
Updated: 6-18-2020
F2Pool Returns $500K of Abnormal ETH Transaction Fee To Sender
F2Pool returns about $500,000 in abnormal ETH transaction fee to its sender after encountering the issue on June 11.
F2Pool, a Chinese mining pool that recently mined an Ether (ETH) transaction with an abnormal transaction fee of 2,310 ETH, has returned 90% of the fee to its sender.
Announcing the news on June 18, F2Pool said that the MiningPoolHub, the original owner of the address behind the transaction, has received back 2,079 ETH, or about $480,000. The mining pool specified the transaction ID showing that F2Pool has returned the amount to its original owner.
In order to complete the reimbursement transaction, the original address holder had to sign the new address using the private key of the original address. This is because the original address is now controlled by a hacker, F2Pool noted.
F2Pool Wrote:
“Out of our humanitarian spirit, F2Pool has decided to return the transaction fee component of the transaction. It’s not feasible to return the fee back to the original sender address as the address is also now controlled by the hacker. Therefore, we agreed to send the fee to a new address provided by the original address owner after full verification of the address and owner.”
According to the statement from F2Pool, the rest 10% of the transaction fee, or 231 ETH ($53,000) will be distributed to miners. The amount will be used as compensation for zero-fee ETH mining during a seven day period from June 20 to June 26.
The Transaction Is Part Of A Series Of Other Abnormal ETH Transactions
F2Pool’s decision to return 90% of the abnormal transaction fee comes soon after the mining pool reported on the troubled transaction on June 12. The suspicious transaction took place on June 11, involving an original 3,221 ETH transaction with an abnormal 2,310 transaction fee. On June 12, the original owner of the address behind the transaction reached out to F2Pool and explained that they became a victim of a malicious attack on their node wallet, causing them to lose combined 5,531 ETH, or $1.2 million.
The latest news is another twist in a series of recent abnormal ETH transactions involving two other mining pools — Etherchain and Sparkpool. As reported by Cointelegraph, the two mining pools consecutively encountered similar abnormal transactions, with both of them involving an incredible $2.6 million transaction fee.
In contrast to the recent F2Pool’s decision, Etherchain and Sparkpool decided to distribute the millions of dollars in gas fees they received from the strange transactions. Both pools emphasized that they have given sufficient time for the sender to get in touch with them. Sparkpool’s transaction took place on June 10, while Etherchain’s one followed on June 11.
This is not the first time when F2Pool returned the abnormal gas fee amount to the sender. In March 2019, the Chinese mining pool returned an abnormal transaction fee worth 2,100 ETH. The amount, worth around $300,000 at the time, was returned to the sender in full, F2Pool’s global business director, Thomas Heller, tweeted on June 10.
Updated: 6-18-2020
Major Crypto Debit Card Issuer Reportedly Missing $2.1B in Cash
A German fintech company responsible for several crypto debit cards, including Crypto.com’s, allegedly misrepresented over $2 billion in cash reserves.
Major fintech company Wirecard, which issues Crypto.com’s debit cards, has fallen into controversy as some of its employees appear to have defrauded the company.
As reported by the Financial Times on June 18, auditors from Big Four accounting company EY “could not confirm the existence of €1.9bn in cash,” or about $2.1 billion.
According to a statement from the company, a trustee of Wirecard’s bank accounts attempted to deceive the auditor and falsely indicate the existence of the cash balance.
The company’s stock price plummeted by almost 50% on Thursday after the issue came to light.
According to earlier reporting by the Financial Times, Wirecard staff in Dubai and Dublin appear to have conspired to falsely inflate sales and profits for almost a decade.
Are Crypto Cards In Jeopardy?
Crypto.com’s popular debit cards are issued by WireCard, which could prove to be a problem for the company.
While it is unlikely that user funds are directly threatened, the hole in the reserves could result in service disruptions on cards issued by WireCard. Cointelegraph reached out to Crypto.com for comment, but did not immediately receive a response.
However, Crypto.com is not the only provider that could be affected by this. WireCard is currently the debit card issuer for Wirex, TenX and CryptoPay.
A notable exception in this group is Coinbase Card, which is currently issued by PaySafe Financial Services. Furthermore, Coinbase became a principal Visa issuer in February, which would put it at the same level of WireCard and PaySafe. However, the company has not yet directly issued its own debit card.
There are few providers willing to work with cryptocurrency companies, and the crypto debit card industry largely remains vulnerable to struggling principal issuers. In January 2018, the sudden collapse of WaveCrest left virtually all crypto debit card companies without a product.
It is unclear whether WireCard’s issues will result in a similar phenomenon, though this is different from the WaveCrest example, which simply had its Visa license revoked.
Germany-based Wirecard, one of the biggest and fastest-growing European fintech companies, delayed publication of its annual report and said its management board was working with auditor Ernst & Young GmbH to clarify the situation. The revelation shook investors, and the company’s shares dropped by nearly two-thirds, wiping out $9 billion in market value in a matter of hours.
The company said the auditor informed it that “no sufficient audit evidence could be obtained” on the €1.9 billion belonging to the company that was supposed to be held in trust accounts. The amount equals about one-quarter of the value of Wirecard’s balance sheet.
Wirecard is a leader among companies that have boomed as commerce shifted online and away from cash payments. It processes electronic payments for retailers, gambling sites, travel companies and others, especially online, and provides related services and loans. It was seen as a great success in Germany’s corporate scene, with high exposure to rapid growth in Asian markets. In 2018, Wirecard’s market value eclipsed that of Deutsche Bank AG , the country’s largest lender.
The €1.9 billion is meant to be held in accounts looked after by a trustee on behalf of Wirecard and payment-processing partners in some countries. Problems obtaining evidence about these balances were raised by KPMG in a recent special report into allegations about Wirecard’s accounting practices, published in April.
“There are indications that spurious balance confirmations had been provided,” Wirecard said Thursday. This was done to “deceive the auditor and create a wrong perception of the existence of such cash balances,” it said.
The German company has been a battleground stock among investors. Wirecard posted steadily rapid sales growth and hit earnings targets for years. Yet skeptical investors who bet against its shares have made it one of the most shorted stocks in Europe. Some allege the company used third parties and shell companies to generate fake revenue, or that cash it claimed to hold wasn’t really there.
Wirecard has consistently denied these allegations. Its chief executive, Markus Braun, on Thursday cast Wirecard as a possible victim. “It is currently unclear whether fraudulent transactions to the detriment of Wirecard AG have occurred,” he said. “Wirecard AG will file a complaint against unknown persons.”
He said that the €1.9 billion in deposits were held in investment-grade-rated banks and managed by a reputable trustee.
Ernst & Young had demanded that the banks holding the deposits issue new confirmations that they had the money before it would sign off on Wirecard’s accounts for 2019. But the two banks, which are based in Asia, refused to do so, according to a Wirecard spokesman.
Troubles for the company intensified in early 2019 when the Financial Times reported about a whistleblower in the company’s Singapore operations, who alleged manipulation of the company’s accounts. Police in Singapore are investigating those allegations.
At first, German regulators appeared to rally round Wirecard. The country’s financial watchdog, BaFin, banned new bets against the company’s shares for three months and said it would investigate claims of market manipulation by short sellers and the Financial Times.
Wirecard also appeared to win support from Japanese technology investment giant SoftBank Group Corp. In April 2019, Wirecard announced a $1 billion investment from an affiliate of SoftBank just before the short selling ban was due to expire.
It later turned out that SoftBank Group never invested any funds in the Wirecard deal. Instead, some SoftBank employees using personal money and Abu Dhabi sovereign-wealth fund Mubadala had put up a fraction of the funding before selling their interests through structured products arranged and sold by Credit Suisse.
Those structured notes collapsed Thursday, losing three quarters of their value, trading at 18 cents in the dollar. Credit Suisse and Mubadala didn’t immediately comment. SoftBank declined to comment.
After initially targeting Wirecard’s critics, German regulators more recently turned their gaze on the company. Members of Wirecard’s management are currently under investigation by the Munich prosecutor after BaFin filed a criminal complaint of market manipulation against them.
A person familiar with the BaFin case said it had examined statements Wirecard had made ahead of the April publication of the special investigation by KPMG. The statements misled investors to believe the report would disprove allegations against it, which it didn’t, according to the person.
KPMG was commissioned by Wirecard to perform a special audit last October in response to a string of allegations about fake revenues, falsified accounting and other matters, including some made in an unsigned report posted on the internet.
KPMG’s report complained of a lack of cooperation from Wirecard and its third-party partners. It said it wasn’t given many documents, or was only given them very late and that many were electronic copies that weren’t verifiable.
The accounting issues could prompt Visa Inc. and Mastercard Inc. to withdraw Wirecard’s licenses to operate, according to Neil Campling, head of telecoms, media and technology research at Mirabaud Securities. Mr. Campling expects Wirecard’s share price to keep falling.
“The only thing likely to go higher related to Wirecard are the bidding rights for the inevitable movie about the company,” he said.
Mastercard declined to comment. Visa didn’t make any immediate comment.
Europe has faced a string of corporate accounting scandals over the years. One that looms large was Parmalat, the Italian dairy giant that falsified more than $4 billion in cash holdings and overstated sales and profits for over a decade. Another was Lernout & Hauspie Speech Products, a Belgian company whose founders were given five-year jail sentences for fraud in 2010.
John Hempton of Bronte Capital, an Australia-based short seller who has been betting against the Wirecard shares for more than a decade, said it had been one his most costly trades ever. The stock had kept rising despite numerous allegations against the company.
“Nothing surprised us except how long the stock went up and how gullible the median European large cap manager was,” he said. “Intellectual satisfaction is nice—I would prefer a refund.”
The company will announce a new date for publication of its 2019 report. It said that if certified annual statements can’t be made available by Friday, then Wirecard’s lenders could terminate €2 billion of existing loans made to the company.
A Wirecard bond plunged Thursday, trading for 37 cents on the dollar from 80 cents yesterday, according to Tradeweb.
Wirecard has a €1.75 billion credit facility split among more than 10 banks including its long-term lender, Commerzbank of Germany, as well as ABN Amro and ING of the Netherlands. The lenders will meet to discuss what to do next, according to a person familiar with the financing.
Late Thursday, the company said it had suspended a long-serving executive, Jan Marsalek, on a revocable basis. It gave no reason for the suspension. It also said James Freis Jr. had been put in charge of compliance immediately. Mr. Fries, formerly a compliance executive at Deutsche Börse Group, was due to join Wirecard in July. Mr. Marsalek didn’t respond to a request for comment.
Updated: 6-19-2020
Markus Braun: Storyteller Behind Wirecard’s Rise and Fall
Evangelist for payments company acknowledges investor confidence is now ‘deeply shaken’.
Markus Braun was the self-styled visionary behind German payments giant Wirecard.
An instantly recognizable fixture at tech conferences, recently adopting Steve Jobs-style black turtlenecks, Mr. Braun became known for grand predictions about the future of payments, big data and artificial intelligence.
His resignation Friday after Wirecard said its auditors couldn’t locate €1.9 billion ($2.1 billion) of the company’s cash raises serious questions about his legacy. Long the company’s face and most passionate advocate, as well as its largest shareholder, Mr. Braun said Friday that “responsibility for all business transactions lies” with the chief executive.
A tall 50-year-old computer scientist from Vienna with an intense manner of speaking, Mr. Braun had been Wirecard’s CEO and chief technology officer since 2002. He was educated at the University of Vienna and previously worked for KPMG LLP’s consulting business.
A former Wirecard employee said Mr. Braun made a formidable double act with the company’s chief operating officer, Jan Marsalek, who was suspended Thursday.
“Markus was the one who spoke to investors, he was the storyteller,” the employee said. “Jan went around the world doing deals.” Others say Mr. Braun lived a quiet, unflashy life in the suburbs of Munich, where Wirecard is based.
He controlled around 7% of the company’s shares, according to FactSet, which were worth $1 billion until earlier this week. With the stock cratering over the past two days, those shares are now worth around $200 million.
“The confidence of the capital market in the company I have been managing for 18 years has been deeply shaken,” Mr. Braun said in a statement.
Mr. Braun presided over Wirecard as it grew into one of Europe’s highest-profile fintech companies. It processes electronic payments for retailers and others and provides related services and loans, and has high exposure to rapid growth in Asian markets.
He would evangelize for the company’s products, hitting on the point that different from its rivals Wirecard offered a single interface to the company’s payments platform. He was proud that Wirecard was a rare European tech success, but also saw it as a global force. “We’re active on all five continents,” he said in a 2019 company video.
Mr. Braun attracted an ardent bunch of detractors who said the company’s uncanny consistency in growing its sales from year to year was too perfect to be true. When the Financial Times published a series of stories on the company’s accounting, Mr. Braun was the chief rebutter, dismissing the allegations and assuring investors the scrutiny would soon be over.
Wirecard initially called the reporting “inaccurate, misleading and defamatory,” although it acknowledged in subsequent days that an internal investigation had been commissioned.
In November, after agreeing to have KPMG conduct an outside audit of the firm, Mr. Braun told investors that nothing would be found. “We can totally confirm today that all of these allegations are unfounded.”
Activist investor Christopher Hohn, who bet the company’s shares would fall, tried to get Mr. Braun fired in April after the audit looking into the company’s accounting practices couldn’t get answers to certain questions.
Mr. Hohn said in an interview Friday that his team had met with Mr. Braun in Germany earlier this year, and that Mr. Braun couldn’t satisfactorily answer questions raised by allegations of fraud at the company.
A tweet posted to Mr. Braun’s Twitter account Friday said the company has “excellent employees, a strong business model, outstanding technology and abundant resources to ensure a great future.”
Updated: 6-19-2020
North Korean Hackers To Launch A Global COVID-19 Phishing Campaign
North Korea-backed hackers are reportedly preparing a massive phishing campaign to take advantage of the COVID-19 crisis.
A study by cybersecurity vendor, Cyfirma, warned about a massive phishing campaign that will be launched by the North Korean hacker group, Lazarus, on June 21. The campaign will allegedly target six nations and over 5 million businesses and individuals.
According to the report published on June 18, Lazarus will subject Singapore, Japan, India, the United Kingdom, South Korea, and the United States to a massive phishing campaign. Hackers will reportedly attempt to take advantage of people receiving payments established by several countries in an attempt to mitigate the COVID-19 crisis.
A Campaign To Collect Cryptocurrencies?
Lazarus seems to be impersonating government accounts using fake emails. They ask recipients to visit fraudulent websites which ask for money and save their personal data. In the past, the North Korean hackers have preferred to be paid in cryptocurrencies.
There are no additional details about the specific methods Lazarus group will use to gather money from their victims.
A Cyfirma’s Spokesperson Told Cointelegraph:
“On June 1, the platform picked up an early indicator from Korean-speaking community discussing a folder called ‘Health-Problem-2020’ and that was when we uncovered the entire campaign targeting the USA, UK, Japan, South Korea, India and Singapore.
This global phishing campaign is well-planned across all fronts, leveraging social engineering to lure individuals and businesses into divulging personal and financial information. Citizens and business owners are in desperate need of these government fiscal support packages and chances of them falling prey to this phishing attack is very high.”
Governments Already Aware Of The Threat
The cybersecurity firm clarifies that they have not yet seen URLs for the phishing sites found in the email templates gathered during their research, but expect that such information will be revealed soon. They also state that the governments of the targeted countries have been warned about the upcoming Lazarus campaign.
Recently, North Korean leader, Kim Jong-un, reportedly encouraged Lazarus to steal cryptocurrencies like Bitcoin (BTC) using phishing scams. Sources indicate that the country has ramped up these efforts to prevent a financial meltdown during the COVID-19 crisis.
Updated: 6-22-2020
NZ Authorities Seize $90M From Alleged Bitcoin Launderer Alexander Vinnik
The New Zealand police have recovered $90 million in assets reportedly belonging to the alleged $4 billion launderer Alexander Vinnik.
According to Jared Savage at the New Zealand Herald, the police Asset Recovery Unit have frozen roughly 140 million NZD ($90 million) controlled by a company in connection to the investigation of Vinnik.
Police Commissioner Andrew Coster told the publication that local authorities had been coordinating with the United States Internal Revenue Service to address the lost funds.
The money recovered is “likely to reflect the profit gained from the victimisation of thousands, if not hundreds of thousands, of people globally as a result of cybercrime and organised crime,” according to Coster.
Money Laundering And Arrest
Vinnik was accused of laundering 300,000 Bitcoin (BTC)—roughly $4 billion—over the course of six years through BTC-e, one of the world’s largest crypto exchanges at the time. Some of the ill-gotten funds may even have come from the infamous hack of Japan-based crypto exchange Mt. Gox.
The Russian national known as “Mr. Bitcoin” was arrested during a vacation in Greece in 2017 and extradited to France earlier this year. As of press time, Vinnik is still in France awaiting charges of money laundering, extortion and conspiracy, but could be extradited to the United States or his native Russia.
Updated: 6-22-2020
PlusToken Moves $67 Million To Unknown Wallet, Signalling A Potential EOS Dump
We only need to look to recent history for what this transaction means.
A wallet associated with alleged crypto Ponzi scheme PlusToken has moved 26,316,339 EOS tokens (worth over $67 million as of press time) to an anonymous crypto wallet created less than 24 hours ago. The transaction was spotted by tracking service Whale Alert earlier today.
PlusToken is believed to be one of the largest scams in the cryptocurrency history, as it reportedly held almost $3 billion worth of assets including Bitcoin (BTC), Ethereum (ETH) and EOS when it went bust in June last year.
Launched in May 2018, PlusToken acted as a crypto wallet service and investment program promising high monthly returns. It was primarily marketed in China and South Korea.
In July 2019, six Chinese nationals were arrested in Vanuatu and extradited to China as part of the investigation regarding PlusToken. At the time, PlusToken claimed that the arrested individuals were regular users and not the company’s co-founders.
Next month, PlusToken reportedly started to move its funds to exchanges in an apparent attempt to cash out.
The scam wasn’t widely discussed in the Western crypto community until August 2019, when blockchain analytics firm Ciphertrace reported on the suspicious project. According to Ciphertrace, PlusToken netted around $2.9 billion from some 3 million people.
Suspicious market moves
As observed by Cointelegraph, similar movements in the past from wallets associated with PlusToken have been followed by suspected massive open market sales on cryptocurrency exchanges. In turn, this led to noticeable spikes in BTC, ETH and altcoin prices.
In November 2019, pseudonymous crypto researcher Ergo suggested that a major market selloff was possibly driven by the PlusToken scammers liquidating 200,000 BTC on the open market. Similarly, research firm Chainalysis suggested in its December 2019 report that PlusToken scammers may be using over-the-counter (OTC) off-ramps to sell BTC, driving down the price.
However, EOS remains unshaken as of press time. It currently trades around $2.56, up 1.26% on the day.
Updated: 6-23-2020
Resigned Wirecard CEO Detained By Police As $2.1B Fraud Threatens Company
The CEO of Wirecard, who resigned recently, was arrested by German police under accusations of conspiring to inflate assets and revenue to entice investors.
The former chief executive officer of Wirecard, a German fintech company, has been detained by Munich police after being charged with misrepresenting the company’s balances.
As reported by Reuters and many others, Markus Braun, who led the company for the better part of two decades, has been arrested by police in Munich, Germany. According to a statement issued by the prosecutor’s office, he is accused of having conspired to inflate assets and total revenue through false transactions with “third-party acquirers.” This was done to make the company appear more attractive to investors, the prosecutors say.
The misrepresented funds in question, amounting to 1.9 billion euros, or $2.1 billion, are supposed to be held in a trust account in two unspecified banks in the Philippines. Between June 21 and 22, Wirecard board of directors issued a statement saying that “with a high degree of probability” the funds do not exist.
The money represents more than 32% of Wirecard’s claimed assets of 5.8 billion euros ($6.5 billion). Since the issue finally came to light last week, Braun resigned from his role.
A judge is set to deliberate whether to continue detention today.
Company In Dire Straits
The hole in the budget and the ongoing turmoil raises questions on whether the company will be able to recover and survive in the long-term. As Cointelegraph mentioned previously, Wirecard is the principal issuer for many crypto debit card companies, like Crypto.com and Wirex’s Asia-Pacific offering.
The CEO of Crypto.com, Kris Marszalek, noted that its debit cards are fully pre-funded, and the reserves are held in a separate U.K. bank distinct from Wirecard.
Meanwhile, Wirecard’s stock price has fallen about 84% to $16 as the news became known.
The longer term fate of the company remains unknown, but Wirecard-issued cards continue operating normally so far.
Updated: 6-24-2020
Plus Token Money Launderers Stopped Short By Congestion
One of the largest ponzi schemes in crypto history is still trying to launder its proceeds, but Ethereum congestion is making that difficult.
Funds from the infamous Chinese-based PlusToken ponzi scheme are moving once again, but they’re being blocked by Ethereum’s block congestion.
According to Whale Alert, funds from a known PlusToken Ether (ETH) stash were seen moving to a fresh address. The fraudsters transferred 789,500 ETH, worth about $186 million, in what appears to be an effort to launder their funds.
The incoming wallet has since signed more than 50 transactions to split the funds across dozens of wallets, but only one of those appears to have been confirmed.
The remaining transactions have been hanging in the mempool for more than 30 minutes as of press time, largely due to their relatively low gas fee.
The transactions are bidding between 25 and 30 Gwei, which is significantly below the current average of 50 Gwei, according to EthGasStation.
Just two days earlier on June 22, PlusToken moved $67 million of its ill-gotten proceeds.
Updated: 6-24-2020
Someone Has Been On A $200M Crypto Exchange Hacking Spree
CryptoCore reportedly launched a phishing campaign against several crypto exchanges and managed to steal $200 million in two years.
A cybercriminal group has allegedly stolen around $200 million from cryptocurrency exchanges over the past two years. In total, they are believed to have hit 10 – 20 victims across the United States, the Middle East, and Asia.
According to research by the cybersecurity firm ClearSky, the gang named “CryptoCore,” known with other pseudonyms like “Dangerous Password” and “Leery Turtle,” has been actively targeting crypto firms since 2018 — specifically exchanges.
They confirmed that CryptoCore stole $200 million from at least five victims, several of whom were located in Japan.
Between 10-20 Additional Companies Could Be Affected
The names of targeted crypto exchanges were not revealed due to non-disclosure agreements with the victims. It is believed that the total number of targets could be as high as 20 in total.
The cybersecurity firm believes CryptoCore may have links to the Eastern European region, Ukraine, Russia, or Romania.
Phishing Attacks Launched Against The Exchanges
The hackers used spear-phishing attacks to gain access to crypto exchanges’ wallets. In some cases, they may have targeted executives’ personal email accounts.
The report details that spear-phishing attacks are “typically” carried out by impersonating employees, mostly those who have a high-ranking role within the company or from another organization like the advisory board.
Speaking with Cointelegraph, Brett Callow, threat analyst at malware lab Emsisoft, provided some comments regarding spear-phishing attacks like CryptoCore did:
“Some phishing campaigns consist of non-targeted mass emails sent to a large number of people. Others, however, are crafted to target specific individuals – a company executive, for example. This known as spear phishing and, because the actor may have spent time collecting information about the individual being targeted, the emails can be extremely convincing.”
Callow Also Adds:
“Many security incidents and data breaches start with phishing emails. Phishing campaigns are typically designed to either collect logins – for example, by directing the recipient to a fake banking site – or to deliver malware via malicious attachments. In either case, the end result can be the same: a compromised network.”
Cryptocore Is Not The Only Headache For The Exchanges
North Korean hacking team, Lazarus Group, targeted several crypto exchanges last year, as per a Chainalysis report. One of the attacks involved the creation of a fake, but realistic trading bot website that was offered to employees of the DragonEx exchange.
Recently, Cointelegraph reported on a study that warned of a massive phishing campaign that could be launched by Lazarus soon. This could allegedly target six nations and over 5 million businesses and individuals.
Updated: 6-24-2020
A Hacker Named “Fxmsp” Managed Built A Million Dollar Cybercriminal Business Over Three Years
A new report shows that a Kazakhstani hacker built a million dollar fortune by breaching private networks and selling their data.
Researchers at threat intelligence company, Group-IB, said that the hacker, who operates under the pseudonym “Fxmsp,” began promoting their services across darknet. They posted data for sale on hacking-related forums, offering valuable resources stolen from private corporate networks. Some customers have taken to calling the hacker “The invisible god of networks.”
Millionaire Profits For Fxmsp
According to the report, the magnitude of Fxmsp’s cybercriminal business is enormous. They reportedly accumulated $1.5 million in profits over three years by targeting 135 companies from 44 countries.
Fxmsp allegedly began promoting cryptojacking services through a Russian forum, selling corporate network data access. Their services allowed purchasers to mine cryptocurrencies using stolen computer power, though it is unknown whether these services were used to specifically mine Bitcoin (BTC).
The Study Revealed A Number Of Instances Where The Hacker Managed To Expand Their Target Capacity:
“During the time that he was active on [removed link], from early October 2017 to July 31, 2018, Fxmsp put access to 51 companies in 21 countries up for sale. The cybercriminal shared the price in only 30% of cases. By that time, after 9 months of activity, the minimum average price for all visible accesses that I’ve advertised was $ 268,000 (without including the sales I’ve made through private messages).”
Were They Really Acting Alone?
Yelisey Boguslavskiy, AdvIntel’s director of security research, believes that Fxmsp was not acting alone, but rather as part of a cybercriminal team named “GPTitan”. This group is made up of numerous hackers who access various financial environments to steal high-profile network data.
An article published by BleepingComputer, citing an independent source, claimed that “the invisible god of networks” had expanded into a team with an undetermined number of members.
Alliances Broken
Fxmsp is known to have worked with a sales manager operating under the pseudonym “Lampeduza”.
Fxmsp disappeared from the forums in May 2019, effectively ending the relationship, however.
The report states that Fxmsp and Lampeduza may still be operating privately.
Cointelegraph recently reported that the total USD value of Bitcoin transferred on the dark web rose by 65% in Q1 2020, despite a decline in transactions during the same period in 2019.
Updated: 6-25-2020
Cybercriminals Use The Blockchain To Relay Secret Messages
SophosLabs published a study that revealed hackers use the blockchain network to share secret messages.
A group of researchers from SophosLabs state that hackers operating the cryptojacking malware, Glupteba, have been using the Bitcoin blockchain network to communicate in secret.
According to the report published on June 24, cybercriminals rely on a command and control center where they send encrypted secret messages that require a 256-bit AES decryption key.
Encrypted Messages Used To Update Malware
The purpose of the communication channel is for hackers to receive updated configuration information for the malware. This data is used by attackers to obtain precise instructions and thus update the malicious software.
Glupteba is what’s known as a zombie or software robot that can be controlled remotely. It has various functions such as a rootkit, security suppressor, virus, router attack tool, browser stealer, and as a cryptojacking tool.
Sophoslabs Explains In Detail About The Curious Feature:
“Glupteba uses the fact that the Bitcoin transactions are recorded on the Bitcoin blockchain, which is a public record of transactions available from a multitude of sources that are unexceptionably accessible from most networks. Bitcoin’ transactions’ don’t actually have to be about money – they can include a field called RETURN, also known as OP_RETURN, that is effectively a comment of up to 80 characters.”
Future malware-delivery-as-a-service provider?
However, the cybersecurity firm warns that the malware could take advantage of this feature as an added value to commercialize it.
Andrew Brandt, A Principal Researcher At Sophoslabs, Told ZDNet:
“I’d say the Glupteba attackers are angling to market themselves as a malware-delivery-as-a-service provider to other malware makers who value longevity and stealth over the noisy quick endgame of, for instance, a ransomware payload.”
But this is not the first case in which the blockchain network is used to send messages in the crypto sphere. On May 25, a message signed by 145 wallets containing Bitcoin (BTC) from a number of early blocks called Craig Wright a “liar and a fraud.”
Updated: 6-26-2020
Crypto Cards Affected As UK Regulator Suspends Wirecard Subsidiary
Wirecard’s subsidiary that is responsible for issuing debit cards has been suspended as the company can no longer access customer funds.
Wirecard’s subsidiary responsible for issuing debit cards, Wirecard Card Solutions Ltd., has been suspended by the United Kingdom’s Financial Conduct Authority, or FCA.
According to a statement issued on June 26 by the regulator, Wirecard’s subsidiary is required to not dispose of any of its funds, stop conducting any of its regulated activity, and it must communicate on its website and to its customers that it is no longer permitted to conduct regulated activity.
As of press time, however, such statements are not present on any of Wirecard’s websites, including the subsidiary’s dedicated domain.
The FCA explained that following the news of the 1.9 billion euros shortfall in Wirecard, it began working with the card issuing subsidiary to ensure that customer funds are protected. On Friday, the regulator took “additional measures” and forced the firm to stop all regulated activities. “This now means customers money cannot be accessed,” the statement concludes.
That suggests that customers may be barred from using any of the debit cards issued by the company. That includes crypto debit cards from Crypto.com, TenX and others.
The CEO of Crypto.com, Kris Marszalek, reassured his customers that funds are secure and are owned by the company. Speaking with Cointelegraph, Marszalek added:
“As of this moment the cards are working fine. As per our statement yesterday, in case of a disruption, we will rapidly proceed to credit the funds back to our users crypto wallets. Given the announcement made by the FCA today, this is highly likely.”
He added that the company is looking for alternative solutions to ensure customers can continue using their cards.
In a subsequent update by Crypto.com, the company said that it was asked to cease operations for its EU and U.K. cards, which means that customers will not be able to use them “later today.” The company promised that within 48 hours, all funds on the debit cards will be returned to customers on their crypto wallets.
Cointelegraph reached out to TenX as well, but did not receive an immediate response.
Developing Scandal
Wirecard’s woes began when the company admitted to lacking over 32% of its claimed assets, worth $2.1 billion.
The CEO, Markus Braun, resigned and was subsequently arrested by German authorities. Prosecutors believe that the company’s management was involved in a long-running fraud to misrepresent the company’s earnings and assets.
On Thursday, the company filed for insolvency due to the sudden shortfall, which can be the first step to bankruptcy. The disruption to its business at the hands of the FCA is likely to worsen its already tenuous financial situation.
Updated: 6-26-2020
Crypto.com To Refund Clients As Wirecard’s Card Issuer Told To Cease Operations
Crypto.com has confirmed to CoinDesk it is moving to refund customers as the U.K. regulator orders Wirecard’s card issuer to cease all operations immediately.
Crypto.com CEO Kris Marszalek told CoinDesk the company is refunding 100% of customer funds after the Financial Conduct Authority (FCA) suspended the activities of Wirecard Card Solutions, a subsidiary of the Wirecard Group, which filed for insolvency on Thursday after admitting last week to be missing $2.1 billion.
“We will rapidly proceed to credit the funds back to our users’ crypto wallets,” Marszalek said.
All funds will be refunded in the next 48 hours.
The FCA ordered Wirecard Card Solutions to cease all regulated activities on Friday. The financial watchdog said it had stepped in to protect customer funds and would prevent the company from accepting or disposing of any more revenue.
While Wirecard Group is headquartered in Munich and is outside the FCA’s jurisdiction, Wirecard Card Solutions has its offices in Newcastle, in the north of England. Friday’s announcement affects all cards issued by Wirecard Card Solutions, including those belonging to Crypto.com and TenX users. Although it still isn’t clear what could happen, one possibility is that all Wirecard cards stop working.
Users will not be able to top up or transact with Crypto.com cards as of later today.
Both Crypto.com and TenX kept quiet after Wirecard admitted last Thursday its $2.1 billion accounting hole may have come from employees purposefully inflating company revenue.
Both companies assured customers their funds were safe because they were held by a separate financial institution, but representatives refused to say whether they were looking for another card issuer.
But Friday’s news has now forced their hands.
“We’ve been working on alternative solutions with our partners to make sure our customers can continue their cards, and will provide an update on this in due course,” Marszalek said.
In a statement, Crypto.com said it was in the process of transferring its card program to a new provider.
TenX did not immediately respond to requests for comment.
Updated: 6-26-2020
Investors Fear Ethereum Price Sell-Off After PlusToken Transfers 789K ETH
PlusToken recently moved $186 million worth of Ethereum, leading investors to fear a dump in ETH price.
Earlier this week PlusToken, one of the largest scams in the cryptocurrency world, tried to move 789,500 Ether (ETH), but the movement of these stolen funds were temporarily held up by congestion issues within the Ethereum network.
The $186 million transfer came from a known Ethereum address and was later split into 50 different transactions, possibly as an attempt to disguise the activity. Whale Alert first spotted the transactions which have since been processed but little information on the funds’ destination has been reported.
Just two days before this latest development, PlusToken also moved $67 million worth of stolen EOS.
PlusToken Sales Lead To ETH And BTC Corrections
Despite being dismantled last year, PlusToken is still causing damage to the crypto industry by liquidating holdings and holding large amounts of Bitcoin (BTC) and other assets like Ether and EOS.
PlusToken still holds a significant amount of stolen crypto-assets and these funds continue to pose a threat to spot markets as large market sales can impact Bitcoin and Ether’s price across various exchanges.
While some believe that the March 12 crash was caused by PlusToken dumping Bitcoin on spot markets, this theory was quickly dispelled by data from blockchain analysis firm, Chainalysis.
According to Chainalysis, BTC movements from PlusToken to exchanges slowed down heavily before the Black Thursday crash, which shows the two events were not related.
While this particular crash was not related to PlusToken, many still believe the group is responsible for some of the accentuated drops in the Bitcoin price, namely in December 2019.
As crypto options and futures continue to grow in popularity, the danger of an accentuated drop caused by a large sell-off becomes bigger as it could potentially trigger a long squeeze for Ether.
Chainalysis head of research Kim Grauer agrees that a PlusToken triggered sell-off is a real risk. Grauer previously told Cointelegraph:
“We found in the past that large inflows to exchanges, such as those from PlusToken last year, tend to increase the price volatility on exchanges. This problem can potentially be exacerbated by trading bots that pick up on those on-chain movements and execute trades, not to mention the highly leveraged positions on derivatives exchanges that can get liquidated rather quickly. But overall, prices tend to bounce back quickly from those one-off events.”
Exchanges Raise Security To Ward Off Scammers
In this instance the Ethereum network acted as a temporary bottleneck for the scammers as the transaction was stalled due to network congestion, which is ironically a very small silver lining in the current scalability issues being faced by the second biggest blockchain network.
However, the biggest deterrent for the liquidation of PlusToken funds should be exchanges’ KYC (know-your-customer) standards.
KYC requires users to divulge their identity which, if done right, could lead to the arrest of the person or people selling the assets. As previously reported, a large portion of the BTC sell-offs conducted by PlusToken took place in the Huobi and Okex exchanges where the KYC and AML policies were not sufficient enough to stop the scammers.
To be fair, Huobi has worked to improve its security standards since the last wave of PlusToken BTC sales. The exchange recently launched an on-chain monitoring tool called Star Atlas in order to identify “crimes like fraud, money laundering and other problematic activities” on their platform.
Peer-to-peer exchange Paxful also recently partnered with Chainalysis to increase monitoring around illicit transactions.
While it’s hard to tell what the PlusToken scammers will do next, traders will be keeping close watch on the upcoming Ether options expiry and the spot price at exchanges to see if the scammers try to dump on open markets after the expiry.
Updated: 6-27-2020
Transnational Cybercrime Group Co-Founder Who Amassed $568M Pleads Guilty
The co-founder of the Infraud Organization pleaded guilty to racketeering charges before a U.S. District Court in the District of Nevada.
A Russian national behind the cybercriminal enterprise Infraud Organization has pleaded guilty on June 26 to racketeering conspiracy, due to his role as a co-founder and admin of the dark web-based carding portal which generated profits over $568 million.
According to the announcement made by the U.S. Department of Justice, or DOJ, 33-year-old Sergey Medvedev, also known under the pseudonyms “Stells,” “segmed,” and “serjbear,” claimed responsibility for his role in the organization created in October 2010 by a Ukraine national, Svyatoslav Bondarenko.
Medvedev pleaded guilty before U.S. District Court Judge James C. Mahan in the District of Nevada.
What Is RICO?
The Racketeer Influenced and Corrupt Organizations Act, or RICO, provides robust criminal penalties for persons who engage in a “pattern of racketeering activity” or “collection of an unlawful debt” and who have a specified relationship to an “enterprise” that affects interstate or foreign commerce.
The DOJ accuses the Infraud Organization of being the “premier destination” for people who want to buy retail items with counterfeit or stolen credit card information, whose transactions were made via cryptocurrencies.
Escrow Service Provided To Facilitate Illegal Crypto Transactions
The cybercriminal cartel also promoted the selling of malware, banking information, and illegal goods.
It provided an escrow service to facilitate illicit digital currency transactions among its members and employed screening protocols that purported to ensure only high-quality vendors were permitted to advertise to members.
The latest figures revealed by the authorities’ investigation assure that the Infraud Organization had around 10,901 registered members.
During its seven-year tenure, the group inflicted approximately $2.2 billion in intended losses, and more than $568 million in actual damages, on a wide swath of financial institutions, merchants, and private individuals, DOJ said.
Medvedev was arrested in 2018 in Bangkok, Thailand, with over 100,000 Bitcoin (BTC), worth $822 million at the time. In the same year, U.S. authorities indicted 36 individuals for allegedly held roles in the cybercriminal enterprise.
Another Russian National Involved In An Ongoing Cybercriminal Case In The U.S.
In a non-related case, a Russian hacker was sentenced to nine years in prison by a U.S. court on June 26.
The hacker, Aleksei Burkov, was accused of running a website called “Cardplanet” which sold payment card information as well.
He was previously considered to be of personal interest by Russian President, Vladimir Putin.
Updated: 6-29-2020
Shareholders File Criminal Complaint Against EY For Alleged Role In Wirecard Scandal
Shareholders in German fintech Wirecard are taking legal action against Big Four auditor EY in the fallout from the scandal now engulfing the company.
Shareholders in German fintech Wirecard are taking legal action against Big Four auditor EY in the fallout from the scandal now engulfing the company.
Earlier this month, the auditor had refused to sign off the fintech’s 2019 financial report after discovering a shortfall of €1.9 billion (roughly $2.1 billion) on its books.
Following EY’s discovery, German authorities arrested Wirecard’s (now-former) CEO, Markus Braun, who had been at the helm of the fintech for almost two decades.
Braun has been accused of conspiring to inflate the company’s assets and misrepresent what amounted to over 32% of Wirecard’s assets — $2.1 billion of a claimed $6.5 billion.
According to CNBC on June 26, EY said that there are “clear indications that this was an elaborate and sophisticated fraud, involving multiple parties around the world in different institutions, with a deliberate aim of deception.”
The auditor defended its position, claiming that “even the most robust and extended audit procedures” would not be able to derail a “collusive fraud” of this nature.
The German shareholders’ association, Schutzgemeinschaft der Kapitalanleger e. V. (SdK), has nonetheless filed a criminal complaint against three EY auditors — two current and one former — for their alleged role in the accounting scandal.
Crypto Debit Cards Impacted By Wirecard Controversy
On June 25, Wirecard filed to open insolvency proceedings. As the extent of the alleged fraud became apparent, regulators moved to suspend its subsidiary, Wirecard Card Solutions Ltd., which is responsible for issuing the firm’s debit cards.
The incident has sparked concern in the cryptocurrency industry, as debit cards from Wirex, TenX and CryptoPay, are among the cards issued by Wirecard.
Following regulators’ action, Crypto.com was asked to cease operations for its EU and U.K. cards, but returned all funds on the affected debit cards to customers’ crypto wallets.
The company is now reportedly working to transfer its card program to a new provider.
Updated: 6-29-2020
Hacker Steals Balancer’s COMP Allowance In Second Attack Within 24 Hours
Balancer hacked twice within 24 hours, though this time the sum is relatively small.
We recently reported that the Balancer DeFit protocol suffered a $500,000 attack. Less than 24 hours later, a second attack claimed about $2,300 worth of Compound tokens (COMP).
Hao, an engineer at DeBank, tweeted that an attacker was able to fool the Balancer system into thinking he was owed a significant portion of the COMP tokens stored in the decentralized exchange’s pool.
The attack involved flash loans from both dYdX and Uniswap. The hacker loaned more than $33 million that was used to generate cTokens representing ownership in a Compound pool.
The attacker then transferred the cTokens to a Balancer pool. This triggered Compound into distributing the COMP accrued by the pool during its normal operation.
The hacker then forced Balancer to update the pool’s balance, which at this point included all of the flash loaned money. The system thus believed that the hacker was entitled to a significant share of the pool’s COMP, despite not having held any money previously.
A call to withdraw the COMP and exchange it to ETH completed the hack, which netted a relatively small sum of about 10 COMP, worth $2,300.
Hao noted that the attack is similar to the $500,000 loss from earlier in the day. Like the first, this second attack relies on the peculiar way that Balancer manages its internal state.
The team has since pledged to make affected users whole. They will also compensate a researcher who reported on the vulnerability in May.
Updated: 6-29-2020
DeFi Protocol Balancer Hacked Through Exploit It Seemingly Knew About
A spat between the Balancer and STA team following the $500,000 hack suggests that the DeFi protocol was aware of the weakness.
The Balancer automated market maker protocol has been hacked for over $500,000 in a single Ether (ETH) transaction, facilitated once again by a dYdX flash loan.
As analyzed by the 1inch.exchange team a few hours after the incident, a carefully crafted transaction taking more than 8 million gas, or about two thirds of an Ethereum block, stole over $500,000 in Ether, Wrapped Bitcoin (WBTC), Chainlink (LINK) and Synthetix (SNX) tokens.
Taking Advantage Of Programmed Burn
Timestamped at 6 PM UTC on Sunday, the transaction begins with a flash loan from dYdX for 104,000 ETH, or about $23 million.
The exploit relied on Statera (STA), a deflationary token where 1% of every transaction is automatically burned. Balancer’s smart contracts seem to have failed to account for this, thus expecting that each transaction would be for the full amount.
The hacker exploited this by exchanging back and forth between Statera and Ether 24 times. At each step, the STA balance available to the contract diminished by 1%, but the smart contract did not account for this. Thus, the price of STA remained stable despite the dwindling supply.
As noted by Balancer’s disclosure, at the end of this procedure the attacker called a function that updated the price based on the effective pool balance. Since the STA side was empty, it was suddenly priced at a huge premium.
The hacker used a “weiSTA,” or one billionth of a token, to swap for other assets on the platform, including ETH, BTC, LINK and SNX. Due to the burn mechanism, the weiSTA was never actually exchanged, which allowed the hacker to perform the transfer multiple times until all STA pools were dried.
They then exchanged the remainder of the STA to Balancer Pool tokens and cashed them out to Ether with Uniswap.
Security Practices Called Into Question
The Balancer team is being accused by a security researcher and the STA team for ignoring a bug report submitted almost two months before. Balancer’s CTO, Mike McDonald, confirmed the existence of the report, claiming that the issue outlined in it was essentially unexploitable and blaming flash loans for the incident. It is worth noting that any exploit made possible by a flash loan is also vulnerable to hackers with significant funds.
In a subsequently deleted tweet, McDonald appears to have taken responsibility for the bug.
Cointelegraph obtained screenshots from the STA team that further suggest that Balancer was keenly aware of the issue with transfer-fee tokens like Statera just days before the incident.
While Balancer took precautions with the STA pool by not including it in the liquidity mining program, it is unclear why the issue was not fixed at a smart contract level. At the same time, the protocol is permissionless and anyone can add new pools at their own risk. This would be similar to an incident that occurred on Uniswap during the dForce hack, where a pool created against the team’s advice was simultaneously hacked.
The Statera team nevertheless believes the risks were not adequately disclosed, with a representative saying:
“The only warning they have is on their website which suggests that the project is in beta and all funds are at risk.”
While Balancer documentation does mention risks for Statera-like tokens, they only involve “arbitrage opportunities.” The Statera representative said that “[we] wouldn’t have gone with Balancer if we knew we were at risk for such an attack.”
Cointelegraph reached out to Balancer to learn more, but did not immediately receive a response.
Updated: 6-29-2020
Digital Currency Guru Commits Cyber Fraud Amounting To $568 million
Sergey Medvedev, a Russian national who operated a digital currency escrow service for the $568 million payment card fraud forum he founded in 2010, pleaded guilty to racketeering charges in what the U.S. government called its largest ever cyber fraud case.
Medvedev, 33, admitted in his June 26 plea before the U.S. District Court for Nevada that he founded and ran the Infraud Organization, an international cybercrime enterprise that facilitated the sale of credit card and equipment theft, malware and stolen account information during its eight year reign.
He also acknowledged running a “digital currency” exchange and escrow service for Infraud’s 10,901 members. A 2018 indictment stated Infraud members used the now-defunct Liberty Reserve and bitcoin, among other “digital currencies,” to launder their funds.
The June plea does not mention the extent to which Medvedev’s exchange service transacted in bitcoin or other cryptocurrencies. It states that Medvedev accrued $1.04 million in Liberty Reserve digital currency through May 2013.
In total, Infraud facilitated the sale of 4 million compromised payment card numbers and caused an actual loss of $568 million dollars to its victims, American Express, Visa, MasterCard and others, Medvedev admitted.
The Department of Justice shut down Infraud in February 2018 and subsequently indicted 36 members of the organization as part of Operation Shadow Web.
At the time of his arrest in Thailand in 2018, Medvedev was estimated to be in possession of more than 100,000 bitcoin, according to the Bangkok Post.
Medvedev’s sentencing hearing is scheduled for December 9.
Updated; 7-6-2020
Ledger Crypto Wallet Claims Purported Vulnerability Is User Experience Flaw
Ledger’s chief technology officer Charles Guillemet said that the recently revealed vulnerability is nothing more than a user experience flaw.
Leading crypto hardware wallet producer Ledger has denied that its product’s transaction management software featured a double-spend vulnerability.
According to Ledger’s CTO Charles Guillemet, the vulnerability recently revealed by software wallet ZenGo is — in fact — nothing more than a user experience flaw. He illustrated the nature of its hardware wallet companion software Ledger Live to Cointelegraph:
“It’s important to understand that rather than an attack, the actual flaw may be seen more as a clever piece of trickery. Trickery is not a vulnerability. However, we do want to prevent anyone from falling victim to these kinds of clever schemes. […] It’s just a UX issue that could be used by a dishonest product buyer. ”
The Claims Are Not New
ZenGo’s claims are closely related to those released by Bitcoin Cash (BCH)-focused firm BitcoinBCH at the end of 2019. At the time, the firm’s CEO Hayden Otto explained in a video how a Bitcoin (BTC) point-of-sale solution misled merchants into believing non-confirmed transactions were final and accepting them.
Like BitcoinBCH, ZenGo noted that Bitcoin’s replace-by-fee (RBF) feature can easily allow users to replace an unconfirmed transaction with a new one with a different target address that has a higher fee. It is worth noting that this feature only makes it easier to leverage the non-finality of unconfirmed transactions, a thing that is harder, but still possible without RBF.
Furthermore, ZenGo’s report also points out that RBF “does not introduce any new vulnerabilities in itself” and instead “it explicitly puts the responsibility on wallet applications and users’ to identify unconfirmed transactions as unsafe.” This is confirmed by Guillemet:
“We want to thank ZenGo for having responsibly disclosed this issue to us. […] We do want to prevent anyone from falling victim to these kinds of clever schemes. A way to prevent this is of course to make sure that any transaction is first confirmed. Ledger Live is releasing an update on July 2nd. A warning is now displayed on pending transactions.”
ZenGo said that it was awarded a bug bounty for bringing attention to the issue.
Updated: 7-8-2020
Kraken Discovers Supply Chain Attacks Against Ledger Wallets
Hardware wallet Ledger is allegedly vulnerable to two new attacks, Kraken exchange warned.
Kraken, a major United States-based cryptocurrency exchange, has identified new potential attacks against the popular hardware wallet, Ledger.
Kraken Security Labs, the exchange’s cyber security division, has discovered two new attack vectors that could compromise the security of Ledger Nano X wallets. The exchange announced the news in a July 8 blog post.
Both Attacks Can Be Exploited Before Users Launch The Wallet For The First Time
According to the post, both attacks can affect Ledger Nano X wallets if exploited prior to the user receiving the wallet. This can happen if the wallet was disturbed during the shipment or obtained from a malicious reseller, Kraken noted.
As a result, the attacks could enable hackers to take control of computers connected to the Ledger wallets and install malware. This could ultimately lead to the loss of funds stored on the wallet.
“Bad Ledger” Attack Turns Ledger Wallets Into A Malicious Keyboard
In the post, Kraken Security Labs described both potential attack vectors. The first one, dubbed “Bad Ledger” attack, is able to infect a Ledger Nano X wallet by modifying its debugging protocol to act as an input device, like a keyboard.
Using keyboard shortcuts, it is capable of opening a browser and navigating to Kraken exchange’s domain, the experts found.
This type of attack is similar to the so-called “Rubber Ducky” and “BadUSB” attacks, which can reflash a device with malicious firmware to compromise the computer, Kraken noted.
“Blind Ledger” Approves Malicious Transactions Through Turned-Off Display
The second attack, described as “Blind Ledger”, is capable of resetting the wallet’s display and convincing users to press a series of buttons to approve a malicious transaction. Once the malicious code is running on their computer, it can alert the user of a fake error and turn off the wallet’s display.
Possible alerts may sound like “your Ledger Nano X stopped responding, please hold both buttons to restart the device,” Kraken noted. With the display disabled, users can not see what is actually happening on their hardware wallet. Blindly following these instructions actually leads to the verification of a malicious transaction, the security group explained.
Ledger’s official response
In response to Kraken’s warning, Ledger issued a security bulletin, confirming that the vulnerability can lead to supply chain attack scenarios. In the post, Ledger said that the latest firmware update protects wallet holders from these attacks by switching off debugging capabilities.
Ledger Wrote:
“Debugging capabilities are permanently switched off as soon as an application is installed […] These attacks cannot be performed once an application has been installed on the device.”
The Ledger Nano X is the latest crypto wallet designed by major hardware wallet manufacturer, Ledger. Released in 2019, the product is the only Ledger wallet that is rechargeable and works wirelessly via Bluetooth. On July 6, Cointelegraph reported on Ledger’s CTO, Charles Guillemet, denying Ledger’s alleged double-spend vulnerability.
Updated: 7-8-2020
Fake Tokens on Uniswap Are Trying To Cash In On DeFi Hype
Uniswap appears to be plagued with scam tokens claiming affiliation with popular DeFi projects.
Scam tokens are a growing problem on the decentralized exchange and liquidity pool Uniswap — owing to the protocol’s open listing policy.
In recent days warnings have been issued about scam tokens targeting four of the most buzz-worthy decentralized finance (DeFi) projects including Curve Finance, 1inchExchange, Tornado.Cash, and dYdX.
With any token able to be listed on the platform’s drop-down menu simply by making a GitHub request, the platform’s users are increasingly calling for more stringent vetting to be introduced.
Open Listing Policy Leads To Scam Tokens
Decentralized derivatives project Opium took to Twitter on July 7 to warn users that a scam token called Opium and trading under the ticker OPM had been listed on Uniswap despite the project not having a native token.
The same day the Defiprime Twitter account noted a ‘DYDX’ token pool purporting association with the similarly tokenless DeFi protocol dYdX, along with a fake ‘Uniswap Community Token.’
A day earlier Tornado.Cash had reported that scammers were selling a fraudulent ‘TC’ token claiming affiliation to the project. Curve Finance and 1inch.Exchange reported fake coins impersonating their yet-to-be-released native tokens on July 5 and July 4 respectively.
A similar scam token impersonating Balancer Labs’ then-forthcoming BAL was also identified last month.
Uniswap Attracts Liquidity
Since its ‘V2’ overhaul in May, Uniswap has emerged as a cornerstone of the nascent DeFi ecosystem, with data published by Dune Analytics indicating that Uniswap comprises DeFi’s top pool by total users with 92,000.
V2 also preceded a dramatic spike in Uniswap volume, with trade activity on the platform exceeding $20 million on July 2 — roughly six weeks after Uniswap’s volume broke above $2 million for the first time.
Updated: 7-8-2020
Anonymous Crypto Hacker’s Identity Revealed by US Authorities
The U.S. Department of Justice unveiled the identity of the hacker behind the pseudonym “fxmsp” after charging him with federal crimes.
The U.S. Department of Justice, or DoJ, indicted Andrey Turchin, known under the pseudonym “fxmsp,” with various federal crimes. Turchin allegedly founded a cybercrime group that targeted the computer networks of several companies. After stealing each company’s data, Turchin’s group allegedly sold the data on the dark web.
Turchin, a 37 year old Kazakhstan national, is affectionately known on the dark web as “the invisible god of networks.” He allegedly sold access to thousands of networks breached with his malware attacks, amassing a million dollar crypto fortune over the course of three years.
The Western District of Washington is now conducting criminal indictment procedures against Turchin, who is accused of attacking companies based in over 40 countries.
No Arrests Yet
The Kazakhstan and British authorities also assisted the U.S. to unseal the indictment against “fxmsp.” U.S. Attorney, Brian T. Moran, said:
“Cybercrime knows no international borders, and stopping these crimes requires cooperation between an array of international partners. I commend Kazakhstan for its assistance in this investigation. I am hopeful these critical international partnerships between cybercrime investigators will lead to holding Andrey Turchin accountable in a court of law.”
Although the DoJ’s announcement didn’t specify that the Kazakhstan police had already arrested Turchin, an unknown number of alleged co-conspirators were also identified by the FBI. The indictment does not mention their identities.
Fxmsp’s Cybercriminal Structure
U.S. Law Enforcement Detailed The Cybercriminal Operations Allegedly Led By “fxmsp” And How They Managed To Process The Transactions:
“Prices typically ranged from a couple thousand dollars to, in some cases, over a hundred thousand dollars, depending on the victim and the degree of system access and controls. Many transactions occurred through use of a broker and escrow, which allowed interested buyers to sample the network access for a limited period to test the quality and reliability of the illicit access.”
Cointelegraph recently reported that the total USD value of Bitcoin (BTC) transferred on the dark web rose by 65% in Q1 2020, despite a decline in transactions during the same period in 2019.
Updated: 7-10-2020
Accomplice In Alleged $722M Bitcoin Ponzi Scheme Pleads Guilty To Charges
One of four men charged with defrauding investors of over $722 million through a long-running cryptomining scheme has pleaded guilty to charges against him.
One of four men charged with defrauding investors of more than $722 million through a long-running cryptocurrency mining scheme has pleaded guilty to charges against him.
The man, a 35-year-old Romanian programmer called Silviu Catalin Bacali, was arrested in Germany in December 2019.
He was charged with one count of conspiracy to commit wire fraud as well as a conspiracy to offer and sell unregistered securities. He faces a maximum of five years in prison and a fine of $250,000.
Three others — Matthew Brent Goettsche, Russ Albert Medlin, Jobadiah Sinclair Weeks and Joseph Frank Abel — were charged in connection with the scheme in the United States that same month.
Prosecutors allege that the scheme — operational between April 2014 and December 2019 — solicited money from investors in exchange for shares in purported cryptocurrency mining pools. Investors were awarded bonuses for recruiting further investors into the network.
The indictment cites correspondence between Goettsche and Balaci, in which they allegedly discussed how to fake mining earnings and referred to their investors as “sheep.”
While the other defendants allegedly offered investors the choice of investing in three separate Bitcoin (BTC) mining pools, Bacali admitted that he himself was unaware that the BitClub Network operated more than one pool.
Further correspondence between the programmer and Goettsche from 2015 apparently revealed that Bacali was asked to “bump up the daily mining earnings starting today by 60%,” which he objected to as being “not sustainable” and “ponzi teritori.”
He is nonetheless charged with changing figures to mislead investors at his accomplice’s urging. Bacali has also confirmed prosecutors’ allegation that the scheme fleeced at least $722 million worth of BTC from investors.
Early Warning Signs
In March 2017, Cointelegraph reported on allegations that BitClub had launched a malleability attack on the Bitcoin network. The scheme had also been flagged as suspicious by crypto media news outlet 99Bitcoins as early as 2016.
Updated: 7-10-2020
Crypto ‘Giveaway’ Scams Continue To Flourish On YouTube
Crypto scams on video hosting platform YouTube are continuing to prey on unsuspecting victims.
* In scam videos seen this week, the identities of Ethereum founder Vitalik Buterin and Tyler and Cameron Winklevoss, founders of the U.S.-based Gemini exchange, have been used to lure people into giving up cryptocurrencies like bitcoin and ether.
* The “giveaway” scams are based on the promise of doubling one’s funds after send an initial amount to a wallet address via QR code.
* Victims, in fact, receive nothing in return and lose the crypto they sent.
* In separate videos, which have since been removed by YouTube, both Buterin and the Winklevoss twins can be seen talking on stage, praising the benefits of their projects.
* The video grabbed for one of the scams featuring Buterin appears to be taken from an Ethereum event held in London earlier this year.
* YouTube has been under fire from Ripple Labs and CEO Brad Garlinghouse, who are suing over allegations the social media giant fails to police its platform against fake XRP giveaway scams.
* YouTube frequently blocks cryptocurrency-focused accounts that are not scams. The firm has previously said errors occur because of the sheer volume of content it has to monitor.
* YouTube, Gemini Exchange and the Ethereum Foundation did not return requests for comment by press time.
Updated: 7-23-2020
Apple Co-Founder Steve Wozniak Sues YouTube Over Bitcoin Giveaway Scams
Apple co-founder Steve Wozniak is suing video-sharing giant YouTube and its parent company Google for allegedly allowing bitcoin giveaway scams that use his likeness to thrive on its platform.
Wozniak was one of 18 plaintiffs that filed the lawsuit on Tuesday, which seeks punitive damages, a trial by jury and demands YouTube remove all bitcoin giveaway scams and promotions using Wozniak’s name and likeness.
The suit praised Twitter for acting “swiftly and decisively” to shut down malicious accounts and “protect its users from the scam” referencing the platform’s response to last week’s coordinated cyberattack that gained access to a host of verified Twitter accounts and posted a crypto giveaway message.
“In stark contrast, for months now, Defendant YOUTUBE has been unapologetically hosting, promoting, and directly profiting from similar scams,” the suit said.
Wozniak is not the first to take action against YouTube over crypto scams. Earlier this year, Ripple Labs, along with CEO Brad Garlinghouse, sued the platform for allegedly failing to effectively police fake XRP giveaway scams that were causing monetary and reputational harm to the company.
According to the new complaint filed with the Superior Court of the State of California in the county of San Mateo, YouTube has “featured a steady stream of scam videos and promotions that falsely use images and videos of Plaintiff Steve Wozniak, and other famous tech entrepreneurs, and that have defrauded YouTube users out of millions of dollars.”
The suit alleged that the image and likeness of other well-known entrepreneurs including Bill Gates, Elon Musk and Michael Dell were also being exploited in these scams.
According to screenshots attached in the complaint, the scams involving Wozniak uses images and videos that tell users that the entrepreneur is hosting a live bitcoin or “BTC” giveaway event. The suit alleges that the posts “convince” users to transfer their cryptocurrency promising that, for a limited time, they “will receive twice as much back”.
“YOUTUBE and GOOGLE took the further step of promoting and profiting from these scams by providing paid advertising that targeted users who were most likely to be harmed,” the suit said.
Wozniak is accusing defendants YouTube and Google of violating his right of publicity, misappropriating his name and likeness, as well as aiding and abetting fraud, and negligent failure to warn users.
“Defendants’ failure to warn was willful, malicious, oppressive, fraudulent, and/or in reckless disregard of the Plaintiffs’ rights, thereby entitling Plaintiffs to punitive damages,” the suit said.
The suit demands a trial by jury on all issues triable, and damages that include legal expenses, and any “gains, profits, or advantages wrongfully obtained by Defendants.”
The lawsuit was filed by Cotchett, Pitre & McCarthy, LLP.
Updated: 7-23-2020
YouTube Seeks to Dismiss Ripple Lawsuit Over XRP Giveaway Scams
In a motion to dismiss a lawsuit brought by Ripple, YouTube argues it isn’t liable for crypto scammers using its platform.
The motion filed on Monday in the U.S. District Court for the Northern District of California, argues that under Section 230 of the Communications Decency Act, “interactive computer services,” like YouTube, cannot be treated as publishers of third-party content and hence aren’t liable for it.
* Ripple had sued YouTube in April, alleging that the video sharing platform did not sufficiently control XRP giveaway scams on its platform that caused monetary loss for users and hurt Ripple’s reputation. The crypto firm’s lawsuit alleged that scammers have defrauded “millions of XRP valued at hundreds of thousands of dollars” from victims and cited at least one instance where a scammer apparently received $15,000 in XRP from a victim.
* In its motion to dismiss the lawsuit, YouTube argues that Ripple’s claims run up against immunity provided against such lawsuits to online publishers under Section 230. The motion said that Ripple has filed the lawsuit “even though YouTube itself is a victim of the scam,” since the attackers took over user accounts on the platform.
* YouTube’s motion to dismiss the allegations boils down to the idea that the video-sharing giant did not willingly or knowingly engage in any of the scams or copyright infringement, and cannot be held liable for any third party content on its website. The firm’s motion also adds that it shut down such scams whenever it was alerted to them.
* Responding to allegations that YouTube also helped scammers advertise their schemes by running paid ads for them, the video sharing giant’s motion to dismiss maintained that it could not be held liable for third-party content.
“And whether YouTube ‘approved’ or ‘endorsed’ the ads by allowing them to be published is immaterial,” the motion noted.
* YouTube argues that Section 230 protects the video-sharing giant from Ripple’s allegations and therefore the case should be dismissed. A Ripple representative did not immediately respond to a request for comment on YouTube’s motion to dismiss.
* In another lawsuit filed against YouTube yesterday, Apple’s co-founder Steve Wozniak alleged that the firm had allowed bitcoin giveaway scams that use his likeness to thrive on its platform. Wozniak, along with 18 other plaintiffs, is seeking punitive damages and demanding that Youtube take down all such scams as well.
Updated: 8-3-2020
Inside A Crypto ‘Ponzi’: How The $6.5M Banana.Fund Fraud Unravelled
U.S. prosecutors are seeking to return $6.5 million in allegedly scammed bitcoin to victims of the “Banana.Fund” crowdfunding project, which the government described in court papers as a Ponzi scheme.
In a forfeiture suit against the cryptocurrency account storing the funds, prosecutors allege Banana.Fund’s unnamed administrator admitted to investors his project had flopped, promised to return $1.7 million to them and then failed to do so.
The operator then pivoted to a laundering and refund scheme that ultimately resulted in the U.S. Secret Service’s (USSS) seizure of 482 bitcoin (BTC) and 1,721,868 tether (USDT).
The lawsuit, filed July 29 in the U.S. District Court for the District of Columbia, seeks to grant the federal government formal ownership of the assets so it can return them to the victims.
The suit did not identify the operator of Banana.fund. But several victims of the alleged scam, and documents reviewed by CoinDesk, show the outfit was run by a British national named Richard Matthew John O’Neill aka “Jo Cook.”
One of the victims, Mike Koenen, told CoinDesk that since at least May 2018 he has been pushing the USSS to investigate Banana.Fund and O’Neill.
Documents reviewed by CoinDesk show that by November 2019, agents with the USSS San Francisco field office were email-canvassing likely victims for information on Richard O’Neill. Law enforcement had frozen O’Neill’s Poloniex account over a year before.
Neither O’Neill nor the Department of Justice responded to requests for comment.
The forfeiture suit represents perhaps the most substantial development yet in a little-known scheme that ran through the height of bitcoin’s historic late-2017 price pump and apparently went belly-up within months of the market’s pop, the documents reveal.
Peeling Back The Fraud
Banana.Fund’s white paper describes a crowdfunded business development company that shepherds fledgling startups through their earliest stages while offering operational transparency to their seed investors.
O’Neill told CoinTelegraph in January 2017 that Banana.Fund would “use blockchain for what it is good for: implementing transparent and irreversible global transactions.” In his view, he was “creating a level playing field for all users to pursue their business ideas, free of charge.”
Investing in O’Neill’s own business idea was not free of charge, however.
The buy-in started at 0.02 BTC, said Telegram user Dutch_Giant, who heard about Banana.Fund on the now-defunct message board MoneyMakersforum.
“The bigger deposit you made, the bigger part of the business you got,” Dutch_Giant said. He put in 0.024 bitcoin – “about $60 at the time.”
Other investors went even bigger on O’Neill’s crowdfunding darling, internal documents show. One user invested 82 bitcoin and nine others contributed 10 bitcoin or more. In all, 417 investors claim to have lost a combined 481 bitcoin, worth almost $5.5 million today, to Banana.Fund.
Those figures come from a spreadsheet of “verified refund claims” that O’Neill began compiling on Jan. 2, 2018, when he emailed Banana.Fund investors that they could be refunded nearly three times the dollar value of their original investment – but not their value in bitcoin.
“Banana.Fund is a failed project,” O’Neill said in a project announcement whose text was shared with CoinDesk and referenced in the criminal complaint. He claimed that while Banana.Fund had already spent around a third of investors’ $600,000 pie on overhead, he had ridden the remaining bitcoin through late 2017’s heights and could now refund them triple their original investment in USDT, a stablecoin that usually trades 1-for-1 with the dollar.
“We’ve failed up!” he said. He claimed to have $1,730,000 in USDT for refunds. “Pure dumb luck.”
His investors would have been far luckier had they never locked their bitcoin up in Banana.Fund, the DOJ points out. Banana.Fund’s founder, referred to in the suit only as “Person 1,” only “stated that due to the increased value of bitcoin, investors would receive more than their initial investment in U.S. dollars, although, realistically, they would all still lose money because of the increased value of bitcoin.”
A Calculated Risk
Prosecutors allege that “Person 1” had an account balance of $11 million and could therefore easily pay back even Banana.Fund’s biggest investors. They further allege that “Person 1” spent the weeks leading up to his USDT conversion “buying and selling multiple coins for personal gain” and attempted one withdrawal to buy a house.
O’Neill “literally gambled with our BTC on Poloniex and he had few good trades,” said another victim of the alleged scam, Kris Zelisko, who invested 1.01 bitcoin in Banana.Fund. “Also, BTC went up in the meantime.”
Prosecutors also allege “Person 1” engaged in a year-long bitcoin laundering scheme that spanned over 40,000 trades and seven different cryptos, and in a two-week spree generated $540,000 in profit from the Banana.Fund pot.
“Person 1” never paid the vast majority of investors back, the prosecutors alleged.
Dutch_Giant said that a number of Banana.Fund users were well aware of the risks involved with “Jo Cook” enterprises. “Cook,” he said, had a track record of operating crowdfunded-oriented website scams that nonetheless paid some investors out.
“It was a reasonably calculated bet,” he said.
Updated: 8-4-2020
Judge Orders Trial In France For Alleged BTC Launderer Alexander Vinnik
Alexander Vinnik, the Russian national accused of laundering 300K Bitcoin through crypto exchange BTC-e, may now face trial in France.
Also awaiting charges in the United States and Russia, suspected Bitcoin money launderer Alexander Vinnik could be facing a trial in France first.
According to news agency Agence France-Presse (AFP), a Paris judge has ordered the Russian national to stand trial for extortion, money laundering, criminal association, and fraudulently accessing and modifying data in data processing systems.
The AFP stated French authorities have accused Vinnik of defrauding more than 100 people out of $160 million between 2016 and 2018.
Vinnik, also known as “Mr. Bitcoin,” is accused of laundering 300,000 Bitcoin (BTC) — roughly $3.4 billion at press time — over the course of six years through crypto exchange BTC-e. He was arrested during a vacation to Greece in 2017 on an indictment from the United States and subsequently extradited to France in January.
Three-Way Tug-Of-War
A Russian national, Vinnik previously requested he be extradited to his home country, where he would reportedly face lesser charges involving defrauding victims out of $11,000.
After his trial in France concludes, Vinnik could be returned to Greece to face extradition to the United States, where authorities reportedly want to question him regarding his connection to the infamous hack of Mt. Gox. Some of the Bitcoin from BTC-e may have come from the now defunct Japanese crypto exchange.
Updated: 8-6-2020
German Police Seize $30M In Crypto From Streaming Site Operator
One of the main operators of the now-shuttered streaming site movie2k.to has forfeited over $30 million worth of crypto to German police.
After a lengthy joint investigation with the American FBI, German police have seized over 25 millions euros worth of cryptocurrency associated with the illegal movie streaming site movie2k.to.
Shuttered in spring 2013 due to copyright infringement concerns, the site’s two main operators are accused of having distributed over 880,000 pirated copies of films, together with their accomplices, via the site between fall 2018 and spring 2013. They have been charged with operating an illegal streaming service, which enabled users to watch pirated films without downloading them.
One of the two, who worked as the site’s programmer, has been in police custody since November 2019.
Streaming site revenue was used to acquire Bitcoin and real estate
On Aug. 3, the Dresden Public Prosecutor’s Office, supported by the State Criminal Police Office in Saxony and the Leipzig Tax Investigation Department announced that the programmer had cooperated in forfeiting over 25 million euros ($29.6 million) worth of Bitcoin (BTC) and Bitcoin Cash (BCH).
Since mid-2012, the two main operators are alleged to have used profits from advertising fees on movie2k.to and subscription revenue to buy large amounts of Bitcoin.
The site’s programmer is alleged to have acquired in excess of 22,000 BTC from this, later using the crypto primarily to acquire various properties via a Berlin real estate firm.
He is also reportedly under suspicion of commercial money laundering in connection with his activities as a real estate entrepreneur in Berlin.
Tracing and identifying the associated Bitcoin was reportedly carried out through joint investigative work between the German Federal Criminal Police Office and the FBI.
The forfeited Bitcoin has been seized as damage reparation by the public prosecutor after their voluntary release by the defendant.
The programmer has now comprehensively confessed to the charges and is reported to be supporting law enforcement authorities in their further investigations into the second main operator, who remains on the run.
As German newspaper Der Spiegel has reported, movie2k.to was — alongside kino.to and neu.to — one of the world’s leading platforms for the distribution of illegal pirated movies for years.
In 2012, the main founder and operator of kino.to was sentenced to a prison term of up to four and a half years.
Updated: 8-6-2020
One Month On, Forsage Continues Despite SEC’s Ponzi Warnings
Forsage members are courting a high risk with the Philippines’ securities regulator.
A full month after the Philippines’ Securities and Exchange Commission flagged Forsage as a likely Ponzi, it remains the second-most popular Ethereum DApp on internet rankings.
As of Aug. 6, Forsage has 390,000 users and a turnover of $3.11 million per 24 hours — despite being marked in dappstat.com rankings as “high risk.”
Speaking to Cointelegraph in July — weeks after the SEC’s official warning — Miguel Cuneta, the co-founder of Phillipine fintech Satoshi Citadel Industries — wrote:
“I received numerous inquiries from friends and family about Forsage and ‘investing’ in Ethereum just within the last month or so. People are posting screenshots of their wallets turning a small amount of money into a large amount of money in a short time.”
“It’s the run-of-the-mill Ponzi scheme using Ethereum, or in the case of the earlier ones that were already busted, Bitcoin, as the ‘product’ they are selling,” Cuneta noted.
“Join by paying X amount of money, and then either do nothing and earn in ETH, or if you want to earn more, recruit three people and let them do the same thing. They use the rising BTC and ETH prices to prove that the investment is really earning. It’s the same formula every single time. Sadly, people are desperate to earn extra income in this pandemic crisis and fall for these schemes more easily,” he said.
Forsage’s Pandemic Tactics
In one recruitment post that remains online as of the time of publication, the author capitalizes on the pandemic crisis to pitch Forsage as a “work from home” smart contract crypto earnings program, which offers investors the chance to “earn a long term residual income” just by recruiting three others.
The pitch attributes the program’s alleged reliability to the inherent properties of smart contracts, citing their automated and “almost unbreakable and unchangeable” qualities.
This purportedly “means that no human being can ever interfere or prevent the intended functioning of the prescribed process, either by bad intention or incompetence.”
Blockchain as a technology designed for decentralized and trustless interactions is thus apparently being exploited to provide an innovative aura for older, fustier forms of investment recruitment schemes.
Cuneta said he believes that “most of these people” involved in propagating the program “are not aware it is a Ponzi scheme and are victims as well.”
Courting A High Penalty
Victims or otherwise, the Philippines’ SEC told Cointelegraph that any of Forsage’s “members and/or representatives that are still actively offering, endorsing, selling and recruiting others to join said illegal scheme despite our prevailing Advisory will be dealt with accordingly.”
Oliver Leonardo, Officer-in-Charge of the SEC’s Enforcement and Investor Protection Department, told Cointelegraph, “We are in the process of gathering information on these representatives to formally file a complaint.”
In the Commission’s view, there is no ambiguity about whether or not Forsage is a violation of national securities laws:
“Forsage’s scheme partakes of the nature of securities through an investment contract which is absolutely within the purview of the SRC [Securities Regulation Code]. That being the case, being decentralized or foreign in nature, as claimed by FORSAGE and its members, does not necessarily imply that its activities are not within the Commission’s jurisdiction considering that it is engaged in investment-taking operations within our country.”
Activities or postings that are intended to recruit others to join a program or invest money are considered as a public offering of investment, requiring prior registration with the SEC, Leonardo wrote.
Any person or entity using Forsage as an “income-generating tool” within the country is therefore within the SEC’s authority and is subject to taxation as well as other applicable laws, notably the Philippines’ 2017 central bank circular containing guidelines for Virtual Currency Exchanges.
The circular is intended to provide a solid framework to regulate the sale or offering of securities “on a limited scale to help raise capital and resources for micro, small and medium-sized local enterprises.”
Forsage, which “appears to offer perpetual or unlimited securities through its smart contract or program, is certainly not exempted” under the central bank’s circular, Leonardo said.
Under Philippine law, a maximum fine of 5 million pesos ($100,000) or imprisonment of 21 years — or both — can be dealt to anyone who acts as salesmen, broker, dealers or agents of entities engaged in unauthorized investment schemes.
“Just A ‘Decentralized’ Financial Fraud”
While appearing to offer securities brings Forsage under registration obligations, as a minimum, the Commission went further in its characterization of the program.
“Based on the foregoing, we wish to make it clear that Forsage is just a ‘decentralized’ financial fraud which depends solely on new investments lured to its referral system for its continuous operation,” Leonardo wrote.
Within what Cuneta characterized as the country’s “very proactive regulatory environment ” for crypto, the SEC has followed up the central bank’s regulatory framework by issuing draft regulations for Digital Asset and Token Offerings as well as proposed Rules for Digital Asset Exchanges.
The Commision has made several interventions by warning the investing public about crypto scams in recent years. It has also issued cease and desist orders and cooperated with the Philippine National Police on arrest warrants for the heads of similar operations.
Despite these precedents and what would appear to be ample deterrents, Cuneta observed that the public health crisis has amplified the existing challenges for taking enforcement action on blockchain scams:
“The issue is that besides the fact that this is supposedly a decentralized platform, the pandemic isn’t making it easy for them to enforce physical action. A lot of movement has been put on hold because priority is on the pandemic on all fronts.”
Updated: 8-13-2020
US DoJ Seizes Millions In Crypto Funds From Al-Qaeda And ISIS Networks
Justice Department announces the largest ever seizure of terrorist-bound crypto assets today in Washington, DC.
Per an Aug. 13 announcement from the United States Department of Justice, the authorities have seized millions of dollars worth of cryptocurrency from over 300 accounts.
The announcement does not specify the specific amount, but does identify the operation as the largest to target terrorist funding in cryptocurrency.
A wide range of agencies including the Department of Homeland Security, the FBI, and the IRS were involved in the campaign. The campaign shut down several websites and Facebook pages that either overtly or, in the case of one fraudulent site selling medical masks, covertly gathered funds for terrorist operations.
According to chief of criminal investigation Don Fort, the IRS used its new crypto tracking capabilities to locate the funds involved:
“IRS-CI’s ability to trace funds used by terrorist groups to their source and dismantle these radical group’s communication and financial networks directly prevents them from wreaking havoc throughout the world.”
It was just over a month ago that the IRS was asking for new tools to monitor privacy coin transactions.
Given that at least one of the images in the DoJ that featured a Bitcoin address belonging to an ISIS affiliate has been floating around government channels for over a year, these are clearly long-term capabilities that the agencies involved have worked to build out.
The U.S. said it seized millions of dollars in cryptocurrency assets and a fake website purporting to sell protective gear in an operation targeting the financial underpinnings of three terrorist groups.
The coordinated law-enforcement action targets the donation networks of al Qaeda and the al-Qassam Brigades, Hamas’s military wing, as well as a scheme to sell N95 respirator masks to U.S. health-care providers by Islamic State in Iraq and the Levant, the U.S. Justice Department said.
The action comes as the U.S. Treasury Department and other federal agencies consider new regulations for the cryptocurrency industry meant to counter terror financing and money laundering and that could mean exchanges and other companies would face steep fines if their platforms are used for illicit finance.
The Justice Department on Thursday unsealed three civil asset-forfeiture complaints in the U.S. District Court for the District of Columbia, which officials said represented the seizure of about 300 cryptocurrency wallets holding about $2 million in assets. Authorities also blacklisted several millions of dollars in other virtual currency assets identified in the investigation that weren’t immediately obtainable, officials said.
One unsealed complaint targets the website FaceMaskCenter.com, which officials said was part of a scheme by an ISIS facilitator to sell fake N95 masks to customers across the globe, including to a customer in the U.S. who sought to purchase the masks and other protective gear for hospitals, nursing homes and fire departments.
Federal prosecutors said they also seized four Facebook pages and four websites used to facilitate the various schemes. Facebook didn’t immediately return a request for comment.
The operation, the largest ever seizure of terrorist organizations’ cryptocurrency accounts, officials said, shows the extent to which terrorist groups have come to rely on cybertools such as virtual currencies to solicit donations to fund their operations.
“These terrorist organizations are no different—apart from their ideology—from other organizations whose main goal is profit,” U.S. Immigration and Customs Enforcement Deputy Director Matthew Albence said Thursday during a conference call with reporters. “Anytime there is a new avenue they can exploit to move money or make money through their criminal enterprises, they are going to utilize it.”
The operation was a coordinated effort by the U.S. attorney’s office in Washington, the Federal Bureau of Investigation, the Internal Revenue Service and the Department of Homeland Security, officials said.
It was sparked in part by public social-media posts by the terrorist groups, they said. In one instance cited by federal prosecutors, a Twitter account identifying itself as the official account of the al-Qassam Brigades asked supporters to “Donate for Palestinian Resistance via Bitcoin.” The group claimed the donations were untraceable.
The Justice Department on Thursday unsealed a criminal complaint against two Turkish nationals whom it said acted as money launderers in the Al-Qassam Brigades scheme by operating an unlicensed money-transmitting business.
Officials also said they are investigating a number of people, including some in the U.S., who donated to the social-media campaigns.
The case could help justify a push by the U.S. Treasury Department and other agencies for tougher regulation of the cryptocurrency sector, including rules meant to counter anonymity and require exchanges and other firms to shoulder the same know-your-customer requirements as the banking industry.
The assets targeted in the complaints unsealed Thursday were seized from numerous virtual currency exchanges. The exchanges cooperated with the U.S. government investigation, officials said.
Updated: 8-18-2020
Researchers Detect Crypto-Mining Worm To Steal AWS Credentials
Cybersecurity researchers now expect future cryptojackers to mimic this worm’s ability to hack Amazon Web Services credentials.
Cybersecurity researchers have detected what they believe to be the first ever stealth crypto mining campaign to steal Amazon Web Services (AWS) credentials.
The mining campaign was described as being relatively unsophisticated by Cado Security in their report on Aug. 17. In total, it seems so far to have only resulted in the attackers — who operate under the name TeamTNT — pocketing a paltry $300 in illicit profits.
What struck the researchers’ attention was the crypto-mining worm’s specific functionality for stealing AWS credentials.
Cado Security understands this as part of a wider trend, showing that hackers and attackers are adapting fast to the rising number of organizations that are migrating their computing resources to cloud and container environments.
Hacking the AWS credentials is relatively simple, the report indicates. TeamTNT’s campaign has moreover recycled some of its code from another worm dubbed “Kinsing,” which is designed to suspend Alibaba Cloud Security tools.
Based on these recycling patterns, the Cado report notes that researchers now expect to see future crypto-mining worms copying and pasting TeamTNT’s code to hack AWS credentials in future.
As is frequently the case with stealth crypto mining campaigns TeamTNT’s worm deploys the XMRig mining tool to mine Monero (XMR) for the attackers’ profit.
Cado Security investigated MoneroOcean, one of the mining pools used by the attackers, and used it to compile a list of 119 compromised systems successfully targeted by the worm.
Stealth cryptocurrency mining attacks are alternately referred to as cryptojacking — an industry term for the practice of using a computer’s processing power to mine for cryptocurrencies without the owner’s consent or knowledge.
This March, Singapore-based unicorn startup Acronis published the results of its latest cybersecurity survey, which revealed that 86% of IT professionals professed concern about the risks posed to their organizations by these attacks.
Updated: 9-2-2020
Ethereum Classic Labs Airs New Plan To Stop Future 51% Attacks
The leading organization supporting the Ethereum Classic network hopes to better safeguard against future 51% attacks by going after platforms that rent out hashing power.
* In a Medium post on Tuesday, Ethereum Classic Labs singled out crypto-mining marketplace NiceHash for allegedly facilitating multiple attacks against the network.
* The firm said it would take “all steps necessary to secure the Ethereum Classic network,” including pursuing “legal action against those who conduct or facilitate malicious attacks.”
* It also plans to bring in law enforcement and engage global regulators to provide “accountability” and “transparency” for hash rentals.
* Malicious actors are claimed to have repeatedly purchased hashrate (computer processing power on the network) from the NiceHash marketplace to execute the so-called 51% attacks.
* A 51% attack on a proof-of-work blockchain occurs when an actor manages to take control of the majority of the network’s hashrate (that is, 51% or more) enabling that person to reorganize (or rewrite) transactions.
* Ethereum Classic has been hit by three such attacks in the last month, resulting in millions of dollars’ worth of its cryptocurrency (ETC) being double spent.
* ETC Labs said is already working with authorities in “relevant jurisdictions,” adding that it will share more information as it becomes available.
* NiceHash is no stranger to controversy, with its former chief financial officer and co-founder Matjaz Skorjanec having been arrested in Germany in late 2019 following U.S. charges that he ran the cybercrime forum Darkode.
* After the first two of the recent attacks caused hashrate to plummet, ETC Labs said in late August it was implementing “a defensive mining strategy” to try and keep levels more consistent.
* While the exact details of the strategy were not revealed at the time due to confidentiality, the initiative failed to stop the third attack.
* The lower the hashrate of a network, the more easy (and affordable) it is to attack.
* ETC’s hashrate has now dropped to its lowest point in over three years – around 1.56 TH/s, according to Ethereum Classic Explorer.
* CoinDesk reached out to ETC Labs for more information on its new legal plan, but had not had a reply by press time.
Updated: 9-6-2020
Electrum Bitcoin Wallet Still Plagued By Known Crypto Phishing Attack
Two new Bitcoin hacks have surfaced recently, showing the Electrum wallet still appears to be troubled by phishing efforts.
Two Electrum software wallet users have recently reported the loss of large sums of Bitcoin (BTC). One victim described the disappearance of 1,400 BTC, totaling $14,595,000 at press time, while another claimed 36.5 BTC, worth $380,512, as stolen. The events appear connected to a long-standing phishing scam affecting Electrum users since 2018.
“Users need to be careful when dealing with their own keys, particularly when they are holding the keys to a wallet with a large amount of cryptocurrency as it makes them attractive to hackers,” Jason Lau, the chief operating officer of crypto exchange OKCoin, told Cointelegraph in response to the 1,400-BTC hack, adding:
“In this incident, it appears that a phishing attack led to the user installing an update that gave the hacker access to the private keys and the funds. Phishing scams are very common across all types of financial applications, and they continue to evolve in levels of sophistication.”
A search through the past
Initial news of a phishing scam impacting the Electrum wallet first hit headlines on Dec. 27, 2018, with nearly $1 million reported stolen. “The hacker setup a whole bunch of malicious servers,” said a Reddit user publicizing the hack.
Essentially, the hacker led users to a malicious webpage via the servers, prompting them to input private data, which, in turn, submitted control of their assets to the nefarious party behind the scheme. The scam also involved a fake wallet update that downloaded malware onto the victims’ devices, a separate Reddit post detailed.
At the time of Cointelegraph reporting in December 2018, the wallet address associated with the scam held 243 BTC. Viewing the address today reveals that 637.44 BTC visited and exited the now-empty wallet.
In the months after the Electrum phishing effort went public, wallet difficulties have continued, including a separate denial-of-service attack that looked very similar to the mentioned 2018 phishing con, also leading victims astray with phony software updates.
Decoding The $14.6-Million Bitcoin Heist
In recent weeks, two additional Electrum wallet users have reported their Bitcoin holdings as stolen. One of the wallet users reportedly suffered a 1,400 BTC loss. “I had 1,400 BTC in a wallet that I had not accessed since 2017,” the victim said in an Aug. 30, 2020, post on GitHub, adding:
“I foolishly installed the old version of the electrum wallet. My coins propagated. I attempted to transfer about 1 BTC however was unable to proceed. A pop-up displayed stating I was required to update my security prior to being able to transfer funds. I installed the update which immediately triggered the transfer of my entire balance to a scammers address.”
Blockchain tracking by Cointelegraph staff showed a likely link between the 1,400 BTC thief, or thieves, and a Binance exchange account, according to a specific transaction ID. The transaction ID, however, involved more than 75 different wallet addresses, a Binance representative told Cointelegraph.
The representative also stated difficulties and gray areas associated with tracking and pegging transactions to foul play due to the nature of crypto and the many parties transacting on a daily basis. “It should not be assumed that flows into a malicious cluster are from an individual/group associated with the campaign, especially if it is a cluster used for receiving funds directly from victims,” the representative added.
Referring to Cointelegraph’s initial reporting on the stolen 1,400 BTC, the representative said: “The account that is the centerpiece for this article was reviewed and no suspicious indicators were found.” Previous Cointelegraph reporting also tracked some of the stolen BTC to Russia, although potential VPN usage voided any definitive conclusion.
“Binance address is upstream of scammer, probably just another victim,” Electrum’s Twitter account posted on Sept. 1 in response to Cointelegraph’s reporting. The tweet also posited the attack as correlated to the 2018 phishing con, adding: “No need to involve Russian Hackers.”
“The peer-to-peer discovery system adopted by Electrum is a design choice to keep the system decentralized, but in this case, it played a part in enabling the hacker to broadcast a fake ‘update your software’ message,” Lau said of the 1,400-BTC hack, adding: “Users should always double-check the authenticity of any wallet client software and take extra vigilance in verifying the source of all updates.”
Revealing Another 36.5-BTC Theft
Shortly after the 1,400-BTC robbery went public, another GitHubber responded to the discussion thread with a similar case they suffered two months prior, as a malicious actor reportedly looted 36.5 BTC from the wallet. Known as Cryptbtcaly on GitHub, the victim tracked the stolen funds to five separate addresses after the heist. “Some of the stolen Bitcoin went to Binance, but they ignore my appeals and do not return,” Cryptbtcaly said on GitHub.
One controversial point in the recent Electrum hacks was that victims were storing large amounts of funds on a software wallet.
A guide from online educational source BitDegree noted software wallets carry the risk of malware and keylogging attacks: “They aren’t as secure as hardware wallets, but they are more convenient to use. This makes them perfect for day to day spending but not ideal for storing large sums of money for a long period of time.”
General industry best practices often steer users toward hardware wallets, such as those provided by Ledger or Trezor. Both companies recently also faced various challenges, although hardware wallets still seemingly appear as the preferred method of crypto storage, all things considered.
Updated: 10-26-2020
Harvest Finance: $24M Attack Triggers $570M ‘Bank Run’ In Latest DeFi Exploit
An arbitrage trade exploiting weak points in decentralized finance (DeFi) protocol Harvest Finance led to some $24 million in stablecoins being siphoned away from the project’s pools on Monday, according to CoinGecko.
According to reports, an attacker used a flash loan – a technique that allows a trader to take on massive leverage without any downside – to manipulate DeFi prices for profit.
The exploit sent the platform’s native token, FARM, tumbling by 65% in less than an hour, followed by the project’s total value locked (TVL), which dropped from over $1 billion before the exploit to $430 million as of press time.
The funds were eventually swapped for bitcoin (BTC), but not before being swept through Ethereum mixing service Tornado Cash.
Mixing the coins didn’t keep the Harvest Finance team in the dark for long. The person behind the exploit “is well-known in the crypto community” after leaving “a significant amount of personally identifiable information,” according to the project’s Discord. All seven bitcoin wallets holding the attacker’s funds are also known.
The anonymous developers behind the project do not want to doxx the party but are instead offering a $100,000 bounty for convincing the attacker to send back the funds.
“For the attacker: you’ve proven your point, if you can return the funds to the users, it would be greatly appreciated by the community, including many bystanders,” the team said via Discord.
Flash Loans Strike Again
The exploit itself was executed by a series of arbitrage trades between DeFi protocols Uniswap, Curve Finance and Harvest Finance, according to Etherscan. The attacker began by taking out a $50 million USDC flash loan from Uniswap.
Then they began swapping between USDC and tether (USDT) to cause the two tokens’ prices to swing wildly.
The price of USDT began to drop on Harvest Finance as the attacker swapped tokens back and forth. The attacker then swapped discounted USDT for stablecoins taken out in the flash loan. The attacker performed the act multiple times. Each successful swap was then turned into ether (ETH) then tokenized bitcoin (WBTC and renBTC, in that order) and then finally BTC, according to Zerion.
Interestingly, some $2.5 million was sent back to the Harvest Finance contract. The developer team said the funds would be distributed pro rata to affected users. The token’s price has slightly rebounded, down 49% in 24 hours to $126.82, according to CoinGecko.
The exploit joins a grouping of similar flash loan–based arbitrage trades conducted against DeFi applications in 2020. For example, lending platform bZx was the first to be hit by a flash loan exploit in February 2020.
Updated: 11-2-2020
Report: Blockchain-Related Hacks Have Declined In 2020
Analysts state that blockchain hacks should remain on the decline.
The amount of cryptocurrency and blockchain-related hacks has been decreasing over the course of 2020, a new report claims.
According to data analyzed by VPN provider Atlas VPN, the number of hacks in the first half of 2020 dropped more than three times compared to the same period in 2019. The data is part of a report released by Atlas VPN on Oct. 28.
According to Atlas VPN, 2019 was a record-breaking year for blockchain hackers that exploited 94 successful attacks in the first half of the year, while in H1 2020 there were 31.
Per the report, 2019 as a whole saw 133 successful attacks on blockchain networks.
Using the historical data, Atlas VPN’s analysts suggested that blockchain hacks will remain on the decline, stating:
“Since 2020 is not over, we can expect more blockchain-related breaches to happen before the end of the year. Nevertheless, based on the historical data, it seems that 2020 will not reach the record heights of last year, and blockchain hacks will remain on the decline.”
According to the report, hackers have stolen $13.6 billion through 330 blockchain-related hacks since 2009. Atlas VPN found that attacks targeting EOS-based decentralized apps, or DApps, were the most successful in terms of the number of breaches. EOS DApps are followed by cryptocurrency exchanges, blockchain wallets and Ethereum blockchain-based DApps, the report noted.
As previously reported, the total volume of cryptocurrency-related fraud and theft resulted in $4.4 billion losses in 2019. In comparison, hackers reportedly stole about $1.7 billion through crypto thefts and scams in 2018.
Updated: 11-30-2020
Bitcoin Theft Is Likely To Surge In Meager Post-COVID Economy: Report
Cybercriminals may favor a different cryptocurrency in the coming months, however.
Cryptocurrency-related fraud and theft are likely to grow in the post-COVID-19 world, according to a new report by cybersecurity and anti-virus provider, Kaspersky Lab.
Securelist, Kaspersky’s cyberthreat research arm, published a report on cyberthreats to financial organizations, forecasting some specific types of financial attacks that are likely to surge in 2021.
Securelist has predicted that a wave of poverty fueled by the COVID-19 pandemic will inevitably lead to “more people resorting to crime including cybercrime.” That could also mean a rise in crimes related to Bitcoin (BTC).
According to Kaspersky’s research arm, Bitcoin is likely to be the most attractive asset for cybercrime because it is the most popular digital asset. The report reads:
“We might see certain economies crashing and local currencies plummeting, which would make Bitcoin theft a lot more attractive. We should expect more fraud, targeting mostly BTC, due to this cryptocurrency being the most popular one.”
Securelist’s researchers also suggested that online perpetrators could switch to more privacy-focused digital assets like Monero (XMR). According to the company, this switch would happen due to increasing “technical capabilities of monitoring, deanonymization and seizing of BTC.” Securelist’s post reads:
“ […] We should expect cybercriminals to switch to transit cryptocurrencies for charging victims. There is a reason to believe they might switch to other privacy-enhanced currencies, such as Monero, to use these first as a transition currency and then convert the funds to any other cryptocurrency of choice including BTC.”
As previously reported by Cointelegraph, crypto-related crimes slowed significantly in 2020, though some crypto sectors (like DeFi) have become new hotbeds for criminal activity. According to a report by VPN firm Atlas VPN, crypto and blockchain-related hacks are likely to continue declining in 2021.
Updated: 11-30-2020
Someone Just Moved $5M In BTC From The 2016 Bitfinex Hack
The exchange’s pilfered funds are on the move once again.
Back in 2016, 119,756 Bitcoin were stolen from the Bitfinex crypto exchange. Some of these coins have continued to move between wallets over the years, including as recently as Monday.
Blockchain data shows that an unknown crypto user has moved 270.97974 Bitcoin (BTC) from a wallet associated with the hack. The sum is worth roughly $5.2 million at time of publication.
The address 1GytseWXyzGpmHkcv9uDzkU9D8pLaGyR5x, which is believed to be associated with the hack, shows less than 0.001 BTC remaining. The BTC were sent to a previously unknown bitcoin address — 3MyXrfSg7JFXLa7bD6YF1GnomEr8EXYRnx, which holds only the transacted amount.
The hackers responsible for the breach have moved only 1-2% of the stolen funds during the four-year interim since the theft took place. Their HODLing strategy appears to be paying off — the haul was worth a mere $72 million at the time, but is now valued at around $2.3 billion.
In June, the thieves transferred 736 BTC from the hack to the Russian darknet marketplace Hydra, with some coins actually ending up back at Bitfinex. Likewise, someone transferred 3,503 BTC from addresses associated with the 2016 Bitfinex hack back in July as well. Coins also moved in October, with 2,900 BTC changing wallets. Various amounts of Bitcoin from the hack have also moved on multiple other occasions.
98% of the stolen funds have remained untouched for four years, however. This may suggest that the hackers have faced difficulties laundering the digital assets as authorities enforce stricter regulations.
Updated: 12-02-2020
CipherTrace Warns Of Surge In Funds Lost To Metamask Phishers
Phishers are coming after MetaMask users in increasingly clever ways.
Cyber Security firm CipherTrace has issued a warning after noting a surge in reports over the past 24 hours of users funds being stolen by a malicious Chrome browser extension posing as popular crypto wallet MetaMask.
The warning was issued under the headline “ALERT: Malicious Crypto Browser Extension—Masked MetaMask” and reported the company had seen “an uptick of alerts and comments within the online cryptocurrency community of users’ funds being stolen.”
In response to online criticism that MetaMask is not doing enough to steer its users away from potentially harmful websites and downloads, MetaMask’s Chief Product Officer Jacob Cantele asked Twitter what more the company should do?
“How can we improve? Currently we’re warning in multiple places within the product, we maintain a phishing detector that warns about tens of thousands of malicious sites, we do regular security marketing campaigns, and we have legal resources to trying to get these sites removed.”
Links to fake MetaMask sites are being inadvertently reposted by cryptocurrency projects and reportedly show up frequently as Google Ads above the first result in Google searches for the term “metamask.”
Phishing warning? @Google is allowing a phisher to buy sponsored ads on their search results. When using crypto, try to use direct links, and if you need to use search, watch out for sponsored links! pic.twitter.com/Fx4WArcH80
— MetaMask (@metamask_io) December 2, 2020
The scam works like this: After arriving at a phishing website that looks just like the real MetaMask site or downloading a malicious browser extension, users are directed to enter their 12 word seed to connect their wallet. The seed is captured by the phisher and the wallet drained of funds.
METAMASK SCAM!
A friend of mine got his account drained. He googled “metamask”, clicked on the 1st link (ad) that came up which prompted him to download the fake metamask plugin. As soon as he installed it everything from his account was drained. Share Retweet! pic.twitter.com/OO9tkq1N6k— Value-Trader (@AbizMind) November 29, 2020
MetaMask stated that the best way to avoid being phished is to download the software only from its official site, or from inside the Google Chrome store, but never by clicking links on other websites.
For those who already have the MetaMask Chrome extension installed, MetaMask will display a warning in bright red if a user attempts to visit a website previously reported as a phishing site.
MetaMask users who are unsure if a website has been reported as malicious are encouraged to visit CryptoScamDB and enter the website URL or IP address where it will be cross-referenced against a database of reported scam and phishing websites.
In October, MetaMask announced that it had surpassed one million active users on a monthly basis, largely thanks to the acceleration of the DeFi trend over the summer and fall. Rising Ether prices and a large user base suggest this type of phishing attack won’t be going away anytime soon.
Updated: 12-07-2020
Paris Court Sentences Alexander Vinnik To Five Years In Prison
Years after his initial arrest, Vinnik has finally been sentenced.
After years of extradition debates, Bitcoin (BTC) launderer Alexander Vinnik has finally been sentenced by a French court.
According to a report on Monday by Novaya Gazeta, Vinnik has been sentenced to five years in prison for “money laundering as part of an organized criminal group and providing false information about the origin of the proceeds” in addition to a fine of 100,000 euro ($121,000).
According to the BBC, the court partially dropped charges related to the ransomware known as Locky. As of publishing time, online reports do not specify whether Vinnik’s sentence is related to his alleged senior role at now-defunct crypto exchange BTC-e.
Vinnik previously denied his involvement at BTC-e, reportedly claiming that he was just an employee. He said that his monthly salary at BTC-e amounted to 10,000 euro.
As previously reported, Vinnik is allegedly the mastermind behind an international money-laundering scheme that processed over $4 billion worth of capital flows through BTC-e.
Colloquially known as “Mr. Bitcoin,” Vinnik was first arrested in Greece in July 2017 for allegedly taking part in the operations of BTC-e. Since the arrest, a number of jurisdictions have sought Vinnik’s extradition, including the United States and Russia, where Vinnik is a citizen. Vinnik was extradited to France in 2018 on charges of fraud and money laundering.
In June, the New Zealand police reportedly recovered $90 million connected to the case against Vinnik.
Updated: 12-14-2020
How Hackers Bled 118 Bitcoins Out of Covid Researchers In U.S.
Transcripts reveal University of California at San Francisco’s weeklong negotiation to free its ransomware-locked servers. The haggling worked, sort of.
The negotiator entered the chatroom four days after the attack. Hackers had locked down several servers used by the epidemiology and biostatistics department at the University of California at San Francisco, and wanted a $3 million ransom to give them the keys. On Friday, June 5, at 6:50 p.m., they directed a UCSF negotiator to a webpage on the dark web—meaning beyond the realm of Google—that listed a dozen or so sets of apparent victims and demands.
The whole thing looked oddly like a customer service portal. Just below the university’s entry was a flashing red timer counting down to a payment deadline. It read: 2 days, 23 hours, 0 minutes. If the counter reached zero, the ransom message said, the price would double.
In a secure chat that the hackers set up with a digital key, the UCSF negotiator said the attack couldn’t have come at a worse time. The department was racing to try to help develop some kind of treatment or vaccine for Covid-19, the negotiator said, and hinted that the researchers hadn’t taken the time to duly back up their data.
“We’ve poured almost all funds into COVID-19 research to help cure this disease,” the anonymous negotiator typed in the chat, pleading something between poverty and force majeure. “That on top of all the cuts due to classes being canceled has put a serious strain on the whole school.”
The hackers’ representative, who went by the handle Operator, said a school that collects more than $7 billion in revenue each year, one with negotiators, lawyers, and security consultants on hand, should be good for a few mil. “You need to understand, for you as a big university, our price is shit,” Operator said.
“You can collect that money in a couple of hours. You need to take us seriously. If we’ll release on our blog student records/data, I’m 100% sure you will lose more than our price what we ask.” By that time, the hackers had shared a sample of data from the stolen servers indicating that they did indeed have sensitive material.
Bloomberg Businessweek received a complete transcript of the chat between Operator and the UCSF negotiator from a person with access to the chat’s digital key. Such keys tend to be distributed to members of the internal crisis response team, law enforcement, and private consultants. The university confirmed the breach but said the transcript shouldn’t be taken at face value because “the statements and claims made by either party were in the context of a negotiation.”
Whatever its exaggerations, the transcript provides a rare look into the kinds of secretive ransomware attacks usually portrayed impersonally through FBI statistics, regulatory filings, and official statements. (Victims don’t usually like to admit that hackers beat their security, or that they paid off the crooks.)
With the affect of a used-car salesman, Operator—probably based somewhere safely out of reach of U.S. law enforcement—led a negotiation that bore a lot of similarities to an old-school, flesh-and-blood kidnapping. The main difference was that the hackers he represented had swiped data, not people.
In some ways, Covid-19 has turbocharged the ransomware business that has proliferated, especially in Russia and Eastern Europe, over the past several years.
The pandemic has made high-value targets out of universities, hospitals, and labs with access to data that are used to analyze new potential treatments or document the safety of vaccine candidates. ( Recent victims include Hammersmith Medicines Research, which conducts clinical trials for new medicines, and antibodies researcher 10X Genomics Inc., though Hammersmith says it repelled the attack and 10X says its business suffered no substantive impact.)
It has also offered a bit of a coming-out party for some of the many ransomware groups that spent 2019 trying to professionalize their operations with a faux-corporate business model, complete with press releases, public websites, and even statements laying out ethical standards.
There’s more at stake in this calculus than just garden-variety scams, too. The U.S. Department of Justice has said that Chinese state-sponsored hackers are targeting global institutions conducting coronavirus research in order steal data that might lead their country more quickly to a vaccine.
The DOJ investigation resulted in the July indictment of two hackers linked to Chinese state security for attacking computer systems connected to Covid-19 research. In the U.K., the National Cyber Security Centre documented a surge in state-sponsored attacks on British research institutions focused on Covid-19, and attributed much of that increase to Russia, Iran, and China.
UCSF hasn’t linked the attackers—whose English was littered with grammatical tics common among native Russian speakers—to any foreign state actors. The university said in a statement following the hack that the attack didn’t hurt its Covid-19 work, although the lost data were “important to some of the academic work we pursue as a university serving the public good.” (The FBI, which typically handles U.S. ransomware cases, referred questions about the hack to the university.)
During the standoff, the negotiator told the hackers that the university didn’t know what was on the locked computers. Yet the transcript suggests that whatever the data were, the university was desperate to account for it.
According to the hackers’ dark web blog, the ransomware used to attack UCSF came from Netwalker, a hacking operation that has boomed since last fall. Netwalker malware can be leased by would-be attackers as a kind of franchise program. In March, the group posted a dark web want ad to recruit new affiliates.
The qualifications included: “Russian-speaking network intruders—not spammers—with a preference for immediate, consistent work.” In June, a further ad prohibited English speakers from applying, according to Cynet, a digital security company in Tel Aviv.
Although ransomware gangs have seized the pandemic as an opportunity, they tend to play a certain amount of Good Cop, too. In a March 18 press release, a big ransomware group known as Maze offered victims in the medical industry “exclusive discounts” on ransoms.
In a blog post the following month, the group declared, “We are living in the same economic reality as you are. That’s why we prefer to work under the arrangements and we are ready to compromise.” (There’s no evidence that Maze ever provided any such discounts.)
UCSF had no way of knowing with any certainly whether the hackers would deliver on their promise to restore the locked-down computers upon payment, a risk inherent in ransomware attacks. Some corporate victims hire professional negotiators in the hope that they’ll be better able to guarantee a happy ending while saving a few bucks. Others try to work it out themselves.
UCSF said in its statement that it chose to retain a private consultant to support the “interaction with the intruders,” but declined to identify a company or individual.
With 2 days, 22 hours, and 31 minutes on the clock, the UCSF negotiator asked for a two-day extension so that “the university committee that makes all the decisions” could meet again. This is a common tactic for victims exploring their options before resorting to payment, but somewhat surprisingly given the school’s lack of leverage, the hackers agreed—on the condition that the school double its payoff to $6 million.
“I expected Operator to say, ‘You know you’re under attack, right?’ There are no weekends off in a cyberattack,” says Moty Cristal, an experienced ransomware negotiator in Tel Aviv who reviewed the transcript. “But in this case, the bad guys were almost enjoying the conversation. It was part of the game.”
Playing for time can help ransomware victims better evaluate the threats to their networks and data. Kevin Jessiman, chief information officer for Price Industries, a Canadian air ventilation manufacturer, says the negotiator his company hired last year enabled his team to diagnose the hack they’d suffered and explore their options.
“Once we were confident that enough of our system could be restored, we ceased correspondence,” says Jessiman, adding that Price stopped talking to the attackers in about 36 hours. Even though the cost of restoring and updating its security system was millions of dollars greater than the ransom demand, he says, Price declined to pay the crooks.
UCSF figured out that its hackers had managed to encrypt data on as few as seven servers, according to a person familiar with the investigation, who spoke on condition of anonymity for fear of retaliation. The attackers had copied at least 20 gigabytes of data from the machines, and so had some idea what they contained.
Throughout the negotiations, the university representative was careful to ply Operator with compliments. Experts say that while this is a transparent, 101-level negotiating strategy, it also works. “I’m willing to work this out with you, but there has to be mutual respect.
Don’t you agree?” said the negotiator, according to the transcript. “I have read about you on the internet and know that you are a famous ransomware hacker group and very professional. I know you will honor your word when we agree on a price, right?”
These appeared to be magic words. “We are 100% about respect, never we will disrespect a client who talk to us with respect,” said Operator. “Do not offer anything ridiculous.” So naturally, the negotiator’s first offer was something close to ridiculous. The committee “said that I can submit a request for the max amount of $780,000, but I’d be lucky if I got even half of it.”
The hacker scoffed at $390,000. This was such an insulting offer, Operator said, that the hacking group threatened to blow the whistle on UCSF’s loss of student and faculty data to the Federal Trade Commission. “I suggest you re-consider another offer and this time, a serious one.”
It was an empty threat, and the negotiator called Operator’s bluff. “The FTC is not a concern for us. We would just like to unlock our computers to get our data back. I know you want to make a lot of money here, I get it, but you need to understand that we don’t have this much cash sitting around,” the negotiator said.
It was 10:46 p.m. on June 9 in San Francisco, and the two had been talking for four days.
Dragging out the negotiations might have been helpful to the hackers, too, says Cristal, the ransomware negotiator, who adds that in Covid-era attacks, there’s more at stake than money. Time to examine their bounty might have allowed Operator’s team to identify lucrative research or intellectual property worth auctioning off. Attackers affiliated with a large-scale criminal enterprise such as Netwalker may also have their own bureaucracy to wade through, Cristal says.
After standing pat at $390,000 for a day, the UCSF negotiator came back with an offer of $780,000. Operator wasn’t impressed. “Keep that $780k to buy Mc Donalds for all employees. Is very small amount for us. I am sorry,” the hacker said.
“How can I accept $780,000? Is like, I worked for nothing.”
At this point, the negotiations became highly emotional, even personal. “I hope you know that this is not a joke for me,” the negotiator replied. “I haven’t slept in a couple of days because I’m trying to figure this out for you. I am being viewed as a failure by everyone here and this is all my fault this is happening.”
“The longer this goes on, the more I hate myself and wish this were to end one way or another,” the negotiator added. “Please sir, what can we work out?”
There’s no real evidence that this was anything more than a negotiating tactic. For that matter, it’s unclear whether either party was really a single person; both could just as easily be several people working in shifts. Still, Operator played along: “My friend, your team needs to understand this is not your failure. Every device on the internet is vulnerable.”
The UCSF representative responded, “I hear you and thank you for thinking I’m [not] a failure. I wish others here would see the same thing.”
The next morning, June 9, UCSF offered just over $1 million. Operator countered with $1.5 million. With both sides perhaps sensing that a deal was close, the university’s negotiator played one last card: “The good news that I wanted to share is that a close friend of the school knows what’s going on and has offered to help and donate $120k to help us.
We normally can’t accept these donations, but we’re willing to make it work only if you agree to end this quickly. Can we please end this so we both can finally get some good sleep?”
That was good enough for Operator, who responded, “When can you pay?” The two had been talking for almost six days.
The negotiator and Operator had an agreement: $1.14 million, worth about 116 Bitcoin. UCSF would spend another day and a half clearing the deal on its side and buying the Bitcoin.
Along with access to the decryption key, the deal included a commitment by the hackers to transmit all the data they had stolen from the university’s network, presumably so UCSF could determine what data the hackers had in their possession and could possibly sell. It would take the attackers almost two nerve-wracking days to decrypt, transmit, and show they’d deleted their copies of the files, but they would deliver at 2:48 a.m. on June 14.
With the deal done, Operator indulged a little professional curiosity about who had really been sitting at the other keyboard, asking, “Which recovery company are you?” The negotiator didn’t answer.
Updated: 12-18-2020
Vinnik’s Attorney Appeals Against 5-Year Prison Sentence
Lawyers of the alleged $4 billion Bitcoin launderer appeal to the court, arguing that Alexander Vinnik was just an employee at BTC-e.
The defense team of Alexander Vinnik, an alleged Bitcoin launderer who was sentenced to a five-year prison term, disagrees with the court’s decision.
According to a Dec. 18 report by Russian news agency Kommersant, Vinnik’s attorney Frederic Belot has appealed the French court’s judgement, arguing that the defendant was not involved in any money laundering operations.
Citing a Dec. 6 judgement charging Vinnik for “money laundering as part of an organized criminal group,” Belot emphasized that no “criminal group” consists of one person. “The court did not name a single name even supposedly belonging to this group,” Belot reportedly said.
According to Belot, Vinnik was rather a victim of his anonymous “employers” at now-defunct crypto exchange BTC-e, as his involvement in managing the platform has not been proved: “Vinnik was just a full-time trader and he did not participate, at least consciously, in any money laundering operations,” Belot declared.
Vinnik’s defense expects the court to hear the appeal in four months, Belot noted. Lawyers also argued that the judgement by the Paris court was based on an investigation subject to interference from United States intelligence agencies. According to the report, Vinnik faces a 50-year prison term in the U.S. in the event of potential extradition.
Colloquially known as “Mr. Bitcoin,” Vinnik is the convicted creator of a global illegal scheme that laundered over $4 billion worth of capital flows through BTC-e. More than three years after his arrest in Greece, Vinnik’s trial finally happened in early December 2020. Vinnik previously denied his involvement at BTC-e, claiming that he was just an employee at the firm.
Updated: 12-23-2020
Notorious Crypto Figures Arrested In 2020
Despite the crypto industry experiencing a major rise in mainstream interest in 2020, the year also saw many prominent crypto personnel apprehended by regulators.
Over the past year, many prominent and colorful crypto personalities have been apprehended and arrested. From the jailing of antivirus pioneer John McAfee to the laying of charges against executives from one of the world’s largest exchanges, 2020 didn’t exactly shake off crypto’s reputation as a honeypot for criminals.
Over the first ten months of 2020, blockchain forensics company CipherTrace estimates that losses from thefts, hacks, and frauds totalled a whopping $1.8 billion, a figure fueled in part by the rise of various DeFi platforms.
The report suggests that 2020 is on track to record the second-highest value in losses linked to cryptocurrency crimes, trailing 2019, when proceeds of those crimes exceeded $4.5 billion.
Let’s take a closer look at some of the highest-profile figures embroiled in legal issues this year.
Arthur Hayes Goes Missing Following DoJ Charges
On Oct. 1, the United States Department of Justice (DoJ) filed criminal charges against BitMEX founder Arthur Hayes as well as three of his associates for violating the Bank Secrecy Act. Compounding their problems, the US Commodity Futures Trading (CFTC) filed a civil enforcement action against Hayes and his company for flouting AML regulations.
The Hong Kong resident has been MIA in public since and is yet to resurface. But in a stroke of good fortune for Hayes, he might not be compelled to face the music anytime soon, as the United States and Hong Kong have suspended their extradition agreements in light of the recent political turmoil there.
The DoJ alleged that BitMEX had been engaged in a variety of shady activities and had weak Anti-Money Laundering (AML) and Know Your Customer (KYC) policies that could easily be misused by third-party actors.
BitMEX was also accused of operating a complex international corporate structure with offices in premium international destinations such as New York, Hong Kong while claiming to be registered and based out of Seychelles.
After the news broke BitMEX announced the departure of Hayes as the company CEO, along with chief technical officer Samuel Reed and the head of business development Greg Dwyer.
‘Star’ Xu’s Mysterious Absence Explained
Prominent cryptocurrency exchange OKEx copped a lot of flak after it suspended crypto withdrawals on Oct. 16, effectively barring customers from taking out their crypto holdings.
Reports surfaced that the suspension was related to the exchange’s Chinese co-founder Mingxing “Star” Xu being arrested by local authorities — although the exchange vigorously denied that was the issue.
After being unreachable for more than thirty days, Xu finally made a media appearance on WeChat on Nov. 19. He revealed that he’d been assisting relevant authorities investigating OK Group’s “backdoor listing in 2017” in which the exchange had sought to partner with an “undisclosed third party entity” so as to make its offerings available to clients all over the world.
Xu indicated that after having looked at his prior business engagements, investigators had finally clarified the matter and given him the all clear.
After a month, OKEx finally re-enabled crypto withdrawals on Nov 27.
John Mcafee’s Spanish Cruise Comes To An Abrupt End
Tech savant, crypto evangelist, and eccentric millionaire John McAfee has been leading the crypto hype train for what feels like time immemorial now. In 2017, he famously proclaimed that within 36 months, Bitcoin would hit a price of $1 million or he’d “eat my d**k on national television.” He retracted his statement earlier this year to the relief of most people.
McAfee was detained in Barcelona by local authorities in October in regard to tax evasion charges levied by the US government against him. He was also charged over fraudulently promoting a series of questionable cryptocurrency projects, from which he allegedly profited millions of dollars.
Prosecutors claim that McAfee failed to file his tax returns for four years running, even while he raked in millions of dollars from his consulting work, speaking engagements, digital currency investments, etc.
According to a statement released by the US Justice Department, McAfee illegally siphoned his income from various bank accounts and cryptocurrency exchange accounts in the names of different nominees. He is also accused of not declaring a number of expensive assets including a yacht and real estate.
This is not the first time McAfee has been in trouble with the law. Back in 2012, he was questioned by police after his name was linked with the death of his neighbor, Florida businessman Gregory Faull. In 2019 he was ordered to pay $25 million in a wrongful death lawsuit filed by the estate, but refused, saying:
“I have not responded to a single one of my 37 lawsuits in the past 11 years.”
If convicted of the new charges, he could face up to 30 years in prison.
Santiago Fuentes’ Billion-Dollar Scheme Collapses
Spanish national, Santiago Fuentes, was the operator of a cryptocurrency arbitrage firm called Arbistar which had tens of thousands of users investing Bitcoin into its arbitrage trading bot. Blockchain investigations firm Tulip Research reported that since its inception, the firm had raised more than $1 billion in Bitcoin.
Suspicions arose in September when Fuentes claimed that due to a “digital error”, Arbistar’s native trading module had been somehow disabled, wiping out more than a quarter of the company’s funds overnight.
In the course of their investigations, Spanish authorities determined that Fuentes had been making use of his crypto outfit to allegedly facilitate various financial frauds and to launder money. Tulip Research traced back some of Arbistar’s withdrawal activity to a deep web marketplace called ‘Hydra’.
Fuentes was arrested in October and has been charged with financial fraud and money laundering. On Dec. 13 lawyers representing 130 former clients said they’d lost 4 million euros ($4.86M) between them, with Spanish media suggesting that in total, 32,000 people had lost 93.4 million euros ($113.5M).
Matthew Piercey’s Daring Sea Scooter Escape
The 44-year-old Shasta County, California man was arrested by the FBI on Nov 16. while trying to flee from authorities using a sea scooter.
Local media outlets reported that Piercey was able to evade agents for over an hour by first speeding off in a truck and then abandoning the vehicle on the edge of Lake Shasta where he used a sea scooter — an underwater mobile device that can typically reach a maximum speed of 5mph — to continue to evade police underwater for 25 minutes. He was arrested when he emerged.
Police allege that Piercey solicited $35 million for crypto mining and other investments through Family Wealth Legacy LLC and Zolla Financial LLC.
The two firms reportedly targeted wealthy investors, obtaining a minimum of $50,000 from each client. However Piercey reportedly admitted that he had little to no understanding of cryptocurrencies.
He reportedly spent $2.5 million obtained via his schemes, renovating two of his homes and paying off his credit card bills. He is now currently facing multiple charges of wire fraud, mail fraud, money laundering and witness-tampering. If found guilty, Matthew could face life in prison.
Harpreet Singh Sahni Is Brought Down By Indian Sleuths
Over the years, Sydney-based socialite and concert promoter Harpreet Sahni built a reputation as a man who regularly rubbed shoulders with Australia’s elites including ex-Prime Minsters such as Tony Abbott and Julia Gillard, the former Premier of New South Wales Mike Baird, and former cricketer Glenn McGrath.
But in October, Indian police authorities claimed that Sahni and his close aides had allegedly swindled around $50 million from clients. He was promoting a scheme called “Plus Gold Union Coin” (PGUC), which promised to deliver profits ranging between $5,000 to $8,000 per day to backers.
Investors who tipped around $7,000 in PGUC, were told they could potentially rake in more than $100,000 within a year. Investors had to lock into a 12-month contract during which they couldn’t cash out their crypto holdings. However, as PGUC’s popularity grew, token holders began to grow suspicious.
The PGUC website would go offline for weeks at a time and when the currency plummeted, there was no way for investors to minimize their losses or withdraw their assets. The invested money — estimated to be around $50 million — disappeared, with all correspondence stopped with clients.
Sanhi now faces roughly 24 years in prison and is awaiting his sentencing.
Conor Freeman’s Million-Dollar Bitcoin Ploy
The US Department of Homeland Security identified Dublin-based IT professional Conor Freeman as the man behind a theft involving more than $2 million worth of crypto. He was arrested by Homeland Security officials on Nov. 16 and forced to hand over more than 142 Bitcoin.
Freeman was reportedly working with a group able to gain access to the email addresses and phone numbers of victims via various social media platforms. They also had contacts inside the telecom industry, enabling them to initiate sophisticated SIM-swap attacks.
That’s where a scam artist is able to obtain a SIM card that is directly linked to their victim’s mobile number, enabling them to gain access to an individual’s 2FA messages and One Time Passwords that are used to validate identities and approve larger financial transactions.
Freeman pleaded guilty to stealing cryptocurrencies worth $1.92 million from Emmy award-winner Seth Shapiro — producer of The Game Changers, The Chosen One — as well as illegally obtaining an additional $250,000 from two other victims, Michael Templeman and Darran Marble.
The Entire Plustoken Team
Earlier this year in July, Chinese police took 109 people into custody in connection with the Plustoken Ponzi scheme. Twenty seven of them — including Chen Bo, Luu Jianghua, Lu Jianghua, Lu Qinghai, Jin Xinghai, Wang Yin, and Zhang Qin — were allegedly the scheme’s masterminds, while the remaining 82 people arrested held smaller roles within the organization.
The Plustoken scam raked in an estimated $5.7 billion from more than two million investors. Based out of China, the project presented itself as being a cryptocurrency wallet that provided high returns if users purchased PLUS tokens with either BTC or ETH.
In 2019, key members moved large amounts of crypto out of the platform, with 25,000 BTC sent to various addresses including Bitcoin mixers between Feb and March and in June, 789,534 ETH was transferred from the firm’s coffers.
However, by the end of the year, the entire scheme had been exposed, and by July 2020, the project had been taken down by Chinese police.
In November the Jiangsu Yancheng Intermediate People’s Court revealed that authorities had confiscated 194,775 BTC, 833,083 ETH, 487 million XRP, 79,581 BCH, 1.4 million LTC, 27.6 million EOS, 74,167 DASH, 6 billion DOGE and 213,724 USDT — estimated to be worth $4 billion. Earlier this month Chen Bo and 13 of his co-conspirators were sentenced to jail terms ranging between two and 11 years.
Updated: 12-28-2020
Cover Protocol Suffers Infinite Minting Attack, Price Tanks 97%
Cover, the peer-to-peer coverage market, is the latest DeFi project to suffer an attack.
A suspected hacker has exploited the Cover staking protocol, inflating the token supply by printing over 40 quintillion “coins”
However, in a surprising move, the suspected attacker returned the funds with a note saying: “Next time, take care of your own shit.”
In the initial exploit, the attacker liquidated over 11,700 coins on the 1inch decentralized exchange aggregator after inflating the token supply according to data from the Ethereum wallet explorer Nansen. In total, the rogue actor drained more than $5 million from the project as of press time.
Cover Protocol Released Addressed The Incident In A Message Posted On Its Discord Group, Stating:
“The Blacksmith farming contract has been exploited to mint infinite $COVER tokens. We have restricted minting access to the farming contract in order to stop the attacker. If you are providing liquidity for $COVER token (uniswap or sushiswap) please remove it immediately.”
According to the Cover Protocol team, the issue only affected the token supply with funds held in “claim/noclaim” pools still safe. The project says it is investigating the incident.
The attack caused a massive decline in the COVER token price, falling by more than 97% while also eliciting negative comments from a cross-section of the crypto community on social media. Back in November, Cover was one of the DeFi protocols to merge with Yearn.Finance.
Monday’s incident makes the Cover the latest DeFi project to suffer a malicious exploit in a year ridden with opportunistic profiteering attacks against numerous protocols.
As previously reported by Cointelegraph, the spate of DeFi hacks throughout the year stand out as one of the major disappointments in the crypto space for 2020 with data manipulation deemed as being easy to accomplish on many projects.
Updated: 2-11-2021
A Crypto Kid Had A $23,000-A-Month Condo. Then The Feds Came
Stefan Qin was just 19 when he claimed to have the secret to cryptocurrency trading.
Buoyed with youthful confidence, Qin, a self-proclaimed math prodigy from Australia, dropped out of college in 2016 to start a hedge fund in New York he called Virgil Capital.
He told potential clients he had developed an algorithm called Tenjin to monitor cryptocurrency exchanges around the world to seize on price fluctuations. A little more than a year after it started, he bragged the fund had returned 500%, a claim that produced a flurry of new money from investors.
He became so flush with cash, Qin signed a lease in September 2019 for a $23,000-a-month apartment in 50 West, a 64-story luxury condo building in the financial district with expansive views of lower Manhattan as well as a pool, sauna, steam room, hot tub and golf simulator.
In reality, federal prosecutors said, the operation was a lie, essentially a Ponzi scheme that stole about $90 million from more than 100 investors to help pay for Qin’s lavish lifestyle and personal investments in such high-risk bets as initial coin offerings.
At one point, facing client demands for their money, he variously blamed “poor cash flow management” and “loan sharks in China” for his troubles. Last week, Qin, now 24 and expressing remorse, pleaded guilty in federal court in Manhattan to a single count of securities fraud.
“I knew that what I was doing was wrong and illegal,” he told U.S. District Judge Valerie E. Caproni, who could sentence him to more than 15 years in prison. “I deeply regret my actions and will spend the rest of my life atoning for what I did. I am profoundly sorry for the harm my selfish behavior has caused to my investors who trusted in me, my employees and my family.”
Eager Investors
The case echoes similar cryptocurrency frauds, such as that of BitConnect, promising people double-and triple-digit returns and costing investors billions. Ponzi schemes like that show how investors eager to cash in on a hot market can easily be led astray by promises of large returns. Canadian exchange QuadrigaCX collapsed in 2019 as a result of fraud, causing at least $125 million in losses for 76,000 investors.
While regulatory oversight of the cryptocurrency industry is tightening, the sector is littered with inexperienced participants. A number of the 800 or so crypto funds worldwide are run by people with no knowledge of Wall Street or finance, including some college students and recent graduates who launched funds a few years ago.
Qin’s path started in college, too. He had been a math whiz who planned on becoming a physicist, he told a website, DigFin, in a profile published in December, just a week before regulators closed in on him. He described himself on his LinkedIn page as a “quant with a deep interest and understanding in blockchain technology.”
In 2016, he won acceptance into a program for high-potential entrepreneurs at the University of New South Wales in Sydney with a proposal to use blockchain technology to speed up foreign exchange transactions. He also attended the Minerva Schools, a mostly online college based in San Francisco, from August 2016 through December 2017, the school confirmed.
Crypto Bug
He got the crypto bug after an internship with a firm in China, he told DigFin. His task had been to build a platform between two venues, one in China and the other in the U.S., to allow the firm to arbitrage cryptocurrencies.
Convinced he had happened upon a business, Qin moved to New York to found Virgil Capital. His strategy, he told investors, would be to exploit the tendency of cryptocurrencies to trade at different prices at various exchanges. He would be “market-neutral,” meaning that the firm’s funds wouldn’t be exposed to price movements.
And unlike other hedge funds, he told DigFin, Virgil wouldn’t charge management fees, taking only fees based on the firm’s performance. “We never try to make easy money,” Qin said.
By his telling, Virgil got off to a fast start, claiming 500% returns in 2017, which brought in more investors eager to participate. A marketing brochure boasted of 10% monthly returns — or 2,811% over a three-year period ending in August 2019, legal filings show.
His assets got an extra jolt after the Wall Street Journal profiled him in a February 2018 story that touted his skill at arbitraging cryptocurrency. Virgil “experienced substantial growth as new investors flocked to the fund,” prosecutors said.
Missing Assets
The first cracks appeared last summer. Some investors were becoming “increasingly upset” about missing assets and incomplete transfers, the former head of investor relations, Melissa Fox Murphy, said in a court declaration. (She left the firm in December.) The complaints grew.
“It is now MID DECEMBER and my MILLION DOLLARS IS NOWHERE TO BE SEEN,” wrote one investor, whose name was blacked out in court documents. “It’s a disgrace the way you guys are treating one of your earliest and largest investors.”
Around the same time, nine investors with $3.5 million in funds asked for redemptions from the firm’s flagship Virgil Sigma Fund LP, according to prosecutors. But there was no money to transfer. Qin had drained the Sigma Fund of its assets. The fund’s balances were fabricated.
Instead of trading at 39 exchanges around the world, as he had claimed, Qin spent investor money on personal expenses and to invest in other undisclosed high-risk investments, including initial coin offerings, prosecutors said.
So Qin tried to stall. He convinced investors instead to transfer their interests into his VQR Multistrategy Fund, another cryptocurrency fund he started in February 2020 that used a variety of trading strategies — and still had assets.
‘Loan Sharks’
He also sought to withdraw $1.7 million from the VQR fund, but that aroused suspicions from the head trader, Antonio Hallak. In a phone call Hallak recorded in December, Qin said he needed the money to repay “loan sharks in China” that he had borrowed from to start his business, according to court filings in a lawsuit filed by the Securities and Exchange Commission.
He said the loan sharks “might do anything to collect on the debt” and that he had a “liquidity issue” that prevented him from repaying them.
“I just had such poor cash flow management to be honest with you,” Qin told Hallak. “I don’t have money right now dude. It’s so sad.”
When the trader balked at the withdrawal, Qin attempted to take over the reins of VQR’s accounts. But by now the SEC was involved. It got cryptocurrency exchanges to put a hold on VQR’s remaining assets and, a week later, filed suit.
Asset Recovery
By the end, Qin had drained virtually all of the money that was in the Sigma Fund. A court-appointed receiver who is overseeing the fund is looking to recover assets for investors, said Nicholas Biase, a spokesman for Manhattan U.S. Attorney Audrey Strauss. About $24 million in assets in the VQR fund was frozen and should be available to disperse, he said.
“Stefan He Qin drained almost all of the assets from the $90 million cryptocurrency fund he owned, stealing investors’ money, spending it on indulgences and speculative personal investments, and lying to investors about the performance of the fund and what he had done with their money,” Strauss said in a statement.
In South Korea when he learned of the probe, Qin agreed to fly back to the U.S., prosecutors said. He surrendered to authorities on Feb. 4, pleaded guilty the same day before Caproni, and was freed on a $50,000 bond pending his sentencing, scheduled for May 20.
While the maximum statutory penalty calls for 20 years in prison, as part of a plea deal, prosecutors agreed that he should get 151 to 188 months behind bars under federal sentencing guidelines and a fine of up to $350,000.
That fate is a far cry from the career his parents had envisioned for him — a physicist, he had told DigFin. “They weren’t too happy when I told them I had quit uni to do this crypto thing. Who knows, maybe someday I’ll complete my degree. But what I really want to do is trade crypto.”
The case is U.S. v Qin, 21-cr-75, U.S. District Court, Southern District of New York (Manhattan)
Updated: 2-12-2021
T-Mobile Sued By Victim Who Lost $450K In Bitcoin In SIM Swap Attack
The wireless carrier is accused of failing to protect its customers from SIM swappers’ lucrative heists.
Telecoms provider T-Mobile has become the latest corporate name to come under fire for its alleged negligence and failure to protect customer information, which indirectly enabled a “SIM swap attack” that led to the successful theft of $450,000, or 15 Bitcoin (BTC).
A SIM swap attack — also referred to as a port-out scam — has proved to be a popular tactic with criminals in recent years. Such an attack involves the theft of a victim’s cell phone number, which can then be used to hijack the victim’s online financial and social media accounts by intercepting automated messages or phone calls that are used for two-factor authentication security measures.
The lawsuit filed against T-Mobile on Feb. 8 in the Southern District of New York by plaintiff Calvin Cheng — the victim who alleges he lost $450,000 in Bitcoin following such an attack — explains exactly how it is that telecoms firms come to play such a crucial role in this particular kind of fraud:
“A criminal third-party convinces a wireless carrier like T-Mobile to transfer access to one of its legitimate customers’ cellular phone number from the legitimate customer’s registered SIM-card […] to a SIM-card controlled by the criminal third party […] This sort of account takeover is not an isolated criminal act, per se, as it requires the wireless carrier’s active involvement to swap the SIM to an unauthorized person’s phone.”
The incident at issue in the lawsuit occurred, according to Cheng, after a SIM-swap was successfully carried out in May 2020 against a T-Mobile customer and co-founder of crypto-focused investment fund Iterative Capital, Brandon Buchanan.
Cheng had conducted several successful transactions with Iterative to purchase Bitcoin in the months prior to the incident, communicating with Buchanan and others in Iterative via Telegram and using a crypto exchange administered by the fund.
After the SIM-swap, the perpetrators allegedly impersonated Buchanan on a Telegram chat with Cheng, reaching out to him asking him whether or not he wanted to sell Bitcoin for an Iterative client at an attractive premium.
Having been lulled into thinking the communications were from Buchanan, Cheng agreed to the deal and transferred the Bitcoin to a digital wallet he believed to be controlled by Buchanan and/or Iterative — a mistaken belief, as it soon turned out.
A couple of days later, Buchanan reached out to Iterative’s exchange clients to inform them that several of his accounts had been compromised by SIM-swappers, who had falsely assumed his identity and used it to initiate trades on Iterative’s supposed behalf.
The rest of the complaint details Cheng’s appeal to the FBI, which is investigating the incident and attempting to identify the perpetrators. Buchanan has also attempted to intercede directly with T-Mobile on behalf of Cheng, but has failed to secure a refund on his behalf.
As the lawsuit underscores, SIM-swapping is hardly a new phenomenon and has been actively discussed by federal agencies since 2016 at the latest. Nor is this the first time T-Mobile has been embroiled in SIM swap-related lawsuits involving cryptocurrency investors.
The lawsuit accuses T-Mobile of failing implement to adequate security policies to prevent unauthorized access to its customers’ accounts, failing to train or supervise its employees to prevent successful fraud, and of wrongful conduct in its “reckless disregard” for various obligations and duties under federal and state law.
The carrier is thus accused of knowingly violating the Federal Communications Act the Computer Fraud and Abuse Act, the New York Protection Act, as well as two counts of negligence.
Updated: 2-19-2021
Austria Finance Regulator Sees Frauds Rising Amid Crypto ‘Hype’
Austria’s Financial Market Authority has seen a record in whistle-blower reports of potential fraud in 2020, with crypto currencies being a focus.
Two thirds of the investment fraud reports were related to crypto- and digital currencies trading products, while the rest was, among others, related to stocks and gold, FMA said in a statement. The regulator said it saw a rise in scam offerings for digital currencies on “dubious” platforms, which were often advertised on social media such as Facebook, WhatsApp, TikTok or Telegram.
“We see a great need for stricter regulation,” FMA spokesman Klaus Grubelnik said on Friday, adding that prosecution of crypto-related fraud was even more difficult as investigations usually have to be conducted across borders. “Fake offerings for stocks and gold have been around forever and these scams are now shifting to digital assets because of the hype,” Grubelnik said.
Despite recent trading booms, the world’s top banks have so far mostly shied away from offering crypto-related services as high volatility and security concerns prevailed.
Updated: 3-5-2021
McAfee Faces Crypto-Related Fraud Charges From NY Court
Meanwhile, the anti-virus mogul is still imprisoned in Spain.
Crypto advocate and internet security pioneer John McAfee faces a number of different criminal charges, based on a new statement from the United States Department of Justice, or DoJ.
The department accused McAfee of “conspiracy to commit commodities and securities fraud, conspiracy to commit securities and touting fraud, wire fraud conspiracy and substantive wire fraud, and money laundering conspiracy offenses stemming from two schemes relating to the fraudulent promotion to investors of cryptocurrencies qualifying under federal law as commodities or securities,” the DoJ’s statement from the Southern District of New York said on Friday.
Jimmy Watson Jr. is also listed under the offenses for his role on the “McAfee Team,” which operated in the digital asset industry. Authorities took Watson into custody in Texas on Thursday, the statement said.
Prior to today’s news, McAfee already faced charges from U.S. governing bodies for tax evasion and initial coin offerings, or ICOs, which he allegedly advertised for compensation without properly informing the public. After going on the run from the U.S. government in 2019, McAfee was arrested in Spain in October 2020.
McAfee remains imprisoned as of the DoJ’s statement. “MCAFEE is currently detained in Spain on separate criminal charges filed by the United States Department of Justice’s Tax Division,” the DoJ said on Friday.
“As alleged, McAfee and Watson exploited a widely used social media platform and enthusiasm among investors in the emerging cryptocurrency market to make millions through lies and deception,” Audrey Strauss, a Southern District of New York attorney, said in the DoJ statement, adding:
“The defendants allegedly used McAfee’s Twitter account to publish messages to hundreds of thousands of his Twitter followers touting various cryptocurrencies through false and misleading statements to conceal their true, self-interested motives. McAfee, Watson, and other members of McAfee’s cryptocurrency team allegedly raked in more than $13 million from investors they victimized with their fraudulent schemes.”
William Sweeney Jr., an assistant director for the Federal Bureau of Investigation, or FBI, referred to some of McAfee’s and Watson’s alleged efforts as “pump-and-dump” tactics. He also mentioned alleged paid ICO promotion, of which the pair did not provide public notice.
The DoJ notice also explained that, “In separate parallel enforcement actions, the United States Securities and Exchange Commission (the “SEC”) and Commodity Futures Trading Commission (“CFTC”) have filed civil charges against MCAFEE and WATSON.”
Updated: 3-8-2021
McAfee Claims DOGE Price Prediction To Blame For Latest US Charges
Detained antivirus software entrepreneur John McAfee points a 1,000% spike of DOGE since he called it the “coin of the week” years ago.
Troubled antivirus software entrepreneur John McAfee has claimed that Dogecoin (DOGE) was part of new charges brought against him by the United States Department of Justice. In a Sunday tweet, McAfee pinpointed that DOGE was one of several cryptocurrencies that he endorsed as part of his “coin of the day” tweets about four years ago. “For a few days in 2017 I chose coins I believed had value,” McAfee stated regarding his choice of cryptocurrencies.
The famous entrepreneur noted that Dogecoin price has increased 1,000% since he “chose it,” hinting that thus his DOGE tweets should not be included in the DoJ’s latest “pump-and-dump” charges. McAfee also emphasized that Dogecoin is “now being touted years later” by Tesla CEO Elon Musk.
McAfee apparently referred to his 2018 tweet composing a short statement: “Coin of the week: DOGE.” On the day of this tweet, Jan. 8, 2018, DOGE was trading at around $0.014, subsequently dropping to $0.007 in two weeks, according to data from CoinGecko. The coin did not retest the $0.014 price mark until Dogecoin started seeing substantial gains in late 2020 following Musk’s tweets.
Dogecoin was just one cryptocurrencies that McAfee promoted on Twitter in late 2017 and early 2018 alongside coins like Electroneum (ETN), Burst (BURST), Digibyte (DGB), Reddcoin (RDD), Humaniq (HMQ), Factom (FCT), and others. As previously reported by Cointelegraph, McAfee himself disclosed that he had a whole team for promoting initial coin offerings and other crypto projects on his official Twitter page, offering one promo tweet at a price of $105,000.
Already being detained on allegations of tax evasion, McAfee faced new fraud-related charges from the DoJ on March 5, 2021.
The regulator wrote in a new action: “The defendants allegedly used McAfee’s Twitter account to publish messages to hundreds of thousands of his Twitter followers touting various cryptocurrencies through false and misleading statements to conceal their true, self-interested motives.”
As previously reported, Tesla CEO Musk has been subject of rumors about a potential investigation by the U.S. Securities and Exchange Commission for his alleged impact on DOGE price moves in late 2020 and early 2021. Following a series of Musk’s DOGE-related tweets, Dogecoin price saw a parabolic surge in February, hitting an all-time high of around $0.08 on Feb. 8. DOGE subsequently saw a major sell-off following Musk urged major holders to sell off their holdings.
Updated: 5-30-2021
SEC Sues Cryptocurrency Promoters Over Deal That Raised $2 Billion
State Regulators in Texas Called BitConnect a ‘Massive Fraud’ in 2018.
Regulators sued a group of cryptocurrency promoters who helped raise over $2 billion from investors with the promise of 40% monthly returns, in one of the largest cases ever brought over digital assets.
The Securities and Exchange Commission on Friday sued five individuals in Manhattan federal court over their promotion of BitConnect. The SEC said the men violated laws that required them to register as brokers and ran afoul of other investor-protection rules. It didn’t accuse them of fraud.
The SEC’s lawsuit seeks to have the defendants give back the money they made and to pay civil monetary penalties.
BitConnect was a digital asset created in 2016 and sold in exchange for bitcoin, the world’s most valuable cryptocurrency. BitConnect told investors it would profitably trade their bitcoin using an automated “trading bot” and required the currency to be locked up for terms ranging from four to 10 months, according to the SEC’s lawsuit.
BitConnect eventually lost 92% of its value, and investors lost all or nearly all of their funds in the lending program, the SEC’s lawsuit said. Thousands invested in BitConnect.
The SEC sued BitConnect promoters Trevon Brown of Myrtle Beach, S.C., Craig Grant of Kissimmee, Fla., Ryan Maasen of Tulsa, Okla., and Michael Noble of Pacific Palisades, Calif. Regulators also sued Joshua Jeppesen of East Falmouth, Mass., who allegedly was a liaison between BitConnect and the promoters. Mr. Jeppesen also represented BitConnect at conferences and other events.
The SEC’s lawsuit said BitConnect’s founder is an Indian citizen who “founded, managed and controlled BitConnect at all times.” The court complaint doesn’t name the person.
The U.S. promoters were part of a network that touted BitConnect’s lending program through videos on YouTube. They earned hundreds of thousands of dollars each in commissions and other payments, the SEC said. Mr. Jeppesen earned $2.6 million, the SEC alleged.
Ian Friedman, an attorney for Mr. Jeppesen, said: “Our legal team has been working on this matter for quite some time, and we expect an amicable resolution shortly.”
Mr. Brown didn’t immediately return a message left with a relative seeking comment. Messrs. Grant, Maasen and Noble couldn’t be reached for comment.
Top promoters were eligible to win trips to Bangkok as well as cash and luxury cars, the SEC said.
Some individual investors poured everything they had into BitConnect, at a time when mainstream interest in cryptocurrencies was at a fever pitch, The Wall Street Journal reported in December 2018. Texas state regulators called it a “massive fraud.”
The Texas State Securities Board ordered BitConnect in January 2018 to cease sales to residents of that state. In response, Mr. Brown created a video that advised Texans to use an encrypted virtual private network to cloak their location and “keep using BitConnect,” the SEC alleged in its lawsuit. BitConnect lost most of its value shortly after the Texas order was issued.
A class-action group of investors sued BitConnect in federal court in 2018. The lawsuit was dismissed, but the plaintiffs have appealed to the U.S. Court of Appeals for the 11th Circuit, said attorney David Silver.
“This is a long time coming but…I am happy to see the SEC utilizing its force to apply the law,” Mr. Silver said Friday.
SEC Sues 5 Over $2B Bitconnect Ponzi
Bitconnect collapsed in 2018 after state regulators in Texas and North Carolina filed cease-and-desist letters against its lending and exchange platform.
The U.S. Securities and Exchange Commission filed charges against five individuals for their alleged involvement in the Bitconnect crypto platform that collapsed in 2018.
According to the SEC’s complaint, filed in the United States District Court for the Southern District of New York, from about January 2017 to January 2018, Bitconnect used a network of promoters to offer and sell over $2 billion in securities without registering the offering with the SEC, and without being registered as broker-dealers as required by the federal securities law.
“We allege that these defendants unlawfully sold unregistered digital asset securities by actively promoting the Bitconnect lending program to retail investors,” said Lara Shalov Mehraban, associate regional director of SEC’s New York office. “We will seek to hold accountable those who illegally profit by capitalizing on the public’s interest in digital assets.”
Bitconnect collapsed in 2018 after state regulators in Texas and North Carolina filed cease-and-desist letters against its lending and exchange platform.
The SEC’s complaint charges promoters including U.S.-based Trevon Brown (aka Trevon James), Craig Grant, Ryan Maasen and Michael Noble (aka Michael Crypto) with violating the registration provisions of federal securities laws. The complaint also charges U.S.-based Joshua Jeppesen with aiding and abetting Bitconnect’s offer and sale of securities.
The promoters touted the benefits of investing in Bitconnect’s lending program to prospective investors, including the use of testimonial style videos and publishing them on YouTube, the SEC said in its release. According to the complaint, the promoters received commissions based on their success in soliciting funds.
The complaint seeks injunctive relief, disgorgement plus interest and civil penalties.
After the complaint was made public, Brown tweeted “I just became a villain again.”
While no criminal complaints were filed, the FBI has been investigating Bitconnect for the last three years. Brown said in March 2018 that he had spoken with FBI agents, and the federal investigator posted a notice in 2019 asking for investors to reach out.
A representative of the criminal division at the Department of Justice’s Southern District of New York office said no criminal charges were anticipated today.
Promotors of the project have been arrested in other countries as well: Indian police arrested promotor Divyesh Darji in 2018, while Australian authorities filed charges against John Bigatton last year.
Binance Smart Chain’s BurgerSwap Drained Of $7.2M In Exploit
The latest in a recent spate of decentralized finance hacks.
Another decentralized finance protocol was subject to a major exploit on Friday after $7.2 million was drained from BurgerSwap on Binance Smart Chain.
Varying amounts of seven different cryptocurrencies were stolen amid the attack, including $3.2 million worth of BURGER tokens, $1.6 million worth of Wrapped BNB (WBNB) and $1.4 million worth of Tether (USDT). The funds were still being sold off at the time of publication.
BurgerSwap launched in late 2020 as what was thought to be a clone of the Uniswap decentralized exchange. However, a post-mortem into the exploit revealed that the omission of a crucial line of code differentiated Uniswap from BurgerSwap and was likely the point of attack for what took place on Friday.
This revelation led some social media observers to speculate that BurgerSwap developers were behind the attack themselves.
The BurgerSwap team announced that it was “working on the issue” and that it had suspended the generation of any more tokens to prevent more losses on Friday morning. The team tweeted:
“BurgerSwap just experienced [a] Flash Loan attack. We have suspended Swap and BURGER generation to avoid further loss. Our tech team is working on the issue and will publish the solution later. More details will be published soon. Thanks for your patience.”
Hacks on Binance Smart Chain have become more numerous this month, after $200 million was drained from PancakeBunny on May 20 and $3 million was stolen from Bogged Finance on Monday.
Blockchain security and analytics firm CipherTrace recently announced it would expand its services to include Binance Smart Chain in response to the sudden spate of exploits.
Updated: 5-31-2021
Belt Finance Victim Of Flash Loan Attack In Latest Exploit Of A BSC DeFi Protocol
Withdrawals and deposits are temporarily paused.
Belt Finance, a platform that provides automated market making for decentralized finance (DeFi), was hacked Saturday in a flash loan attack that resulted in a profit of $6.23 million for the perpetrator and an overall $50 million loss for the platform.
* It’s the latest attack on a DeFi protocol built on Binance Smart Chain, one of the so-called Ethereum killers that’s built by centralized crypto exchange giant Binance.
* In a blog post, Belt Finance said the attacker created a smart contract that used PancakeSwap for flash loans and exploited its beltBUSD pool and its strategy protocols and then proceeded to execute the contract eight times for a total profit of 6.23 million BUSD (US $6.23 million).
* BeltBUSD vault users suffered a 21.36% loss of funds, while 4Belt pool users lost 5.51%, the protocol said. No other pools/vaults were affected. Overall, the attack cost the beltBUSD pool a combined loss of 50m BUSD (US $50 million) consisting of 43.8m in fees and the 6.23 million BUSD that the attacker withdrew as profit.
* The protocol said it paused withdrawals and deposits as soon as it were aware of the attack and that the vulnerability that allowed the attack to occur has been patched.
* In its blog post dated Sunday, Belt Finance said withdrawals and deposits would resume sometime in the next 24 to 48 hours and that it’s working on a “compensation plan” that will be released in next 48 hours.
Updated: 6-7-2021
Crypto Frauds Target Investors Hoping to Cash In On Bitcoin Boom
FTC says consumers have reported losing more than $80 million to crypto-investment scams since October.
Scams are running rampant in the cryptocurrency markets as a huge rally in bitcoin, a lack of regulation and the anonymity of digital money have created a ripe environment for fraudsters.
Consumers reported losing nearly $82 million to crypto scams during the fourth quarter of 2020 and first quarter of 2021, more than 10 times the amount from the same six-month period a year earlier, according to the Federal Trade Commission.
From October to March, the price of bitcoin jumped 450% to nearly $59,000, while rival coins such as ether and dogecoin also surged. Bitcoin has since retreated to around $36,000, still substantially higher than where it traded for all of last year.
Scammers have targeted everyone from small investors scouring social media for investing tips to the Wall Street veterans who backed an Australian crypto-fund manager recently charged with running a $90 million fraud.
Sebastian, a 28-year-old pharmacy technician, is still kicking himself after he lost about $10,000 in ether to a crypto venture whose anonymous creators vanished in May, leaving behind hundreds of unhappy investors.
The creators of “LUB Token” purported to be building a crypto exchange based on the Telegram messaging app. On their now-defunct website and in a press release distributed on multiple crypto websites, they touted LUB, a new cryptocurrency that promised daily returns of up to 10%.
Sebastian, who lives in the suburbs of London, said he normally researches crypto projects carefully before investing, but he broke his own rule and dove in. He made several deposits into a digital wallet controlled by LUB and even plugged the venture on Reddit himself before others warned him it was a scam. By then it was too late. Unlike credit-card purchases, crypto transfers generally can’t be reversed.
“I feel ashamed and still can’t get my head around how stupid I was,” said Sebastian, who asked that his last name not be published so he wouldn’t be targeted by internet trolls.
Hundreds of people with similar stories, mostly in Europe, have since joined Telegram groups such as “LUB Token = SCAM !!!” An administrator of one group, who uses the name Tobias, estimated victims in Germany lost between €500,000 and €1.5 million ($600,000 to $1.8 million) to the scheme. German police are investigating complaints about the LUB scheme across the country, said a police spokesman in the city of Aalen, which received one complaint in May.
It is difficult to say how much money investors lose to crypto fraud. The FTC’s figures are based on self-reporting by scam victims and largely limited to the U.S., so they likely reflect only a slice of total losses. CipherTrace, a blockchain analytics firm that tracks reports of crypto crime worldwide, says fraudsters are taking in less than they used to—from $4.1 billion in 2019 to $432 million during the first four months of this year. CipherTrace’s tallies for 2019 and last year were elevated due to the exposure of a few large Ponzi schemes in Asia.
Still, CipherTrace says fraud is surging in the buzzy area of DeFi, or decentralized finance. DeFi is a broad term for efforts to provide financial services—such as lending, asset trading or insurance—using blockchain, the technology behind bitcoin.
DeFi projects offer yields on investors’ crypto assets far higher than conventional interest rates, and even some legitimate DeFi projects are run by anonymous teams. That makes it easy to carry out “rug pulls,” a scam in which unscrupulous operators raise money for a project, only to abscond with investors’ funds.
From January through April, DeFi fraudsters stole $83.4 million, more than double the haul from all last year, according to CipherTrace. DeFi has “exploded and there are a lot of innovative products, but it’s also ripe ground for fraud,” CipherTrace CEO Dave Jevans said.
Fraud frustrates crypto advocates who have pushed for mainstream acceptance of digital currencies.
“Bad guys are always going to follow the money,” said J. Christopher Giancarlo, a former chairman of the Commodity Futures Trading Commission who is now on the board of crypto startup BlockFi. “As the industry matures and surveillance tools get better, hopefully the cops will catch up.”
Even sophisticated investors can fall victim to crypto frauds. In February, crypto hedge-fund manager Stefan Qin pleaded guilty to one count of securities fraud. In a New York federal court, the 24-year-old Australian confessed he had lied to investors for years about the returns of his $90 million flagship fund, Virgil Sigma Fund LP. He now faces up to 20 years in prison.
Mr. Qin had claimed a near-perfect record of profitability, saying the fund made monthly returns sometimes greater than 20%, by arbitrage trading—using computers to exploit price differences between crypto exchanges. He was featured in an article in The Wall Street Journal in 2018, which repeated some of his false claims.
“Mr. Qin has accepted full responsibility for his actions and is committed to doing what he can to make amends,” his attorneys with law firm Kaplan Hecker & Fink LLP said in a statement.
Virgil drew dozens of well-heeled investors, with balances ranging from $103,000 to $5.7 million, according to one court filing. Two of those investors, who spoke to the Journal on condition of anonymity, are New York-area financial professionals who have worked for multinational banks.
In retrospect, the two investors said they overlooked a red flag: the fund never produced audited returns, a situation Mr. Qin chalked up to the nascent nature of crypto. “Being on the leading edge of the industry has put us ahead of regulators and accounting firms, and often there are no standard paths to follow,” Virgil told investors in a 2019 email.
Court filings show Mr. Qin came under pressure last year after investors sought to pull money from the Virgil Sigma Fund. In December, Mr. Qin urgently sought to withdraw money from a separately managed sister fund, Virgil Quantitative Research, telling its employees that he needed to pay off Chinese loan sharks, according to a Dec. 22 lawsuit filed against him by the Securities and Exchange Commission.
Alarmed employees alerted the SEC, triggering Mr. Qin’s downfall, a person familiar with the matter said. An SEC spokesman declined to comment.
One of the investors texted Mr. Qin after learning about the SEC’s lawsuit. In a reply seen by the Journal, Mr. Qin said he couldn’t discuss the suit. “It kills me to say that, but my firm belief is that things will be OK and the justice system will prevail,” he added.
Six weeks later, he pleaded guilty.
Updated: 6-17-2021
‘I Have Nothing’: Imprisoned John McAfee Claims His Crypto Fortune Is Gone
John McAfee asserted in an extradition hearing in Spain that the tax evasion charges aimed against him are politically motivated.
Software antivirus pioneer John McAfee has told his one million Twitter followers that his entire crypto fortune is gone — although he concedes not everyone will believe he’s telling the truth.
The McAfee antivirus founder has been behind bars in Spain since October 2020 — when he was arrested for tax evasion — but that hasn’t stopped him from posting on Twitter on a near-daily basis.
The 76-year-old tweeted earlier today that “I have nothing. Yet, I regret nothing,” and noted that:
“The US believes I have hidden crypto. I wish I did but it has dissolved through the many hands of Team McAfee (your belief is not required), and my remaining assets are all seized. My friends evaporated through fear of association.”
The U.S. government is currently seeking McAfee’s extradition, with a ruling set to come from Spanish courts in the coming days.
McAfee has a litany of charges aimed against him, including the alleged operation of two “pump and dump” related crypto scams that duped investors out of $13 million.
If extradited, McAfee will face court on charges for evading taxes between 2014 and 2018, after he failed to report income from multiple revenue streams such as crypto gains, paid crypto promotions, consultancy work, and selling the rights to his life-story documentary.
I can see a small piece of sky above the tall concrete walls of the prison yard. The walls seem to frame, in contrast, the deep blue sky and the fluffy clouds drifting through it.
It turns this tiny sky window into a jewel of extraordinary beauty.
— John McAfee (@officialmcafee) May 25, 2021
McAfee’s life behind bars appears to be one of contemplation, as he regularly tweets messages with tones that switch between sorrow, acceptance for his circumstances, mixed in with sparks of aggression towards the U.S. governing bodies.
In the June 9 tweet, he notes that “after uncountable lawsuits and the reach of the FED’s I now have nothing. But inside these prison bars I have never felt more free. The things you believe you own, in reality own you.”
I have a million followers but I’d be surprised if even 1% bother to read my tweets.
Ramblings of an old man lost in a near infinite Twitter verse – like tears in rain.
As you may guess I’m having a down day.
— John McAfee (@officialmcafee) June 8, 2021
It is a stark contrast to McAfee’s earlier years in which his net worth grew to $100 million from his successful anti-virus software firm. McAfee used to own a mansion worth more than $5 million in Colorado Springs, and even lived on a luxury yacht out in Dominican Republic waters, which he dubbed a “freedom boat.”
According to the June 2020 indictment from the Justice Department’s Tax Division and Tennessee prosecutors, McAfee faces a minimum of five years on each count of tax evasion and a one-year minimum on each count of willful failure to file a tax return.
Given his age, the serial entrepreneur is likely to spend the remainder of his life behind bars if found guilty.
McAfee spoke at Spanish High Courts this week during the first hearing of his extradition trial and asserted that charges from U.S. governing bodies are politically motivated due to his two attempts to run as a Libertarian Party candidate in the U.S. presidential elections. He says he drew the IRS’s attention in 2018 when:
“I also announced I would target the IRS and its corruption, and two months later the IRS filed charged against me.”
Spanish prosecutor, Carlos Bautista rejected this claim and described McAfee as a “tax rebel, nothing else. A millionaire who doesn’t want to pay taxes.”
There is much sorrow in prison, disguised as hostility.
The sorrow is plainly visible even in the most angry faces.
I’m old and content with food and a bed but for the young prison is a horror – a reflection of the minds of those who conceived them.
— John McAfee (@officialmcafee) June 10, 2021
Updated: 6-23-2021
Spanish Court Rules John McAfee Can Be Extradited To The United States
Lawyers will have the opportunity to appeal the court’s decision and local lawmakers will need to approve the extradition before it is final.
John McAfee, the founder of the antivirus software company of the same name, is one step closer to facing prosecution in the United States for tax evasion.
In a ruling released today, the Spanish National Court approved the extradition of McAfee to the United States. The U.S. government had been seeking his extradition for charges including failing to submit tax returns from 2014 to 2018 and allegedly illegally profiting from “promoting cryptocurrencies, consulting work, speaking engagements, and selling the rights to his life story for a documentary.”
McAfee’s legal team will have the opportunity to appeal the court’s decision. In addition, Spain’s Council of Ministers will need to approve the extradition before it is final.
The 76-year-old antivirus company founder has been detained in Spain since October 2020. However, someone with access to his account regularly posts on his behalf concerning his condition and thoughts on the legality of his situation. Last week, he claimed he no longer has any crypto, as it has “dissolved through the many hands of Team McAfee” or otherwise been seized by authorities.
Updated: 6-23-2021
South African Brothers Vanish, And So Does $3.6 Billion In Bitcoin
A pair of South African brothers have vanished, along with Bitcoin worth $3.6 billion from their cryptocurrency investment platform.
A Cape Town law firm hired by investors says they can’t locate the brothers and has reported the matter to the Hawks, an elite unit of the national police force. It’s also told crypto exchanges across the globe should any attempt be made to convert the digital coins.
Following a surge in Bitcoin’s value in the past year, the disappearance of about 69,000 coins — worth more than $4 billion at their April peak — would represent the biggest-ever dollar loss in a cryptocurrency scam. The incident could spur regulators’ efforts to impose order on the market amid rising cases of fraud.
The first signs of trouble came in April, as Bitcoin was rocketing to a record. Africrypt Chief Operating Officer Ameer Cajee, the elder brother, informed clients that the company was the victim of a hack. He asked them not to report the incident to lawyers and authorities, as it would slow down the recovery process of the missing funds.
Lawyers Hired
Some skeptical investors roped in the law firm, Hanekom Attorneys, and a separate group started liquidation proceedings against Africrypt.
“We were immediately suspicious as the announcement implored investors not to take legal action,” Hanekom Attorneys said in response to emailed questions. “Africrypt employees lost access to the back-end platforms seven days before the alleged hack.”
The firm’s investigation found Africrypt’s pooled funds were transferred from its South African accounts and client wallets, and the coins went through tumblers and mixers — or to other large pools of bitcoin — to make them essentially untraceable.
South Africa Plans To Regulate Crypto Trading In Phased Manner
Calls to a mobile number for Cajee were immediately directed to a voicemail service. He and his brother, Raees, 20, set up Africrypt in 2019 and it provided bumper returns for investors. Calls to Raees also went straight to voicemail. The company website is down.
The saga is unfolding after last year’s collapse of another South African Bitcoin trader, Mirror Trading International. The losses there, involving about 23,000 digital coins, totaled about $1.2 billion in what was called the biggest crypto scam of 2020, according to a report by Chainalysis. Africrypt investors stand to lose three times as much.
Crypto Havens Lure Firms Fleeing South Africa Regulator Fear
While South Africa’s Finance Sector Conduct Authority is also looking into Africrypt, it is currently prohibited from launching a formal investigation because crypto assets are not legally considered financial products, according to the regulator’s head of enforcement, Brandon Topham. The police have not yet responded to a request for comment.
China has recently escalated its crackdown on cryptocurrency trading after a frenzied surge in Bitcoin and other tokens over the past six months heightened longstanding Communist Party concerns about the potential for fraud, money laundering and trading losses by individual investors.
In January, the daily value of crypto-asset trading exceeded 2 billion rand ($141 million) for the first time in South Africa, suggesting significant appetite in a market that was largely going unchecked by regulatory powers.
Updated: 6-28-2021
Lawyers For Africrypt’s Missing Founders Say They’ve Been Fired: Report
The Cajee brothers are still missing–along with $3.6 billion in bitcoin.
Lawyers for the missing co-founders of South African crypto investment platform Africrypt say their relationship with the brothers has been terminated, according to a report from Bloomberg.
Twenty-year-old Ameer Cajee and 17-year-old Raees Cajee, who are brothers, are thought to have vanished in April, after sending an email to investors telling them the platform had been “hacked” and shuttering Africrypt’s website. Bitcoin worth an estimated $3.6 billion is allegedly missing.
Johannesburg-based attorney John Oosthuizen, told Bloomberg via email that his firm’s “mandate to assist the Cajee Brothers has been terminated” when asked to comment on the brothers’ whereabouts. Oosthuizen’s statement comes only two days after he first spoke with the BBC about the scandal.
The launch of a formal investigation is constrained by South African law, which does not consider cryptocurrencies a financial product. But if the Cajee brothers absconded with the $3.6 billion in bitcoins, the theft would rank among the largest in crypto history.
Oosthuizen previously told the BBC that the brothers “categorically denied” the accused heist, saying that it was a hack and the money was missing.
According to Oosthuizen, the reason the brothers didn’t immediately contact the police was not that they were making their getaway, but rather that they were young men with “very little life experience” who were afraid for their lives after receiving death threats from involved parties.
McAfee Found Dead In Spanish Prison As Extradition Loomed; Autopsy Planned
The software magnate and crypto investor had been facing extradition to the U.S. on fraud charges.
John McAfee, the controversial software magnate and crypto booster, has died in what’s preliminarily being called a suicide in a prison in Barcelona. El Pais was first to report the news.
Prison sources tell CoinDesk an autopsy is being planned.
McAfee was awaiting extradition to the U.S. to stand trial on charges of tax fraud, which the Spanish High Court authorized just this morning.
“Everything indicates that it could be a death by suicide,” the Catalan Department of Justice said in a statement.
When reached by phone by CoinDesk, a prison staffer said: “For information about John McAfee, you may call tomorrow at 9 a.m. local time.”
According to an October 2020 indictment by the U.S. Department of Justice (DOJ), “McAfee earned millions in income from promoting cryptocurrencies, consulting work, speaking engagements, and selling the rights to his life story for a documentary.”
During an extradition hearing earlier this month, McAfee claimed that the extradition efforts were politically motivated.
He faced a total of 10 years in prison for allegedly cheating his way out of $4 million.
McAfee was arrested in October 2020 at Barcelona’s El Prat airport as he prepared to board a flight to Turkey, according to El País.
In a November 2020 interview with Spanish journal El Diario, McAfee said, “Life in Spanish prisons is like living in a Hilton compared to the surreal submissive and dehumanizing conditions of American prisons.”
McAfee was a controversial figure in the later years of his life, participating in alleged “pump and dump” schemes as well as being paid to promote a number of initial coin offerings, without disclosing those payments.
The DOJ declined to comment. In an email, the agency referred CoinDesk to the Spanish authorities.
Updated: 7-2-2021
WhaleFarm Crash Is Latest Too-Good-To-Be True DeFi Collapse
On Monday, something called WhaleFarm was trading above $200 on crypto exchanges. By Wednesday, it was worth close to zero.
It’s the latest easy-come, easy-go DeFi project to raise eyebrows, after its crash likely wiped out millions in value in a matter of hours, prompting Twitter lamentations on its obliteration and warnings from market pros on avoiding too-good-to-be true investments.
“The whole thing is just fake — people get fake yields, they get fake balances and then eventually the founders just take everything. A competitor platform is offering 10%, so I say I can get you 20%. You send me your money and then I run,” said Stephane Ouellette, chief executive and co-founder of FRNT Financial.
“All the platforms are perpetuating this stuff because it trades actively, but there is just so much junk and this is only going to continue to get worse.”
WhaleFarm was likely what’s known as a rug pull, a malign move that’s becoming more prevalent in the DeFi space whereby a developer abandons a project and absconds with the funds. In other words, the holder of the cryptocurrency in question dumps their stake all at once, leading to a catastrophic price drop that wipes out other investors.
Here’s how it might play out, according to Wilfred Daye, chief executive officer of Enigma Securities: A token developer copies an existing smart contract code off a public venue and then issues a platform token.
The developer then markets it, lists it on a decentralized exchange, and attracts higher-value coins like wrapped Bitcoin or Ether in what’s known as a liquidity pool. The developer then sells or redeems their platform token, depleting the liquidity pool of the project. They can then make off with the proceeds.
“Obviously, investors need to be vigilant about such DeFi products. There are always tell-tale signs,” including promises of sky-high returns, copied codebases, and anonymous teams, said Daye.
WhaleFarm is just one of the latest projects to attract attention after the DeFi Titanium token earlier this month in one day went from being valued around $60 to $0 — something that’s considered a rare feat even for the famously volatile crypto space.
Renowned mogul Mark Cuban had invested, telling Bloomberg News that though it represented a small percentage of his crypto portfolio, the wipe-out “was enough that I wasn’t happy about it.”
DeFi apps are designed to let people lend, borrow, trade and take out insurance directly from each other, without use of intermediaries such as banks. Many essentially let users lend out their coins to new users and to earn returns on the loan — though yields can also fall if there aren’t fresh users clamoring for the coins.
DeFi coins gained popularity this year to become one of the hottest sectors in an already volatile market. But the space — though it’s been plagued by hacks, fraud and a copy-and-paste coding culture — has come crashing down, in tandem with a retreat in the wider cryptosphere that’s seen Bitcoin’s year-to-date gains diminish to about 20% from as much as 115%.
The DeFi Pulse Index is down roughly 60% from a recent high, according to CoinMarketCap.com. Meanwhile, Bloomberg recently reported, the number of new DeFi user accounts opened daily has dropped to the lowest levels since the embryonic sector started hitting its stride in September.
“The DeFi stuff in general, they pay huge yields but there’s massive currency risk,” said Justin Litchfield, who is the Austin, Texas-based chief technology officer at ProChain Capital, a crypto hedge fund.
And so-called rug pulls are not exactly new — they’re just catching more investor attention after huge run-ups for many DeFi tokens. A report from CipherTrace showed the maneuver was one of the top exit scams. In the second half of 2020, almost 99% of major fraud stemmed from rug pulls and exit scams, the company said.
To FRNT’s Ouellette, it’s reminiscent of what happened during the initial coin offering (otherwise known as ICO) boom in 2017 and 2018, which saw investors lose billions when the bubble burst. In rare cases, some were able to retrieve their investments. “But when people are running away with the money, I doubt there’s very much anyone can do,” he said.
Aaron Brown, a crypto investor who writes for Bloomberg Opinion, said that not all the facts are in about WhaleFarm — the team could, after all, reveal itself tomorrow and pay back all the money.
But “while this is a sad story for the victims, it’s not a big deal. $2 million frauds are everyday occurrences,” he said. “If the crooks aren’t doing them in crypto, they’re selling fake stock, or worthless gemstones, or phantom gold, or real estate they don’t own.”
Updated: 7-8-2021
Crypto Scammers Rip Off Billions As Pump-and-Dump Schemes Go Digital
Billions are getting pilfered annually through a variety of cryptocurrency scams. The way things are going, this will only get worse.
Listen to The Money Chant of the Wolves of Crypto.
You remember The Money Chant: Matthew McConaughey thumping his chest, talking fools and money before — sniff! — a little lunchtime “tootski.”
Titan Maxamus has been there. Well, not there, in a “Wolf of Wall Street”-style boiler room. There on the other side — as the mark.
Titan Maxamus knows the game. All the brazenly cynical players do. In Scorsese’s cinematic bender of sex, drugs and stocks, it’s called the pump and dump. In today’s cryptocurrencies, it’s known as the rug pull.
Maxamus thinks he got rug-pulled the other month in some sketchy digital token called — wait for it — Safe Heaven. Like countless dreamers in today’s memeified markets, he’s been gambling $50 here, $100 there on what are known as Shit Coins, obscure digital something-or-others being minted by the thousands. This stuff makes Bitcoin look good as gold.
One moment, Safe Heaven was flying. The next, it was crashing. Maxamus (that’s his online persona. His real name is Glenn Titus), can’t prove anything. But he suspects what, in retrospect, seems forehead-slappingly obvious: some small-time hustler created Safe Heaven with a few deft keystrokes, hyped the hell out of it — and promptly cashed out.
Telegram, a popular instant messaging app that’s become a major crypto boiler room, immediately fell silent. The Safe Heaven Telegram group, once thronging with rocket emojis and Elon Musk GIFs, was deleted. The Safe Heaven Twitter account hasn’t been updated since May 28.
“Everybody I know has gotten rug-pulled,” says Titus, a 38-year-old butcher in Salem, Oregon. “You know, you win some, you lose some. Hopefully, win more than lose.”
It might sound like a joke, given the crypto meltdowns of late, but serious money is at stake here. Billions — real billions — are getting pilfered annually through a variety of cryptocurrency scams. The way things are going, this will only get worse.
Back in the Wall Street Dark Ages — six, 12, 18 months ago — these sorts of shenanigans were mostly associated with shlocky brokerages like the one depicted in the 2013 Wolf. In those halcyon days before GameStop, Dogecoin and the rest, schlubs on Long Island might pitch ridiculous over-the-counter stocks to the gullible.
Nowadays crypto hustlers and star-gazers like Titan Maxamus have established a weird symbiotic relationship. It seems to capture everything that’s gone wrong with money culture, from Reddit-fueled thrill-seeking to conspiracy theorizing to predatory wheeling-dealing.
The rug pull is only one play. There’s also the gentler soft rug, the crypto version of getting ghosted on Hinge. And the honey pot, which functions like a trap. Old-fashioned Ponzi schemes, newly cryptodenominated, have swindled people out of billions too.
At times the result can start to resemble the Agatha Christie mystery classic “Murder on the Orient Express”: The who in this dunnit is somehow everyone. Grifters will grift. But like Maxamus, many marks actually expect to get snookered once in a while. Both sides, the swindler and the swindled, are in on this one. Elaborate social-media systems have sprung up to flag potential trouble, not only to avoid it but maybe even to profit from it.
“Everybody I know has gotten rug-pulled”
Many who feel they’ve been ripped off just shrug. They chalk it up to the cost of doing crypto, the price of buying a lottery ticket that maybe just might hit that big jackpot.
Titan Maxamus says he’s still in the money, swindlers be damned. And he’s not giving up. He’s got anywhere from $20 to $1,000 in dozens of different meme coins. (A recent pick, Blue Lighting, looks like it fell victim to a honey pot — more on that later).
“People have a fear of missing out on the next big thing, so they’re just dumping money here and there,” Maxamus said with earnest understatement, just before Bitcoin and Shit Coins began to crater recently. He concedes his own FOMO lured him into a rug-pull or three. “I guess you never know,” he reflects. “That’s part of the risk you take.”
The list on Tokensniffer.com runs on and on. Six minutes ago, CatRocket. One hour ago, MoonMiner. Three hours ago, GoldenShiba. Four hours ago, EverRise. So it goes, hour after day after week after month, in a sort of running Trip Advisor review of bad crypto experiences.
They all appear under the same heading: “Latest Scams & Hacks.” Tokensniffer, aptly named for Shit Coins, claims to have tracked 42,071 tokens and 2,250 scams or hacks. That was as of June 16. More than 200 supposed stings were logged by users during the first two weeks of June alone.
Just how many of these coins have actually been rug-pulled, soft-rugged or otherwise manipulated is anyone’s guess. The website was developed in October 2020 by a software-engineer-cum-crypto-trader. He is 44 years old and lives in the western United States. Like many players in crypto, he prefers to remain anonymous.
The idea for Tokensniffer came to him after he fell victim to rug pulls himself. His website scrapes data about new meme tokens from popular social media channels and scans the source code. Sometimes users also flag tokens that aren’t in the system. Tokensniffer functions a bit like a virus scanner looking for malicious code patterns.
A “smell test” program searches for vulnerabilities. Clones of existing meme tokens are often a red flag. Most recent scams — the site flagged 450 in in one recent 30-day period — were honeypots. Those tend to be easier to spot because of their code, Tokensniffer’s creator says. Rug pulls are more complicated.
Some crypto wolves work alone, others in packs, and almost all use online aliases.
Such supposed safeguards aside, people are getting scammed in growing numbers. So far this year, over $2.6 billion has been grabbed, according to Chainalysis, a New York-based blockchain researcher.
That figure doesn’t include a giant Ponzi scheme that just came to light in South Africa. Local authorities put the haul at $3.6 billion worth of Bitcoin. Gob-smacking as all of this might sound, these numbers in fact represent a marked decline from 2019, when fraudsters walked away with an estimated $9 billion.
But here’s a key difference: the sheer number of people getting hoodwinked. With a few outsize exceptions, most crypto scams seem to be getting smaller. That’s the good news. The bad news is that there are more of them, and more people are getting stung. From 2019 to 2020, the number of victims has jumped 48% to an estimated 7.3 million, a figure approaching the official population of Hong Kong.
Between the last three months of 2020 and the first three months of 2021, the number of unique scams rose nearly 18%, to 1,335, according to Chainalysis.
Most individual scams are so small that the authorities don’t bat an eye. Regulators around the world tend to prioritize cases involving lots of money, or violations that seem particularly egregious. Cases involving less than $100,000 tend to get a pass, and buyers have little incentive to chase after fraudsters on their own.
Most swindlers simply disappear. The phenomenon is big, growing — and global. Some crypto wolves work alone, others in packs, and almost all use online aliases. Even people who are in on the same scam don’t necessarily know their accomplices true identities.
“You can’t draw blood from a stone,” Paul Sibenik, lead case manager at CipherBlade, a Blockchain investigation company, says of trying to get your money back. “If there’s nothing left or if the loss wasn’t that high, nailing down the people behind these scams vary case-by-case.”
CipherBlade, founded in 2018, hasn’t taken on any meme-coin scam cases — yet. Sibenik expects business to roll in as more people give meme coins a whirl, lose their shirts or both, and the inevitable lawsuits pile up.
“There is going to be consequences,” Sibenick says, “but it’s not going to happen quick.”
Sibenik goes on: “There’s so much financial opportunity. It’s definitely not a single or even a small group of people.”
Where are they all?
“All over the world, really,” Sibenick says.
The word went out on Twitter: Safetrade was supposedly “rug proof.” The person or persons behind it couldn’t cut and run. An account that promotes meme coins, Crypto Gems, was urging their followers to get in — and get in fast. (Crypto Gems didn’t reply to messages from Bloomberg; whoever is behind it couldn’t be reached.)
It was April 10, a Saturday, and Safetrade was getting buzz across social media. People were saying this looked like the next “it” coin. Robert Turner placed $50 on Safetrade through PancakeSwap, one of the most popular decentralized exchanges for meme coins.
A couple of days later, the rug got pulled. Or at least that’s what Turner thinks happened. He was monitoring Safetrade on Poocoin.com, a scatologically named crypto platform, when the price collapsed to nearly zero in less than a minute. He checked the Safetrade Telegram group. Deleted. Members had been kicked out.
That’s when things got really weird. Minutes later, Turner got a private message from someone on Telegram. The person was offering to help recover his money. All Turner had to do was transfer any remaining tokens from his digital wallet to theirs.
“You need to send the remaining balance of the Safetrade to the burn wallet we will assign you too,” the anonymous user wrote to him. “This is a professional issue, I’m not going to scam you, I’m here to resolve this issue.”
Turner, a 42-year-old software engineer in Melbourne, Australia, smelled trouble. He didn’t do it. Turner says his tokens were worth pennies by that point. But then, pennies can add up. “If he was able to collect enough from various people, they could be worth quite a bit,” he says of the supposed Good Samaritan.
Then there was Mooncharge — what now looks like a “soft rug.” That’s when the creator of a coin project jumps ship and abandons efforts to promote his or her creation. Often, this essentially renders a coin worthless. Turner bought $50 worth of Mooncharge in April after reading about the coin on Reddit. Before long, he was left high and dry. Here’s what happened:
The admin of the Telegram group, presumably Mooncharge’s creator, promised fans in April that he was working on a new version of the coin. “We will keep everyone posted on Mooncharge v2,” the person wrote, using shorthand for Version 2. “Get ready this will be mental.”
“V2?” Moonchargers on Telegram were confounded.
“Anyone want to tell me what is happening. Have we been scammed?” one asked.
“I’m down $600 from 20-30 minutes ago, what happened,” said another.
By early May, the admin of the group was still insisting Version 2 was on the way. “Stay tuned,” the admin wrote. Then: nothing. As of July 1, no further updates had arrived.
“The token essentially became worthless after that,” Tuner says. He held on for a bit, hoping that V2 might materialize, and then sold what was left of his Mooncharge. “Everyone still lost their money,” he says.
“If there’s nothing left or if the loss wasn’t that high, nailing down the people behind these scams vary case-by-case.”
Ben Ghrist knows all about crypto scams. He’s lives at his parents’ home in Roanoke, Texas, and, for the moment, is trading meme coins as a full-time job. At 35, Ghrist is a millionaire in Safemoon, a billionaire in Kishu Inu and Sanshu Inu and a trillionaire in Keanu Inu.
He’s got money in at least 15 different coins, with about a quarter of his $25,000 “portfolio” in Dogecoin, the one created as a joke back in 2013 and known for its Shiba Inu mascot.
Ghrist suspects he’s gotten rug-pulled, soft-rugged and even fallen victim to a honey pot — when a seemingly legitimate coin sets up a trap, like the inability for investors to sell once they’ve bought in. Ghrist says he wanted to trade the momentary 1000% gain of a coin launch called Space Jupiter but couldn’t sell for about 20 minutes.
He says the creators of the coin eventually re-enabled selling, but only after the coin price had slumped and after he suspects they had taken gains for themselves.
“It’s pretty much hit-or-miss wherever you go,” says Ghrist, who typically works from his bed with two laptops. He says he’s pulled all-nighters and worked 48 hours straight moiling for meme-coin gold.
In picking his meme coins, he considers a range of factors to minimize risk. One is the number of social media accounts a coin has (legit coins, he says, tend to have more than dodgy ones).
Another is whether those accounts are public or private (he says public is safer than private): how much time those accounts spend chatting with investors (more is better than less). Then he looks at what’s happening in Telegram groups, known in meme-coin-speak as “shilling groups.” When the whole package looks slapdash, that’s a bad sign, he says.
Ghrist feels scammed at times, but he’s pressing on too. “When I feel that fear of losing my money, because I know I might, I also balance that with I might make five times my money or three times my money,” he says. “You can literally do 30 times or more if you if you get a coin that lasts more than a day.”
The biggest crypto heist on record came to light only recently, and it appears that one was neither a rug-pull nor a soft-pull nor a honey pot. It looks like an old-fashioned Ponzi scheme. In April, two bothers in South Africa said their crypto investment platform had been hacked. Then they vanished — along with an estimated $3.6 billion of Bitcoin.
Lawyers who’d been working for the men, Raees and Ameer Cajee, said on June 29 that they were no longer representing them and didn’t know where they were. The previous record-holder involved the Chinese crypto wallet and exchange PlusToken. According to Chinese authorities, PlusToken users were bilked out of more than $2 billion in another Ponzi scheme. Last November, the ringleaders were sentenced to between two and 11 years in prison.
Mostly, though, authorities around the world are struggling to keep pace. A decade after Bitcoin was created, regulators are still grappling with how to police cryptocurrencies when the whole point is that they operate without governments or central banks. As more institutions and ordinary investors dip their toes into crypto — and, despite all the wild gyrations, more probably will — new scams are bound to emerge.
“Cryptocurrency is entering a new phase,” says Kim Grauer, head of research at Chainalysis. Technology is improving. Trading is getting easier. Institutions and ordinary investors who once wouldn’t go near crypto are bound to take a long view and give it a try at some point.
The Bank for International Settlements, the central bank for central bankers, just laid out tough capital standards for banks looking to deal in Bitcoin. It was a nod to the patently obvious — Bitcoin is risky — but also a recognition of cryptocurrencies’ new place in the financial order.
The Wolves of Crypto know all this, too. Somewhere out there, The Money Chant runs on.
During the pandemic in the U.S., boredom, social media and old-fashioned greed has had people running in and out of crypto and meme stocks. Elon Musk tweets, and prices soar or swoon. Michael Burry, of “The Big Short”-fame, has been warning all of this could all go horribly wrong. An estimated 10,000 new coins have been minted this year.
Who can say how many will turn out to be shams? So many Shit Coins are flying around out there, and prices can be so volatile, that many people can’t even tell if they’ve been scammed.
The bad guys often cover their tracks by blending identifiable cryptocurrencies with anonymous ones, an old money-laundering maneuver known as “mixing” or “blending.” They engage in “peel chains,” which involve skimming a little crypto here, a little there, and routing it to different digital wallets on different exchanges.
And Jason Gottlieb, a partner in New York at the law firm Morrison Cohen, whose practice focuses on regulatory enforcement and cryptocurrencies, says some people tar particular coins for their own nefarious ends. “You also have purely malicious people who go on and they say project X is a scam because they’re actually working for project Y that’s a competitor, or they’re working for trolls,” Gottlieb says.
This much is sure: no one complains when they’re making money. It’s when people start losing money — and lately, many have been — that they scream they’ve been taken.
“When the price goes up, people don’t ask as many questions,” says Tyler Moore, a cybersecurity professor University of Tulsa who’s studied cryptocurrency scams. “And then you see the flip side when things go down.”
Updated: 7-10-2021
Africrypt Turns Sour On Investors: Founders Flee As Court Cases Build Up
Africrypt founders are still on the run as investors turn to legal action to try to recoup funds lost in South Africa’s latest cryptocurrency theft scandal.
Two South African brothers are facing mounting pressure to come forward to authorities as investigators delve into one of the biggest cryptocurrency thefts in the country.
Raees and Ameer Cajee are central figures in the now infamous Africrypt cryptocurrency investment scheme saga. Local investors have been left in the dark and out of pocket following what the Cajee brothers claimed was a hacking incident that saw the company’s cryptocurrency holdings stolen.
The brothers headed up the purported investment firm which promised lucrative returns on investments, as per its 2020 investment presentation. Clients could either make South African rand or Bitcoin (BTC) deposits to Africrypt, which then managed those investments.
Things fell apart in April 2021 after Raees Cajee informed investors through a letter that hackers had allegedly stolen an unconfirmed amount of its holdings. Shortly after the Cajees had pleaded with clients not to opt for legal proceedings, the Africrypt website went offline.
There are conflicting reports around the actual value of cryptocurrency that was managed by Africrypt — but a June 2021 report by the Wall Street Journal quoted the eldest brother’s estimate that Africrypt was managing around $200 million worth of cryptocurrency at the height of the market’s 2021 boom.
Investors have sought legal counsel in order to wrestle back their funds from Africrypt, while financial regulators have been hamstrung by current regulations of cryptocurrencies in South Africa, which leaves the space out of their jurisdiction.
It’s important to note that the Africrypt saga is not the first time that the Cajee brothers’ businesses have fallen prey to alleged hacking incidents. Back in 2019, RaeCreate Wealth, which is incorporated in Hong Kong and ran by Cajees’ informed investors, had some of its cryptocurrency stolen during a Binance hack.
It is unclear whether investors were ever reimbursed for their losses as the Cajees registered Africrypt in the same year, according to the company’s registration documentation verified by Cointelegraph.
The Cajee Brothers Disappear
The exact whereabouts of the Cajee brothers are still unknown, and the pair have previously claimed their flight from South Africa was necessitated by subsequent threats from a number of disgruntled clients that have banded together to seek legal recourse.
Local company Badaspex (Pty) Ltd. is spearheading its own legal effort to recoup funds invested in Africrypt. The company launched an application on April 19, seeking for Africrypt to be liquidated following the scheme’s claims that it had lost investors’ holdings.
Cointelegraph contacted Johannesburg-based attorney Gerhard Botha who is representing Badaspex, as well as other investors that lost funds to Africrypt. Botha confirmed that Badaspex is looking to recover $2.4 million (35 million rands) invested in Africrypt, a figure that has not accounted for the appreciation in value of the BTC that was entrusted to the Cajee brothers’ firm.
The attorney is representing a total of 105 investors, whose lost investments amount to what he described as a “conservative” $8 million (115 million rands).
The attorney also refuted the Cajees’ claim in the WSJ in June that Badaspex’s director Juan Meyer, a figure once linked to locally convicted Czech gangster Radovan Krejcir, had threatened them after Africrypt shuttered.
Meyer’s attorney said his client had tried to meet with one of the brothers at a hotel in Johannesburg to discuss Africrypt’s closure. After agreeing to meet, Meyer was left waiting at reception for about 15 minutes before the hotel’s security requested him to vacate the premises. Botha told Cointelegraph that the version of events put forward by the Cajees was “opportunistic,” given that the incident was clearly set out in the court-order application:
“The version that the Cajees put forward is unfortunate because the visitation of Mr. Meyer was recorded in the court application. […] There was no physical interaction between the two. The Cajee brothers were allowed to answer that version in court and they’ve elected not to.”
The Cajee brothers employed the legal services of Johannesburg-based attorney John Oosthuizen soon after the hacking incident was claimed to have taken place. Oosthuizen had made several comments to the media before announcing that he was no longer representing the brothers or Africrypt in late June 2021. Africrypt has until July 19 to make a case against the Badaspex liquidation order application.
A separate source undertaking a private investigation into the Africrypt debacle told Cointelegraph that it was aware that 35 separate criminal cases have been opened, seeking around $3.2 million (46 million rands) invested in the scheme.
Bank documents seen by Cointelegraph show that more than $7 million (100 million rands) passed through the Cajees’ local business bank account — a point of contention that has been denied by First National Bank.
It is understood that the brothers left South Africa in December 2020 and have been traced to different hotels in the United Arab Emirates.
Africrypt Not Under South Africa’s FSCA Jurisdiction
This type of financial fraud would usually fall under the jurisdiction of the South African Financial Sector Conduct Authority (FSCA). Cointelegraph reached out to the regulatory body to ascertain whether it is actively involved in ongoing investigations into the Africrypt case.
The FSCA replied with a public statement it had released acknowledging complaints received against Africrypt and was investigating whether the firm had actually offered a financial product or service to the public. This is a crucial aspect, as it would have required Africrypt to have registered with the regulator, which it has not. The FSCA statement read:
“At this stage, we have only found evidence of crypto-asset transactions. Currently, crypto assets are not regulated in terms of any financial sector law in South Africa and consequently, the FSCA is not in a position to take any regulatory action.”
While the FSCA is not in a position to impose any sanctions on the company, it did state that its own investigations into the firm suggest that it was operating a dubious investment scheme: “This entity was offering exceptionally high and unrealistic returns akin to those offered by unlawful investment schemes, commonly known as Ponzis.”
In another local report, Raees Cajee claimed that Africrypt had been registered with the Financial Intelligence Centre (FIC) and that the company had abided by necessary Anti-Money Laundering (AML) controls. Cointelegraph has reached out to the FIC to ascertain whether Africrypt was registered with the center, but has not received a reply at the time of publication.
Clients Used The Local Exchange To Send Crypto To Africrypt
Information provided to Cointelegraph by private investigators allowed for some basic blockchain analysis of transactions sent to and from Bitcoin addresses provided to Africrypt clients over the past few months.
Some clients’ wallets received BTC from an original wallet that has received more than 689,000 BTC, worth around $22 billion, since November 2020. Cointelegraph has ascertained that this is the hot wallet belonging to prominent South African cryptocurrency exchange Luno.
International blockchain analytics firm CipherTrace assisted in this regard but noted that the exchange was likely to have only been used to handle Africrypt customers’ deposits and not to accumulate holdings. The CipherTrace spokesperson told Cointelegraph:
“It is certainly possible that some of the Africrypt funds were either deposited to or sent to this exchange, which could be an indicator that Africrypt was not a standalone ‘exchange,’ but actually more of a high-yield investment program.”
Luno Africa’s general manager, Marius Reitz, told Cointelegraph that Africrypt does not hold a Luno account and that there is no relationship between either company: “Although Africrypt began the process of applying for a Luno account in 2019, the process was never completed and therefore the business account was never opened.”
Reitz added that Luno did not receive any customer queries in relation to Africrypt prior to news reports of the company’s collapse. He added that Africrypt had not been flagged by any of the blockchain analytics companies that focus on detecting and preventing the use of cryptocurrencies in illicit activities. Nevertheless, the exchange is involved in ongoing investigations:
“Luno has engaged and continues to work with authorities and interested parties. Our preliminary investigations indicate that the amount claimed appears to be grossly overstated. In addition, the overwhelming majority of known related companies and associates provided to us did not hold Luno accounts.”
Private investigators also told Cointelegraph that some BTC was allegedly moved to VALR, another popular South African cryptocurrency exchange, after blockchain analysis was carried out on another Africrypt client’s Bitcoin wallet address.
VALR CEO and co-founder Farzam Ehsani told Cointelegraph that they could not share any information on its users, while adding that it was registered with the FIC and did what it could to prevent illicit activity through its platform: “VALR is registered with the Financial Intelligence Centre and we engage with the regulators on a regular basis to combat any activity by any actor that seeks to abuse our industry or cause harm to others.”
Africrypt’s Theft Amount “Grossly Overstated”
Initial media reports on the Africrypt saga pinned astronomically high values to the amount of assets under the company’s management. Figures as high as $3.6 billion had originally been touted — numbers that Reitz believes are improbable:
“At present, it appears that the amount of almost 70,000 BTC claimed to have been moved is grossly overstated. The movement of such a large amount of BTC would have raised several red flags for exchanges and blockchain analytics companies, particularly given the claim that it was moved in the space of a few hours.”
Reitz also noted that the accuracy of the reported scale of the Africrypt scheme is an important consideration. The sheer scale of the initial amounts reported would simply be unable to be moved or mixed without affecting cryptocurrency markets or being flagged by analytic firms.
Reitz further said that following the collapse of Mirror Trading International in 2020, this latest incident serves as an important reminder to investors to do their homework when entrusting assets to third parties:
“Any guarantee of earnings should be viewed with suspicion, as returns cannot be guaranteed when it comes to cryptocurrencies. Many financial fraud schemes talk about ‘bots’ that trade on your behalf and present fake testimonials as proof of guaranteed or outsized returns. If something sounds too good to be true, it probably is.”
Updated: 8-12-2021
Over Half of Stolen Fund From Poly Network (DeFi) Hack ($600 Million+) Returned
$342 million had been returned as of 08:18 AM UTC Thursday, according to a tweet by Poly Network.
More than half of the $600 million+ drained from the Poly Network earlier this week has now been returned.
* About $342 million had been returned as of 08:18 a.m. UTC (4:18 a.m. ET) Thursday, according to a tweet by Poly Network.
* The decentralized finance (DeFi) platform which operates on Binance Smart Chain (BSC), Ethereum and Polygon was hit by a hack that drained over $600 million in crypto earlier this week.
* The hacker began returning the funds on Tuesday to wallet addresses across the three chains.
* The $342 million now returned is made up of $4.6 million on Ethereum, $252 million to BSC and $85 million to Polygon.
* The $268 million still outstanding is on Ethereum.
Hackers Return Funds From Likely Record DeFi Crypto Attack
Hackers returned about half of the $610 million or so they pilfered Tuesday in what was likely one of the biggest cryptocurrency thefts on record in the burgeoning DeFi sector.
In a unusual twist, the online thieves pledged to return the entire amount stole from a decentralized finance, or DeFi, protocol known as PolyNetwork that lets users swap tokens across multiple blockchains. It isn’t clear from the PolyNetwork website who runs the protocol.
In a message the unidentified hackers said that they “just dumped all the assets,” adding, “hacking for good, I did save the project.” About $260 million has been returned so far, according to Tom Robinson, co-founder of blockchain forensics firm Elliptic.
Even more brazen, the hackers are asking for donations as a reward for returning the funds. So far, they’ve garnered $200, Robinson said.
The hackers also posted a Q&A online, explaining motivations for the attack as “for fun:).” The online pirates said they took the funds “to keep it safe” after spotting a bug in the computer code. The hackers ended the missive saying they will be impossible to trace. “I prefer to stay in the dark and save the world.”
Blockchain security researcher SlowMist had said that it’s found the attackers’ email address, IP address and device fingerprint.
Elliptic, as well as scores of cryptocurrency exchanges and trackers, have been on the hunt for the hackers. Thousands of people were affected by the attack, PolyNetwork said in a letter posted Tuesday on Twitter.
“This demonstrates that even if you can steal crypto assets, laundering them and cashing out is extremely difficult, due to the transparency of the blockchain and the use of blockchain analytics,” Robinson said. “In this case the hacker concluded that the safest option was just to return the stolen assets.”
The heist netted 11 different cryptocurrencies, including $93 million in Ether, according to blockchain researcher Chainalysis, which tracked some of the hackers’ transactions. The attacker had attempted to launder part of the money by using PolyNetwork to cash in Dai and USDC coins and converting them all back to Dai, Chainalysis said.
DeFi apps — which let people lend, borrow and trade coins without using intermediaries — have become frequent targets of attacks lately, as they gain in popularity. Some $156 million was netted from DeFi-related hacks in the first five months of the year, surpassing the $129 million stolen in such attacks through all of 2020, according to crypto security firm CipherTrace.
Updated: 8-15-2021
Hacker Returns Stolen (Poly Network) Cryptocurrency In Heist Reversal
All stolen crypto assets have been returned, except those that were frozen, Poly Network says.
The hacker or hackers who plundered more than $600 million of cryptocurrency assets from a decentralized finance platform finished returning almost all of the money Friday, marking a surprise conclusion to a heist that rattled the crypto industry.
The assets were transferred back to blockchain addresses controlled by Poly Network on Friday, according to an emailed statement from the company. All that remains outstanding are $33 million of tether tokens, frozen by the company Tether in the effort to recover the stolen goods.
Poly Network is still waiting for the hacker to provide access, known as the final key, to the wallet containing the returned crypto, the company said.
The incident highlights the risks of trading in crypto markets. Securities and Exchange Commission Chairman Gary Gensler said recently that the area is rife with “fraud, scams and abuse” and in need of investor protections and regulation.
“When I look at DeFi projects, this stuff is not tried-and-true-tested,” said Halsey Huth, head of growth at MoonPay, a cryptocurrencies payments platform, referring to companies that provide financial services using blockchain technology. “Everyone interacting with this stuff knows there’s always a chance there’s going to be a bug or an exploit.”
Poly Network, which uses digital assets for lending and other financial transactions, on Tuesday disclosed the hack in a Twitter post, saying cryptocurrencies including ether, tokens backed by bitcoin and Shiba Inu coin had been taken. The blockchain security company SlowMist said the missing assets were valued at $610 million.
The theft rippled across platforms, with executives at Tether and Binance—the world’s largest cryptocurrency exchange—tweeting that the companies were coordinating in the effort to help.
Tether’s chief technical officer said the company froze $33 million of its cryptocurrency in one of the hackers’ addresses.
Then Poly Network said Wednesday that assets worth around $260 million had been returned. In a series of question-and-answer posts about the heist on a blockchain account used to hijack the funds, the purported hacker or hackers said they intended to expose vulnerabilities in the system and had always planned to return the money.
“I am not very interested in money! I know it hurts when people are attacked, but shouldn’t they learn something from those hacks?” one of the posts said. The hacker or hackers said that they were negotiating with the Poly Network team and that they “would like to give them tips on how to secure their networks.”
Some analysts said the stolen assets might have proved harder than expected to liquidate. The transparent nature of blockchain technology, which records every transaction on a public ledger, can make “the process of cashing out and laundering many cryptocurrencies prove difficult for the lesser professional career criminal,” said Jake Moore, a specialist at cybersecurity firm ESET.
“However, next time, the attackers may plan an exit strategy involving cryptocurrencies that aren’t so well monitored.”
Poly Network said it offered $500,000 to the hacker, who the company called Mr. White Hat, as a reward. A white hat is a term for an ethical computer hacker.
“We would now like to thank his commitment for helping us improve Poly Network’s security and hope he will help contribute to the blockchain sector’s continued development upon accepting the Bug Bounty,” Poly Network said.
It also said that it is working with Tether to unfreeze and recoup the remaining $33 million of assets.
The Poly Network hack is on par in size with breaches at Coincheck in 2018 and Mt. Gox in 2014, in which digital assets valued at around $550 million and $400 million, respectively, went missing.
In May, the Federal Bureau of Investigation was able to trace cryptocurrencies paid in a $4.4 million ransom by Colonial Pipeline Co. and recover around 64 bitcoin.
Poly Network was founded by a China-based entrepreneur and operates in the burgeoning DeFi sector, which includes companies that offer financial services on public blockchains, the digital ledgers that underpin cryptocurrencies.
Like banks, DeFi firms perform services including lending out assets and writing derivative contracts. Investors often use DeFi companies to borrow against their crypto holdings and amplify their bets.
Unlike regular financial institutions, everything revolves around privately generated digital currencies. No central bank processes transactions and oversight and regulation are limited.
Poly Network’s system allows users to operate between multiple blockchains and transfer assets across the chains, the company has said in public postings.
The hack accessed the assets by exploiting a vulnerability between “contract calls,” according to Poly Network. That means the hackers found vulnerabilities when two programs that automatically execute transactions on the blockchain were running at the same time, analysts said.
“There’s certain responsibilities when you’re in this space, you’re responsible for your wallet and your keys,” said Joel Kruger, a currency strategist at LMAX Group, a platform for foreign exchange and cryptocurrency trading. “It’s a bit of a Wild West out there. You have to be diligent.”
Poly Network Offers To On Board ‘Mr. White Hat’ As Chief Security Advisor
“Poly Network has no intention of holding Mr. White Hat legally responsible,” said the team.
Decentralized finance protocol Poly Network has offered the person behind a $610 million hack an advisery position and $500,000 — whether they like it or not.
In a Tuesday update, the Poly Network team said, in a seeming attempt to gain access to the hacker’s expertise, that it would be inviting them to the position of chief security adviser. In addition, the project will be sending a $500,000 bounty for the attacker, whom Poly dubbed “Mr. White Hat,” despite the fact they have previously refused any payment.
“Poly Network has no intention of holding Mr. White Hat legally responsible, as we are confident that Mr. White Hat will promptly return full control of the assets to Poly Network and its users,” said the team. “As we have stated in previous announcements and encrypted messages that have been made public, we are grateful for Mr. White Hat’s outstanding contribution to Poly Network’s security enhancements.”
The hack was reported on Aug. 10, when analysts noted that roughly $610 million had been removed from the Polygon network, the Binance Smart Chain and Ethereum. The hacker subsequently communicated with the Poly Network team and others through embedded messages in Ethereum transactions, agreeing to return the funds. Poly Network said it determined that the attack constituted “white hat behavior” and offered Mr. White Hat a $500,000 bounty.
The Poly Network team said it was “counting on more experts like Mr. White Hat to be involved” in the future development of the project, “since we believe that we share the vision to build a secure and robust distributed system.” The hacker returned all the funds with the exception of $33 million in frozen Tether (USDT), but has not yet turned over the key to the multisig wallet Poly set up for the transfer.
It’s a somewhat surprising turn for the individual responsible for the largest hack in decentralized finance, or DeFi, to be offered a reward and a — presumably — paid position at the company which was the target of their attack. Though the hacker’s identity has yet to be made public, Chinese cybersecurity firm SlowMist posted an update shortly after news of the hack broke, saying its analysts had identified the attacker’s email address, IP address and device fingerprint.
“We are grateful for Mr. White Hat’s outstanding contribution to Poly Network’s security enhancements,” said the Poly Network. “While there were certain misunderstandings in the beginning due to poor communication channels, we now understand Mr. White Hat’s vision for Defi and the crypto world, which is in line with Poly Network’s ambitions from the very beginning.”
With the exception of thousands of users being temporarily unable to access their funds, the events of the last week seem to have had a net result of additional media attention over the Poly Network. Data from Google shows interest in the DeFi project reached an all-time high on Wednesday and is still well above what it had been since Poly launched last year.
Updated: 8-19-2021
Liquid Exchange Hacked To The Tune Of $80 Million
Over $80 million worth of digital assets has been removed from Liquid Global exchange. KuCoin has responded by blacklisting the addresses that received stolen funds.
Japanese exchange Liquid has been hacked, with about $80 million in digital assets moved off the platform.
The exchange confirmed the security breach in a Thursday tweet, with Liquid revealing the wallet addresses implicated in the breach. The exchange noted that only its warm wallets were affected, adding that its assets are currently being moved into cold storage.
Withdrawals and deposits have been suspended on Liquid, with the exchange promising to provide regular updates as its investigation unfolds.
The following assets had been transferred to hacker’s following addresses (Further investigation to come):
BTC: 1Fx1bhbCwp5LU2gHxfRNiSHi1QSHwZLf7q
ETH/EWT: 0x5578840aae68682a9779623fa9e8714802b59946
TRX: TSpcue3bDfZNTP1CutrRrDxRPeEvWhuXbp
XRP: rfapBqj7rUkGju7oHTwBwhEyXgwkEM4yby— Liquid Global Official (@Liquid_Global) August 19, 2021
While Liquid is yet to confirm exactly how much has been taken, Cointelegraph has identified that more than 107 Bitcoin (BTC), 9,000,000 Tron (TRX), 11,000,000 XRP, and almost $60 million worth of Ether (ETH), and ERC-20 tokens appear to have been taken by the hackers.
There are unconfirmed reports that the Ethereum wallet compromised held deposits from crypto yield provider Celsius Network. In April, Celsius announced that it had integrated with Liquid to offer the exchange’s customers a compounding return on digital asset purchases.
The announcement noted that Liquid became one of the first fiat-to-cryptocurrency exchanges to support Celsius’s native CEL token in 2019, stating that the two firms “have continued to grow their partnership” since.
Another exchange, KuCoin, promptly responded to the hack by blacklisting the addresses involved in the hack, according to a tweet from the exchange’s CEO, Jonny Lyu.
We are aware of the #LiquidGlobal security incident, and the hacker’s addresses have been added to the blacklist of #KuCoin. Hope everything is OK. https://t.co/IasscGItZH
— Johnny_KuCoin (@lyu_johnny) August 19, 2021
In November 2018, Liquid suffered a breach that saw its users’ personal information exposed to hackers, possibly including names, addresses and passwords.
White Hats Just Defused A Potential $350M Heist On SushiSwap
“Chad af,” one Twitter user commented on the rescue action.
A group of people in the crypto community, led by crypto investment firm Paradigm’s research partner Sam Sun, may have just prevented SushiSwap’s token fundraising platform Miso from losing more than $350 million worth of ether (ETH, +7.93%), after discovering and fixing a bug on the platform in under just five hours.
Because of the collective efforts, SushiSwap says no funds have been lost.
According to a post published by SushiSwap on Monday, Sam Sun, and his colleagues Georgios Konstantopoulos and Daniel Robinson – all from San Francisco-based crypto investment firm Paradigm – reached out to the team at Sushi to alert them to “a vulnerability” on the “Dutch auction” contract on the Miso platform.
In a Dutch auction, investors place bids reflecting the maximum amount that they are willing to pay. Once the bids are collected, the highest bid is declared the winner. After the auction is finalized, unsuccessful bids are returned to their owners.
The vulnerability
The SushiSwap team and Paradigm’s Sun, in separate posts, both identified that, essentially, the vulnerability was centered around the ability to batch multiple calls to commitEth and reuse a single msg.value across every commitment, allowing an attacker to bid in the auction for free.
“Combining batch with commitEth (a function on Miso Dutch Auction) creates a two-pronged issue where a user can both put up a commitment higher than ‘msg.value’ thereby draining any unsold tokens and additionally drain the raised funds on the contract as refunds if the auction has reached max commitment,” SushiSwap’s team wrote in the post.
“The bug was created when a convenience function for wallet addresses interacted with the refund mechanism of the auction contract,” explained Duncan Townsend, CTO at Immunefi, a bug bounty platform for decentralized finance (DeFi) that was also recruited to help solve the issue.
“Users could over-bid and get a refund of the difference between the current bid and the amount they submitted, but the refund could be repeated to drain the auction contract,” Townsend added.
“All future planned auctions utilizing the specific Dutch auction contracts with ETH commitments have been paused until an updated version is redeployed,” SushiSwap’s team wrote.
The Takeaway: Smart Contracts Are Hard
At the conclusion of his blog post, Sun reflected that one of the most important lessons to be learned from this discovery is that even “safe components can come together to make something unsafe.”
The smart contracts that underpin DeFi are complex, combining “composable” “Lego blocks” to create new contracts and protocols. But the manner in which these blocks are combined can have inadvertent, disastrous consequences, even when programmers are using inherently safe individual components.
“This incident shows that even safe contract-level components can be mixed in a way that produces unsafe contract-level behavior. There’s no catch-all advice to apply here like ‘check-effect-interaction,’ so you just need to be cognizant of what additional interactions new components are introducing,” Sun said.
The event took place just after the biggest DeFi exploit to date took place last week: Cross-chain DeFi site Poly Network was attacked, losing more than $600 million worth of cryptocurrencies, due to a bug.
In the case of the SushiSwap vulnerability, however, many in the crypto community have taken to social media to praise the five-hour collective rescue efforts led by the research arm at Paradigm.
“Chad af,” Twitter user @KadenZipfel wrote (a “chad” usually refers to an “alpha male” in the common parlance of internet slang).
“Absolute King,” another Twitter user, @BanhbaoCrypto, wrote. “The Defi super hero we all need but don’t deserve!”
Updated: 8-24-2021
Poly Network Hacker Releases Private Key For Remaining Looted $141M
In a note to the Poly Network team, the attacker referred to the saga as “one of the most wild adventures in our lives.”
The attacker who hacked more than $600 million from the China-based Poly Network platform has released the private key for the remaining $141 million of the stolen cryptocurrency.
* In a note to the Poly Network team, the attacker or attackers referred to the saga as “one of the most wild adventures in our lives.”
* The note was posted to Twitter by Chinese reporter Colin Wu.
* Poly Network subsequently tweeted its thanks to the attacker or attackers, posting a link to a transaction on the Ethereum blockchain confirming that the key worked.
* The majority of the funds stolen in the Aug. 10 attack had already been recovered, but the hacker or hackers last week threatened to delay publishing the private key for the remainder.
* In the note to Poly Network, the attacker or attackers described their reasoning behind the delay, citing desire to “unlock the USDT.”
* Tether, the developer of USDT, had frozen $33 million worth of the dollar-linked stablecoin that was looted in the attack.
* “In my selfish view, the story is tainted by the locked USDT. It would have been a perfect example of building trust between anonymous ‘adversaries’ by leveraging the power of smart contract,” the hacker or hackers wrote in the note.
* The hack is considered the largest of its kind in decentralized finance (DeFi), highlighting the risks for investors and traders in the crypto sector.
Updated: 8-26-2021
Hacked Liquid Exchange Receives $120M Debt Funding From FTX
The funding comes soon after Liquid suffered a major hacking incident last Thursday when the exchange’s hot wallets were compromised.
Japanese cryptocurrency exchange Liquid has secured $120 million in debt financing from FTX Trading after suffering a nearly $100-million hack last week.
Announcing the news Thursday, Liquid Group and FTX Trading — the owner and operator of crypto exchange FTX — said that the new funds will help Liquid improve its balance sheet and contribute to the exchange’s licensing opportunities in the key jurisdictions of Japan and Singapore. The new funding also targets new capital generation, increasing liquidity, as well as improving Liquid’s customer support, the announcement notes.
FTX CEO and founder Sam Bankman-Fried said that the new financing underpins collaborative efforts of both exchanges to drive crypto adoption and provide better service to the ecosystem. ”This opportunity with Liquid allows both organizations to strengthen and reinforce the belief that regulation in crypto and knowing your customer is an important part of the future of our industry,” he stated.
The funding comes soon after Liquid suffered a major hacking incident last Thursday when the exchange’s hot wallets were compromised. According to calculations by blockchain analytics firm Elliptic, the Liquid hackers stole a total of $97 million in various cryptocurrencies, including Ether (ETH), XRP, stablecoins, Bitcoin (BTC) and other tokens.
In an incident update on Monday, Liquid reassured customers that “they will not suffer any loss due to the incident,” adding that user balances will be unaffected. “We continue to work diligently to gradually restore crypto deposit and withdrawal services,” Liquid noted.
Incident update – 25th August 2021:
We want to reassure our users that they will not suffer any loss due to the incident that took place on the 19th of August. There will be no impact on user balances at Liquid. https://t.co/UaakRgafFV
— Liquid Global Official (@Liquid_Global) August 25, 2021
Founded in 2014, Liquid is a major cryptocurrency exchange licensed under Japan’s Payment Services Act through its Japanese operating entity, Quoine Corporation. Liquid’s Singapore operating entity, Quoine Pte, has also applied to the Monetary Authority of Singapore for a license under Singapore’s Payment Services Act.
Liquid’s hack was the second major crypto heist that took place this month, following a massive exploit of cross-chain protocol Poly Network on Aug. 10. As of Monday, Poly Network regained control of $610 million in assets affected in the attack as the unknown hacker returned the stolen funds to the network.
Bitstamp And Ledger Execs Weigh Customer Service Debate After Coinbase Saga
A new investigation has revealed hundreds of Coinbase customer complaints around hacking and lost funds, drawing attention to the customer experience at crypto exchanges.
Popular cryptocurrency exchange Coinbase recently amassed a panoply of customer service complaints regarding account locking, hacking and even lost funds.
A recent tweet by crypto analyst Kaleo garnered hundreds of user comments on their unfavorable experiences with the exchange. This isn’t the first time the firm has experienced a backlash over its customer service practices. Back in March, the New York Times published the story of a customer who lost over $100,000 on the platform and went on to sue the company.
Coinbase users have reportedly filed over 11,000 complaints against the platform with the Federal Trade Commission and Consumer Financial Protection Bureau since 2016. The majority of these claims are based on customer service issues.
Cointelegraph spoke to two industry experts — Bobby Zagotta, US CEO at Bitstamps, and Iqbal Gandham, the vice president of transactions at Ledger — who shared their perspective on the Coinbase saga, a fresh vision for customer service experiences in crypto, as well as the pitfalls of centralized exchanges. Zagotta told Cointelegraph:
“Crypto is experiencing a massive rate of adoption so dramatic that doing customer service right is challenging for everyone. I feel what is happening is that some crypto companies approach customer service like a tech company. What this means, is a lot of MVP products, with automated customer service powered by chatbots. What is missing, is the human element.”
Iqbal Gandham, VP Of Transactions At Ledger Shared His Thoughts On The Importance Of Truly Owning Your Crypto Assets:
“It seems like the term ‘Not your keys, not your crypto’ will never lose resonance. With so many folks entering the crypto space, we can never have enough education on what it means to actually OWN your crypto. The typical crypto journey narrative has remained the same: Coinbase and others serve as crypto on-ramp for many folks, and down the line, some users eventually learn enough to move their assets into hardware wallets.”
In April, Coinbase became an industry pioneer as the first crypto exchange to debut on the Nasdaq stock exchange. The move fuelled mass enthusiasm across the market, promising to be a catalyst for greater awareness from the traditional markets and, in turn, technical price rises for a multitude of assets.
Under the ticker COIN, shares are currently valued at $260 with a market capitalization of just shy of $68 billion.
Although no significant impact has been witnessed on its share price, this saga has certainly harmed the public reputation of a firm vying to be the benchmark for crypto exchanges as the industry emerges into the mainstream.
Gandham Outlined The Benefits Of Using An External Hardware Wallet Such As A Ledger To Store Your Crypto Assets:
“Thanks to the strides the industry has made in mass adoption, we now seem to be entering into a phase where those new to crypto understand their journey should begin with security. Over the recent months, we have seen hacks on exchanges, funds being lost. The best way to prevent this is to take ownership of your crypto. By using a Ledger nano, you ensure that funds can only be sent when you physically sign the transaction.”
Zagotta Shared The Steps Bitstamp Has Taken Regarding Its Customer Service Experience:
“Having access to a real person to help our customers when they need it, is important to us. Our client service team are real people who care about crypto and care about our customers. For example, our average wait time for customer service is only 22 seconds. We’re constantly looking to improve because we believe that a focus on customer experience will drive industry growth and introduce more people to the benefits of crypto.”
Updated: 8-27-2021
Steven Seagal On Hook For SEC Crypto Fine Despite Move To Moscow
Steven Seagal who starred in the film “Beyond the Law” found out that even relocating to Russia doesn’t mean he’s beyond the reach of U.S. courts as the Securities and Exchange Commission won a judgment against him.
A federal judge in Brooklyn, New York, said the SEC can go through Seagal’s business manager to try and collect more than $200,000 that the actor owes the U.S. government for failing to disclose he was being paid to promote a digital token.
U.S. District Judge William Kuntz signed the order Friday allowing the SEC to pursue collection of the remaining fines, penalties and interest. Seagal had agreed to pay a disgorgement of more than $330,000, but the actor made just one $75,000 payment and is delinquent on the remainder, according to a letter from Maureen Peyton King, a lawyer for the SEC.
Chris Nassif, a spokesman for Seagal, didn’t immediately have a comment about the court order.
Seagal agreed to settle the commission’s allegations that he’d been promised $250,000 in cash and $750,000 in tokens for promoting an initial coin offering for Bitcoiin2Gen. In social media posts, Seagal had urged fans not to miss out on the offering. The actor settled the allegations without admitting or denying wrongdoing.
Seagal, who now lives in Moscow, hasn’t responded to the SEC’s repeated demands after making his initial payment, according to the commission.
Russian President Vladimir Putin issued a presidential decree in 2016 granting the actor Russian citizenship.
Kuntz last week directed Seagal or his representatives to appear in court to respond to the SEC. But on Friday, neither Seagal, his former lawyer nor his manager appeared.
After Kuntz signed the order Friday afternoon, Peyton King asked if she could serve the papers upon King’s business manager.
“Absolutely, yes,” Kuntz said with a smile.
The case is Securities and Exchange Commission v. Seagal, 21-mc-01797, U.S. District Court for the Eastern District of New York (Brooklyn).
Updated: 8-30-2021
Money Trail From Liquid Exchange Hack Points To Wasabi Privacy Wallets
Hackers are using Wasabi wallets to launder BTC stolen from Liquid or received in exchange for other stolen cryptos, according to Crystal Blockchain.
Hackers who stole about $97 million in cryptocurrency from the Liquid exchange used the non-custodial, privacy-focused Wasabi wallet to protect some of their gains, according to sleuthing firm Crystal Blockchain.
Bitcoin from the wallets Liquid identified as belonging to the hackers has been on the move over the past two weeks, public blockchain data shows.
For example, on Aug. 29, 100 BTC (worth over $4.8 million) from one hacker-linked address was split up and sent to two separate addresses, then further broken into smaller pieces and distributed to yet more addresses.
At least some of that bitcoin was then sent to addresses believed to be generated by a Wasabi wallet, according to Crystal Blockchain data.
This was one of many similar transactions that the hackers made using Wasabi, presumably to disconnect the stolen funds from their criminal history, according to Crystal. This would be a necessary step to spend such funds or sell them for fiat money, because centralized exchanges tend to freeze funds that are known to come from hacks, exploits and scams.
Over 437 BTC (worth over $20 million) associated with the Liquid hackers have been laundered using Wasabi’s CoinJoin feature, and the process is still ongoing, according to Crystal.
Earlier this month, CoinDesk tracked other funds funneled out of Liquid, finding that ethereum (ETH, 2.84%) and ERC20 tokens were sent to Ethereum-based online mixer Tornado.cash and decentralized exchanges (DEXs).
Wasabi is a privacy-focused desktop wallet that allows users to make their bitcoin less traceable on the public ledger by arranging so-called CoinJoin transactions. Multiple users can commingle their bitcoin in joint transactions and get it back disconnected from the previous history of payments. It also routes transactions over the Tor network which further helps to conceal the user’s IP address.
Although Wasabi is a non-custodial wallet that doesn’t store users’ funds, it generates addresses for CoinJoin transactions that blockchain analytics tools have learned to identify. Crypto sleuthing firm Elliptic did this last year, following bitcoin coming from the infamous Twitter hack to addresses associated with Wasabi.
According to Kyrylo Chykhradze, product director for Crystal Blockchain, identification of such addresses is more challenging than attributing addresses to custodial crypto services, so Crystal makes “a lot of double-checks before the final labeling” of the addresses in their analytics system.
Wasabi did not immediately respond to a request for comment.
Swapped And Tumbled
According to Crystal Blockchain, wallets associated with the Liquid hackers received some 1,168 BTC in total, most of which they got by swapping other cryptocurrencies for bitcoin on several exchanges.
CoinDesk previously reported that the hackers sent stolen xrp (XRP, 1.55%) tokens to three exchanges – Binance, Huobi and Poloniex – where they managed to exchange them for bitcoin on the first day after the hack. That bitcoin stash was later partially laundered via Wasabi’s CoinJoin addresses, according to Crystal.
ERC20 tokens, which run on the Ethereum blockchain, had been sent to decentralized exchanges (DEXs), swapped for ether and then sent to Tornado.cash, an online mixer for ether. Some tokens were also swapped for bitcoin on the decentralized exchange Ren, resulting in additional 394 BTC in the hackers’ stash, Chykhradze said.
“For almost two weeks hackers have been using different methods to cover their tracks – substantial amounts of XRP, ETH and ERC20 tokens were either converted into BTC or mixed through the Tornado tumbler service,” Chykhradze said.
Plus, several dozen BTC were put on multiple unidentified wallets and left there for now.
Liquid, a Japanese cryptocurrency exchange, was hacked on Aug. 18. About $97 million worth of multiple cryptocurrencies were siphoned out. The exchange immediately started publishing updates on the hack and the addresses to which the hackers withdrew money.
Several exchanges worked with Liquid to label and block the addresses related to the hackers, they previously told CoinDesk. However, in many cases the hackers managed to get funds out faster than the exchanges reacted.
On Aug. 30, Liquid posted an update urging users to generate new deposit wallets.
Updated: 9-1-2021
BitConnect Promoter Pleads Guilty Over Ponzi Scheme As Platform Faces New SEC Charges
Former BitConnect promoter Glenn Arcaro has pled guilty to his role in the saga, but the whereabouts of the firm’s founder, Satish Kumbhani, are unknown.
Glenn Arcaro, former director and promoter of the notorious BitConnect Ponzi scheme, has pled guilty to fraud charges related to his role in the now-defunct crypto exchange and lending platform.
He has been ordered to pay back $24 million to investors.
In a parallel action in the long-running saga, the United States Securities and Exchange Commission has charged BitConnect, its founder, Satish Kumbhani, former director Arcaro, and Future Money Ltd. for the scheme. The defendants are accused of running a fraudulent, unregistered securities offering that netted $2 billion.
The latest developments come three years after BitConnect shut down its lending platform and crypto exchange in light of warnings from Texas and North Carolina regulators.
BitConnect has been widely accused of being a Ponzi scheme, and the scheme lives on in countless memes.
“Fraudulent Marketing”
According to a Wednesday release from the Department of Justice, Arcaro pled guilty to charges alleging conspiracy to commit wire fraud.
The Los Angeles resident admitted to conspiring with “others” to exploit investors by “fraudulently marketing” BitConnect’s coin offering and crypto trading platform as a highly profitable investment.
The 44-year-old also admitted to misleading investors about the “BitConnect Trading Bot” and “Volatility Software” as being able to generate large profits and guaranteed returns by using investor funds to trade on the volatility of crypto markets.
“In truth, BitConnect operated a textbook Ponzi scheme by paying earlier BitConnect investors with money from later investors,” the DOJ release read.
Arcaro is said to have operated a large network of promoters in North America that formed a pyramid scheme dubbed the “Bitconnect Referral Program.” He earned around 15% per investment into BitConnect’s lending program, while he also received a cut from all investments via a hidden “slush” fund.
The former promoter admitted to earning around $24 million from his fraudulent activities and has been ordered to pay back the full amount to investors.
“Arcaro capitalized on the emergence of cryptocurrency markets, enticing innocent investors worldwide to get in early by promising them guaranteed returns, and exploiting the internet and social media to reach a larger pool of victims with greater ease and speed,” said Special Agent in Charge Ryan L. Korner of the Internal Revenue Service Criminal Investigation’s Los Angeles Field Office.
New SEC Charges
The SEC charges announced on Wednesday are aimed at BitConnect founder Kumbhani, former director Arcaro and Future Money Ltd — a firm incorporated by Arcaro in Hong Kong.
According to the complaint on Wednesday, the SEC alleges that the defendants conducted a fraudulent and unregistered securities offering via BitConnect’s lending platform between 2017 and 2018 that generated approximately 325,000 Bitcoin (BTC), worth $2 billion at the time.
Today, we announced that we have filed an action against an online crypto lending platform, its founder, and its top U.S. promoter and his affiliated company.
They allegedly defrauded retail investors out of $2 billion!
More:https://t.co/gO10Ag0tfh pic.twitter.com/XghdUBqaCz— SEC (@SECGov) September 1, 2021
The complaint asserts that users were duped into investing in the lending platform via claims that BitConnect’s trading bot would produce guaranteed returns of 40% a month, and it accuses BitConnect of posting “fictitious returns” on the website equating to an average of 1% per day, or 3,700% annually.
“These claims were a sham. As Defendants knew or recklessly disregarded, BitConnect did not deploy investor funds for trading with its purported Trading Bot. Rather, BitConnect and Kumbhani siphoned investors’ funds off for their own benefit and their associates’ benefit.”
The SEC notes that the whereabouts of BitConnect’s founder, Kumbhani, are currently unknown.
The SEC is seeking a full disgorgement of funds, the enjoinment of the defendants from violating securities laws in the future, and civil monetary penalties.
In May, the SEC charged six other BitConnect promoters for their role in the alleged insecurities offering, and Cointelegraph reported on July 8 that the SEC had closed in on settlements with four of the six individuals.
Updated: 9-2-2021
Biggest Crypto Coin Sale (EOS) Fueled By ‘Pump’ Scheme, Research (Integra FEC / Prof. John Griffin) Says
Bullish crypto exchange bankrolled by Block.one funds, discussed in newly published paper.
It would become the biggest digital token sale on record. Over 11 months in 2017 and 2018, a little known software maker named Block.one held an initial coin offering for a new cryptocurrency, raising more than $4 billion.
Backed by billionaire heavyweights including PayPal co-founder Peter Thiel, hedge fund magnates Alan Howard and Louis Bacon, and German entrepreneur Christian Angermayer, Block.one said it would use the money to build tools that would speed adoption of blockchain technology.
The newly minted currency, EOS, soon became mired in controversy.
The U.S. Securities and Exchange Commission fined Block.one $24 million in 2019 for failing to register the ICO, and token holders sued Block.one last year, calling the sale a “fraudulent scheme” and alleging that the company violated securities laws by making “false and misleading statements about EOS, which artificially inflated the prices for the EOS securities and damaged unsuspecting investors.” And some programmers and digital asset managers have said that the company for years showed scant progress toward its mission.
Newly published research by forensic financial analysis firm Integra FEC, led by University of Texas at Austin McCombs School of Business finance professor John Griffin, raises fresh concerns about the EOS initial coin sale.
Griffin, in interviews and a 14-page paper posted to the Integra website Tuesday, highlights a pattern of what he says are suspicious trades during the ICO. The transactions, between potentially connected associates, “pumped up” the price of EOS and induced unwitting investors to buy the currency, he alleges in the paper.
EOS Raised More Money Than Any Other ICO
Although thousands of companies have held an initial coin offering (ICO), EOS is the world champion, raising $4.2 billion. Competing cryptocurrencies like Ether raised less than $20 million in its ICO.
Griffin identified 21 accounts that over the course of the ICO engaged in regular, unusually large purchases of EOS, followed by sales of the currency to an exchange less than an hour later, a process he refers to as recycling. In all, the recycled funds amounted to 1.206 million Ether, the cryptocurrency used to trade EOS, or $814.6 million, Griffin estimates, saying the actual amount could be substantially higher and “could have also consisted of other means to manipulate the EOS price upward.”
The paper doesn’t identify the owners of the accounts, and Griffin doesn’t allege wrongdoing by any specific individual or Block.one itself. While crypto transactions are traceable through publicly available information, the entities behind them are harder to pinpoint. Griffin said neither he nor his firm received compensation for the paper.
In a statement in response to the paper, Block.one pointed to a report issued in July by the law firm Clifford Chance LLP that said it “found no evidence of any arrangements between Block.one and third parties by which third parties bought tokens on Block.one’s behalf.”
Clifford Chance, which completed the analysis with help from PwC and DMG Blockchain Solutions Inc., also said it found “no evidence that Block.one purchased tokens on the primary market.” (Block.one had commissioned the study in 2019 amid allegations that surfaced as early as 2017 over whether Block.one purchased its own tokens during the sale.)
Griffin’s paper “fails to acknowledge this and makes many errors in fact and logic in pursuit of a false thesis that can be easily disproven with publicly available information,” Block.one said in the statement. Block.one’s statement didn’t elaborate on what it believes those errors are. Block.one investors Thiel and Angermayer didn’t respond to requests for comment, while Bacon and Howard declined to comment.
Questions over the ICO take on added significance now that Block.one has shed more light on how it plans to use the money the company earned as revenue from it. Block.one said in May it will use proceeds from the sale and other sources of funding to launch a subsidiary called Bullish, a cryptocurrency exchange valued at about $9 billion.
The exchange, set to go public this year through a merger with a special purpose acquisition company, boasts several of the same investors who backed Block.one, including Thiel, Howard, Bacon and Angermayer. Other Bullish investors include Hong Kong scion Richard Li and a unit of Japanese investing giant SoftBank Group Corp. Its three-person board is comprised entirely of Block.one executives.
Bullish is preparing its public debut just as concerns around cryptocurrencies crescendo. SEC Chairman Gary Gensler is contemplating tighter oversight of digital money, and regulators around the world are grappling with how to rein in the excesses of a $2 trillion craze that involves wild price swings and a dearth of disclosure around the businesses that underlie publicly traded coins.
“We just don’t have enough investor protection in crypto,” Gensler said in a recent speech, comparing it to the Wild West. “This asset class is rife with fraud, scams and abuse in certain applications. . . . In many cases, investors aren’t able to get rigorous, balanced and complete information.”
How It Worked
Here’s how the trading volley played out, according to Griffin. First, parties transferred large amounts of Ether, another cryptocurrency, to specially created accounts on an exchange. Account holders then used Ether to purchase newly minted EOS coins at Block.one’s crowdsale — essentially an auction. But rather than hold onto EOS, as the other EOS buyers did, the parties “quickly and repeatedly” sold the EOS to the same exchanges for Ether — typically within 40 minutes of purchasing it. Those funds were then used to buy more EOS.
This Behavior Was Unusual For Several Reasons, According To Griffin:
Account holders typically sold EOS at a loss, instead of earning a profit by holding EOS throughout the ICO.
The accounts bought and sold a similar amount of Ether on a daily or weekly basis and, unlike other accounts that participated in the sale, “appear almost solely created for this purpose.”
Griffin flagged accounts as suspicious if they invested $15 million or more, compared with less than $10,000 for a typical account.
The Ether sent back from EOS’s crowdsale wallet to the Bitfinex exchange was delivered in an unusually complicated manner consistent with trying to obfuscate the identity and tracking of the funds, he said.
“The suspicious accounts created legitimacy and the perception of wide-scale interest in EOS, and thus were able to make EOS move from an obscure ICO to become a token of widely perceived value,” Griffin said.
EOS peaked at $21.54 in April 2018 before falling below $2 that December. Interest in the token revived in May when Block.one announced plans for Bullish, and it was recently trading at about $4.97.
Flagged Accounts
Griffin identified 21 suspicious accounts. Besides engaging in recycling, the accounts were rarely used for anything but buying EOS, he said. Here’s how Integra says it worked:
“The possible motive of arbitrage is an alternative hypothesis examined in the report, but — contrary to profitable arbitrage trading — the repeated trading pattern appears generally unprofitable,” Griffin said. “Sophisticated traders typically don’t repeatedly lose money on a trade unless they have an offsetting profit source or motive.”
A person close to Block.one disputes these findings, saying that the transactions reflect systematic traders taking advantage of price arbitrage. This person also said that selling the tokens would have had the effect of depressing the price of EOS, just as purchasing it buoyed the currency’s price.
No one would have the incentive to do that, said the person, who added that he didn’t know who the counterparties were.
Other factors could explain the rapid successions of buying and selling EOS around the time of its initial offering. A May 2018 posting on the software collaboration site GitHub describes an arbitrage opportunity generated by price discrepancies in the crowdsale and on crypto exchanges like Binance.
According to the writer, EOS coins distributed in the crowdsale chronically sold for less than coins trading simultaneously on the secondary market, and nimble traders who could buy and sell fast enough could sometimes lock in fast profits.
Griffin defended his work. Supply was fixed each day, so purchasing the tokens in the sale would buoy the price, he said in an interview. It was unprofitable to buy at the crowdsale and sell at the exchange almost twice as often as that same trade was profitable, he explained.
“Selling through the exchange could have minimal impact on the price, especially since it can be sold slowly and in a liquid market,” he said. He also disputed the idea that these trades were carried out simply to take advantage of price differences. “Market makers make a spread and make money on the spread,” he said. “These traders consistently lost money on their trades. Why would one engage in a losing strategy unless making money somewhere else?”
At Bloomberg’s request, Cornell Law School Professor Robert Hockett reviewed Griffin’s research and called the analysis “impeccable.”
“There’s enough smoke here to suggest there’s a fire,” said Hockett, who specializes in corporate law and financial regulation. Hockett said the actions described in Griffin’s report, if true, could violate the Securities Act of 1933 and the Exchange Act of 1934, which prohibit fraud and manipulative activities.
“This is what the SEC would call classic fraud and pump and dump. This is taking advantage of retail investors who don’t know what’s going on underneath and could be easily fooled.” The SEC and Department of Justice “should definitely be investigating,” he said.
Bloomberg Intelligence analyst James Seyffart also examined Griffin’s research using Etherscan, a tool for searching the Ethereum blockchain, a digital ledger of cryptocurrency transactions, and reached similar conclusions.
“The only reason they would be doing this is because they’re pumping or have failed miserably at attempting an arbitrage trade,” Seyffart said. “This definitely deserves a closer look.”
The SEC and Justice Department declined to comment.
EOS Recycling Scheme?
Circular transaction patterns, described in a new report, are consistent with fraudulent “pumping” of the token’s price, according to Griffin.
Recycling Accounts Typically Sold EOS Tokens Within 40 Minutes
While the Clifford Chance report was extensive, it also admits to limitations. In a section entitled “assumptions and limitations,” the report said “Block.one shareholders, employees, equity holders, directors, officers, suppliers and consultants (past, present or future) were permitted to participate in the token sale on the same terms as all other purchasers,” using their own funds — meaning that any such activity was outside the scope of the review of accounts, or wallets.
Also, the report only examined cryptocurrency wallets owned by Block.one with addresses provided by Block.one.
“Given the caveat that their analysis only applies to blockchain addresses that were provided by Block.one, the report seems to be unrelated to what we investigated,” Griffin said in an interview. “Due to the anonymous nature of the blockchain, it is very difficult to confirm whether the list of Block.one addresses analyzed by Clifford Chance and PwC is comprehensive.”
Clifford Chance explained its methodology in a statement, saying that while the review was limited to Block.one wallets, “our review of Block.one’s documents and information went much further.”
Wallet Withdrawals
Registered in the Cayman Islands, with offices in Hong Kong and the Washington, D.C., area, Block.one was established in 2016 by Dan Larimer, a Virginia Tech-trained software engineer and entrepreneur, and Brendan Blumer, an entrepreneur whose previous ventures include selling in-game items and creating software for realtors in India. Brock Pierce, the former child actor who co-founded a coin that became Tether, was an early adviser.
Block.one’s early investors included Bitmain Technologies, the Bitcoin mining giant co-founded by Chinese billionaire Jihan Wu, and billionaire Mike Novogratz’s Galaxy Digital, a cryptocurrency-focused financial services provider that plans to go public on a U.S. exchange later this year.
Block.one was birthed in the ICO heyday — when one obscure company after another unveiled plans to raise funds by issuing new virtual tokens, typically accompanied by a white paper outlining business plans. Few had any actual products, and many discussed plans in the vaguest terms.
In its white paper, Block.one said it would treat the ICO proceeds as revenue and use it for a “consulting business focusing on helping businesses reimagine or build their businesses on the blockchain,” according to the SEC, citing a website touting the coin.
One of Griffin’s findings dovetails with an allegation outlined in the 2020 token holder lawsuit. This concerns multiple withdrawals from what’s known as a crowdsale wallet, where coin investors deposit their payments to Block.one.
Typically, these funds would remain in the wallet until completion of the ICO. But in the EOS sale, 2.895 million Ether ($1.72 billion) were withdrawn during the sale and sent to one exchange in particular, Bitfinex, Griffin found.
That accounted for 39% of all Ether raised and made Bitfinex the biggest destination of funds, he said. Griffin also raised flags over how the funds made their way to Bitfinex, saying they were done in a way that made them hard to track.
“These transactions took place over a series of four hops to overlapping Bitfinex deposit addresses, the design of which is consistent with obfuscating deposits to common accounts at Bitfinex,” he wrote.
The token holder lawsuit explored other ways these withdrawals might be problematic. Block.one executives “permitted the funds to be withdrawn nearly a hundred times, accounting for close to 90% of the total funds raised throughout the ICO period and averaging one withdrawal every three to four days,” the lawsuit alleged.
“While withdrawal of funds during an ICO is not expressly prohibited, there are significant concerns about how the withdrawn funds might be used, e.g., to buy tokens on cryptocurrency exchanges, resulting in artificially inflated demand for EOS, increasing market price, and fueling speculation and interest in the sale,” the lawsuit said.
Block.one disclosed in June that it paid $27.5 million to settle the lawsuit, saying that it was “without merit and filled with numerous inaccuracies.” The company didn’t specify what it believes those inaccuracies were.
Clifford Chance’s report addressed withdrawals, saying that Block.one withdrew funds, in the form of Ether, from wallets related to the coin sale, including the funding wallet. Block.one said it made the withdrawals to prevent theft and to hedge against fluctuations in the value of Ether, according to Clifford Chance. Another reason was to avoid selling a large Ether holding in one fell swoop, the report said.
If that had happened, it “would have been far more likely to negatively impact Ether prices than sales in smaller tranches over a long period of time,” Clifford Chance wrote.
Griffin has unearthed irregularities in cryptocurrency trading before. He alleged that Bitcoin’s surge in 2017 was triggered by manipulation and that a single participant, or whale, was likely behind the misconduct. He contended that a single entity on Bitfinex, using Tether, was seemingly capable of supporting the price of Bitcoin when it fell below a certain threshold.
A lawyer representing Tether disputed Griffin’s research at the time, saying it was based on an insufficient data set. The findings nevertheless roiled digital asset markets and contributed to investor skepticism.
Block.one said in May it would bankroll Bullish with $10 billion, funding that includes 20 million EOS coins and 164,000 Bitcoin. Investors, including Thiel’s Founders Fund, Thiel Capital, Howard, Bacon, Angermayer, Li, investment bank Nomura and Galaxy Digital, put in an additional $300 million in Bullish.
Thiel, Howard, Li and Angermayer will also serve as board advisers. The exchange’s directors are Blumer as well as Kokuei Yuan and Andrew Bliss, all of them Block.one executives.
Li and Nomura didn’t respond to requests for comment. Galaxy declined to comment.
Block.one has faced concerns over the effectiveness of the technology it helped create and the vitality of its related developer network. Many software developers have abandoned the EOS effort. Electric Capital, which analyzes the crypto developer community, found that the number of monthly active EOS developers fell to about 70 in July from 130 at the beginning of 2020.
“I think its technology is now outmoded,” said Aaron Brown, a crypto investor who writes for Bloomberg Opinion. “It’s not surprising to find it revitalizing when crypto came back, and also taking advantage of the boom in SPACs. But it has yet to demonstrate any technical successes.”
To be sure, Block.one’s technology has gained some traction. Accounting firm Grant Thornton said last year it would let clients handle intercompany transactions using what it later confirmed was blockchain technology based on EOS. Grant Thornton declined to comment on the progress of the initiative.
While it prepares for the Bullish market debut, Block.one may have trouble luring crypto investors who believe they got burned in the ICO, said Katie Talati of Arca, a digital-asset manager. In a March 19, 2019, email to shareholders, Block.one said its assets, including cash and investments, totaled $3 billion at the end of the preceding February. About $2.2 billion of those holdings were in liquid fiat assets, such as U.S. government bonds.
“They are going to have bad PR associated with the project that’s going to follow them,” she added. “Crypto is very community driven — if you are going to burn your community, it’s hard to rebuild that.”
New Research Claims 21 Accounts Pumped The $4.4B EOS ICO With Wash Trades
New research asserts that EOS and ETH were wash-traded on exchanges to manipulate prices during EOS’ multi-billion-dollar ICO.
New research has shed more light on the crypto industry’s largest-ever token sale, alleging that foul play may have been afoot during EOS’ initial coin offering (ICO) four years ago.
Researchers from the University of Texas have raised fresh concerns regarding Block.one’s record $4.362-billion ICO for the EOS blockchain in 2017 and 2018. The highly-anticipated project was backed by industry heavyweights, including PayPal co-founder Peter Thiel, alongside billionaire hedge fund managers Alan Howard and Louis Bacon. The research does not accuse Block.one itself of any wrongdoing, and the company has cited a report stating there was no evidence it was involved.
On Tuesday, professor John Griffin of the Austin McCombs School of Business and financial analysis firm Integra FEC published their findings in a paper titled “Were ETH and EOS Repeatedly Recycled during the EOS Initial Coin Offering?” — alleging that wash-trading played a key role in EOS’ price discovery.
According to the paper and outlined in an investigation by Bloomberg, EOS was allegedly wash-traded on the Binance and Bitfinex cryptocurrency exchanges in an effort to artificially inflate the prices. Wash-trading describes the process where an entity simultaneously acts as the buyer and seller for the same asset to artificially bolster volume or manipulate prices.
Griffin wrote that artificial demand from suspect accounts created the illusion of demand for the token and pushed prices up:
“First, it directly manipulated EOS’s offering price upward through the extra buying and inflated the market value of the token. Second, it created the false impression of value of the token which enticed others to want to purchase the ICO token.”
The research allegedly identified 21 accounts that recycled EOS tokens during the ICO. Funds identified as suspect amounted to 1.2 million Ether (ETH) worth around $815 million at the time. Ether was the sole cryptocurrency used to buy EOS during the year-long ICO.
The analysis claims that Ethereum accounts were created in order to repeatedly purchase EOS over time. It claims that a “significant portion” of the Ether raised during the token sale appears to have been “recycled by transferring the ICO contributions through a series of obfuscating intermediary accounts and finally arriving at Bitfinex.”
“2.895 million Ether ($1.721 billion USD), or 39% of the Ether raised in the crowdsale, are also traced from the ICO crowdsale wallet back to Bitfinex.”
Griffin did not identify the owners of the accounts or point the finger at Block.one regarding the alleged wash-trading but noted, “These suspicious accounts accounted for almost a quarter of EOS purchases by the end of the crowdsale.”
Robert C. Hockett, professor of law at Cornell Law School, said that he worked for more than one month on the story alongside media outlet Bloomberg, which published its findings on Thursday.
According to Bloomberg, Block.one responded to the paper by referencing a July document authored by law firm Clifford Chance LLP that asserted there was “no evidence that Block.one purchased tokens on the primary market.”
The same John Griffin published a paper in October 2019 titled “Is Bitcoin Really Un-Tethered?” that claimed the leading stablecoin Tether (USDT) was wash-traded to influence Bitcoin (BTC) prices during the 2017 bull market. Speaking to Cointelegraph in February 2020, the firm behind Tether, iFinex, labeled the claims “reckless and false.”
Manipulation or otherwise, EOS has largely fallen out of favor with crypto traders and investors. Since ranking among the top five crypto assets by market capitalization in mid-2018, EOS has since tumbled to rank 35th.
The token is currently trading for $5, down 77% from its April 2018 all-time high of $22.70.
Updated: 9-3-2021
Kaspersky Ranks Cryptojackers Among Top Malware Threats In Africa
Some of the most common methods of duping crypto investors include false advertisements claiming to sell mining equipment and fake websites posing as crypto exchanges.
Russian cybersecurity firm Kaspersky has detected more than 1,500 fraudulent entities targeting potential crypto investors and miners just in the first half of 2021.
Kaspersky’s research shows that 0.60% of users from South African countries have already been targeted by malicious crypto miners. The report also suggests that the most common methods of duping unwary users involved false advertisements claiming to sell mining equipment and fake websites posing as crypto exchanges.
Kaspersky’s data based on anonymized statistics revealed that 0.85% of crypto investors from Kenya and 0.71% Nigerians were targets of crypto-miner malware, while investors from Ethiopia (3.68%) and Rwanda (3.22%) faced the most number of threats in this regard. Bethwel Opil, Africa’s enterprise sales manager at Kaspersky, warned that the low percentages do not mean that the threat is insignificant:
“Crypto-miner malware has been identified as one of the top 3 malware families rife in South Africa, Kenya and Nigeria at present, which we believe emphasises that as cryptocurrency continues to gain momentum, more users will likely be targeted.”
The report also suggests that the most common methods of duping unwary crypto investors involve false advertisements claiming to sell mining equipment and fake websites posing as crypto exchanges.
These fraudulent platforms require users to make an upfront payment under the pretext of advanced payment or verification, after which the scammers stop responding. Cybercriminals also make use of phishing platforms to gain access to users’ private keys of their crypto wallets. Alexey Marchenko, head of content filtering methods development at Kaspersky, said:
“Both those who want to invest or mine cryptocurrency and simply the holders of such funds can find themselves on the fraudsters’ radar.”
Back in June 2021, South Africas Intergovernmental Fintech Working Group (IFWG) established a roadmap for defining the continent’s regulatory framework for handling crypto assets.
The IFWG also highlighted the inherent risk and volatility of investing in cryptocurrency and shared 25 regulatory recommendations against Anti-Money Laundering, terror financing and market manipulation.
Updated: 9-15-2021
Crypto Kid Fraudster Gets 7 1/2-Years For Ponzi Scheme
Stefan Qin’s investors thought they’d found a sure thing — a hedge fund that was generating 500% returns by exploiting the price gaps between cryptocurrencies on 40 exchanges throughout the world.
Instead, the 24-year-old self-proclaimed math whiz used their money on a lavish lifestyle, including a $23,000-a-month Manhattan penthouse apartment, and failed investments in initial coin offerings and real estate. Federal prosecutors said Qin defrauded more than 100 people out of about $90 million.
After some of his victims said Qin should spend as long as possible behind bars for securities fraud, U.S. District Judge Valerie Caproni sentenced him Wednesday to seven and a half years and called him “a potentially very dangerous person.”
Qin “deliberately and consciously chose a path” to rip off investors, including fake account statements and lying to clients about how he was using their money, Caproni said. “This kind of white collar crime is just as devastating to victims as other types of crime, and it will be punished severely.”
The judge also said the sentence was intended to discourage others from similar crimes and to protect the public from Qin, who had no trouble lying to his investors.
“Virgil had a stated market strategy of ‘market neutral,’ safe investments,” Manhattan U.S. Attorney Audrey Strauss said in a statement. “Qin’s investors soon discovered that his strategies weren’t much more than a disguised means for him to embezzle and make unauthorized investments with client funds.”
More than a dozen investors had written letters to the judge, including several who said they had lost their life savings to Qin, an Australian national who dropped out of college to found Virgil Sigma Fund LP in 2017. One woman said she was left “homeless and destitute.”
Qin told the judge he “felt absolutely heartbroken” to read the letters, many of whom were family, friends or business associates.
‘I Feel Ashamed’
“I feel ashamed to look them in the eye and tell them I’m sorry, but I must,” he said.
Qin had claimed he developed a special trading algorithm called Tenjin that could earn profits by buying a cryptocurrency on one exchange and selling it at a higher price on another. Shortly after starting Virgil, he bragged the fund produced an annual return of 500% in 2017. The Wall Street Journal wrote a profile of him in 2018, when he managed $23.5 million. By 2020, he’d raised more than $90 million.
He said he started the hedge fund in his first year of college using an algorithm he thought was an “amazing money making machine.” But “things started to go south, people started to become suspicious of my promises,” Qin told the judge.
“Instead of coming clean I did the worst thing and doubled down on my lies,” Qin said. “I thought I was the main protagonist and life was a video game and I had just found the cheat code to beat it. As we know life is not a video game.”
Near the end of last year, as losses mounted, investors started to demand their money back. To make those payments, Qin tried to raid another fund he had started, the VQR Multistrategy Fund LP, according to prosecutors. But the U.S. Securities and Exchange Commission in December got cryptocurrency exchanges to put a freeze on VQR’s assets.
After that, Qin flew back to the U.S. from South Korea, surrendered to authorities in February and pleaded guilty the same day.
While Qin faced as much as 20 years in prison, federal sentencing guidelines call for 151 to 188 months. Probation officials recommended 96 months, based on his lack of a criminal record and his voluntary return from overseas to face charges.
‘Brazen’ Fraud
Prosecutors had urged “substantial” prison time given the “brazen nature” of Qin’s crime and the need to stop discourage others from doing the same thing.
“Qin used that hedge fund as his own piggy bank, stealing investor money to live a lavish lifestyle and repeatedly lying to investors about what he was doing with their money,” Assistant U.S. Attorney Daniel Tracer said in a sentencing memo.
Defense lawyers asked for a sentence of 24 months, noting Qin took responsibility for his actions and helped authorities to recover some of the lost money.
One investor told the judge in a letter not to be swayed by Qin’s personal charm, a characteristic that helped him defraud so many.
“Mr. Qin did not steal food from a grocery to feed his family,” said the investor, Steve Reich. “He stole over $90 million from ordinary people and has shown no genuine remorse.”
The case is U.S. v. Qin, 21-cr-00075, U.S. District Court, Southern District of New York (Manhattan)
Updated: 9-16-2021
Bitcoin Ledger As A Secret Weapon In War Against Ransomware
“While it may at first seem like cryptocurrency enables ransomware, cryptocurrency is actually instrumental in fighting it.”
Ransomware, malicious software that encrypts computers and keeps them “locked” until a ransom is paid, is the world’s fastest-growing cyber threat, according to Coinfirm.
Recent attacks on critical national infrastructure, like the Colonial Pipeline incursion that crippled oil and gas deliveries for a week along the U.S. East Coast, have set off alarms. Ransom payments are almost always made in Bitcoin or other cryptocurrencies.
But while many were shaken by May’s Colonial Pipeline attack — the Biden administration issued new pipeline regulations in its aftermath — relatively few are aware of that drama’s final act: Using blockchain analysis, the FBI was was able to follow the ransom payments fund flow and recover about 85% of the Bitcoin paid to ransomware group DarkSide.
In fact, blockchain analysis, which can be further enhanced with machine learning algorithms, is a promising new technique in the battle against ransomware. It takes some of crypto’s core attributes — e.g., decentralization and transparency — and uses those properties against malware miscreants.
While crypto’s detractors tend to emphasize its pseudonymity — and attractiveness to criminal elements for that reason — they tend to overlook the relative visibility of BTC transactions.
The Bitcoin ledger is updated and distributed to tens of thousands of computers globally in real time each day, and its transactions are there for all to see. By analyzing flows, forensic specialists can often identify suspicious activity. This could prove to be the Achilles’ heel of the ransomware racket.
An Underused Means
“The blockchain ledger on which Bitcoin transactions are recorded is an underutilized forensic tool that can be used by law enforcement agencies and others to identify and disrupt illicit activities,” Michael Morrell, former acting director of the U.S. Central Intelligence Agency, declared in a recent blog, adding:
“Put simply, blockchain analysis is a highly effective crime fighting and intelligence gathering tool.[…] One expert on the cryptocurrency ecosystem called blockchain technology a ‘boon for surveillance.’”
Along these lines, three Columbia University researchers recently published a paper, “Identifying Ransomware Actors in the Bitcoin Network,” describing how they were able to use graph machine learning algorithms and blockchain analysis to identify ransomware attackers with “85% prediction accuracy on the test data set.”
Those on the frontlines of the ransomware struggle see promise in blockchain analysis. “While it may at first seem like cryptocurrency enables ransomware, cryptocurrency is actually instrumental in fighting it,” Gurvais Grigg, global public sector chief technology officer at Chainalysis, tells Magazine, adding:
“With the right tools, law enforcement can follow the money on the blockchain to better understand and disrupt the organization’s operations and supply chain. This is a proven successful approach as we saw in January’s ‘takedown’ of the NetWalker ransomware strain.”
Whether blockchain analysis alone is enough to thwart ransomware incursions or whether it needs to be joined with other tactics, like bringing political/economic pressure to bear on foreign countries that tolerate ransomware groups, is another question.
Unmasking Criminals?
Clifford Neuman, associate professor of computer science practice at the University of Southern California, believes that blockchain analysis is an underutilized forensic tool. “Many people, including criminals, assume Bitcoin is anonymous.
In fact, it is far from being so in that the flow of funds is more visible on the ‘public’ blockchain than it is in almost any other kinds of transactions.” He adds: “The trick is to tie the endpoints to individuals, and blockchain analysis tools can sometimes be used to do this linking.”
A valid means for unmasking ransomware attackers? “Yes, absolutely,” Dave Jevans, CEO of crypto intelligence firm CipherTrace, tells Magazine.
“Using effective blockchain analytics, cryptocurrency intelligence software” — the sort his firm produces — “to track where ransomware actors are moving their funds can lead investigators to their true identities as they attempt to off-ramp their crypto to fiat.”
Updated: 10-13-2021
New Australian Ransomware Plan Allows For Seizure Of Crypto
Australian authorities will be able to seize or freeze cryptocurrencies linked to cybercrime under new legislation.
Australian lawmakers are taking a tougher stance against ransomware with a new plan that increases penalties for offenders.
The new measures and proposed Surveillance Legislation Amendment announced by the federal government on Wednesday come after a 60% surge in cyberattacks on Australian businesses and state agencies last year. According to reports, these incursions cost the economy AU$1.4 billion (around $1 billion dollars).
The Ransomware Action Plan would give authorities the power to seize or freeze financial transactions in cryptocurrencies that are associated with cybercrime regardless of the country of origin.
The government aims to modernize current legislation to make it easier for authorities to try and recover crypto funds stolen by cybercriminals.
Home Affairs Minister Karen Andrews said that the new measures were designed to deter the targeting of Australian businesses by international hackers. “Our tough new laws will target this online criminality, and hit cybercrooks where it hurts most — their bank balances,” she added.
Dealing with stolen data and buying and selling malware used in ransomware attacks will also be criminalized.
A multi-agency task force called Operation Orcus was set up in July to tackle ransomware attacks. Most of the attacks originated in Russia with the deployment of malware such as REvil or DarkSide, which encrypts or steals data before demanding a ransom in cryptocurrency.
There have been several recent ransomware attacks on Australian targets including Uniting Care Queensland, brewing company Lion, Nine Entertainment, the NSW Labor Party, Toll Holdings and BlueScope Steel. The attack on the JBS meat processing company in May forced it to shut down its 47 sites in Australia.
Lawmakers in the United States are also ramping up efforts to tackle ransomware. Earlier this month, anti-crypto Senator Elizabeth Warren introduced the Ransom Disclosure Act, which aimed to gather data on the role of cryptocurrency in ransomware attacks.
Last Wednesday, blockchain analytics firm Chainalysis purchased cybercrime investigative firm Excygent to bolster its arsenal in the ongoing war against ransomware.
Updated: 10-14-2021
Crypto Adoption In Sights: Regulators And Industry Join To Fight Ransomware
As the crypto industry continues to develop at a rapid pace, so do the ransomware attacks, but regulators now seem ready to step in.
With an increasing number of people forced to work from their homes, data suggests that ransomware attacks are at their all-time highest with the frequency of these incidents increasing by 45% over the course of April 2021 alone.
Not only that, some are adamant that the rise in ransomware attacks is closely connected to the meteoric growth of the crypto sector.
Also, in the midst of the recent positive crypto market activity, news of the United States regulators aggressively studying the link between crypto and ransomware seems to be dampening the mood somewhat, especially since various government agencies are seemingly seeing crypto ransomware as a big issue requiring stringent action.
As digital asset adoption continues to spread across the U.S., it appears as though lawmakers are looking to better understand how these offerings can be used for a slew of legal as well as illegal purposes.
For example, the Ransom Disclosure Act, which was introduced by Senator Elizabeth Warren and Representative Deborah Ross on Oct. 5, requires victims of ransomware attacks to disclose information about any ransom payments they may have faced to the Department of Homeland Security (DHS).
The goal here, as per Warren and Ross, is to amass critical data on fiat and cryptocurrency payments, which can eventually be used by relevant regulatory agencies to protect investors from cybercrimes as well as to curb any illicit financial activities taking place in the United States.
Furthermore, the bill also seeks to investigate the direct role of cryptocurrencies in ransomware attacks, an effort that will be helmed by the Department of Homeland Security.
Similarly and just recently, Deputy Attorney General Lisa Monaco revealed that the Justice Department has launched a new initiative dubbed the National Cryptocurrency Enforcement Team that looks to weed out any projects that can allow criminals to launder their crypto proceeds.
“We want to strengthen our capacity to dismantle the financial ecosystem that enables these criminal actors to flourish and to profit from what they’re doing,” Monaco was quoted as saying.
What’s Driving This Wave?
To gain a better understanding of why the U.S. regulators are making such a concerted effort to crack down upon any crypto-related ransomware, Cointelegraph reached out to Kadan Stadelmann, chief technological officer for open-source blockchain solutions provider Komodo.
In his view, one quick look at data available online shows that all kinds — not just crypto — of ransomware attacks are becoming more frequent, adding: “Just look at the statistics.
Palo Alto Networks reported last month that the average ransom payment for 2021 is currently around $570,000 — 82% higher than the 2020 average of $312,000. 2020 was also much worse than 2019.” He added:
“To reverse this trend, a more mature regulatory landscape is necessary for the blockchain industry as well as improved cybersecurity as a whole in the next decade.”
When asked about whether major spending on such research activities is warranted, Stadlemann opined that not only should governments be putting more measures in place but they should also allocate additional funds and resources in regard to the same.
On the subject, he went on to state that governments can begin by adopting policies that ensure companies and anyone running critical infrastructure are better prepared for such events: “Together, having both proactive and reactive plans for cybersecurity would certainly reduce the fallout of ransomware attacks.”
Sharing a relatively similar sentiment, Du Jun, co-founder of cryptocurrency exchange Huobi, told Cointelegraph that it is the responsibility of every government to prevent Anti-Money Laundering (AML) as well as Combating the Financing of Terrorism (CFT) within their borders, adding that it is only natural for the U.S. government to have taken the regulatory actions it has to regulate its crypto market. He added:
“It is difficult to deal with cryptocurrencies as a payment method, given the lack of clarity regarding responsibility for AML/CFT compliance and the lack of a central oversight body. These actions may introduce challenges to crypto businesses but will be good for the ecosystem in the long run, protecting investors from uncertainty and fostering a better business environment.”
Lastly, he opined that in addition to supervision alone, the American government ought to also allocate more resources to encourage the growth of new businesses within this space, making the country more competitive and appealing to crypto enthusiasts.
The Spending Is Justified
Taking a more numbers-oriented approach to the matter, Marie Tatibouet, chief marketing officer for cryptocurrency trading platform Gate.io, told Cointelegraph that in 2020, the total ransom paid by cyberattack victims reached nearly $350 million worth of crypto. With that figure in mind, she added:
“This number is inevitably going to keep increasing year on year. So Warren’s ‘Ransom Disclosure Act’ on paper makes sense. If you are a victim, you must disclose information about ransom payments no later than 48 hours after the payment date.”
That said, she did acknowledge that the primary issue that most people have with the U.S. government is that, of late, Biden and company have been cracking down very hard on the crypto industry via the introduction of the recent infrastructure bill, as well as other sanctions.
“So, it is understandable why people have been a little cautious about anything that the government does,” Tatibouet added.
Sergey Zhdanov, chief operating officer for digital currency trading platform EXMO, told Cointelegraph that the measures taken by the U.S. confirm the fact that regulatory authorities are not looking to ban cryptocurrencies (the way China did) but rather want to carve out a way through which digital assets can be incorporated into the traditional financial system. He then went on to state:
“Coming up with new effective methods to stop the illegal use of cryptocurrencies and money laundering is a crucial step that will take the crypto industry to its next level of development.”
Increased Regulations A Win-Win For Everyone?
Hunain Naseer, senior editor for OKEx Insights, told Cointelegraph that the regulatory efforts being initiated globally seek to usher in a level of clarity to this space that can help make it easier for investors to enter this fast-growing space with complete peace of mind. He further expounded on the subject by saying:
“It makes sense to focus on such initiatives that make online interactions and commerce, including cryptocurrency transactions, safer for all. These steps will also contribute toward regulators allowing a wider variety of crypto-based financial products for retail.”
Nischal Shetty, founder of cryptocurrency exchange WazirX, told Cointelegraph that any regulatory steps that seek to track and eliminate criminal activities should always be welcome, especially in an industry as fast-growing as this.
In his view, the rationale behind such movements seems to quite clearly be rooted in governments ultimately wishing to protect consumers without stifling innovation, adding:
“For crypto, it’s an even more of a positive sign as this proves that digital asset innovation can thrive while ensuring criminal activities are identified and eliminated.”
Furthermore, On Oct 5. blockchain analytics firm Chainalysis announced that it had facilitated the purchase of cybercrime investigative company Excygent for an undisclosed amount, hinting that the buyout will enable the two firms to work together and “dismantle ransomware operations” that may be active globally.
In the past, Chainalysis has collaborated with Excygent on the seizure of cryptocurrency connected to the now-defunct darknet market Silk Road, as well as in the shutting down of various terrorism and child abuse portals operating online.
In general, crypto native blockchain analytics firms have grown to accrue support not only from the U.S. government but also a number of significant private players, with CipherTrace being bought out by a mainstream entity — in this case like MasterCard — earlier this year.
What Is The Future Of Ransomware Crime?
As the crypto landscape continues to evolve and grow, Chainalysis CEO Michael Gronager believes that tracing the flow of ransomware payments on the blockchain will be instrumental for law enforcement agencies to deter, analyze and dismantle any ransomware operations in existence today, as he told Cointelegraph:
“As paradoxical as it seems, it can actually be beneficial to investigators when bad actors choose to use cryptocurrency when committing crimes.”
In this regard, it is pertinent to mention that hackers have become wise to the fact that, contrary to what people keep reiterating like crypto is totally anonymous, it is in fact actually extremely easy to trace individual transactions back to their owners, since all records and transitions are maintained on a blockchain.
Additionally, amid the slew of recent big hack stories such as the ones related to Poly Network and SushiSwap, the interesting thing is that the incidents did not result in the platform or its users losing any money, as companies and regulators stepped in to secure the movement of funds through the blockchains.
And while that may be bad for the notion of decentralization, the fact of the matter remains that the funds are safe.
Gronager further alluded to cases such as NetWalker, a ransomware operator who allegedly targeted hospitals during the pandemic and collected more than $25 million from ransom payments in 2020, as well as Suex OTC, a firm that allegedly allowed hackers to access crypto sent as payment for ransomware attacks, as prime examples of why increased defense against ransomware is needed in this day and age.
Thus, the fact that regulatory agencies are making decisive steps to focus on crypto ransomware-related initiatives, is not unilaterally welcomed by everyone in the crypto industry.
While some believe more can be done to make the digital asset ecosystem safer for newer entrants through the use of regulation, others say that the role of ransomware in crypto is overblown and that tight regulation will stifle freedoms and worsen the image of the industry.
However, most agree that ransomware has no place in the industry and that regulation, if done right, will go a long way toward securing the industry and ensuring long-term prosperity and adoption.
Updated: 10-15-2021
Ransomware Payments In 2021 Already Dwarf Last Year’s Total, FinCEN Reports
FinCEN identified over $5 billion in transactions tied to ransomware payments based on $590 million detailed in Suspicious Activity Reports.
Payments tied to ransomware attacks in 2021 are already exceeding 2020′s total, the U.S. government’s financial crimes watchdog said Friday.
Exchanges and other financial institutions reported more than $590 million in payments tied to ransomware attacks, including cryptocurrency payments, to the Financial Crimes Enforcement Network (FinCEN) in the first half of 2021, outstripping a 2020 total of just $416 million.
It was not immediately clear what amount of this total was comprised specifically of cryptocurrency transactions, versus more traditional payment methods.
A Treasury Department press release said attackers are “increasingly requesting payments in Anonymity-Enhanced Cryptocurrencies” such as monero.
Crypto SARs
FinCEN tied the reported amounts, which came through Suspicious Activity Reports (SARs), to a total of $5.2 billion in transactions that may be “potentially tied” to ransomware payments, according to Treasury Department official Todd Conklin.
Last year, former FinCEN Director Kenneth Blanco told CoinDesk that less than 1% of SARs filed to the agency mentioned crypto, though he did not share any monetary figures tied to these reports.
Conklin, counselor to Deputy Treasury Secretary Adewale Adeyemo, told TRM Labs’ Ari Redbord that the announcement is part of the Treasury Department’s broader push against ransomware.
Ransomware, where an attacker encrypts a victim’s computer or network until the victim pays a ransom for a decryption key, has been employed in several high-profile attacks in 2021, disrupting critical supply-chain vendors like a gas transport firm and a meat processing plant.
Last month, the Treasury Department added an over-the-counter crypto trading platform to a global blacklist for the first time in its ongoing fight to tamp down on ransomware attacks and payments.
“We have seen an aggressive sustained effort on ransomware the last few weeks from the administration that started even before the Suex designation,” Redbord, a former Treasury official, told CoinDesk in a statement. “We are rightfully seeing the most focus on hardening cyber defenses, and when it comes to crypto, we are seeing Treasury, DOJ and others target the illicit parts of the crypto ecosystem rather than the overwhelmingly compliant industry itself.”
Remaining Compliant
In addition to the FinCEN findings, the Treasury Department’s Office of Foreign Asset Control (OFAC) published a “sanctions compliance guidance” brochure for crypto businesses, detailing the requirements for U.S. persons and entities that come into contact with “blocked” cryptocurrencies.
“Once a U.S. person determines that they hold virtual currency that is required to be blocked pursuant to OFAC’s regulations, the U.S. person must deny all parties access to that virtual currency, ensure that they comply with OFAC regulations related to the holding and reporting of blocked assets, and implement controls that align with a risk-based approach,” the brochure said.
The document includes recommended best practices and controls that crypto industry businesses can implement to remain in compliance with federal law.
“We are going to continue to target the illicit parts of the crypto ecosystem while also ensuring we are helping to bolster compliance regimes across the entire ecosystem,” Conklin said. “Fundamentally, though, we see ransomware as a cybersecurity issue. It gets framed in many areas as a crypto currency issue, but just attacking the crypto ecosystem is not going to fix the core problem, which is cyber vulnerabilities across multiple sectors.”
Heightened Focus
OFAC said in a press release that cryptocurrencies are being increasingly used for ransomware payments, though it also did not specify a breakdown between fiat transactions and cryptocurrency transactions.
The Treasury Department is recommending that “industry participants … consider incorporating the elements and controls” detailed in the brochure.
“Ransomware actors are criminals who are enabled by gaps in compliance regimes across the global virtual currency ecosystem,” Deputy Secretary of the Treasury Wally Adeyemo said in a statement. “Treasury is helping to stop ransomware attacks by making it difficult for criminals to profit from their crimes, but we need partners in the private sector to help prevent this illicit activity.”
U.S. Treasury Offers Crypto Guidance Amid Ransomware Surge
There was $590 million in suspicious activity related to ransomware in the first six months of 2021, exceeding the entire amount in 2020, when $416 million was reported, according to a report released Friday by the U.S. Treasury Department’s Financial Crimes Enforcement Network.
The average amount of reported ransomware transactions per month in 2021 was $102.3 million, according to the report.
If the current trend continues, suspicious activity reports filed in 2021 “are projected to have a higher ransomware-related transaction value than SARs filed in the previous 10 years combined,” according to the report. SARs is shorthand for suspicious activity reports.
U.S. based cybersecurity companies filed most of the SARs related to ransomware while banks and cryptocurrency exchanges filed more than a third of the reports. The reports reflect just how quickly ransomware attacks have grown.
The report offers new insight into the scale of ransomware attacks devastating U.S. businesses and impacting critical infrastructure. A Treasury spokesperson said the SARs don’t represent all ransomware payments.
Reporting ransomware payments to the Treasury via a suspicious activity report is often a requirement of cybersecurity insurance policies, according to a person familiar with the matter.
The Treasury Department also identified 68 ransomware variants, noting that the most commonly reported types were REvil, Conti and DarkSide. Ransomware groups often sell their malware, or variant, to affiliates who then use it to plot attacks, in what is known as ransomware-as-a-service.
REvil, Conti and DarkSide are suspected by cybersecurity firms of being tied to Russia in some way — because they use the Russian language or are suspected of being based there.
The report was filed as the Treasury Department issued guidance to the virtual currency industry to prevent exploitation by entities sanctioned by the U.S. and ransomware groups.
It is part of a broader effort by the Biden administration to attempt to curb ransomware attacks. In ransomware attacks, hackers encrypt a victim’s files and promise to unlock them if they are paid a fee.
Among the more notable attacks were those in May on Colonial Pipeline Co. in May that squeezed fuel supplies on the East Coast and on the meatpacker JBS SA.
The Treasury report stated that ransomware actors are increasingly requesting payment in cryptocurrencies like Monero, which are designed to enhance anonymity.
Updated: 10-22-2021
After ‘Stealing’ $16M, This Teen Hacker Seems Intent On Testing ‘Code Is Law’ In The Courts
Will DeFi’s unofficial ethos hold up in court? A Canadian math prodigy could be betting his future on just that.
Some $16 million in cryptocurrency was pilfered in an exploit of a decentralized finance (DeFi) protocol last week, and the victims believe they know exactly who did it.
Despite threats from the team, however, the alleged attacker – a Canadian teenaged graduate student – is refusing to return the funds, potentially setting the stage for a groundbreaking legal confrontation.
On one side of the conflict is a child math prodigy and an outspoken champion of DeFi’s self-regulating “code is law” ethos. On the other, a pair of DeFi developers and their advisers who felt forced to make an unprecedented series of troubling ethical choices on behalf of a DAO community.
At stake in the fight are a number of thorny issues that have so far been successfully obscured by DeFi’s explosive growth: What is the role of law enforcement in an unregulated $220 billion sector?
When, if at all, should the gendarmes be summoned? And, most importantly, is the notion of “code is law” sufficient to grapple with all of DeFi’s ethical complexities?
First Breach
On Oct. 14, the official Twitter account for Indexed, a DAO-governed DeFi protocol, reported an error with two of its index fund-style automatically rebalancing liquidity pools, one that had drained nearly half of Indexed’s $34 million in total value locked.
We’re aware of an incident that has just taken place within the DEFI5 and CC10 pools.
Looking into it.
— Indexed Finance (@ndxfi) October 14, 2021
An analysis from exploit-focused publication Rekt shows the error was in fact an attack launched from an Ethereum address funded by privacy mixer Tornado Cash.
From that address, an attacker used flash loans to knock the balance of the pools out of kilter and buy out component assets at a heavily discounted rate.
In the days since, the Indexed team and an ad-hoc “war room” of industry experts convened to mitigate the damage and gather information. And in the course of their investigation they believe they have found the attacker’s real-world identity: It’s an 18-year-old mathematics prodigy who goes by “Andy.”
Both the Indexed core team and DeFi community members who claim to have spoken with Andy say that he has refused to return the funds, and that he intends to face any criminal charges resulting from his exploit in court – arguing that he simply executed a fully legal arbitrage trade.
A tweet thread from an account claiming to belong to Andy thanked well-wishers for their comments over the past week and asked for lawyer recommendations on Thursday.
Likewise, in an email exchange with CoinDesk, Andy did not confirm he had conducted the attack, but did say that he was seeking legal counsel. (Andy has since stopped returning CoinDesk’s emails, though other attempts have been made to contact him.)
Speaking seriously now:
I want to thank everyone that has been sending me letters of support. I have one favor to ask for followers and friends. I am looking for the most elite crypto lawyers. I will need an entire team.— ZetaZeroes (@ZetaZeroes) October 21, 2021
If the case does go before a judge, it could be a test of “code is law” – a popular phrase in DeFi circles referring to a common mindset.
In the absence of regulation, the thinking goes, the DeFi ecosystem is purely adversarial and anything permissible by code is also by nature ethically permissable. Where one man might see an exploit, another may just see “crypto trading.”
A number of legal experts who spoke to CoinDesk dismissed this notion, however, and said that while a case might be complex and perhaps novel, a court will not necessarily cede to DeFi’s unofficial ethos.
‘War Room’
Shortly after the attack was discovered, the core Indexed team found a number of clues leading them to believe that they had identified the hacker: a young developer who had been speaking with team member Laurence Day for months.
“It was perfectly affable, friendly, smiles, lots of emojis. A perfectly normal dude,” Day said of Andy in an interview with CoinDesk.
While Day did not write the code for the protocol, he maintains it and, as a result, “understands it pretty deeply.”
“I don’t feel like I got catfished or something because I was discussing information that was publicly available, but this did take me by surprise,” Day added.
Once they had a suspect, the team assembled its online “war room.” Members included Curve contributor Julien Bouteloup, Rotki founder Lefteris Karapetsas and pseudonymous Yearn.Finance core contributor “Banteg,” among others.
In an interview with CoinDesk, Banteg said the decision to join the war room was an easy one.
“I don’t turn these invitations down because I know how it feels when you find yourself in a situation like this, and I believe I can provide meaningful support and the needed outside perspective to help handle it gracefully and avoid stupid mistakes caused by stress no human should endure alone,” Banteg said.
Ethical debate
Once the team had information on the attacker, they decided to issue an ultimatum: Return the funds or be reported to law enforcement authorities.
Update: we have identified the Indexed attacker and found links to exchanges. We are now presenting an ultimatum.https://t.co/6up6ekN26g
— Laurence Ξ. Day (@laurence_e_day) October 16, 2021
In the past, threats of doxxing have proven to be effective. Following a $3 million exploit of a non-fungible token (NFT) drop in September, developers successfully intimidated the attacker into returning the stolen funds after, among other negotiation tactics, ordering miso soup to the attacker’s house.
Actually following through with the threat is perhaps novel, however, and the decision prompted significant internal debate among the team.
According to core Indexed contributor Dillon Kellar, the nature of Indexed’s DAO structure played heavily into the team’s thinking.
“Once he made it clear that he’s not gonna give up, that he doesn’t care we’ve found this damning evidence on him, at that point we had a difficult decision because if we just go to law enforcement, if we keep that information to ourselves, we’re effectively taking ownership of the situation ourselves, and we couldn’t do that,” Kellar said.
Other DAO members may wish to individually or collectively pursue remuneration in civil court, and if core team members withheld Andy’s personal information, it could prevent them from doing so – ultimately prompting a moral argument in favor of doxxing.
“We’re not comfortable with the idea of publicly doxxing, but Indexed is not a legal entity – it’s a DAO. And Dillon and I don’t have the right to solely own this information, or to take ownership of the legal battle. This is a cornered response,” said Day.
Banteg likewise expressed discomfort with the decision, but backed going forward with it.
“It’s unprecedented. Ethics-wise, as you can imagine, all this feels quite uneasy. I believe Indexed gave the hacker more than enough ways out, but he thinks he’s invincible.”
In the end, the war room had a full consensus.
“There’s no one in the room that’s given serious pushback to the route that’s been taken. We know we’ve done everything we can,” said Day. “I don’t care for the edgelords and the frogs. Anyone who has something valuable to say on this is with us.”
Child Prodigy
However, as the team’s deadline passed with no word from Andy, Banteg made a surprise discovery: The attacker isn’t just “immensely talented” – at just 18 years old, he’s a teenage genius.
According to a cached version of his now-defunct personal website, Andy will soon complete his master’s degree in applied mathematics from the University of Waterloo in Ontario (also Ethereum co-founder Vitalik Buterin’s alma mater); he has authored papers on smooth Schubert varieties and Riemann spheres, among other complex subjects; and according to a 2016 article from Canada’s Globe and Mail, he completed high-school math at just 13 years old.
His online presence also indicates a vainglorious streak. On a Wikipedia forum in 2016, Andy referred to himself as an “expert in mathematics and theoretical physics.” He even entered himself in a game show wiki as a “notable mathematician.”
The claim is now a “dark joke” in the Indexed war room, Day said: He’s become exactly that, though not for his scholarship.
“I guess he out-manifested all of us,” Day added.
Paternal Concerns
This discovery presented the war room with yet another ethical conundrum, as many felt that reporting a teenager carried additional weight.
The new information prevented them from “dropping the hammer” immediately, as Kellar put it.
“I taught computer science and I never had someone quite of Andy’s level, but I know the type. When you’re this particular type of person – look, 18 is a man in the eyes of the law, but mentally you’re still a child,” said Day. “I don’t know if that comes off as denigrating to him or whether I’m sounding excessively sympathetic, but I think this is a case of vast, vast skill at the expense of almost everything else.”
Likewise, Jason Gottlieb of U.S. law firm Morrison Cohen framed the situation in paternalistic terms. Gottlieb was retained by Day and Kellar to represent Indexed in reporting the crimes to law enforcement.
“I think the fact that he is only 18 is something that could be some cause for empathy. I have a son who is close to that age, so from a dad’s viewpoint I have some empathy, knowing that teenagers can do stupid things. I know I did stupid things as a teenager,” said Gottlieb.
However, the new information led the team to new leads, including the discovery that Andy had allegedly been frequenting extremist circles online. During the investigation the team found he was part of a data leak from a web service hosting alt-right communities.
There are also a host of other clues suggesting hateful ideologies: the calldata for Andy’s attack included a racial slur; the attacking Ethereum address starts with “BA5Ed1488,” a numerological reference to a neo-Nazi slogan; a bizarre tweet thread from ZetaZero included bracketing certain words in triple brackets, a popular anti-Semitic dog whistle.
Additionally, the ZetaZero account recently retweeted a post referring to Andy as “the Dylan Roof of Balancer pools,” a reference to a white supremacist terrorist who killed nine black churchgoers in 2015.
@ZetaZeroes the Dylan Roof of Balancer Pools
— Well EnDAO’d (@DAOhound_) October 17, 2021
While members of the war room said they could not identify a particular moment where they made the firm decision to release Andy’s information despite his age, the ties to extremism played into their thinking.
“The frustrating thing is, until he had made all these ugly parts of himself known – the white supremacy, the anti-Semitism, the general, unbearable dickish nature of him – if he had returned 90% and kept a bounty, we would have at least asked him to audit code. And had he disclosed this stuff with us, we would have given him $50K to $100K and had him join the team in a heartbeat,” said Day.
Kellar also said that age alone could not distract from the gravity of Andy’s actions.
“For a regular 18-year-old, I would have concerns about releasing his information. And it’s not to say I still don’t, but the fact is he’s a very advanced 18-year-old. He has a master’s degree. He finished high school at 13. And he has taken the action of stealing $16 million. And if he’s going to be adult enough to do those things, he’s adult enough to face the legal consequences,” said Kellar.
Codeslaw
In the eyes of some members of the DeFi community, however, Andy didn’t steal anything at all.
A popular rallying cry for many DeFi die-hards is “code is law,” often derisively referred to as “codeslaw.”
This view, perhaps best elucidated in an essay by pseudonymous e-Girl Capital intern “Odette,” holds that there is no such thing as a “hack” or a “rug pull” in DeFi, and that it’s the responsibility of each actor to thoroughly vet all on-chain actions – if you lose money to a hack or a faulty contract, it’s on you.
Because all information is freely available on-chain and actions on-chain are immutable, DeFi is ultimately then a self-contained and deterministic environment operating outside of normal regulatory and ethical parameters, or so the thinking goes.
what a boomer take 🙁
code is law if the market is unregulated
welcome to crypto
no place for mistakes
you snooze you lose
— AnonDeFiBaron (@AnonDeFiBaron) October 21, 2021
Day worries that a faction of the DeFi community who believes in code is law is now egging Andy on.
“I think he’s listening to a legion of frogs. They’re calling him based, and asking him for money, and hailing him as a hero,” he said.
Admirers flocking to successful hackers isn’t unusual. In the wake of the $613 million Poly Network hack, panhandlers and admirers used messages on the Ethereum network to cheer the culprit on.
Social Consensus
However, in practice, the notion of “code is law” may have already been disproven.
“Frankly, it’s tiring,” Lefteris Karapetsas told CoinDesk. “We had this fight five years ago.”
Back in 2016, Karapetsas was the technical lead for Slock.it, a startup that spearheaded The DAO – a notorious early investment experiment whose failure led to a chain split that led to the creation of Ethereum Classic.
“The ‘code is law’ version of Ethereum was born out of that. It’s called ETC and it still exists. The coleslaw proponents can just go play there,” Karapetsas said.
The current, canonical Ethereum chain is the result of the community reaching social consensus to effectively “undo” The DAO hack rather than let code be fully deterministic – and that’s a good thing, according to Karapetsas.
“No builder in this space in their right mind believes that code is law. It’s just a meme that is perpetuated by anon on-lookers who just like to see chaos unfold,” he said.
cOdE iS laW https://t.co/9WSh3uE2O1 pic.twitter.com/qFjgSVgT7z
— Lefteris Karapetsas | Hiring for @rotkiapp (@LefterisJP) October 17, 2021
He added that if the community were to embrace such principles, the end result would quickly turn dystopian.
“If code was law then this field would just be a playground for hackers who will be continuously trying to steal funds out of protocols. They would be eponymous and idolized. While the users would be blamed for ‘not reading the code well enough.’ Which is essentially what every coleslaw proponent says,” he said.
Legal wrinkles
The question now turns to whether “code is law” will hold up in a court of law.
Gottlieb confirmed to CoinDesk that he has turned over all relevant information to multiple law enforcement agencies, but declined to specify which ones.
While it’s an open question as to if those agencies will have the technical expertise to analyze the case and issue an arrest warrant, Gottlieb suggested they’re further along than some DeFi-natives might think.
“I wouldn’t assume that the authorities are not familiar with these sorts of things,” he said. “I’ve already reached out to contacts that I have in various agencies in law enforcement, and there are folks in law enforcement who deal with cryptocurrency hacks and thefts.”
Gottlieb noted that the individuals he’s spoken to are “very sophisticated” in their understanding of the space and that they are “interested” in the case.
Regardless of whether he’s arrested, Andy may also have grounds to file counter-charges.
Matt Burgoyne, a securities and crypto lawyer at Canadian firm McLeod Law LLP, said that even before the case gets before a judge there could already be complications. Burgoyne told CoinDesk he is not representing Andy.
“Doxxing can be illegal in Canada and the extent of legal consequences depends on the circumstances. Doxxing can give rise to charges of criminal harassment, invasion of privacy and stalking. I don’t believe this will go to court and if it did, I’m sure there would be damages on both sides,” he said.
Erich Dylus, a legal engineer for the oracle network API3, voiced personal discomfort with doxxing and also said it may lead to counter-charges.
“I think public doxxing can be extremely dangerous and often leads to undesirable misplaced vigilantism or trial by public opinion. Not to mention potentially opening avenues of liability for the doxxers,” he said.
In a tweet on Thursday, Kellar said Andy and his family have been receiving threats, and called on the community cease with the abuse and to pursue other “legal remedies.”
If you feel our efforts to address the situation have been inadequate, there are legal remedies you can pursue; threatening him or his family isn’t one of them.
— Dillon Kellar (@d1ll0nk) October 21, 2021
Stealing From The Collection Plate
Once these grievances have been parsed, however, the question then turns to whether a court can grapple with the complexity of weighted automated market makers (AMM), flash loans and so-called “economic exploits.”
Geoff Costeloe, an associate at Canadian firm Lindsey MacCarthy LLP and LexDAO member, said that Indexed’s DAO structure could lead to hiccups.
“I’m going to be following the recovery side of the matter,” he said. “Because Indexed is a decentralized DAO, I am curious to see how they file their claim and how they describe their relation to the protocol and other DAO members. Will they say it is a partnership or a corporation? Or will they say they are individuals?”
Gottlieb, the Indexed lawyer, brushed these concerns aside. He compared the exploit to a church congregation which had raised funds for some cause: if stolen, it’s no less of a crime just because it would be difficult to track precisely who owned what at a specific time.
Pure Delusion
Of the half-dozen lawyers CoinDesk spoke to, all agreed that while the potential case may seem as if it will set a number of precedents at first blush, the reality is that a court will likely evaluate the exploit in simple terms.
Crypto attorney Stephen Palley warned that if the case does make it to court, it could be a moment that definitively ends DeFi’s fanciful notions of self-regulation.
“It’s the height of stupidity to say ‘code is law’ in this situation. It’s a magical incantation that means nothing,” the Anderson Kill lawyer told CoinDesk.
“There’s nothing terribly new here,” he added. “Old wine, new bottles; self-serving human greed. Is robbing a bank an ‘economic exploit?’ Saying that is frigging stupid. There’s nothing about this, if handled properly, that is groundbreaking precedent.”
If a door to a bank is open and you go in and the vault is open and you take the money and leave it’s a really great idea to defend yourself when the police arriving by saying “lissen ossifers, door is law!”
They will let you go then.
Guaranteed.
— Palley (@stephendpalley) October 20, 2021
Multiple lawyers and Indexed core team members pointed in particular towards signs of Andy’s intent that might erode his defense.
“This wasn’t some case where there was a contract that just had a simple mistake, what some people are calling an economic exploit,” said Kellar, the Indexed core team member. “He didn’t pull a lever that spit out too many coins, it was a sophisticated attack that exploited a very specific vulnerability that nobody found for a year.””
A sequence of actions leading into the attack will undermine any attempt by Andy to frame the exploit as a “happy accident,” Kellar added.
“If a [bank] teller or system makes an error and someone gets unjustly enriched, that certainly doesn’t impose criminal sanctions on the individual who received a boon,” said Costeloe, the MacCarthy LLP lawyer. “They may have been unjustly enriched but they were also innocently enriched, with no intention on their part. The situation with Indexed is a bit different than that because the hacker wrote code and attacked the protocol in a way that shows clear intent to enrich him or herself.”
In the end, multiple lawyers dismissed the “code is law” argument, referring to it as “delusion” and holding it as “delusional.”
Grim Determination
On Thursday morning, Andy’s alleged ZetaZero Twitter account posted a short thread in which he framed the forthcoming legal battle as a “duel.”
Speaking seriously now:
I want to thank everyone that has been sending me letters of support. I have one favor to ask for followers and friends. I am looking for the most elite crypto lawyers. I will need an entire team.— ZetaZeroes (@ZetaZeroes) October 21, 2021
Despite the seeming inertia tilting towards a legal confrontation, both Gottlieb and Palley noted that if Andy were to return the funds there’s a chance the incident might not have to be litigated.
Palley said that returning the funds “doesn’t undo the crime,” but it could lead a prosecutor to decline to pursue charges.
The core Indexed team, however, has reached a point of “grim determination,” according to Day.
“I’ve had the time to process all of this now, and there’s going to me a maelstrom that kicks up on Twitter, but on the balance of things I know this was the right thing to do. Dillon [Kellar] and I will be pariahs in parts of the space now, but it was the right thing to do,” he said of doxxing Andy.
Kellar made it clear that they’re also viewing court as an increasingly likely outcome.
“Some people have said he might move to Venezuela or some place without extradition – I don’t think that will happen. It really seems like he wants this to be a precedent-building case, so if he doesn’t returns the funds I expect this to go to court,” said Kellar.
“He’s trying to stamp his name in history, and he’s going to get it, but ruinously so,” said Day. “It’s a little bit heartbreaking. A colossal waste of talent, time and money. And for what? I just want to say to him, ‘God damn it, Andy, why have you made us do this?’”
Almost $7M In Bitcoin Held By Colonial Pipeline Attacker Is On The Move
Elliptic has linked the activity to ransomware group REvil, with which DarkSide has close ties, being hacked and forced offline by a U.S. government-led operation.
Bitcoin now worth nearly $7 million held by the DarkSide ransomware group involved in the Colonial Pipeline attack in May is on the move, according to blockchain analytics firm Elliptic.
* Following the attack, which threatened the petroleum supplies of five eastern states in the U.S., DarkSide’s share of the amount paid in ransom remained dormant until Oct. 21, Elliptic said Friday in a blog.
* The developer of “ransomware as a service,” DarkSide, maintained a wallet to hold its share of the funds, which included 11.3 BTC. That was identified by Elliptic using its intelligence collection and analysis of blockchain transactions.
* DarkSide subsequently said the wallet had been claimed by an unknown third party, sending 107.8 BTC ($6.8 million) to a new address.
* These bitcoin have now been sent through a series of new wallets over a period of several hours, with small amounts being ejected at each step – a common money laundering technique to make funds harder to track.
* Elliptic has linked this activity to ransomware group REvil, with which DarkSide has close ties, being hacked and forced offline by a U.S. government-led operation.
Updated: 10-23-2021
CoinMarketCap Hack Reportedly Leaks 3.1 Million User Email Addresses
3.1 million email addresses linked to CoinMarketCap accounts were reportedly being traded on hacking forums, according to Have I Been Pwned.
CoinMarketCap, a price-tracking website for cryptocurrencies, has reportedly fallen victim to a hack that leaked 3.1 million (3,117,548) user email addresses.
The information came into light after the hacked email addresses were found to be traded and sold online on various hacking forums, and revealed by Have I Been Pwned, a website dedicated to tracking hacks and compromised online accounts.
CoinMarketCap, a subsidiary of cryptocurrency exchange Binance, confirmed that the list of leaked user accounts matched its user base:
“CoinMarketCap has become aware that batches of data have shown up online purporting to be a list of user accounts. While the data lists we have seen are only email addresses, we have found a correlation with our subscriber base.”
While confirming the correlation of the 3.1 million (3,117,548) user email addresses with its user base on Oct. 12, the company has assured that the hackers did not gain access to any of the account passwords.
“We have not found any evidence of a data leak from our own servers — we are actively investigating this issue and will update our subscribers as soon as we have any new information,” a CoinMarketCap spokesperson said.
Despite the confirmation, CoinMarketCap has yet to identify the exact cause of the hack. Responding to Cointelegraph’s request for comment, CoinMarketCap said:
“As no passwords are included in the data we have seen, we believe that it is most likely sourced from another platform where users may have reused passwords across multiple sites.”
A recent hack on the Coinbase crypto exchange resulted in the compromise of 6,000 user accounts.
The attack was a result of exploiting the exchange’s multifactor authentication (MFA) system, which suggests that the hackers had access to users’ email addresses.
According to Coinbase, the attackers identified a vulnerability in the account recovery process:
“In this incident, for customers who use SMS texts for two-factor authentication, the third party took advantage of a flaw in Coinbase’s SMS Account Recovery process in order to receive an SMS two-factor authentication token and gain access to your account.”
While the value of stolen assets has yet to be revealed by Coinbase, the incident was complemented by thousands of formal complaints from account holders against the company.
Updated: 10-24-2021
YouTube Channels Hacked And Rebranded For Livestreaming Crypto Scams
Google’s Threat Analysis Group (TAG) attributes the attacks to a group of hackers recruited in a Russian-speaking forum that sells the hacked YouTube channels to the highest bidder.
A new report shared by Google’s Threat Analysis Group (TAG) highlights an ongoing phishing campaign against YouTube creators, typically resulting in the compromise and sale of channels to broadcast cryptocurrency scams.
TAG attributed the attacks to a group of hackers recruited in a Russian-speaking forum that hacks the creator’s channel by offering fake collaboration opportunities. Once hijacked, the YouTube channels are either sold to the highest bidder or used to broadcast cryptocurrency scams:
“A large number of hijacked channels were rebranded for cryptocurrency scam live-streaming. On account-trading markets, hijacked channels ranged from $3 USD to $4,000 USD depending on the number of subscribers.”
The YouTube accounts are reportedly being hacked using cookie theft malware, a fake software configured to run on a victim’s computer without being detected. TAG also reported that the hackers also changed the names, profile pictures and content of the YouTube channels to impersonate large tech or cryptocurrency exchange firms.
According to Google, “The attacker live-streamed videos promising cryptocurrency giveaways in exchange for an initial contribution.” The company has invested in tools to detect and block phishing and social engineering emails, cookie theft hijacking and crypto-scam live streams as a countermeasure.
Given the ongoing efforts, Google has managed to decrease the volume of Gmail phishing emails by 99.6% since May 2021. “With increased detection efforts, we’ve observed attackers shifting away from Gmail to other email providers (mostly email.cz, seznam.cz, post.cz and aol.com),” the company added.
Google has shared the above findings with the United States Federal Bureau of Investigation for further investigation.
Over 3.1 million (3,117,548) user email addresses were reportedly leaked from crypto price-tracking website CoinMarketCap.
As Cointelegraph reported, Have I Been Pwned — a website dedicated to tracking online hacks — found the hacked email addresses being traded and sold online on various hacking forums.
CoinMarketCap acknowledged the correlation of the leaked data with its userbase but maintains that no evidence of a hack has been found on their internal servers:
“As no passwords are included in the data we have seen, we believe that it is most likely sourced from another platform where users may have reused passwords across multiple sites.”
Updated: 10-27-2021
Cream Finance Appears To Have Suffered Major Loss In Flash Loan Hack
Malicious actors continue to target decentralized finance projects for their exploits. On Wednesday, a major DeFi lending platform suffered a flash loan attack.
Decentralized lending platform Cream Finance appears to have suffered a severe exploit on Wednesday, with an attacker stealing over $100 million worth of funds through a large flash loan attack.
Blockchain data analytics company PeckShield first identified the flash loan on Wednesday. The compromised funds were mainly Cream liquidity provider tokens, as well as other Ethereum-based tokens.
#FlashLoanAlert https://t.co/XzAvHqoINN
— PeckShield Inc. (@peckshield) October 27, 2021
During a flash loan attack, an attacker exploits vulnerable smart contracts in order to create their own arbitrage opportunity. Typically, this is done by modifying the relative value of a trading pair by flooding the contract using their loaned tokens.
Cream Finance has been routinely targeted by attackers, as evidenced by the $19-million flash loan hack of the protocol in August. As Cointelegraph reported at the time, the attack was facilitated by a reentrancy bug introduced by the Amp cryptocurrency, an Ethereum-based token designed to collateralize digital payments on Flexa.
At the time of writing, Cream’s total value locked (TVL) was worth over $1.5 billion, according to industry sources.
Cream Finance’s forums appear to have been pulled in the wake of the attack, though the protocol did notify its Twitter followers that the flash loan is being investigated. The Twitter thread is filled with angry responses about Cream’s poor track record when it comes to safeguarding user funds.
We are investigating an exploit on C.R.E.A.M. v1 on Ethereum and will share updates as soon as they are available.
— Cream Finance (@CreamdotFinance) October 27, 2021
While decentralized finance, or DeFi, has been lauded for revolutionizing traditional finance and promoting financial inclusion, the industry’s track record regarding consumer protection has been shoddy.
A comprehensive list of DeFi attacks reveals 63 exploits as of Sept. 16, with the lost funds totaling roughly $1.2 billion, according to CryptoSec. The latest exploit of Cream Finance would be one of the largest.
The value of Cream Finance’s CREAM token crashed amid the news, falling more than 26% to $115.47, according to Cointelegraph Markets Pro.
UK Police Seize $2.7M In Crypto From Teenager In Money Laundering Investigation
The 17-year-old appeared in court on Tuesday and was sentenced to community service.
U.K. police seized more than £2 million ($2.7 million) in cryptocurrency from a 17-year-old during an investigation into what they called a “sophisticated cyber fraud.”
* Detectives from the Cyber Crime Unit said they had uncovered links to money laundering through cryptocurrency, which led to the seizure of more than 48 bitcoin and other cryptocurrencies.
* The teenager, who was not identified for legal reasons, was arrested in August 2020 following an investigation into reports of credit card fraud and the theft of personal information to defraud a digital gift voucher company out of approximately £6,000 ($8,200).
* Links to money laundering through cryptocurrency were discovered later.
* The youth appeared in court in the northern English city of Lincoln on Tuesday and was sentenced to service in the community.
* “This was a sophisticated cyber fraud and a complex investigation which involved our Cyber Crime Unit working collaboratively with a number of external agencies and other internal departments,” said Cyber Crime Investigator Detective Constable Luke Casey.
Updated: 10-29-2021
Why Cybersecurity Is An Important Consideration For Crypto Hedge Fund Launches
The looming threat of an exploit remains a hurdle as traditional asset managers spin up crypto funds.
More investment managers are trading digital assets as interest in cryptocurrencies continues to grow. AIMA’s Global Crypto Report, released over the summer, showed that around 20% of hedge funds are now investing in the space.
As a fund manager, protecting intellectual property, the complex algorithms, systems and data that allow them to generate returns, is paramount. That is why cybersecurity is an important consideration for both traditional managers moving into the space and newer startup funds.
George Ralph, global managing director of cybersecurity firm RFA, has witnessed a large uptick in crypto clients in the U.K. looking for security and infrastructure solutions.
Ralph says the three biggest challenges that traditional funds cited when looking at a potential move into the crypto space were “regulatory uncertainty, reputational risk and lack of infrastructure.’’
Exploits remain common in the digital assets space, especially in the more experimental realm of decentralized finance (DeFi).
In August, more than $600 million was stolen in one of the biggest crypto heists to date. Hackers were able to exploit a vulnerability in Poly Network, a decentralized finance platform that allows different blockchains to connect to work together.
In an unexpected twist, the hacker responsible returned a large majority of the stolen funds after experts and businesses said they would track their activity on the blockchain. Mt. Gox, the world’s largest bitcoin exchange at the time, filed for bankruptcy in March 2014 after hackers stole $460 million worth of crypto.
“Simple and secure storage solutions are urgently needed for the more than 221 million crypto users around the world who are targets for fraud and theft,” according to Jon Wilk, CEO of CompoSecure.
“More than $8 billion in crypto has been hacked or stolen in 2021 thus far, doubling the previous year, including examples of crypto exchanges being hacked, personal devices being compromised, or usernames and passwords being phished that were part of these growing losses,” Wilk said.
With regard to crypto fund launches, the key thing in terms of threats is event-driven, there is a huge focus on insider threats, said RFA’s Ralph, and this has been exacerbated by the move to working from home following the COVID-19 outbreak.
Investors looking to launch funds in the post-COVID era are having to hire people they have never met before; conducting checks on potential new hires is harder in this current paradigm, Ralph said.
Peter Habermacher, CEO of Aaro Capital, said the “key targets for criminals are usually bank accounts or the assets of a fund. However, leakage of confidential information, intellectual property and personal data can be equally harmful and the issues in this regard can sometimes be internal.”
But not all that’s new is without precedent.
“Crypto asset funds are like hedge funds in the 1990s”, said Habermacher. “The market is dominated by startup managers who are operationally weaker than their established counterparts in traditional asset management and, as such, they often do not have the necessary cybersecurity procedures in place to completely satisfy institutional due-diligence processes.”
More needs to be done on the regulatory side, Habermacher said, to ensure that “crypto service providers such as exchanges and custodians are properly regulated and adhere to minimum security and process standards.”
Crypto criminals stole $1.9 billion in 2020, according to a report from blockchain sleuthing firm Ciphertrace, down from $4.5 billion in 2019.
Updated: 11-1-2021
$139M BXH Exchange Hack Was The Result of Leaked Admin Key
The hack might have been the work of one of BXH’s own employees, CEO says.
A hack on Boy X Highspeed (BXH), a decentralized cross-chain exchange, that drained $139 million of funds was probably the result of a leaked administrator key, and possibly an inside job, CEO Neo Wang told CoinDesk
* Based on a consultation with an external security team, BXH says the hacker was probably able to break into the exchange’s Binance Smart Chain address after getting hold of the administrator’s private key, Wang said.
* The hacker either broke into the keyholder’s computer or might have been one of BXH’s technical staff, Wang said. The team is looking into the possibility the hacker set up a virus on BXH’s own site that the administrator clicked on, giving the attacker access to his computer and eventually the key, the CEO said.
* BXH announced the hack in a tweet on Sunday. BXH user funds on Ethereum, Huobi ECO Chain and OKEx OEC are safe, the team said. BXH halted withdrawals until the issue is resolved.
* The inside-job theory is supported by findings that indicate the attacker was in China, where most of BXH’s technical team is based, according to the CEO.
* Wang attributed these findings to PeckShield, a blockchain security company that is working on the case with BXH. He said he is confident that with the support of PeckShield and Chinese authorities the hacker will be tracked down.
* If the hacker is not found or returns the money, BXH will take full responsibility for the incident and figure out a user repayment plan, Wang said.
* BXH is offering a $1 million bounty to any teams that help retrieve the funds, and will give the hacker an unspecified reward if the money is returned.
* PeckShield confirmed the leaked admin key theory in a tweet early on Monday, without providing details.
* BXH has also filed a case with China’s network security police, a special force that investigates digital crime, the CEO said.
* The hack is one of several attacks on DeFi projects in the last couple months. Just days before the attack on BXH, Cream Finance suffered $130 million in losses. August saw the largest hack in DeFi history when cross-chain protocol Poly Network lost $600 million, which was eventually returned.
Investors Rug-Pulled After Pouring $57M Into Dog-Themed OlympusDAO Fork
Hong Kong police have reportedly been notified of the incident, with the primary suspect having filed a police report and handed a computer over to authorities.
After launching via a Discord channel on Oct. 28, AnubisDAO went on to raise roughly 13,256.4 Ether (ETH) using AlchemistCoin’s liquidity bootstrapping protocol (LBP), Copper. However, the funds were unexpectedly sent to a different address roughly 20 hours into the LBP.
CNBC spoke to one investor who claims to have lost almost $470,000 to AnubisDAO. The investor, Brian Nguyen, conceded to subscribing to a “buy first, do research later mentality,” describing the loss as “pretty painful.”
Nguyen noted that he was attracted to AnubisDAO because of its canine-themed branding amid the meteoric gains recently reaped by some dog-token investors after seeing Anubis promoted on Twitter by prominent pseudonymous decentralized finance advocate Sisyphus.
Anubis is the Greek name for the Egyptian god of death and the underworld, with Egyptian imagery depicting the god as donning the body of a human and the head of a dog.
Investors appear to have lost roughly $57 million worth of Ether in what many are describing as a rug-pull executed by the upstart canine-themed OlympusDAO fork, AnubisDAO.
Sisyphus has published a detailed timeline outlining AnubisDAO’s formation and launch and claims to have engaged law enforcement in both the United States and Hong Kong. Sisyphus has also offered to cease the civil proceedings should the perpetrator return the stolen finds minus a 1,000-ETH bounty.
In lieu of a case number which can be released to the public (hopefully this is available tomorrow), please see below for confirmation I am actually in touch with authorities https://t.co/jCgOwaq129
— Sisyphus (@0xSisyphus) October 31, 2021
Inside Job?
According to Sisyphus, the idea for an OlympusDAO fork inspired by Shiba Inu’s branding arose from discussions among members of the PebbleDAO project during Tuesday and Wednesday.
A Telegram channel for the project was created on the same Wednesday, with its six original members all hailing from PebbleDAO. The following day, it is decided that the pseudonymous founding member “Beerus” would be tasked with deploying the LBP — a decision that Sisyphus now describes as a “critical mistake”:
“This was the critical mistake. This should have been done from the original multisig wallet.”
With just hours left until the LBP was scheduled to close on Friday, Beerus claimed “to have opened a malicious link from a PDF” and exposed the private keys used for the LBP launch.
13,556 ETH was then pulled from the LBP shortly after. However, Beerus’ personal wallet funds appear to remain “intact and under his control.”
Sisyphus also notes that “security researchers provided the PDFs from phishing emails” distributed during the day Beerus claimed to have clicked the malicious link, noting tha “at this point, none have found any malicious content contained in the PDFs.”
Beerus’ real-world information is also collated and partially published on Twitter, and Hong Kong authorities were contacted on Friday. Beerus filed a report and turned one computer over to Hong Kong police the following day.
Sisyphus also notes that wallets associated with the incident have since sent ETH to Coinbase, adding that the exchange has been notified of the transactions.
Updated: 11-2-2021
Ransomware HQ: Moscow’s Tallest Tower Is A Cybercriminal Cash Machine
One of the city’s most prestigious addresses houses companies providing a vital service to hackers.
The crown jewel of Moscow’s business district, a 97-story glass tower known alternately as Federation Tower East or Vostok, is a tribute to Russia’s post-Soviet economic influence and national strength.
Promotional materials for the building, which was the tallest in Europe when it was completed in 2017 and is now No. 2, boast of its highly paid staff and its supposed fortification against “missiles and explosions.” Its apartments are rented and owned by high-ranking government officials and C-suite executives. Residential units sell for upwards of $36 million.
The building has also been home to more than a dozen companies since 2018 that convert cryptocurrencies to cash, judging from the addresses listed on company websites.
Although there’s nothing inherently illegal about this, such businesses can enable criminals to cash out profits from digital crimes if they don’t vigilantly monitor their customers, and some find lax oversight to be a useful market niche.
Experts have linked at least four of the companies in Vostok to money laundering associated with the ransomware industry, which has generated $1.6 billion in ransom payments since 2011, according to the U.S. Treasury Department.
The perception that the Russian government tolerates, or even encourages, some types of cybercrime has been at the heart of the Biden administration’s conflict with Russian President Vladimir Putin.
According to the Treasury Department, this year criminal hackers, mostly based in Russia or Eastern Europe, have made $590 million from ransomware attacks against schools, businesses, government entities, and health-care providers—42% more than they did in all of 2020.
At a summit about a month after a Russia-linked cybergang extracted $4.4 million from Colonial Pipeline Co., Biden warned Putin that failure to end these attacks would be met with retaliation. Nevertheless, profit-driven hackers have continued to target U.S.-based networks.
It’s hard to come up with a stronger illustration of the ineffectiveness of Russian enforcement than the existence of multiple entities with links to ransomware operating out of what is perhaps Moscow’s most prestigious office tower.
One of the Vostok companies is Suex OTC, the first Russian company to face U.S. sanctions for helping ransomware cartels launder money.
Suex, which operates out of Suite Q on the 31st floor, has processed at least $160 million in Bitcoin from illicit and high-risk sources since 2018, according to the blockchain research firm Chainalysis. These transactions account for 40% of the company’s known business.
Egor Petukhovsky, Suex’s largest shareholder at the time of the Treasury Department’s sanctions, denied in a Facebook post in October that he or his business helped launder money for hackers and vowed to “firmly defend my name in litigation” in the U.S.
An occupant of the 22nd floor, EggChange, is under investigation in the U.S. and Europe for allegations of money laundering, according to three sources familiar with the probe who sought anonymity because they’re not authorized to discuss the investigation. (The Treasury Department declined to confirm the existence of the investigation.)
Binance, the world’s largest cryptocurrency marketplace, says it has also “flagged several accounts and illicit flows associated with” platforms including EggChange and CashBank, another company operating out of Vostok.
After alerting law enforcement of “potentially illicit activities,” Binance says it shut down the accounts it identified.
Buy-bitcoin.pro, which also lists Vostok as its headquarters, has processed hundreds of thousands of dollars in ransomware funds and for other illicit operators including Hydra, the largest darknet market based in Russia, according to Chainalysis. EggChange, CashBank, and Buy-bitcoin.pro didn’t respond to requests for comment.
Cryptocurrency companies are a major presence in Moscow City, the business district surrounding Vostok. Spreading over about a quarter square mile on the former site of an industrial park that was razed just after the fall of the Soviet Union, the financial district has housed at least 50 companies that convert cryptocurrencies into cash, some with connections to illicit activities.
That makes it one of the world’s most influential stations for cashing out digital coins, according to cybersecurity and cryptocurrency experts.
Russian law requires companies to conduct know-your-customer, or KYC, checks for cash transactions exceeding 600,000 rubles (about $8,500), although cryptocurrency exchanges aren’t regulated and their reporting obligations aren’t entirely clear, according to Maria Agranovskaya, a lawyer who represents Binance in Russia.
KYC rules typically involve cross-referencing an individual’s personal information against public databases; financial institutions can also limit the size of large transactions involving newly created accounts until they’re satisfied about the account holder’s identity and source of funds.
These requirements aren’t particularly onerous, according to Jackie Singh, a former senior cybersecurity staffer at the Biden campaign who’s now an adviser and senior strategist to the blockchain security startup Metaversable.
She sees skipping customer identification norms as a red flag for investigators hunting for illicit operators.
“There’s no reason for a person who is conducting legal business to seek out an exchange of any kind that does not comply with their country’s legal KYC processes,” she says.
One reason Vostok has become a locus for this activity is the credibility the address conveys, according to Stanislav Bibik, a partner at Colliers, the property investment firm. Operating there “gives status to the tenant and says that he has a solid business,” Bibik says.
The reality is that companies operating in the building don’t necessarily have any direct connection to its management firm, billionaire Roman Trotsenko’s Aeon Corp.
Aeon manages the building and acts as its broker while owning a small percentage of its space, and individual floors are now owned by more than 100 other entities.
These have recruited their own tenants without any direct involvement from Aeon, according to real estate experts in Moscow. Aeon didn’t respond to requests for comment.
The cryptocurrency companies operating within the building are using it as more than a P.O. box—in at least one instance it’s the location where money actually changes hands.
A digital coin trader recently described the experience of cashing out coins at Vostok through EggChange, requesting anonymity to protect the identities of those involved in an investigation aimed at identifying players central to global cryptocurrency laundering.
The transaction, like most others, began by exchanging messages with an account on the messaging service Telegram, which EggChange advertised on its website and on cryptocurrency web forums.
The person running the account provided a document with formal terms of exchange, including the vendor’s commission of 1.7%.
The document had spaces for the trader to include a name, passport number, and signature, which the trader was instructed to return to EggChange. But the trader never provided the information, and EggChange never demanded it.
All the platform wanted was a name—any name—so the front desk at Vostok could print out a visitor’s badge. Bloomberg Businessweek confirmed the trader’s account by reviewing Telegram chats with EggChange.
EggChange allows customers to cash out cryptocurrencies through couriers in multiple countries, but it has presented its office at Vostok as a kind of salon for cryptocurrency enthusiasts.
“Besides a safe and quick exchange—we guarantee fun and educational conversations about the world of crypto, coffee, tea and strong beverages,” reads a 2018 forum post advertising its services.
The reality was more pedestrian. The trader sent a proxy, also known as a money mule, to pick up the cash. The mule was equipped with a fake passport, but the trader says no one at the security desk or EggChange’s office ever asked to see any identification.
Instead, the mule gave a fake name to obtain a generic plastic badge and was given instructions to ride an elevator to the 22nd floor to gain access to Suite 9.
Upon arrival, the mule found a metal door and keypad. The Telegram contact had provided the four-digit code 2209. At entry, the mule was met by a nondescript, two-room office with views of the meandering banks of the Moskva River.
A receptionist was waiting, equipped with a mobile phone and barricaded behind a desk with a bowl of candies, coffee, and tea. There was no EggChange signage, no fun or educational crypto conversations, and no indication that anyone else worked there.
The mule was asked to recite another passcode that had been shared over Telegram, this one to identify and verify the transaction, then asked to deposit any electronics into a locker to defend against electronic surveillance.
The receptionist directed the mule toward another door, which swung open to reveal a man who handed over an envelope of cash.
That was the end of the transaction. The mule walked out of the gleaming tower and back onto Moscow’s streets, blending into foot traffic, pocketing the cash without ever having to reveal an identity. It was as if no one had been there at all. —With Alexander Sazonov
BOTTOM LINE – Companies are enabling the Russian ransomware industry with brazen openness in a prestigious building in the country’s capital city.
Updated: 11-3-2021
Shiba Wallet With Billions Is Scrutinized As Coin Tumbles
The unlikely star of the cryptocurrency world in October was Shiba Inu, named after the same breed of dog that inspired the market’s former unlikely meme-coin darling Dogecoin.
The value of the token has tumbled in recent days after surging for most of last month, temporarily leapfrogging over Dogecoin and putting it among the top cryptocurrencies in existence — despite the fact that its provenance as a meme leaves it without much of a fundamental economic reason to thrive.
As the price frenzy reversed in recent days, the crypto world’s attention has been fixated on a “whale” wallet controlling billions of dollars worth of the token. There was unsettling news for all the minnows who bought Shiba Inu and were sitting on paper gains of a lifetime: The whale has been moving the coins into different wallets, raising concern the holder was about to sell.
The dog-coin drama is the latest episode that highlights the fact that, despite an abundance of transparency in a market where every transaction is recorded on a blockchain for the public to see, the anonymity of some of the players involved — including, in this case, even the creators of the coin — leads to a house-of-mirrors effect because no one really knows exactly who is doing what.
“Legitimate crypto is fully transparent about transactions, code and other matters — but is usually opaque about matching transactions to individuals,” Aaron Brown, a crypto investor who also writes for Bloomberg Opinion, said Wednesday. “This is the opposite of the banking system, which is opaque about everything except personal identification.”
The ownership of Shiba Inu has come under scrutiny as the token — known by its ticker SHIB — started flying out of the whale’s wallet at a fast clip.
“It looks like there were four transactions out of that account yesterday, each sending $695 million of SHIB to a different account — so a total of $2.78 billion,” Tom Robinson, co-founder of Elliptic, which does blockchain forensics, said on Wednesday. “Whoever it is purchased the SHIB on Uniswap about a year ago, for not very much.”
JUST IN: Shiba owner that turned $8k into $5 billion removed $2.9 billion worth #Shiba tokens from its original wallet. pic.twitter.com/usX4LjpDBd
— Blockworks (@Blockworks_) November 3, 2021
As has been widely reported, Ethereum co-founder Vitalik Buterin was given more than half of all Shiba Inu tokens by the token’s anonymous creator, and then took most of them out of circulation by sending them to what’s known as a “burn wallet.”
“Limiting supply, pricing the coin at extremely low decimals, timely Twitter posts and gifting Shiba Inu coins to Ethereum co-founder Vitalik Buterin are part of what captivates speculators,” Bloomberg Intelligence analyst Mike McGlone wrote in an Oct. 29 note. “Shiba Inu presents a unique blend of exploitation, good marketing, ESG, supply vs. demand economics and gambling on an unprecedented 24/7 global scale, and faces reversion worthy of its parabolic rise.”
After surging in price for most of October, Shiba Inu has tumbled in recent days. The coin, each of which trades for tiny fractions of a penny, is currently down about 30% over the last 24 hours and has fallen about 48% from its peak on Oct. 27 to $0.00004546 midday Thursday, according to CoinMarketCap.com
Shiba Inu is not the first coin to trigger concern about high ownership concentration. Initially, Bitcoin and Ethereum were highly influenced by whales whose trades could sway market prices. Their ownership concentration has since declined, as more institutions and retail investors jumped into crypto. That said, even today about 2,000 addresses own more than 40% of all Bitcoin, per BitInfoCharts.
There are many pockets of the crypto market where coin ownership is still highly concentrated. Many of the smaller of the more than 13,500 cryptocurrencies are majority owned by a handful of wallets. In decentralized-finance apps, which create their own tokens to let people trade, lend and borrow from each other, a small percentage of users controls everything. Between 20 and 50 crypto-trading firms “are pushing most of the volume in crypto,” said Antonio Juliano, founder of DeFi exchange dYdX.
“I don’t think it’s so totally different than the way things work in traditional finance,” he said. “Big Wall Street funds push most of the volume.”
Still, a lack of regulation and official market surveillance leaves meme coins like Shiba Inu vulnerable to suspicion even as its surge in price brings it to a broader, mainstream audience. While it’s available for trading on Coinbase’s exchange, others such as Kraken and Robinhood have so far resisted — despite vocal lobbying from their clients.
“Legitimate crypto has a solid underlying economic case, its value does not depend heavily on who holds how much of it,” adds Brown. “But for crypto with no underlying economics — whose value is determined only by speculation — concentrated ownership suggests a rigged game.”
Updated: 11-4-2021
‘PlugWalkJoe’ Indicted For $784K Cryptocurrency Theft Scheme
Joseph O’Connor indicted on a raft of wire fraud, computer hacking, money laundering and identify theft counts.
Joseph O’Connor, known in some corners of the internet as PlugWalkJoe, was indicted on an array of charges relating to a May 2019 cryptocurrency exchange hack. During the attack, he is alleged to have absconded with digital assets valued at approximately $784,000.
In the criminal scheme, authorities believe O’Connor utilized SIM swap attacks (an artifice of fraud where 2FA phone calls and text messages are rerouted to a device controlled by the scammer) on three separate executives at an undisclosed cryptocurrency company to take control of their employers’ systems.
O’Connor may have then diverted over 7 BTC, 407 ETH, 6363 LTC and 770 BCH from wallets maintained by the corporation on behalf of their users to wallets under his own control.
The indictment was brought by the US Attorney’s office in the Southern District of New York, which is well known for its prosecution of high-profile financial crimes. The case is assigned to Judge Richard Berman and was investigated by the FBI.
O’Connor is specifically charged with conspiracy to commit computer hacking, conspiracy to commit wire fraud, conspiracy to commit money laundering and aggravated identity theft. The identity theft count carries a mandatory minimum of two years in prison to be served consecutive to any other sentence imposed.
O’Connor is currently fighting extradition to the United States from Spain, where he was arrested in July on charges brought in the Northern District of California related to the 2020 Twitter hack in which he is alleged to have gained control of 130 separate prominent Twitter accounts — including those of Barack Obama, Elon Musk, Apple and Kanye West.
The guilty parties used these accounts to promote a cryptocurrency scam before making off with about $110,000 in ill-gotten gains.
MetaMask, Phantom Wallet Users Targeted In Crypto Phishing Scam: Report
The scam campaigns, which imitated popular crypto wallet websites like Metamask, have resulted in losses of at least $500,000.
Users of crypto wallets MetaMask and Phantom, as well as the crypto swap platform PancakeSwap, have been targeted in a crypto phishing scam involving at least half a million dollars being stolen, according to a Check Point Research (CPR) report.
* CPR said that in the past few days there have been “multiple events” in which hundreds of crypto wallet users have had their funds stolen while trying to download and install well-known wallets like Metamask or change their currencies on crypto swap platforms such as PancakeSwap or Uniswap.
* The scam campaigns used search engine advertisements to target crypto wallet users. They then employed fake URLs and websites to allow scammers to steal wallet passwords and access crypto funds held in wallets, said CPR.
* The report gives an example of how an attacker uses a Google ad campaign to steal the user’s private key and access their MetaMask wallet by giving them a phrase that allows them to steal the funds upon transfer.
* CPR advised crypto wallet users to “refrain from clicking on ads and only use direct, known URLs.”
Updated: 11-5-2021
FBI Warns of Scams Using Crypto ATMs And QR Codes
The U.S. law enforcement agency says there has been an increase in scammers directing victims to use physical crypto ATMs and QR codes to complete transactions.
The Federal Bureau of Investigation (FBI) is warning there has been a rise in fraudulent schemes using cryptocurrency automated teller machines (ATM) and quick response (QR) codes to facilitate payments.
* The FBI said it has seen an increase in scammers directing victims to use physical crypto ATMs and QR codes to complete payment transactions.
* Scammers will request payment from the victim and then direct the victim to withdraw money from the victim’s financial accounts, such as investment or retirement accounts.
* The FBI warns they will also provide a QR code associated with the scammer’s cryptocurrency wallet for the victim to use during the transaction.
* The scammer will then direct the victim to a physical cryptocurrency ATM to insert their money, purchase cryptocurrency and use the provided QR code to auto-populate the recipient address. Often the scammer is in constant online communication with the victim and provides step-by-step instructions until the payment is completed, said the FBI.
* “It is important to remain vigilant and not make payments to someone you have only spoken to online, even if you believe you have a relationship with the individual,” advised the FBI.
DeFi Lender bZx Suffers Hack For Reported $55M
bZx tweeted that a private key controlling the protocol’s deployment on Polygon and Binance Smart Chain was breached.
Decentralized finance (DeFi) lender bZx suffered a hack of reportedly $55 million, according to a tweet on Friday by the blockchain security firm SlowMist.
* “#bZx private key compromised, over $55 million dollars stolen so far. We’ll continue to update as more information is discovered,” SlowMist tweeted.
* bZx responded in a tweet that a private key controlling the protocol’s deployment on Polygon and Binance Smart Chain was compromised, but that its smart contracts were not.
* The protocol added that about 25% of the stolen amount was “personal losses from the team wallet that was compromised,” and that the incident is still under investigation.
* bZx suffered three hacks last year, although it was able to recover $8 million in cryptocurrency from the third and largest of these attacks, which occurred in September. The other two hacks for $630,000 and $350,000, respectively, occurred in February.
Updated: 11-8-2021
US Officials Seize $6.1M In Crypto From Ransomware Actors, Add Chatex To Sanctions List
“This will not be the last time — the U.S. government will continue to aggressively pursue the entire ransomware ecosystem and increase our nation’s resilience to cyber threats,” said Attorney General Merrick Garland.
The United States Department of the Treasury has announced it will impose sanctions on the cryptocurrency exchange Chatex and its support network for allegedly facilitating transactions for ransomware actors.
In an advisory update issued on Monday, the Treasury Department Office of Foreign Assets Control (OFAC) added Chatex as well as Izibits OU, Chatextech SIA and Hightrade Finance to its list of entities sanctioned by the U.S. government.
The department claimed Chatex has “direct ties” with Czech Republic- and Russia-based business Suex OTC, which it sanctioned in September.
According to OFAC, Chatex has helped facilitate transactions for ransomware groups, with more than half of the exchange’s transactions “traced to illicit or high-risk activities such as darknet markets, high-risk exchanges, and ransomware.”
The addition of the exchange to the sanctions list follows Latvian and Estonian authorities suspending Chatextech’s operations and revoking Izibits OU’s license, respectively.
“Unprincipled virtual currency exchanges like Chatex are critical to the profitability of ransomware activities, especially by laundering and cashing out the proceeds for criminals,” said the department.
“Treasury will continue to use all available authorities to disrupt malicious cyber actors, block ill-gotten criminal proceeds, and deter additional actions against the American people.”
In the same announcement, OFAC alleged Ukrainian national Yaroslav Vasinskyi and Russian national Yevgeniy Polyanin had been part of ransomware attacks against multiple U.S. government entities as well as many in the private sector.
As part of the Treasury Department’s actions, U.S. residents are prohibited from engaging in transactions with Vasinskyi, Polyanin, Chatex, and all associated entities, or they may face enforcement action or sanctions themselves.
The State Department announced it would be offering a $10-million reward for information leading to the location of anyone in a “key leadership position” in the Sodinokibi/REvil ransomware group.
In addition, it would offer a $5-million reward leading to the arrest or conviction of anyone attempting to initiate a major ransomware attack.
During a press conference on Monday, U.S. Attorney General Merrick Garland said the Justice Department had indicted Vasinskyi in August for his alleged role in hacking personal computers as well as conspiring to commit money laundering by demanding payment for the ransomware attacks.
According to the Attorney General, Polish authorities arrested Vasinskyi in October, and he is awaiting extradition to the United States.
In addition, the Justice Department announced a similar indictment against Polyanin, having seized $6.1 million in crypto from 3,000 ransomware attacks for which he was allegedly responsible.
“For the second time in five months, we announced the seizure of digital proceeds of ransomware deployed by a transnational criminal group,” said Garland. “This will not be the last time — the U.S. government will continue to aggressively pursue the entire ransomware ecosystem and increase our nation’s resilience to cyber threats.”
Under President Joe Biden, combating ransomware attacks on critical U.S. infrastructure has been a major issue. In June, a government task force seized more than $2 million in crypto used to pay for ransom following an attack on the Colonial Pipeline system.
Updated: 11-10-2021
Electronics Retailer MediaMarkt Hit By Ransomware Demand For $50M Bitcoin Payment: Report
Following the attack on Sunday, the attackers initially asked for $240 million.
MediaMarkt, Europe’s largest electronics retailer, has reportedly been hit by a Hive ransomware attack with demands to pay $50 million in bitcoin.
* Following the attack on Sunday, the attackers were initially demanding a ransom payment of $240 million, Bleeping Computer reported Monday.
* A subsequent report by retail news site RetailDetail said the amount had been reduced to $50 million, with payment demanded in bitcoin.
* The attack by the Hive ransomware group encrypted MediaMarkt’s servers, causing the retailer to shut down its IT systems to prevent further problems. That caused many stores, mainly in the Netherlands, to be unable to accept credit and debit card payments.
* Germany-based MediaMarkt has more than 1,000 stores across the continent.
* Recent research by the U.S. Financial Crimes Enforcement Network (FinCEN) found that payments linked to ransomware attacks this year have amounted to $590 million so far, already exceeding the total for all of 2020. It isn’t clear what proportion of those transactions involve crypto.
* Hive’s modus operandi involves gaining access to a network to steal encrypted files, while also deleting backups to prevent the target from being able to recover their data. Hive has also been known to steal files and publish them on its data leaks site unless a ransom is paid, according to Bleeping Computer’s report.
Updated: 11-16-2021
US Justice Dept Is Selling $56M In Crypto To Compensate Victims Of BitConnect’s Fraud
“This liquidation is the largest single recovery of a cryptocurrency fraud by the United States to date,” said the Justice Department.
The United States Department of Justice is planning to sell $56 million worth of cryptocurrency seized in connection with its case against Ponzi scheme BitConnect.
In a Tuesday announcement, the Justice Department said it would sell the seized crypto and hold the proceeds in U.S. dollars until it could use the funds to provide restitution to BitConnect victims.
The U.S. government is currently holding the $56 million in crypto in wallets, and said the amount of compensation to those affected by BitConnect’s fraud would depend on a “future restitution order by the court at sentencing.”
“This liquidation is the largest single recovery of a cryptocurrency fraud by the United States to date,” said the Justice Department, indicating that BitConnect was the largest cryptocurrency fraud scheme in the U.S. for which criminal charges had been filed.
It’s unclear through what means the U.S. government would handle the sale of millions of dollars worth of cryptocurrency, or what effect it may have on the price of major assets like Bitcoin (BTC) and Ether (ETH).
According to data from Cointelegraph Markets Pro, the BTC price is hovering close to $60,000 after dropping roughly 7% Tuesday, while the price of ETH is $4,254 at the time of publication, following a similar drop.
The actors behind BitConnect were responsible for running a fraudulent unregistered securities offering that netted them $2 billion. The project’s former director and promoter Glenn Arcaro pled guilty to fraud charges in September and has been ordered to pay $24 million to BitConnect’s victims.
The Securities and Exchange Commission, or SEC, also filed charges against both Arcaro and BitConnect founder Satish Kumbhani, whose whereabouts are unknown at the time of publication.
Settlements with the SEC for other individuals involved in the Ponzi scheme are pending, but many people are facing prison time or severe financial penalties for their role in allegedly scamming investors.
Created in 2017, BitConnect had promoters lure investors with promises of large returns, enticing them to use BTC as collateral against which they could borrow and trade the platform’s native token.
The lending platform closed in 2018 after cease and desist orders from state regulators, leaving many investors unable to redeem their crypto holdings.
Updated: 11-18-2021
Israeli Football Club Boss Detained In Crypto Fraud Case
The owner of an Israeli Premier League soccer club has been arrested alongside seven others on suspicion of cryptocurrency fraud of as much as hundreds of millions of U.S. dollars, Israeli police said.
Moshe Hogeg, who owns the Beitar Jerusalem soccer club, was arrested with the others in early morning raids on their homes and businesses Thursday, the police said in a statement.
Those detained are suspected of enticing investors into cryptocurrency projects that did not eventuate. They “acted jointly in a systematic manner, while deceiving investors in a number of projects in the field of cryptocurrencies,” according to the statement.
The investigation, which lasted for several months, also unearthed suspected money laundering and tax offenses, the police said.
The eight are being held on remand, a court spokesman said.
Hogeg wrote on his Facebook page on Thursday afternoon that a cryptocurrency conference scheduled for this evening would have to be canceled. “Apologies,” wrote Hogeg.
“Its all for the best.” Hogeg frequently posts about cryptocurrencies on his Twitter feed, where he describes himself as an entrepreneur, investor and “CryptoPunk.”
“Hogeg vehemently denies the suspicions against him and is cooperating fully with the investigators,” his attorneys Moshe Mazor and Amit Hadad said in a joint statement. “We are sure that at the end of the investigation it will become clear that there is no basis for the allegations against him.”
Soccer club FC Barcelona issued a statement on its website late on Thursday saying that, in “light of information received today that goes against the Club’s values,” it had canceled a contract to create and market digital assets known as non-fungible tokens with NFT marketplace Ownix.
Ownix in turn said on its Twitter feed that it was terminating a consultation agreement with Hogeg that had been in place for several months and said the Israeli businessman did not own shares in it. Ownix added it had nothing to do with Hogeg’s legal matters.
Updated: 11-19-2021
Binance Labs Invests $8M In Hackathon Organizer DoraHacks
As part of the funding, DoraHacks will co-host the latest round of Binance Labs’ startup incubator.
DoraHacks, a global hackathon organizer and Web 3 developer community, has received $8 million in strategic funding from Binance Labs, the venture capital and incubator arm of the world’s largest crypto exchange by volume.
DoraHacks provides on-chain toolkits to help developers raise funds for their startups. DoraHacks community members have received over $12 million in grants and donations so far this year, according to the company.
“Since 2018, DoraHacks has partnered with Binance on 15 global hackathons and grant rounds. Through DoraHacks’ developer events and grant toolkits, Binance has distributed over $2 million in funding to more than 100 teams,” said DoraHacks founder Eric Zhang in a press release.
“This new round of strategic investment will help us accelerate the innovation of developer incentive mechanisms, deliver more effective products to support hackathon organizers and Web 3 open-source applications and promote Dora Factory’s infrastructure and ecosystem development.”
DoraHacks partner Steve Ngok told CoinDesk the funding would also help recruit more senior management to improve efficiency and accelerate development.
As part of the funding, DoraHacks is co-organizing the recently launched third session of the Binance Labs Incubation Program, an eight-week session providing growth assistance for nine startups.
Prior participants in the incubation program include Polygon and Cere Network.
DoraHacks and Binance Labs will work together on funding and supporting more early-stage Web 3 startups. The companies will also conduct joint research and development on decentralized governance technologies and decentralized autonomous organization (DAO) infrastructure.
DoraHacks will work with Binance Smart Chain (BSC) on BSC grants, hackathons and integration of Dora DAO infrastructure.
“Backing early-stage startups and developers has always been a strategy for Binance Labs. DoraHacks is one of the largest multi-chain developer communities with great Web 3 projects emerging,” Binance Labs Fund head Bill Chin said in the press release.
Updated: 11-20-2021
Game Over! ‘Squid Game’-Inspired Crypto Scam Collapses As Price Crashes From $2.8K To Zero
Dubbed SQUID, the cryptocurrency had rallied by as much as 75,000% to cross over $2,850 but dropped to near zero on Nov. 1.
A cryptocurrency inspired by Netflix’s internationally hit TV show Squid Game scammed investors in what appears to be a $3.38-million “rug pull” scheme.
Dubbed SQUID, the cryptocurrency plunged to almost a fraction of a cent minutes after crossing over $2,850 at 09:35 UTC on Nov. 1. The deadly drop oed following a 75,000% bull run, showcasing a greater demand for SQUID among traders after its debut on Oct. 26.
At the core of the retail craze lay the popularity of Squid Game. The scammers promoted SQUID as a play-to-earn cryptocurrency inspired by the South Korean TV fictional show in which people put their lives at risk to play a series of children’s games for the opportunity to win 45.6 billion won (~$38.7 million).
The marketing ploy helped push SQUID prices from $0.01 on Oct. 26 to over $38 on Sunday. The cryptocurrency then jumped to $90 on Nov. 1, ushering in a massive pumping round that pushed its price further to over $2,850, only to crash all the way down to $0.002 minutes later.
Red Flags
In the days leading up to the massive crash, traders had complained that they could not sell their SQUID holdings in the only available market, a decentralized exchange called PancakeSwap.
In their defense, SQUID founders said they had deployed an innovative “anti-dumping technology” that limits people from selling their tokens against lower demand.
A lot of my normie friends bought this $SQUID game token and couldn’t sell i (“anti-dump feature”)
Now look what happened pic.twitter.com/wq5egYBKFa
— Friend of Peach (@WaymanCap) November 1, 2021
“The More People Join, The Larger Reward Pool Will Be (Sic),” The Squid Game White Paper Read, Adding:
“Developers will take 10% of the entry fee with the remaining 90% given to the winner.”
Major news network CNBC also published the Squid Game cryptocurrency founders’ claims without omissions, insofar that it called SQUID the “very own brand” of the Netflix show.
The Squid Game cryptocurrency founders also said they were affiliated with the Netflix show as its official token partner.
They also claimed that they had entered a strategic partnership with CoinGecko, a crypto data provider. However, in an interview with Cointelegraph, CoinGecko co-founder Bobby Ong refuted the claims, saying:
“[SQUID] did not meet our listing criteria, hence it will not be listed on CoinGecko. It’s most likely a scam.”
CoinMarketCap, a rival of CoinGecko, listed SQUID on its platform but warned visitors about the cryptocurrency’s dubious nature in a notice that read:
“There is growing evidence that this project has rugged. Please do your own due diligence and exercise extreme caution. This project, while clearly inspired by the Netflix show of the same name, is NOT affiliated with the official IP.”
Meanwhile, analysts also noted that the Squid Game token founders had no profiles on LinkedIn, with Twitterati Crypto Tyrion ruling SQUID as a “100% rug pull.”
Closed Telegram group: ❌❌❌❌
Closed discord: ❌❌❌❌
Blocked Tweets comments: ❌❌❌❌
No founder Linkedin: ❌❌❌❌
CNBC article to pump: ❌❌❌❌CONFIRMED SCAM@IncomeSharks @jaynemesis
— Crypto Tyrion (@Cryptotyrion) October 29, 2021
It now appears like a “game over” scenario for the SQUID bag holders.
Updated: 11-23-2021
U.S. Pursues Young Briton Over $8.5 Million Bitcoin Plunder
The U.S. is pursuing a British man over allegations he helped hijack an American citizen’s identity to steal $8.5 million in crypto assets while he was a teenager.
Corey De Rose, who is facing extradition to the U.S., is accused of helping hack into the man’s crypto wallet and transferring the digital currency to him and his alleged co-conspirators in 2017, lawyers for the U.S. said at the start of a London court hearing. He received 108.18 Bitcoins, valued at around $300,000 at the time.
De Rose was part of a wider team of hackers called “The Community” which allegedly hijacked U.S. identities to steal over $50 million in cryptocurrencies between 2017 and 2018, lawyers for the U.S. alleged. He’s accused of speaking to other members of the group using the Skype moniker “live:cr00k000.”
The group conspired to hack numerous individuals through SIM hijacking, a technique where a person’s identity is stolen by gaining control of their mobile phone number with the objective of stealing crypto, prosecutors allege.
Lawyers for the 22-year-old said he should stand trial in the U.K. rather than being extradited to the U.S. because a substantial part of his alleged offending took place in his home country. They are fighting against his extradition on mental health grounds and say he is a suicide risk.
Part of their case is that the cryptocurrency had no value and no harm was caused because the man he’s alleged to have helped defraud was found to have illegally sold it into the market. It’s therefore “questionable” that the man is in fact a victim, his lawyers say.
“We’re dealing with an 18 year-old boy” who’s accused of playing some part in this “over a period of two days” against someone “found to be so crooked,” that the cryptocurrency has no value, Edward Fitzgerald, De Rose’s lawyer, said in court on Monday.
Peter Caldwell, a lawyer for the U.K.’s Crown Prosecution Service, told the court it was irrelevant that the alleged victim had himself fallen foul of the U.S. Securities and Exchange Commission.
It doesn’t “allow Mr. Rose and his friends to act as Robin Hood” and take his assets for their gain, he said. “This is a very serious fraud.”
The CPS and another lawyer for De Rose who’s instructing Fitzgerald declined to comment on the case.
Updated: 11-26-2021
Hackers Can Use Compromised Google Cloud Accounts To Install Mining Software In Under 30 Seconds: Report
The report said the actors usually gained access to Cloud accounts because of “poor customer security practices” or “vulnerable third-party software.”
In a report aimed at assessing threats to Cloud users, Google’s Cybersecurity Action Team said that some attackers are exploiting “poorly configured” accounts to mine cryptocurrency.
On Wednesday, the Google team said out of 50 analyzed incidents that compromised the Google Cloud Protocol, 86% were related to crypto mining.
The hackers used the compromised Cloud accounts to access resources from individuals’ CPUs or GPUs to mine tokens or take advantage of storage space when mining coins on the Chia Network.
However, Google’s team reported that many of the attacks were not limited to a single malicious action like crypto mining, but were also staging points to conduct other hacks and identify other vulnerable systems.
According to the cybersecurity team, the actors usually gained access to Cloud accounts as a result of “poor customer security practices” or “vulnerable third-party software.”
“While data theft did not appear to be the objective of these compromises, it remains a risk associated with the Cloud asset compromises as bad actors start performing multiple forms of abuse,” said the Cybersecurity Action Team. “The public Internet-facing Cloud instances were open to scanning and brute force attacks.”
The speed of the attacks was also noteworthy. According to Google’s analysis, hackers were able to download crypto mining software to the compromised accounts within 22 seconds in the majority of the incidents analyzed.
Google suggested that “the initial attacks and subsequent downloads were scripted events not requiring human intervention” and said it would be nearly impossible to manually intervene to stop such incidents once they started.
An attack on multiple users’ Cloud accounts to gain access to additional computing power is not a new approach to illicitly mining crypto. “Cryptojacking,” as it is known by many in the space, has had several high-profile incidents including a hack of Capital One in 2019 to allegedly use credit card users’ servers to mine crypto.
However, browser-based cryptojacking as well as mining crypto after gaining access through deceptive app downloads is also still a problem for many users.
Updated: 12-3-2021
Crypto Lending Firm Celsius Reportedly Affected In BadgerDAO Exploit
The BadgerDAO attack has reportedly impacted Celsius Network for more than $50 million, sources suggest.
Cryptocurrency lending platform Celsius has reportedly lost over $50 million in the exploit of decentralized finance (DeFi) protocol BadgerDAO.
As reported by Cointelegraph on Thursday, the attack targeted the protocol on the Ethereum network, reaping an unconfirmed $120 million in assets.
According to one Redditor, the biggest alleged victim of the hack was an address that lost 896 Wrapped Bitcoin ($51 million). The address is supposed to be owned by Celsius “since it has interacted with other addresses known to be owned by them.”
The address regularly transacts with an address that has a $67 million balance, $40 million of which is Celsius’ eponymous native token CEL.
The address is also alleged to be owned by Celsius as it is related to at least one address that is tagged as Celsius Network Wallet 5 on Etherscan as they share several major transactions.
“All this means that there’s a high chance that the address who lost 900 BTC was owned by Celsius. Celsius has not confirmed anything yet, so this is all speculation for now, so we don’t know for sure if Celsius was affected or not,” the user suggested.
Celsius did not immediately respond to Cointelegraph’s request for comment.
The first reports on BadgerDAO’s security breach surfaced in early December, with the protocol officially announcing that it received multiple exports of unauthorized withdrawals of user funds on Wednesday.
The Badger team continued investigating the issue and paused all smart contracts on the protocol to avoid any further losses.
The Celsius token experienced a notable drop in late November. After reaching $4.5 on Nov. 25, CEL dropped to as low as $3.9 the next day, slightly recovering since then. At the time of writing, CEL is trading at $4.00, which is down around 9% over the past seven days but up around 1% over the past 14 days.
Celsius Network is a major crypto lending platform, allowing users to earn interest on holding digital assets like Bitcoin (BTC).
The company has emerged as one of the biggest players in DeFi, smashing a valuation between $3.5 billion after expanding its $400-million Series B funding round from October to $750 million in late November.
DeFi Disasters: $31M Drained From MonoX And BadgerDAO Losses Top $120M
A disappointing week of exploits has put a temporary grim cloud over the end of 2021, with BadgerDAO and Huobi-listed MonoX suffering major losses.
More than $150 million has been lost this week in separate security breaches at DeFi projects MonoX and BadgerDAO.
Multi-chain decentralized exchange (DEX) MonoX (MONO) suffered a cyber attack on Tuesday leading to about $31 million in losses. BadgerDAO (BADGER) suffered a front-end attack that was discovered on Thursday with estimates of Badger’s losses hitting more than $120 million.
The MonoX DEX platform suffered a single attack on Tuesday. In this attack, a bug in the smart contract allowed for a discrepancy to exist between prices of assets when manually changed.
Rekt News explained that hackers were able to inflate the price of MONO via the smart contract, then buy up other assets from the protocol with MONO.
“The hacker created a loop in which the price of tokenOut would overwrite the price of tokenIn, pumping the price of MONO over the course of many “swaps.’”
The MonoX team confirmed as much in a Tuesday tweet. In a postmortem published on Thursday, total losses were confirmed at about $31 million. The team added:
“Days like yesterday are horrible, there is no sugar coating the harsh reality of a contract being exploited and people losing money. Our supporters put their faith in a new project like us, and yesterday we let them down.”
MONO listed on Huobi only five days before the hack on MonoX.
The Badger security breach was an ongoing threat to users interacting with Badger DAO’s platform rather than a single large exploit.
Discord users began reporting unusual spend requests from the Badger platform and alerted admins on social media and on Discord as early as Saturday.
Admin Blackbear responded that the request was unusual, but likely caused by a benign bug in the front-end user interface (UI).
https://twitter.com/0xMoves/status/1466275399944445952
The bug in the UI turned out to be the malicious attacker attempting to steal funds from that user’s withdrawal. The same tactic would be used on random users for days or even weeks before it was discovered as a security breach.
At time of writing, losses from the Badger attack amounted to over $120 million, including 2078.76 BTC, 30.27 ibBTC, and 151.32 ETH, according to blockchain analytics company PeckShield. The Badger team has been investigating the issue and has paused all smart contracts on the protocol to avoid any further losses.
Updated: 12-5-2021
Bitmart Hacked For $200M Following Ethereum, Binance Smart Chain Exploit
The hackers made away with a mix of over 20 tokens that includes altcoins such as BNB, Safemoon, BSC-USD and BPay.
Crypto exchange Bitmart lost nearly $200 million in a hot wallet compromise hosted over the Ethereum and Binance Smart Chain blockchains.
The $200 million Bitmart hack was first revealed by Peckshield, a blockchain security and data analytics company that initially identified a transfer of roughly $100 million over the Ethereum blockchain.
Further investigation from the team revealed a concurrent hack of $96 million over the crypto exchange’s BSC reserves:
Total estimated loss: ~200M (~100M on @ethereum and ~96M on @BinanceChain ). (Previously we only counted the loss on @ethereum). And here is the list of affected assets/amounts on @BinanceChain pic.twitter.com/cXXApDFtd7
— PeckShield Inc. (@peckshield) December 5, 2021
The hackers made away with a mix of over 20 tokens that includes altcoins such as Binance Coin (BNB), Safemoon, BSC-USD and BNBBPay (BPay). Sizable amounts of meme coins such as BabyDoge, Floki and Moonshot were also compromised in the hack.
3/3 At this moment we are temporarily suspending withdrawals until further notice. We beg for your kind understanding and patience in this situation. Thank you very much.
— Sheldon Xia (@sheldonbitmart) December 5, 2021
In what seems like an ongoing threat to the crypto ecosystem, cryptocurrency lending platform Celsius confirmed a loss of $50 million in the exploit of decentralized finance (DeFi) protocol BadgerDAO.
The first reports on BadgerDAO’s security breach surfaced on Thursday with the protocol officially announcing that it received multiple exports of unauthorized withdrawals of user funds on Wednesday.
Taking preventive measures similar to Bitmart, the Badger team continued investigating the issue and paused all smart contracts on the protocol to avoid any further losses.
Updated: 12-6-2021
Huobi And Shiba Inu Community To Help BitMart Overcome $200M Hack
Over the weekend, hackers made away with nearly $200 million in 20 different tokens.
Following a near-$200-million hack on the BitMart exchange, the Shiba Inu (SHIB) community and crypto exchange Huobi Global aim to help the exchange strengthen security and track inflows of stolen assets.
On Sunday, crypto exchange BitMart became victim to a hot wallet compromise hosted over the Ethereum and Binance Smart Chain (BSC) blockchains. As a result, the hackers stole over $196 million, roughly $100 million over the Ethernet network and around $96 million over the BSC blockchain.
1/3 We have identified a large-scale security breach related to one of our ETH hot wallets and one of our BSC hot wallets. At this moment we are still concluding the possible methods used. The hackers were able to withdraw assets of the value of approximately USD 150 millions.
— Sheldon Xia (@sheldonbitmart) December 5, 2021
Soon after BitMart CEO Sheldon Xia confirmed the hack, Huobi announced it would help BitMart track the inflow of assets on its exchange and report matches to the stolen funds.
Huobi will do our best to assist #BitMart in handling this issue. If there are any inflows of related assets, we will report and assist in a timely manner.
— Huobi (@HuobiGlobal) December 5, 2021
Speaking to Cointelegraph, Huobi director of global strategy Jeff Mei suggested that transparency and quick responses are essential in dealing with such attacks:
“Exchanges should alert their users, other exchanges and law enforcement authorities as soon as possible and be transparent about what they are doing to handle the hack and the loss of user funds.”
Mei also stressed that users should not pool all of their assets on a single platform or a single wallet. He advised users to closely research safety measures of a platform before investing and promptly notify the personnel of the relevant exchange if they become aware of any potential security incident.
Following suit, the Shiba Inu community also confirmed it would help the hacked crypto exchange, citing its already existing efforts in reviewing potential security threats for ShibaSwap, a community-built decentralized exchange.
Dear #ShibArmy,
Even though the core of our project is decentralization, we want to show our support and give some love to our friends at @BitMartExchange, who are already working hard to fix the security incident that happened yesterday. pic.twitter.com/CJZjQHaP59
— Shib (@Shibtoken) December 5, 2021
Xia also said the exchange would compensate affected investors with its own funds. “We are also talking to multiple project teams to confirm the most reasonable solutions such as token swaps. No user assets will be harmed,” he added.
The hack forced the exchange to stop all withdrawals and deposits temporarily. However, Xia is confident BitMart will have resumed services by Tuesday.
Cross-chain protocol Synapse Bridge recently averted a multi-million-dollar exploit on the Avalanche Neutral Dollar (nUSD) Metapool.
As Cointelegraph reported, Synapse Bridge prevented a hacker from stealing approximately $8 million worth of cryptocurrencies:
“Over the past 16 hours, we encountered and discovered a contract bug in the way that the AMM Metapool contracts handle virtual price calculations against the base pool’s virtual price.”
While the threat was averted, Synapse Bridge soon deployed new nUSD pools to strengthen its security against similar attacks.
Updated: 12-10-2021
DeFi Platform BadgerDAO Says Cloudflare Flaw Led To $130 Million Heist
Decentralized finance platform BadgerDAO said a flaw in the account creation process of the software company Cloudflare Inc. led to the theft of $130 million in cryptocurrencies earlier this month.
BadgerDAO detailed how the hack took place in a blog post on Thursday, saying a phishing attack that occurred on Dec. 2 was a result of “maliciously injected snippet provided” by Cloudflare Workers, a serverless application platform that runs on its cloud network.
The post, which was prepared by BadgerDAO and cybersecurity firm Mandiant Corp., said the Cloudflare flaw had been since been remediated.
BadgerDAO hired Mandiant and blockchain forensic analysis firm Chainalysis Inc. to investigate the breach, according to the blog post.
Asked about the claims, Cloudflare said in a statement that its systems “were not compromised” and that “this has not impacted any other customers.”
“Last week, we were made aware that BadgerDAO experienced an incident,” according to Cloudflare. “We have been in touch with the organization and have provided active support to their investigation.” Cloudflare said there is no vulnerability in its Cloudflare Workers product.
BadgerDAO said more than $9 million in stolen funds are recoverable, as they were transferred by the attacker but not yet withdrawn from the company’s vaults, according to the blog post. The hacker’s identity isn’t publicly known.
BadgerDAO didn’t respond to a request for comment. Mandiant and Chainalysis also declined to comment, citing an ongoing investigation. In a tweet, Chainalysis said the hackers converted the stolen cryptocurrencies to Bitcoin.
In its blog postings, BadgerDAO said it is considering how it may repay the stolen funds, and that the breach has been reported to law enforcement in the U.S. and Canada.
The theft is just the latest in a string of hacks on decentralized finance platforms, which have resulted in hundreds of millions of dollars of losses this year. The theft is the fifth largest decentralized finance hack in terms of losses, according to Rekt News, which maintains a “leaderboard” of compromised organizations
“By the end of July 2021, major crypto thefts, hacks and frauds totaled $681 million,” according to an August report published by blockchain forensics company CipherTrace Inc. DeFi crimes continue to grow, and in the second quarter of this year, criminals netted “new highs in DeFi-related proceeds,” according to the report.
In its blog post describing the hack, BadgerDAO provided screen shots of its internal logs, revealing how a hacker allegedly leveraged a flaw in Cloudflare’s product to inject malicious code into the BadgerDAO application. The blog is unusually detailed, as most organizations that suffer hacks reveal little information.
“Badger appreciates our community’s patience while we figure out how to balance our commitment to transparency with the fact that this is still an ongoing investigation with rapidly changing information,” the blog post said.
Though BadgerDAO says the attack occurred on Dec. 2, “the actual compromise may actually date back to Nov. 20,” according to an analysis by TRM Labs, which helps financial institutions and governments fight crytocurrency fraud, money laundering and financial crime.
The hacker intercepted several large customer transactions, with one of them netting more than 900 wrapped Bitcoin — an Ethereum token representing Bitcoin — or roughly $50 million, TRM said. In total, the hacker appears to have stolen more than 2,000 Bitcoin equivalent and 151 Ethers, the blockchain forensics firm said.
“As the various forms of wrapped Bitcoin were diverted to the hacker’s address, they were converted in real-time to renBTC, a tokenized version of Bitcoin on the Ethereum blockchain, then swapped to the Bitcoin blockchain,” TRM said in a recent blog.
Updated: 12-11-2011
Bitmart Pledges To Reimburse Hack Victims As Crypto Community Voices Support
With cases of crypto-related exploits on the rise again, it appears that more can be done by platforms to bolster investor confidence.
As regulatory uncertainty continues to plague the global digital asset ecosystem, there are many anti-crypto proponents who continue to harp on the fact that the industry as a whole has a long way to go when it comes to securing itself in a manner that is anywhere comparable to the traditional finance system.
Now, with the recent Bitmart hack coming to light, these individuals have been given even more firepower.
To recap, on Dec 5, cryptocurrency exchange Bitmart was on the receiving end of a major hack that saw the platform lose nearly $200 million via a hot wallet compromise hosted over the Ethereum and Binance Smart Chain blockchains.
The breach was first exposed by blockchain security firm Peckshield whose cybersecurity team revealed that nefarious third parties were able to initially transfer roughly $100 million via the Ethereum blockchain, followed by another concurrent hack of $96 million using the crypto exchange’s BSC reserves.
The hackers were able to accrue over 20 tokens including a number of altcoins such as Binance Coin (BNB), SafeMoon (SAFEMOON), BSC-USD and BNBBPay (BPay).
They were also able to steal decent quantities of meme tokens including Baby Doge Coin (BabyDoge), Floki Inu (FLOKI) and Moonshot (MOONSHOT). As per PeckShield’s security team, the entire scheme can be attributed to a simple “transfer-out, swap and wash” maneuver.
Bitmart Responds
To gain a better understanding of how the entire incident came to be, Cointelegraph reached out to Bitmart.
A spokesperson for the trading platform pointed out that as soon as the breach was discovered, the firm took action by shutting down multiple systems to “limit any sort of immediate harm” — the actions included halting token withdrawals as well stopping users from trading certain pairs. The representative added:
“We plan to continue to gradually restore services but only following our security team’s thorough testing process. Security remains our No. 1 priority. In fact, as of Tuesday, Dec. 7, 2021, EST we have resumed ETH and ERC20 token deposits and withdrawals.”
Additionally, a written response from the exchange also highlighted that in order to bolster its native security infrastructure, Bitmart had replaced all of its token deposit addresses in relation to currencies like Bitcoin (BTC), Ether (ETH) and Solana (SOL), as well as all the other tokens involved in the incident.
“We have also notified our users of the pertinent changes”, the statement closed out by saying.
Lastly, on Dec 6. Sheldon Xia, founder and CEO of BitMart, announced via Twitter that the xchange was going to be using its own funding to compensate for any losses emanating as a result of the incident:
“We are also talking to multiple project teams to confirm the most reasonable solutions such as token swaps. No user assets will be harmed.”
The Crypto Community Shows Solidarity
Following the near $200-million hack, members of the global Shiba Inu (SHIB) community and crypto exchange Huobi Global jumped in to offer Bitmart with any sort of assistance needed by the exchange to not only strengthen its existing security setup but also to keep an accurate tab on the inflows of its misplaced assets.
Speaking with Cointelegraph, Huobi’s director of global strategy Jeff Mei noted that in cases like the one witnessed in relation to Bitmart, it is a must that transparency and immediate action be given top priority, adding:
“Exchanges should alert their users, other exchanges and law enforcement authorities as soon as possible and be transparent about what they are doing to handle the hack and the loss of user funds.”
Additionally, Mei emphasized that users should avoid pooling all of their assets on a single platform or a single wallet, and in cases where they feel something fishy might be going on, users should not hesitate to reach out to the relevant exchange and tell them about the potential security incident.
Much like Huobi, the Shiba Inu community also confirmed its intentions to help Bitmart, adding that it had already ramped up its efforts to review any potential security threats for ShibaSwap, a community-built decentralized exchange (DEX).
More Education Is Needed
Raimundo Castilla, CEO of digital asset custody platform Prosegur Crypto, told Cointelegraph that what happened to Bitmart with its recent security breach was something that was easily preventable only if the platform’s users had been educated enough to keep their digital assets externally and not on the exchange itself:
“Hot wallets should be reserved just for the funds you want to trade with. This amount of money should have been guarded on cold storage with an air-gapped system and 100% offline transactions.”
Nevertheless, Castilla went on to add that in order for platforms like Bitmart to prevent future incidents, they need to employ a combination of innovative technologies coupled with rigid governance protocols.
For starters, their private keys shouldn’t have been guarded online since anything stored online is susceptible to being attacked regardless of how well it may be protected.
“They should have worked with whitelisting so even though someone gets access to any private key, he could only send funds to a pre-confirmed wallet direction”, he elucidated.
Moreover, Bitmart could have potentially employed an advanced multiparty computation (MPC) co-signing system that made use of a multisignature approval module.
This would have required the hackers to need several people to approve the transactions in question.
Castilla added that: “Hacking just one private key can do nothing at all.” Furthermore, someone performing the role of a key account manager could have stepped in and “stopped the transaction to get to the client to see if it was legitimate.”
Better Security Measures Are The Need Of The Hour
With the crypto ecosystem seemingly under an ongoing onslaught of nefarious hacking incidents, it is worth noting that recently digital asset lending platform Celsius also confirmed that it had been faced with a loss of $50 million via an exploit related to decentralized finance (DeFi) protocol BadgerDAO.
Reports of the attack first surfaced on Dec 9. with the protocol’s core developer team announcing that they received “multiple exports of unauthorized withdrawals” related to their clients. After, they paused all of their existing smart contracts so as to mitigate any more potential losses.
That said, it hasn’t all been bad news recently, as cross-chain protocol Synapse Bridge revealed that on Nov. 9, its security team was able to avert a multimillion-dollar exploit on the Avalanche Neutral Dollar (nUSD) metapool, preventing miscreants from making their way with nearly $8 million worth of digital currencies.
Updated: 12-13-2021
Crypto Exchange AscendEX Hacked, Losses Estimated At $77M
Assets not affected have been transferred to cold wallets while the investigation is carried out, the exchange said.
Cryptocurrency exchange AscendEX suffered a hack for an estimated $77 million following a breach of one its hot wallets.
* On Sunday, AscendEX announced via Twitter that it had identified a number of unauthorized transactions from one of its hot wallets on Saturday.
* Assets not affected have been transferred to cold wallets while the investigation is carried out, the exchange added.
* AscendEX said it will fully reimburse all impacted users and is working with law enforcement and forensic firms to find the stolen assets.
* Blockchain analytics firm PeckShield estimated that the stolen funds amounted to $77 million spread across three chains: Ethereum ($60 million), Binance Smart Chain ($9.2 million) and Polygon ($8.5 million).
* The largest share of the $77 million was accounted for by the relatively minor taraxa (TARA) with $10.8 million, while the combined shares of stablecoins USDT and USDC accounted for $10.7 million.
* The Singapore-based exchange, which was formerly known as BitMax, claims to serve one million institutional and retail clients. It recently raised a $50 million Series B led by Polychain Capital and Hack VC.
Updated: 12-16-2021
DeFi ‘Rug Pull’ Scams Pulled In $2.8B This Year: Chainalysis
‘Rug pulls’ accounted for 37% of all scam revenue this year compared to just 1% in 2020.
Crypto investors lost over $2.8 billion to “rug pulls,” a colloquial term for a type of crypto scam, in 2021, according to a report by Chainalysis. The rise in scams mirrored a general rise in cryptocurrency prices this year, the report added.
Rug pulls, the seemingly tame crypto Twitter buzzword, accounted for 37% of the over $7.7 billion in total illicit revenue from crypto scams this year, according to the report published on Thursday. In 2020, rug pulls accounted for just 1% of the under $5 billion in total illicit revenue.
Turkish crypto exchange Thodex accounted for a majority of the lost funds on the list after its founders went missing with over $2 billion in client funds in April 2021. This was followed by dogecoin-inspired AnubisDAO at $58 million, and Binance Smart Chain-based exchange Uranium Finance at $50 million.
Other names on the list ranged from funny to absurd, such as Meerkat Finance and Evolved Apes, to Polybutterfly.
Thodex was the only “centralized” rug pull on the list, with all others belonging to the decentralized finance (DeFi) category. DeFi projects rely on smart contracts for offering financial services, such as trading, lending, or borrowing, to users.
What Are Rug Pulls Anyway?
Rug pulls are unlike vanilla scams like fake giveaways or more sophisticated crypto hacks.
In the case of DeFi platforms – developers conduct seemingly legitimate work on a blockchain, such as launching a working application and carrying out social media marketing, before issuing a token and listing on a decentralized exchange (DEX).
The listing is where the scam starts: Investors purchase the scam projects’ tokens in hopes of a price increase and supply liquidity to those projects on DEXs.
The liquidity is provided in the tokens of whichever blockchain that project is built on – such as ERC-20 tokens for Ethereum or SPL tokens for Solana – and can run into millions of dollars.
When the project is live for a few hours or days, liquidity pools can run into tens of millions or even hundreds of millions of dollars. This is where a scammer strikes in and “pulls” all liquidity away from the DEXs pocketing the entire amount. The rug pull is then complete.
An important point here is that developers of such projects do not “lock” their control over the token’s liquidity pool on a DEX and are able to retract the entire pool.
Locking the liquidity can be done via burning the private key used to start the liquidity pool, at which time it’s technically impossible for a rug pull to occur.
Scammers can also get creative at times. In early 2021, a Twitter account called “WarOnRugs” gained a following of nearly 100,000 on the microblogging site after auditing DeFi code and exposing the creators behind rug pull projects.
The account later raised $2 million from investors to battle the growing rug pull problem … before pulling the rug later.
Updated: 12-16-2021
After $130M Hack, Badger’s Restitution Plan Tests Limits of DAO Governance
One of the most devastating hacks in recent memory has led to an ambitious payback plan.
After a devastating $130 million hack, BadgerDAO is moving forward with the first steps in an ambitious restitution plan that may be among the most complex in decentralized autonomous organization (DAO) history.
In early December, a front-end exploit drained the DeFi yield vault platform of $130 million in various assets – upwards of 10% of its total value locked (TVL) at the time of the attack. Now the DAO – in this case, an ostensibly leaderless collective governing a decentralized finance (DeFi) protocol – is grappling with how and if to make users whole.
While restitution plans are a common occurrence in DeFi – an emerging and dangerous $250 billion sector where exploits themselves happen all too frequently – BadgerDAO’s effort to compensate victims may be the largest of its kind yet.
According to BadgerDAO founder Chris Spadafora, the undertaking depends on the contributions of Badger’s 32,000 users and 25 core contributors, many of whom have differing ideas about how to best handle a situation where losses well exceed the DAO’s current treasury of roughly $53 million.
In an interview with CoinDesk, Spadafora said tthe DAO has broken the lost assets into three “tranches,” each of which will require a separate governance process in order to make users whole.
Across a half dozen Badger Improvement Proposals (BIP), numerous blog posts and ongoing discussions in community forums, an outline of the protocol’s payback plan for each of the tranches is beginning to form.
The effort also comes amid a period of greater scrutiny for DAO processes.
DAOs as a model have come under criticism in recent weeks as DeFi platform Sushi has been hobbled by internal squabbling, and an ad-hoc DAO formed to buy a rare copy of the U.S. Constitution failed, in part, because their highest possible bid was public knowledge ahead of the auction.
Spadafora, however, believes Badger can rise to the challenge.
“This is one of the more precedent-setting and monumental, large-scale DAO decisions – or multitude of decisions – that the space has ever seen,” he said.
Governance Assets
The first tranche of lost assets to address is also the simplest from a governance perspective: the 192,000 BADGER tokens stolen in the attack, currently worth $2.8 million.
Restoring this asset is especially important for the governance process, as this token grants holders the right to vote in major BadgerDAO decisions.
“What the community seems to think is that those that were affected should have their governance rights reinstituted by distributing BADGER from the treasury to allow them to participate in governance related to their restitution, and moving forward with the protocol,” said Spadafora.
The protocol’s treasury currently has 7.5 million BADGER not earmarked for other uses and can distribute the tokens with a simple vote. BIP-79, a proposal to do exactly that, is currently on its way to reaching quorum in Badger governance forums and will be headed to an on-chain vote for approval in the coming days.
Per Spadafora, restoring the governance tranche would lead to 17% of all affected users getting 100% of their assets back from the exploit, though BADGER has fallen over 50% in value to $14.68 per token since the attack.
Badger Claws Back
The second tranche represents what Spadafora refers to as “reclaimable” assets.
BIP-33 introduced an emergency function that would allow for the ability for various wallets to pause the protocol’s smart contracts to mitigate the damage of an exploit, which is exactly what occurred on the night of Dec. 1.
“The contract pause prevented 50% more users that had already approved that malicious actor from spending their funds, and what it also did, it prevented any other vault tokens in the exploiter’s address from being withdrawn,” said Spadafora.
Now, the DAO wants to upgrade Badger’s smart contracts to enable “rugging the funds back,” said Spadafora.
The exploiter’s address currently has $9.2 million in vault tokens that could be seized in a “one-time function” contract upgrade. This would enable an additional 38% of affected users to get a token-for-token refund on losses.
However, for security purposes, this requires multiple governance proposals: BIP-76, which upgrades the contract to enable the seizure of stolen assets; BIP-77, which will restart the contracts and seize the funds; and BIP-78, which will return the funds.
All three are currently up for voting and appear as if they will pass with an overwhelming majority.
Major Losses
While distributing governance tokens and reclaiming vault tokens will compensate over half the affected users in the hack, the largest tranche the DAO will have to address is the most complicated, accounting for $121 million.
Because of the nature of the exploit, the attacker started with the largest affected users and worked his way down the list, meaning 10 victims make up the majority of the loss. This presents an unusual conundrum for the majority of Badger’s users.
“How do those 32,000 Badger holders feel about the disparity, the effect of the exploit on the protocol as a whole, versus a very small amount of specific victims. It’s not like 10,000 people lost $10,000 each, and that changes the dynamic quite substantially,” said Spadafora.
The supermajority didn’t lose, but hypothetically they want to act in a way that benefits them, which means restoring confidence in the protocol for the long term with full restitution.
The treasury, however, cannot afford full restitution immediately, leading to a number of thorny questions.
“There are fundamental decisions here: Should there be restitution, step one. Step two, should it be immediate or over time? If immediate, what percentage? And if it’s over time, via what mechanic? Governance tokens, maybe a vault-type product that pays back over time versus interest generated … there’s a lot of options,” said Spadafora.
Badger’s various yield vault products produce income that could be included in a compensation plan, and the overall platform has brought in $24,511,918 in revenues since launching in December 2020, per a Dune Analytics dashboard.
So far, Spadafora says that the community is attempting to take a balanced approach that will include immediate compensation as well as a payback mechanism of some sort via the vaults, with weighted immediate payouts versus long-term options.
“It might not have a defined timeframe or a complete commitment to full restitution, but the community is putting together a very clear mechanic for how restitution is happening and how it’s tracked – that’s what I’ve seen bubble up,” Spadafora added.
Precedents And Monuments
The scale of what the DAO is attempting isn’t lost on Spadafora, who notes that marshaling the community’s resources and reaching consensus hasn’t always been a smooth process.
However, he hopes the ongoing restitution debates – held just two weeks after the initial exploit – will be seen as a model for what open organizations can accomplish.
“You’re talking about people who have never met, from around the world, going through such a dramatic thing as a collective, then mustering up the strength to respond in such a high integrity way,” he said. “It’s very amazing to see.”
Updated: 12-20-2021
DeFi Protocol Grim Finance Lost $30M In 5x Reentrancy Hack
An apparent security flaw in the Grim Finance protocol allowed the attacker to fake five additional deposits.
The decentralized finance (DeFi) protocol Grim Finance reported $30 million in losses due to a reentrancy exploit of the platform’s deposits.
Grim Finance officially announced on Saturday that an “external attacker” had exploited the DeFi platform, stealing “over $30 million” worth of cryptocurrencies.
According to Grim Finance, the hack was an “advanced attack,” with the attacker exploiting the protocol’s vault contract through five reentrancy loops, which allowed them to fake five additional deposits into a vault while the platform was processing the first deposit.
Grim paused all vaults after the attack to minimize the risk for future funds: “We have paused all of the vaults to prevent any future funds from being placed at risk, please withdraw all of your funds immediately.”
Grim noted that they also notified entities involved in operating major cryptocurrencies like Circle (USDC), Dai (DAI) and the cross-chain protocol AnySwap regarding the attacker address to freeze further fund transfers.
Grim Finance positions itself as a “compounding yield optimizer” built on a DeFi-focused blockchain protocol, Fantom, allowing users to stake liquidity provider tokens by employing complex vault strategies.
According to the Fantom (FTM) Blockchain Explorer data, Grim Finance Exploiter continued transacting on Sunday. One of the addresses associated with the exploit holds $1.2 million in Bitcoin (BTC), $1.7 million in SpookyToken (BOO) alongside $13,700 in FTM tokens.
Some in the crypto community suggested that Grim Finance should hold responsibility for the exploit due to failing to adopt proper reentrancy protection tools. DeFi security platform Rugdoc.io also argued that the protocol gave the user “more privilege than is necessary.”
5) So what was the big mistake of grim finance?
1. No reentrancy guard on a pattern that absolutely needs it (@0xPaladinSec always points this out)
2. Giving the user more privilege than is necessary: There is absolutely no need for the user to be able to choose the deposit token— Rugdoc.io (@RugDocIO) December 18, 2021
The rising popularity of DeFi has triggered a number of new challenges for the cryptocurrency industry as hackers were rushing to exploit the flaws of the emerging industry. In early December, DeFi protocol BadgerDAO was reportedly exploited to the tune of $120 million.
Updated: 12-21-2021
Bent Finance Confirms Pool Exploit, Advises Investors To Withdraw Funds
Bent Finance proactively advised investors to withdraw funds and plans to reimburse losses “one way or another.”
Staking and farming platform Bent Finance has become the sixth crypto establishment to get hacked this December. The acknowledgment of the attack was followed by requesting investors to withdraw their pool funds and disabling the reward claims on the compromised platform.
Bent Finance first realized the exploit on Monday at roughly 8:55 pm EST, a timeline when the company reported no loss of funds. However, the community suspected a rug-pull event when blockchain investigator PeckShield allegedly located the source of the hack transactions.
We have located the hack tx, which interestingly is sent from the Bent Finance: Deployer @BENT_Finance !!! What is going on?! https://t.co/3L4F1gcNYJ
— PeckShield Inc. (@peckshield) December 21, 2021
“Yes, we see the same and are working through it right now,” said Bent Finance as the team appointed two independent white hat developers to get a better understanding of the unfolding situation. The company confirmed soon after:
1/ There was an exploit from the bent deployer address, it added balance of cvxcrv and mim to an address on an unvierifed update 20 days ago. We just discovered this today. There are multiple members on this team and we will make this right.
— Bent Finance (@BENT_Finance) December 21, 2021
Bent Finance continues to advise its pool investors to withdraw the funds until the exploit is addressed.
However, the company has confirmed to recover all stolen funds from the Bent curve pool:
“We recommend you withdraw from the protocol until further notice. We are not going anywhere and will recover from this one way or another.”
According to crypto fraud investigator and former member of the United States Secret Service Joe McGill of TRM Labs, the attackers managed to steal approximately 440 Ether (ETH) worth more than $1.6 million at the time of writing.
McGill’s investigations hinted that the attack has been ongoing since Dec. 12, which contradicts Bent Finance’s finding that suspects the attacker’s presence over the network since Dec. 1.
In December alone, five crypto companies — including Grim Finance, BitMart and AscendEX — have cumulatively lost over $600 million as a direct result of successful hacks. However, further investigations are underway to identify the losses from the Bent Finance exploit.
Bent Finance has not yet responded to Cointelegraph’s request for comment.
Running parallel to the ongoing exploits on crypto businesses, December has also witnessed a momentary compromise of Indian Prime Minister Narendra Modi’s Twitter account, which was used to spread misinformation about Bitcoin’s (BTC) mainstream adoption in India.
As Cointelegraph reported, hackers from unknown origins took control of the prime minister’s account on Dec. 12, who has over 73.4 million followers, to declare BTC as a legal tender in addition to announcing a 500-BTC giveaway for Indian citizens.
Updated: 12-22-2021
Hong Kong NFT Project Monkey Kingdom Loses $1.3M In Phishing Hack, Launches Compensation Fund
The exploited nonfungible token project is looking to make things right before the holidays with the help of a compensation fund.
On Tuesday, Solana nonfungible token (NFT) project Monkey Kingdom, which has received notable backing from American DJ Steve Aoki, announced via Twitter that hackers made off with $1.3 million of the community’s crypto funds through a security breach on Discord.
According to its developers, the hack first occurred with the breach of Grape, a popular solution for verifying users on Solana.
Hackers then used the exploit to take over an administrative account, which posted a phishing link in the Monkey Kingdom Discord’s announcement channel. Users who followed the link connected their wallets expecting they would receive an NFT but instead were drained of their SOL tokens by the scammer.
Announcement on the discord hack pic.twitter.com/1r7svjlZcB
— Monkey Kingdom (@MonkeyKingdom_) December 21, 2021
Tragically, the hack took place when users were lining up for the project’s second drop. The Monkey Kingdom consists of 2,222 algorithmically-generated NFTs centered around Sun Wukong, otherwise known as “The Monkey King” in Chinese folklore.
All proceeds from the initial sale of the NFTs were to go to a charity of choice, with the intent of supporting Asian communities worldwide. It was one of the most successful NFT projects to have originated in Asia.
Guys I got drained 650 $SOL.
It is one my biggest mistake.
I am always recommending people using burner but I was nervous and fomo the Monkey Kingdom Mint. Never thought it was not a legit mint link in official discord.
It is important money to my family: my wife, my son. pic.twitter.com/rtWbCu81Ga
— commenstar (@commenstar) December 21, 2021
One Twitter user, who goes by the name of “commenstar,” claims to have lost 650 SOL, worth roughly $120,400, due to the scam. But all was not lost. The staff at Monkey Kingdom has set aside a compensation fund for victims and is on track to fully reimburse those affected. The timeline and process for distributing the funds has not yet been disclosed.
Phishing attacks are nothing new for the crypto industry. Over the past year, scammers have been repeatedly targeting Discord users and exploiting the platform, itself, to orchestrate such NFT hacks.
Monkey Kingdom community, we have your back! We have begun processing compensation requests and will be contacting individuals starting today. Thank you for your patience! Once you receive your compensation, please kindly share the news with the community. For the Kingdom!! pic.twitter.com/TVbuSqdKtq
— Monkey Kingdom (@MonkeyKingdom_) December 22, 2021
$113 Million In Dirty Crypto Cleaned By Frankfurt Prosecutors
Prosecutors in the German state of Hesse tapped a local bank to “clean” cryptocurrencies worth about 100 million euros ($113 million) they seized in a criminal case against three drug traders.
The anti-cybercrime unit of the Frankfurt General Prosecutor turned to Bankhaus Scheich Wertpapierspezialist AG, a specialist in digital assets, to return the cryptocurrency to regular circulation, the agency said in a statement Wednesday.
The pair said they will cooperate in future criminal cases to put confiscated cryptocurrencies back into the markets.
The 100 million worth of digital currency was sold within a week earlier this month, Bankhaus Scheich said.
“As the cryptocurrencies are related to crime, they are considered ‘contaminated coins’ and cannot be traded on mainstream exchanges,” the Frankfurt-based lender said. The process now established “ensures that trading partners are informed that the currencies are back in legal possession and have been declared ‘clean,’ allowing them to be sold.”
The proceeds from the crypto sale will now be transferred to the state government budget.
Updated: 12-24-2021
Beware Of Sophisticated Scams And Rug Pulls, As Thugs Target Crypto Users
The year 2021 has seen an increase in “rug pulls,” a new scam capable of luring both early adopters and new crypto investors.
This year has been monumental for the cryptocurrency sector in terms of mainstream adoption. A recent report published by Grayscale Investments found that more than one-quarter of United States investors (26%) surveyed own Bitcoin (BTC), up from 23% in 2020.
With the holidays around the corner, financial services provider MagnifyMoney also found that nearly two-thirds of surveyed Americans hope to receive cryptocurrency as a gift this year.
While crypto’s growth is notable, there has also been an increase in the number of scams associated with digital assets. A Chainalysis blog post highlighting the company’s “2022 Crypto Crime Report” revealed that scams were the dominant form of cryptocurrency-based crimes by transaction volume this year.
The post notes that over $7.7 billion worth of cryptocurrency has been taken from scam victims globally. According to Chainalysis’ previous research, this number represents an 81% increase compared to 2020, a year in which scamming activity dropped significantly compared to 2019.
Scams Are The Biggest Threat For Building Trust In Crypto
Kim Grauer, head of research at Chainalysis, told Cointelegraph that while there are many different crypto-related crimes, scamming has become the largest in terms of value received by criminals.
She added that scams represent a significant threat to building trust within the crypto ecosystem, as this may prevent people from investing in digital assets.
Grauer further mentioned that scams related to decentralized finance (DeFi) have been on the rise this year. With an annualized revenue in all DeFi protocols estimated at around $5 billion, this shouldn’t come as a surprise.
More interesting, though, is that Chainalsyis has discovered that “rug pulls” have contributed to this year’s increase in scam revenue. According to Grauer, Chainalysis defines rug pulls as an instance when a person or developer decides to unexpectedly cease a project and run away with funds:
“Rug pulls have accelerated the amount of scamming the crypto space has seen this year. In addition to financial scams, rug pulls have exploited different vulnerabilities in the crypto space. Overall, they have taken $2.8 billion of cryptocurrency.”
Although rug pulls are a relatively new crime, Grauer believes these cases are becoming common in the growing DeFi ecosystem.
To put this in perspective, the Chainalysis blog post notes, “Rug pulls have emerged as the go-to scam of the DeFi ecosystem, accounting for 37% of all cryptocurrency scam revenue in 2021, versus just 1% in 2020.”
The Chainalysis blog post also provides examples of some of the biggest rug pulls of 2021. For instance, the AnubisDAO case is mentioned as the second-biggest rug pull of this year, with over $58 million worth of cryptocurrency stolen.
According to the post, AnubisDAO launched on Oct. 28, 2021, with claims of offering a decentralized currency backed by a number of assets.
However, the project didn’t contain a website or white paper, and all of the developers went by pseudonyms.
Miraculously, AnubisDAO still managed to raise nearly $60 million overnight, yet 20 hours later, all of those funds disappeared from AnubisDAO’s liquidity pool.
While AnubisDAO demonstrates a large-scale DeFi rug pull, new cases are occurring almost daily. An early Ethereum and DeFi investor who wishes to remain anonymous told Cointelegraph that they fell victim to a rug pull on Dec. 19, 2021.
The anonymous source shared that the project is called “up1.network,” noting that many early Ethereum investors were discussing Up1 in a Discord chat group. They added:
“People I trusted were mentioning the project so I checked it out. I thought it was strange to see Up1 giving away airdrops, but thought it could have been affiliated with a DeFi token I had. I then connected my MetaMask wallet and clicked on ‘get airdrop’ but kept getting an error message. I did this three times, which gave the project access to my account.”
Unfortunately, once Up1 gained access to their account, three DeFi tokens worth $50,000 were instantly taken. “I revoked access after the fact on Etherscan so they couldn’t steal any more tokens,” they mentioned.
The Ethereum investor then checked the DeFi platform Zerion where they saw the notifications that the DeFi tokens had left their wallet. Zerion also provided them with a wallet address to where the funds went, along with a message:
“0xc28a580acc42294787f44cffbaa788eaa4958056; You gave a web3 site / smart contract unlimited access to your funds (check who you gave access to and revoke here).”
While both AnubisDAO and Up1 are examples of DeFi rug pulls, it’s important to point out that the nonfungible token (NFT) ecosystem is also vulnerable to rug pulls.
Most recently, the Bored Ape Yacht Club community fell victim to a rug pull when some members decided to connect their wallets to mint NFTs from a link posted in the group’s Discord channel.
Even more surprising is that rug pull scams are also targeting mainstream NFT projects. For example, on Oct. 28, 2021, the global beauty pageant Miss Universe sent out an official tweet announcing the launch of its NFTs on the Wax blockchain. Unfortunately, the people who minted these nonfungible tokens were part of a rug pull.
As a reminder: DON’T MINT from the links posted in Discord.
Due to amazing members of the community, we’ve obtained pertinent information about the hackers.
We’re working diligently to fix this. Priorities are restoring the server, prosecuting, and making it up to the minters
— Jenkins The Valet (@jenkinsthevalet) December 21, 2021
Jessica Yang, an NFT photographer, told Cointelegraph that when Miss Universe announced the launch of an NFT project, she didn’t question whether it was a scam or not because the pageant is widely known.
“The price of each NFT was 0.06 Ethereum. That translates to around $230 for one. The artwork also has the beauty contestant’s face and country they are associated with plastered on it,” she remarked.
Yang Also Mentioned That The Project Was Geared Toward Women, Noting That Paula Shugart, The President Of Miss Universe, Previously Stated:
“Miss Universe is going to be the first brand in the NFT space that is about women, about women’s empowerment, and embracing the technology, and moving forward. I love it; this is the first one that is away from other more male-oriented spaces.”
Given the brand’s reputation and appeal, Yang and many others minted Miss Universe NFTs, connecting their wallets to the platform.
Yet Yang noted that the next day, Miss Universe deleted its official Instagram account. She then noticed that her funds disappeared entirely. Yang added:
”One red flag I saw was coming from their Discord. The moderators kept trying to get everyone to buy Miss Universe NFTs, promising that they were going along with the roadmap. Their roadmap promised monthly AMAs, signed prints, and much more. Even Steve Harvey vetted the project.”
Do Your Own Research
As the DeFi and NFT ecosystems continue to mature and grow, these environments will, unfortunately, be prone to rug pull scams until industry solutions are developed. In the meantime, the best course of action is for users to do their own research.
For instance, Grauer shared that every DeFi project should have a code audit available to make investors feel safer. “Many of the DeFi platforms that have been hacked don’t have code audits,” she remarked.
The Chainalysis blog post also pointed out that “rug pulls are prevalent in DeFi because with the right technical know-how, it’s cheap and easy to create new tokens on the Ethereum blockchain or others and get them listed on decentralized exchanges (DEX) without a code audit.”
In addition to code audits, the anonymous Ethereum investor shared that after reviewing the Up1 site more closely, they could tell that it was fake. “For instance, the team was all anonymous, with just first names that couldn’t be clicked on to open a Twitter or LinkedIn profile.”
Even with these precautions the anonymous source mentioned that wallet providers also need to do a better job of keeping users safe:
“If there is a questionable site, wallets should seek them out. I believe this technology can scale, but it has to be able to handle these scams. Otherwise, people will lose all their money.”
Following the Up1 rug pull, the anonymous source contacted MetaMask and shared that they got a response noting that it would flag the website.
It’s also important to point out that while a clear industry solution is yet to be developed, Grauer noted that, unlike fiat-related crimes, crypto payments can be traced to their source.
With this in mind, she added that some cryptocurrency platforms are starting to take action to keep users safe from scams.
For example, crypto exchange Luno partnered with Chainalysis in 2020 to protect against a scam targeting South African crypto users.
Eva Crouwel, head of financial crime at Luno, told Cointelegraph that one of the requirements from a regulatory framework point of view is to be able to monitor and act upon transactions that have a suspicion of money laundering, terrorist financing, sanctions or any other type of illicit activity.
She noted that on-chain transactions must be monitored, as well as the design and the development of case management and user interface.
In Terms Of Crypto Investors Keeping Themselves Safe From Scams, Crouwel Recommends Staying Away From Offers That Sound Too Good To Be True, Adding:
“Start by doing as much due diligence as possible. Look at the company’s/token’s social media profiles to see what other users’ experiences have been. You should also go through the company directors’ personal social media pages and look into their industry connections and employment background so ensure their history is sound.”
Updated: 12-26-2021
Crypto Wallets Attacked By Echelon Malware Through Telegram
Cybersecurity researcher @officer_cia of LobsterDAO and Immunefi bug bounty platform shared the details of another malware focused on crypto wallets and account credentials.
Echelon Is Here To Steal Your Crypto
The expert has taken to Twitter to warn all users of Telegram about the new attacks on crypto wallets registered on Telegram.
Warning ❗️ An attack on thematic @telegram crypto chats ongoing now. The attackers use an account named “Smokes Night” to spread Echelon malware by dropping a file into the chat room.
TLDR: Disable auto-downloading in Telegram settings right now.
???? See the thread below ????
— CIA Officer (@officer_cia) December 25, 2021
According to the expert, the user with the “Smokes Night” handle spreads Echelon malware by dropping an infected file into chat rooms without comment.
The expert has attached a report about a similar attack with a list of affected cryptocurrency services.
It includes a number of noncustodial wallets (AtomicWallet, Electrum, Exodus) for Bitcoin, Litcecoin, ZCash, Monero and other cryptos.
This version of Echelon has multiple credential-stealing functions, domain detection and computer fingerprinting. It also attempts to take a screenshot of the victim’s device.
Here’s How You Can Protect Yourself
The malware can steal the information even if a Telegram user does not open the file. The option of auto-downloading that is built-in to the messenger makes this possible.
As such, the reporter recommends disabling the auto-downloading option in Telegram’s settings.
In 2021, Echelon malware was described as ransomware, a malicious software program that encrypts files for ransom.
As covered by U.Today previously, in 2021, ransomware programs stole millions of dollars; typically, the malefactors demand a ransom in Bitcoin, Ethereum or Monero.
What Is A Honeypot Crypto Scam And How To Spot It?
A virtual trap to lure attackers so that you can improve security policies is what honeypot aims for!
What Is A Crypto Honeypot And Why Is It Used?
Smart contracts programs across a decentralized network of nodes can be executed on modern blockchains like Ethereum. Smart contracts are becoming more popular and valuable, making them a more appealing target for attackers. Several smart contracts have been targeted by hackers in recent years.
However, a new trend appears to be gaining traction; namely, attackers are no longer looking for susceptible contracts but are adopting a more proactive strategy.
Instead, they aim to trick their victims into falling into traps by sending out contracts that appear to be vulnerable but contain hidden traps. Honeypots are a term used to describe this unique sort of contract.
But, What Is A Honeypot Crypto Trap?
Honeypots are smart contracts that appear to have a design issue that allows an arbitrary user to drain Ether (Ethereum’s native currency) from the contract if the user sends a particular quantity of Ether to the contract beforehand.
However, when the user tries to exploit this apparent flaw, a trapdoor opens a second, yet unknown, preventing the ether draining from succeeding. So, what does a honeypot do?
The aim is that the user focuses entirely on the visible weakness and ignores any signs that the contract has a second vulnerability.
Honeypot attacks function because people are frequently easily deceived, just as in other sorts of fraud. As a result, people cannot always quantify risk in the face of their avarice and assumptions. So, are honeypots illegal?
How Does A Honeypot Scam Work?
In crypto cyber attacks like honeypots, the user’s cash will be imprisoned, and only the honeypot creator (attacker) will be able to recover them. A honeypot usually works in three stages:
To set up honeypots in Ethereum smart contracts, an attacker does not need any specific skills. An attacker, in reality, has the same skills as a regular Ethereum user. They only need the money to set up the smart contract and bait it.
A honeypot operation, in general, consists of a computer, programs and data that mimic the behavior of a real system that might be appealing to attackers, such as Internet of Things devices, a banking system, or a public utility or transit network.
Even though it looks like a part of the network, it is isolated and monitored. Because legitimate users have no motive to access a honeypot, all attempts to communicate with it are regarded as hostile. Honeypots are frequently deployed in a network’s demilitarized zone (DMZ).
This strategy separates it from the leading production network while keeping it connected. A honeypot in the DMZ may be monitored from afar while attackers access it, reducing the danger of a compromised main network.
To detect attempts to infiltrate the internal network, honeypots can be placed outside the external firewall, facing the internet.
The actual location of the honeypot depends on how intricate it is, the type of traffic it wants to attract and how close it is to critical business resources. It will always be isolated from the production environment, regardless of where it is placed.
Logging and viewing honeypot activity provides insight into the degree and sorts of threats that a network infrastructure confronts while diverting attackers’ attention away from real-world assets.
Honeypots can be taken over by cybercriminals and used against the company that set them up. Cybercriminals have also used honeypots to obtain information on researchers or organizations, serve as decoys and propagate misinformation.
Honeypots are frequently hosted on virtual machines. For example, if the honeypot is compromised by malware, it can be rapidly restored. For example, a honeynet is made up of two or more honeypots on a network, whereas a honey farm is a centralized collection of honeypots and analysis tools.
Honeypot deployment and administration can be aided by both open source and commercial solutions.
Honeypot systems that are sold separately and honeypots that are combined with other security software and advertised as deception technology are available. Honeypot software may be found on GitHub, which can assist newcomers in learning how to utilize honeypots.
Types Of Honeypots
There are two types of honeypots based on the design and deployment of smart contracts: research and production honeypots. Honeypots for research collect information on attacks and are used to analyze hostile behavior in the wild.
They acquire information on attacker tendencies, vulnerabilities and malware strains that adversaries are currently targeting by looking at both your environment and the outside world. This information can help you decide on preventative defenses, patch priorities and future investments.
On the other hand, production honeypots are aimed at detecting active network penetration and deceiving the attacker. Honeypots provide extra monitoring opportunities and fill in common detection gaps that surround identifying network scans and lateral movement; thus, obtaining data remains a top responsibility.
Production honeypots run services that would typically run in your environment alongside the rest of your production servers. Honeypots for research are more complicated and store more data types than honeypots for production.
There are also many tiers inside production and research honeypots, depending on the level of sophistication your company requires:
High-interaction Honeypot: This is comparable to a pure honeypot in that it operates a large number of services, but it is less sophisticated and holds less data. Although high-interaction honeypots are not intended to replicate full-scale production systems, they run (or appear to run) all of the services commonly associated with production systems, including functioning operating systems.
The deploying company can observe attacker habits and strategies using this honeypot form. High-interaction honeypots need a lot of resources and are difficult to maintain, but the results can be worth it.
Mid-Interaction Honeypot: These imitate characteristics of the application layer but lack their operating system. They try to interfere or perplex attackers so that businesses have more time to figure out how to respond appropriately to an attack.
Low-Interaction Honeypot: This is the most popular honeypot used in a production environment. Low-interaction honeypots run a few services and are primarily used as an early warning detection tool. Many security teams install many honeypots across different segments of their network because they are simple to set up and maintain.
Pure Honeypot: This large-scale, production-like system runs on multiple servers. It is full of sensors and includes “confidential” data and user information. The information they provide is invaluable, even though it can be complex and challenging to manage.
Client Honeypots: The majority of honeypots are servers that are listening for connections. Client honeypots actively search out malicious servers that target clients, and they keep an eye on the honeypot for any suspicious or unexpected changes. These systems are usually virtualized and have a containment plan in place to keep the research team safe.
Malware Honeypots: These identify malware by using established replication and attack channels. Honeypots (such as Ghost) have been designed to look like USB storage devices. For example, if a machine becomes infected with malware that spreads by USB, the honeypot will deceive the malware into infecting the simulated device.
Honeynets: A honeynet is a network of several honeypots rather than a single system. Honeynets are designed to follow an attacker’s actions and motives while containing all inbound and outbound communication.
Open mail relays and open proxies are simulated using spam honeypots. Spammers will first send themselves an email to test the available mail relay. If they are successful, they will send out a tremendous amount of spam.
This form of honeypot can detect and recognize the test and successfully block the massive amount of spam that follows.
Database Honeypot: Because structured query language injections can often go undetected by firewalls, some organizations will deploy a database firewall to build decoy databases and give honeypot support.
How To Spot A Crypto Honeypot?
Examining the trade history is one technique to recognize a honeypot crypto fraud. A cryptocurrency should generally allow you to buy and sell it whenever you desire. There will be a lot of buys for the coin in a honeypot scam, but people will have a hard time selling it. This indicates that it is not a legitimate coin, and you should avoid it.
Moreover, the data science approach based on the contract transaction behavior can be used to classify contracts as honeypots or non-honeypots.
Where Can Honeypots Arise In Ethereum Smart Contracts?
Honeypots might appear in three different areas of Ethereum smart contracts implementation.
These Are The Three Levels:
The Etheruem Virtual Machine (EVM)– Although the EVM follows a well-established set of standards and rules, smart contract writers can present their code in ways that are misleading or unclear at first glance. These tactics might be costly for the unsuspecting hacker.
The Solidity Compiler-The compiler is the second area where smart contract developers may capitalize. While certain compiler-level bugs are well-documented, others may not be. These honeypots can be difficult to discover unless the contract has been tested under real-world settings.
The Etherscan Blockchain Explorer-The third sort of honeypot is based on the fact that the data presented on blockchain explorers is incomplete. While many people implicitly believe Etherscan’s data, it doesn’t necessarily show the whole picture. On the other hand, wily smart contract developers can take advantage of some of the explorer’s quirks.
How To Protect Against Honeypot Contract Scams?
This section guides how to get out of the honeypot scams to avoid losing your money. There are tools available to assist you in seeing red signals and avoiding these currencies.
For instance, use Etherscan if the coin you’re buying is on the Ethereum network or use BscScan if the coin under consideration is on the Binance Smart Chain.
Find out your coin’s Token ID and enter it on the appropriate website. Go to “Token Tracker” on the next page. A tab labeled “Holders” will appear. You can see all of the wallets that hold tokens and the liquidity pools there.
Unfortunately, there are numerous combinations of items of which to be aware. The following are some of the red flags that you should know to protect against honeypot crypto scams:
No Dead Coins: If more than 50% of coins are in a dead wallet, a project is relatively protected from rug pulls (but not a honeypot) (usually identified as 0x000000000000000000000000000000000000dead). If less than half of the coins are dead or none are dead, be cautious.
No Audit: The chances of a honeypot are nearly always eliminated if a trustworthy company audits them.
Large Wallets Holders: Avoid cryptocurrencies that have only one or a few wallets.
Scrutinize Their Website: This should be pretty straightforward; but, if the website appears rushed and the development is poor, this is a warning sign!
One Trick Is To Go To Whois.Domaintools.com and type in the domain name to see when it was registered for a website. You might be quite sure it’s a fraud if the domain was registered within 24 hours or less of the project’s start.
Check Their Social Media: Scam projects usually feature stolen and low-quality photos, grammatical problems and unappealing “spammy messages” (such as “drop your ETH address below!”), no links to relevant project information and so on.
Token Sniffer is another excellent resource to spot honeypot crypto. Look for the “Automated Contract Audit” results by entering the Token ID in the top right corner. Stay away from the project if there are any alerts. Because many projects now employ contract templates, the “No prior similar token contracts” indication can be a false positive.
If your coin is listed on the Binance Smart Chain, go to PooCoin, enter the Token ID again and monitor the charts.
Stay away if there aren’t any wallets selling or if only one or two wallets are selling your chosen coin.
Most likely, it’s a honeypot. It’s not a honeypot if many wallets are selling the chosen coin. Lastly, you should conduct thorough research before parting with your hard-earned cash when purchasing cryptocurrencies.
How Is A Honeypot Different From A Honeynet?
A honeynet is a network made up of two or more honeypots. It can be beneficial to have a honeypot network that is connected. It allows businesses to track how an attacker interacts with a single resource or network point and how an invader moves between network points and interacts with many points at once.
The goal is to persuade hackers that they have successfully breached the network; therefore, adding more false network locations to the realism of the arrangement.
Honeypots and honeynets with more advanced implementations, such as next-generation firewalls, intrusion detection systems (IDSes), and secure web gateways, are referred to as deception technology.
Intrusion detection systems refer to a device or software program that watches for hostile activity or policy breaches on a network. Automated capabilities of deception technology allow a honeypot to respond to potential attackers in real-time.
Honeypots can assist firms in keeping up with the ever-changing risk landscape as cyber threats emerge.
Honeypots provide vital information to ensure an organization is prepared and are possibly the best means to catch an attacker in the act, even though it is impossible to forecast and prevent every attack. They’re also a good source of knowledge for cybersecurity professionals.
What Are The Pros And Cons Of Honeypots?
Honeypots collect data from genuine attacks and other illicit activity, giving analysts a wealth of knowledge.
Furthermore, there are fewer false positives. For example, ordinary cybersecurity detection systems can generate many false positives, but a honeypot minimizes the number of false positives because genuine users have no motive to contact the honeypot.
Additionally, honeypots are worthwhile investments since they only interact with harmful actions and do not demand high-performance resources to process enormous volumes of network data in search of attacks. Lastly, even if an attacker is using encryption, honeypots can detect malicious activities.
Although honeypots provide many advantages, they also have a lot of drawbacks and risks. For instance, honeypots only collect data in the event of an attack. There have been no attempts to access the honeypot; thus, no data exists to examine the attack.
Furthermore, malicious traffic acquired by the honeypot network is only collected when an attack is launched against it; if an attacker suspects a network is a honeypot, they will avoid it.
Honeypots are generally recognizable from legal production systems, which implies that skilled hackers can easily distinguish a production system from a honeypot system using system fingerprinting techniques.
Despite the fact that honeypots are isolated from the real network, they eventually connect in some way to allow administrators to access the data they hold. Because it seeks to lure hackers to get root access, a high-interaction honeypot is often deemed riskier than a low-interaction one.
Overall, honeypots aid researchers in understanding risks in network systems, but they should not be used in place of standard IDS. For example, if a honeypot isn’t set up correctly, it might be exploited to acquire access to real-world systems or a launchpad for assaults on other systems.
Updated: 12-27-2021
Metaswap Gas Incommunicado As Experts Link MGAS Price Drop To Rug Pull
Following the unexpected MGAS price drop, Metaswap Gas’ social media accounts were deleted, supporting PeckShield’s claim of a rug pull.
#RugPull PeckShield has detected that @MetaSwapMGAS soft-rugged, the stolen funds (1,100 BNB) are transfered to @TornadoCash (#BSC). DO NOT STAKE in this contract and if you’ve approved it, REVOKE https://t.co/b7sSsMz3ZE
— PeckShield Inc. (@peckshield) December 27, 2021
Blockchain security company PeckShield has alerted investors of a possible rug pull event after identifying a massive 46.99% price drop on MetaSwap’s MGAS token. The MetaSwap protocol allows nonfungible token (NFT) swaps over the Ethereum, Binance and Polygon blockchains.
Following the unexpected price drop, all official accounts linked with Metaswap Gas — including Twitter, Instagram and Medium — were removed, supporting PeckShield’s claim of a rug pull.
According to PeckShield, 1,100 Binance Coin (BNB) tokens, worth almost $602,000, were transferred to an account on Tornado Cash, an Ethereum-based non-custodial solution that is used to break the on-chain link between the sender and the receiver. This process adds to the difficulty in tracking the stolen funds.
PeckShield advises investors to stop staking on Metaswap Gas and revoke existing contracts to avoid further monetary losses.
In December, alone, numerous crypto entities became victims to a series of exploits, resulting in a cumulative loss of over $600 million. On Dec. 21, Bent Finance proactively asked investors to withdraw their funds after confirming a pool exploit.
1/ There was an exploit from the bent deployer address, it added balance of cvxcrv and mim to an address on an unvierifed update 20 days ago. We just discovered this today. There are multiple members on this team and we will make this right.
— Bent Finance (@BENT_Finance) December 21, 2021
Similar to other victims of the crypto community including Grim Finance, BitMart and AscendEX, Bent Finance promised its investors to return all the stolen funds. However, the team is yet to announce a plan for the same:
“We recommend you withdraw from the protocol until further notice. We are not going anywhere and will recover from this one way or another.”
Updated: 12-29-2021
Polygon Discloses Patched Exploit That Put 9B MATIC At Risk
“There is a natural tension between security and transparency,” Polygon’s team said in a Wednesday blog post.
A hacker who helped Polygon avert a multibillion-dollar disaster in early December won a $2.2 million bug bounty, the blockchain network said Wednesday.
The so-called “white hat,” known as “Leon Spacewalker” on Twitter and GitHub, reported an exploit in a critical Polygon smart contract that held more than 9 billion MATIC tokens on Dec. 3, then worth around $20.2 billion. Core developers rushed a fix by Dec. 5.
It wasn’t fast enough to protect all the contract’s funds, according to Immunefi, the crypto security startup that managed Polygon’s bug bounty program. Separate hackers pilfered 801,601 MATIC tokens (then worth around $1.4 million) on Dec. 4. Polygon Foundation said it took the hit.
Still, the fix, a hard fork live across 90% of network validators by Block #22156660, according to Polygon’s timeline of events, protected a massive trove of funds for the Ethereum scaling tool. Polygon hadn’t publicly discussed the reasoning for the hard fork before Wednesday.
Consulting The Record
CoinDesk reviewed the Polygon Discord server’s validator channel on Dec. 5. It contained multiple validators expressing anger over the core developers’ silence on pushing what is usually a major and well-publicized software upgrade through the shadows.
Indeed, the abrupt hard fork had spillover effects for the network as validators unprepared for the shift were knocked offline, according to the Discord logs.
Polygon’s developers acknowledged on Wednesday their initial silence created a precarious position.
“There is a natural tension between security and transparency,” the team said in its blog post. They said a “minimal” initial disclosure followed the Ethereum community’s “silent patch” standard.
“What’s important is that this was a test of our network’s resilience as well as our ability to act decisively under pressure,” co-founder Jaynti Kanani said in a blog post. “Considering how much was at stake, I believe our team has made the best decisions possible given the circumstances.”
Polygon’s bug bounty program awarded Leon Spacewalker $2.2 million in stablecoins; a different white hat who reported the same bug after the initial thefts won 500,000 MATIC.
Spacewalker didn’t respond to CoinDesk by press time.
Updated: 1-14-2022
Vitalik Buterin On Why Cross-Chain Bridges Will Not Be A Part Of The Multi-Chain Future
While cross-chain bridging solutions are popular, many users do not realize the full risks associated with using them.
In a much-publicized tweet this past week, Vitalik Buterin voiced his opposition to the use of cross-chain solutions by Ethereum and other blockchains, in favor of a multi-chain future.
My argument for why the future will be *multi-chain*, but it will not be *cross-chain*: there are fundamental limits to the security of bridges that hop across multiple “zones of sovereignty”. From https://t.co/3g1GUvuA3A: pic.twitter.com/tEYz8vb59b
— vitalik.eth (@VitalikButerin) January 7, 2022
For Buterin, cross-chain bridges are not ideal because they increase the security risks in the process of transferring assets. This tradeoff to security happens because the attack vectors of the assets are increased across a wider network surface area as it is moved across an increasing number of chains and decentralized applications with different security principles.
If your ETH is contained within Ethereum, then it depends only on the security validation of Ethereum’s network. But when ETH is moved across different chains on cross-chain bridges, ETH’s security is now dependent not only on Ethereum, but also on the security verification of the destination chain and any other cross-chain solutions which are used to transfer, wrap and lock up the asset.
Buterin Puts It Aptly In His Tweet:
“Now, imagine what happens if you move 100 ETH onto a bridge on Solana to get 100 Solana-WETH, and then Ethereum gets 51% attacked. The attacker deposited a bunch of their own ETH into Solana-WETH and then reverted that transaction on the Ethereum side as soon as the Solana side confirmed it.
The Solana-WETH contract is now no longer fully backed, and perhaps your 100 Solana-WETH is now only worth 60 ETH. Even if there’s a perfect ZK-SNARK-based bridge that fully validates consensus, it’s still vulnerable to theft through 51% attacks like this.”
Spreading assets across different blockchain security networks also means that chains become more interdependent on one another, since the same capital assets are being collateralized and used for different purposes.
This increased contagion risk could lead to a domino effect that would ripple through different blockchain ecosystems if one were to suffer an attack, as opposed to if the asset remained in one blockchain:
“The problem gets worse when you go beyond two chains. If there are 100 chains, then there will end up being dapps with many interdependencies between those chains, and 51% attacking even one chain would create a systemic contagion that threatens the economy on that entire ecosystem.”
Additional Security Risks With Cross-Chain Bridges
Buterin highlights a key security problem of cross-chain bridges, but its risks do not stop there. The mass majority of cross-chain bridges today typically facilitate asset transfers through centralized federations and external validators.
These solutions bypass the arduous and more expensive process of decentralized chain validation, making transactions cheaper and quicker. Popular examples include BitGo’s Wrapped Bitcoin (WBTC), Axie Infinity’s Ronin bridge, Terra’s Shuttle bridge, and much more.
However, this also means that transactions are moving away from a trustless form of verification, thereby increasing reliance on the operator of the cross-chain bridge, rather than the decentralized security of the underlying blockchain network.
In short, the key risks of cross-chain solutions can be summarized as being grounded in two points.
First, cross-chain solutions increase the number of attack vectors for the crypto assets, intensifying contagion risk across chains.
Second, the transferred assets are funneled through a variety of external validator networks that may no longer remain decentralized and trustless, thereby increasing the risk across those same attack vectors.
Users are going to lose *so much* money in cross-chain bridges over the next year. pic.twitter.com/d0nntkpde7
— Dmitriy Berenzon (@dberenzon) August 27, 2021
The Multi-Chain Future
Cross-chain bridges remain popular among users for the simple reason that it offers a premium in speed and low costs. It is a temporary band-aid on a larger problem. But as with all band-aids, they must come off.
Like Buterin, Kadan Stadelmann, CTO of Komodo, believes that this security risk will gradually become heightened in awareness and accelerate crypto’s path towards the multi-chain future:
“In the future, we’ll have both multi-chain ecosystem networks like Polkadot and Cosmos where chains rely upon a shared security mechanism as well as cross-chain bridges like AtomicDEX that connect blockchains ecosystems that would otherwise be siloed. This will likely mean that DEXs and bridging solutions will reach mass adoption.”
Multi-chain ecosystems (sometimes referred to as Layer-0 chains) such as Cosmos and Polkadot are designed to avoid the security problems of cross-chain bridges. The Polkadot blockchain allows Dapp developers to set up their own customized blockchains (named “parachains”) on top of its foundation.
All parachains are interconnected through the Polkadot’s main Relay Chain hub, which serves to coordinate security and the transfer of assets across all its parachains.
The concept is similar for Cosmos, which consists of an ecosystem of multiple independent Cosmos chains (called zones) that can send tokens and data to one another.
Unlike Polkadot however, there are multiple central hubs that zones can plug into in order to reach other zones. Terra, THORChain and Crypto.com’s Cronos chain are among the most popular names that have settled on Cosmos.
Both Polkadot and Cosmos strive to achieve interoperability of assets while guaranteeing the trustless transfer of assets that do not require users to place their trust in intermediary entities like cross-chain solutions.
Updated: 2-8-2022
DoJ Seizes $3.6B In Crypto And Arrests Two In Connection With 2016 Bitfinex Hack
“The department once again showed how it can and will follow the money,” said Deputy Attorney General Lisa Monaco.
Authorities in the United States have made arrests and announced the seizure of $3.6 billion in cryptocurrency more than five years after hackers stole 119,756 Bitcoin (BTC) from the Bitfinex exchange.
In a Tuesday announcement, the U.S. Department of Justice said it had ordered the arrest of Ilya Lichtenstein and his wife Heather Morgan for allegedly conspiring to launder crypto connected to the 2016 Bitfinex hack.
The 119,756 Bitcoin (BTC) — worth $72 million at the time hackers breached security at the exchange in August 2016 — is now valued at more than $5.1 billion.
Since the 2016 hack, individuals connected to the stolen coins have periodically moved small amounts of BTC in separate transactions, leaving the bulk of the funds untouched. The DoJ reported that it had traced 25,000 BTC of these transferred funds to financial accounts controlled by Lichtenstein and Morgan.
Special agents were then able to gain access to and seize more than 94,000 BTC — worth $3.6 billion at the time — from Morgan and Lichtenstein after a search warrant allowed them to view files containing private keys to the wallet.
“Today’s arrests, and the department’s largest financial seizure ever, show that cryptocurrency is not a safe haven for criminals,” said Deputy Attorney General Lisa Monaco. “In a futile effort to maintain digital anonymity, the defendants laundered stolen funds through a labyrinth of cryptocurrency transactions. Thanks to the meticulous work of law enforcement, the department once again showed how it can and will follow the money, no matter what form it takes.”
Assistant Attorney General for the Criminal Division of the DoJ Kenneth Polite added that federal authorities had the ability to “follow money through the blockchain.” The announcement stated that Morgan and Lichtenstein used a variety of methods to launder the illicit crypto, including chain hopping, depositing the coins at exchanges and darknet markets and withdrawing them, and automating transactions using computer programs.
In addition, the pair allegedly set up business accounts in the United States to “legitimize their banking activity.”
Both investigative teams from the FBI and the Cyber Crimes Unit of the Internal Revenue Services’ criminal investigation agency said they had worked to trace the funds from the 2016 hack. Though neither agency specified how authorities were initially led to Morgan and Lichtenstein, FBI Deputy Director Paul Abbate said the agency had “the tools to follow the digital trail.”
The DoJ’s actions represent the biggest seizure of crypto by government authorities, with the 2016 Bitfinex hack one of the biggest thefts in the history of the crypto space. Authorities have charged Lichtenstein and Morgan with conspiracy to commit money laundering and conspiracy to defraud the United States. Each could face up to 25 years in prison.
Judge Stops Release of Bitfinex Hack Laundering Suspects
Ilya Lichtenstein and Heather Morgan were arrested Tuesday on allegations they conspired to launder bitcoin from the 2016 hack.
A federal judge has halted the release of two individuals suspected of laundering proceeds from the 2016 Bitfinex hack.
Chief Judge Beryl Howell, of the U.S. District Court for Washington, D.C., stayed an earlier order by a New York magistrate judge to release Ilya “Dutch” Lichtenstein and Heather Morgan on bail.
The two were arrested Tuesday by federal officials on charges stemming from a 2016 hack of the Bitfinex cryptocurrency exchange. The U.S. Department of Justice also said officials seized 94,000 BTC, worth over $3.5 billion at today’s prices.
Inner City Press first reported the news late Tuesday. Howell’s order will delay the couple’s release at least until her court can review the initial order.
Prosecutors sought pretrial detention during the hearing this afternoon, arguing the pair might be a flight risk. Magistrate Judge Debra Freeman of the Southern District of New York sentenced Lichtenstein to home detention with a wearable GPS and a $5 million bond, while Morgan got the same with a $3 million bond.
The parents of both defendants were required, as a condition of the bond, to pledge their homes as collateral. The couple will spend at least Tuesday night in jail, pending an investigation by pretrial services officers.
The government initially asked for a $100 million bond, which was quickly rejected. The defense countered with $1 million, which was also rejected.
Lichtenstein must obtain signatures on his bond from five people, the judge ordered. Morgan was required to get two, which her parents agreed to provide.
Defense attorneys told the court that Morgan has health problems (including recent breast surgery) and that incarceration would be dangerous for her. She gets migraine headaches when exposed to bright lights and had to go to the hospital Tuesday after her arrest at around 7 a.m. Eastern time, her attorneys said.
According to a criminal complaint attached to the Department of Justice’s press release, the two are both being charged with money laundering conspiracy and conspiracy to defraud the United States. They aren’t being charged with conducting the hack itself.
An attached statement of facts further alleged that Lichtenstein and Morgan had control of a crypto wallet that held the proceeds from the 2016 hack, as well as numerous other addresses. All told, the two were allegedly in control of 2,000 different addresses and their corresponding seed phrases, which were recorded on a spreadsheet saved to a cloud storage service used by Lichtenstein.
According to Cornell Law School’s Legal Information Institute, the first charge carries a maximum sentence of 20 years in prison, no more than twice the value of the property involved or both, while the second charge carries a maximum sentence of five years in prison or a fine, or both.
Depending on how the case proceeds, prosecutors can seek a lighter sentence or a judge can choose to impose a below-maximum sentence. Tuesday’s hearing was intended to determine whether the defendants would be held in pretrial detention.
Defense attorneys said the defendants have “been aware” of the investigation since at least this past November after one of their service providers received a subpoena, but had not fled ahead of their arrest. That was the reason the judge said she granted bail.
Prosecutors said during the hearing that the defendants had a file on their computer titled “passport_ideas.txt” with information about obtaining passports through darknet markets.
“Here’s what I’m thinking, on flight risk, the standard is a preponderance of the evidence. It’s clear that the defendants have means, have traveled, and that the charges are serious. I’m troubled by the cloud-based account about passports,” Freeman said during the hearing.
One of the defense attorneys said the file was meant to open financial accounts, rather than to facilitate a flight to safety.
A plastic bag full of cellphones, labeled “burner phones,” was found under the couple’s bed, prosecutors said in court.
As a condition of their bond, the defendants are allowed to spend up to $10,000 a month on living expenses but they are forbidden to drain their bank accounts or make any cryptocurrency transactions, the judge said.
Another condition: The couple’s cellphones and computers will be confiscated and they will be given a flip phone and one internet-connected device, monitored by pretrial services, so that they can access their bank accounts and email their lawyers.
A $4.5 Billion Crypto Crime Stars An NYC Couple, Stolen Bitcoin And Rap
Heather Morgan and Ilya Lichtenstein’s world of TED talk-style speeches and music videos collapsed around them when they were arrested over stolen Bitcoin worth $4.5 billion.
They are, to hear the feds tell it, a Bonnie and Clyde for the crypto age — made-for-TikTok personalities who broke bad, glamorously, right before their followers’ eyes.
She billed herself as “The Crocodile of Wall Street” and “Razzlekhan,” a surrealist artist and rapper with tattooed hands and, she boasted, more pizzazz than Genghis Khan.
He assumed a tamer persona: that of a “tech entrepreneur” and “occasional magician” who’d proposed, in a social media moment, via flashing billboards in Times Square.
At 7 a.m. on Tuesday, their blingy world of TED talk-style salons and music videos collapsed around them when they were arrested by federal law enforcement officials in New York City and accused of a crime that would’ve seemed preposterous in a halcyon, pre-cryptocurrency era: enriching themselves off a cache of stolen Bitcoin that is today worth about $4.5 billion.
Heather Morgan, 31, and her husband Ilya Lichtenstein, 34, were detained on charges of conspiring to launder 119,754 Bitcoin. The digital currency, the authorities say, came from the 2016 hack of Bitfinex, a cryptocurrency exchange owned and operated by iFinex Inc.
At an initial appearance in a Manhattan federal court on Tuesday evening, Morgan wore a white hooded sweatshirt, her long hair down. Lichtenstein, who goes by the nickname “Dutch,” showed up wearing jeans and a gray shirt. Neither wore shackles nor spoke publicly. Their lawyers — they have retained separate counsel — did the talking. The trial will eventually be held in Washington.
The judge granted both bail, setting a bond of $3 million for Morgan and asking her parents to post their home as security. For Lichtenstein, the amount was $5 million. The government initially asked the judge not to allow them to be released on bail. Each is facing the possibility of a 20-year prison sentence, so they have the motivation to run, a prosecutor told the judge.
Overnight, a judge in Washington granted an emergency request by the U.S. government to hold the couple in jail ahead of their trial. “The defendants are sophisticated cyber criminals and money launderers who present a serious risk of flight,” prosecutors said. While the majority of the stolen funds have been seized, Morgan and Lichtenstein control several other virtual currency addresses that hold about 7,506 Bitcoin, valued at more than $328 million, the government says.
None of this could have happened 20 years ago. Or 10. Or maybe even five. The couple’s audacious plan, as laid out by federal authorities, as well as the brazen lifestyle that plan supposedly afforded, seemed tailored to these times, and these times alone.
The Department of Justice says that the Bitcoin stolen during the 2016 hack was sent to a digital wallet controlled by Lichtenstein and then to one the couple controlled via a complex laundering scheme.
The cryptocurrency was worth $71 million when it was spirited away in 2016. Now the stash is worth $4.5 billion as Bitcoin prices have skyrocketed, of which $3.6 billion worth of tokens has been recovered by federal agents. The couple weren’t accused of doing the actual hacking.
Until Tuesday, Morgan and Lichtenstein lived lives made for social media. Even Lichtenstein’s 2019 proposal appeared to be aimed at boosting his future wife’s career as Razzlekhan, an artist specializing in collage, sculpture, painting and fashion design. In a Facebook post, Lichtenstein said he planned the marriage proposal around “a weird, creative multi-channel marketing campaign.”
That campaign featured posters and digital ads that “captured the essence of Razzlekhan: surreal, mysterious, creepy and sexy.” He proposed to Morgan as images of her face flashed across a digital billboard.
Morgan, for her part, also dropped singles and music videos on YouTube. In her 2019 song, “Versace Bedouin” — a number she characterized as an “anthem for misfits and weirdos” — she struts across cobbled streets in New York’s financial district and dons a shimmering gold jacket in front of a statue of George Washington.
As the “Crocodile of Wall Street,” she also rapped about investment strategies, calling herself a risk-loving moneymaker who was “sly as a gator.” She was an active TikToker too. In one of her videos, Morgan free-style rapped about investing in the meme stocks often discussed on the “Wall Street Bets” subreddit.
“My tendies going global / Bitcoin, Ethereum HODL!” Morgan rapped.
Morgan — who was born in Oregon and grew up in California — has foreign ties, having lived in Hong Kong and Egypt, the prosecutor said on Tuesday. Lichtenstein, a dual Russian and American citizen, moved to the U.S. at age 6, according to his lawyer. He grew up in the suburbs of Chicago and gained U.S. citizenship in 2002.
Tarun Chitra and Ruthie Nachmany, co-founders of the speaker series NYC Salon, on Tuesday recalled meeting Morgan in July 2019. Morgan told them she had just flown in first class from Japan and, over lunch at a French-style bistro downtown, pitched herself as a potential speaker.
Amazingly, Heather Morgan gave a talk at NYC Salon (an event I used to run with @ruthienachmany) in 2019
Here’s her talk: pic.twitter.com/RFovec0tek
— Tarun Chitra (@tarunchitra) February 8, 2022
“I was actually quite surprised she knew so much about cryptocurrencies,” Chitra recalled.
Morgan’s eventual talk, held at the Williamsburg Hotel, in hipster Brooklyn, was titled, “How to Social Engineer Your Way Into Anything.” She defined social engineering as “the act of manipulating someone into divulging information or taking a particular action.”
She told the crowd that she had sent 10,000 cold emails over the previous decade and had helped 720 companies improve email campaigns. The talk focused mostly on how to crash events, suggesting that would-be crashers bring cash for tips, wear a black T-shirt to appear as if they were security, and also bring layered outfits in case they need to change their look quickly.
Time to put practice into action I guess pic.twitter.com/2q6aybJe0p
— zerosnacks (@zerosnacks) February 8, 2022
Her presentation ended with another slide: “How Can You Socially Engineer Yourself OUT of a Bad Situation?” Below the line was an image of two cuffed hands behind bars.
Updated: 2-9-2022
Edward Snowden Raises Doubts Over Whether The Feds Are Telling The Whole Story On $4.5B Confiscated Bitcoin
Former CIA agent and whistleblower Edward Snowden has reacted to the arrest of two persons by the U.S. Department of Justice over an alleged conspiracy to launder $4.5 billion in stolen Bitcoin linked to the 2016 hack of cryptocurrency exchange Bitfinex.
What Happened: Snowden said on Twitter the DOJ seemed to be alleging that one of the arrested persons — a man named Ilya Lichtenstein — was the same person who had previously warned people on social media about the threat of hacks in the cryptocurrency space.
Snowden also noted tongue-in-cheek that the Cloud is a place “trivially accessible” to the U.S. government.
Ed, are you saying that the US Government isn’t telling the whole story?!?? I’m shocked. Shocked I say!
— Charles Hoskinson (@IOHK_Charles) February 9, 2022
Why It Matters: Lichtenstein’s Twitter profile says he is a Web 3.0 developer and serial entrepreneur.
A tweet by the Fintwit investor community noted that Lichtenstein is a tech entrepreneur and alumnus of the Silicon Valley accelerator program Y Combinator, while his wife Heather Morgan — who was also arrested — is a Forbes columnist.
Ilya Lichtenstein, a tech entrepreneur and Y combinator alum.
Heather Morgan, a Forbes columnist.
Today they were arrested for trying to launder billions in stolen crypto. They face up to 20 years in prison. pic.twitter.com/iUNRJDfVfL
— Fintwit (@fintwit_news) February 8, 2022
Snowden — a cryptocurrency enthusiast — revealed in November last year that he used Bitcoin to aid the process of leaking classified government documents in 2013.
The prominent privacy campaigner had also criticized Apple Inc.’s
Controversial plan to scan users’ iPhones for child sexual abuse material (CSAM), saying it marked the dawn of a “dark future.”
Updated: 2-9-2022
Bitfinex Hack Recovery Spurs Crypto Community Responses
As the Bitfinex hack recovery ensued, crypto figures across social media shared their thoughts, raised questions, and expressed disbelief.
On Feb. 1, there were movements of around $2.5 billion from the 2016 Bitfinex hack wallets. After reviewing the transactions, Cointelegraph reported that around 90,000 Bitcoin (BTC), worth $3.6 billion, consolidated into one wallet address. More than a week later, the hackers were caught.
The United States Department of Justice seized $3.6 billion in crypto and arrested two suspects connected to the 2016 hack. Alleged hackers Ilya Lichtenstein and Heather Morgan were apprehended after federal authorities exercised their ability to “follow the money through the blockchain” according to the DoJ.
While some of the funds were partially recovered in 2019, the most recent recovery shocked the community, as many didn’t think it would be possible to retrieve the funds after five years. Following this, the crypto community responded with diverse sentiments.
Emin Gün Sirer, founder of Ava Labs, thinks that Morgan, whose middle name is “Reyhan,” a common name in Turkey, may have a Turkish background, making her one of the richest Turks for some time. He also praised the authorities for recovering the funds.
Binance CEO Changpeng Zhao raised two questions related to the recovery of the funds. He tweeted, “Did Bitfinex lose or make money from the hack?” He added, “If they get the BTC back, how should they split that with LEO holders or the people who took a loss to accept LEO at the time of the hack, and then sold LEO?”
Crypto Banter host Ran Neuner may have an answer to this question. According to Neuner’s tweet, the hack may be the best trade ever made.
The Bitfinex hack was the best trade ever made.
119,000 Bitcoin was stolen in 2017. Value $76m.
Bitfinex repaid the victims the USD equivalent ($76m)over time through a recovery token.
Bitfinex get $3.6bn 5,5 years later.
Borrow $76m, repay it slowly , get $3,6bn. 5,5 years.
— Ran NeuNer (@cryptomanran) February 8, 2022
Jack Niewold, founder of Crypto Pragmatist, believes that this has enormous implications for BTC and LEO. “With selling methods like TWAP as well as OTC deals, it’s likely that it doesn’t affect the $BTC market too much, but $4 billion is a decent chunk,” he wrote.
Crypto Entrepreneur Anthony Pompliano Simply Expressed His Disbelief Over Who The Perpetrators Were:
One of the Bitfinex hackers was verified on Twitter and wrote articles for Forbes.
Unreal.
— Pomp (@APompliano) February 8, 2022
Meet The ‘Comedic Rapper’ Charged Over Bitfinex Hack Laundering
Heather Morgan, who goes by the rap name “Razzlekhan,” is a self-proclaimed serial entrepreneur and prolific writer — and she’s been charged with money laundering and conspiracy in relation to the 2016 Bitfinex hack.
New York resident Heather Morgan claims to be many things: “a serial entrepreneur, prolific writer, irreverent comedic rapper, and investor in B2B software companies with high growth potential.”
But her LinkedIn bio doesn’t mention anything about her alleged capability to help launder hacked cryptocurrency.
On Tuesday morning, United States Federal Bureau of Investigation agents arrested Morgan (or was it her rapper alter-ego Razzlekhan?) and her husband Ilya Lichtenstein for allegedly conspiring to launder crypto connected to the 2016 Bitfinex hack that saw 119,756 Bitcoin (BTC) drained from the crypto exchange.
The pair has strongly proclaimed their innocence during a New York court appearance on Tuesday and were released on multi-million-dollar bonds.
This whole thing is a psyop to make us look stupid for being hacked by the most inept criminals on earth
— nic carter ᵍᵐ (@nic__carter) February 8, 2022
The 119,756 BTC stolen from Bitfinex was worth $72 million in August 2016 but is now valued at more than $5.1 billion. Since the 2016 hack, individuals connected to the stolen coins have periodically moved small amounts of BTC in separate transactions, leaving the bulk of the funds untouched.
The U.S. Department of Justice reported that it had traced 25,000 BTC of these transferred funds to financial accounts controlled by Lichtenstein and Morgan. Special agents were then able to gain access to and seize more than 94,000 BTC — worth $3.6 billion at the time — from Morgan and Lichtenstein after a search warrant allowed them to view files containing private keys to the wallet.
According to the DoJ complaint, the pair is charged with laundering conspiracy and conspiracy to defraud the United States; however, they are not charged with carrying out the hack itself. The first charge can be punished by up to 20 years in jail and the second by five years.
Weird AF
While Lichtenstein appears to be your run-of-the-mill tech entrepreneur, Morgan has a prolific presence on social media where you can find TikToks showcasing art pieces inspired by her Synesthesia and her “WEIRD AF” music videos.
Heather Morgan, an individual alleged of laundering $4,500,000,000 in Bitcoin cryptocurrency, frequently uploaded videos of herself onto TikTok under the username “realrazzlekhan”. She raps, “following rules is for fools, instead I work the edge case with my tools” pic.twitter.com/bHbsf9QPGf
— vx-underground (@vxunderground) February 9, 2022
And you don’t want to miss those; they include gems like “I’m the grandmother you want to bang.” Morgan, who is in her early thirties, raps this while sitting in a bathtub full of glitter during her song “Versace Bedouin.” The question is, how does one go from being a rapper to the focus of an FBI hacking investigation?
According to her LinkedIn, she started her career working as an economist in Asia and the Middle East, including post-revolutionary Egypt following the Arab Spring.
Heather Morgan’s trash fire of a public LinkedIn page not only includes this deranged outfit choice but, “While traveling abroad, her favorite past times include haggling in informal markets and feeding crocodiles.” https://t.co/2ptack1FsK pic.twitter.com/Rkfq1Y2Zsw
— Sarah Solomon (@sarahsolfails) February 8, 2022
When she returned to California and eventually moved to Silicon Valley, she “became immersed in the tech startup scene.” In 2009, she founded a business-to-business company called SalesFolk, which specializes in cold emails.
I bet you’re all gonna think twice about your internet presence before you steal 4 billion dollars now huh
— CryptoFinally (@CryptoFinally) February 9, 2022
Although she didn’t get started with her rapping career until 2018, she was clearly practicing her lines for some time. The company’s slogan “be a goat, not a sheep!” has just the right balance of absurdity and cryptic philosophical reference that it’s a wonder it didn’t come straight from one of her tracks.
Amazingly, Heather Morgan gave a talk at NYC Salon (an event I used to run with @ruthienachmany) in 2019
Here’s her talk: pic.twitter.com/RFovec0tek
— Tarun Chitra (@tarunchitra) February 8, 2022
Meanwhile, she was also racking up some bylines on business and tech publications, like her December 2017 article “Should your company worry about getting blacklisted” and her seemingly well-informed June 2020 piece “Experts Share Tips To Protect Your Business From Cybercriminals,” both of which were published on Forbes. She also has a lengthy author profile for Inc Magazine.
How The Feds Tracked Down $3.6 Billion In Stolen Bitcoin
U.S. government said couple acted to break up crypto transactions to make them harder to track.
The U.S. government’s $3.6 billion bitcoin bust this week appears to reflect its success five years ago in disrupting some operations used by criminals to launder stolen funds.
The Justice Department said that it executed a search warrant last week and seized 94,636 bitcoins from the online wallets of two alleged money launderers, Heather Morgan, 31 years old, and her husband, Ilya Lichtenstein, 34.
The seized bitcoin allegedly comprised the bulk of about 120,000 bitcoins stolen in 2016 from the crypto exchange Bitfinex in a hack.
According to the federal government’s complaint, the couple moved the stolen funds through sites such as AlphaBay, which exist in what is called the dark web—a part of the internet accessible only through special browsers designed to hide identities—and services called mixers used to break up crypto transactions to make them harder to track.
They set up fictitious accounts with unhosted wallets and at about 10 other cryptocurrency exchanges, using numerous email addresses, according to the government.
The couple haven’t been charged with the original theft from Bitfinex, nor has anybody else so far been charged with that.
Attempts to reach Mr. Lichtenstein and Ms. Morgan for comment on Wednesday were unsuccessful. An attorney for the couple, Anirudh Bansal, declined to comment.
Mr. Bansal on Tuesday told a judge that his clients had been aware of the government’s investigation since November and hadn’t tried to flee the country.
On Tuesday, federal prosecutors announced that they had arrested Mr. Lichtenstein and Ms. Morgan and charged them with trying to launder the stolen funds.
In July 2017, the Justice Department seized and shut down AlphaBay, which the government said had 200,000 users buying and selling stolen identification documents, counterfeit goods, malware, firearms and other illicit goods.
Prosecutors didn’t detail in this week’s complaint exactly how they initially linked Ms. Morgan and Mr. Lichtenstein to the stolen bitcoins. According to Tom Robinson, co-founder of the crypto analytics firm Elliptic Enterprises Ltd., it is likely the government identified the two through the AlphaBay marketplace.
The complaint includes flow charts that show the stolen funds moving from Bitfinex through AlphaBay, and across the bitcoin blockchain to the various other accounts the couple had allegedly set up.
“This likely allowed [the government] to access AlphaBay’s internal transaction logs, which would enable them to trace the stolen Bitfinex funds,” Mr. Robinson said.
The Justice Department declined to comment.
The authorities said they traced the flow of funds through the unhosted wallets and across exchanges, according to the complaint, finding transactions that landed in accounts on exchanges that the two alleged launderers had in their real names. In one instance, according to the complaint, two of these accounts shared a login from the same location in New York.
About $2.9 million was moved from those accounts into bank accounts held by Mr. Lichtenstein and Ms. Morgan, prosecutors alleged.
The authorities also traced some of the funds through two exchanges and different accounts to transactions in 2020 with a gift-card service, the account for which was held in Mr. Lichtenstein’s real name, according to the complaint.
Mr. Lichtenstein and Ms. Morgan allegedly exchanged some of the bitcoin into other cryptocurrencies, according to the complaint, cashed some out via bitcoin ATMs and used the stolen funds to purchase nonfungible tokens, or NFTs. These digital collectibles have lately become another way crypto thieves launder digital money, the U.S. Treasury Department said last week in a report.
On Jan. 31 and Feb. 1, agents with the U.S. Justice Department executed a search warrant and seized the bitcoins from the online wallets, according to the complaint.
Federal authorities have had their own crypto wallets they use to hold seized assets.
Over the past decade the U.S. government has built up its infrastructure to track down crypto thefts, supplementing its traditional investigative methods with those aimed at the unregulated digital-asset market.
The federal government has contracts with analytics firms including Chainalysis Inc. and Elliptic to build software programs designed to track illicit funds across the blockchain. While the blockchain tracks every bitcoin transaction publicly, there are hundreds of millions of pseudonymous transactions for authorities to wade through.
Everyone Lays Claim To $3.6 Billion Bitcoin Bag From Hack
* Exchange Indicated It Expects To Receive The Recovered Funds
* Determination Of Who Is Entitled To Restitution May Take Years
Who walks away with the $3.6 billion in Bitcoin that the U.S. recovered from the Bitfinex currency exchange hack has become the cryptosphere’s favorite guessing game.
David Silver, a lawyer who specializes in financial and cryptocurrency-related fraud, said since the seizure was announced Tuesday he’s received dozens of calls from individuals saying they lost money in the 2016 online heist and they want to get their coins back.
Twitter has been whipped into a frenzy as well, with posters asking how to claim lost crypto. Justice Department officials said they plan to establish a court process for victims to reclaim the stolen digital assets, which have since surged in value.
Figuring out whom the crypto belongs to may not be simple, however. Bitfinex considers that it’s made investors whole, and said in a statement that it will “follow appropriate legal processes to establish our rights to a return of the stolen Bitcoin.” If Bitfinex and users start off on a collision course, the legal battle would likely be protracted.
“The world has changed dramatically since 2016, and everyone is going to lay claim to this newfound bag of Bitcoins,” Silver said.
Bitfinex, a unit of British Virgin Islands registered iFinex Inc., declined comment.
Does this get distributed to the people who were stolen from?
— Glenn Mack (@glenn_mcan) February 8, 2022
At the heart of Bitfinex’s argument is a long-ago token distribution. After the attack in August 2016, when a hacker made away with more than 119,000 Bitcoin, Bitfinex allocated losses of more than 30% to all customer accounts. It then created and credited BFX tokens to customers at a ratio of one for every $1 lost.
Within eight months, all holders had those tokens redeemed, or had exchanged them for iFinex capital stock. During that time, Bitcoin’s price had nearly doubled, according to Bloomberg data.
Bitfinex also created another coin named Recovery Right Token, or RRT, for holders that had converted their BFX tokens into iFinex shares. In case the stolen Bitcoins were ever recouped, recovered funds would be distributed to RRT holders, at up to $1 per RRT. There are currently 30 million RRT tokens outstanding, according to Bitfinex. That could lead to a reimbursement of up to $30 million.
Bitfinex plans to use a portion of at least 80% of the recovered net funds to buy up and destroy another token called Leo it issued in 2019 to beef up its coffers. The tokens traded at about $6.50 on Thursday after climbing as high as $8 on Feb. 8, according to CoinMarketCap pricing data.
“Bitfinex doesn’t owe me anything, they made me whole years ago,” said Erik Voorhees, an early crypto advocate who runs the ShapeShift cryptocurrency exchange.
Many customers disagree, particularly given Bitcoin’s appreciation from less than $600 in August 2016 to around $44,700. The tokens were worth about $71 million at the time of the hack, with the total amount now valued at about $4.5 billion.
“I think that’s ridiculous,” Alan Aronoff, a 52-year-old San Francisco resident, said in an interview. “That’s my Bitcoin that they took from my multisig wallet. I would like my Bitcoin back.” Aronoff doesn’t remember whether he signed away any rights to his stolen Bitcoin while accepting the Bitfinex reimbursement.
“They can have their equity back,” said Aronoff, who claims to own about $50,000 of “illiquid” Bitfinex stock. “I’ll take my Bitcoin, thank you very much.”
Much will depend on what the user agreement Bitfinex had people sign in 2016 said, said Kyle Roche, of Roche Freedman LLP, which is involved in litigation against Bitfinex. He’s already fielded inquiries from about 10 people about how to claim funds.
Another difficulty may lie even in verifying customer identities. Even today, anyone with an email address can simply open an account on Bitfinex, without any further verification for most basic functions.
“I don’t believe DoJ will turn $3.6 billion to an organization that can’t identify who this Bitcoin belongs to,” Silver said. iFinex had previously settled with the New York Attorney General over false claims related to its Tether product, the world’s most popular stablecoin.
Many observers point out that creditors of defunct crypto exchange Mt. Gox are still waiting to receive reimbursements under a plan that became final and binding in November. Mt. Gox closed in early 2014 after losing the coins of thousands of customers.
Who hacked the Bitfinex is still unclear as well, and could be pertinent to any distribution, Silver said. The married couple who were arrested on Feb. 8 were accused of money laundering, not stealing the coins.
Assuming the couple enters a guilty plea, the criminal process could take a year to play out, said Kellen Dwyer, former assistant U.S. Attorney who is now an Alston & Bird partner and co-leader of the firm’s national security and digital crimes team. The determination of who is entitled to restitution and how much could take years, he said.
“That process could take the heck of a long time,” Dwyer said. “It certainly could be multiple years before anybody sees any cash.”
Updated: 2-12-2022
FBI Warns Against Rising Crypto Romance Scams During Valentine’s Week
In 2021 alone, victims within the FBI San Francisco division’s territory lost more than $64 million to romance scams, compared to just over $35 million in 2020.
The United States Federal Bureau of Investigation (FBI) has issued a warning against the rise in romance scams in the San Francisco Bay Area, with the latest trend involving cryptocurrencies.
Just a few days ahead of Valentine’s day, the FBI San Francisco field office alerted the public about the rise in romance scams based on the complaints filed with the FBI’s Internet Crime Complaint Center (IC3).
A romance scam involves creating fake accounts and convincing unwary investors — both men and women — to transfer funds under the pretext of getting romantic. According to the information shared by the FBI:
“Victims within the FBI San Francisco division’s territory lost more than $64 million to romance scams compared to just over $35 million in 2020.”
In 2021 alone, the intelligence and security service logged 742 complaints within the Northern District of California, overshadowing the 720 and 526 complaints lodged back in 2020 and 2019 respectively.
Moreover, the IC3 received more than 23,000 complaints about confidence/romance scams in 2020 — with reported losses of more than $600 million. The FBI warning read:
“The FBI San Francisco has seen a rising trend in which romance scammers are persuading individuals to send money to invest or trade cryptocurrency.”
A typical romance scam starts off with gaining the trust of the victims who are then redirected to fraudulent platforms citing investment opportunities. While the scammers allow the investors to withdraw some profits from the initial trade as a way to prove credibility, the victims are coerced into investing more money or cryptocurrencies:
“When the victim is ready to withdraw funds again, the scammers create reasons why this cannot happen. The victim is informed additional taxes or fees need to be paid, or the minimum account balance has not been met to allow a withdrawal.”
However, the scammers typically stop responding after the victims refuse to add more funds. The FBI recommends victims of romance scams report the activities and contact their banks.
Some of the tips recommended by the FBI to avoid romance scams include not taking investment advice from purely online interactions, not disclosing financial information, staying away from promises of unrealistic profits and being “cautious of individuals who claim to have exclusive investment opportunities and urge you to act fast.”
Changpeng Zhao, the CEO of Binance recently alerted the crypto community against a “massive” SMS phishing scam targeting Binance customers.
There is a massive Phishing scam via SMS with a link to cancel withdrawals. It leads to a phishing website to harvest your credential as in the screenshot below.
NEVER click on links from SMS!
Always go to https://t.co/9rMMAmtCxH via a bookmark or type it in.
Stay #SAFU pic.twitter.com/erNwe90FN1
— CZ Binance (@cz_binance) February 4, 2022
As Cointelegraph reported, the scam involves sending users a text message with a link to cancel withdrawals, leading users to a fake website designed to harvest their login credentials. Zhao recommends manually typing the crypto exchange’s URL as a measure to counter the ongoing scams.
Updated: 2-13-2022
Love In The Time Of Crypto: Does Owning Cryptocurrency Make Daters More Desirable?
New findings suggest that adding “crypto” to a dating profile makes you more desirable, but the crypto community expresses concerns with online dating.
Cryptocurrency has become one of the most widely discussed topics of 2022. As such, it shouldn’t come as a surprise that mentioning “crypto” in an online dating profile may generate additional attention.
A new study from brokerage firm eToro found that 33% of Americans who were surveyed would be more likely to go on a date with someone who mentioned crypto assets in their online dating profile.
Out of the 2,000 adult residents in the United States between the ages of 18 and 99 surveyed, more than 40% of men and 25% of women indicated that their interest in a potential date is stronger when crypto is written on a dating profile.
Crypto: What’s love got to do with it?
Callie Cox, U.S. investment analyst at eToro, told Cointelegraph that the findings from eToro’s inaugural “Crypto & Culture” survey demonstrate the crossover between money, culture and identity. “We talked a lot about identity in the survey and how this has a strong place in the crypto community. The genesis of this campaign was to better understand how people think of big life projects and finding that perfect partner,” said Cox.
With this in mind, Cox explained that one of the most notable findings in the report was that 33% of respondents would be open to dating someone who mentioned crypto in their profile. “This shows there is a connection between money, love and identity when people look for a partner on a dating app,” she remarked.
Cox added that it was also interesting to see that nearly 74% of survey respondents noted they would likely go on a second date with a person who paid the first date’s bill in Bitcoin (BTC). “We also wanted to test the environment to see how people felt about using crypto as a currency. We were surprised to see this percentage so high, which also speaks to identity.”
While these findings suggest that publicly open crypto holders and enthusiasts may attract more attention across dating apps, Cox shared that Millennials and Gen Z respondents were the majority of people who participated in the survey.
“Everyone had to self-identify and most of the respondents were from the younger generation,” she said. Regarding using crypto as a currency, Cox further mentioned that eToro’s findings show that paying a bill in Bitcoin is of greater interest to men than to women.
The Crypto Community And Online Dating
Although eToro’s survey suggests that crypto terminology may make daters more desirable, some crypto community members find mentioning the trait to be a double-edged sword.
For instance, Hailey Lennon, law partner at Anderson Kill and founder of Crypto Connect, told Cointelegraph that she didn’t initially have “Bitcoin” anywhere in her online dating profile, but that she eventually added it since the digital asset has been a long-time passion of hers.
While Lennon didn’t notice an increase in responses to her profile from adding Bitcoin, she’s had some matches that have piqued her interest due to commonalities:
“There is a commonality between people that are interested in Bitcoin. For example, if I post a photo in a Bitcoin hat, that will likely attract others interested in the space. I’ve also jokingly tweeted before when I find someone with ‘Bitcoin’ mentioned in their dating profile that I’ve found my soulmate. But, it really does show a common interest and that we can connect and talk about a common passion.”
However, Lennon also pointed out that including crypto terminology in your online dating profile can backfire. “Sometimes I will reframe things and say that I’m an attorney in financial technology, without mentioning Bitcoin or cryptocurrency to not make the entire conversation become about Bitcoin and what I do for a living.
You also have those people who still associate cryptocurrency with this false narrative of it being used only for criminal activity and money laundering, so it can be interesting to try to explain how you are a lawyer in the digital asset space,” said Lennon.
Moreover, while Lennon finds eToro’s survey results to be interesting, she noted that many people in the crypto community focus so much on digital assets in their day-to-day lives that they may want to have non-crypto-focused conversations in romantic settings.
“Sometimes a date can only consist of wanting to talk about Bitcoin and how it works when people find out what you do for a living. That can get kind of old and take the romance/fun out of the date.”
Echoing this, Ivan Perez, owner at Multiplied — a crypto-focused PR firm — told Cointelegraph that since adding “investing and working in crypto” to his online dating profiles, he’s connected three times with women who also work in the cryptocurrency space.
While Perez mentioned that the commonality can be an added plus, he shared that each date he went on with someone in the crypto sector felt more like work than pleasure. “All we did was talk about crypto,” expressed Perez.
Perez further explained that having “crypto” in his online dating profile has also attracted the wrong attention at times:
“Some girls will like my profile and then start off by saying ‘you work in crypto, how cool.’ Then, when we go on a date, the first 10–20 minutes usually focus on how crypto works and what I do. Some women focus on the money aspect only. I’ve had many experiences where I go on dates and crypto becomes the whole topic of conversation.”
In turn, Perez explained that working in crypto can make dating frustrating. “Now that NFTs are generating more mainstream attention, I’ve had women at conferences start to look for crypto-rich individuals. This is frustrating because it puts you in a place of doubt. Are these women interested in me or the industry I work in,” questioned Perez.
From a woman’s perspective, adding crypto to their online dating profile can also result in challenges. Jessica Salama, community lead at GoodDollar Foundation — a non-profit initiative focused on financial education in digital assets — told Cointelegraph that while she thinks adding crypto to her profile has increased her desirability, it hasn’t necessarily been for the right reasons:
“Yes, I got more matches, but then came the ‘mansplainers.’ Working in Web3 — which still very much feels like a man’s world — has no shortages of challenges. Dodging mansplainers in and out of work and on Tinder is exhausting.”
According to Salama, “mansplainers” are patronizing men who assume that women don’t understand the basics of the blockchain industry. Unfortunately, the crypto space is still largely male-dominated and can, therefore, be frustrating for some women. On the upside, Salama is aware of the fact that she is part of a transformative industry, which can also be beneficial in terms of finding romance.
“I met a great guy at a friend’s dinner who is a crypto day trader and took a genuine interest and respect in my work and passion for Web3. We spent the whole night talking. I can’t say it was love since the relationship slowly fizzled out (we forked?) but he gave me that extra push to speak up for and own what I do and love,” explained Salama.
NFTs: Personalized Love For The Digital Age
Crypto and dating aside, eToro’s study also found that 8% of respondents would be interested in receiving a nonfungible token (NFT) as a Valentine’s Day gift this year. According to Cox, this statistic wasn’t much of a surprise given the rise of the NFT market.
Yet, Cox noted that this finding was interesting since it demonstrates that Millennials and Gen Z’s value identity-themed products. “The younger generation wants to own something in real life or in the Metaverse and that shows who they are — NFTs represent this.”
As a result, a number of identity-themed Valentine’s Day NFTs are being offered this year. For example, jewelry designer MYKA has created a limited edition NFT collection consisting of digital drawings on three of their best selling jewelry pieces.
Ronnie Elgavish, vice president of global marketing at MYKA, told Cointelegraph that he believes more couples will give NFTs this Valentine’s Day due to the rise of the Metaverse and desire for a digital identity.
Ivan Sokolov, founder of Mintmade — a platform that offers programmable templates for NFTs — agrees with Elgavish. He told Cointelegraph that he thinks more couples will give tokenized Valentine’s Day cards this year.
Sokolov said that Mintmade allows users to mint a pair of custom NFTs with their and their partner’s names on them. “These NFTs are user generated, meaning it is created by the buyer. The buyer simply enters two names on the platform and can mint the NFT with these names on it,” explained Sokolov.
In addition to NFT Valentine’s Day gifts, eToro’s study found that nearly 20% of singles would be more interested in dating someone if they used an NFT as a profile picture on a social platform or dating site. “So, if your gift of an NFT doesn’t pan out, you can always use it to find a new date for March,” joked Cox.
Crypto May Be Sexy, But Safety Concerns Remain
Although eToro’s findings suggest that crypto terminology and features may make online dating profiles more attractive, safety is a major factor that must also be considered when publicly mentioning cryptocurrency. Keeping a user’s crypto safe has become a main concern as the industry goes mainstream.
To put this in perspective, a recent report from blockchain analysis firm Chainalysis found that the intersection between cryptocurrency and crime grew to become a $14 billion industry in 2021.
Justin Maile, manager of investigations at Chainalysis, told Cointelegraph that it’s best not to flaunt that you own crypto — especially investing or any holdings — on your dating profile to avoid making yourself a target.
Maile added that scams are not confined to dating apps. “Meta (Facebook), Instagram, LinkedIn, Quora, Discord, WeChat and others are all platforms scammers use to find their victims,” he said.
Maile further noted that while he believes it’s okay to publicly mention an interest in crypto, additional details shouldn’t be revealed. “Similar to how you wouldn’t publicly share that you have a savings account and how much is in it, it’s safest to not publicly share that you own crypto to avoid making yourself a target.”
Moreover, Cox remarked that eToro’s findings demonstrate that adding the term “crypto” to a dating profile helps hone in on a user’s identity, but that online daters must be wise and prudent about what they reveal. “There are good and bad actors everywhere, so individuals must be careful whether or not ‘crypto’ is mentioned in their profiles.”
Updated: 2-23-2022
Why White Hat Hackers Are Vital To The Crypto Ecosystem
Jay Freeman stopped a potential $750 million vulnerability from being exploited on three of Ethereum’s layer 2 networks.
This past weekend at ETHDenver, Jay Freeman took the stage to highlight his nearly billion-dollar bug discovery within the core code of Optimism, Boba and Metis, which he dubbed “Unbridled Optimism.”
Freeman has a history of software development and hacking, notably playing a critical role in the development of software for jailbreaking iOS. His experience has proven to be priceless within the Wild West, open-source crypto industry.
Just two weeks ago a smart contract vulnerability left the Wormhole bridge with a $350 million hole to repair – and that wasn’t even the largest exploit in recent history.
However, Freeman mentioned that bridge exploits are often found quickly as they are used often and watched over constantly by the teams responsible for maintaining them.
During the first week of February, Freeman discovered a critical bug within Optimism’s virtual machine – one that developers might not have been ready to patch quite as quickly. The bug was rooted in Optimism’s selfdestruct function that allows contracts to be destroyed and sends any remaining ether balance to a designated address.
It sounds dangerous, so why do blockchains contain the selfdestruct function? The function allows for obsolete or dangerous contracts to be removed from the chain while returning the ether balance to the rightful owner.
Unless there is a bug, of course.
Optimism’s selfdestruct function returned the ether balance to the designated address without ever burning the balance within a contract. According to Freeman, “This means that, when a contract self-destructs its balance is BOTH given to the beneficiary AND ALSO KEPT.” If attackers were able to successfully call the contract, they could create a loop that doubles their OETH balance until noticed and patched by Optimism developers.
Freeman noted that he was not the first person to find the bug after scanning previous selfdestruct calls on Optimism and tracking one wallet back to an employee of Etherscan. The employee had found and tested the bug, but apparently hadn’t understood the severity of the situation and let it be.
The vulnerability had gotten worse over time as more funds were bridged to Optimism and other layer 2 systems copied the code Optimism had put in place. Layer 2s are companion networks connected but functionally separate from the base layer.
Consequently, Freeman noted, had he not found the bug, a minting vulnerability would have allowed an attacker to double their funds every time the selfdestruct function was called on Boba and Metis as well.
White Hats And DeFi
Even if the Optimism team had noticed and temporarily paused bridge transactions via the sequencer during a theoretical attack, an attacker could have still wreaked havoc on layer 2 decentralized finance (DeFi). Using the falsely minted OETH, any attacker would be able to drain decentralized exchanges and exploit lending platforms with useless collateral.
The exploit would have likely caused irreparable damage within the Ethereum ecosystem and layer 2 users could have had all of their funds rendered useless, with no assets left on the other end of the bridge. Combined, Optimism, Boba and Metis had around $750 million locked in DeFi the day the vulnerability was reported, almost all of which was at risk.
The Need For Friendly Adversarialism
Decentralized finance continues to be a vulnerable industry with anonymous founders, open-source code and billions of dollars looking to take on risk. This enormous amount of capital has created an incentive system aligned with teams that build fast and release tokens.
Conversely, caution and professionalism are a lot less exciting to traders and investors. The world economy has seen over and over again the effect of incessant risk taking, even though the market eventually punishes shortcuts. There is no reason to think this same outcome won’t continue to play out in crypto and decentralized finance, with only the most meticulous protocols coming out alive in the end.
Freeman has also contemplated where the middle ground between “Code is Law” and third-party trust falls. He raised the point that bug bounties are essential in incentivizing good actors to seek out and find vulnerabilities. By setting the reward for being a good actor on a similar scale as the payout for being a bad actor, that scale suddenly tilts the incentives toward white hatting.
As Freedman put it, this sort of “friendly adversarialism” can encourage ecosystem participants to be more open, honest and even pessimistic about new ideas.
That pessimism is key. Today, the environment is perhaps overly optimistic, getting investors and DeFi users excited about protocols that could never work or might even be dangerous. This lack of oversight, combined with the nature of open-source code, creates the perfect environment for hackers and scammers, an issue much of the crypto industry does not seem ready to admit.
Security Firms Seek To Make It More Difficult For Scammers To Get Away With DeFi Project Hacks
While projects cannot wholly prevent bad actors from infiltrating the DeFi realm, security specialists say there are ways to deter such practices.
The rise of community-oriented blockchain security companies may be making it more difficult for alleged bad actors to get away without a trace.
Early Wednesday, CertiK issued a community alert regarding Flurry Finance, where its smart contracts were allegedly breached by hackers, leading to $293,000 worth of funds being stolen.
Shortly after the incident, CertiK published the wallet addresses of the alleged perpetrator, the address of the malicious token contract, and a PancakeSwap pair address allegedly involved in the attack, leading to a warning issued on BscScan. While the firm audited the project’s smart contracts, it appears that the exploit was the result of external dependencies.
#CommunityAlert @FlurryFi’s Vault contracts were attacked leading to around $293K worth of assets being stolen from Vault contracts
Incident Analysis
— CertiK Security Leaderboard (@CertiKCommunity) February 22, 2022
In another instance, on Feb. 20, social media users reported that Avalanche (AVAX)-based project Atom Protocol allegedly turned into a rug-pull hours after launch, with a screenshot from the project’s alleged Twitter account (now deleted) stating:
“There is a problem/mistake in the contracts; we can’t do anything. So we have to close the project, sorry.”
In a report published Tuesday, Assure DeFi, a verification company providing Know Your Customer, or KYC, as well as checks on project developers, lists one French national on file as responsible for Atom Protocol. The firm conducts such checks and then creates publicly viewable compliance content.
Through a statement to Cointelegraph, Assure DeFi explained that it’s important to understand that knowing someone’s name, address, nationality, etc., does not prevent them from committing a crime. But, Assure DeFi reps elaborated:
“It does, however, create an accountability path to pursue legal recourse against bad actors…which is the value that the Assure DeFi KYC Verification process provides.”
The report lists $87,440 being stolen via the alleged rug pull and estimates that the number of “injured parties” surpasses 1,000. According to Assure DeFi, victims are urged to contact Binance support asking to freeze the alleged perpetrator’s wallet and contact French law enforcement authorities regarding the alleged crime.
We believe that many people are still misunderstanding the role of KYC/verification.
KYC is a deterrent and not a scam prevention and if anyone says otherwise they are misleading you.
The real value of KYC is having a validated real-world identity behind a project..
— Assure DeFi (@AssureDefi) February 20, 2022
Updated: 2-24-2022
IRA Financial ‘Swatted’ At Time Of $36M Crypto Hack, Police Officer Tells Victim
The detail adds another layer of intrigue to the seemingly inexplicable hack of IRA Financial Trust, an institutional partner of the Gemini exchange.
IRA Financial Trust was being “swatted” at the time the retirement investment company was hacked for $36 million worth of cryptocurrency, according to a local police account obtained by CoinDesk.
A detective at the Sioux Falls police department recounted the chain of events to a victim of the hack in a Feb. 15 voicemail reviewed by CoinDesk. Officers responded to reports of an alleged “robbery” in progress at IRA Financial Trust’s offices in the South Dakota city on the afternoon of Feb. 8, the detective said.
Police officers quickly determined the robbery call was bogus, the detective said. He described the incident as “swatting”: the practice of tricking police into responding to a nonexistent crisis.
There was a robbery, however – but it was happening in cyberspace, not the Midwest.
“What we were then informed of was that once the employees returned to their desks, after, like, while this ‘robbery’ was taking place or whatever, once they got back to their desks, they all found that customers’ accounts had been hacked into and that money was actively being taken at that time,” the officer said in the voicemail. He did not immediately respond to a request for comment from CoinDesk.
He said in the voicemail that IRA Financial soon managed to stop the money drain. “But by that point roughly a number of minutes had passed and a lot of damage had been done. They reported hundreds of victims as a result of this.”
The officer said he was sharing this information with the victim because “it doesn’t appear that [IRA Financial is] telling their customers very much.”
In a statement, IRA Financial Trust said it was “aware” of the law enforcement’s recounting of events.
“Coordinated efforts like these emphasize the growing sophistication of cybercrime that make cyber threats both difficult to prevent and challenging to recover from,” the company said. “We are currently dedicating our attention and efforts to our active investigation and the potential recovery of funds through civil and law enforcement resources. To preserve the integrity of our investigation, we cannot provide further comment or details at this time.”
A Baffling Break-In
The detail adds another layer of intrigue to the seemingly inexplicable hack of IRA Financial Trust, an institutional partner of the Gemini exchange servicing retirement-minded crypto investors. Gemini, a $7 billion company that touts its security chops, has denied responsibility, instead blaming IRA Financial for the loss of millions of dollars in crypto.
Victims who spoke with CoinDesk said the hack should have been impossible. They described imposing strict controls on their Gemini accounts, including withdrawal address whitelisting, two-factor authentication, email notifications and other steps that they thought would stymie hackers.
A source close to Gemini previously said the company makes those safeguards available to institutional customers in order to prevent such incidents. It is unclear how those protocols were compromised on Feb. 8.
Updated: 2-25-2022
Crypto Scammers Have A New Target: Dating Apps
The man from the dating app Hinge checked all of Tho Vu’s boxes.
He was a boyishly handsome architect from China, staying in Maryland on a long-term assignment. They had never met in person — he was still waiting to get his COVID-19 booster shot, he said — but they had texted back and forth for months, and she’d developed a serious crush.
He called her his “little sweetheart” and told her that he was planning to take her to China to meet his family when the pandemic was over.
So when the man, who went by the name Ze Zhao, told Vu, who works in customer service for a security company, that he could help her make money by trading Bitcoin and other cryptocurrencies, she was intrigued.
“I’d heard a lot about crypto in the news,” she said. “I’m a curious person, and he actually was very knowledgeable about the whole trading process.”
But the man wasn’t trying to help Vu invest her money. He was entrapping her in an increasingly popular type of financial scam, she said, one that combines the age-old allure of romance with the newer temptation of overnight cryptocurrency riches.
Within weeks, Vu, 33, had sent more than $300,000 worth of Bitcoin, nearly her entire life savings, to an address that Zhao had told her was connected to an account on the Hong Kong cryptocurrency exchange OSL. The website looked legitimate, offered 24/7 online customer support and had even been updated to show Vu’s balance changing as the price of Bitcoin rose and fell.
Zhao — whose real name could not be verified — had promised her that her crypto investments would help them get married and start a life together.
Niki Hutchinson, who said she was targeted by scammers on a dating app , swindling both her and her father out of hundreds of thousands of dollars, in Chapel Hill, Tenn., Feb. 13, 2022. Romance scams — the term for online scams that involve feigning romantic interest to gain a victim’s trust — have increased in the pandemic.
“We can make more money on top of OSL and go on a honeymoon,” he said, according to a screenshot of their texts that Vu shared with me.
But there was no honeymoon, and no crypto windfall. Instead of going into an exchange account, Vu’s money went into the scammer’s digital wallet, and he vanished.
Now, she is struggling to make sense of what happened.
“I thought I knew him,” she said. “Everything was a lie.”
Romance scams — the term for online scams that involve feigning romantic interest to gain a victim’s trust — have increased in the pandemic. So have crypto prices. That has made crypto a useful entry point for criminals looking to part victims from their savings.
About 56,000 romance scams, totaling $139 million in losses, were reported to the Federal Trade Commission last year, according to agency data. That is nearly twice as many reports as the agency received the previous year.
In a bulletin last fall, the FBI’s Oregon office warned that crypto dating scams were emerging as a major category of cybercrime, with more than 1,800 reported cases in the first seven months of the year.
Experts believe this particular type of scam originated in China before spreading to the United States and Europe. Its Chinese name translates roughly as “pig butchering” — a reference to the way that victims are “fattened up” with flattery and romance before being scammed.
Jan Santiago, the deputy director of the Global Anti-Scam Organization, a nonprofit that represents victims of online cryptocurrency scams, said that unlike typical romance scams — which generally target older, less tech-savvy adults — these scammers appear to be going after younger and more educated women on dating apps like Tinder, Bumble and Hinge.
“It’s mostly millennials who are getting scammed,” Santiago said.
Jane Lee, a researcher at the online fraud-prevention firm Sift, began looking into crypto dating scams last year. She signed up for several popular dating apps and quickly matched with men who tried to offer her investing advice.
“People are lonely from the pandemic, and crypto is super hot right now,” she said. “The combination of the two has really made this a successful scam.”
Lee, whose company works with several dating apps to prevent fraud, said that these scammers typically tried to move the conversation off a dating app and onto WhatsApp — where messages are encrypted and harder for companies or law enforcement agencies to track.
From there, the scammer bombards the victim with flirtatious messages until turning the conversation to cryptocurrency. The scammer, posing as a successful crypto trader, offers to show the victim how to invest his or her money for fast, low-risk gains.
Then, Lee said, the scammer helps the victim buy cryptocurrency on a legitimate site, like Coinbase or Crypto.com, and provides instructions for transferring it to a fake cryptocurrency exchange.
The victim’s money appears on the exchange’s website, and he or she starts “investing” it in various crypto assets, under the scammer’s guidance, before the scammer ultimately absconds with the money.
What makes this particular scam so insidious is how much more elaborate it is than the Nigerian prince scams of yore. Some victims have described being directed to realistic-looking websites with charts and tickers showing the prices of various crypto assets.
The names and addresses of the fake exchanges are changed frequently, and victims are often allowed to withdraw small amounts of money early on, making them more comfortable depositing larger sums later.
“This kind of scam is quite labor-intensive and time-consuming,” said Santiago, of the Global Anti-Scam Organization. “They’re very meticulous in their social engineering.”
Cryptocurrencies are particularly useful to scammers, experts say, because of the relative privacy they offer. Bitcoin transactions are publicly visible, but because digital wallets can be set up anonymously, technically sophisticated criminals can obscure the trail of money.
And because there is no central bank or deposit insurance to make victims whole, stolen money usually can’t be recovered.
Niki Hutchinson, a 24-year-old social media producer from Tennessee, fell victim to a crypto romance scam last year. She was visiting a friend in California when she matched on Hinge with a man named Hao, who said he lived nearby and worked in the clothing business.
The two continued texting on WhatsApp for more than a month after she returned home. She told Hao that she was adopted from China; he told her that he was Chinese, too, and that he hailed from the same province as her birth family.
He started calling her “sister” and joking that he was her long-lost brother. (They video-chatted once, she said — but Hao only partly showed his face and hung up quickly.)
“I thought he was shy,” she said.
Hutchinson had just inherited nearly $300,000 from the sale of her childhood home, after her mother died. Hao suggested that she invest that money in cryptocurrency.
“I want to teach you to invest in cryptocurrency when you are free, bring some changes to your life and bring an extra income to your life,” he texted her, according to a screenshot of the exchange.
Eventually she agreed, sending a small amount of crypto to the wallet address he gave her, which he said was connected to an account on a crypto exchange named ICAC. Then — when the money appeared on ICAC’s website — she sent more.
She couldn’t believe how easy it had been to make money, just by following Hao’s advice. Eventually, when she’d invested her entire savings, she took out a loan and kept investing more.
In December, Hutchinson started to get suspicious when she tried to withdraw money from her account. The transaction failed, and a customer service agent for ICAC told her that her account would be frozen unless she paid hundreds of thousands of dollars in taxes. Her chat with Hao went silent.
“I was like, oh, God, what have I done?” she said.
Now, Hutchinson is trying to pull her life back together. She and her father live in their RV — one of the few assets they have left — and she is working with police in Florida to try to track down her scammer.
Hutchinson doesn’t expect to get her money back, but she hopes that other people will be more cautious about strangers who promise to help them invest in cryptocurrency.
“You hear all these stories about people becoming millionaires,” she said. “It just felt like, oh, well, cryptocurrency’s the new trend, and I need to get in.”
Updated: 3-1-2022
Nvidia Hackers Are Selling Software To Bypass Ethereum Hashrate Limiter
The hacker group said it’s selling a customized driver that could help miners get around the software installed on Nvidia’s high-end gaming cards.
The hacker group LAPSUS$, which claims to be responsible for a recent hack of chipmaker Nvidia (NVDA) in which it stole 1 terabyte of internal information, said it is now selling software that can bypass the Ethereum Lite Hash Rate (LHR) limiter that Nvidia had implemented to prevent miners from competing with gamers for its graphics cards.
“We decided to help [the] mining and gaming community, we want Nvidia to push an update for all [GeoForce RTX 30-series] firmware that remove every lhr limitations,” the group said in its public Telegram chat. It noted that it has a customized version of a driver and firmware that could bypass the limiter.
For its part, Nvidia said in an emailed statement to CoinDesk that it became aware of a cybersecurity incident on Feb. 23 that affected its IT resources. In response, it hardened its network, engaged cybersecurity incident response experts and notified law enforcement.
“We are aware that the threat actor took employee credentials and some Nvidia proprietary information from our systems and has begun leaking it online,” a representative from Nvidia said.
Nvidia is working to analyze the breached information and doesn’t expect any disruption to its business, the company said.
Last year, Nvidia introduced “hashrate limiters” for its flagship GeForce GPUs to keep more products available for its core gamers. In a recent Wall Street conference, the chipmaker said that almost all of its Ampere-based products will incorporate a hashrate limiter to deter crypto miners from using them for mining.
To further keep its product lines separate, Nvidia also introduced a crypto-specific mining chip last year, called Cryptocurrency Mining Processors (CMP). Nvidia said its CMP-related revenue fell to $24 million in its fiscal fourth quarter ended Jan. 30, a 77% decline from $105 million in the previous quarter.
They Were Jailed For Hacking An Exchange. Blockchain Data Cleared Them
How blockchain forensics helped two suspects in a cyber crime prove their innocence.
Cryptocurrency hacks usually make the news. So do arrests of alleged perpetrators. The recent seizure of around $3.6 billion worth of bitcoin along with the highly publicized arrest of two individuals tied to a 2016 attack on the crypto exchange Bitfinex by federal officials is but one example.
Crypto analytics played a key role in helping federal officials identify the alleged Bitfinex launderers. In another case, blockchain analysis may have helped clear the names of two suspects in an exchange hack.
In November 2020, two Venezuelan software developers, José Manuel Osorio Mendoza and Kelvin Jonathan Diaz, were detained by local authorities under suspicion of stealing around $1 million worth of bitcoin from a local cryptocurrency exchange called Bancar.
Mendoza and Diaz maintained their innocence but remained doubtful they would be able to prove that in court.
“There is a lot of technological ignorance in my country, despite being an economy open to crypto … Even though we worked at a technology enterprise, we felt this doubt about how we could explain something that was so new and so difficult to understand” to a local judge, Mendoza said.
At the time of their detainment, Mendoza and Diaz worked at POSINT, a Venezuelan software development company that had previously provided services to Bancar. Eager to clear his company’s and colleagues’ names, Danny Penagos, chief operations officer at POSINT, hired blockchain analytics company CipherBlade to independently investigate the attack on Bancar.
CipherBlade’s resulting report, reviewed by CoinDesk, tells a complex story of security vulnerabilities and scapegoating while tracking the stolen funds from Bancar through recently blacklisted Suex.io all the way to Russia. The report shows that the stolen bitcoin eventually ended up on leading digital asset exchange Binance.
The Venezuelan court agreed to take a look at CipherBlade’s report. Based on the investigation’s findings, in January 2021, over a month after the developer duo were detained, the court granted Mendoza and Diaz conditional freedom. In August 2021, the court officially dismissed all charges against them, according to an official document obtained by CoinDesk.
While illicit crypto transaction volumes fell by more than half from 2019 to 2020, it’s still a multibillion-dollar market. And the demand for blockchain intelligence services to track illicit transactions is booming.
Blockchain intelligence firm Chainalysis has multimillion-dollar contracts with the U.S. government, and last September, global payments giant Mastercard agreed to buy CipherTrace, a firm that scans blockchains for illicit activity.
Miguel Alonso Torres, a senior investigator at CipherBlade (not to be confused with the Mastercard acquisition), said his firm works on a range of cases from hacks and theft to the occasional divorce case where a spouse was suspected of not disclosing their total crypto holdings.
But clearing two suspects was a first for Torres.
“Having someone in prison and being asked to investigate a hack just to be able to prove to the court that they were in fact innocent, that’s absolutely unique. I never had a case like this one,” said Torres.
The Exchange Hack
It all started when Bancar hired POSINT in 2018 to help build its cryptocurrency exchange.
In 2018, Venezuela’s president, Nicolas Maduro, launched the petro, the country’s controversial government-issued digital currency backed by a portion of Venezuela’s oil reserves. His aggressive tactics to force the petro’s adoption ranged from ordering a number of state-owned companies to convert a part of their sales to petro to reportedly requiring citizens to pay for new passports with petro.
In October 2018, local media outlets began to report that Maduro had approved six local cryptocurrency exchanges to sell petro.
According to the reports, Bancar was one of the six exchanges approved by Maduro. Penagos said that following Bancar’s approval, POSINT was hired to build out the firm’s trading platform. He added that after completing the work, POSINT handed the source code over to Bancar.
Bancar didn’t respond to multiple requests for comment.
A year later, 103.99 BTC worth around $1 million disappeared from the Bancar exchange in a cyberattack, according to the CipherBlade report. The bitcoin was stolen in five separate transactions that occurred on two different days – three transactions on Sept. 4, 2019, and the rest on Sept. 7, 2019.
According to Penagos, Bancar immediately suspected POSINT, the company that had built the software Bancar was using, of the theft. Penagos, meanwhile, ran a simple trace and found the stolen bitcoin had ended up on Binance.
“I think a professional attacker or hacker would not deposit that amount of money in a big exchange like Binance,” Penagos said.
Penagos says he notified Bancar by email and asked it to consider hiring CipherBlade to investigate the hack or contact Binance to try to recover the funds.
Then, a year later, in December 2020, local media reported that Venezuelan authorities had detained Mendoza and Diaz as the suspects behind the attack. At the time, Mendoza was the chief technology officer at POSINT and Diaz was a senior developer at the company, Penagos said.
“We were confused,” Diaz said, recalling the first days he was detained.
Local news outlets and international crypto news sites published stories on their detainment.
“After circumventing the platform’s security, [Mendoza and Diaz] allegedly proceeded to make bitcoin and fiat transfers to various accounts associated with them,” crypto news platform Decrypt wrote.
Meanwhile, Mendoza and Diaz weren’t sure how to prove their innocence.
“While we were detained, doubts kept increasing,” Mendoza said.
All POSINT had to do was prove the two couldn’t have stolen the funds, but that wasn’t easy.
“Cryptocurrency is uniquely transparent as all transactions are recorded on a public, immutable, permanent blockchain ledger,” Gurvais Grigg, global public sector chief technology officer at Chainalysis, said in an email. “The challenge is that the blockchain is not human-readable. It’s difficult to know what services are behind transactions on the blockchain because they are pseudonymous.”
After his colleagues were detained, Penagos said he tried to contact Binance himself but received no reply. Failing that, he finally turned to CipherBlade.
“When the investigation started, we finally started to feel relaxed,” Mendoza said.
Tracking The Flow Of Funds
Within a month of starting its investigation, CipherBlade was able to map out the trajectory of the stolen Bancar funds in considerable detail.
“When you look at the flow of funds, you know there were some obfuscation techniques that weren’t executed particularly well,” said Paul Sibenik, lead case manager at CipherBlade.
Once the 103.99 BTC were lifted from the exchange in five separate transactions, the perpetrator deposited the stolen bitcoin to two addresses, or virtual locations denoted by a string of numbers and letters where the bitcoin can be sent.
Then, the stolen bitcoin eventually converged to an address on Binance: 1ECeZBxCVJ8Wm2JSN3Cyc6rge2gnvD3W5K.
But something wasn’t adding up.
“We initially saw all funds go to Binance,” Sibenik said. “But we could tell that the address that the funds went to was not a personal account at Binance that belonged to the hacker. It was some type of service.”
According to the CipherBlade report, Binance informed investigators that the address was associated with Suex.io, a Moscow-based firm that offered over-the-counter (OTC) trading services.
That meant that Bancar’s stolen bitcoin first ended up in two addresses belonging to the perpetrator, and the perpetrator then used Suex.io to convert the bitcoin to another asset. In other words, the perpetrator used Suex.io’s OTC service to launder the stolen bitcoin. Suex.io then sent the stolen bitcoin to its account at Binance.
CipherBlade tried to request information from Suex.io but Sibenik and Torres said the Russian firm wasn’t cooperative.
“The first thing is that anyone that was a potential client of Suex.io at the time knew that they didn’t have requirements at all,” Torres said. “They didn’t care who they were dealing with or where the funds came from. I respect pseudonymity and privacy a lot but there are also ethical values. This case was critical. There were two people in prison.”
According to the report, Binance helped CipherBlade fill in the blanks by making a source-of-funds request to Suex.io. A crypto exchange can make such a request to clients asking them to explain the origin of the money or assets deposited on the platform.
The information eventually shared by Suex.io allowed CipherBlade to retrieve everything from the perpetrator’s internet protocol (IP) address to their Telegram handle, internet service provider and web browser. All information pointed to a Russian national.
“It became evident to us that, indeed, Mendoza and Diaz were just being scapegoated,” Sibenik said.
Meanwhile, in September 2021, Suex.io became the first cryptocurrency exchange to be sanctioned by the U.S. Treasury Department’s Office of Foreign Assets Control (OFAC), placing it in the same category as terrorists and drug traffickers.
Interestingly, the Suex.io address on the Binance platform was one of the digital currency addresses flagged on OFAC’s sanctions list. Suex.io didn’t respond to multiple requests for comment.
Binance confirmed to CoinDesk that it participated in CipherBlade’s investigation and that it had de-platformed the account in question based on internal safeguards. However, it didn’t specify when the account was de-platformed.
“Similarly to banks and other traditional financial institutions, whenever any illicit flows come through exchanges, the exchange itself is not harboring the actual criminal groups, but rather is being exploited as a middleman,” a Binance spokesperson said in an emailed statement.
Exchange Vulnerabilities
CipherBlade’s report also looked into Bancar and found a number of vulnerabilities that may have exposed the platform to attack.
For one, the CipherBlade investigation found that there are more than 7,000 spam web pages on “http://bancarexchange.io” that weren’t created by Bancar. The CipherBlade report said (and CoinDesk confirmed) that a simple search for the website returns pages advertising everything from Russian brides to car rentals to ghostwriting.
During its investigation, CipherBlade also found the platform’s SSL certificate, which authenticates the website’s identity, had been correctly installed but revoked in December 2020, a year after the hack. A certification can be revoked for a number of reasons, including signs its private keys have been compromised.
At the end of the report, the intelligence firm also outlines potential steps Venezuelan authorities could take to follow the culprit and close the case. It is unclear whether Venezuelan authorities are pursuing the individual in question. But CipherBlade is hopeful.
“I was not super-optimistic at first that the authorities would take our opinions into account. But they obviously did,” Sibenik said.
Updated: 3-4-2022
Convex Finance Bug Causes CVX Token To Sink On Forced Token Unlock
After a smart contract exploit, locked CVX tokens flooded the market, dragging down prices.
A smart contract bug has forced a team to prematurely unlock a huge portion of its token’s circulating supply, sending markets into disarray.
In a Twitter post Friday, the Convex Finance team wrote that it had redeployed the contracts responsible for the vote-locking governance mechanism after the discovery of a bug that would have granted certain users disproportionate rewards.
Important update for vote-locked $CVX holders: the vote-locking contract has been re-deployed, and users will need to re-lock their $CVX tokens.
Full details in our latest medium post:https://t.co/qMGhn7aAqP
— Convex Finance (@ConvexFinance) March 4, 2022
“There were no instances of [the bug] being used prior to deployment of the new vlCVX contract. However, since Convex Finance contracts are immutable and non-upgradeable, a new contract had to be deployed. The new vlCVX contract has implemented a fix for this potential bug going forward,” the team wrote in a blog post.
It’s the latest example of the perilously experimental nature of decentralized finance (DeFi), a $200 billion industry where supply shocks, smart contract bugs and volatile prices are often the norm.
Convex’s vote locking mechanism is key to the project’s token economy, one that allows for users to collect “bribes” from protocols and direct liquidity deposits into another protocol, Curve Finance, but only if users lock their tokens for 16 weeks.
This mechanism plays a key part in the complex, multilayered battle to control voting power in another protocol’s token, Curve Finance’s CRV, colloquially known as the “Curve Wars.”
The vote locking mechanism also plays a key role in managing CVX’s circulating supply, with over 72% of the supply locked earlier on Friday. Frequent CVX traders often track major unlock dates, as they can lead to supply and price fluctuations.
As such, the sudden, unexpected unlock of millions of tokens has led to a significant supply shock on Friday.
Prices fell as much as 20% from $19.10 to $15.22 in a matter of hours.
However, large holders have stepped in to add to their positions, and many users have opted to re-lock their tokens rather than take the opportunity to sell, even during a time of macroeconomic uncertainty due to the war in Ukraine.
Also seeing the best fill size buyers (filtered for +$100k buys) entering back into positions, this address bought $2.5m CVX about 30 minutes ago. https://t.co/pyO19oWVxo pic.twitter.com/zBkoLhNKtu
— Matt Casto (@mcasto_) March 4, 2022
While volatile, prices have been rebounding throughout the afternoon, as CVX currently sits at $16.55, down 15% on the day.
Updated: 3-5-2022
OpenSea Phishing Scandal Reveals A Security Need Across The NFT Landscape
OpenSea’s latest vulnerability poses a larger and more deeper question relating to the global NFT ecosystem’s existing security infrastructure.
Despite the ongoing volatility plaguing the digital asset sector, one niche that has undoubtedly continued to flourish is the nonfungible token (NFT) market.
This is made evident by the fact that a growing number of mainstream mover and shakers including the likes of Coca-Cola, Adidas, the New York Stock Exchange (NYSE) and McDonalds, among many others, have made their way into the burgeoning Metaverse ecosystem in recent months.
Also, owing to the fact that over the course of 2021 alone, global NFT sales topped out at $40 billion, many analysts expect this trend to continue into the future. For example, American investment bank Jefferies recently raised its market-cap forecast for the NFT sector to over $35 billion for 2022 and to over $80 billion for 2025 — a projection that was also echoed by JP Morgan.
However, as with any market growing at such an exponential rate, issues related to security have to be expected as well. In this regard, prominent nonfungible token (NFT) marketplace OpenSea recently fell victim to a phishing attack that took place just hours after the platform announced its week-long planned upgrade to delist all inactive NFTs.
Diving Into The Matter
On Feb 18, OpenSea revealed that it was going to initiate a smart contract upgrade, requiring all of its users to transfer their listed NFTs from the Ethereum blockchain to a new smart contract. Owing to the upgrade, users who failed to facilitate the above said migration stood at a risk of losing their old and inactive listings.
That said, due to the small migration deadline provided by OpenSea, hackers were presented with a potent window of opportunity. Within hours of the announcement, it was revealed that nefarious third party individuals have initiated a sophisticated phishing campaign, stealing NFTs from many users that were stored on the platform before they could be migrated over to the new smart contract.
We are actively investigating rumors of an exploit associated with OpenSea related smart contracts. This appears to be a phishing attack originating outside of OpenSea’s website. Do not click links outside of https://t.co/3qvMZjxmDB.
— OpenSea (@opensea) February 20, 2022
Providing a technical breakdown of the matter, Neeraj Murarka, chief technical officer and cofounder of Bluezelle, a blockchain for GameFi ecosystem, told Cointelegraph that at the time of the incident, OpenSea was making use of a protocol called Wyvern, a standard tech module that most NFT web apps make use of since it allows for the management, storage, and transfer of these tokens within users’ wallets.
Because the smart contract with Wyvern allowed users to work with the NFTs stored in their “wallets,” the hacker was able to send out emails to OpenSea clients masquerading as a representative for the platform, encouraging them to sign “blind” transactions. Murarka further added:
“Metaphorically, this was like signing a blank check. Normally, this is okay if the payee is the intended recipient. Keep in mind that an email can be sent by anyone, but be made to appear to be sent by someone else. In this case, the payee appears to be a single hacker who was able to use these signed transactions to transfer out and effectively steal the NFTs from these users.”
Also, in an interesting twist of events, following the incident the hacker apparently returned some of the stolen NFTs to their rightful owners, with further efforts being made to return other lost assets.
Providing his take on the entire matter, Alexander Klus, founder of Creaton, a Web3 content creation platform, told Cointelegraph that the phishing email campaign used a malicious signing transaction to approve all holdings to be able to be drained at any time.
“We need better signing standards (EIP-712) so people can actually see what they are doing when approving a transaction.”
Lastly, Lior Yaffe, cofounder and director of Jelurida, a blockchain software company, pointed out that the episode was a direct result of the confusion surrounding OpenSea’s poorly planned smart contract upgrade, as well as the platform’s transaction approval architecture.
NFT Marketplaces Need To Step Up Their Security Game
In Murarka’s view, web apps making use of the Wyvern smart contract system should be augmented with usability improvements to ensure that users don’t fall for such phishing attacks time and time again, adding:
“Very clear warnings should be made to educate the user about phishing attacks and driving home the fact that emails will never be sent, soliciting the user to take any steps. Web apps like OpenSea should adopt a strict protocol to never communicate with users via email apart from maybe just registration data.”
That said, he did concede that even if OpenSea were to adopt the safest security/privacy protocols and standards, it is still up to its users to educate themselves about these risks. “Unfortunately, the web app itself is often held responsible, even though it was the user that was phished. Who is responsible? The answer is unclear,” he noted.
A similar sentiment is shared by Jessie Chan, chief of staff at ParallelChain Lab, a decentralized blockchain ecosystem, who told Cointelegraph that regardless of how the entire attack was orchestrated, the issue is not entirely dependent on OpenSea’s existing security protocols but also on user awareness against phishing.
The question remains whether the marketplace operator should have been able to provide sufficient information to its users to keep them informed of how to deal with such scenarios.
Another possibility to mitigate any potential phishing events is by having all interactions between users and their web apps being driven solely via the use of a dedicated mobile/desktop interface. “If all interactions required the use of a desktop app, such attacks could be bypassed completely.”
Providing his take on the subject, Yaffe noted that the main problem — which lies at the heart of this whole issue — is the basic architecture of most NFT marketplaces, enabling users to simply sign a carte blanche approval for a third-party contract to use their private wallet without setting a spending limit:
“Since the OpenSea team did not really figure out the source of the phishing operation, it might as well happen again next time they attempt to make a change to their architecture.”
What Can Be Done?
Murarka noted that the best way to eliminate the possibility of these attacks is if people start making use of hardware wallets. This is because most software wallets as well as other custodial storage solutions are too vulnerable in their general design and operational outlook.
He further elaborated: “Much like Bitcoin, Ethereum, etc, NFTs themselves should be moved to hardware wallet accounts instead of leaving them on a centralized platform,” adding:
“Users need to be super aware of the risks of responding to and acting upon emails they receive. Emails can be faked very easily, and users need to be proactive about the safety of their crypto assets.”
Another thing NFT owners need to remember is that they should only be visiting web apps that employ high-quality security protocols, checking that the accessed marketplaces utilize the HTTPS mechanism (at the very least) while being able to clearly see a lock symbol on the top left of their browser window — which correctly points to the intended company — while visiting any webpage.
Yaffe believes that users should be careful with contract approvals and keep an accurate track of the contracts they have greenlighted in the past. “Users should revoke unnecessary or unsafe approvals. If possible users should specify a reasonable spending limit for every contract approval,” he concludes.
Lastly, Chan believes that in an ideal scenario, users should keep their wallets on a dedicated platform that they don’t use to read email or browse the web, adding that any such avenues are subject to all manners of third party attacks. She further stated:
“This is inconvenient, but when dealing with assets of great value and where there is no recourse in the event of theft, extreme care is justified. And, as with all financial transactions, they should be very careful in deciding who to deal with, since the counterparties can also steal your assets and disappear.”
Therefore, while moving into a future driven by NFTs and other similar novel digital offerings, it remains to be seen how platforms operating within this space continue to evolve and mature, especially as a growing amount of capital keeps making its way into the NFT market.
Updated: 3-9-2022
Siblings Charged Over Mining Coin That Turned Into Alleged $124M Fraud
The brother and sister team will face charges of wire fraud, securities fraud and conspiracy for their alleged roles in the Ormeus Coin ICO.
A pair of siblings is now in very hot water with the United States government with criminal charges filed against them for allegedly committing fraud in the Ormeus Coin scheme.
On Tuesday, the Securities and Exchange Commission (SEC) charged siblings John Albert Loar Barksdale and sister JonAtina (Tina) Barksdale with violating federal securities laws and allegedly defrauding at least 12,000 “retail investors out of more than $124 million.” The Department of Justice (DOJ) arrested John abroad and charged him with wire fraud, securities fraud and conspiracy.
Both of the Barksdale siblings are U.S. citizens. John, 41, was living in Thailand while JonAtina, 45, was in Honk Kong, according to Reuters.
There were two Ormeus Coin (ORME) initial coin offerings (ICOs) starting in 2017. The SEC complaint specifically states that the Barksdales lied about “the size, value, and purported profitability of Ormeus Coin’s cryptocurrency mining assets.”
ORME is an ERC-20 token and a BEP-20 token found on Ethereum and BNB Chain.
While both siblings created social media posts and videos marketing the project, only John attended traveling roadshows and conferences to promote it.
Associate director of the SEC’s Division of Enforcement Melissa Hodgman likened John to a “snake-oil salesman.” She also said both siblings used “social media, promotional websites, and in-person roadshows to mislead retail investors for their own personal benefit.”
Hodgman Also Reaffirmed The SEC’s Position On Fraudsters In The Crypto Industry In Stating:
“We will continue to vigorously pursue persons who sell securities in schemes to defraud the investing public no matter what label the promoters apply to their products.”
Both the SEC and DOJ are basing fraud charges on alleged misrepresentations the Barksdales told investors about the state of the Ormeus mining operation. The Oremus Coin website states that mining operations for the coin started in Nov. 2017 with physical Bitcoin (BTC), Litecoin (LTC) and Dash (DASH) mining devices.
The Barksdales claimed that the project had invested $250 million into the mining operation backing ORME and that it was generating $5 million in monthly revenue.
The project allegedly misled investors by showing its vault wallet was worth more than $190 million as of last November. However, the display was allegedly set up through a separate website that showed the value of an unrelated wallet. The SEC claims that the project’s real wallets “were worth less than $500,000.”
The DOJ also stated that the mining operation “never approached a value close to $250 million and never produced revenues exceeding one million dollars in any month.”
John, who wrote a blog post on February 26, 2018, about “Why Taking Calculated Risks In Life Is Important,” is still listed on the Ormeus Coin and Ormeus Cash websites as an adviser. A court date will be set while the Barksdales are held in custody.
A recent decision by the 11th Circuit Court of Appeals could give the SEC more leverage in this case as it allows prosecutors to use a broader range of evidence. The court reversed a decision by an inferior court which prevented prosecutors from including videos from being used in the securities fraud case against the BitConnect founders on Feb. 18.
The SEC has been hawkish on common advertising methods in the crypto industry and whether it constitutes securities fraud. Reports emerged on Thursday that the Commission currently has its sights set on nonfungible tokens (NFT) used for fundraising purposes “like traditional securities.”
Updated: 3-11-2022
Vitalik Buterin Asks Court For Leniency In Upcoming Sentencing of Virgil Griffith
The Ethereum co-founder’s letter paints a moving picture of his relationship with Griffith, his long-time friend and former collaborator, whom Buterin credits with shaping both his own world view and the culture of the Ethereum Foundation.
Ethereum co-founder Vitalik Buterin has added his voice to the chorus of people asking a federal court in New York for leniency in the upcoming sentencing of former Ethereum developer Virgil Griffith.
Griffith was arrested in November 2019 after giving a presentation on cryptocurrency and blockchain technology at a North Korean crypto conference in April of that year. He was charged with violating U.S. sanctions law and, in September 2021, pleaded guilty in an agreement with federal prosecutors that could see him serve up to 6.5 years in prison.
In a letter to U.S. District Judge Kevin Castel of the Southern District of New York, Buterin detailed his seven-year friendship with Griffith, with whom he met in 2013 and began collaborating on research in 2016. In 2018, Griffith formally joined Ethereum as a developer after Buterin said he “convinced him to agree.”
Buterin wrote about Griffith’s kind and peaceful nature – which also played heavily in many of the nearly 40 other letters written to Castel from Buterin’s family, friends and community members, including a homeless man Griffith met at a Waffle House while on bail in Alabama in 2020.
The man’s letter to the court credits Griffith with helping him get a general educational development (GED) degree and finding steady work as a barber.
“Virgil sees the good in everyone [except] spiders. They make him jumpy,” the man, Eugene Hays, wrote to Castel.
That goodness, Buterin wrote, “left a lasting legacy in the Ethereum Foundation and the wider community,” as well as on Buterin himself.
“[Griffith] has also left some deep personal changes in myself,” Buterin wrote Castel. “His attitudes and actions over the years helped to foster an open-mindedness and an orientation towards cooperation that guide my actions to this day, in a way that was absent from my personality five years ago.”
Buterin also described Griffth’s curiosity about other cultures, which led him to move to Singapore in 2016 and his work to make Ethereum compatible with Islamic finance law.
Though Buterin did not directly connect this curiosity to Griffith’s decision to travel to North Korea, Griffith’s lawyer wrote that the trip was “the culmination of Virgil’s unique and unfortunate curiosity and obsession with North Korea.”
In a letter from Griffith himself to the judge, he writes: “I became obsessed with seeing the country before it fell, akin to someone offered the chance to see East Berlin in its final days before the Wall came down.”
Griffith’s lawyers, as well as his loved ones, said they hope his remorse will earn him a shorter sentence.
They have asked the court to consider allowing him to serve a two-year sentence and allowing him to receive credit for time served in jail and a period of three years’ supervised release, including 270 days of home detention.
Updated: 3-16-2022
Unchained Capital Discloses Data Leak At Email Marketing Partner
The bitcoin-only financial services provider says, however, that none of its own systems were compromised.
In an email to clients and a letter posted on the company website on Wednesday, Unchained Capital CEO Joe Kelly said ActiveCampaign (AC), an outside email marketing provider used by Unchained until earlier this year, was hit with a social engineering attack last week. Unchained Capital is a bitcoin-only financial services provider.
* Kelly pointed out the attack occurred on the AC platform, meaning that only information shared with AC – client email addresses, usernames, account status, whether the client had an active multisig vault or loan with Unchained Capital and possibly IP addresses – may have been exported without authorization.
* Not compromised, said Kelly, were any of Unchained’s systems, meaning client profile information that was never shared with AC was not leaked. This would include data including physical addresses, Social Security numbers, dates of birth, IDs, phone numbers, bank account numbers, passwords, bitcoin (BTC) addresses, bitcoin balances, loan balances, trading activity, vault statements and loan statements.
* Kelly added that while client bitcoin custody is protected by multisig cold storage, clients nevertheless should be aware of what happened and be vigilant against phishing attacks.
* “We are deeply sorry this incident occurred as we take our clients’ privacy very seriously,” concluded Kelly. “We want to reinforce the fact that, due to our collaborative custody model, no such incidents could ever put any client funds at risk.”
‘Unlucky’: Agave And Hundred Finance DeFi Protocols Exploited For $11M
Agave and Hundred Finance have paused operations while investigations continue into the exploit.
A hacker has made off with approximately $11 million in wrapped ETH (wETH), wrapped BTC (wBTC), Chainlink (LINK), USD Coin (USDC), Gnosis (GNO) and wrapped XDAI (wxDAI) after using a “re-entrancy” attack on decentralized finance (DeFi) lending protocol applications Agave and Hundred Finance.
The attack comes within 24 hours of the news breaking of the Deus Finance exploit, where hackers stole over $3 million in Dai (DAI) and Ether (ETH) from the lending contract platform.
Agave token AGVE dropped by 20% following the attack, according to data from CoinGecko. Hundred Finances token HND fell 3.5% after it announced the exploit. However, it’s since recovered to hit a 24-hour high.
“Agave is currently investigating an exploit on the agave finance protocol,” Agave tweeted on Tuesday. “We will update you as soon as we know more.” It noted that contracts have been paused until the situation is resolved.
The Hundred Finance team also tweeted that it was exploited on the Gnosis chain and has paused its markets while pursuing investigations.
According to on-chain analysis, the address associated with the attacker has sent over 2,100 ETH, worth over $5.5 million, to a crypto mixer in an attempt to launder the stolen tokens.
Solidity developer and creator of an NFT liquidity protocol application Shegen (@shegenerates), tweeted that she lost $225,000 in the exploit. Her investigations revealed the attack worked by exploiting a wETH contract function on Gnosis Chain, allowing the attacker to continue borrowing crypto before the apps could calculate the debt preventing further borrowing.
The attacker ran this exploit, continually borrowing against the same collateral they were posting until the funds were drained from the protocols.
Shegen told Cointelegraph that while the smart contract on Agave is essentially the same as Aave, which secures $18.4B, “every security researcher has audited it,” she said. “So it’s reasonable to assume the contract is safe.”
“I think this hack stands out more than some bigger ones,” Shegen said, noting that even if it was a smaller hack compared with others that stole millions more, the similarity to Aave meant “it seems top tier safe, but wasn’t, and that break of trust hurts.”
“It’s like you can’t even trust ‘safe’ code.”
Blockchain security researcher Mudit Gupta says the difference between Aave and Agave is that “Aave actively checks for re-entrancy before listing tokens on the mainnet to avoid similar attacks.”
Shegen stated that she did not blame the Agave developers for failing to prevent the attack.
“Agave was used in an unsafe way”, she said. “Maybe the developer should not have allowed tokens with callbacks in them to be used in the platform, or added more re-entrancy guards.”
“Curve, for example, was not hacked today, because it has extra re-entrancy guards, but I don’t really blame Luigy and the Agave team because it‘s so unlikely that this would have happened, and slipped past many people.”
Shegen also didn’t point the blame at Gnosis for creating tokens with a callback function that the hacker exploited, saying that the feature stops users from accidentally losing their crypto.
“That‘s actually a great feature for bridged tokens, it‘s just a really unfortunate, and unlucky circumstance in my opinion.”
Updated: 3-15-2022
Deus Finance Exploit: Hackers Get Away With $3M Worth Of DAI And Ether
Deus Finance had acknowledged the exploit on its lending contract and the CEO of the firm was quick to come up with a reimbursement plan.
Multi-token decentralized finance (DeFi) marketplace Deus Finance has become the latest victim of an exploit resulting in over $3 million losses in the Dai (DAI) and Ether (ETH).
DeFi analytic firm PeckShield took to Twitter to explain the cause and manner in which the funds were exploited. The hackers behind the attack managed to exploit and manipulate a price oracle for flash loans, resulting in the insolvency of users’ funds.
1/ @deusdao Deus Finance was exploited in https://t.co/bfYCQcz5rZ, leading to the gain of ~$3M for the hacker (The protocol loss may be larger), including 200,000 DAI and 1101.8 ETH
— PeckShield Inc. (@peckshield) March 15, 2022
The hackers manipulated the price from the pair of StableV1 AMM – USDC/DEI, which the protocol used to set a price oracle for its flash loans.
PeckShield revealed that hackers managed to steal 200,000 DAI and 1101.8 ETH, and the total amount of stolen funds could be larger than the early estimates of $3 million.
The hacker behind the attack then funneled the stolen funds using the coin mixer tool Tornado cash via the Multichain Protocol (previously known as AnySwap).
Deus Finance acknowledged the exploit on its lending protocol and claimed it has closed its DEI lending contract. The DeFi protocol also claimed that both DEUS and DEI are unaffected by the exploit.
We are aware of the recent exploit reports regarding the $DEI lending contract.
Contract has been closed, both $DEUS & $DEI are unaffected. Devs are working on a summary of the events, all information will be communicated once we have assessed the full situation.
— DEUS Finance DAO (@DeusDao) March 15, 2022
Deus Finance provides DeFi infrastructure to help others create financial instruments including synthetic stock trading platforms, options and futures trading.
Lafayette Tabor, the CEO of Deus Protocol, took to Twitter to inform the community about the reimbursement plans. He said that the developers would create a new contract where affected users would be able to repay their loans. He explained:
“We will create a contract you will be able to repay your DEBT on it and get your sAMM that were liquidated, we will also implement a feature that lets you swap DEI against a small MUON allocation. (paying from my team allocation).”
Bitcoin Stealing Malware: Bitter Reminder For Crypto Users To Stay Vigilant
A Bitcoin user was tricked into sending 0.255 Bitcoin to the wrong address due to malware running on their computer.
An unfortunate Bitcoin (BTC) user was duped out of 0.255 BTC, almost $10,000, due to malware running on their computer.
Louis Nel, a tech blogger and crypto enthusiast, flagged the issue on Twitter, referring to his friend as ‘C.’
A friend sent 0.255BTC from his bitcoin wallet to an exchange.
He copied and pasted the wallet address on his computer.
After 4 hours he was worried when the funds did not arrive at the exchange…
— Louis Nel (@LouisNel) March 14, 2022
Nel told Cointelegraph that C’s “Bitcoin was sent from Kraken to VALR, a South African exchange,” however, “malware running on his computer intercepted the copied data and inserted a new wallet address when he pasted this without realizing.”
VALR exchange confirmed that the wallet address does not belong to them; in further warning signs, Nel added that “there are nine transactions into that wallet, so others have been duped as well.”
The wallet address in question now has a value of 0.27 BTC but the funds have not moved. Nel shared a photo of the wallet address with connected addresses.
Malware attacks are nothing new to the world of crypto finance or indeed to Bitcoin transactions. Chainalysis estimates that as much as $500,000 was stolen by just one malware bot over the course of 2021.
Plus, malware attacks can happen to seasoned cryptocurrency enthusiasts: C first got involved in Bitcoin and cryptocurrency in 2018. The malware attack is rotten luck for C, but a poignant reminder for cryptocurrency users.
Transactions on Bitcoin are irreversible, or “immutable,” meaning that once the funds have left a wallet, no party can manipulate or falsify data, or send back the money. While it’s one of the protocol’s strengths, in situations such as this malware attack, it’s a double-edged sword. Nel suggested:
“When working with Bitcoin and cryptocurrency you are responsible for your own security. When copying and pasting wallet addresses, always check the first four to six characters and the last four to six to ensure that they match.”
It boils down to one of the most crucial Bitcoin mantras, “don’t trust, verify.” If sending money, always reread addresses, checking “the entire address.” If it’s a large amount, send a test transaction of a few Satoshis to ensure the funds arrive safely at the desired wallet address.
For C, despite discovery then removal of the malware software, “the issue was still there and he sent me [Nel] a video where the wallet address would still dynamically change.” The laptop, which was running Windows 10, appears to still be compromised:
“All we know is that the malicious software became embedded in his operating system and was still doing its thing.”
Updated: 3-22-2022
Microsoft Confirms Hacker Group Lapsus$ Breached Its Systems
* Company Says It Found An Account That Was Compromised
* Microsoft Cybersecurity Team Has Been Tracking Group For Weeks
Microsoft Corp. said that the hacker group Lapsus$ gained “limited access” to its systems, following a claim by the group that it obtained source code for the Bing search engine and Cortana voice assistant.
The software giant had been tracking the activities of Lapsus$ — which it labels a “large-scale social engineering and extortion campaign” — for several weeks and provided some details on the methods of its attacks in a blog post late Tuesday.
Lapsus$ had previously breached the cybersecurity defenses of Nvidia Corp. and Samsung Electronics Co., and this week also claimed to have gained access to the system privileges of Okta, the San Francisco-based company that manages user authentication services for thousands of corporate clients.
“Our investigation has found a single account had been compromised, granting limited access,” Microsoft said. “Our cybersecurity response teams quickly engaged to remediate the compromised account and prevent further activity. Microsoft does not rely on the secrecy of code as a security measure and viewing source code does not lead to elevation of risk.”
The hacking group, which has been given the designation DEV-0537 by Microsoft’s cybersecurity researchers, has been expanding the geographic range of its targets and going after government organizations as well as the tech, telecom and health-care sectors, according to the blog post. They are also known for hijacking cryptocurrency accounts, Microsoft said.
Lapsus$ has made claims on social media that it’s infiltrated several large tech companies besides Microsoft. Its Telegram channel was first to announce the Microsoft and Okta breaches this week and also included mention of breaching employee accounts of LG Electronics Inc.
“Unlike most activity groups that stay under the radar, DEV-0537 doesn’t seem to cover its tracks,” said Microsoft, based in Redmond, Washington. “They go as far as announcing their attacks on social media or advertising their intent to buy credentials from employees of target organizations.”
DeFiance Capital Founder Loses $1.6M In Hot Wallet Hack
The hackers took on one of the biggest names in DeFi, but may have bitten off more than they could chew, as “Arthur_0x” warned, “you messed with the wrong person.”
Founder of major crypto investment firm DeFiance Capital “Arthur_0x” has suffered a hack on one of his hot wallets resulting in the loss of more than $1.6 million in nonfungible tokens (NFTs) and cryptocurrency.
In a tremendous show of support, the crypto community has come to his aid to help retrieve the stolen items as he asked people to blacklist the hacker’s wallet. Several individuals on Twitter have attempted to determine exactly how the hack occurred and where the hacker gained access to his wallets.
NFT community member “Cirrus” went as far as buying two of the stolen Azuki NFTs and deciding to return them to Arthur at cost. Cirrus told Cointelegraph on Tuesday that he,
“found out they were hacked, and instead of selling them for profit like the other folks who got some of his, decided I’d sell them back to him at cost to help him out.”
Cirrus added that this “isn’t the first time” this has happened to him. He said, “I could easily go sell them for 6-8 Ether (ETH) profit, but it just isn’t right.” His profile states that he has been a victim of rug pulls three times before, which likely guided his sympathies for his fellow victim.
Yo @Arthur_0x two of my bids got accepted on your hacked Azukis. Willing to get them back to you at cost. DM me pic.twitter.com/cBIX9QNLNu
— Cirrus (@CirrusNFT) March 22, 2022
A rug pull is when a crypto or NFT project suddenly closes down and the value of their token or NFT plummets without prior warning. In most cases, rug pulls are confirmations of a scam.
In total, Arthur appears to have lost 78 different NFTs from five collections, mostly “Azukis.” He also lost 68 wrapped Ether (wETH), 4,349 staked DYDX (stkDYDX) and 1,578 LooksRare (LOOKS) tokens.
The hacker began moving assets at about 12:30 am UTC, then promptly put all the NFTs up for bid on the OpenSea NFT marketplace. As of the time of writing, the hacker’s wallet held 545 ETH, worth about $1.6 million.
This hack highlights the importance of operational security when dealing with the self-custody of crypto assets because even people in the highest echelons of the industry can be attacked. In Arthur’s case, he is baffled by how this happened to him as he wrote in a tweet: “Hot wallet on mobile phone is indeed not safe enough.”
Was pretty careful and stuck with only using hardware wallet on PC until I start trading NFT more regularly.
Hot wallet on mobile phone is indeed not safe enough
— Arthur ⛩️ (@Arthur_0x) March 22, 2022
Had Arthur used a hardware wallet, otherwise known as a cold wallet, he still may not have been protected from this attack. Unlike a hot wallet, a hardware wallet is not always connected to the network. This feature can keep one’s private key and seed phrase safe from intrusion.
However, Arthur believes that the security breach happened due to a transaction he made on-chain which may also have compromised the seed phrase or private key from a hardware wallet.
NFT and crypto scams are always a danger, so investors should take the highest security precautions with their assets. There are even serial scammers who design projects to take advantage of the NFT community and pull the rug then move on to the next scam. As Cirrus pointed out:
“This is a gold rush for hackers and they’re doing everything they can to come up with new ways to take advantage.”
In light of the frustration and irritation at the hack, Arthur had stern words for the party who stole his assets, stating in a tweet: “The only thing I can say to the hacker is: you mess with the wrong person.”
Updated: 3-23-2022
Teen Suspected By Cyber Researchers Of Being Lapsus$ Mastermind
* Unconventional Hacking Group Has Hit Microsoft And Nvidia
* Teen Lives With Mother Near Oxford, England, Researchers Say
Cybersecurity researchers investigating a string of hacks against technology companies, including Microsoft Corp. and Nvidia Corp., have traced the attacks to a 16-year-old living at his mother’s house near Oxford, England.
Four researchers investigating the hacking group Lapsus$, on behalf of companies that were attacked, said they believe the teenager is the mastermind.
Lapsus$ has befuddled cybersecurity experts as it has embarked on a rampage of high-profile hacks. The motivation behind the attacks is still unclear, but some cybersecurity researchers say they believe the group is motivated by money and notoriety.
The teen is suspected by the researchers of being behind some of the major hacks carried out by Lapsus$, but they haven’t been able to conclusively tie him to every hack Lapsus$ has claimed. The cyber researchers have used forensic evidence from the hacks as well as publicly available information to tie the teen to the hacking group.
Bloomberg News isn’t naming the alleged hacker, who goes by the online alias “White” and “breachbase,” who is a minor and hasn’t been publicly accused by law enforcement of any wrongdoing.
Another member of Lapsus$ is suspected to be a teenager residing in Brazil, according to the investigators. One person investigating the group said security researchers have identified seven unique accounts associated with the hacking group, indicating that there are likely others involved in the group’s operations.
The teen is so skilled at hacking — and so fast– that researchers initially thought the activity they were observing was automated, another person involved in the research said.
Lapsus$ has publicly taunted their victims, leaking their source code and internal documents. When Lapsus$ revealed it had breached Okta Inc., it sent the company into a public-relations crisis. In multiple blog posts, Okta disclosed that an engineer at a third-party vendor was breached, and that 2.5% of its customers may have been impacted.
Lapsus$ has even gone as far as to join the Zoom calls of companies they’ve breached, where they have taunted employees and consultants who are trying to clean up their hack, according to three of the people who responded to the hacks.
Microsoft, which itself confirmed it was hacked by Lapsus$, said in a blog post that the group has embarked on a “large-scale social engineering and extortion campaign against multiple organizations.”
The group’s primary modus operandi is to hack companies, steal their data and demand a ransom in order to not release it. Microsoft tracks Lapsus$ as “DEV-0537,” and said that the group has successfully recruited insiders at victimized companies in order to assist in their hacks.
The group suffers from poor operational security, according to two of the researchers, allowing cybersecurity companies to gain intimate knowledge about the teenage hackers.
“Unlike most activity groups that stay under the radar, DEV-0537 doesn’t seem to cover its tracks,” Microsoft said in a blog post. “They go as far as announcing their attacks on social media or advertising their intent to buy credentials from employees of target organizations. DEV-0537 started targeting organizations in the United Kingdom and South America but expanded to global targets, including organizations in government, technology, telecom, media, retail and health-care sectors.”
The teenage hacker in England has had his personal information, including his address and information about his parents, posted online by rival hackers.
At an address listed in the leaked materials as the teen’s home near Oxford, a woman who identified herself as the boy’s mother talked with a Bloomberg reporter for about 10 minutes through a doorbell intercom system. The home is a modest terraced house on a quiet side street about five miles from Oxford University.
The woman said she was unaware of the allegations against her son or the leaked materials. She said she was disturbed that videos and pictures of her home and the teen’s father’s home were included. The mother said the teenager lives at that address and had been harassed by others, but many of the other leaked details couldn’t be confirmed.
She declined to discuss her son in any way or make him available for an interview, and said the issue was a matter for law enforcement and that she was contacting the police.
The Thames Valley Police, and the National Crime Agency, which investigates hacking in the U.K., didn’t immediately respond to messages about the alleged teen hacker. The FBI’s San Francisco field office, which is investigating at least one of the Lapsus$ intrusions, declined to comment.
Lapsus$ has also claimed to have breached Samsung Electronics Co., Vodaphone and Ubisoft. After breaching Nvidia, Lapsus$ posted stolen source code from the company on their Telegram channel.
After its claim of hacking Okta generated a wave of headlines Tuesday, Lapsus$ suggested it would be taking some time off from hacking the world’s biggest companies.
“A few of our members has a vacation until 30/3/2022. We might be quiet for some times,” the hackers wrote in its Telegram channel. “Thanks for understand us. – we will try to leak stuff ASAP.”
Stablecoin Cashio Suffers ‘Infinite Glitch’ Exploit, TVL Drops By $28M
Cashio’s CASH token has lost almost all its value, as of the time of writing.
Solana-based stablecoin protocol Cashio was exploited in an “infinite glitch” attack, developers said on Wednesday.
* Following the exploit, the value of Cashio’s CASH token dropped to nearly zero.
* “Please do not mint any CASH. There is an infinite mint glitch. We are investigating the issue and we believe we have found the root cause. Please withdraw your funds from pools,” the team wrote in a tweet.
Please do not mint any CASH. There is an infinite mint glitch.
We are investigating the issue and we believe we have found the root cause. Please withdraw your funds from pools. We will publish a postmortem ASAP.
— Cashio ($CASH) ???? (@CashioApp) March 23, 2022
* CASH is a stablecoin pegged to the U.S .dollar and is backed by USDC and USDT via a liquidity pool on Saber, a Solana-based market maker. Users can mint their CASH by providing liquidity with USDT and USDC.
* The incident on Wednesday allowed the hacker to manipulate Cashio’s smart contracts to mint an infinite supply of CASH without providing any liquidity in return. Blockchain data shows over 2 billion CASH were minted, without any USDC or USDT backing.
* The hacker used the newly minted tokens to exchange them for stablecoins on Cashio’s liquidity pools. Data from tracking tool DeFiLlama shows the total value locked on Cashio dropped by $28 million after the attack.
* Stablecoins based on other protocols has suffered similar attacks in the past. Polygon-based Safedollar dropped to $0 after an exploit in June 2021, with both USDC and USDT siphoned off by the hacker at the time.
Microsoft Says Digital Extortion Gang Lapsus$ Targets Cryptocurrency, Too
* Group Has A Murky Background And Unconventional Methods
* Microsoft Found Compromised Account Granting Limited Access
A digital extortion gang with a murky background and unconventional methods — one researcher called them “laughably bad” at times — has claimed responsibility for a string of compromises against some of the world’s largest technology companies.
The group, known as Lapsus$, said in a series of public posts on the messaging app Telegram this week that it had accessed Okta Inc., the San Francisco-based identity-management firm that provides authentication tools for an array of business clients.
Okta said Tuesday that attackers may have viewed data from approximately 2.5% of its customers after breaching the laptop of an engineer at a third-party vendor.
Lapsus$ previously claimed to breach organizations including Nvidia Corp., Samsung Electronics Co., and the gaming company Ubisoft Entertainment SA. The group said it also accessed data from Microsoft Corp., saying it had gathered source code from the company’s Bing search engine, Bing Maps and the Cortana digital assistant.
Microsoft said attackers gained “limited access” to its systems, and that attackers had compromised a single account to gather data.
In recent years, most hacking groups have used malware to encrypt a victim’s files, then demanded payment to unlock them, so-called ransomware. Sometimes the groups steal sensitive data and threaten to make it public unless they are paid.
Lapsus$ functions as a “large-scale social engineering and extortion campaign,” though it does not deploy ransomware, Microsoft said. The group uses phone-based tactics to target personal email accounts at victim organizations and pays individual employees or business partners of an organization for illicit access, according to Microsoft.
Lapsus$ also is known for hijacking individual accounts at cryptocurrency exchanges to drain user holdings.
In a March 10 post on its Telegram channel, the group urged followers to provide access to a virtual private network inside their employers’ systems, or share details on how to access remote work tools. In addition, they sought access to telecommunication companies, software and gaming corporations and Latin American phone service providers.
Joshua Shilko, a senior principal analyst at the cybersecurity firm Mandiant Inc., said Lapsus$ may have been active as early as mid-2021 when group members were posting in underground forums. “They’re into the notoriety. They’re interested in being in the spotlight,” he said, adding that the evidence shows they are financially motivated.
In a Twitter post responding to the Lapsus$ allegation, Okta Chief Executive Officer Todd McKinnon said the matter dated back to a January security incident.
Okta Chief Security Officer David Bradbury on Tuesday revealed a five-day window in January when an attacker gained access to a laptop for a support engineer who worked for a third-party vendor. Bradbury also said the company had detected an unsuccessful hacking attempt in January. Okta shares fell by more than 8% before recovering almost all the loss Tuesday.
The group’s Telegram channel posted a series of screenshots that it claimed were evidence of the hack and said that Okta wasn’t the ultimate target. “BEFORE PEOPLE START ASKING: WE DID NOT ACCESS/STEAL ANY DATABASES FROM OKTA – our focus was ONLY on okta customers.”
Brett Callow, a threat analyst at the cybersecurity firm Emsisoft, called the group’s tactics “quite bizarre.” Their actions, he said, “suggest that they may be kids who’re in it for the lulz as much as they are the bucks.” (“Lulz” is a variation of LOL, for laugh out loud).
Initial activity from the group suggested that at least some of its members were in Brazil, as that was the home nation of many of the companies first targeted, said Allan Liska, intelligence analyst at the threat-intelligence firm Recorded Future.
Membership in hacking collectives is fluid, Liska said. Recorded Future hasn’t observed any activity from apparent Lapsus$ members on popular Russian-speaking forums, he said.
“They seem laughably bad at times, but then here they are publishing Microsoft source code,” he said. “This may be that same mix of really talented members and some idiots. Even idiots stumble into success once in a while.”
Updated: 3-24-2022
Frosties NFT Creators Charged With ‘Rug Pull’ Investor Fraud
* Defendants Allegedly Made Off With $1 Million Within Hours
* Fraud Tied To NFTS Has Surged With Popularity Of Crypto Assets
Two 20-year-old Los Angeles men were charged with defrauding investors of more than $1 million by creating a series of NFTs and abandoning the project after selling out of the tokens.
Federal prosecutors in New York on Thursday charged Ethan Nguyen and Andrew Llacuna with wire fraud and conspiracy to commit money laundering. According to the government, the two created a series of non-fungible tokens called “Frosties,” which were supposed to grant purchasers the exclusive rights to giveaways, a metaverse-based game, and passes to future seasons of the NFTs.
But instead, prosecutors said, the two men executed a “rug pull” in January — giving up on the Frosties project within hours after selling out of the tokens, deactivating a website devoted to the NFTs and transferring about $1.1 million in cryptocurrency proceeds to wallets they controlled.
They were advertising a second, similar project under the name “Embers” that was supposed to launch later this week when they were arrested in Los Angeles, authorities said.
“NFTs have been around for several years, but recently mainstream interest has skyrocketed,” Manhattan U.S. Attorney Damian Williams said. “Where there is money to be made, fraudsters will look for ways to steal it.”
NFTs exploded in popularity last year, and remain the most talked about sector in the digital world, with the Bored Ape Yacht Club boosting crypto’s brand. Celebrities, including rapper Eminem and talk-show host Jimmy Fallon, own the NFTs.
Powerful and wealthy investors such as Andreessen Horowitz and Animoca Brands have earned major profits and gained substantial influence over a space that prides itself on decentralization and control by users.
Crypto criminals are making off like bandits as digital assets grow in popularity, according to a recent report from blockchain analytics firm Chainalysis. Scamming revenue rose 82% in 2021 to $7.8 billion of stolen cryptocurrency, with more than a third of that total procured from so-called rug pulls, according to Chainalysis.
“The Frosties rug pull was a modern take-the-money-and- run scheme, one of many in the NFT space,” said Ian McGinley, an attorney with Akin Gump Strauss Hauer & Feld LLP and a former federal prosecutor in the Southern District of New York who served as co-chief of the unit that probes complex frauds and cybercrime. “While it’s the first federal prosecution in the space, it won’t be the last.”
Frosties was launched in January with a private presale, and the public sale went live on Jan. 9 on the OpenSea platform, according to court filings. All 8,888 tokens, which were priced at about 0.04 Ether each, were sold within 48 minutes. The scam may have been the first NFT “rug pull” of the year, Blockworks reported.
Nguyen, who also went by the names “Frostie,” “Jakefiftyeight” and “Meltfrost,” and Llacuna, who was known as “heyandre,” face as long as 20 years in prison if convicted. Lawyers for the pair couldn’t be immediately identified.
The case is US v Nguyen, 22-mj-2478, U.S. District Court, Southern District of New York.
U.K. Police Arrest 7 Related To Lapsus$ Hacks On Tech Firms
* Suspects Released As Investigation Into Allegations Continues
* Alleged Mastermind Of Hacking Spree Is 16-Year-Old Near Oxford
City of London Police arrested seven people in connection with an investigation into a hacking group called Lapsus$, which has said it’s responsible for a rash of recent cyberattacks against companies including Microsoft Corp. and Nvidia Corp., according to a person involved in the investigation.
The suspects, ages 16 to 21, have been released while the investigation continues, Detective Inspector Michael O’Sullivan said in a statement. “Our inquiries remain ongoing,” he said. Police didn’t identify the hacking gang, but the arrests were related to a broad investigation into the Lapsus$ hacks, according to the person.
The arrests followed a report Wednesday by Bloomberg News in which cybersecurity researchers investigating the Lapsus$ hacks said they had traced the breaches to a 16-year-old who lives with his mother near Oxford, England. The researchers said they believed the teenager was the mastermind of the operation.
The identities of the people who were arrested in the U.K. weren’t known.
In the U.K., it’s common for suspects in nonviolent offenses to be released after their arrest, pending the results of the investigation. When authorities detain suspects, they typically have only 24 hours to bring charges before being required to release them. There are also strict rules prohibiting the release of information about suspects, after they’re charged, to avoid prejudicing a potential trial.
Lapsus$ seeks to compromise companies by persuading employees at victim organizations to provide hackers with access to company data.
BBC News previously reported that seven people had been arrested.
Okta Says Hundreds of Its Customers May Have Been Caught In Hack
Identity-verification provider seeks to allay concerns about impact from breach in its security by Lapsus$ group.
Okta Inc., one of the world’s leading providers of digital identity verification, said that a January data breach revealed by hackers this week may have affected hundreds of customers that rely on its software to manage secure access to their internal computer networks.
Okta said the attack had affected as many as 366 customers, or 2.5% of the more than 15,000 businesses and institutions it services world-wide. The breach, claimed by the Lapsus$ group, originated from the laptop of an engineer employed by a subcontractor, which the hackers had access to between Jan. 16 and Jan. 21, Okta said. Tuesday.
Okta said it had contacted customers that were potentially affected. Shares of Okta fell 11% to $148.55 on Wednesday.
Reports of the breach emerged earlier this week after Lapsus$ posted screenshots that appeared to be of Okta internal systems to its Telegram social-media account. The group said its primary target wasn’t Okta but its customers.
Okta said in separate statements on Tuesday that the screenshots were from a computer used by a customer-support engineer from a unit of a subcontractor, Miami-based Sitel Group. Taking control of the computer effectively gave the hackers the same level of access as the engineer, according to Okta.
Support engineers can access only limited data and while they can help reset passwords and multifactor authentication factors, they can’t see the passwords themselves, Okta said. The engineer didn’t have “godlike access,” and had no power to create or delete user accounts, download customer databases or access source-code repositories, it said.
“The scenario here is analogous to walking away from your computer at a coffee shop, whereby a stranger has (virtually in this case) sat down at your machine and is using the mouse and keyboard.”
Okta said it notified Sitel of the breach in late January, and Sitel hired an outside forensic firm to investigate. The full results of the investigation were shared with Okta on Tuesday, it said, expressing disappointment at the time taken to issue the results.
The unit of Sitel where the breach took place, Tampa, Fla.-based Sykes Enterprises Inc., said it took swift action to contain the incident after learning of the hack.
“Following completion of the initial investigation, working in partnership with the worldwide cybersecurity leader, we continue to investigate and assess potential security risks to both our infrastructure and to the brands we support around the globe,” the company Sykes said. in a statement Tuesday.
‘The scenario here is analogous to walking away from your computer at a coffee shop, whereby a stranger has (virtually in this case) sat down at your machine and is using the mouse and keyboard.’
— Okta
In a follow-up Telegram post, Lapsus$ disputed some of Okta’s findings. It denied that it compromised a laptop and said support engineers have more-extensive access than Okta suggested, including to internal communications.
It also took issue with Okta’s assertion that the impact of the breach on customers was limited. The ability to reset passwords and multifactor authentication factors “would result in complete compromise of many clients’ systems,” Lapsus$ said.
When asked about the hackers’ hacker’s claims, an Okta spokeswoman referred to the company’s earlier statement describing the limitations of the breach.
In a blog post on Tuesday, Microsoft Corp. confirmed it had been hacked by the group, and that for weeks had been tracking what it described as a large-scale campaign by Lapsus$ against multiple organizations. It described the group as often acting openly and not trying to cover its tracks, using extortion and destruction of data.
After gaining access to an organization, the group has been known to listen in on crisis communication calls and internal messaging forums, Microsoft said.
The group—which communicates in Portuguese and broken English on Telegram—cut its teeth with attacks in Brazil, Portugal and the U.K. before expanding to target some of the world’s biggest and most prestigious companies. In recent weeks, Lapsus$ has taken credit for hacks on Samsung Electronics Co. and Nvidia Corp. and has offered to pay employees from companies such as Apple Inc. for help obtaining access.
It also has taken over individual accounts at cryptocurrency exchanges and drained users’ holdings.
Updated: 3-24-2022
Former CPA Pleads Guilty To Helping Bitclub Architect Launder Funds In $722M Ponzi Scheme
The 57-year-old Nevada man pleaded guilty to one count of conspiracy to commit money laundering and one count of aiding in the preparation of a false tax return.
A former accountant is the latest associate of the notorious BitClub Ponzi scheme to plead guilty.
Gordon Brad Beckstead, 57, admitted to helping the architects of the scheme – which defrauded investors of about $722 million over five years – cover their tracks.
The scheme ran from April 2014 to December 2019, when three of the BitClub leaders were arrested and charged with fraud and the sale of unregistered securities. BitClub purported to sell shares of nonexistent crypto mining pools to gullible investors, only to pay them back with money from newer investors, according to the government.
In addition to Beckstead and the architects of the scheme, the government has also nabbed a high-level promoter and a Romanian programmer who designed and operated the site.
Beckstead, who was also an investor in BitClub, said he controlled bank accounts associated with the scheme and its alleged “creator and operator,” Matthew Brent Goettsche, in order to hide Goettsche’s association with the scam and evade tax reporting requirements.
The Nevada man, who is a CPA, also admitted to helping at least two outside tax preparers to create false tax returns for Goettsche in 2017 and 2018. The returns didn’t include over $60 million in income Goettsche received through his role in BitClub.
According to a press release issued by the Department of Justice on Thursday, Beckstead’s tax hijinks shorted the government of $20 million federal income taxes.
Beckstead pleaded guilty to one count of conspiracy to commit money laundering and one count of aiding in the preparation of a false tax return. He faces up to 23 years in prison, as well as a fine.
Bitcoin Veteran Tricks Crypto Scammer Into Learning Lightning
A Bitcoiner called Felix Crisan outfoxed a crypto scammer, getting them to set up a Bitcoin Lightning Wallet before putting them in their place.
There’s poetic justice to scammers getting beat at their own game. A cryptocurrency scammer met their match when trying to trick Bitcoiner Felix Crisan into sending them Tether (USDT).
The scammer tried to impersonate John Carvalho, the CEO of Synonym, a Bitcoiner Cointelegraph regularly cites. The scammer, who we will call “Fake John” from now on, wanted Crisan to send USDT, but Crisan, who’s been learning and getting involved with Bitcoin (BTC) for almost a decade, had other ideas.
Today I’ve convinced a scammer to install a Lightning Network wallet. BTW @BitcoinErrorLog there’s someone impersonating you on Telegram pic.twitter.com/Qd0I9pAney
— felix crisan (@fixone) March 23, 2022
In brief, Crisan, chief technology officer of Netopia Payments, convinced the scammer to install a Lightning Network (LN) wallet, as he only deals with “LN assets.” So, Fake John installed a Bitcoin LN wallet, Blue Wallet. However, instead of sending Fake John the money, Crisan sent a message saying “Eat shit you fucking scammer!”
Justice was duly served — all while providing a free lesson in how to use Bitcoin LN.
On the other hand, it does raise questions as to whether Fake John will continue scamming people but now with Bitcoin LN addresses at their disposal.
The Bitcoin Lightning Network is a fast-growing near-instant layer-2 payment network built on top of the Bitcoin base chain.
It’s brought innovations such as a quick way to pour a pint, while the aforementioned (real) John Carvalho is building his company on Lightning in partnership with Tether.
Crisan told Cointelegraph that he “constantly get DMs shilling one investment scheme or another.” Prudence and precaution are key when interacting and transacting online: Scammers, bots and cryptocurrency shills are commonplace on social media platforms, such as Twitter, while malware bots can sometimes interfere with wallet addresses to steal Bitcoin.
In terms of pursuing and maybe catching the miscreant, Crisan said that “if the scammer opened a channel with this node, then it would be possible. But there are also services that offer sort of on-demand channel creation, so that’s not a very reliable method.” However, ultimately, “only the node operator would be able to do this enhanced tracing.”
It’s not Crisan’s first time playing tricks on scammers. In 2019, he outsmarted a Bitcoin illiterate scammer into sending 21 million (and one) Bitcoin to their address. Bitcoin has a hard cap of 21 million Bitcoin, so the scammer clearly needs to do some homework.
1/ I spent some time today trolling a scammer. At one point I was “ready” to send him 21mil BTC to “trade”. He was being considerate, though, only wanting 100k pic.twitter.com/4sxgf0d4DI
— felix crisan (@fixone) July 7, 2019
The above Tweet thread makes clear that some scammers are misinformed at best, while Bitcoin needs more people like Crisan.
Asked whether Crisan had any advice to share with cryptocurrency and internet users faced with a seemingly constant threat of scams, Crisan told Cointelegraph:
“Avoiding scams should always stem from a common history with the requestor — i.e., to determine if they are who they claim they are — to ask for a common reference. (Yesterday, this type of question was the first I asked this scammer, and the response almost confirmed that he’s not John.)”
Updated: 3-28-2022
Microsoft Security Chief Issues Call To Arms To Protect Metaverse
Hackers will target users with things like faked avatars of people they trust, Bell says.
Microsoft Corp.’s new security chief Charlie Bell issued a call to arms to build protection from hackers and criminals in the emerging metaverse from the start of the new technology.
“There’s going to be a lot of innovation and there will be a lot of struggling to figure out what has to be done,” Bell said in an interview. “But I think because of the speed, there will be fast innovation on the security side.”
The metaverse — a concept that promises to let users live, work and play within interconnected virtual worlds — will present some unique and more serious security challenges for technology and cybersecurity companies.
As an example, hackers may be able to make avatars that look like a user’s trusted contacts, a twist on the traditional email phishing scheme that will be hard for users to resist, he said. The nature of the metaverse, which offers the possibility of less centralized control of content and users, also is a challenge for those trying to protect customers.
“Picture what phishing could look like in the metaverse — it won’t be a fake e-mail from your bank,” wrote Bell, Microsoft’s executive vice president, security, compliance, identity, and management, in a blog posted Monday on Microsoft’s web site. “It could be an avatar of a teller in a virtual bank lobby asking for your information. It could be an impersonation of your CEO inviting you to a meeting in a malicious virtual conference room.”
It’s critical for companies operating in the metaverse, which include Microsoft and Meta Platforms Inc., formerly known as Facebook, to design their new products with security and safety built in from the start, rather than bolted on later, after issues crop up.
With applications likely to run the gamut from games to entertainment to corporate meetings, developers who are building the software and people using it will have to figure out how to police the metaverse, keeping out hackers, abuse, harassment and inappropriate content.
The software companies will need to work together on interoperability of identities — so a user can show they are who they say they are across multiple metaverses — and on other security tools and steps, Bell wrote. Failing to plan ahead may doom the new technology.
“We have one chance at the start of this era to establish specific, core security principles that foster trust and peace of mind for metaverse experiences.
If we miss this opportunity, we’ll needlessly deter the adoption of technologies with great potential for improving accessibility, collaboration, and business,” said Bell, who, until he joined Microsoft in 2021, worked many years for Andy Jassy at Amazon.com Inc.’s cloud unit.
With many metaverse platforms and many apps built on top of them, companies will need to work together to secure the potential gaps and seams between different systems. Tools will need to be designed such as multifactor authentication and customized ways to login without passwords.
Bell also suggested something similar to recent advances in cloud security in which companies offer a single program to manage and watch security and access to multiple cloud programs from different vendors.
Still the decentralized nature of the metaverse can also be an advantage if it means multiple companies bring their security expertise to bear in things like verifying identities and providing transparent bug reports, he said.
Updated: 3-29-2022
Axie Infinity’s Ronin Bridge Hacked For Over $600M
“We are in touch with security teams at major exchanges and will be reaching out to all in the coming days,” said the team at Ronin.
According to Axie Infinity’s official Discord and Ronin Network’s official Twitter thread, along with its Substack page, the Ronin bridge and Katana Dex have been halted after suffering an exploit for 173,600 Ethereum (ETH) and 25.5 million USD Coin (USDC), worth a combined $612 million at Tuesday’s prices.
In a statement, its developers said they are “currently working with law enforcement officials, forensic cryptographers and our investors to make sure that all funds are recovered or reimbursed. All of the AXS, RON and SLP [tokens] on Ronin are safe right now.”
There has been a security breach on the Ronin Network.https://t.co/ktAp9w5qpP
— Ronin (@Ronin_Network) March 29, 2022
As told by Ronin developers, the attacker used hacked private keys in order to forge fake withdrawals, draining the funds from the Ronin bridge in just two transactions.
More importantly, the hack occurred on March 23 but was only discovered on Tuesday after a user allegedly uncovered issues after failing to withdraw 5,000 in ETH from the Ronin bridge. At the time of publication, RON, Ronin’s primary governance token, has fallen nearly 20% to $1.88 in the past hour.
Sky Mavis’ Ronin chain currently consists of nine validator nodes, of which at least five signatures are needed to recognize a deposit or withdrawal event.
The attacker managed to gain control over five private keys, consisting of Sky Mavis’s four Ronin validators and a third-party validator run by Axie Decentralized Autonomous Organization, or DAO. Obtaining unauthorized access to the latter was especially time-consuming.
Last November, when Sky Mavis, the developer of the Axie Infinity and Ronin ecosystems, requested help from the Axie DAO, to distribute free transactions due to a surge in the number of users. The Axie DAO whitelisted Sky Mavis to sign various transactions on its behalf, and the process was discontinued in December. However, access to the whitelist was not revoked.
Once the attacker obtained access to Sky Mavis systems, they acquired the final signature from the Axie DAO validator, thereby completing the node threshold required for the illicit siphoning of funds from Ronin. At the time of publication, most of the hacked funds are still sitting inside the attacker’s wallet.
Updated: 3-30-2022
Apple And Meta Gave User Data To Hackers Who Used Forged Legal Requests
* Hackers Compromised The Emails Of Law Enforcement Agencies
* Data Was Used To Enable Harassment, May Aid Financial Fraud
Apple Inc. and Meta Platforms Inc., the parent company of Facebook, provided customer data to hackers who masqueraded as law enforcement officials, according to three people with knowledge of the matter.
Apple and Meta provided basic subscriber details, such as a customer’s address, phone number and IP address, in mid-2021 in response to the forged “emergency data requests.” Normally, such requests are only provided with a search warrant or subpoena signed by a judge, according to the people. However, the emergency requests don’t require a court order.
Snap Inc. received a forged legal request from the same hackers, but it isn’t known whether the company provided data in response. It’s also not clear how many times the companies provided data prompted by forged legal requests.
Cybersecurity researchers suspect that some of the hackers sending the forged requests are minors located in the U.K. and the U.S. One of the minors is also believed to be the mastermind behind the cybercrime group Lapsus$, which hacked Microsoft Corp., Samsung Electronics Co. and Nvidia Corp., among others, the people said.
City of London Police recently arrested seven people in connection with an investigation into the Lapsus$ hacking group; the probe is ongoing.
An Apple representative referred Bloomberg News to a section of its law enforcement guidelines.
The guidelines referenced by Apple say that a supervisor for the government or law enforcement agent who submitted the request “may be contacted and asked to confirm to Apple that the emergency request was legitimate,” the Apple guideline states.
“We review every data request for legal sufficiency and use advanced systems and processes to validate law enforcement requests and detect abuse,” Meta spokesman Andy Stone said in a statement. “We block known compromised accounts from making requests and work with law enforcement to respond to incidents involving suspected fraudulent requests, as we have done in this case.”
Snap had no immediate comment on the case, but a spokesperson said the company has safeguards in place to detect fraudulent requests from law enforcement.
Law enforcement around the world routinely asks social media platforms for information about users as part of criminal investigations. In the U.S., such requests usually include a signed order from a judge. The emergency requests are intended to be used in cases of imminent danger and don’t require a judge to sign off on it.
Hackers affiliated with a cybercrime group known as “Recursion Team” are believed to be behind some of the forged legal requests, which were sent to companies throughout 2021, according to the three people who are involved in the investigation.
Recursion Team is no longer active, but many of its members continue to carry out hacks under different names, including as part of Lapsus$, the people said.
The information obtained by the hackers using the forged legal requests has been used to enable harassment campaigns, according to one of the people familiar with the inquiry. The three people said it may be primarily used to facilitate financial fraud schemes. By knowing the victim’s information, the hackers could use it to assist in attempting to bypass account security.
Bloomberg is omitting some specific details of the events in order to protect the identities of those targeted.
The fraudulent legal requests are part of a months-long campaign that targeted many technology companies and began as early as January 2021, according to two of the people. The forged legal requests are believed to be sent via hacked email domains belonging to law enforcement agencies in multiple countries, according to the three people and an additional person investigating the matter.
The forged requests were made to appear legitimate. In some instances, the documents included the forged signatures of real or fictional law enforcement officers, according to two of the people. By compromising law enforcement email systems, the hackers may have found legitimate legal requests and used them as a template to create forgeries, according to one of the people.
“In every instance where these companies messed up, at the core of it there was a person trying to do the right thing,” said Allison Nixon, chief research officer at the cyber firm Unit 221B. “I can’t tell you how many times trust and safety teams have quietly saved lives because employees had the legal flexibility to rapidly respond to a tragic situation unfolding for a user.”
On Tuesday, Krebs on Security reported that hackers had forged an emergency data request to obtain information from the social media platform Discord. In a statement to Bloomberg, Discord confirmed that it had also fulfilled a forged legal request.
“We verify these requests by checking that they come from a genuine source, and did so in this instance,” Discord said in a statement. “While our verification process confirmed that the law enforcement account itself was legitimate, we later learned that it had been compromised by a malicious actor. We have since conducted an investigation into this illegal activity and notified law enforcement about the compromised email account.”
Apple and Meta both publish data on their compliance with emergency data requests. From July to December 2020, Apple received 1,162 emergency requests from 29 countries. According to its report, Apple provided data in response to 93% of those requests.
Meta said it received 21,700 emergency requests from January to June 2021 globally and provided some data in response to 77% of the requests.
“In emergencies, law enforcement may submit requests without legal process,” Meta states on its website. “Based on the circumstances, we may voluntarily disclose information to law enforcement where we have a good faith reason to believe that the matter involves imminent risk of serious physical injury or death.”
The systems for requesting data from companies is a patchwork of different email addresses and company portals. Fulfilling the legal requests can be complicated because there are tens of thousands of different law enforcement agencies, from small police departments to federal agencies, around the world. Different jurisdictions have varying laws concerning the request and release of user data.
“There’s no one system or centralized system for submitting these things,” said Jared Der-Yeghiayan, a director at cybersecurity firm Recorded Future Inc. and former cyber program lead at the Department of Homeland Security. “Every single agency handles them differently.”
Companies such as Meta and Snap operate their own portals for law enforcement to send legal requests, but still accept requests by email and monitor requests 24 hours a day, Der-Yeghiayan said.
Apple accepts legal requests for user data at an apple.com email address, “provided it is transmitted from the official email address of the requesting agency,” according to Apple’s legal guidelines.
Compromising the email domains of law enforcement around the world is in some cases relatively simple, as the login information for these accounts is available for sale on online criminal marketplaces.
“Dark web underground shops contain compromised email accounts of law enforcement agencies, which could be sold with the attached cookies and metadata for anywhere from $10 to $50,” said Gene Yoo, chief executive officer of the cybersecurity firm Resecurity, Inc.
Yoo said multiple law enforcement agencies were targeted last year as a result of previously unknown vulnerabilities in Microsoft Exchange email servers, “leading to further intrusions.”
A potential solution to the use of forged legal requests sent from hacked law enforcement email systems will be difficult to find, said Nixon, of Unit 221B.
“The situation is very complex,” she said. “Fixing it is not as simple as closing off the flow of data. There are many factors we have to consider beyond solely maximizing privacy.”
Crypto-Bridge Hacks Reach Over $1 Billion In Little Over A Year
* More Than $21 Billion Locked On Ethereum Bridges, Dune Says
* Ronin Was Built To Handle Surging Demand From Axie Gamers
The $600 million hack this month of a crypto “bridge” supporting Axie Infinity’s play-to-earn video game highlights the increasingly problematic nature of the arcane software used within the world of digital assets, blockchains and the metaverse.
Weaknesses in bridges, which allow tokens designed for one blockchain to be used on another, has led to more than $1 billion in stolen cryptocurrency in a little more than a year across seven different incidents, according to data compiled by researcher Chainalysis.
In the case of the Ronin Bridge, which was recently hacked, the software was adopted to help Axie Infinity’s network accelerate transactions and reduce costs since the underlying Ethereum blockchain wasn’t able to handle the surging demand from gamers quickly or cheaply.
“Bridges, in my opinion, are the single largest potential point of failure in crypto right now,” said Sam Peurifoy, head of interactive at Hivemind Capital, who also leads the play-to-earn guild Kapital DAO in Axie Infinity.
More than $21 billion is locked on Ethereum bridges, data from Dune Analytics show. Just last month, hackers stole around $300 million from Wormhole, a bridge connecting Ethereum to the Solana blockchain. That same month, the Meter Passport bridge got hacked for several million dollars of crypto. In January, Qubit Finance, a project that enables cross-chain function was hacked.
In addition to hacks, bridges have proven to be vulnerable to other unique problems. Last year, the Optics bridge on the Celo network ended up being inoperable after its bridge development team effectively lost control of the project.
It’s often hard to figure out who created a particular bridge or who operates it. Developers can be anonymous, and the names of the validators — a handful of computers that secure the bridge’s transactions — may be purposefully kept secret.
Many are run by organizations with little security staff — it can take days for an issue to be even discovered. At Ronin, the roughly $600 million theft happened on March 23 but was only discovered on March 29.
Bridges are becoming increasingly vulnerable as the value of tokens going through them increases. Some 13 years ago, there was only the Bitcoin blockchain. Now, there are thousands of blockchains, each with its own advantages — such as lower transaction fees — and with its own army of applications, ranging from nonfungible marketplaces to decentralized crypto exchanges.
Investors have to increasingly jump from one chain to another to earn yields or to buy art: Someone who has Ether token may wish to go onto Solana to purchase NFTs or to Polygon to play games, for example.
“I know it sounds like the cross bridges is a bit of a train wreck, but I don’t think it’s as bad as that,” Peter Robinson, a bridge expert at blockchain infrastructure builder ConsenSys, said in an interview before the Ronin hack.
Axie Infinity’s Ronin was built to handle more demand from Axie gamers who are looking for ways to avoid Ethereum’s expensive transaction fees.
“Bridges are an incredibly critical piece of infrastructure at this point,” Kanav Kariya, president of Jump Crypto, said in an interview after the Wormhole hack. “We are strongly moving toward a multi-chain world.”
Back in February, Jump Crypto ended up providing more than $300 million of Ether so Wormhole’s users wouldn’t lose funds. A loss of a bridge can reverberate throughout a small blockchain’s ecosystem of apps, all of which may end up with massive losses.
“We’ve invested billions of dollars into the crypto ecosystem,” Kariya said. “Given the possible ripple effects of such a critical piece of infrastructure having a loss, we thought it was critical to step in in the early stages.”
Ronin’s situation is a bit different. Axie Infinity, created by the Sky Mavis gaming studio, is the chain’s main app, and Sky Mavis also built the Ronin Bridge. The firm said it will reimburse users, also, though exactly how remains unclear.
Ethereum co-founder Vitalik Buterin warned in January that bridges have “fundamental security limits.” Buterin advocates holding native assets on each blockchain they were designed for to keep them safe. But that may not be affordable for many.
One key underlying problem is that most bridges don’t have insurance, and don’t guarantee a reimbursement of funds if they are lost.
“We don’t provide implicit guarantees,” Yat Siu, co-founder of Animoca Brands and an investor in Sky Mavis, said in an interview before the Ronin hack. “We think of it as more of a warranty service. If a product ended up being faulty, if you have a faulty car, we’ll give you back your money.”
13 Apps Removed After Researchers Uncover Trojan Crypto Wallet Scheme
The scheme, which has been in operation since May 2021, targeted Chinese users through social media groups and fake websites.
Research by cybersecurity firm ESET has uncovered a “sophisticated scheme” that disseminates Trojan applications disguised as popular cryptocurrency wallets.
The malicious scheme targets mobile devices using Android or Apple (iOS) operating systems which become compromised if the user downloads a fake app.
According to ESET‘s research, these malicious apps are distributed through bogus websites and imitate legitimate crypto wallets including MetaMask, Coinbase, Trust Wallet, TokenPocket, Bitpie, imToken and OneKey.
The firm also discovered 13 malicious apps impersonating the Jaxx Liberty wallet, available on the Google Play Store. Google has since removed the offending apps installed more than 1,100 times, but there are still many more lurking out there on other websites and social media platforms.
The threat actors disseminated their wares through social media groups on Facebook and Telegram, intending to steal crypto assets from their victims. ESET claims to have uncovered “dozens of trojanized cryptocurrency wallet apps,” going back to May 2021. It also stated that the scheme, which it believes is the work of one group, was primarily targeting Chinese users via Chinese websites.
Lukáš Štefanko, the researcher who unraveled the scheme, said that there were other threat vectors such as sending seed phrases to the attacker’s server using unsecured connections, adding:
“This means that victims‘ funds could be stolen not only by the operator of this scheme but also by a different attacker eavesdropping on the same network.”
The fake wallet apps behave slightly differently depending on where they are installed. On Android, it targets a new cryptocurrency that the user may not have previously traded, prompting the user to install the appropriate wallet.
While on iOS the apps need to be downloaded using arbitrary trusted code-signing certificates circumnavigating Apple’s App Store. This means that the user can have two wallets installed simultaneously, the genuine one and the Trojan, but poses less of a threat since most users rely on App Store verification for their apps.
ESET advises cryptocurrency investors and traders to only install wallets from trusted sources that are linked to the official website of the exchange or company.
In February, Google Cloud unveiled the Virtual Machine Threat Detection system, which scans for and detects “cryptojacking” malware designed to hijack resources to mine digital assets.
According to a January Chainalysis report, cryptojacking accounted for 73% of the total value received by malware-related wallets and addresses between 2017 and 2021.
Binance Suspends Deposits And Withdrawals On Ronin Network After Hack
Gaming-focused Ronin on Tuesday disclosed a loss of more than $625 million in USDC and ether.
Global exchange giant Binance said Wednesdaythat deposits and withdrawals on Axie Infinity’s Ronin Network have been suspended since Tuesday.
Binance said it is assisting with supporting the investigation into the Ronin hack, which could be the largest in decentralized finance history.
* Ronin on Tuesday said an attacker “used hacked private keys in order to forge fake withdrawals” from the Ronin bridge across two transactions, and pegged losses at 173,600 ether (ETH) and 25.5 million USDC, or more than $625 million at current values.
* Besides supporting the Axie Infinity team and law enforcement in the investigation, Binance said it has suspended all deposits and withdrawals on the Ronin network and blocked potential hacker addresses, with a dedicated monitoring team watching for any unusual transactions.
* In addition, Binance has paused withdrawals of wrapped ether (wETH) on the Ethereum network, and the convert function from wETH to ETH.
* The company will reopen deposits and withdrawals on the Ronin network, withdrawals for (wETH) on the Ethereum network, and the convert function from wETH to ETH once it determines the network is stable.
* At press time RON had fallen by 20%, according to data provider CoinGecko.
So You’ve Stolen $600M. Now What?
After one of the largest exploits in DeFi history, the hacker of Axie’s Ronin network has limited options.
The crypto community was rocked Tuesday by what is solidly among the largest hacks in Web 3 history: a $625 million exploit that drained funds from Ronin, the blockchain that is home to the wildly popular Axie Infinity play-to-earn game.
Despite the eye-watering sum, however, experts told CoinDesk in a series of interviews that it’s unlikely the attacker will ever get to enjoy their ill-gotten gains.
On Tuesday, Axie developer Sky Mavis announced in a blog post that the exploit resulted in losses of over 173,000 ETH and 25.5 million USDC, worth more than $625 million at the time of publication.
Immediately after the attack, however, observers noted that the hacker used centralized exchanges to fund the address that launched the attack, and that they have been depositing thousands of ETH to exchanges including Huobi, FTX and Crypto.com – a move that many security experts have characterized as a likely misstep.
Because these platforms have know-your-customer (KYC) verification systems, these deposits could be used to discover the hacker’s identity and ultimately force them to return the funds.
“If I was in their shoes, I would seek to get out of this situation as quickly as possible,” blockchain analytics firm Elliptic co-founder Tom Robinson told CoinDesk. “That might include returning the funds.”
Know Your Exploiter
The attacker’s current method of trying to launder funds through centralized exchanges struck a range of experts across the industry as odd.
“It’s unusual to see such direct flows of funds from thefts to large exchanges,” Robinson said. “They might have purchased accounts, or they could be using an intermediary to launder on their behalf.”
In an exclusive from October, CoinDesk found that there is a flourishing black market for KYC’d accounts at centralized exchanges. However, Robinson noted that the exchanges being used, including FTX and Crypto.com, have strong reputations for regulatory compliance and KYC.
In all, he characterized the attacker’s current efforts to launder their funds as “surprisingly naive.”
“That doesn’t quite match with the sophistication that it would seemingly require to compromise these validators and get their private keys,” he added.
how tf do you steal $600m and send to a cex bruh ????
— FΞYI (@feyi_x) March 29, 2022
A more common strategy from exploiters is to use a mixer like Tornado Cash, send stolen funds through non-KYC’d exchanges and generally “not rushing to cash out everything straight away, maybe waiting years even,” said Robinson.
Indeed, the broader crypto community has expressed befuddlement at the attacker’s laundering strategy.
As is often the case in the aftermath of an attack, Ethereum users have been using the network to communicate with the attacker, and in one case an individual has attempted to give the attacker tips for how to better launder their ETH.
“Hello, [your] initial deposit was from Binance, be careful and be sure to use tornado.cash you must leave the funds in for multiple days or it can be traced,” they wrote to the attacker’s address as part of an Ethereum transaction. “Afterwards you should use stealthex.io to swap to other currencies over a long period of time. Thanks, feel free to tip / retire me.”
However, even with rigorous privacy-preserving tools and a careful plan, Robinson told CoinDesk it’s extraordinarily difficult to launder a sum as large as $600 million.
Indeed, despite the alleged launderers taking a number of precautions over a period of years, U.S. officials seized $3.6 billion in bitcoin related to the 2016 Bitfinex hack just last month.
Fumbling the bag
If Axie does have information on the attacker, identifying hackers has proven to be a successful tactic for developers in the past.
When reached by CoinDesk, blockchain sleuthing firm Chainalysis declined to comment, citing involvement in the ongoing investigation.
You’re talking about GDP-sized figures acquired through hacks.
Last September, in one of the most colorful hacking incidents in blockchain history, developers of the Jay Pegs Auto Mart non-fungible token (NFT) drop successfully intimidated a hacker into returning funds by – among other tactics – ordering miso soup to their house.
Former Sushi Chief Technology Officer Joseph Delong, who was involved with the Jay Pegs negotiations, said that identifying a hacker can help “prevent an anonymous getaway” and will increase public pressure.
“People will get angry at you doxxing the attacker but those cryptoanarchists can go f**k themselves with their superiority complex,” Delong said in a Tuesday interview.
“Laundering $600 million, I don’t think it’s possible,” said Adrian Hetman, a DeFi expert at Immunefi, a bug bounty service. “The best-case scenario is instead of black-hatting your way into the protocol, you should use that knowledge to submit bugs on a bug bounty platform – you could easily become a millionaire.”
Sushi’s Delong also noted that giving the hacker options can be a useful tool, such as a “clear bounty program and partners like Immunefi to help.”
Indeed, Immunefi is among the slew of services that have emerged as DeFi and Web 3 look to secure the ecosystem from the rising tides of hacks.
Immunefi alone has paid out $20 million in bug bounties, and currently has $120 million available for white hats, coding lingo for the benevolent opposite of black-hat hackers who abscond with stolen funds rather than reporting vulnerabilities.
History shows that attempting to steal and launder $625 million may have been the lowest-upside option for the attacker. Last August the hacker who managed to swipe $611 million from Poly Network ultimately returned the funds after deciding it would be impossible to cash out.
“I think either he gets caught, or he’s forced to return the funds. Or both,” said Hetman of the Ronin hacker.
Ideological Motivations
In a worst-case scenario for Axie Infinity, however, the exploiter might not even care about the money at all.
“I think that – fundamentally – the ideology of the exploiter is the key thing to consider when you’re talking about GDP-sized figures acquired through hacks,” said Laurence E. Day, a blockchain developer and scholar. “If they’ve simply done it to send a message about vulnerability or ‘because-they-could, consequences be damned,’ the question ‘was it worth it’ depends on whether they consider that sufficient self-validation as to their skill.”
Day is intimately familiar with hackers looking to send a message. Last October, a protocol Day contributed to, Indexed Finance, was exploited by a Canadian teenage math prodigy, Andean “Andy” Medjedovic.
Despite the team doxing Medjedovic and taking the case to court, the Canadian graduate student has thus far refused to return the funds. In a series of tweets from an account claiming to belong to Medjedovic, he framed the confrontation as a “duel” and a “fight to the death.”
While Medjedovic is currently a fugitive from the law, the incident has earned him significant notoriety, which may have been his primary motivation.
free my homie @ZetaZeroes
— anon (@anon75374998) February 4, 2022
However, Day noted that if the Ronin hacker is interested in fame rather than money, even that end-goal currently appears to be a losing game: They may never be able to claim responsibility without getting caught.
“We’ve seen time and again that ego is the downfall of the people that pull off exploits, and I imagine it’d be quite hard to never be able to own up to it in the same way that negotiating a white-hat bounty and becoming a god in the eyes of the community would allow you to,” said Day.
Sky Mavis Pledges To Reimburse Players Following Axie Infinity Hack
The company behind the popular play-to-earn game made the promise after a $625 million hack.
Sky Mavis, the company behind popular play-to-earn game Axie Infinity, has pledged to reimburse players after hackers stole $625 million from the underlying Ronin blockchain.
“We are committed to ensuring that all of the drained funds are recovered or reimbursed, and we are continuing conversations with our stakeholders to determine the best course of action,” a Sky Mavis spokesperson said in a statement to CoinDesk. Bloomberg first reported on Sky Mavis’ pledge.
The stolen funds included the deposits of players and speculators, plus revenue from the Axie Infinity Treasury, Sky Mavis Chief Operating Officer Aleksander Leonard Larsen told Bloomberg.
The attacker found a backdoor in a Ronin node then used hacked private keys to create withdrawals. The losses included 173,600 ether and $25.5 million in USDC.
AXS, the token behind Axie Infinity, fell as much as 11% after the hack was announced, while the Ronin blockchain token RON fell about 20%. AXS is down 7% over the last 24 hours and has declined over 20% since the announcement of the hack.
Updated: 3-31-2022
Ola Finance Exploited For $3.6M In Re-Entrancy Attack
The attack targeted Fuse Lending, which is an implementation of Ola Finance on the EVM-compatible Fuse blockchain.
Ola Finance disclosed Thursday that it has suffered an exploit that allowed an attacker to grab $3.6 million worth of crypto. The attack targeted Fuse Lending, which attempted to use Ola’s lending-as-a-service protocol with incompatible token standards.
According to PeckShield, a blockchain security firm that worked with Ola to diagnose the exploit, the attacker took advantage of a so-called “re-entrancy” bug in one of Ola’s smart contracts.
The attack comes after this week’s disclosure of a $625 million exploit of Axie Infinity’s Ronin network – one of the largest in decentralized finance (DeFi) history. While much smaller in comparison, the Ola attack stands as a reminder of how multimillion-dollar thefts – now commonplace in DeFi – continue to pile up as big money flows into lesser-known ecosystems.
Ola’s DeFi protocol operates across several blockchains, and Thursday’s attack targeted its deployment on the Fuse network – an Ethereum Virtual Machine-compatible blockchain with a mere $12.8 million in total value locked (TVL) prior to the attack, according to data compiled by DefiLlama.
The attacker began by withdrawing funds using Tornado Cash, which enables users to transfer crypto without leaving a trace. After transferring the funds to the Fuse network, the borrower used them as collateral to take out loans on Ola’s decentralized lending platform. Taking advantage of the re-entrancy bug, the attacker was then able to remove the collateral without first paying back the loan.
We will soon be publishing an official report detailing the exploit that occurred on the @voltfinance Lending Network and the plan for recourse.
Thank you to @peckshield for providing swift coverage and helping us analyze the root of the exploit.
Read Primer ????: https://t.co/UDU10C2YSa
— Ola.finance (@ola_finance) March 31, 2022
The hacker repeated this process several times across different Ola pools. They then transferred the drained funds to wallets on Ethereum and BNB Chain.
Ola has paused the use of its lending protocol on Fuse network and tweeted that it will soon publish an “official report detailing the exploit.” The project says its services on other blockchains were unaffected by the exploit and will remain operational.
This is not the first, nor the largest re-entrancy attack in recent memory.
Little more than two weeks before the Ola attack, two lending protocols on the Gnosis blockchain suffered similar exploits. The DAO attack in 2016, an infamous exploit that led to an Ethereum hard fork, was also a version of a re-entrancy attack.
Expensive Crypto Hacks Are Becoming Part of Web3 Life
Early adopters of decentralized finance have lost millions of dollars in multiple breaches. Who’d want to return after that?
A popular blockchain game called Axie Infinity has suffered what could well be the biggest security breach in the history of decentralized finance.
Hackers forged withdrawals last week from the game’s Ronin Network, which lost approximately $615 million and said it was working with law enforcement to recover the funds and reimburse players, many of whom had to pay hundreds of dollars up front to play. It’s unclear how many were affected.
It’s also postponing the launch of a similar play-to-earn game. The incident points to a mounting challenge for web3, the catchall term describing digital services built on blockchain technology.
A growing list of breaches that stem in part from errors in writing web3 code is upending one of the great promises of blockchain — enhanced security — and holding back the technology’s progress toward mainstream acceptance.
Last August, hackers stole more than $600 million from a blockchain program called Poly Network. Then in February, around $320 million was stolen from a so-called bridge that allowed people to transfer crypto assets between two popular blockchain networks, Solana and Ethereum. In both cases, most, if not all, funds were restored to the original holders.
But DeFi, or the passel of blockchain networks trying to serve as an alternative to traditional financial systems, has become an attractive target for hackers thanks to the billions of dollars locked up in various applications that are also largely run autonomously. (Money stolen in the latest hack had not moved from the wallet of the attackers at the time of writing.)
The amounts lost through hacks of DeFi projects more than doubled in 2021, according to cryptocurrency security firm CertiK. A timeline on security website CryptoSec.Info lists 83 reported breaches of DeFi services, with approximately $2.3 billion lost between January 2020 and February 2022.
For those still willing to invest in web3: Steel yourself for the hacks to keep coming. An investor in Sky Mavis, the developer of Axie Infinity, has said the latest hack should serve as a warning to venture capitalists about underlying security weaknesses in blockchain services, particularly with bridges.
One issue with Ronin was that it worked off-chain, acting as another layer on top of the Ethereum blockchain to conduct transactions more quickly and cheaply. The trade-off: a secondary layer isn’t as secure as the blockchain itself.
Ronin Network did not go into much detail in a blog post about the mechanics of the hack, but the attackers may have taken advantage of a rush to validate a large number of transactions at once, according to Dan Hughes, founder of British DeFi startup Radix.
In other words, Ronin’s attackers may have been exploiting a weakness in the network’s processes rather than a stray bug, pointing to some of the broader difficulties of building blockchain-based apps.
Many developers who create apps for Ethereum use a programming language called Solidity, which is designed for smart contracts, a simple program on a blockchain. But building with Solidity is one of the most complex forms of programming. Coders have to plot out their steps carefully and don’t have multiple tries to get something right.
Making a mistake doesn’t just cause a glitch as it might with a site or app on the traditional web. It can lead to a security vulnerability, and with financial services making up such a high number of web3 apps, that can risk large sums of money too.
“Sometimes something as simple as a typo can be exploited by savvy hackers,” Hughes said in a Twitter Spaces discussion last week with Bloomberg Opinion. He added on Wednesday that it looked unlikely that a coding mistake with smart contracts was behind the cause of Ronin Network’s security breach.
Even so, a recurring string of hacks should serve as a wake-up call for prospective investors, and for web3 companies themselves to invest more in securing their highly complex systems.
Hughes says there’s a prevailing “move fast and break things” culture in web3 development. That could become increasingly dangerous when badly designed algorithms cause financial ruin.
“The problem with hacks is if you build a secure system, there’s hundreds of thousands of ways you have to get it right,” Hughes adds, alluding to an issue that affects web 2.0 as much as web3. “You’ve got to get it right every time. A hacker only one has to get it right once.”
Updated: 4-1-2022
Understanding Crypto Bridges And $1 Billion In Thefts
There’s a reason bridges are more important than an average stretch of road — and why holes in them are more dangerous. As the cryptocurrency world has grown more complex, more and more transactions have come to rely on so-called crypto bridges that enable transactions involving a wide range of tokens.
A roughly $600 million hack of the Ronin bridge in March brought the total stolen from bridges in a year’s time to more than $1 billion, a stark reminder that just because something is useful, fast and cheap doesn’t mean it’s safe.
1. What’s A Crypto Bridge?
A platform that allows tokens designed for one blockchain — the digital ledger that records and verifies transactions conducted using that token — to be used on another. Bridges weren’t needed in crypto’s early days. Some 13 years ago, there was only the Bitcoin blockchain. Now, there are thousands of blockchains, each with its own advantages — such as lower transaction fees — and with its own army of applications, ranging from nonfungible token (NFT) marketplaces to decentralized crypto exchanges.
The rising interest in DeFi, in which users often seek to lend or trade a variety of currencies, has increased the need for mechanisms to bridge the gulf between blockchains. More and more investors are seeking to jump from one chain to another to earn yields or to buy art. Someone who has Ether tokens may wish to go onto blockchains that have lower “gas,” or transaction fees than Ethereum, like Solana, to purchase NFTs, or to Polygon to play games, for example.
2. How Do Crypto Bridges Work?
Most often, by using so-called wrapped coins. Those are tokens that are meant to function as a one-to-one representation of the value of other currencies, similar to stablecoins. Just as a stablecoin like Tether pegs the value of a single token at $1, a token of wrapped Ether is worth whatever a single Ether (the currency of the Ethereum blockchain) is worth.
Bridges typically use so-called smart contracts to automatically convert a user’s currency into a wrapped token that can be used on a different blockchain. But if the underlying Ether deposited with a bridge is stolen, the wrapped Ether becomes worthless.
3. How Big Is The Problem With Bridges?
More than $21 billion is locked on Ethereum bridges, data from Dune Analytics show. On March 23, the Ronin Bridge, which is connected to the popular Axie Infinity online game was attacked, with the hacker stealing 173,600 Ether and 25.5 million USDC tokens in two transactions, for a total take of about $600 million. In February, hackers stole around $300 million from Wormhole, a bridge connecting Ethereum to the Solana blockchain.
That same month, the Meter Passport bridge got hacked for several million dollars of crypto. In January, Qubit Finance, a project that enables cross-chain function was hacked. A total of seven bridge hacks have been recorded, according to data compiled by researcher Chainalysis.
4. Why Are Bridges So Vulnerable?
It’s not only hacks. Bridges have proven to be vulnerable to other unique problems. In 2021, the Optics bridge on the Celo network saw its bridge development team effectively lose control of the project. Figuring out what’s gone wrong or who is responsible for the design or operation of a particular bridge can be hard. Developers can be anonymous, and the names of the validators — a handful of computers that secure the bridge’s transactions — may be purposefully kept secret. Many are run by organizations with little security staff — it can take days for an issue to be even discovered. At Ronin, the theft was only discovered six days later.
5. What Does This Mean For Crypto Users?
They need to be aware that security remains a widespread issue. Fortunately for Wormhole users, its sponsor Jump Crypto ended up covering the bridge’s losses. Axie Infinity creator Sky Mavis said it will cover Ronin Bridge losses, too, without revealing specifics. But such compensation isn’t guaranteed, and shouldn’t be expected. Ethereum co-founder Vitalik Buterin said in January that bridges are insecure, and users need to keep tokens only on blockchains they are native to to stay safe.
Who Hurts Most In $600 Million Axie Heist? ‘Not The Venture Capitalists’
Gamers complain and swap theories about their trapped crypto after an epic breach.
After learning that hackers had made off with an eye-popping $600 million from a software system tied to their beloved Axie Infinity video game, players reacted with shock and disbelief — and for the most part, kept on playing.
In the Philippines and Vietnam, users took to Twitter and Facebook to air everything from complaints about cryptocurrencies frozen in their wallets to conspiracy theories. “I feel sad this happened,” Axie player Joni Watanabe said on Twitter on March 30, the day after the hack was announced.
He added an admonishment to Axie’s operator about using proper security protocols, joining a chorus of crypto gamers clamoring for an explanation of how this could happen — and demanding that it be fixed.
While players can still steer their blob-like Axie creatures around the game’s virtual world of Lunacia in search of Smooth Love Potion (SLP) and Axie (AXS) tokens, one crucial aspect is now missing: The ability to move some crypto earned in the game out of the virtual world and into other digital currencies or fiat, and vice versa.
That’s because the hackers targeted software known as a “bridge,” penetrating its security protocols and making off with a huge haul of Ether as well as USDC stablecoins. That software, called the Ronin Bridge, was designed to allow Axie Infinity users to swap their AXS and SLP into Ether or USDC, an intermediary step to converting them to cash. It’s attached to the Ronin Network, the blockchain Axie Infinity runs on.
Activity on the Ronin Bridge has been paused while its operators investigate the incident and try to plug any security holes, though access to AXS and SLP withdrawals via crypto exchange Binance came back online Saturday. Sky Mavis, Axie Infinity’s owner, says it plans to make whole those players who lost funds in the heist, but has yet to provide further details on how.
A recent exploit on the Wormhole bridge, which transfers tokens between Ethereum and Solana, was resolved when its sponsor Jump Trading replaced roughly $300 million in stolen Ether.
“The easiest way to look at this is like the bridge is the bank for the Ronin Network,” Aleksander Leonard Larsen, chief operating officer of Sky Mavis, said Thursday by text message. “The heist that happened took out all the ETH and USDC. So the ETH/USDC on Ronin Network is not currently backed by anything. But we are looking at other options.”
While Sky Mavis hasn’t said whether the hack has caused an exodus of players from Axie Infinity, blockchain data compiled by DappRadar as of early evening Friday New York time showed a roughly 34% plunge in the volume of trading on the Axie Marketplace in the previous 24 hours and a 24% drop during the prior seven days.
However, that doesn’t necessarily mean game playing is down, because you can still play Axie Infinity without registering transactions on the blockchain, which is what DappRadar monitors, said Pedro Herrera, a senior data analyst at the firm.
Trapped money is a big deal in markets such as the Philippines and Vietnam, low-wage countries where gamers have come to rely on Axie Infinity to pad their incomes. In the Philippines, by far the largest market for Axie Infinity, its popularity has been such that the authorities last year saw fit to remind gamers that profits from playing are subject to tax, local media reported.
A Dec. 10 post on Axie Infinity’s blog, “The Lunacian,” showed the number of daily active users had jumped to around 2.5 million, an increase of roughly 1 million from three months before. The Philippines accounts for about 40% of active players, according to two different third-party websites that track gaming usage.
The carbon footprint from mining Bitcoin and many other (though not all) digital currencies means crypto as a whole typically isn’t associated with the “E” in ESG — short for environmental, social and governance.
But proponents have argued that it easily meets the “S” in that it helps with cheap and instant cross-border transfers in developing countries, or in the case of Axie Infinity, offers the promise of financial gains to those in poverty.
Players Hurting
With a large chunk of Axie Infinity players’ money locked in the virtual realm, that argument gets less convincing. Sky Mavis’s investors include billionaire Mark Cuban, Animoca Brands and Alexis Ohanian, the co-founder of Reddit.
“In terms of who gets harmed the most by this, it’s not the venture capitalists,” said Catherine Flick, associate professor in computing and social responsibility at De Montfort University in the U.K. “Even a few days’ delay in refilling the bridge, that’s going to affect someone feeding their family or paying bills, and in much, much greater a way than having a bit of a blip on someone’s investment portfolio.”
As Axie Infinity grew more popular, the up-front cost of playing by buying a squad of its mini monsters rose too high for some new users to afford. This led to the creation of “scholarship” programs, where Axie players can have their entry cost funded in exchange for providing these backers, known as guilds, with a chunk of their earnings.
What this effectively created was a form of payday lending within the game — and as long as the Ronin bridge remains offline, scholars aren’t able to repay their debts.
“It’s basically indentured labor,” said Flick, noting that Axie Infinity’s developers are still able to reap the benefits of player activity even if the users can’t cash out their earnings. “These games create this kind of two-tier system, further dividing the haves and have-nots.”
Discussions in Axie Infinity’s Discord group showed guild managers complaining that the hack might be a catalyst that causes scholars to lose trust in the game’s earnings potential, similarly affecting their ability to monetize the teams they run.
They lamented a lack of public assurances from Sky Mavis’s investors to date, noting that the delay to re-fund the Ronin bridge has now gone on longer than it took for VCs to step in during other previous high-profile bridge attacks.
Conspiracy Theories
Manh Hung, a 27-year-old from Ho Chi Minh City who’s been playing Axie Infinity for six months, said that because deposits and withdrawals via the Ronin network were suspended after the attack was revealed, he wasn’t able to add Ether or SLP from outside then.
With prices of Axie characters initially falling sharply after the hack announcement, that means he an missed opportunity for bargains, Hung said in a Facebook message. Prices of both SLP and AXS fell more than 10% after the hack news Tuesday before largely recovering by Saturday, according to data from CoinGecko.
Hung, who would only give his first and middle names, said he’s joined several social-media communities for Axie Infinity players. He said they’re rife with conspiracy theories, including that the hack was a “publicity stunt” by the game’s developer, or a convenient excuse to delay the launch of the new “Axie Infinity: Origin” game, as Axie on Thursday announced it would do.
Sky Mavis’s Larsen said the theft was the result of a “social engineering attack combined with a human error,” and that the company doesn’t suspect insider involvement. He told players on Friday that the firm’s “top priority” was to ensure the Ronin bridge was safe and secure before it would reopen for business.
Ronin said on Saturday that the ability to convert tokens into Ether remains closed for the moment, while an exact timeline for the bridge’s reopening is dependent on security audits and updates to the bridge.
Whatever is behind the Ronin Bridge shutdown, it doesn’t change Hung’s calculus. “I still keep playing the game as normal,” he said, adding that he doesn’t plan to alter how he manages his wallets. “I hope the developer will improve the security of Ronin Network.” Others may not be so forbearing.
Police Charge Two U.K. Teenagers Linked To Lapsus$ Hackers
* Teens Aged 16 And 17 Appeared At Court, Were Released On Bail
* Charges Include Counts Of Unauthorized Computer Access, Fraud
Two teenagers who are linked to a probe into the Lapsus$ hackers have been charged by London police in connection with an investigation into hacking.
The pair, aged 16 and 17, who can’t be identified because they are minors, appeared at a London court on Friday afternoon and were released on bail. The two teens will appear at a pretrial hearing at London’s Southwark Crown Court on April 29.
This coincides with a police investigation into the Lapsus$ hacking gang, as Bloomberg has reported. The same police force arrested seven people in connection with the alleged hackers late last month.
One of the crimes alleged by prosecutors against both teens involved hacking into Nvidia Corp.’s systems, while another involved using BT Group Plc and EE mobile phones and SIMS for fraudulent money transfers, court documents show.
“Both teenagers have been charged with: three counts of unauthorized access to a computer with intent to impair the reliability of data; one count of fraud by false representation and one count of unauthorized access to a computer with intent to hinder access to data,” City of London detective inspector Michael O’Sullivan said in the statement.
The 16-year-old has also been charged with a count of causing a computer to perform a function to secure unauthorized access to a program.
City of London Police declined to comment beyond their statement.
Crypto Pundits Gather Online To Discuss Innovation And National Security
Sheila Warren and Jerry Brito joined security expert Juan Zarate to address ways to use cryptocurrency in the national interest.
The George Mason University Antonin Scalia Law School National Security Institute hosted a webinar on Wednesday, March 30, titled “Crypto and National Security: How to Validate American Innovation and Verify U.S. National Security.” Journalist Laura Shin moderated the discussion.
CEO of the Crypto Council for Innovation Sheila Warren, executive director of Coin Center Jerry Brito, and global managing partner and chief strategy officer of risk compliance and monitoring firm K2 Integrity Juan Zarate were participants.
After opening comments, the first of three questions posed to the panel concerned American innovation. Brito expressed hope that crypto would be allowed to develop with open access like the Internet did. He spoke of the process as letting “a thousand flowers bloom.” Zarate spoke of using blockchain technologies “to challenge U.S. adversaries.”
It will be possible, Zarate said, to reinforce U.S. capital markets and the role of the dollar “if we have a say and a hand in how” the technology is developed. He mentioned, in particular, the use of dollar-denominated stablecoin to the nation’s advantage.
The second question concerned regulation. Zarate bemoaned the “shoehorning” approach to crypto regulation, which is based on agencies’ purviews rather than the nature of crypto, while Brito spoke in favor of principle-based regulations. Brito criticized the IRS for being a regulatory “laggard.”
Warren spoke about incentivization and risk, and Zarate rejoined the discussion to say that absolutism — the unwillingness to accept any risk of bad action — is “not how the financial world deals with risk.”
The discussion of the digital yuan proved to be the liveliest, with Brito and Warren sharing their very different perspectives. Brito argued that
“a digital yuan is still a yuan, and nobody wants to hold yuan.”
The Belt and Road Initiative, he said, would not change the attitude toward the Chinese currency. But a “bearer-private” digital dollar could “dollarize the Internet overnight” and “cement dollar dominance in the world,” Brito said. Warren saw a greater threat from the Chinese debt trap for developing countries, which could result in the forced adoption of the digital yuan.
The webinar had an audience of about 100, according to host Jamil Jaffer. It is available for viewing on YouTube.
Updated: 4-2-2022
DeFi Lender Inverse Finance Exploited For $15.6M
It is the third multimillion-dollar crypto attack to make headlines in recent days.
Ethereum-based lending protocol Inverse Finance (INV) said Saturday that it suffered from an exploit, with an attacker netting $15.6 million worth of stolen cryptocurrency.
According to Inverse, the attacker targeted its Anchor (ANC) money market – artificially manipulating token prices to borrow loans against extremely low collateral.
This morning Inverse Finance’s money market, Anchor, was subject to a capital-intensive manipulation of the INV/ETH price oracle on Sushiswap, resulting in a sharp rise in the price of INV which subsequently enabled the attacker to borrow $15.6 million in DOLA, ETH, WBTC, & YFI
— Inverse+ (@InverseFinance) April 2, 2022
This is the third multi-million dollar hack of a decentralized finance (DeFi) protocol to make headlines this week, and it underscores the increasingly sophisticated techniques being levied by attackers.
On Tuesday the gaming-focused Ronin network announced a loss of more than $625 million in crypto and then two days later lending protocol Ola Finance said it was exploited for $3.6 million.
According to blockchain security firm PeckShield, the Inverse attacker took advantage of a vulnerability in a Keep3r price oracle Inverse uses to track token prices. The attacker tricked the oracle into thinking that the price of Inverse’s INV token was extraordinarily high, and then took out multi-million-dollar loans on Anchor using the inflated INV as collateral.
The attack was notably well-financed; in order to pull it off, the attacker first withdrew 901 ETH (about $3 million) from Tornado Cash, which is used to disburse crypto without leaving a clear trail. The attacker then injected the mystery funds into several trading pairs on the decentralized exchange SushiSwap – inflating the price of INV in the eyes of the Keep3r price oracle.
With the price of INV sufficiently high, the attacker then took out INV-backed loans on Anchor before arbitrageurs brought the price of INV back down to normal levels.
A representative from PeckShield noted to CoinDesk that the attack was high-risk, since the $3 million worth of crypto used to trick the price oracle would have been completely lost if the price of INV fell back to normal levels before the attacker took out the loans.
Altogether, the attacker managed to run away with 1,588 ETH, 94 WBTC, 39 YFI and 3,999,669 DOLA. The attacker has cycled most of the funds back through Tornado Cash – meaning it’s difficult to know where the funds will end up – but 73.5 ETH (about $250,000) remains in the attacker’s original Ethereum wallet.
Inverse said in its announcement that it has temporarily paused all borrowing on Anchor, and a representative for the protocol told CoinDesk that it is working with Chainlink to build a new INV oracle.
Inverse also announced that it plans to make a proposal to its decentralized autonomous organization (DAO) to “ensure all wallets impacted by the price manipulation are repaid 100%,” though without providing further details.
Updated: 5-1-2022
Warning: Smartphone Text Prediction Guesses Crypto Hodler’s Seed Phrase
Redditor Andre highlighted the ease with which hackers can use the text prediction feature to drain a user’s funds just by being able to first word out of the BIP 39 list.
Seed phrases, a random combination of words from the Bitcoin Improvement Protocol (BIP) 39 list of 2048 words, act as one of the primary layers of security against unauthorized access to a user’s crypto holdings. But, what happens when your “smart” phone’s predictive typing remembers and suggests the words next time you try to access your digital wallet?
Andre, a 33-year-old IT professional from Germany, recently posted on the r/CryptoCurrency subreddit after discovering his mobile phone’s ability to predict the entire recovery seed phrase as soon as he typed down the first word.
As a fair warning to fellow Redditors and crypto enthusiasts, Andre’s post highlighted the ease with which hackers can use the feature to drain a user’s funds just by being able to type the first word out of the BIP 39 list:
“This makes it easy to attack, get your hands on a phone, start any chat app, and start typing any words off the BIP39 list, and see what the phone suggests.”
Speaking to Cointelegraph, Andre, otherwise known as u/Divinux on Reddit, shared his shock when he first experienced his phone literally guessing the 12-24 word seed phrase. “First, I was stunned. The first couple words could be a coincidence, right?”
As a tech-savvy individual, the German crypto investor was able to reproduce the scenario wherein his mobile phone could accurately predict the seed phrases. After realizing the possible impact of this information if it went out to the wrong hands, “I thought I should tell people about it. I’m sure there are others who also have typed seeds into their phone.”
Andre’s experiments confirmed that Google’s GBoard was the least vulnerable as the software did not predict every word in the correct order. However, Microsoft’s Swiftkey keyboard was able to predict the seed phrase right out of the box. The Samsung keyboard, too, can predict the words if “Auto replace” and “Suggest text corrections” have been manually turned on.
Andre’s initial stint with crypto dates back to 2015 when he momentarily lost interest until he realized he could buy goods and services using Bitcoin (BTC) and other cryptocurrencies.
His investment strategy involves purchasing and staking BTC and altcoins such as Terra (LUNA), Algorand (ALGO) and Tezos (XTZ) and “then dollar-cost averaging out into BTC when/if they moon.” The IT professional also develops his own coins and tokens as a hobby.
A safety measure against possible hacks, according to Andre, is to store significant and long-term holdings in a hardware wallet. To Redditors across the world, he advises “not your keys not your coins, do your own research, don’t FOMO, never invest more than you are willing to lose, always double-check the address you are sending to, always send a small amount beforehand and disable your PMs in settings,” concluding:
“Do yourself a solid and prevent that from happening by clearing your predictive type cache.”
Blockchain security firm PeckShield warned the crypto community about a large number of phishing websites targeting users of the Web3 lifestyle app STEPN.
As Cointelegraph recently reported, based on PechShield’s findings, hackers insert a forged MetaMask browser plugin through which they can steal seed phrases from unsuspecting STEPN users.
Access to seed phrase guarantees complete control over the user’s crypto funds via the STEPN dashboard.
What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,What Are The Biggest,
Related Articles:
Bitcoin Information & Resources (#GotBitcoin?)
Coinbase Accidentally Saves Unencrypted Passwords Of 3,420 Customers (#GotBitcoin?)
Bitcoin Is A ‘Chaos Hedge, Or Schmuck Insurance‘ (#GotBitcoin?)
Bakkt Announces September 23 Launch Of Futures And Custody
Coinbase CEO: Institutions Depositing $200-400M Into Crypto Per Week (#GotBitcoin?)
Researchers Find Monero Mining Malware That Hides From Task Manager (#GotBitcoin?)
Crypto Dusting Attack Affects Nearly 300,000 Addresses (#GotBitcoin?)
A Case For Bitcoin As Recession Hedge In A Diversified Investment Portfolio (#GotBitcoin?)
SEC Guidance Gives Ammo To Lawsuit Claiming XRP Is Unregistered Security (#GotBitcoin?)
15 Countries To Develop Crypto Transaction Tracking System: Report (#GotBitcoin?)
US Department Of Commerce Offering 6-Figure Salary To Crypto Expert (#GotBitcoin?)
Mastercard Is Building A Team To Develop Crypto, Wallet Projects (#GotBitcoin?)
Canadian Bitcoin Educator Scams The Scammer And Donates Proceeds (#GotBitcoin?)
Amazon Wants To Build A Blockchain For Ads, New Job Listing Shows (#GotBitcoin?)
Shield Bitcoin Wallets From Theft Via Time Delay (#GotBitcoin?)
Blockstream Launches Bitcoin Mining Farm With Fidelity As Early Customer (#GotBitcoin?)
Commerzbank Tests Blockchain Machine To Machine Payments With Daimler (#GotBitcoin?)
Man Takes Bitcoin Miner Seller To Tribunal Over Electricity Bill And Wins (#GotBitcoin?)
Bitcoin’s Computing Power Sets Record As Over 100K New Miners Go Online (#GotBitcoin?)
Walmart Coin And Libra Perform Major Public Relations For Bitcoin (#GotBitcoin?)
Judge Says Buying Bitcoin Via Credit Card Not Necessarily A Cash Advance (#GotBitcoin?)
Poll: If You’re A Stockowner Or Crypto-Currency Holder. What Will You Do When The Recession Comes?
1 In 5 Crypto Holders Are Women, New Report Reveals (#GotBitcoin?)
Beating Bakkt, Ledgerx Is First To Launch ‘Physical’ Bitcoin Futures In Us (#GotBitcoin?)
Facebook Warns Investors That Libra Stablecoin May Never Launch (#GotBitcoin?)
Government Money Printing Is ‘Rocket Fuel’ For Bitcoin (#GotBitcoin?)
Bitcoin-Friendly Square Cash App Stock Price Up 56% In 2019 (#GotBitcoin?)
Safeway Shoppers Can Now Get Bitcoin Back As Change At 894 US Stores (#GotBitcoin?)
TD Ameritrade CEO: There’s ‘Heightened Interest Again’ With Bitcoin (#GotBitcoin?)
Venezuela Sets New Bitcoin Volume Record Thanks To 10,000,000% Inflation (#GotBitcoin?)
Newegg Adds Bitcoin Payment Option To 73 More Countries (#GotBitcoin?)
China’s Schizophrenic Relationship With Bitcoin (#GotBitcoin?)
More Companies Build Products Around Crypto Hardware Wallets (#GotBitcoin?)
Bakkt Is Scheduled To Start Testing Its Bitcoin Futures Contracts Today (#GotBitcoin?)
Bitcoin Network Now 8 Times More Powerful Than It Was At $20K Price (#GotBitcoin?)
Crypto Exchange BitMEX Under Investigation By CFTC: Bloomberg (#GotBitcoin?)
“Bitcoin An ‘Unstoppable Force,” Says US Congressman At Crypto Hearing (#GotBitcoin?)
Bitcoin Network Is Moving $3 Billion Daily, Up 210% Since April (#GotBitcoin?)
Cryptocurrency Startups Get Partial Green Light From Washington
Fundstrat’s Tom Lee: Bitcoin Pullback Is Healthy, Fewer Searches Аre Good (#GotBitcoin?)
Bitcoin Lightning Nodes Are Snatching Funds From Bad Actors (#GotBitcoin?)
The Provident Bank Now Offers Deposit Services For Crypto-Related Entities (#GotBitcoin?)
Bitcoin Could Help Stop News Censorship From Space (#GotBitcoin?)
US Sanctions On Iran Crypto Mining — Inevitable Or Impossible? (#GotBitcoin?)
US Lawmaker Reintroduces ‘Safe Harbor’ Crypto Tax Bill In Congress (#GotBitcoin?)
EU Central Bank Won’t Add Bitcoin To Reserves — Says It’s Not A Currency (#GotBitcoin?)
The Miami Dolphins Now Accept Bitcoin And Litecoin Crypt-Currency Payments (#GotBitcoin?)
Trump Bashes Bitcoin And Alt-Right Is Mad As Hell (#GotBitcoin?)
Goldman Sachs Ramps Up Development Of New Secret Crypto Project (#GotBitcoin?)
Blockchain And AI Bond, Explained (#GotBitcoin?)
Grayscale Bitcoin Trust Outperformed Indexes In First Half Of 2019 (#GotBitcoin?)
XRP Is The Worst Performing Major Crypto Of 2019 (GotBitcoin?)
Bitcoin Back Near $12K As BTC Shorters Lose $44 Million In One Morning (#GotBitcoin?)
As Deutsche Bank Axes 18K Jobs, Bitcoin Offers A ‘Plan ฿”: VanEck Exec (#GotBitcoin?)
Argentina Drives Global LocalBitcoins Volume To Highest Since November (#GotBitcoin?)
‘I Would Buy’ Bitcoin If Growth Continues — Investment Legend Mobius (#GotBitcoin?)
Lawmakers Push For New Bitcoin Rules (#GotBitcoin?)
Facebook’s Libra Is Bad For African Americans (#GotBitcoin?)
Crypto Firm Charity Announces Alliance To Support Feminine Health (#GotBitcoin?)
Canadian Startup Wants To Upgrade Millions Of ATMs To Sell Bitcoin (#GotBitcoin?)
Trump Says US ‘Should Match’ China’s Money Printing Game (#GotBitcoin?)
Casa Launches Lightning Node Mobile App For Bitcoin Newbies (#GotBitcoin?)
Bitcoin Rally Fuels Market In Crypto Derivatives (#GotBitcoin?)
World’s First Zero-Fiat ‘Bitcoin Bond’ Now Available On Bloomberg Terminal (#GotBitcoin?)
Buying Bitcoin Has Been Profitable 98.2% Of The Days Since Creation (#GotBitcoin?)
Another Crypto Exchange Receives License For Crypto Futures
From ‘Ponzi’ To ‘We’re Working On It’ — BIS Chief Reverses Stance On Crypto (#GotBitcoin?)
These Are The Cities Googling ‘Bitcoin’ As Interest Hits 17-Month High (#GotBitcoin?)
Venezuelan Explains How Bitcoin Saves His Family (#GotBitcoin?)
Quantum Computing Vs. Blockchain: Impact On Cryptography
This Fund Is Riding Bitcoin To Top (#GotBitcoin?)
Bitcoin’s Surge Leaves Smaller Digital Currencies In The Dust (#GotBitcoin?)
Bitcoin Exchange Hits $1 Trillion In Trading Volume (#GotBitcoin?)
Bitcoin Breaks $200 Billion Market Cap For The First Time In 17 Months (#GotBitcoin?)
You Can Now Make State Tax Payments In Bitcoin (#GotBitcoin?)
Religious Organizations Make Ideal Places To Mine Bitcoin (#GotBitcoin?)
Goldman Sacs And JP Morgan Chase Finally Concede To Crypto-Currencies (#GotBitcoin?)
Bitcoin Heading For Fifth Month Of Gains Despite Price Correction (#GotBitcoin?)
Breez Reveals Lightning-Powered Bitcoin Payments App For IPhone (#GotBitcoin?)
Big Four Auditing Firm PwC Releases Cryptocurrency Auditing Software (#GotBitcoin?)
Amazon-Owned Twitch Quietly Brings Back Bitcoin Payments (#GotBitcoin?)
JPMorgan Will Pilot ‘JPM Coin’ Stablecoin By End Of 2019: Report (#GotBitcoin?)
Is There A Big Short In Bitcoin? (#GotBitcoin?)
Coinbase Hit With Outage As Bitcoin Price Drops $1.8K In 15 Minutes
Samourai Wallet Releases Privacy-Enhancing CoinJoin Feature (#GotBitcoin?)
There Are Now More Than 5,000 Bitcoin ATMs Around The World (#GotBitcoin?)
You Can Now Get Bitcoin Rewards When Booking At Hotels.Com (#GotBitcoin?)
North America’s Largest Solar Bitcoin Mining Farm Coming To California (#GotBitcoin?)
Bitcoin On Track For Best Second Quarter Price Gain On Record (#GotBitcoin?)
Bitcoin Hash Rate Climbs To New Record High Boosting Network Security (#GotBitcoin?)
Bitcoin Exceeds 1Million Active Addresses While Coinbase Custodies $1.3B In Assets
Why Bitcoin’s Price Suddenly Surged Back $5K (#GotBitcoin?)
Zebpay Becomes First Exchange To Add Lightning Payments For All Users (#GotBitcoin?)
Coinbase’s New Customer Incentive: Interest Payments, With A Crypto Twist (#GotBitcoin?)
The Best Bitcoin Debit (Cashback) Cards Of 2019 (#GotBitcoin?)
Real Estate Brokerages Now Accepting Bitcoin (#GotBitcoin?)
Ernst & Young Introduces Tax Tool For Reporting Cryptocurrencies (#GotBitcoin?)
Recession Is Looming, or Not. Here’s How To Know (#GotBitcoin?)
How Will Bitcoin Behave During A Recession? (#GotBitcoin?)
Many U.S. Financial Officers Think a Recession Will Hit Next Year (#GotBitcoin?)
Definite Signs of An Imminent Recession (#GotBitcoin?)
What A Recession Could Mean for Women’s Unemployment (#GotBitcoin?)
Investors Run Out of Options As Bitcoin, Stocks, Bonds, Oil Cave To Recession Fears (#GotBitcoin?)
Goldman Is Looking To Reduce “Marcus” Lending Goal On Credit (Recession) Caution (#GotBitcoin?)

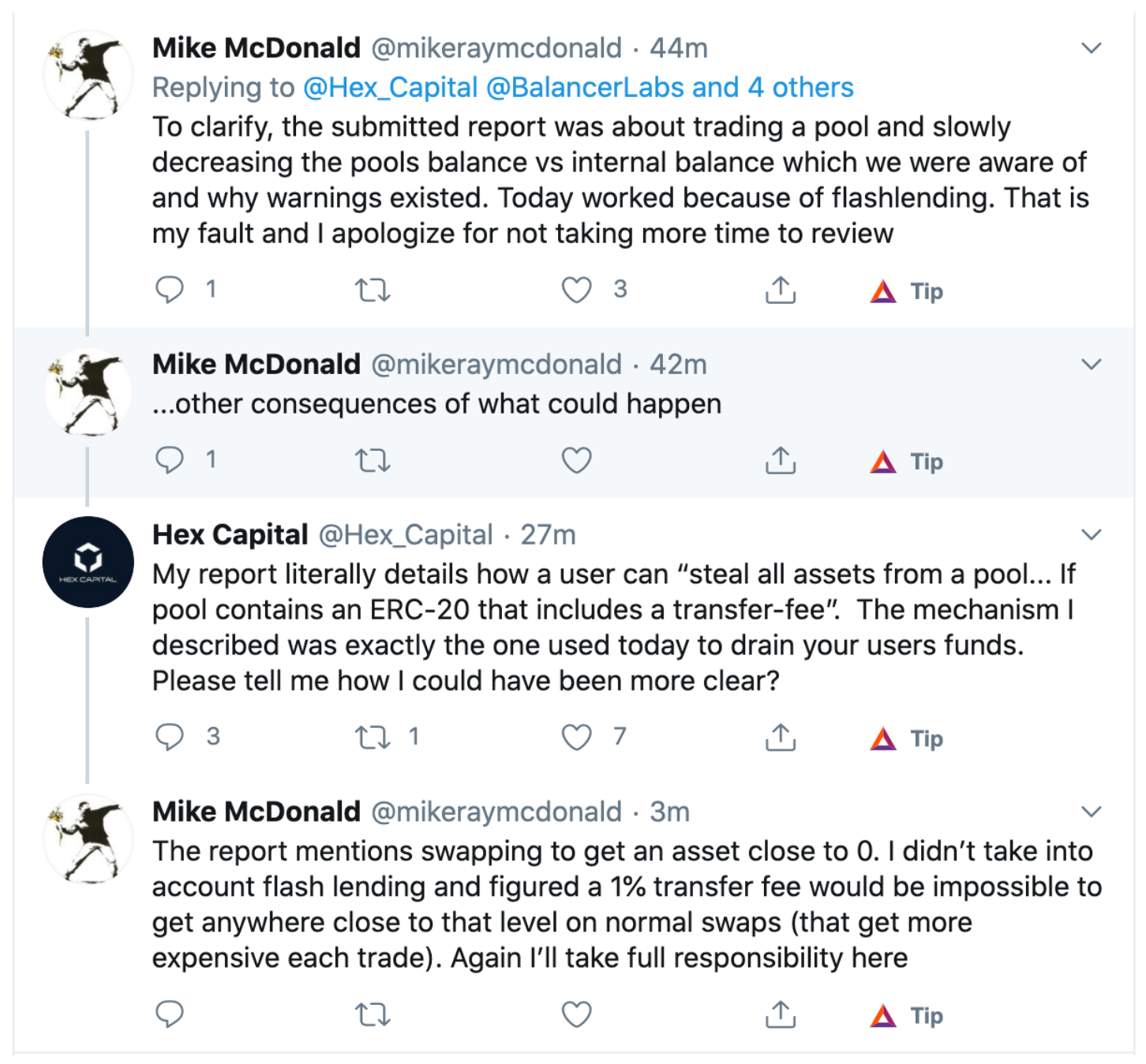
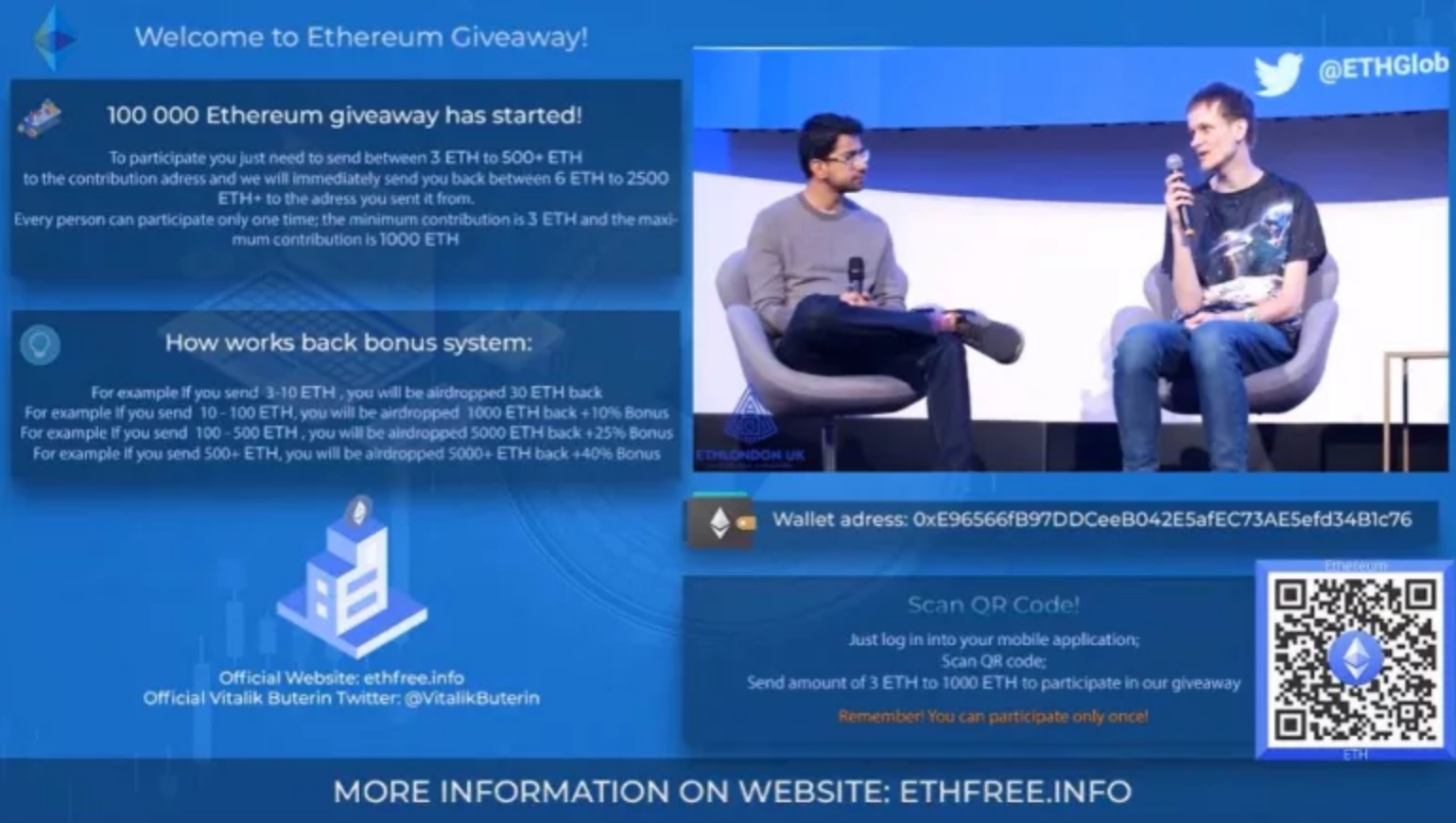
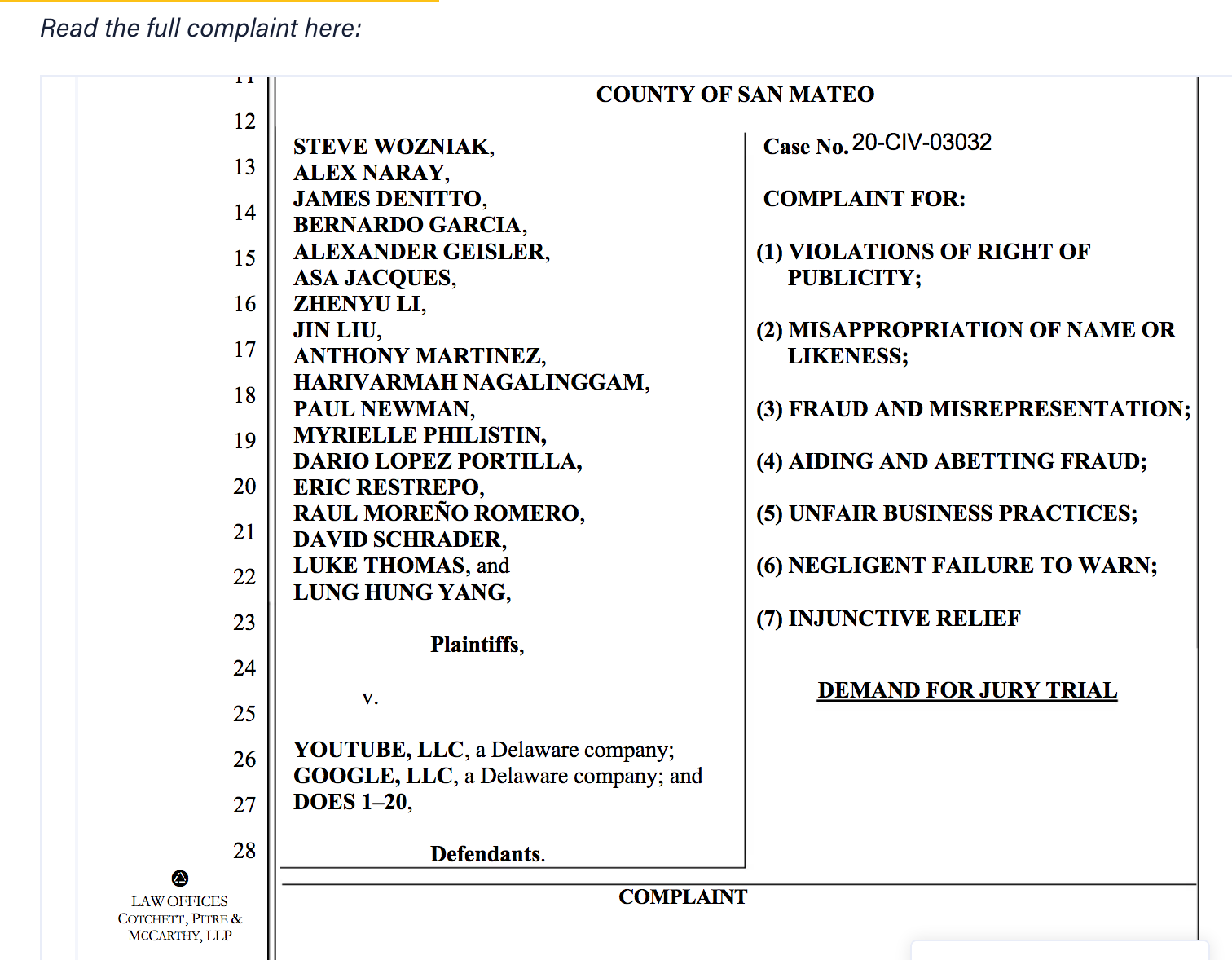
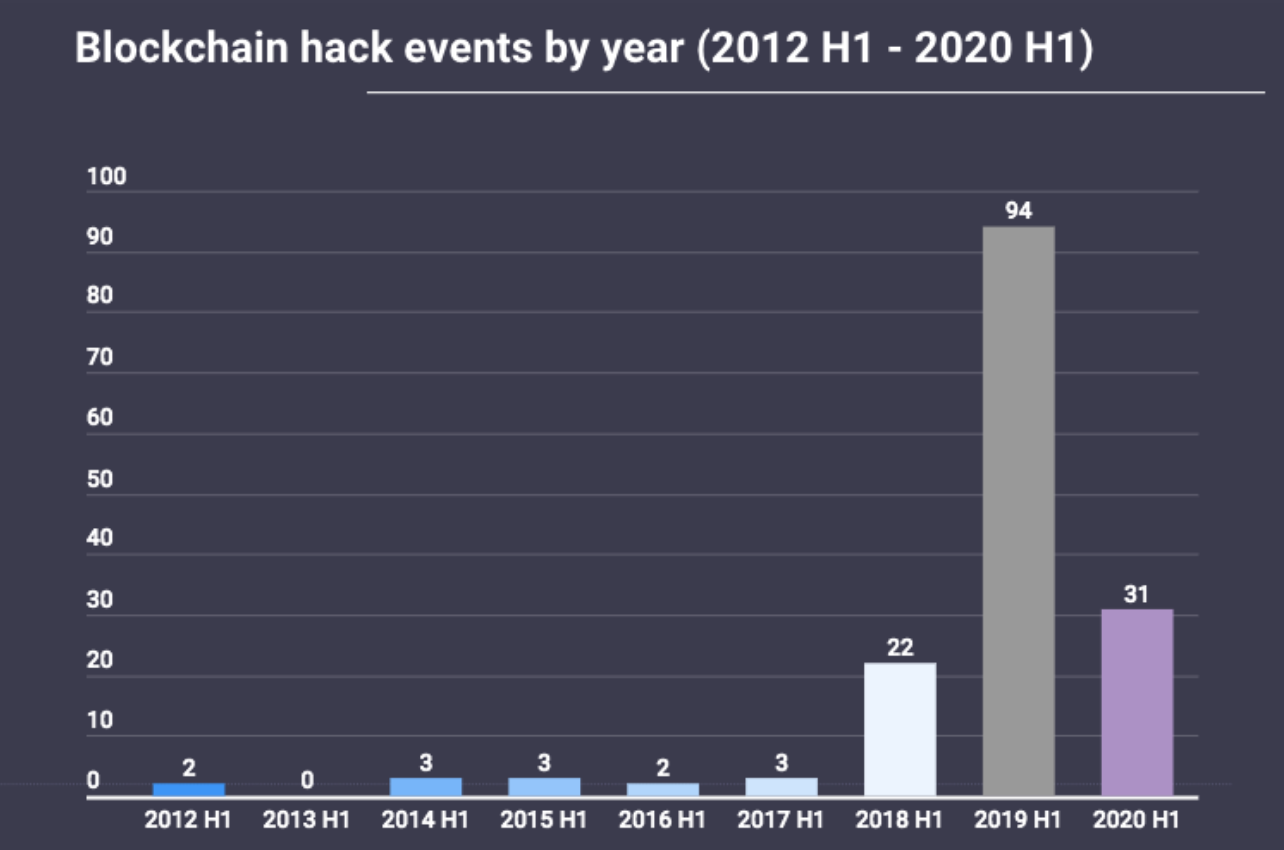
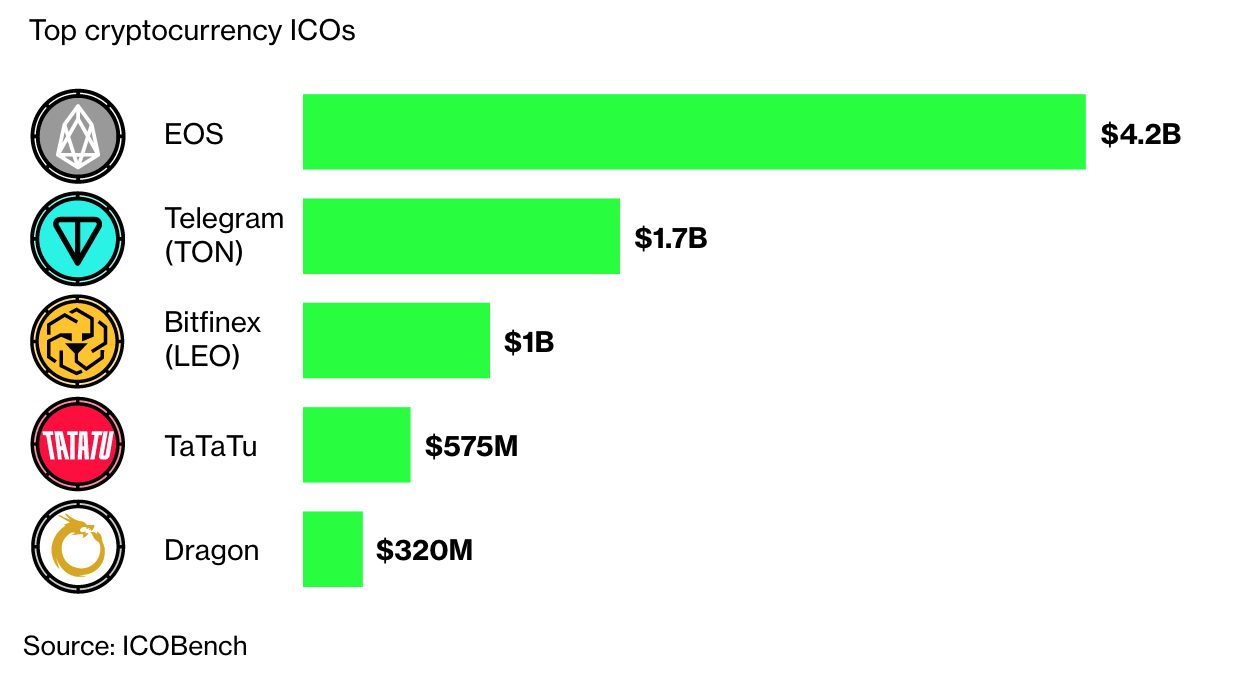
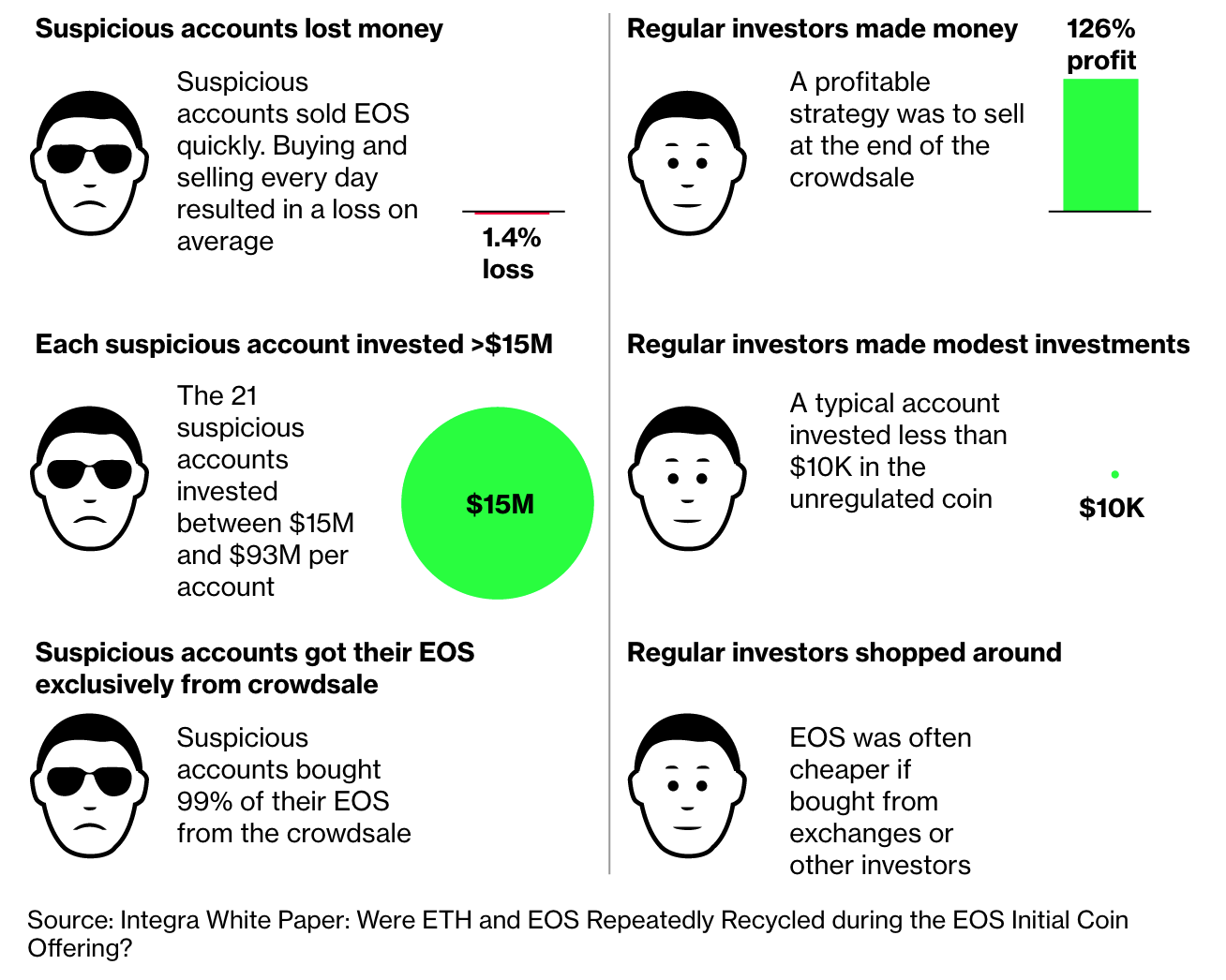
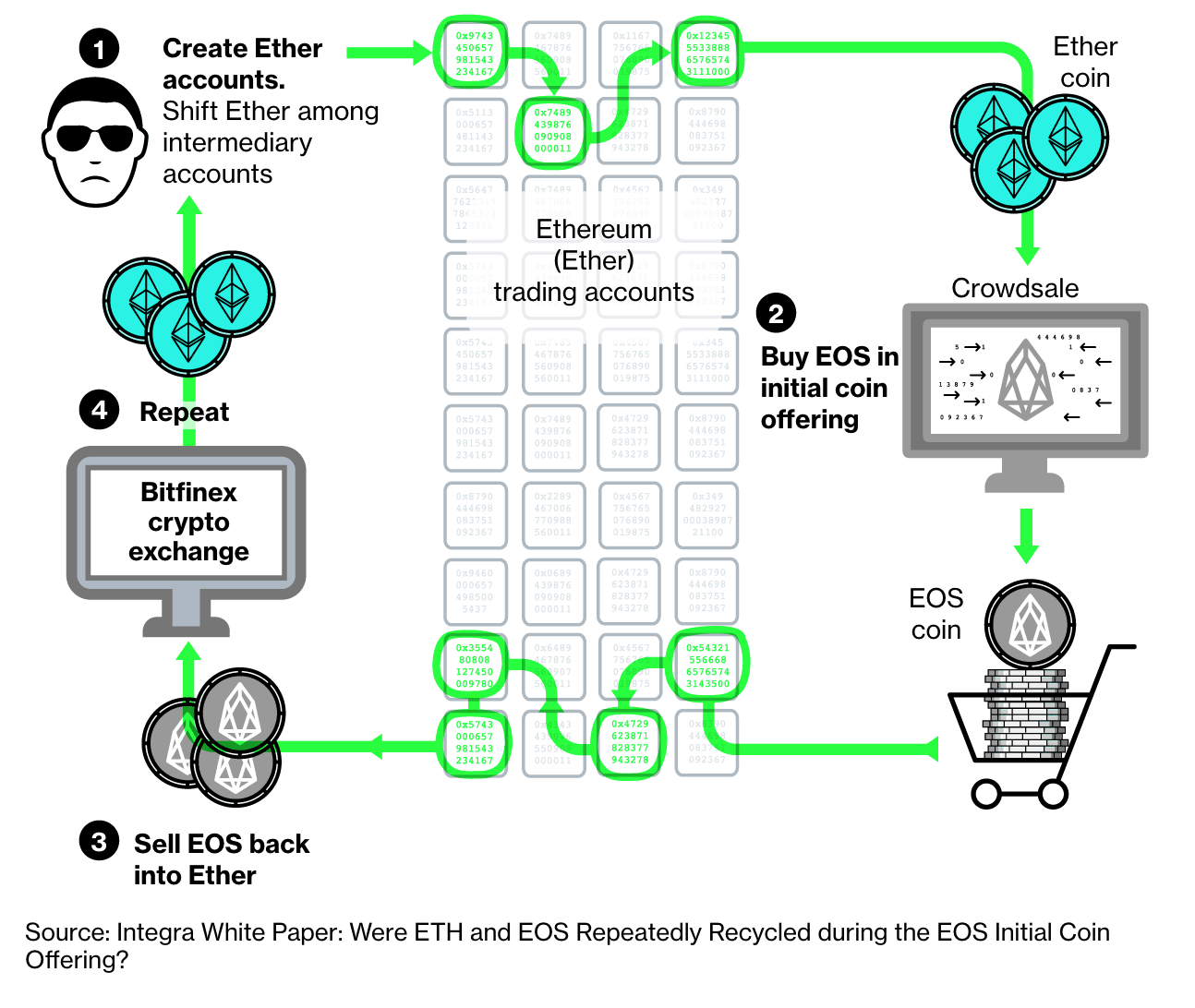

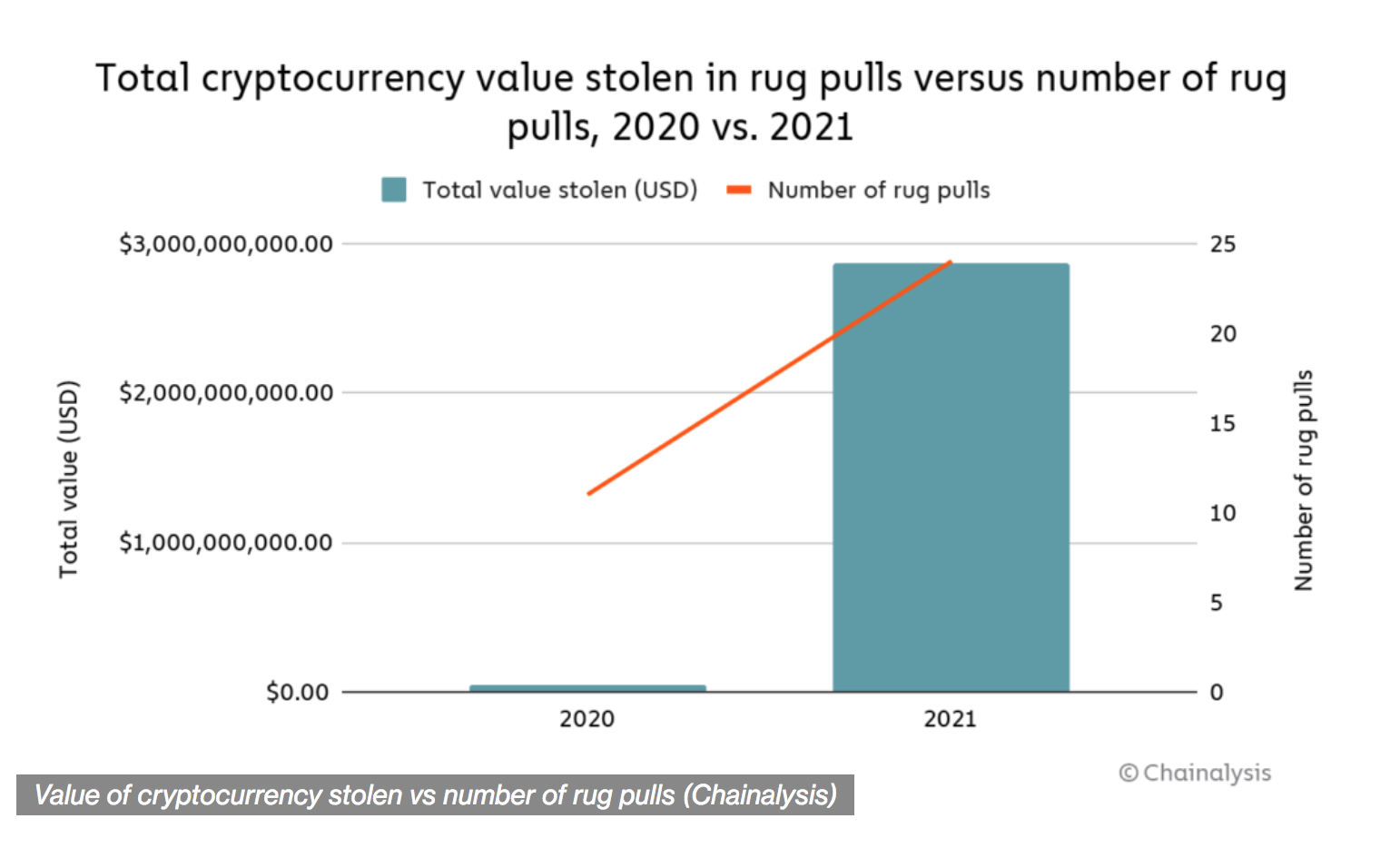
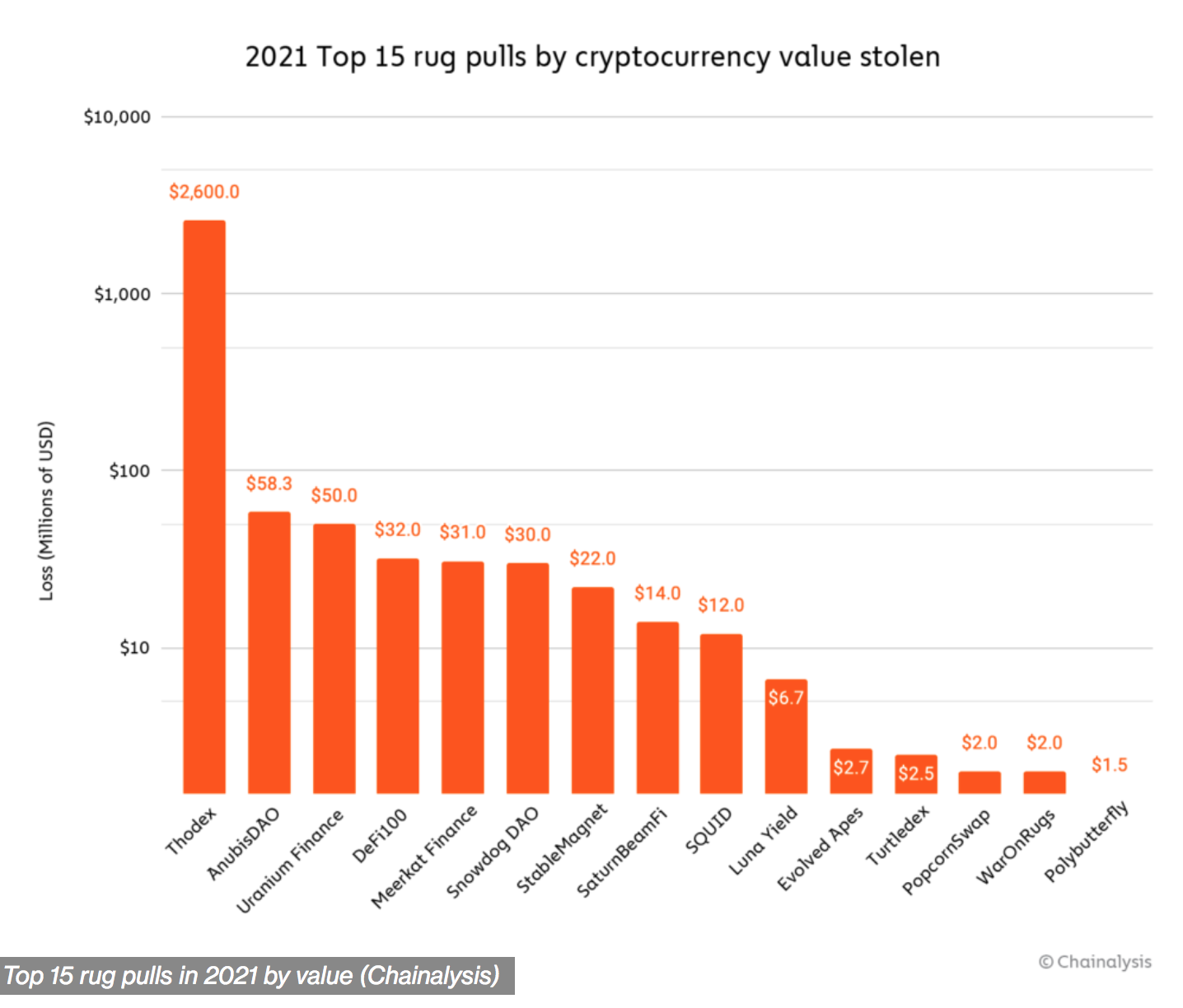
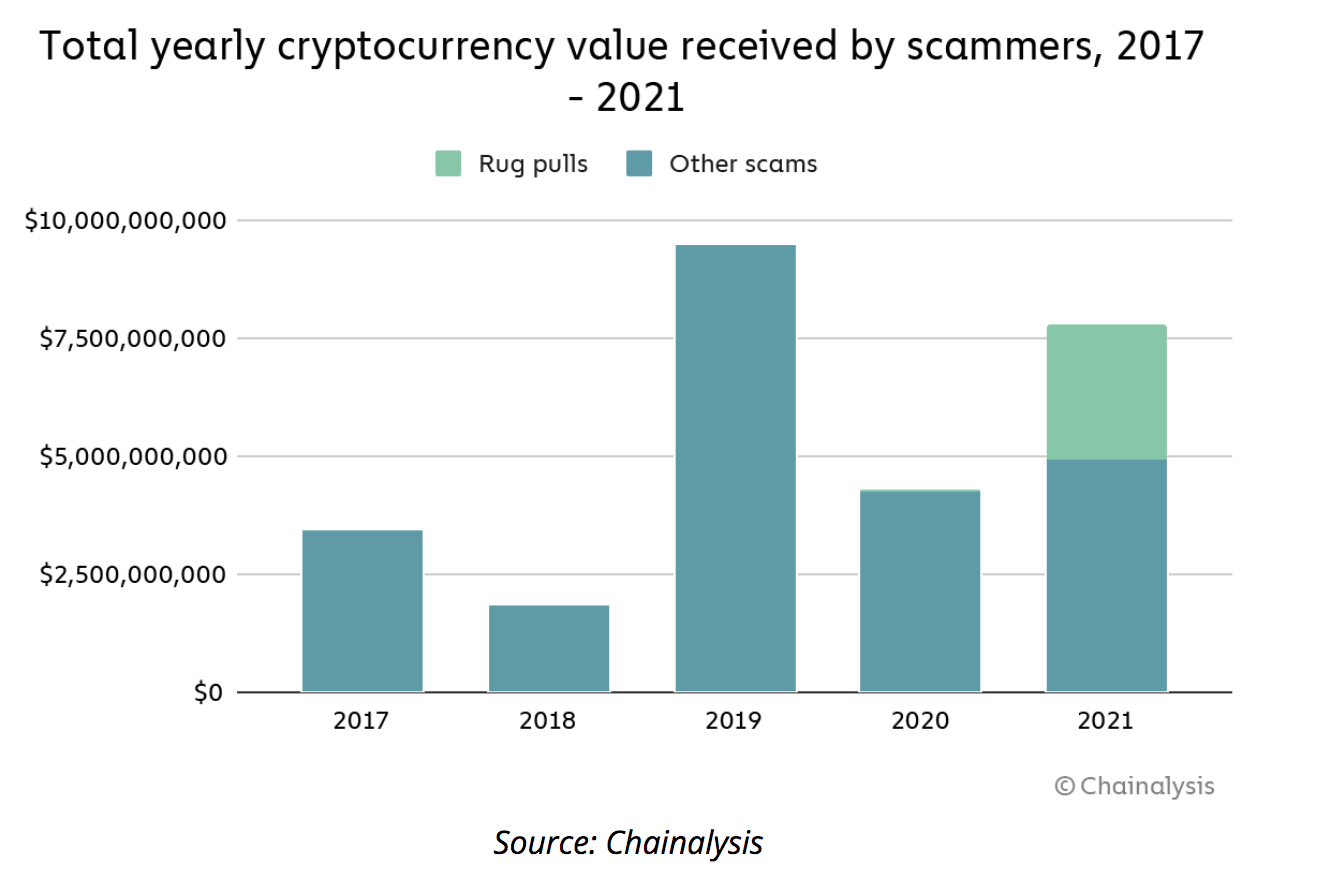
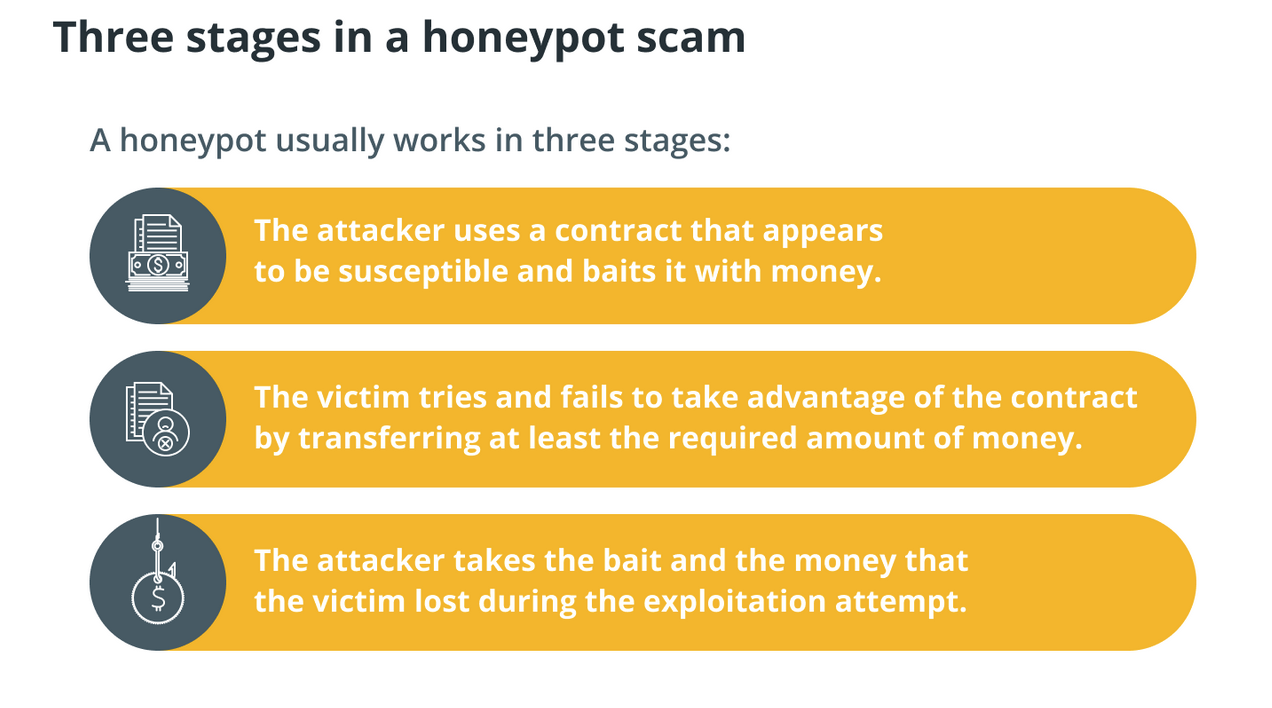
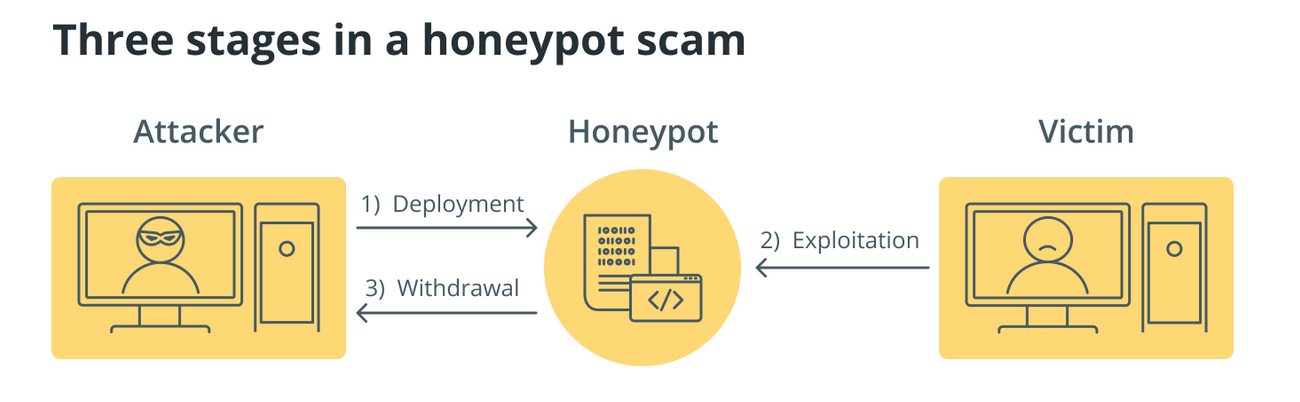


Leave a Reply
You must be logged in to post a comment.