Ultimate Resource For Crypto-Currency Ransomware, Hacks And Malware Attacks (#GotBitcoin)
Cybersecurity company Varonis has discovered a new cryptojacking virus, dubbed “Norman,” that aims to mine the cryptocurrency Monero (XMR) and evade detection. Ultimate Resource For Crypto-Currency Ransomware, Hacks And Malware Attacks (#GotBitcoin)
Varonis published a report about Norman on Aug.14. According to the report, Varonis found Norman as one of many cryptojacking viruses deployed in an attack that infected machines at a mid-size company.
Related:
Accenture Confirms Hack After LockBit Ransomware Data Leak Threats
US Taps Amazon, Google, Microsoft, Others To Help Fight Ransomware, Cyber Threats
US Fights Ransomware With Crypto Tracing, $10 Million Bounties
Russia ‘Cozy Bear’ Breached GOP As Ransomware Attack Hit
REvil Ransomware Hits 200 Companies In MSP Supply-Chain Attack
It Wasn’t Until Anonymous Payment Systems That Ransomware Became A Problem
UK Cyber Chief Cameron Says Ransomware Key Online Threat
A New Ransomware Enters The Fray: Epsilon Red
This Massive Phishing Campaign Delivers Password-Stealing Malware Disguised As Ransomware
Kia Motors America Victim of Ransomware Attack Demanding $20M In Bitcoin, Report Claims
Hackers and cybercriminals deploy cryptojacking hardware to use the computing power of unsuspecting users’ machines to mine cryptocurrencies like the privacy oriented coin Monero.
Norman in particular is a crypto miner based on XMRig, which is described in the report as a high-performance miner for Monero cryptocurrency. One of the key features of Norman is that it will close the crypto mining process in response to a user opening up Task Manager. Then, after Task Manager closes, Norman uses a process to relaunch the miner.
The researchers at Varonis concluded that Norman is based on the PHP programming language and is obfuscated by Zend Guard. The researchers also conjectured that Norman comes from a French-speaking country, due to the presence of French variables and functions within the virus’ code.
Additionally, there are French comments within the self-extracting archive (SFX) file. This indicates, according to the report, that Norman’s creator used a French version of WinRAR to create the SFX file.
Beyond Crypto-jacking
Another cybersecurity company uncovered an unsettling update to a strain of XMR mining malware last week. Carbon Black discovered that a type of malware called Smominru is now stealing user data alongside its mining operations.
The firm believes that the stolen data may be sold by hackers on the dark web. In its report, Carbon Black wrote:
“This discovery indicates a bigger trend of commodity malware evolving to mask a darker purpose and will force a change in the way cybersecurity professionals classify, investigate and protect themselves from threats.”
Updated: 9-27-2019
New Malware Swaps Out Crypto Wallet Addresses As You Type Them
A new bit of malware called Masad Stealer can replace wallet addresses as you type them thanks to malicious code injected into your browser. According to Juniper Networks, it also steals:
- PC And System Information
- Credit Card Browser Data
- Browser Passwords
- Installed Software And Processes
- Desktop Files
- Screenshot Of Desktop
- Browser Cookies
- Steam Files
- Autofill Browser Fields
- Discord And Telegram Data
- Filezilla Files
The program dumps this information to the malware controller’s Telegram account, ensuring relative security for the data it steals. It can also clip and change monero, litecoin, zcash, dash and ethereum addresses automatically and uses special search functions to pinpoint these addresses on your clipboard. Once it swaps the addresses it can intercept crypto as its being sent to legitimate wallets.
The particular version of the malware Juniper studied sent crypto to this wallet which currently contains almost a one full bitcoin.
“Based on our telemetry, Masad Stealer’s main distribution vectors are masquerading as a legitimate tool or bundling themselves into third party tools,” wrote the research organization.
“Threat actors achieve end user downloads by advertising in forums, on third party download sites or on file sharing sites.”
The software masquerades as useful-looking software like Tradebot_binance.exe, Galaxy Software Update.exe, and Fortniteaimbot 2019.exe. Once infected, the computer then begins communicating with the command and control Telegram channel and sends back private data.
The malware allegedly costs $40 on the dark web and is completely configurable and very dangerous, said Juniper.
“Juniper Threat Labs believes that Masad Stealer represents an active and ongoing threat.
Command and Control bots are still alive and responding as of this writing, and the malware appears to still be available for purchase on the black market,” wrote the researchers.
New Bitcoin Wallet-Focused Trojan Uncovered By Security Researchers
A new Remote Access Trojan (RAT) malware that steals Bitcoin (BTC) wallet data has been discovered by security researchers, according to a Sept. 12 report from Zscaler ThreatLabZ.
The RAT, dubbed InnfiRAT, is designed to perform a wide range of tasks on the infected machines, including specifically seeking out Bitcoin and Litecoin (LTC) wallet data.
A Multi-Pronged Attack On Infected Systems
As the researchers note, InnfiRAT is written in .NET, a software framework developed by Microsoft and used to develop a wide range of applications.
The malware is designed to access and steals personal data stored on victims’ computers — grabbing browser cookies to steal stored usernames and passwords, as well as session data. It can also take screenshots to steal information from open windows and scour the system for other running applications to target.
Once collected, the data is sent to a command-and-control (C&C) server, requesting further instructions, which can include downloading additional payloads onto the infected system.
Zscaler ThreatLabZ Details How The Rat Is Designed To Retrieve Bitcoin Wallet Data As Follows:
“The Malware Creates An Empty List Of The Bitcoinwallet Type Where Bitcoinwallet Has Two Keys, Namely:
‘WalletArray’
‘WalletName’
A Check Is Performed To See If A File For A Litecoin Or Bitcoin Wallet Is Present In The System At The Following Location:
Litecoin: %AppData%\Litecoin\wallet.dat
Bitcoin: %AppData%\Bitcoin\wallet.dat
If it is found, then the element of type BitcoinWallet is added to the list after assigning a name to the WalletName key and reading the corresponding wallet file in the WalletArray key.
Finally, the created list is sent in response to the C&C server.”
Caution Against Untrusted Sources
In conclusion, the security researchers warn of the prevalence of RATs such as InnfiRAT, which can be designed to not only to access and steal confidential data but also to log keystrokes, activate a system’s webcam, format drives and spread to other systems on a given network.
They note that systems are usually infected by a RAT by downloading infected applications or email attachments, warning users not to download programs or open attachments from unknown sources.
As reported this summer, Zscaler ThreatLabZ had previously published its discovery of another RAT called Saefko, also written in .NET and designed to retrieve browser history and look for activities including cryptocurrency transactions.
Updated: 10-2-2019
Zcash Bug Could Reveal Shielded Full Nodes’ IP Addresses
A bug in all Zcash (ZEC) implementations and most of its forks could leak metadata containing the full nodes’ with shielded addresses (zaddr) IPs.
Komodo (KMD) core developer Duke Leto disclosed the bug in a blog post published on his personal website. A Common Vulnerabilities and Exposures (CVE) code has already been assigned to track the issue on Sept. 27. Leto explained:
“A bug has existed for all shielded addresses since the inception of Zcash and Zcash Protocol. It is present in all Zcash source code forks. It is possible to find the IP address of full nodes who own a shielded address (zaddr). That is, Alice giving Bob a zaddr to be paid, could actually allow Bob to discover Alice’s IP address. This is drastically against the design of Zcash Protocol.”
Per the announcement, everyone who published their zaddr or provided it to a third party could be affected by the vulnerability. Leto claims that users should consider their “IP address and geo-location information associated with it as tied to […] zaddr.”
Multiple Cryptocurrencies Affected
According to Leto, users who never used a zaddr, only used it over the Tor Onion Routing network or only to send funds, are not affected. Furthermore, Leto also claims that Zcash is not the only cryptocurrency affected and provides a non-exhaustive list.
The cryptocurrencies included in the list are Zcash, Hush, Pirate, Komodo smart chains with zaddr enabled by default, Safecoin, Horizen, Zero, VoteCoin, Snowgem, BitcoinZ, LitecoinZ, Zelcash, Ycash, Arrow, Verus, Bitcoin Private, ZClassic and Anon. Leto also points out that Komodo has already disabled the shielded addresses feature and transitioned it to the Pirate chain, which means that KMD no longer contains the bug.
As Cointelegraph recently reported, Electric Coin Company, which launched and supports the development of privacy-coin Zcash, recently published a paper describing a trustless cryptographic system called Halo.
Updated: 10-4-2019
$160 Malware Botnet Tries To Steal Crypto From 72,000 Devices
Around 72,000 devices in 2019 alone were infected during a suspiciously cheap yet successful malware campaign to steal cryptocurrency, new data warns.
Mastermana Continues To Spread
According to the research report published by cyberintelligence company Prevailion on Oct. 2, the MasterMana botnet uses budget Russian malware that is delivered as a Trojan via a phishing email scam.
The malware itself likely costs just $100, though the hackers also required a virtual public server at a cost of $60.
Despite costing just around $160 in total, MasterMana achieved considerable success, Prevailion warned, concluding that the bad actors behind it reached 2,000 devices each week since December 2018. The researchers noted:
“This campaign’s threat actors saw an opportunity and appear to have carved out a nice niche for themselves. We suspect that this particular threat actor is likely to continue operations, as previous public reporting has not deterred them, therefore we wanted to highlight their new modus operandi, so that network defenders may more easily identify their operations.”
Threats Abound For Crypto Users
The malware works by arriving as an infected document in a phishing email. If a user opens the document, it would trigger a series of events which would create backdoors to steal any cryptocurrency holdings in associated hot wallets.
The resurgence in the price of cryptocurrencies this year has led to new threats being detected on an almost weekly basis.
Just last week, cybersecurity experts warned about a new spyware which used encrypted messenger Telegram to replace user wallet addresses with its own.
Recently, major Slovakia-based antivirus software provider ESET has discovered a banking trojan that can steal cryptocurrencies and is especially widespread in Latin America.
As Cointelegraph reported, estimates put the total amount raised by cybercriminals this year at $4.3 billion.
HackerOne User Reveals Critical Bug Through MakerDAO Bounty Program
MakerDAO, the decentralized organization that runs on Ethereum, has fixed a critical bug that could have resulted in a complete loss of funds for all Dai users.
$50,000 bounty
On Oct. 1 HackerOne user lucash-dev disclosed a report that revealed a critical bug in MakerDAO’s planned Multi-Collateral Dai (MCD) upgrade. The bug could have allowed an attacker to steal all of the collateral stored in the MCD system – possibly within a single transaction, Lucash-dev said.
The bug was caught during the testing phase of the MCD upgrade and before any users had access to the system.
The report reveals that the attack was possible due to a complete lack of access control in a MakerDAO smart contract. The report reads:
“A lack of validation in the method flip.kick allows an attacker to create an auction with a fake bid value. Since the end contract trusts that value, it can be exploited to issue any amount of free Dai during liquidation. That Dai can then be immediately used to obtain all collateral stored in the end contract.”
Lucash-dev reported the security flaw via the HackerOne forum and received a $50,000 bounty from MakerDAO’s bounty program which was the first critical finding in the program.
MakerDAO Gives Grant To Freelance Employment Platform
Cointelegraph reported in September that blockchain-based employment platform Opolis received a developer grant from MakerDAO, which will allow them to bring MakerDao’s stablecoin DAI to Opolis’ blockchain-based employment platform for freelancers.
Richard Brown, head of community development at MakerDAO, explained that while the freelance and gig economy offers freedom to many, it does not come without its downsides, and added:
“Maker is looking forward to seeing how Dai can help de-risk this emerging workforce.”
Updated: 10-14-2019
N. Korean Hackers’ New MacOS Malware Hides Behind Fake Crypto Firm
The notorious North Korean hackers known as the Lazarus APT Group have created another malware targeting Apple Macs that masquerades behind a fake cryptocurrency firm.
Apple Mac security specialist and principal security researcher at Jamf Patrick Wardle published a blog post on Oct. 12 outlining the nature of the malware, revealed by MalwareHunterTeam (MHT) researchers the previous day.
Closely Related To Earlier Macos Crypto-Malware
MHT and Wardle have warned that at the time of their warning, the malware was undetected by any engines on VirusTotal and that the sample appears to be closely related to a strain of Mac malware created by the Lazarus Group and identified by Kaspersky Labs back in summer 2018.
Like the previous strain, the hackers have set up a fake cryptocurrency firm — this time dubbed “JMT Trading” — through which to perpetrate their attack. Having written an open-source cryptocurrency trading app, they uploaded its code on GitHub, concealing the malware within it.
Wardle analyzed the installation process for the app, identifying the suspicious package and launch daemon concealed within it and analyzing the malicious functionality of the hackers’ backdoor script.
While the backdoor affords a remote attacker complete command and control over infected macOS systems, Wardle notes that open-source security tools and manual detection processes by alerted users should have no issue detecting the malware. However, he reiterated his warning that VirusTotal engines were not picking it up at the time of writing.
He also considers that the most likely targets of the malware are crypto exchange employees, rather than everyday retail investors.
Cyber Villains
As reported, the allegedly North Korean state-sponsored Lazarus Group has achieved infamy for its malign activities. As of fall 2018, the group was estimated to have stolen a staggering $571 million in cryptocurrencies since early 2017 and was accused of involvement in the industry record-breaking $532 million NEM hack of Japanese exchange Coincheck.
This September, Anne Neuberger — director of the United States’ National Security Agency (NSA) Cybersecurity Directorate — singled out North Korea as being particularly creative in its cyber warfare strategy, pointing to the rogue state’s alleged use of cryptocurrency to compile funds for President Kim Jong-Un’s regime.
Updated: 10-17-2019
Hackers Use Malicious Code in WAV Audio Files To Mine Cryptocurrencies
Threat researchers have discovered malicious code in WAV audio files, code that hackers use to mine cryptocurrencies.
Hackers Earn Thousand Of Dollars Per Month
On Oct. 16, researchers at BlackBerry Cylance, a software company that develops anti-virus programs, reported the discovery of malicious code hidden within WAV audio files. This type of malware campaign, where hackers conceal malware codes in ordinary-looking files, is known as steganography.
The analysis showed that some of the WAV files contained code to deploy malware for financial gain and establish remote access within the victim machine. The report reads:
“When played, some of the WAV files produced music that had no discernible quality issues or glitches. Others simply generated static (white noise).”
The malicious WAV files allow hackers to deploy CPU miners onto the victim’s device, which steals processing resources and generates thousands of dollars per month from mining cryptocurrency. For that reason, crypto miners are a popular malware payload amongst hackers as they provide financial benefit while operating in the background without the user’s knowledge — an attack commonly called crypto-jacking.
North Korean Hackers Target Apple Macs
Cointelegraph previously reported that the notorious North Korean hackers known as the Lazarus APT Group have created another malware that targets Apple Macs and hides behind a fake cryptocurrency firm. Researchers said that at the time of their warning, the malware was undetected by any engines on VirusTotal. The sample appeared to be closely related to a strain of Mac malware identified by Kaspersky Labs back in summer 2018.
Updated: 10-18-2019
Fake Tor Browser Steals Bitcoin From Darknet Users, Warns ESET
Major antivirus software supplier ESET has discovered a trojanized Tor Browser designed to steal Bitcoin (BTC) from buyers in the darknet.
Fake Browser Distributed Via 2 Websites
Targeting users in Russia, the fake Tor Browser was distributed via two websites and has been stealing crypto from darknet shoppers by swapping the original crypto addresses since 2017, ESET’s editorial division WeLiveSecurity reported Oct. 18.
Created back in 2014, the two fake Tor Browser websites — tor-browser[.]org and torproect[.]org — are mimicking the real website of the anonymous browser, torproject.org.
According to the Slovakian software security firm, these websites display a message that users have an outdated version of Tor Browser even if they have the most up-to-date Tor Browser version, offering to download the fake version containing malware.
Over $40,000 Stolen In Bitcoin
According to the firm, the newly discovered malware has been distributed for Windows, while there are no signs that the same websites have distributed Linux, macOS or mobile versions.
After being installed, the malicious Tor Browser automatically swaps users’ crypto addresses to the addresses controlled by criminals.
According to ESET, the total amount of received funds for all three wallets allegedly involved in the campaign accounted for 4.8 Bitcoin so far. One of the reported wallets contains 2.66 BTC at press time with the latest transaction in September 2019.
In addition to Bitcoin, the campaign has also been stealing money by altering QIWI wallets, the firm said.
Related Warnings
In early October, ESET flagged another form of malware stealing crypto from users. Called “Casbaneiro” or “Metamorfo,” the banking trojan targets banks and crypto services located in Brazil and Mexico and has allegedly stolen 1.2 BTC to date.
Meanwhile, Tor Browser users have already been warned about potential money losses due to security breaches. In mid-September, Finnish peer-to-peer crypto exchange LocalBitcoins warned Tor users about the risks of using Tor Browser, claiming that Tor Browser exposes them to the risks of having their Bitcoin stolen.
Updated: 10-21-2019
Zcash Community Discovers Likely Malicious Fake Version of ZecWallet
Members of the Zcash (ZEC) community have discovered a suspicious and potentially malicious counterfeit version of Zcash Foundation’s native ZecWallet.
According to a Twitter post published on Oct. 20 and retweeted by Zcash developer Electric Coin Company, the fake ZecWallet likely contains malware. The tweet reads:
“PSA to all Zcash users! There is a fake version of ZecWallet that likely contains malware (size and checksum is different) double check you are downloading from official @zecwallet repo on GitHub: https://github.com/ZcashFoundation/zecwallet”
As Cointelegraph reported on Sept. 29, a bug was found in all Zcash implementations and most of its forks that could leak metadata containing the full nodes’ with shielded addresses IPs.
On Oct. 18, major antivirus software supplier ESET has discovered a “trojanized” version of Tor Browser designed to steal Bitcoin (BTC) from buyers in the darknet.
Targeting users in Russia, the fake Tor Browser was distributed via two websites and has been stealing crypto from darknet shoppers by swapping the original crypto addresses since 2017.
Earlier in October, ESET also flagged another form of malware stealing crypto from users. Called “Casbaneiro” or “Metamorfo,” the banking trojan targeted banks and crypto services located in Brazil and Mexico and has allegedly stolen 1.2 BTC at the time.
Updated: 11-19-2019
Malware on Official Monero Website Can Steal Crypto: Investigator
The software available for download on Monero’s (XMR) official website was compromised to steal cryptocurrency, according to a Nov. 19 Reddit post published by the coin’s core development team.
The command-line interface (CLI) tools available at getmonero.org may have been compromised over the last 24 hours. In the announcement, the team notes that the hash of the binaries available for download did not match the expected hashes.
The Software Was Malicious
On GitHub, a professional investigator going by the name of Serhack said that the software distributed after the server was compromised is indeed malicious, stating:
“I can confirm that the malicious binary is stealing coins. Roughly 9 hours after I ran the binary a single transaction drained the wallet. I downloaded the build yesterday around 6pm Pacific time.”
An Important Security Practice
Hashes are non-reversible mathematical functions which, in this case, are used to generate an alphanumeric string from a file that would have been different if someone was to make changes to the file.
It is a popular practice in the open-source community to save the hash generated from software available for download and keep it on a separate server. Thanks to this measure, users are able to generate a hash from the file they downloaded and check it against the expected one.
If the hash generated from the downloaded file is different, then it is likely that the version distributed by the server has been replaced — possibly with a malicious variant. The Reddit announcement reads:
“It appears the box has been indeed compromised and different CLI binaries served for 35 minutes. Downloads are now served from a safe fallback source. […] If you downloaded binaries in the last 24h, and did not check the integrity of the files, do it immediately. If the hashes do not match, do NOT run what you downloaded.”
In general, blockchain development communities are vigilant in tracking possible vulnerabilities and maintaining network integrity.
In mid-September, the developer of Ethereum decentralized exchange protocol AirSwap’s developers announced a different important development for their project’s security. More precisely, they revealed the discovery of a critical vulnerability in the system’s new smart contract.
In order to incentivize network integrity, some organizations have founded bounty programs that reward so-called white-hack hackers for exposing vulnerabilities.
Updated: 11-27-2019
Cyber Criminals Are Using YouTube To Install Cryptojacking Malware
Slovakian software security firm Eset has uncovered that cyber criminals behind the Stantinko botnet have been distributing a Monero (XMR) cryptocurrency mining module via Youtube.
On Nov. 26, the major antivirus software supplier Eset reported that the Stantinko botnet operators have expanded their criminal reach from click fraud, ad injection, social network fraud and password stealing attacks, into installing crypto malware on victims’ devices using Youtube.
Stantinko Botnet Has Been Active Since At Least 2012
The Stantinko botnet, which has been active since at least 2012 and predominantly targets users in Russia, Ukraine, Belarus and Kazakhstan, reportedly uses YouTube channels to distribute its cryptojacking module, which mines the privacy-focused crypto coin Monero on the CPUs of unsuspecting victims.
This cryptocurrency-stealing malware has reportedly infected around 500,000 devices, and is similar to the recently discovered malicious malware, Dexphot, malware discovered by Microsoft that has already infected more than 80,000 computers.
These crypto-hijacking codes steal processing resources, take over legitimate system processes and disguise the nefarious activity with the ultimate goal of running a crypto miner on the infected devices.
Eset informed YouTube, which reportedly responded by removing all the channels that contained traces of Stantinko’s code.
Malware On Monero’s Official Website Was Stealing Crypto
In November, Monero’s core development team said that the software available for download on Monero’s official website might have been compromised to steal cryptocurrency. A professional investigator going by the name of Serhack confirmed that the software distributed after the server was compromised was indeed malicious:
“I can confirm that the malicious binary is stealing coins. Roughly 9 hours after I ran the binary a single transaction drained the wallet. I downloaded the build yesterday around 6pm Pacific time.”
Upodated: 12-4-2019
Researchers Detect New North Korea-Linked MacOS Malware on Crypto Trading Site
Security researchers have discovered a new cryptocurrency-related macOS malware believed to be the product of North Korean hackers at the Lazarus Group.
As tech-focused publication Bleeping Computer reported on Dec. 4, malware researcher Dinesh Devadoss encountered a malicious software on a website called “unioncrypto.vip,” that advertised a “smart cryptocurrency arbitrage trading platform.” The website did not cite any download links, but hosted a malware package under the name “UnionCryptoTrader.”
Linkage To North Korean Hackers
According to the researchers, the malware can retrieve a payload from a remote location and run it in memory, which is not common for macOS, but more typical for Windows. This feature makes it difficult to detect the malware and carry out forensic analysis. Per VirusTotal, an online service for analyzing and detecting viruses and malware, only 10 antivirus engines flagged it as malicious at press time.
After conducting an analysis of the newly detected malware, security researcher Patrick Wardle determined “clear overlaps” with malware found by MalwareHunterTeam in mid-October, which purportedly led to the Lazarus group. At the time, the researchers detected that Lazarus had created another malware targeting Apple Macs that masquerades behind a fake cryptocurrency firm.
Recent North Korea-related Developments
In recent months, there has been plenty of news about North Korea-related developments. In late November, United States prosecutors announced the arrest of Virgil Griffith, who allegedly traveled to North Korea to deliver a presentation on how to use crypto and blockchain technology to circumvent sanctions.
Following the arrest, Ethereum (ETH) co-founder Vitalik Buterin declared his solidarity with Virgil Griffith, having supported a petition to free the blockchain developer.
The United Nations Security Council’s Sanctions Committee on North Korea accused the country of using a Hong Kong-based blockchain firm as a front to launder money.
Updated: 12-5-2019
Texas-Based Data Center CyrusOne Hit by Ransomware Attack
Texas-based data center provider CyrusOne has reportedly fallen victim to an attack from REvil (Sodinokibi) ransomware, business tech-focused publication ZDNet reported on Dec. 5.
One of the largest data centers in the United States, CyrusOne has reportedly been exposed to an attack by a variant of the REvil (Sodinokibi) ransomware, which previously hit a number of service providers, local governments and businesses in the country.
The Scope Of The Attack
In An Email To Cointelegraph, CyrusOne Confirmed:
“Six of our managed service customers, located primarily in our New York data center, have experienced availability issues due to a ransomware program encrypting certain devices in their network.”
The firm went on to assure viewers that law enforcement was working on the matter and that their “data center colocation services, including IX and IP Network Services, are not involved in this incident.”
Just Business
Per the ransom note obtained by ZDNet, the attackers targeted CyrusOne’s network, with the sole objective of receiving a ransom. Those behind the attack claimed in the note that they consider the attack nothing more than a business transaction, aimed exclusively at profiting.
In the event the company does not cooperate with the attackers, it will purportedly lose the affected data as the cybercriminals claim to have the private key.
To Pay Or Not To Pay?
This spring, Riviera Beach, Florida, was hit by a hacker attack, in which the hackers allegedly encrypted government records, blocking access to critical information and leaving the city without an ability to accept utility payments other than in person or by regular mail. The city council eventually agreed to pay nearly $600,000 worth of Bitcoin (BTC) to regain access to data encrypted in the attack.
In late October, hackers compromised the website of the city of Johannesburg, South Africa, and demanded ransom in Bitcoin. The breach affected several customer-facing systems — hardware or software customers interact with directly, such as user interfaces and help desks. The city authorities refused to pay the ransom.
Meanwhile, a number of Finnish cities and organizations are rehearsing how to respond when a group of hackers demands the participants pay ransomware during a series of simulated cyberattacks.
Updated: 12-19-2019
Monero Malware Botnet Lurks Behind Taylor Swift JPEGs
Researchers have published a new report on what they deem to be a “relentless” crypto mining botnet that lurks behind seemingly innocuous content such as JPEG images of Taylor Swift.
The botnet — best known as MyKings (alternatively as DarkCloud or Smominru) — has been active since 2016, according to a Dec. 18 news release from Gabor Szappanos at SophosLabs.
While all “underpatched, low-hanging fruit” on the internet — to use Sophos’ phrasing — has long been vulnerable to its attacks, recently the actors behind MyKings have allegedly added bootkit functionality, which makes it all the more resistant to detection and effective removal.
$3M In Monero Illicitly Mined Via MyKings To Date
SophosLabs’ report provides a full overview of the botnet’s operations, which Szappanos characterizes as a “relentlessly redundant [i.e. repetitive] attacker” that attacks mostly Windows-based services that hosts database management systems such as MqSQL and MS-SQL, network protocols such as Telnet, and even servers running CCTV camera storage.
The report notes that the botnet’s creators appear to prefer to use open source or other public domain software and are highly skilled at customizing and enhancing source code to insert custom components that can execute attacks and perform automated update processes.
The botnet launches a series of attacks against a server with the aim of delivering a malware executable, frequently a Trojan dubbed “Forshare,” which was found to be the most common payload on infected servers.
Forshare is used to ensure that various different Monero (XMR) cryptominers run on the targeted hardware, with SophosLabs’ estimating that the botnet operators have earned roughly $3 million in Monero to date. This translates into a current income of around $300 per day, due to the cryptocurrency’s recently lower relative valuation.
Not What She Seems
In the studied example — an imperceptibly modified image of the pop star Taylor Swift — SophosLabs explains that the .jpg photo had been uploaded to a public repository, concealing within it an executable that would automatically update the botnet when downloaded.
SophosLabs’ research reveals the sophisticated nature of MyKings’ persistence mechanism, which perpetuates itself through aggressive repetition and self-updating procedures using multiple command combinations.
“Even if most of the components of the botnet are removed from the computer, the remaining ones have the capability to restore it to full strength simply by updating themselves. All of this is orchestrated using self-extracting RAR archives and Windows batch files.”
The report indicates that the countries with the highest number of infected hosts are currently China, Taiwan, Russia, Brazil, the United States, India and Japan.
Recent Monero Crimes
In November, Cointelegraph reported that the software available for download on Monero’s official website, getmonero.org, had been briefly compromised to steal cryptocurrency and drain users’ wallets.
That same month, Slovakian software security firm Eset revealed that cybercriminals operating a botnet known as Stantinko had been distributing a Monero cryptocurrency mining module via Youtube.
Updated: 1-1-2020
Chrome Browser Extension Ethereum Wallet Injects Malicious JavaScript To Steal Data
An Ethereum (ETH) wallet known as “Shitcoin Wallet” is reportedly injecting malicious javascript code from open browser windows to steal data from its users. On Dec. 30, cybersecurity and anti-phishing expert Harry Denley warned about the potential breach in a tweet:
According to Denley’s tweet, Chrome browser crypto wallet software Shitcoin Wallet is targeting Binance, MyEtherWallet and other well-known websites containing users’ passwords and private keys to cryptocurrency.
The Shitcoin Wallet Chrome extension – ExtensionID: ckkgmccefffnbbalkmbbgebbojjogffn – works by downloading a number of javascript files from a remote server. The code then searches for open browser windows containing webpages of exchanges and Ethereum network tools.
The code attempts to scrape data input into those windows. Once it does, the information is sent to a remote server identified as “erc20wallet.tk,” which is a top-level domain address belonging to Tokelau, a group of South Pacific Islands that are part of New Zealand’s territory.
Google Chrome removed MetaMask, but for different reasons
Shitcoin Wallet stealing user data may sound similar to recent incidents including Apple threatening to unlist Coinbase’s mobile DApp browser from its app store and Google removing Ethereum wallet app MetaMask from its Google Play App Store last week. Both of those instances, however, have been subject to considerable controversy due to lack of evidence of malicious conduct on the part of those apps.
A number of cryptojacking extensions were found on the Google Chrome web store last year. According to a recent report from McAfee Labs, cryptojacking, which occurs when a user’s computing device is secretly used to mine cryptocurrency, has been on the rise, up 29% in Q1 2019.
Shitcoin Wallet was built for trouble online
While the name should be a dead giveaway that it’s better to stay away from this particular Ethereum wallet software, Shitcoin Wallet contains some suspicious added features.
According to a company blog post, the Ethereum wallet, which launched on Dec. 9 and claims to have over 2,000 users, is a web-based wallet that has several extensions for different browsers. The blog post notes;
“It is a web wallet which has several extensions for different browsers, which I will discuss further in the article.”
However, this doesn’t square with what the company mentions at the end of that very blog post, which says/reads that Shitcoin Wallet is currently only supported by Chrome.
A few days prior to the malicious javascript attack, Shitcoin Wallet announced the launch of its new desktop app, giving away 0.05 ETH to users who download and install the Shitcoin Wallet desktop app.
While those users may have received a bit of free ETH, they are now left vulnerable to having their data scraped and personal information compromised.
Updated: 1-2-2020
Ledger Wallet User Allegedly Lost $16K to Malicious Browser Extension
Twitter user and software architect WizardofAus (@BTCSchellingPt) has warned cryptocurrency holders against a Chrome extension for Ledger crypto wallets that allegedly contains malware.
In A Tweet Posted On Jan 2., WizardofAus Claimed That:
“Malware Chrome extension alert. If you have “Ledger Secure” installed – REMOVE IT. The @ChromeExtension “Ledger Secure” contains malware that passes your seed phrase back to the extension’s author. This is *not* a @Ledger product. Successfully used against @hackedzec.”
“@hackedzec”’s Twitter handle was notably created in Jan. 2020; both the handle’s novelty and the chosen name suggest that he created the account specifically to spread awareness following his experience of the malware.
The official Ledger Support Twitter handle confirmed the detection of the extension malware on Jan. 2, using the header “PHISHING ALERT.”
Former Trezor executive and contributor to the “Little Bitcoin Book” Alena Vranova retweeted WizardofAus’ tweet with the comment: “another proof that the word ‘secure’ does not imply security.”
Learning From Others’ Expensive Mistakes
In WizardofAus’ account, 600 in Zcash (ZEC) — worth roughly $16,000 by press time — was stolen from @hackedzec’s holdings in his Ledger Nano by the Chrome extension’s creator.
Referring to Casa founder Jeremy Welch’s warnings last year against browser extension malware at the Bitcoin (BTC) event Baltic HoneyBadger in Riga, WizardofAus outlined the risks posed by these products — and what users can do to protect themselves:
“Firstly, be very careful what extensions you install. If you’re using the same computer for your crypto as you use generally, be extra diligent. Better to have a separate minimal machine – or use a Virtual Machine that is the only place you do crypto activity.”
Other due diligence includes using only the wallet vendor’s proprietary software — in this case, Ledger’s — and double-checking that it really comes from the vendor’s website via a secure link.
Users can also verify the checksum of the downloaded file before running the software. A checksum, also known as a hash, is a hexadecimal number that is unique to the installer .exe file created by the author. The downloaded file, assuming it has not been tampered with by a third party, should match the checksum on the vendor’s site.
Browser Risks
Just two days ago, Cointelegraph reported on an Ethereum (ETH) wallet Chrome browser extension known as “Shitcoin Wallet” that has reportedly been injecting malicious javascript code from open browser windows to steal data from its users.
Updated: 1-9-2020
North Korean Hacker Group Modifies Crypto-Stealing Malware
The Lazarus hacker group, which is allegedly sponsored by the North Korean government, has deployed new viruses to steal cryptocurrency.
Major cybersecurity firm Kaspersky reported on Jan. 8 that Lazarus has doubled down its efforts to infect both Mac and Windows users’ computers.
The group had been using a modified open-source cryptocurrency trading interface called QtBitcoinTrader to deliver and execute malicious code in what has been called “Operation AppleJeus,” as Kaspersky reported in late August 2018. Now, the firm reports that Lazarus has started making changes to the malware.
Kaspersky identified a new macOS and Windows virus named UnionCryptoTrader, which is based on previously detected versions. Another new malware, targeting Mac users, is named MarkMakingBot. The cybersecurity firm noted that Lazarus has been tweaking MarkMakingBot, and speculates that it is “an intermediate stage in significant changes to their macOS malware.”
Researchers also found Windows machines that were infected through a malicious file called WFCUpdater but were unable to identify the initial installer. Kaspersky said that the infection started from .NET malware that was disguised as a WFC wallet updater and distributed through a fake website.
The malware infected the PCs in several stages before executing the group’s commands and permanently installing the payload.
Attackers may have used Telegram to spread malware
Windows versions of UnionCryptoTrader were found to be executed from Telegram’s download folder, leading researchers to believe “with high confidence that the actor delivered the manipulated installer using the Telegram messenger.”
A further reason to believe that Telegram was used to spread malware is the presence of a Telegram group on the fake website. The interface of the program featured a graphical interface showing the price of Bitcoin (BTC) on several cryptocurrency exchanges.
The windows version of UnionCryptoTrader initiates a tainted Internet Explorer process, which is then employed to carry out the attacker’s commands. Kaspersky detected instances of the malware described above in the United Kingdom, Poland, Russia and China. The report reads:
“We believe the Lazarus group’s continuous attacks for financial gain are unlikely to stop anytime soon. […] We assume this kind of attack on cryptocurrency businesses will continue and become more sophisticated.”
Lazarus has been known to target crypto users for a long time. In October 2018, Cointelegraph reported that the group had stolen a staggering $571 million in cryptocurrencies since early 2017.
In March 2019, reports by Kaspersky suggested that the group’s efforts in targeting cryptocurrency users were still ongoing and its tactics were evolving. Furthermore, the group’s macOS virus was also enhanced in October last year.
Updated: 1-31-2020
Cybercriminals Hide Crypto Mining Script Behind Kobe Bryant Wallpaper
Opportunistic cybercriminals are capitalizing on the death of basketball legend Kobe Bryant earlier this week by setting booby-traps for those searching for mementos of the star. According to a tweet by Microsoft Security Intelligence on Jan. 31, hackers are hiding malicious html code containing a cryptojacking script in desktop wallpaper of the NBA all-time great.
Cryptojacking is a practice whereby cybercriminals hijack processing power from other computers to mine cryptocurrencies remotely.
Following the tragic helicopter crash which claimed the lives of Byrant, his 13-year old daughter, and seven other occupants, there has been increased interest in the star from both fans and the general public.
Perhaps unsurprisingly, it did not take long for cybercriminals to take advantage of this. An increasing number of people searching for information and images of the star is just a fresh crop of potential victims.
The Microsoft team found the malicious html file, Trojan:HTML/Brocoiner.N!lib with its Defender Virus Protection software. The coin mining script was disguised as a desktop wallpaper featuring an image of Bryant. The website hosting the coin miner was blocked by the software.
Reminiscing Or Cashing In?
As Cointelegraph reported, Bryant’s death brought an outpouring of grief from across social media, including a personal account from Tron founder Justin Sun. Bryant was an avid supporter of crypto, and Tron in particular, having discussed the future of blockchain with Sun on stage at the niTROn conference in 2019.
As a gesture of respect, Sun announced that this year’s niTROn conference would be dedicated to the star. However, given Sun’s prior history of dubious promotional methods, some on social media were quick to criticize this move as a shameless cash-in.
Updated: 2-5-2020
North Korean Hackers Created Realistic Trading Bot To Steal Money
The North Korean hacking team Lazarus Group targeted several crypto exchanges last year, Chainalysis reports. One of the attacks involved the creation of a fake, but realistic trading bot website that was offered to employees of DragonEx exchange.
In March 2019 the hackers stole approximately $7 million in various cryptocurrencies from Singapore-based DragonEx exchange. Though a relatively small sum, the hackers went to great lengths to obtain it.
The group used a sophisticated phishing attack where they created a realistic website and social media presence for a fake company named WFC Proof. The supposed company had created Worldbit-bot, a trading bot that was then offered to DragonEx employees.
Though the software allegedly resembled an actual trading bot, it contained malware that could hijack the computer it infected. Eventually the software was installed on a machine that contained the private keys to DragonEx’s hot wallet, allowing the hackers to steal the funds.
The attack is notable for its highly specific target and execution. The hackers appear to be very well versed in cryptocurrencies, even placing an ironic warning on its website to not let anyone access personal private keys.
Quick Cash Out
The group was previously known for parking the stolen money for up to 18 months and cashing it out once the coast seemed clear.
In 2019 they changed their behavior, choosing to exchange the money as soon as possible. In order to do this, Lazarus began using CoinJoin-enabled wallets to mix their coins.
The hackers cashed out the majority of the money in the 60 days following the attack, as opposed to almost a full year for 2018 attacks.
Updated: 2-10-2020
Cryptojacking Protection An Area Of Focus For Microsoft’s Edge Browser
Edge, the web browser of information technology giant Microsoft, now blocks cryptojacking malware.
A Microsoft Edge spokesperson told Cointelegraph on Feb. 10 that the latest version of the web browser features a new PUA (Potentially Unwanted Apps) blocking feature that may block some illicit cryptocurrency mining malware.
When asked about whether Microsoft plans to protect Edge users from illicit cryptocurrency miners, the spokesperson said that “this will be a particular area of focus.” As cryptojacking is increasingly becoming a cybersecurity threat, efforts to tackle the issue are also scaling up.
A New Cybersecurity Feature
Cryptojacking is the practice of illicitly mining cryptocurrencies on the hardware of unknowing hosts. Devices that fall victim to cryptojacking often show lower battery life and become less responsive.
Microsoft’s principal product manager Amitai Rottem pointed out the new feature in a tweet on Jan. 30. The tech giant’s program manager for the web platform Eric Lawrence explained that the feature blocks downloads that contain PUAs.
Microsoft noted that the long-implemented Microsoft Edge Tracking Protection feature also blocks known cryptocurrency mining software by default. A blog post published by Microsoft in early December 2019 reads:
“It’s worth noting that tracking prevention, when enabled, will always block storage access and resource loads for sites that fall into the Fingerprinting or Cryptomining categories on Disconnect’s tracking protection lists.”
Authorities worldwide are taking action against cryptojacking as the practice becomes more widespread. In early January, Interpol collaborated with cybersecurity firm Trend Micro to reduce cryptojacking affecting MikroTik routers across South-East Asia, while in August 2019, French police shut down a massive botnet that has been used for Monero mining on the machines of unsuspecting users.
Updated: 2-11-2020
Hacking Group Outlaw Upgrades Malware For Illicit Income Sources: Report
Cybersecurity firm Trend Micro has detected that hacking group Outlaw has been updating its toolkit for stealing enterprises’ data for nearly half a year at this point.
Outlaw — who had ostensibly been silent since last June — became active again in December, with upgrades on their kits’ capabilities, which now target more systems, according to an analysis from Trend Micro published on Feb. 10. The kits in question are designed to steal data from the automotive and finance industries.
The New Capabilities Of The Kits
The group’s new developments include scanner parameters and targets, advanced breaching techniques used for scanning activities, improved mining profits by killing off both competition and their own earlier miners, among others.
Per the analysis, the new kits attacked Linux- and Unix-based operating systems, vulnerable servers and Internet of Things devices. The hackers also used simple PHP-based web shells — malicious scripts uploaded on a server, with the objective to provide the attacker with a remote access and administration of the device. The analysis further explained:
“While no phishing- or social engineering-initiated routines were observed in this campaign, we found multiple attacks over the network that are considered ‘loud.’ These involved large-scale scanning operations of IP ranges intentionally launched from the command and control (C&C) server. The honeynet graphs, which show activity peaks associated with specific actions, also suggest that the scans were timed.”
Where Attacks Started
Attacks ostensibly started from one virtual private server (VPS) that looked for a vulnerable device to compromise. “Once infected, the C&C commands for the infected system launches a loud scanning activity and spreads the botnet by sending a “whole kit” of binary files at once with naming conventions same as the ones already in the targeted host, likely banking on breaking through via ‘security through obscurity’,” the post read.
Along with the new tools, Outlaw ostensibly exploits previously developed codes, scripts and commands. The group also uses a vast amount of IP addresses as input for scanning activities grouped by country. This ostensibly enables them to attack specific regions or areas within particular periods of the year.
Hackers’ Tools Advancement
Back in June, Trend Micro claimed to have detected a web address spreading a botnet featuring a Monero (XMR) mining component alongside a backdoor. The firm attributed the malware to Outlaw, as the techniques employed were almost the same used in previous operations.
The software in question also came equipped with Distributed Denial of Service (DDoS) capabilities, “allowing the cybercriminals to monetize their botnet through cryptocurrency mining and by offering DDoS-for-hire services.”
In January, the Lazarus hacker group, which is allegedly sponsored by the North Korean government, deployed new viruses to steal cryptocurrency. The group had been using a modified open-source cryptocurrency trading interface called QtBitcoinTrader to deliver and execute malicious code in what has been called “Operation AppleJeus.”
Updated: 2-26-2020
Australian Minister Slams Gov’t For Weak Response To Ransomware ‘Epidemic’
On Feb. 24, Tim Watts, Australia’s Shadow Assistant Minister for Cybersecurity, has published an article in the Financial Review on Feb. 24, criticizing the country’s government for its response to the 2019 “ransomware epidemic.”
Watts states that Australia was not immune to last year’s ransomware outbreaks, citing a Victorian government regional health network that shut down their systems after becoming infected. The incident resulted in multiple surgeries being delayed.
Watts also notes that during late Jan. 2020, Melbourne-based global transport company Toll “lost the use of up to 1,000 servers in a ransomware attack,” forcing the company to implement manual processes. The shadow assistant minister added that Toll’s systems still have not fully recovered.
Watts Attacks Government Silence
Despite the occurrences, Watts claims that the word “ransomware” has not been mentioned in Australia’s parliament in two years. He criticized Prime Minister Scott Morrison’s government for failing to spark public discourse surrounding the issue of ransomware, stating:
“There’s been no public health-style campaign. No minister has faced the media, flanked by cybersecurity experts. No minster has been sounding the alarm internally about the poor cyber resilience of government networks that have been revealed in a series of audits going back five years.”
Australia Lacks A Ministerial Position With A Direct Cybersecurity Portfolio
Watts further criticized the Morrison government for abolishing the ministerial position with direct responsibility for cybersecurity. He asserted that “since Scott Morrison abolished this dedicated role, there has been no one to provide the public, or, the government, with any leadership on the issue.” He added:
“We need a dedicated position in government to meet challenges like ransomware — cybersecurity is too complex and too important for it not to be somebody’s day job.”
According to New Zealand-based cybersecurity company Emsisoft, 2,874 ransomware attacks targeted Australia’s public and private sectors, causing approximately $1.08 billion in damages to the country’s economy during 2019.
Monero Malware Targets Australian Banks
On Feb. 25, the Australian Cyber Security Centre (ACSC) announced that Australian banks are being threatened by a hacking group promising Denial-of-Service (DoS) attacks unless “a sum of the Monero cryptocurrency is paid.”
Monero (XMR) is a favored cryptocurrency among darknet market and ransomware operators as transactions are anonymized using a ring-signature system that facilitates “transaction mixing” to occur. The threats have been made by email, and the ACSC has so far received “no reports of the threats eventuating in DoS.”
Updated: 2-28-2020
Microsoft Updates Edge Browser To Protect Against Illicit Crypto Miners
With malicious cryptocurrency miners having proliferated over the internet in the last two years, Microsoft has moved to protect users of its Edge web browser from the effects of the malicious software.
In a blog post on Thursday, the tech giant said it had enabled a feature that will spot and prevent the download of “potentially unwanted applications” (PUAs) such as cryptojackers or adware.
Cryptojackers utilize code hidden on websites or downloaded onto users’ devices to harness computer processing power to mine cryptocurrencies.
Microsoft explained it added the feature after users complained that when downloading free software from the internet, they often had apps “with a poor reputation” being installed at the same time.
The new feature – available in Edge versions from 80.0.338.0 on – is off by default, but can be switched on in the Privacy and Services settings panel.
As Microsoft said, PUAs like miners can slow a user’s computer. They can also lead to excessive fan noise and overheating while they steal victim’s electricity to carry out mining tasks in the background.
While users complained of free software sites being laden with cryptojackers, they can find their way into apparently legitimate sources too. A year ago, eight Windows apps on the Microsoft Store were discovered by Symantec to be hosting a version of Coinhive, a commonly deployed script for mining the monero (XMR) cryptocurrency. The apps were removed from the site after Microsoft was alerted.
A report from Skybox Security in 2018 said crypto mining malware had overtaken ransomware as the cybercriminal’s weapon of choice. The firm’s figures suggested cryptojacking comprised 32 percent of all cyberattacks at the time.
Referring to its new miner blocking feature, Microsoft said: “Our goal is to assist users in getting the apps they want, while empowering them to maintain control over their devices and experiences.”
Updated: 2-29-2020
Threat Alert: New Trojans Targeting Major Crypto Exchanges Apps Discovered
ThreatFabric, an Amsterdam-based cybersecurity firm specializing in threats to the financial industry, has identified the “Cerberus” Trojan that steals 2-Factor Authentication (2FA) codes generated by the Google Authenticator app for internet banking, email accounts, and cryptocurrency exchanges.
US-based cryptocurrency exchange Coinbase is one of the crypto platforms listed in Cerberus’ exhaustive list of targets — which also includes major financial institutions around the world and social media apps.
The cybersecurity firm notes that it has not identified any advertisement on the dark beb for Cerberus’ updated features, leading it to believe that the updated version is “still in the test phase but might be released soon.”
Cerberus Updated During Early 2020
ThreatFabric’s report states that the Remote Access Trojan (RAT) “Cerberus,” was first identified during the end of June, superseding the Anubis Trojan and emerging as a major Malware-as-a-Service product.
The report states that Cerberus was updated in mid-January 2020, with the new version introducing the capability to steal 2FA tokens from Google Authenticator, as well as device screen-lock PIN codes and swipe patterns.
Once installed, Cerberus is able to download a device’s contents, and establish connections providing the malicious actor with full remote access over the device. The RAT can then be used to operate any app on the device, including bank and cryptocurrency exchange apps.
“The feature enabling theft of device’s screen lock credentials (PIN and lock pattern) is powered by a simple overlay that will require the victim to unlock the device. From the implementation of the RAT we can conclude that this screen-lock credential theft was built in order for the actors to be able to remotely unlock the device in order to perform fraud when the victim is not using the device. This once more shows the creativity of criminals to build the right tools to be successful.”
Banking Trojans Increasingly Target Crypto Wallet Apps
The report also examines two other RATs that rose to prominence after Anubis — “Hydra” and “Gustaff.”
Gustaff targets Australian and Canadian banks, cryptocurrency wallets, and government websites, while Hydra has recently expanded in scope after mostly targeting Turkish banks and blockchain wallets.
Including Cerberus, the three Trojans target at least 26 cryptocurrency exchanges and custody providers. The targets include several leaders in the crypto sector, including Coinbase, Binance, Xapo, Wirex, and Bitpay.
More than 20 of the targets are wallets providers offering support for leading cryptocurrencies including Bitcoin (BTC), Ethereum (ETH), and Bitcoin Cash (BCH)
A potential defense against Cerberus is to use a physical authentication key to prevent remote attacks. These keys require a hacker to have the actual device in their presence, which helps minimize the risk of a successful attack.
Updated: 2-29-2020
‘Digileaker’ Claims To Have Stolen KYC Documents For 8,000 Digitex Users
An ex-employee of cryptocurrency derivatives exchange Digitex began leaking stolen Know-Your-Customer (KYC) on Telegram. The stolen data reportedly includes passport and driving license scans and other sensitive documentation pertaining to more than 8,000 Digitex customers.
The Seychelles-based exchange issued Cointelegraph a statement indicating that it is not currently able to comment on the incident and is seeking legal counsel:
“Digitex Futures is aware of a leak of confidential data. We are not able to comment fully on the incident at this time and are currently seeking legal counsel. However, we can confirm that this was not an external hack but an internal security breach orchestrated by an ex-employee with a conflict of interest against the company. We will be releasing more information on the incident as soon as possible.”
The Extent Of The Digitex Breach Is Unknown
However, one source who is familiar with the matter told Cointelegraph that the data of 8,000 customers “has not been breached,” adding:
“Only three ids have been leaked although the perpetrator confirms that he has them all and is starting to post demands so as not to leak the rest.”
On Telegram, the “Digileaker” has claimed to be in possession of “the entire KYC documentation of every single user who has used the Digitex Treasury from its inception date until today.”
In an interview with cryptocurrency scam hunter CryptoVigilante, the Digileaker claimed to have used login information obtained when Digitex registered with its KYC provider Sum and Substance.
According to the hacker, the login “gives unrestricted access to all the KYC information of 8000+ customers including documents, address, phone numbers and other information like IP address.”
Digitex Data Breach Gains Momentum
The Digitex debacle has escalated over recent weeks, starting with the ex-employee hijacking its Facebook account to publicly disclose users’ email addresses. In a Feb. 10 blog post, Digitex stated that the breach was an “internal issue” that had been perpetrated by a “scheming and highly manipulative ex-employee.”
The company also assured customers that “beyond their email addresses, no other sensitive information was gathered or released.”
Crypto Exchanges See Several Attacks During February
Digitex’s data breach comes amid an increasing number of malicious attacks targeting cryptocurrency exchanges.
On Feb. 27, Okex and Bitfinex suffered simultaneous distributed denial of service (DDoS) attacks. While Okex’s platform was “largely unaffected,” Bitfinex entered into maintenance mode to quickly execute countermeasures and patch for all similar attacks.
On Feb. 28, the Tim Draper-backed Singaporean crypto exchange Coinhako announced that it has fully reimbursed all customers were affected by a “sophisticated attack” that began targeting the exchange seven days prior.
The exchange responded by suspending send functionality. Coinhako has since restored send capabilities for Bitcoin (BTC), Bitcoin Cash (BCH), Ethereum (ETH), Tether (USDT), TrueUSD (TUSD) and USD Coin (USDC).
Updated: 3-3-2020
DDoS Attacks on OKEx and Bitfinex Were Sophisticated, Possibly Related
As the cryptocurrency industry continues to mature, security remains a major challenge. Over the last few weeks, a number of cryptocurrency exchanges — namely, OKEx, Bitfinex, Digitex and Coinhako — have experienced security breaches.
Although the attackers apparently did not manage to steal any funds, one of the incidents resulted in a leak of Know Your Customer data. All of the breaches have reportedly been dealt with as of press time, and all of the affected exchanges are back online.
OKEx And Bitfinex Targeted In A Series Of DDoS Attacks
Two different major crypto exchanges were reportedly hit with distributed denial-of-service attacks last week. A DDoS attack is a common type of cyberattack that overloads a system with numerous requests from multiple virus-infected servers.
The OKEx crypto exchange platform was the first one hit, as it started to experience problems on Feb. 27 at approximately 11:30 a.m. EST. Notably, as the exchange’s servers were dealing with the increased output, CEO Jay Hao took to his personal Weibo page to blame unspecified competitors for the incident.
The raid lasted two days, as an OKEx spokesperson confirmed in an email to Cointelegraph. Initially, the attack routed 200 gigabytes per second of traffic, and then increased it to 400 GB per second during the second wave.
Such traffic volume makes it safe to deem this a relatively major attack. Telegram CEO Pavel Durov has previously encountered such attacks and told TechCrunch that his messenger was often hit by DDoS attacks of a similar scale (200–400 GB per second) during protests in Hong Kong — which he labeled as “state actor-sized” disruption attempts. Lennix Lai, financial markets director at OKEx, called the attack “very sophisticated.”
Despite being high-grade, the DDoS attack “was properly handled within a short period of time and no client is impacted,” an OKEx representative told Cointelegraph. The second wave of the attack occurred shortly after “temporary system maintenance” on OKEx’s servers was completed, which temporarily disabled options and futures trading. The spokesperson claimed that the two events were completely unrelated.
Related: Crypto Exchange Hacks in Review
On Feb. 28, while OKEx was experiencing the second wave of attacks, fellow cryptocurrency exchange Bitfinex also started to experience problems. Per the Bitfinex status page, the attack lasted one hour, severely hindering the exchange’s activity during that period, with throughput falling close to zero. As a result, all trading activity was suspended during that time frame.
Nonetheless, Bitfinex’s chief technology officer, Paolo Ardoino, told Cointelegraph that it was the company’s decision to go offline, as it allegedly allowed Bitfinex to deal with the attack in a timely fashion:
“The matching engine, websockets and core services were not affected by the DDoS attack. However, it was of paramount importance to speedily react in order to avoid any damage escalation. The decision to enter in maintenance was not due to the inability of the platform to resist, rather, it was a decision taken in order to quickly bring in the countermeasures and patch for all similar attacks.”
Ardoino went on to add that the attack was notably sophisticated, as the attackers attempted to exploit several platform features to increase the load on the infrastructure, adding: “The huge number of different IP addresses used and the sophisticated crafting of the requests toward our API v1 exploited an internal inefficiency in one of our non-core process queues.”
Soon after the attack was dealt with, Ardoino tweeted that he was unaware of the OKEx incident but was “interested to understand similarities.” He added:
“We’ve seen a level of sophistication that means a deep preparation from the attacker. Good news: This family of attacks won’t work again against Bitfinex.”
A Bitfinex representative told Cointelegraph that the company had no further comment, declining to discuss the similarities between the two attacks. A representative for OKEx informed Cointelegraph that they have not been in touch with other exchanges in regard to the attacks.
In a separate tweet, OKEx’s Hao offered a bounty “to any team who got paid to do this” and to Bitfinex in case it is willing to cooperate and “expose the malicious buyer of the DDoS attack.”
Cryptocurrency exchanges have been hit by DDoS attacks in the past. For instance, Bitfinex experienced a DDoS attack in June 2017, when the exchange was forced to suspend transactions for a short period of time.
Coinhako Was Also Hit By A “Sophisticated Attack” And Claims It Is Not Related To Other Incidents
On Feb. 21, the Tim Draper-backed Singaporean exchange Coinhako was also affected by a “sophisticated attack,” although seemingly of a different nature. During the said incident, “unauthorized cryptocurrency transactions were found from Coinhako accounts and sent out.”
The trading platform decided to deactivate the “send” option as a preventive measure. Eight days later, on Feb. 29, Coinhako announced it was back to “full operational capacity, with tightened security,” and that the “send” function had been made available for all cryptocurrencies available on the platform.
A Coinhako representative has provided a minimal comment to Cointelegraph, saying that the incident “was not related to the recent DDoS attacks on other exchanges.”
Digitex Suffered A KYC Leak Supposedly Orchestrated By An Ex-Employee
Earlier in February, a pseudonymous hacker began leaking KYC data of users who were registered on cryptocurrency derivatives exchange Digitex via a Telegram channel. The stolen data reportedly included scans of passports and drivers’ licenses, as well as other sensitive documentation pertaining to more than 8,000 Digitex customers — although, so far, the hacker has leaked only seven IDs and blurred all photos “out of respect for the users.” The attacker also stated that they “will reach out to all three users in the near future and compensate them accordingly” after leaking the first three IDs.
The leak followed a Feb. 10 announcement from Digitex stating that its Facebook page had been compromised during “an internal issue orchestrated by a scheming and highly manipulative ex-employee whose professional interests are now in conflict with Digitex’s success.” In a Feb. 14 interview on CNBC Africa’s Crypto Trader, Digitex CEO Adam Todd clarified that “no sensitive data” had been taken, only email addresses.
In an interview with Cointelegraph, a hacker under the pseudonym Zincer clarified that the leaked KYC data belonged to the buyers of DGTX, Digitex’s in-house token. When asked about the specific reason for leaking personal information, the hacker replied:
“To get Digitex to admit their incompetence and sort out their blatant lax security practices. […] This is a startup that is going to launch soon I believe. So, they should sort out their security before going live.”
Zincer denied ever being employed by Digitex or doing any freelance work for the company. The attacker also said that the exchange has been ignoring any attempts to communicate:
“For what it is worth, I have received no messages from them or anyone in affiliation with them.”
On March 2, Soon After The Interview, Zincer Posted On Digileaker That Digitex Had Apparently Addressed The Security Weakness:
“Finally they seem to have closed off access, it only took a few days. You should be safe doing KYC now.”
Meanwhile, Digitex published another announcement, stating that it initially denied that sensitive information had been stolen because “at that point, we were only aware of the email data that had been taken.” According to the trading platform, there was a second breach, during which sensitive data was indeed compromised. The statement also stipulated that the attack was performed by an ex-employee:
“We have not yet been able to verify the amount of user data taken and if it was, in fact, as many as 8,000 Digitex users. This data is kept in a different system. We do not hold it at Digitex, it is held with a third-party provider to which Adam and one other person had access.”
According to the statement, Digitex is also “investigating the possibility of removing the need for KYC on our exchange entirely.” A representative for Digitex refrained from commenting on the incident and referred to the aforementioned statement.
When speaking with Cointelegraph, Zincer said that other exchanges aren’t currently being targeted, although they have “in the past.” When asked about the DDoS attacks on OKEx and Bitfinex, the hacker said that “the timing would suggest it was related.” Zincer also added:
“I find it unlikely two separate people or organizations would just happen to have their attacks work at the same time.”
Security Remains A Major Concern In The Industry
Although apparently no funds were stolen during these attacks, 2020 has already seen a number of crypto-related heists that have resulted in money loss. Among the most high-profile was an attack involving Bitcoin Cash (BCH) and BTC, during which a major investor reportedly lost as much as $30 million worth of cryptocurrency in a wallet hack. According to a recent report issued by Big Four accounting firm KPMG, more than $9.8 billion worth of crypto has been stolen since 2017.
Updated: 3-14-2020
‘CovidLock’ Exploits Coronavirus Fears With Bitcoin Ransomware
Opportunistic hackers are increasingly seeking to dupe victims using websites or applications purporting to provide information or services pertaining to coronavirus.
Cybersecurity threat researchers, DomainTools, have identified that the website coronavirusapp.site facilitates the installation of a new ransomware called “CovidLock.”
The website prompts its visitors to install an Android application that purportedly tracks updates regarding the spread of COVID-19, claiming to notify users when an individual infected with coronavirus is in their vicinity using heatmap visuals.
CovidLock Ransomware Launches Screen Lock Attack On Unwitting Victims
Despite appearing to display certification from the World Health Organization and the Centers for Disease Control and Prevention, the website is a conduit for the ‘CovidLock’ ransomware — which launches a screen lock attack on unsuspecting users.
Once installed, CovidLock alters the lock screen on the infected device and demands a payment of $100 worth of BTC in exchange for a password that will unlock the screen and return control of the device to the owner.
If a victim does not pay the ransom within 48 hours, CovidLock threatens to erase all of the files that are stored on the phone — including contacts, pictures, and videos.
The program displays a message intended to scare users into compliance with its demand, stating: “YOUR GPS IS WATCHED AND YOUR LOCATION IS KNOWN.
IF YOU TRY ANYTHING STUPID YOUR PHONE WILL BE AUTOMATICALLY ERASED.”
DomainTools claims to have reversed engineered the decryption keys for CovidLock, adding that they will publicly post the key.
Coronavirus-Themed Website Are 50% More Likely To Be Malicious
According to cyber threat analyst, Check Point, coronavirus-themed domains are 50% more likely to be a front for malicious actors than other websites.
Since January 2020, the firm estimates that more than 4,000 domain names that relate to the coronavirus have been registered globally — 3% of which are deemed to be “malicious,” and 5% of which are described as “suspicious.”
U.K. Public Lose $1 Million To Coronavirus Scams
On March 11, the U.K. Financial Conduct Authority warned of an increasing proliferation of coronavirus-themed scams – including investment scams fraudulently offering investments in crypto assets.
According to the U.K. National Fraud Intelligence Bureau (NFIB), many malicious sites are offering maps and visualizations tracking the spread of coronavirus — much like CovidLock. An NFID representative stated:
“They claim to be able to provide the recipient with a list of coronavirus infected people in their area. In order to access this information, the victim needs to click on a link, which leads to a malicious website, or is asked to make a payment in bitcoin.”
The NFIB estimates that coronavirus-themed scams have already defrauded the British public out of roughly $1 million.
Updated: 3-23-2020
Over 172 Million Weibo Users’ Personal Data Is For Sale on Dark Web
Chinese social media giant saw a massive data breach result in data of millions of users available for sale on the dark web.
According to a March 19 report from Chinese blockchain news outlet Jinse, basic account information of 172 million users was available, priced at 0.177 BTC. The account information for sale included user ID, number of Weibo posts, number of fans and followers, gender and geographical location.
Weibo Confirmed The Privacy Issue Yet Deleted The Post Later On
According to Jinse, Weibo’s security director Luo Shiyao responded to the incident in a now-deleted post, explaining that:
“Users’ mobile phone numbers were leaked through forced matching with an address book API in 2019. The rest of the public information was scraped on the web.”
Luo added that the company took immediate measures to shut down the API and reported the leak to the policy as soon as they detected it. He claimed the company was doing everything they can to find those responsible. He added that:
“User privacy is crucial, especially when it comes to mobile phone numbers.”
Jinse Also Reported On A Post From Former Director Of Ali Group Security Research Lab’s That Said:
“Many people’s mobile phone numbers have been leaked. All you need is the Weibo account address and the user’s phone number is revealed.”
Both Weibo security director and former Ali group lab director later deleted these posts, according to Jinse.
Privacy Issue Continues To Be A Concern For Social Media Users
As Cointelegraph reported, a similar incident happened to social media giant Facebook. In September, 17% of Facebook’s 2.4 billion users had their data exposed.
In that instance, a database of information from 419 million Facebook accounts including names, phone numbers, gender and country of residence became available for download.
Using Ransomware, Hackers Steal And Publish Medical Data of Firm Researching Coronavirus
Black hat hacker group Maze has infected the infrastructure of a firm researching the coronavirus with ransomware, managing to steal and publish sensitive data.
The Hack Of Medical Information
Cybersecurity firm Emsisoft told Cointelegraph on March 23 that Maze group’s hackers compromised United Kingdom medical firm Hammersmith Medicines Research. The published data includes sensitive data on medical test volunteers such as id documents like passports, medical background and details of the tests. Emsisoft threat analyst Brett Callow said:
“[The data] is on the clear web where it can be accessed by anybody with an internet connection. […] The criminals almost certainly haven’t published all the data that was stolen. Their modus operandi is to first name the companies they’ve hit on their website and, if that doesn’t convince them to pay, to publish a small of the amount of their data — which is the stage this incident appears to be at — as so-called ‘proofs.’”
Fortunately, ComputerWeekly reports that the Hammersmith Medicines Research was able to make the systems operational by the end of the day. Callow noted that “it would appear they were able to quickly restore their systems from backups.” He also said that the data previously published on the hacker’s website is no longer available:
“Note that, since the ComputerWeekly report ran, the data stolen from HMR has been ‘temporarily removed’ from the criminals’ website. […] But here’s the problem. Other criminals download the data posted on these leak sites and use it for their own purposes.”
Callow told Cointelegraph that he does not know how high the ransom demanded was. Still, he pointed out that the group has previously asked for about $1 million in Bitcoin for restoring access to the data and another $1 million in BTC to delete their copy and stop publishing it.
As Cointelegraph reported in early February, Maze also compromised five United States law firms and demanded two 100 Bitcoin ransoms in exchange for restoring data and deleting their copy. Callow said that ransomware groups nearly always request to be paid in Bitcoin:
“99% of ransom demands are in Bitcoin and, to date, it has been the Maze group’s currency of choice.”
Criminals Are Not Robin Hood
In previous incidents, Maze also published stolen data on Russian cybercrime forums recommending to “Use this information in any nefarious ways that you want.” Callow also criticized “a not inconsiderable number of publications” that recently reported about how some ransomware groups — including Maze — stopped their attacks for the time of the pandemic. He said:
“A not inconsiderable number of publications recently reported that some ransomware groups, including Maze, had declared an amnesty on attacks on medical organizations for the duration of the Covid-10 outbreak and I’ve since seen them described as ‘Robin Hood-esque.’ This clearly demonstrates that, to the surprise of absolutely nobody, criminals cannot be trusted and it is a mistake for them to be given a voice.”
Callow said that the threat level is the same that it has always been, or possibly higher. He also insisted that “these groups should not be given a platform which enables them to downplay that fact.” This is in line with the recent Emsisoft report according to which ransomware attacks have a seasonal aspect and the number of attacks spikes during the spring and summer months.
Updated: 3-25-2020
The Role of Cryptocurrencies In The Rise of Ransomware
Cryptocurrency and ransomware have had a long history together. They are so closely intertwined, in fact, that many have blamed the rise of cryptocurrency for a parallel rise in ransomware attacks.
Ransomware attacks are certainly increasing — they rose by 118% in 2018 — but it’s not clear that this is due to cryptocurrency. While the vast majority of ransoms are paid in crypto, the transparent nature of these currencies actually means that they are a pretty bad place to hide stolen funds.
In this article, we’ll take a look at the relationship between cryptocurrency and ransomware, as well as what the future holds.
The Ransomware Crypto Economy
There are at least two ways in which cryptocurrency is important for ransomware attacks. The first one is the most obvious — the majority of the ransoms paid during these kinds of attacks are generally in cryptocurrency. This was the case, for instance, in the WannaCry ransomware attacks, still the largest attack of its kind in history. Victims of the attack were instructed to send roughly $300 of Bitcoin (BTC) to their attackers.
There is another way in which crypto and ransomware are intertwined, though. Today, plenty of hackers are offering “ransomware as a service,” essentially letting anyone hire a hacker from online marketplaces. If you are so inclined, you can even buy ransomware off-the-shelf from these marketplaces. Both of these “services” can be paid for in — you’ve guessed it — cryptocurrency.
Cryptocurrency is also implicated in many other forms of cyberattack. Cryptojacking — a form of attack that uses victim’s computers to mine cryptocurrencies — is also on the rise, and new forms of malware such as Adylkuzz can be used by almost anyone with even a slight level of technical knowledge. Though these forms of attack are not technically ransomware, they further suggest the deep relationship between cryptocurrency and cybercrime.
Following The Money
At first glance, it seems obvious that ransomware hackers would demand payment in cryptocurrency. Surely these currencies, based on anonymity and encryption, offer the best place to store stolen funds?
Well, not really. There is actually a different reason why ransomware attacks make use of cryptocurrencies. As Coin Center director of research Peter Van Valkenburgh wrote in 2017, it is the efficiency of cryptocurrency networks, rather than their secrecy, that attracts hackers. As he later put it:
“It’s electronic cash, so it’s easy to write software that can automatically demand payment and automatically demand that payment has been made.”
The value of cryptocurrency during a ransomware attack is actually the transparency of cryptocurrency exchanges. A hacker can simply watch the public blockchain to see if victims have paid up, and can automate the process of giving a victim their files back once this payment has been received.
This point also suggests a slightly curious aspect of the role of crypto in ransomware attacks: Cryptocurrency is, perhaps, the worst place to store ransom money. The open, transparent, nature of Bitcoin blockchain transactions means that the global community is closely watching the ransom money. That makes it extremely difficult to convert these funds into another currency, and means that they can be tracked by law enforcement.
As The Director Of Research At Coin Center, Peter Van Valkenburgh, Stated:
“In the U.S., every major bitcoin exchange is regulated by FINCEN. Right now the $50,000 extorted from victims is just sitting on the bitcoin network. … That [exchange into local currency] is where you’re vulnerable to being identified.”
Regulation And Enforcement
The fact that stolen funds can be tracked in this way doesn’t necessarily mean that the hackers who stole them can be brought to justice, of course. The anonymity of cryptocurrency means that it is often impossible for law enforcement agencies to uncover the true identity of ransomware hackers, though of course there are exceptions.
Chief among these, according to Coin Center, is that the “blockchain allows one to trace all transactions involving a given bitcoin address, all the way back to the first transaction. That gives law enforcement the records it needs to ‘follow the money’ in a way that would never be possible with cash.”
Because of that, and also in response to a number of recent high-profile ransomware attacks, some have called for cryptocurrency to be regulated more closely. Regulation will need to be implemented carefully, however, because one of the major attractions of cryptocurrency — for ordinary citizens and hackers alike — is the fact that it is anonymous.
This means that attempts to regulate the space may make catching criminals even more difficult. As pointed out by Will Ellis, head of research at community advocacy group Privacy Australia, cryptocurrency bans led to a rise in VPN use, as investors seek to circumvent Know Your Customer and Anti-Money Laundering requirements in their home countries.
In addition, most governments simply don’t have the understanding or the resources to regulate the crypto space effectively. Some are so far behind that they aren’t even certain how to define what cryptocurrencies are. In this context, it is difficult to see how the close link between ransomware and cryptocurrency can ever be broken.
The lack of governmental oversight of cryptocurrency, combined with the rapid rise in ransomware attacks, means that individuals need to protect themselves.
Some companies and individuals have taken unusual approaches. Companies have stockpiled Bitcoin not as an investment, but rather in case they need to pay a ransom as part of a future attack. Some enterprising individuals have even taken matters into their own hands, such as the German programmer who “hacked back” following a cyberattack using his own systems.
For most of us, though, protecting against ransomware attacks means doing the basics correctly. You should ensure that all of your systems are up to date, subscribe to a secure cloud storage provider and backup frequently. Companies of all sizes should partner with a managed security services provider to monitor enterprise networks, perform risk assessments and make recommendations specific to their data environment.
Ultimately, the relationship between cryptocurrency and ransomware is unlikely to be broken anytime soon. And while cryptocurrencies are certainly involved in the majority of ransomware attacks, we should not make the mistake of blaming crime on the currency it is conducted in.
Updated: 2-17-2021
US Charges Three North Korean Hackers Over Crypto Attacks And WannaCry Ransomware
The Department of Justice has indicted three hackers affiliated with the infamous Lazarus Group.
On Wednesday, the United States Department of Justice announced charges against three North Korean hacker.
Making the announcement, Assistant Attorney General John Demers condemned the North Korean program, the most famous branch of which is Lazarus Group. Demers said:
“North Korea’s operatives, using keyboards rather than guns, stealing digital wallets of cryptocurrency instead of sacks of cash, are the world’s leading bank robbers.”
With a country largely sequestered from the international economy, North Korea’s hacking program has been a critical source of revenue. Many have linked hacking income from sources like the WannaCry malware and crypto exchange Coincheck with the nuclear weapons program. Demers elaborated:
“The DPRK cyber threat has followed the money and turned its revenue generation sights on the most cutting edge aspects of international finance, including through the theft of cryptocurrency from exchanges and other financial institutions.”
North Korea’s hacking program has been the subject of extensive scrutiny, both from the U.S. and internationally. As the country has no widespread internet access, many cite China’s role in training North Korean hackers. Indeed, the U.S. sanctioned two Chinese affiliates of Lazarus Group back in March 2020.
The indictment comes more than two years after prosecutors filed charges against one of the men, Park Jin Hyok, a computer programmer working for North Korea’s military intelligence team, who was allegedly part of a team of hackers who helped carry out the cyberattack on Sony. The attack erased a vast trove of data, divulged confidential emails among top Hollywood executives and forced the company offline until it could rebuild its computer network.
Authorities believe the motive for the attack was retaliation for Sony’s production of the 2014 film “The Interview,” a comedy starring Seth Rogen and James Franco that ridiculed North Korean dictator Kim Jong Un and included the portrayal of an assassination plot against him.
The indictment describes a vast and multilayered scheme that went well beyond the Sony attack, targeting international banks and cryptocurrency companies. The defendants deployed malicious cryptocurrency applications and developed and fraudulently marketed a Blockchain platform, striking financial institutions and companies in multiple continents, prosecutors said.
“The scope of the criminal conduct by the North Korean hackers was extensive and long-running, and the range of crimes they have committed is staggering,” acting U.S. Attorney Tracy L. Wilkison for the Central District of California said in a statement.
“The conduct detailed in the indictment are the acts of a criminal nation-state that has stopped at nothing to extract revenge and obtain money to prop up its regime.”
The 33-page indictment unsealed Wednesday charges Park, Jon Chang Hyok and Kim Il with criminal conspiracy, conspiracy to commit wire fraud and bank fraud.
Prosecutors said the defendants were part of North Korea’s military intelligence agency called the Reconnaissance General Bureau, or RGB. The agency was was headquartered in Pyongyang, but the trio traveled to and worked from other countries, including the People’s Republic of China and the Russian Federation, prosecutors said.
The indictment was made public two months after it was returned by a Los Angeles grand jury.
The prospect of any of the North Korean hackers facing justice in a U.S. court is remote at best given their role in the regime.
As part of the alleged scheme, the defendants sought to steal more than $1.2 billion in banks from multiple countries including Vietnam, Mexico and Malta, the indictment says. They also stole tens of millions of dollars’ worth of cryptocurrency, including $75 million from a Slovenian cryptocurrency company and $11.8 million from a financial services company in New York, according to the indictment. They are also accused of carrying out the WannaCry 2.0 ransomware attack in 2017.
“As laid out in today’s indictment, North Korea’s operatives, using keyboards rather than masks and guns, are the world’s leading 21st century nation-state bank robbers,” said assistant Attorney General John Demers.
The Justice Department also announced Wednesday that a Canadian-American man agreed to plead guilty in a money laundering scheme connected to the hackers.
Ghaleb Alaumary, 37, of Ontario, admitted to being a “high-level” money launderer for multiple criminal schemes including ATM “cash out” operations and a cyber related bank heist orchestrated by North Korea, prosecutors said.
Alaumary could not immediately be reached for comment. His attorneys did not immediately respond to a request for comment.
The scope of the cyberassaults allegedly carried out by Park and his fellow North Korean hackers “is virtually unparalleled,” federal investigators said in the 2018 criminal complaint filed in Los Angeles. The hacks hit hundreds of thousands of computers around the world and causing serious damage at entertainment companies, hospitals and defense contractors over several years,
The WannaCry 2.0 ransomware attack in 2017 struck computers in more than 150 countries, temporarily crippling the computer system of Britain’s public health care service. At the time, National Health Service staff had to delay operations and appointments while doctors used pen and paper until the computer network was restored. The malicious software also hit Germany’s railways and Russia’s interior ministry.
Updated: 3-29-2020
Fake Ledger Chrome Extensions Continue To Steal Crypto From Victims
Fake Google Chrome extensions for crypto hardware wallet manufacturer and custody provider, Ledger, continue to claim victims.
On March 28, a post was published to Reddit by a user seeking to warn others that they had just lost 14,908 Ripple (XRP) (roughly $2,577) to a fake Ledger Wallet extension on the Google Chrome store.
According to the poster, ‘leannekera’, the lost funds comprised a nest egg that she and her husband had been growing since 2017. The wallet that her XRP was sent to quickly forwarded her funds to a second wallet that currently holds nearly 15 million in XRP.
Fake Ledger Wallet Chrome Extension Claims COVID-19 Patient As Victim
Leannekera claims to be a confirmed victim of COVID-19. She states that she is in self-imposed isolation in a single room of her house. She also notes that her husband works in an ‘essential industry’ in the United Kingdom.
In response to financial difficulties resulting from her isolation, leannekera sought to liquidate some of her family’s crypto holdings, and move any excess funds into XRP. She stated:
“I begin the day by selling a load of our other cryptocurrency for bitcoin, sold some to help us and I then consolidate the remaining into xrp. I then load up our Ledger. It’s been a while since I last accessed our Ledger (2018), and have since changed my computer. I recalled the Ledger having a Chrome extension and this is when the scam starts.”
Leannekera recounts finding only one Ledger extension on the Chrome store, with the application claiming affiliation with Ledger.com and boasting 70 positive reviews of between four and five stars. When prompted, she entered her Ledger’s recovery seed into the extension — allowing the funds to be stolen.
Ledger Warns Of Malicious Chrome Extensions
On March 5, Ledger published a tweet warning users of malicious Chrome extensions. These extensions — identified by cybersecurity researcher Harry Denley — claim to be directly affiliated with the company. The application seeks to emulate Ledger’s desktop and mobile application Ledger Live and was even advertised on Google Ads.
By March 24, researchers at xrplorer forensics estimated that a fake Ledger extension had absorbed 1.4 million XRP in March alone.
Crypto Scammers Target Hardware Wallet Users
Opportunistic scammers have long sought to target hardware wallet users, with hackers even distributing fake hardware wallets imitating the appearance of Tezor or Ledger products at crypto conferences in 2017.
Last October, a now-deleted Reddit user posted a link to a Shopify website purporting to offer KeepKey hardware wallets for only $5 — triggering the suspicions of other Redditors.
During May 2019, researchers also discovered a fake Chrome extension targeting Trezor users.
Updated: 3-29-2020
Maze Hacker Group Claims Infecting Insurance Giant Chubb with Ransomware
Black hat hacker group, Maze, claims to have used ransomware to compromise the systems of insurance giant, Chubb. They also claim to have stolen the firm’s data.
Brett Callow, threat analyst at cybersecurity firm, Emsisoft, told Cointelegraph on March 27 that Maze published the claim on its website. While the website does not provide any direct proof of the hack so far, Callow pointed out facts that give the claim an air of credibility:
“Maze’s past victims include governments, law firms, healthcare providers, manufacturers, medical research companies, healthcare providers and more.”
Maze’s Modus Operandi
Callow explained that the group usually first claims the hacks after successful attacks and then — if the victim does not pay — they publish a small amount of the stolen data as proof of the hack. At this point, if the compromised entity still does not pay, Maze will start publishing more and more sensitive data:
“Should the company still not pay, more data is published, sometimes on a staggered basis, to ramp up the pressure. In previous cases, the criminals have also published the data on Russian cybercrime forums with a note to ‘Use this information in any nefarious ways that you want.’
In one previous incident, the group demanded $1 million to decrypt a company’s data plus an additional $1 million to destroy the copy that had been stolen.”
In February, Maze compromised five United States law firms and demanded two 100 Bitcoin ransoms in exchange for restoring data and deleting additional copies of their files. The ransom amount demanded from Chubb is not currently known.
According to company data website, Owler, Chubb is an insurance provider headquartered in Zurich with 32,700 employees and an annual revenue of $34.2 billion. The firm did not answer Cointelegraph’s inquiry by press time.
An Organized Hacker Group
Maze is a particularly notorious and well-organized cybercriminal group. Callow also told Cointelegraph that “Maze was the first ransomware group to steal and publish data, and it is a strategy that other groups have since adopted.”
Maze also publishes press releases on the same website where stolen data is published. Those announcements closely resemble the statements released by ordinary companies, although they often contain grammatical errors. In one such press release — published on March 22 — the group claims that it carries on its activities in an attempt to bring attention to the lack of cybersecurity. The release reads:
“We want to show that the system is unreliable. The cybersecurity is weak. The people who should care about the security of the information are unreliable. We want to show that nobody cares about the users. […] Some people like Julian Assange or Edward Snowden were trying to show the reality. Now it’s our turn. We will change the situation by making irresponsible companies pay for every data leak.”
The announcement also promises that the public will hear more about successful attacks by the group in the future. In another announcement — dated March 18 — the Maze group also promised that firms they hack amid the pandemic will have right to a discount in the ransom:
“Due to the situation with the incoming global economy crisis and virus pandemic, our Team decided to help commercial organizations as much as possible. We are starting an exclusive discount season for everyone who has faced our product. Discounts are offered for both decrypting files and deleting of the leaked data. To get the discounts our partners should contact us using the chat or our news resource.”
As Cointelegraph recently reported, Maze also infected the systems of Hammersmith Medicines Research, a United Kingdom firm researching the coronavirus. Maze published sensitive data on its website including the results of medical tests and id documents, such as passports.
Updated: 3-30-2020
Ryuk Ransomware Targets Hospitals Amid Coronavirus Pandemic
The operators of Ryuk ransomware continue to target hospitals, despite the intense pressures they are already facing as a result of the coronavirus pandemic.
On March 27, ‘PeterM’ of British IT security firm Sophos, tweeted that a United States-based healthcare provider had been targeted by Ryuk’s ransomware. PeterM stated that the cyber offensive “looks like a typical Ryuk attack,” posting:
“I can confirm that #Ryuk ransomware are still targeting hospitals despite the global pandemic. I’m looking at a US health care provider at the moment who were targeted overnight. Any HC providers reading this, if you have a TrickBot infection get help dealing with it ASAP.”
Two Of Seven Ransomware Operators Claim To Cease Targeting Hospitals
On March 18, cybersecurity publication BleepingComputer published a report after contacting seven ransomware operators to ask if they would continue to target hospitals despite the COVID-19 outbreak.
Only Maze and DoppelPaymer indicated that they would no longer target hospitals. Maze later decrypted and released data that it had stolen from a drug testing company that it had targeted prior to the pandemic.
Ryuk Did Not Respond To The Publication’s Request For Comment
One week later, Bleepingcomputer reported that software security firm SentinelOne had identified at least ten instances of Ryuk targeting at least 10 healthcare organizations during March — including one attack on a network of 9 hospitals.
Dutch Cybersecurity Firm Freely Fights Ransomware For Hospitals
As part of the “Tech against Corona” initiative — where a consortium of local tech companies are freely offering their services and technologies to the Dutch government to fight COVID-19 — IT security firm Cybersprint is helping hospitals fight ransomware.
In addition to providing its security services to the hospitals free of charge, it is also conducting a deep investigation into recent ransomware attacks to develop best practices to secure against future incidents.
Updated: 4-5-2020
Sophisticated Mining Botnet Identified After 2 Years
Cybersecurity firm, Guardicore Labs, revealed the identification of a malicious crypto-mining botnet that has been operating for nearly two years on April 1.
The threat actor, dubbed ‘Vollgar’ based on its mining of the little-known altcoin, Vollar (VSD), targets Windows machines running MS-SQL servers — of which Guardicore estimates there are just 500,000 in existence worldwide.
However, despite their scarcity, MS-SQL servers offer sizable processing power in addition to typically storing valuable information such as usernames, passwords, and credit card details.
Sophisticated Crypto-Mining Malware Network Identified
Once a server is infected, Vollgar “diligently and thoroughly kills other threat actors’ processes,” before deploying multiple backdoors, remote access tools (RATs), and crypto miners.
60% were only infected by Vollgar for a short duration, while roughly 20% remained infected for up to several weeks. 10% of victims were found to have been reinfected by the attack. Vollgar attacks have originated from more than 120 IP addresses, most of which are located in China. Guardicore expects most of the addresses corresponding to compromised machines that are being used to infect new victims.
Guidicore Lays Part Of The Blame With Corrupt Hosting Companies Who Turn A Blind Eye To Threat Actors Inhabiting Their Servers, Stating:
“Unfortunately, oblivious or negligent registrars and hosting companies are part of the problem, as they allow attackers to use IP addresses and domain names to host whole infrastructures. If these providers continue to look the other way, mass-scale attacks will continue to prosper and operate under the radar for long periods of time.”
Vollgar Mines Or Two Crypto Assets
Guardicore cybersecurity researcher, Ophir Harpaz, told Cointelegraph that Vollgar has numerous qualities differentiating it from most cryptojacking attacks.
“First, it mines more than one cryptocurrency – Monero and the alt-coin VSD (Vollar). Additionally, Vollgar uses a private pool to orchestrate the entire mining botnet. This is something only an attacker with a very large botnet would consider doing.”
Harpaz also notes that unlike most mining malware, Vollgar seeks to establish multiple sources of potential revenue by deploying multiple RATs on top of the malicious crypto miners. “Such access can be easily translated into money on the dark web,” he adds.
Vollgar Operates For Nearly Two Years
While the researcher did not specify when Guardicore first identified Vollgar, he states that an increase in the botnet’s activity in December 2019 led the firm to examine the malware more closely.
“An in-depth investigation of this botnet revealed that the first recorded attack dated back to May 2018, which sums up to nearly two years of activity,” said Harpaz.
Cybersecurity Best Practices
To prevent infection from Vollgar and other crypto mining attacks, Harpaz urges organizations to search for blind spots in their systems.
“I would recommend starting with collecting netflow data and getting a full view into what parts of the data center are exposed to the internet. You cannot enter a war without intelligence; mapping all incoming traffic to your data center is the intelligence you need to fight the war against cryptominers.”
“Next, defenders should verify that all accessible machines are running with up-to-date operating systems and strong credentials,” he adds.
Opportunistic Scammers Leverage COVID-19
In recent weeks, cybersecurity researchers have sounded the alarm regarding a rapid proliferation in scams seeking to leverage coronavirus fears.
Last week, U.K. county regulators warned that scammers were impersonating the Center for Disease Control and Prevention and the World Health Organization to redirect victims to malicious links or to fraudulently receive donations as Bitcoin (BTC).
At the start of March, a screen lock attack circulating under the guise of installing a thermal map tracking the spread of coronavirus called ‘CovidLock’ was identified.
Updated: 4-6-2020
Researchers Detect Ambitious Bitcoin Mining Malware Campaign Targeting 1,000s Daily
Cybersecurity researchers have identified a persistent and ambitious campaign that targets thousands of Docker servers daily with a Bitcoin (BTC) miner.
In a report published on April 3, Aqua Security issued a threat alert over the attack, which has ostensibly “been going on for months, with thousands of attempts taking place nearly on a daily basis.” The researchers warn:
“These are the highest numbers we’ve seen in some time, far exceeding what we have witnessed to date.”
Such scope and ambition indicate that the illicit Bitcoin mining campaign is unlikely to be “an improvised endeavor,” as the actors behind it must be relying on significant resources and infrastructure.
Using its virus analysis tools, Aqua Security has identified the malware as a Golang-based Linux agent, known as Kinsing. The malware propagates by exploiting misconfigurations in Docker API ports. It runs an Ubuntu container, which downloads Kinsing and then attempts to spread the malware to further containers and hosts.
The campaign’s end-goal — achieved by first exploiting the open port and then carrying through with a series of evasion tactics — is to deploy a crypto miner on the compromised host, the researchers say.
Security Teams Need To Up Their Game, Says Aqua
Aqua’s study provides detailed insight into the components of the malware campaign, which stands out as a forceful example of what the firm claims is “the growing threat to cloud native environments.”
Attackers are upping their game to mount ever more sophisticated and ambitious attacks, the researchers note. In response, enterprise security teams need to develop a more robust strategy to mitigate these new risks.
Among their recommendations, Aqua proposes that teams identify all cloud resources and group them in a logical structure, review their authorization and authentication policies, and adjust basic security policies according to a principle of “least privilege.”
Teams should also investigate logs to locate user actions that register as anomalies, as well as implement cloud security tools to strengthen their strategy.
Growing Awareness
Last month, Singapore-based unicorn startup Acronis published the results of its latest cybersecurity survey. It revealed that 86% of IT professionals are concerned about cryptojacking — the industry term for the practice of using a computer’s processing power to mine for cryptocurrencies without the owner’s consent or knowledge.
Updated: 4-7-2020
Microsoft Helps Hospitals Fight Ransomware Amid Coronavirus Pandemic
Global computing conglomerate Microsoft is notifying hospitals that are vulnerable to ransomware attacks to help prevent healthcare institutions from becoming overwhelmed amid the COVID-19 pandemic.
The firm also published recommendations to hospitals for securing their systems and preventing ransomware attacks on April 1.
Through the company’s network of threat intelligence analysts, Microsoft states that it “identified several dozens of hospitals” with vulnerable virtual private networks and other public-facing gateway applications in their systems:
“During this time of crisis, as organizations have moved to a remote workforce, ransomware operators have found a practical target: network devices like gateway and virtual private network (VPN) appliances. Unfortunately, one sector that’s particularly exposed to these attacks is healthcare.”
The document cites REvil as an egregious offender of targeting hospitals during the coronavirus crisis, while Cointelegraph has covered the recent prevalence of Ryuk attacks targeting healthcare organizations struggling amid the pandemic.
Hospitals Encouraged To Engage Opsec Specialists
Microsoft distributed “first-of-its-kind” targeted notifications to the hospitals containing “important information about the vulnerabilities, how attackers can take advantage of them, and a strong recommendation to apply security updates that will protect them from exploits.”
Hospitals were recommended to ensure regular updates for VPN and firewall configurations, greater monitoring of remote access infrastructure, and strengthened protocols for responding to breaches.
They are advised to seek greater engagement with operational security professionals and to schedule regular audits.
Microsoft is also participating in the “Tech Against Corona” initiative alongside roughly a dozen tech companies to freely provide technology to the Dutch government to fight coronavirus — which includes efforts to help hospitals fight ransomware.
Maze And DoppelPaymer Pledge Not To Attack Hospitals
Some ransomware and darknet marketplace operators have taken a rare moral stance amid COVID-19.
The operators of both Maze and DoppelPaymer have claimed that they will not launch ransomware attacks targeting hospitals during the pandemic.
Anonymous free-market Monopoly has also announced it will permanently ban all vendors caught using COVID-19 as a “marketing tool” — including selling purported coronavirus treatments, facemasks and toilet paper.
Dark web analysis firm Digital Shadows also found that the darknet community has exhibited “atypical” behavior in recent weeks, such as “discouraging other users from profiting off the pandemic, and “providing health and safety information.”
Updated: 4-15-2020
Google Removes 49 Phishing Extensions That Steal Cryptocurrency Data
Google recently removed 49 phishing Google Chrome web browser extensions after receiving reports about their activity.
Harry Denley, director of security at cryptocurrency wallet startup MyCrypto, explained in an April 14 Medium post how he got the extensions removed from Chrome’s store within 24 hours with the help of phishing-specialized cybersecurity firm PhishFort.
The removed extensions include ones that targeted the owners of hardware wallets produced by Ledger, Trezor and KeepKey, and users of software wallets Jaxx, MyEtherWallet, Metamask, Exodus and Electrum.
The extensions triggered the users to enter the credentials needed to access the wallet — such as mnemonic phrases, private keys and keystore files — and sent them to bad actors. Hackers were then able to steal the crypto assets contained in the wallets.
Some of the extensions also had fake five-star ratings in the Chrome extension store, but the reviews contained little to no info ranging from “good,” “helpful app” to “legit extension.”
One of the extensions reportedly had the same review copied and pasted eight times by different users. The copypasta included an introduction to Bitcoin (BTC) and explained why MyEtherWallet — the extension’s targeted wallet — was the preferred wallet option. It is worth noting that MyEtherWallet does not actually support Bitcoin.
One Bad Actor Controlled Most Extensions
The investigation uncovered 14 control servers behind all the extensions, but fingerprinting analysis revealed that some of the servers were managed by the same bad actors, with the oldest domain being linked to many other control servers. Denley subsequently concluded that the same bad actors were behind most of the extensions.
Some of the domains used in the phishing campaigns were relatively old, but 80% of them were registered in March and April 2020. Most of the extensions were published on Chrome’s store this month.
Not The First Phishing Extensions Targeting Crypto Users
This is not the first time that the community has discovered a malicious Google Chrome browser extension targeting crypto users. As Cointelegraph reported in late March, a Redditor warned the community that he lost some crypto assets after falling victim to a fake Ledger extension.
Google Chrome extensions targeting crypto users are so common, that earlier this month MyEtherWallet warned its user that its official extension was removed for allegedly containing malware. Fortunately, the extension was restored shortly after the team contacted Google to solve the issue.
Updated: 4-29-2020
Colorado Hospital Patient Information System Hit By Crypto Ransomware
Hackers have infected the infrastructure of Parkview Medical Center with ransomware that demands cryptocurrency in exchange for an encryption key.
Hackers have infected the infrastructure of Parkview Medical Center — the largest health center in Pueblo County, Colorado — with cryptocurrency ransomware.
Citing a hospital employee, Fox News reported on April 24 that Meditech — the Parkview Medical Center’s system for storing patient information — was infected with ransomware and rendered inoperable. The hospital confirmed the incident in a statement:
“On Tuesday, April 21, Parkview Medical Center was the target of a cyber-incident which has resulted in an outage in a number of our IT systems.”
As Cointelegraph recently reported, ransomware attacks against hospitals are ongoing, despite the fall in the overall number of attacks amid the coronavirus crisis.
Parkview Medical Center also told Fox that it has switched to a paper record system to track and treat patients:
“Upon learning of the incident, Parkview immediately engaged leading third-party forensic experts to investigate and mitigation is well underway. Patient care is always our first priority. Patients will not see any impact to the level or quality of care being delivered.”
Ransomware Is A Major Cybersecurity Threat
Ransomware malware is rapidly evolving and is increasingly viewed by many as a major — if not the biggest — cybersecurity threat. While nearly all ransomware discovered so far demands a ransom in cryptocurrencies, cybersecurity firm Check Point recently unveiled a new ransomware attack wherein the attackers require credit card payment.
As Cointelegraph reported earlier this month, another innovative ransomware recently started its switch from Bitcoin (BTC) to Monero (XMR) in an attempt to protect the cybercriminal’s identity.
Updated: 5-4-2020
Devs At Blogging Platform Ghost Take Down Crypto-Mining Malware Attack
Developers at blogging platform Ghost have spent the past 24 hours fighting a crypto mining malware attack.
Announced in a status update on May 3, the devs revealed that the attack occurred around 1:30 a.m. UTC. Within four hours, they had successfully implemented a fix and now continue to monitor the results.
No Sensitive User Data Compromised
Yesterday’s incident was reportedly carried out when an attacker targeted Ghost’s “Salt” server backend infrastructure, using an authentication bypass (CVE-2020-11651) and directory traversal (CVE-2020-11652) to gain control of the master server.
The Ghost devs have said that no user credit card information has been affected and reassured the public that no credentials are stored in plaintext. They were alerted to the incident as the hackers attempted to mine cryptocurrency using the platform servers:
“The mining attempt spiked CPUs and quickly overloaded most of our systems, which alerted us to the issue immediately.”
In an update posted within the last hour, the Ghost team announced that all traces of the crypto-mining virus have now been completely eliminated. They continue to “clean and rebuild” the entire network, and are apparently cycling all sessions, passwords and keys on every affected service on the platform as a precautionary measure.
A post-mortem of the incident will be published later this week.
Crypto-Mining Malware — A.K.A. Cryptojacking
As Cointelegraph has previously reported, crypto-mining malware — sometimes referred to as “cryptojacking” — has been increasingly rife in recent years.
These stealth attacks attempt to install malware that uses a target computer’s processing power to mine for cryptocurrencies without the owner’s consent or knowledge. As with Ghost, the load on the CPU of the hardware can be a telltale sign, although many attacks have previously continued to operate for significant stretches of time without detection.
Last month, international hacker and cybersecurity expert group Guardicore Labs revealed that as many as 50,000 servers worldwide had been infected with an advanced cryptojacking malware that mined a privacy-focused altcoin, Turtlecoin (TRTL).
The privacy-centric coin Monero (XMR) has been particularly prevalent in cryptojacking campaigns, with researchers reporting back in mid-2018 that around 5% of the altcoin in circulation had been created through stealth mining.
Updated: 5-4-2020
Hackers Plant Crypto Miners By Exploiting Flaw In Popular Server Framework Salt
A hacking group has installed crypto mining malware into a company server through a weakness in Salt, a popular infrastructure tool used by the likes of IBM, LinkedIn and eBay.
Blogging platform Ghost said Sunday an attacker had successfully infiltrated its Salt-based server infrastructure and deployed a crypto-mining virus.
“Our investigation indicates that a critical vulnerability in our server management infrastructure … was used in an attempt to mine cryptocurrency on our servers,” reads an incident report. “The mining attempt spiked CPUs and quickly overloaded most of our systems, which alerted us to the issue immediately.”
Ghost said Monday developers had removed the mining malware from its servers and added whole new firewall configurations.
Salt is an open-source framework, developed by SaltStack, that manages and automates key parts of company servers. Clients, including IBM Cloud, LinkedIn, and eBay, use Salt to configure servers, relay messages from the “master server” and issue commands to a specific time schedule.
SaltStack alerted clients a few weeks ago there was a “critical vulnerability” in the latest version of Salt that allowed a “remote user to access some methods without authentication” and gave “arbitrary directory access to authenticated users.”
SaltStack also released a software update fixing the flaw on April 23.
Android mobile operating system LineageOS said hackers had also accessed its core infrastructure via the same flaw, but the breach was quickly detected. In a report Sunday the company admitted it hadn’t updated the Salt software.
It remains unknown whether the same group is behind the LineageOS and Ghost attacks. Some attacks have planted crypto mining software, while others have instead planted backdoors into servers.
It isn’t clear if hackers mined a particular cryptocurrency. Hacking groups have generally favored monero (XMR), as it can be mined with just general purpose CPUs, not dedicated mining chips, and can be traded with little risk of detection.
Updated: 5-6-2020
Maze Ransomware Group Hacks Two Plastic Surgeons
Ransomware leaks social security numbers and other sensitive information from plastic surgery studios.
A cybercrime group recently infected two plastic surgery studios with ransomware. They subsequently leaked patient’s social security numbers and other sensitive information onto the internet.
Emsisoft threat analyst, Brett Callow, told Cointelegraph on May 5 that Maze recently took credit for hacking a plastic surgeon named Kristin Tarbet. They also claim to have hacked the Ashville Plastic Surgery Institute. He explained that in Tarbet’s case, the hackers have already leaked highly sensitive data:
“The data that has been posted included names, addresses, social security numbers as well as what appears to be before and after photos and photos taken during surgical procedures. The Maze group typically start by posting only a small amount of the data that was exfiltrated — it’s the equivalent of a kidnapper sending a pinky finger — so they may well have more data than has already been published.”
Callow explained that many ransomware incidents are caused by basic security failings. These include easy-to-crack credentials or unpatched remote access systems. He said that organizations should focus more on cybersecurity since “Maze uses a combination of strategies in order to gain access to networks including [Remote Desktop Protocol] exploitation, phishing, and spear-phishing.”
When It Comes To The Ransom Requested By The Hackers, He Said That It Cannot Be Known, But Past Attacks Could Serve As A Guide:
“Only the criminals and the plastic surgeon will know the amount of the demand. In a previous case, Maze claimed their demand was $2 million: $1 million to decrypt the victim’s data and an additional $1 million to destroy the copy of it.”
More Data To Be Leaked
When it comes to the Ashville Plastic Surgery Institute, the published data includes patient names, dates of birth, insurance details, patients’ implant order forms, before and after photos, and internal documents like income statements. Callow explained:
“This data dump is simply an initial warning shot. Should the company not pay, more data may be published.”
Callow said that this is not the first time the group has attacked two targets in the same industry. He explained that Maze’s victims often reside in the same geographic location or operate in the same industry. Maze claimed that there is a reason behind those instances in a statement:
“We don’t need to use phishing attacks and slowly move from one target to another as we have the access to the hosting provider.”
From Encrypting Data To Stealing It: The Evolution Of Ransomware
In recent months, Ransomware groups have started threatening to leak victim’s sensitive information if they are not paid. There was a time when ransomware groups would only render user data inaccessible and ask for the ransom for restoring access to it. As Cointelegraph reported in late April, a cybercrime group has published personal and financial data from the Californian City of Torrance and threatened to release 200 gigabytes more after the city’s officials denied that any data was stolen.
In mid-April, the first major ransomware group — REvil — also announced that it intends to switch from Bitcoin (BTC) to privacy-centric altcoin Monero (XMR). At the time Callow said:
“Like other businesses, criminal enterprises adopt strategies that have been proven to work and, accordingly, if this switch proves successful for REvil, we’d expect to see other groups begin to experiment with demands in currencies other than bitcoin.”
Updated: 5-6-2020
Ransomware Hackers Threaten To Release Credit Card Data From Costa Rican Bank
A group of ransomware hackers has reportedly stolen sensitive information from a major Costa Rican state-owned bank, Banco BCR.
A group of hackers dubbed Maze claims to have compromised the infrastructure of Banco BCR, a Costa Rican state-owned bank, and is now threatening to leak millions of credit card numbers.
On April 30, Maze Claimed That It Has Scoped Out The Bank In August 2019:
“According to Financial Institutions Protocol this bank had to notify other institutions about the security breach case. But nothing was made. Servers and workstations were not blocked. Private data was not secured. Anyway the Bank decided to conceal information about the breach. Though the security personnel were able to analyze the attack logs and to see that the attackers have accessed the payment processing system. We have stopped the attack as the possible damage was too high.”
Maze states that subsequently, in February 2020, they checked the systems and saw that nothing was done to fix the cybersecurity vulnerabilities. The hackers claim that because of this, they decided to steal the data from the bank, including transaction information and credit card data:
“We have got over 11 milion credit card credentials. Over 4 millions of those credit cards are unique. [Of those cards,] 140,000 belong to US citizens.”
The ransomware group announced on May 5 that it was going to leak the information without concealing card numbers. While in this particular instance there is no data on the amount of Bitcoin (BTC) requested by the hackers, the group has ransomed data in the past.
Do Not Take Ransomware Group’s Claims Too Seriously
Brett Callow, cybersecurity threat analyst at Emsisoft previously told Cointelegraph that hacker’s claims should be viewed suspiciously:
“Claims made by ransomware groups should be taken with a grain of salt. […] The details that the criminals choose to release will be cherry-picked and only information that they want to be in the public domain — probably because they believe it will help their cause in some way. […] The press should avoid portraying ransomware groups as being in any way Robin Hood-like or repeating claims that assist them.”
As of press time, Banco BCR has not answered Cointelegraph’s request for comment.
Ransomware Activity Continues Amid The Pandemic
As Cointelegraph reported in late April, a recent report showed a major drop in the number of ransomware attacks carried out during the pandemic on the United States public sector. Still, this is unlikely to be linked to the cybercriminals’ willingness to avoid damaging the public sector amid the distress already caused by the coronavirus.
In fact, at the end of April, hackers reportedly compromised the largest health center in Pueblo County, Colorado with cryptocurrency ransomware.
While the hospital’s official statements claim that it won’t affect patient care, workers allegedly said that the paper-based record-keeping methods to which they have resorted are cumbersome and could negatively impact services.
Updated: 5-7-2020
Europe’s Largest Private Hospital Hit By Crypto Ransomware Amid Pandemic
Hackers infected the largest private hospital in Europe with ransomware.
Hackers infected the IT infrastructure of the largest private hospital in Europe with ransomware.
Cybersecurity news outlet, KrebsonSecurity, reported on May 6 that hackers compromised the IT systems of Germany-based private hospital, Fresenius. An anonymous source reportedly informed the outlet that the hospital’s systems were infected by the ransomware known as Snake.
The ransomware in question was discovered earlier this year, and is being actively used to target large businesses. Fresenius spokesperson, Matt Kuhn, reportedly confirmed to KrebsonSecurity that the hack took place:
“I can confirm that Fresenius’ IT security detected a computer virus on company computers. […] As a precautionary measure in accordance with our security protocol drawn up for such cases, steps have been taken to prevent further spread. We have also informed the relevant investigating authorities.”
Kuhn also told the outlet that while some functions within the hospital are currently limited, patient care is still ongoing. He also said that Fresenius’ IT experts are currently working to solve the issues caused by the malware.
Ransomware Groups Attack Healthcare Providers Amid The Pandemic
Ransomware is believed by many to be the biggest threat among all existing malware. Given the strain that the coronavirus pandemic has placed on global healthcare systems, ransomware attacks on hospitals are of particular concern right now.
Cybersecurity firm, Emsisoft, has been offering free help to healthcare providers that fall victim to cryptocurrency-demanding ransomware since March. In April, Microsoft began notifying vulnerable hospitals to prepare for potential ransomware attacks.
Hackers continue to attack healthcare organizations despite a general fall in ransomware attacks amid the pandemic. At the end of April, hackers infected the infrastructure of the largest health center in Pueblo County, Colorado with ransomware. In late March, black hat hacker group, Maze, infected the infrastructure of a firm researching the coronavirus with ransomware.
A ransomware gang is threatening to release almost 1TB of private legal secrets from the world’s biggest music and movie stars.
The private legal affairs of dozens of the world’s biggest music and movie stars — Lady Gaga, Elton John, Robert DeNiro, and Madonna among them — are at risk of exposure following a ransomware attack on a high profile New York entertainment law firm.
Grubman Shire Meiselas & Sacks have reportedly been hit by the REvil ransomware (also known as Sodinokibi), with the attackers threatening to release up to 756GB of stolen data in nine staged releases.
The stolen data includes confidential contracts, telephone numbers, email addresses, personal correspondence, non-disclosure agreements and more. The ransom amount demanded is not available, however it is invariably paid in Bitcoin.
Cointelegraph has viewed the gang’s darknet site where they published screenshots of legal contracts for Madonna, Christina Aguilera and of the company’s computer folder system.
Credible And Proven Threat
Brett Callow from information security firm Emsisoft said the breach could have serious privacy ramifications as law firms hold highly sensitive information about their clients..
“It’s not only bad news for the firm; it also puts the clients whose data has been exposed at risk of blackmail, spear phishing, identity theft and other types of fraud. In this instance, REvil claim to have exfiltrated a total of 756GB of data.”
Callow described the screenshots leaked by the hackers as “the equivalent of a kidnapper sending a pinky finger”.
The firm represents a ‘Who’s Who’ of Hollywood and the music industry including: AC/DC, Barbara Streisand, Bette Midler, KISS, U2, Madonna, Maroon 5, Robert De Niro, Elton John, John Mellencamp, Rod Stewart, Ricky Martin, Shania Twain, KISS, The Weeknd, Lil Wayne, and David Letterman.
It also represents companies including Facebook, Activision, iHeartMedia, IMAX, Sony, HBO, and Vice Media, as well as athletes including LeBron James, Carmelo Anthony, Sloane Stephens and Colin Kaepernick.
Just A Warning Shot … For Now
“The data published so far would seem to simply be a warning shot,” Callow said. “Should the firm not pay, whatever data the criminals the criminals may have obtained will be published online, probably in instalments in order to gradually ramp up the pressure.”
REvil has previously attacked Travelex, 10x Genomics, Brooks International, Kenneth Cole and National Association of Eating Disorders and published data online from each. Travlex paid $2.3 million to recover its files.
Threatening to release company secrets has become an increasingly popular method by ransomware crews to ratchet up the pressure on companies to pay.
It was popularized by the Maze Crew who made good on threats late last year to release confidential information from security contractor Allied Universal after it failed to pay up.
Cointelegraph has contacted Grubman Shire Meiselas & Sacks for comment.

Updated: 5-8-2020
22 More Crypto-Stealing Google Chrome Extensions Discovered
A security researcher discovered another 22 Google Chrome web browser extensions that tried to steal users’ cryptocurrencies.
A security researcher has discovered another 22 Google Chrome web browser extensions built to steal their user’s cryptocurrencies.
Cybersecurity news outlet, Naked Security, reported on May 8 that Harry Denley, a security researcher specializing in cryptocurrencies, discovered 22 more malicious Google Chrome extensions. The extensions he discovered impersonated well-known crypto firms like Ledger, KeepKey, MetaMask, and Jaxx. Their purpose is to trick users into giving away the credentials needed to access their wallets.
Most of the phishing extensions have already been taken down as of press time. Per the report, most were down within 24 hours of Denley reporting them. Cointelegraph reached out to Harry Denley, but the researcher has not returned our inquiry by press time.
Google Chrome Extensions Are Often Used For Phishing
Google Chrome’s extensions store appears to be a major area of focus for cybercriminals looking to steal cryptocurrencies. At the end of April, Google managers changed the rules governing the publication of Chrome extensions in an attempt to make it more difficult for scammers to spread malicious code.
As Cointelegraph reported in mid-April, Google removed 49 phishing Chrome web browser extensions after reports of malicious activity. In early March, leading cryptocurrency hardware wallet producer, Ledger, warned its users about the phishing extensions on the store.
Late April reports suggest that Google still has to address the broader issue of phishing campaigns which utilize its platforms. A report suggests that the firm’s advertisement platform, Google Ads, was used to attract victims to the phishing clone of a cryptocurrency exchange. Meanwhile, blockchain firm Ripple Labs filed a lawsuit against Youtube, seeking damages after crypto scammers impersonated them on the platform.
Updated: 5-15-2020
Hackers Sell Data Of 129 Million Russian Car Owners For Bitcoin
A database of 129 million Russian car drivers is being exposed on the darknet for just 0.3 Bitcoin or about $2,900.
The major cryptocurrency, Bitcoin (BTC), continues to be actively used for illicit activity. Anonymous hackers have taken the data of over 129 million Russian car owners to expose it on the darknet in exchange for cryptocurrency.
The leaked information includes the full names, addresses, passport numbers and other data belonging to millions of Russian car drivers, Russian news agency RBC reported May 15.
The stolen data is claimed to be leaked from the registry of Russia’s patrol jurisdiction, the General Administration for Traffic Safety of the Ministry of Internal Affairs of Russia. The authenticity of data has reportedly been confirmed by an employee of a local car sharing company.
The leaked data is being sold for cryptocurrency, RBC said, citing an original report by local publication Vedomosti. As such, the full version of the database costs 0.3 BTC, which amounts to about $2,900 as of press time. The hackers also offered to buy some “exclusive” data for 1.5 BTC ($14,400), the report notes.
Cryptocurrencies are being increasingly used for illicit activity on darknet markets. According to Chainalysis — a New York-based blockchain analytics firm — the volume of darknet markets’ crypto flows doubled in 2019 for the first time in four years.
Cybercriminals often sell stolen data on the darknet for almost nothing or even give it away for free. In mid-April 2020, hackers were selling over 500,000 accounts of popular video conferencing platform Zoom for less than a penny each.
In March, cryptocurrency fund Trident Crypto Fund suffered a major security breach, resulting in the theft of 266,000 usernames and passwords.
Updated: 5-15-2020
Ransomware Gang Demands $42M or It Releases Trump’s ‘Dirty Laundry’
The ransomware gang responsible for stealing almost 1 TB of legal secrets from celebrities and entertainers last week is now targeting the President.
The ransomware gang that stole almost 1 terabyte of legal secrets from the biggest names in the entertainment industry is now demanding $42 million in cryptocurrency or else it will expose United States President Donald Trump’s “dirty laundry.”
The gang has already released a 2-gigabyte trove of legal documents marked “Lady Gaga” and fired the link to media outlets including Cointelegraph, which broke the news last week about the attack on New York law firm Grubman Shire Meiselas & Sacks.
The law firm has clients that include Elton John, Robert DeNiro and Madonna. The gang hacked and encrypted the firm’s server, stealing 756 GB of data on confidential contracts, telephone numbers, email addresses, personal correspondence, nondisclosure agreements and more. The company has so far refused to pay up.
Doubling Down
The REvil ransomware group —also known as Sodinokibi — posted a new message on May 14 that said they were doubling their original ransom and using dirt on Trump as leverage: “The next person we’ll be publishing is Donald Trump. There’s an election going on, and we found a ton of dirty laundry on time.”
Addressing Trump directly, REvil recommended he “poke a sharp stick at the guys” (referring to the law firm) within a week if he wanted to remain president. And to the voters: “We can let you know that after such a publication, you certainly [won’t] want to see him as president.”
The attackers have threatened to release the stolen data in nine staged releases unless their demands for a ransom are met by the firm. The ransomware gang prefers to be paid in Monero, but also accepts Bitcoin for a higher fee.
It’s unclear what link Trump has to the firm, as he’s not believed to have ever been a client.
Response From The Law Firm
According to the New York Post, Grubman is refusing to negotiate with the hackers, despite their threats to “destroy [the law firm] down to the ground if [they] don’t see the money.” He believes the hackers may release the documents even if he does pay, and the Federal Bureau of Investigation considers the hack an act of terrorism. The U.S. famously does not negotiate with terrorists.
Brett Callow of information security firm Emsisoft described the ransom as “one of the largest demands ever heard” and echoed Grubman’s sentiment:
“Companies in this situation have no good options available… Even if they pay the ransom demand, there is no guarantee the criminals will destroy the stolen data if it has a high market value. The data may still be sold or traded… In these cases, it’s possible that the criminals will attempt to extort money directly from the people whose information was exposed.”
Updated: 5-17-2020
Hackers Are Using Supercomputers To Mine Crypto
Hackers attacking supercomputers across Europe, trying to get their hands on mining crypto.
Hackers have attacked multiple supercomputers across Europe this week with the intention of mining cryptocurrency. Clusters of supercomputers have been forced to shut down in order to investigate the intrusions, according to a ZDNet news report on May 16.
These security incidents were reported in the UK, Germany, and Switzerland. Additionally, another possible attack occurred in a high-performance computer center in Spain, according to the report.
College Campuses Are The Main Victims
Most of the attacks appear to have targeted universities. University of Edinburgh,which runs the ARCHER supercomputer, reported the first incident on Monday.
Then, major universities’ high-performance computing clusters in the state of Baden-Württemberg, Germany also announced that they were attacked on Monday with similar security incidents, and had to be shut down.
More attacks happened in institutions in other parts of Germany, Spain, and Switzerland later in the week. Clusters in the Leibniz Computing Center, or LRZ, an institute under the Bavarian Academy of Sciences, the Julich Research Center in the town of Julich, Germany, the Faculty of Physics at the Ludwig-Maximilians University in Munich, Germany, and the Swiss Center of Scientific Computations, or CSCS, in Zurich, Switzerland were all counted amongst the victims.
SSH Logins Are Compromised And The Goal Is To Mine Crypto
The malware samples released by the Computer Security Incident Response Team were reviewed by a US-based cyber-security firm, says the news. The Computer Security Incident Response Team, or CSIRT, is a pan-European organization that coordinates research on supercomputers across Europe.
The cyber-security company said the attackers appear to have stolen university members’ SSH credentials in Canada, China, and Poland in order to gain access to the supercomputer clusters. Secure Shell, or SSH, is a cryptographic network protocol for operating network services securely over an unsecured network.
Chris Doman, Co-Founder Of Cado Security Explained That:
“Once attackers gained access to a supercomputing node, they appear to have used an exploit for the CVE-2019-15666 vulnerability to gain root access and then deployed an application that mined the Monero (XMR) cryptocurrency.”
As Cointelegraph reported previously, university campuses were ranked the second biggest miners of digital currency across industry.
Updated: 5-19-2020
Egg Producer’s Data Poached by Ransomware, Will They Shell Out Bitcoin?
Ransomware group Maze claims to have hacked United States egg producer Sparboe in a post on its website.
The website of cybercriminal organization Maze recently published a new entry claiming that the group hacked Sparboe. The post includes sample data that the group claims was stolen from the company.
Maze: A Major Cybercrime Organization
Threat analyst at cybersecurity firm Emsisoft Brett Callow told Cointelegraph that in every hack by Maze so far, the group asked for a ransom in Bitcoin (BTC). There also appears to be no particularly easy and focused way to protect companies from such hacks, as the group uses multiple attack vectors:
“Like other ransomware groups, Maze has been observed to use multiple methods to penetrate corporate networks including malspam, the use of stolen credentials and attacks on misconfigured or unpatched internet-facing systems.”
Maze is known for attacking high-profile companies and ask for particularly high ransoms. Previously, the group threatened to leak millions of credit card numbers after having allegedly hacked Banco BCR, a Costa Rican state-owned bank.
Maze is seemingly following its usual strategy, which includes rendering the victim’s data inaccessible by encrypting it and stealing a copy. Later the group asks for two separate ransoms to restore access to the data for the victim and another one to promise not to leak it.
As Cointelegraph Reported In Early May, Brett Callow Told Cointelegraph About Another Hack By Maze:
“In a previous case, Maze claimed their demand was $2 million: $1 million to decrypt the victim’s data and an additional $1 million to destroy the copy of it.”
A Controversial Hack Victim
According to Sparboe’s website, the Minnesota chick and egg distributor “hatched in 1954” and, according to company data website Owler, now has an estimated annual revenue of $30 million. The company is a major producer, but in 2011 it was dropped by McDonald’s and Target — one of its biggest clients — after Sparboe found itself in the midst of an animal cruelty scandal.
As CNN reported at the time, animal rights group Mercy for Animals shot an alleged undercover video at three of the Sparboe’s barns in Colorado, Iowa and Minnesota. The footage showed workers mistreating animals for fun, burning beaks and the birds being crammed into crowded cages. McDonald’s said in a statement:
“Regarding the undercover videos, the behavior on tape is disturbing and completely unacceptable. McDonald’s wants to assure our customers that we demand humane treatment of animals by our suppliers. […] It’s important to note that the most alarming actions on video did not occur at Sparboe’s Vincent, Iowa, facility that supplies McDonald’s.”
Updated: 5-19-2020
New Ransomware Uses A Banking Trojan To Attack Governments and Companies
A study from Group-IB reveals the modus operandi of the newly discovered ProLock’s ransomware attack.
A new type of ransomware attack emerged in recent months, raising red flags among the cybersecurity community and authorities such as the FBI in the United States. Cybersecurity firm Group-IB has warned that it comes in the form of a Trojan, according to a report published on May 17.
According to Group-IB’s study, the ransomware is known as ProLock and relies on the Qakbot banking trojan to launch the attack and asks the targets for six-figure USD ransoms paid out in BTC to decrypt the files.
The roster of victims includes local governments, financial, healthcare and retail organizations. Among them, the attack that Group-IB considers the most notable was against ATM provider Diebold Nixdorf.
35 BTC As The Total Payment In A ProLock Attack
The FBI detailed that the ProLock attack initially gains access to victim networks through phishing emails that often deliver Microsoft Word documents. Qakbot then interferes with configuring a remote desktop protocol and steals login credentials for systems with single-factor authentication.
According to Group-IB, the ransomware attacks ask for a total payment of 35 BTC — worth $337,750 as of press time. However, a Bleeping Computer study shows that ProLock demands an average of $175,000 to $ 660,000 per attack, depending on the size of the targeted network.
Speaking with Cointelegraph, Brett Callow, threat analyst at malware lab Emsisoft, explained some details about this new cyber threat:
“ProLock is unusual in that it is written in assembly and deployed using Powershell and shellcode. The malicious code is stored in either XML, video, or image files. Notably, the ProLock decryptor supplied by the criminals does not work correctly and corrupted data during the decryption process.”
Callow added that although Emsisoft developed a decryptor to recover victims’ data affected by ProLock without loss, such software does not remove the need for the ransom to be paid as it relies on the key supplied by the criminals.
ProLock Doesn’t Leak The Stolen Data
Although the techniques used by ProLock operators are similar to those of known ransomware groups that filter stolen data like Sodinokibi and Maze, Group-IB clarified the following:
“Unlike their peers, though, ProLock operators still don’t have a website where they publish exfiltrated data from companies that refuse to pay the ransom.”
Latest Ransomware Attacks
Cointelegraph has reported several ransomware attacks in recent weeks.
Ransomware group Maze claimed on May 19 to have hacked United States egg producer Sparboe, leaking preliminary information on a website to prove that they committed the attack.
A ransomware gang called REvil recently threatened to release almost 1TB of private legal secrets from the world’s biggest music and movie stars, such as Lady Gaga, Elton John, Robert DeNiro, Madonna, among others.
Updated: 5-22-2020
New Ransomware Employs Never-Before-Seen Attack Method
A UK-based cybersecurity firm unveiled new details of Ragnar Locker ransomware attack that uses a VirtualBox app.
A new study warns of a new ransomware attack method that runs a virtual machine on target computers in order to infect them with the ransomware. This may play the attack beyond the reach of the computer’s local antivirus software.
According to the UK-based cybersecurity firm Sophos, the Ragnar Locker attack is quite selective when choosing its victims. Ragnar’s targets tend to be companies rather than individual users.
Almost 1,850 BTC In Ransom Demanded In A Single Attack
Ragnar Locker asks victims for large amounts of money to decrypt their files. It also threatens to release sensitive data if users do not pay the ransom.
Sophos gave the example of the network of Energias de Portugal, who stole ten terabytes of sensitive data, demanding payment of 1,850 Bitcoin (BTC) in order not to filter the data. 1,850 BTC is worth roughly $11 million as of press time.
The modus operandi of ransomware is to take advantage of vulnerabilities in the Windows remote desktop app, where they obtain administrator-level access to the computer.
With the necessary permissions granted, attackers configure the virtual machine to interact with the files. They then proceed to boot up the virtual machine, running a stripped-down version of Windows XP called “Micro XP v0.82.”
Ransomware Tactics Are Getting More “Insidious And Extreme”
Speaking with Cointelegraph, Brett Callow, threat analyst at malware lab Emsisoft, provided more details on Ragnar Locker:
“The operators have recently been observed to launch the ransomware from within a virtual machine to avoid detection by security products. Like other ransomware groups, Ragnar Locker steals data and uses the threat of its release as additional leverage to extort payment. Should the company not pay, the stolen data is published on the group’s Tor site.”
Callow claims that the tactics deployed by ransomware groups are becoming ever more “insidious and extreme”, considering that the ransomware gangs behind Ragnar Locker now threaten to sell the data to the victim’s competitors or use it to attack their customers and business partners.
The Threat Specialist From Emsisoft Adds The Following:
“Companies in this situation have no good options available to them. Even if the ransom is paid, they simply have a pinky-promise made by a bad faith actor that the stolen data will be deleted and not misused.”
Recent Ransomware Attacks
On May 10, Cointelegraph reported on a study by Group-IB that revealed another type of ransomware that uses banking trojans to attack governments and companies, raising the red flags among the cybersecurity community and the FBI.
A ransomware gang called REvil also recently threatened to release almost 1TB of private legal secrets from the world’s biggest music and movie stars, such as Lady Gaga, Elton John, Robert DeNiro, Madonna, among others.
Updated: 5-26-2020
Ransomware Attacks Are Exploding In The Education Sector
A Verizon report highlights the growing number of ransomware attacks across educational services.
Educational services across the globe have been witnessing a surge in ransomware attacks in 2020. According to Verizon’s 2020 Data Breach Investigation Report, ransomware attacks account for approximately 80% of all cyberattacks suffered.
The data suggests 92% of these incidents were motivated by financial reasons, while only 3% aimed to perform espionage activities on businesses operating within education.
A Sharp Increase In Ransomware Attacks Since 2019
Ransomware attacks are growing at an alarming rate. Currently accounting for an overwhelming majority of all cyberattacks, ransomware was just 48% of the whole during 2019. Phishing is partially to blame here — ransomware attacks are more commonly made through fake websites than through emails.
Verizon report also says that that attackers don’t even need to be able to do the work themselves — they can rent the malicious software as a service. Verizon furthermore states that many companies still have a considerable lack of protection against ransomware, which also explains the increase.
Casey Ellis is founder and CTO of security company Bugcrowd. Speaking to Cointelegraph, he highlighted that many companies are vulnerable to the rise in ransomware in the age of COVID-19:
“As more organizations shift to remote work, we can expect to see more targeted ransomware attacks against remote working employees. Attackers will capitalize on vulnerabilities in the outside perimeter, allowing for more effective and destructive phishing attacks, such as subdomain takeovers, due to the high amount of rushed domain and configuration changes.”
Although ransomware can be mostly be executed by publicly known vulnerabilities, Ellis expects to see an increase of sophisticated attacks across all industries.
Updated: 5-28-2020
A New Ransomware Deploys Human-Operated Attacks Against Healthcare Sector
Microsoft unveiled a new human-operated ransomware called “PonyFinal” that deploys the attack by launching manually a payload.
Microsoft’s security team revealed a new ransomware that is deployed in human-operated attacks. It uses “brute force” against a target company’s systems management server, and mainly has targeted the healthcare sector amid the COVID-19 crisis.
According to a series of tweets published by the tech giant on May 27, the human-operated ransomware attack, named “PonyFinal”, requires hackers to break the security scheme of corporate networks in order to deploy the ransomware manually.
That means PonyFinal doesn’t rely on tricking the users into launching the payload through phishing links or emails.
A Java-Based Ransomware Attack
The Java-based Pony Final deploys a Java Runtime Environment, or JRE. Evidence found by Microsoft shows that attackers use information stolen from the systems management server to target endpoints where JRE is already installed.
The report further states that the ransomware is delivered via an MSI file that contains two batch files, including the payload that will be activated by the attacker.
Phillip Misner, research director of Microsoft Threat Protection, clarifies that there are other human-operated ransomware campaigns such as Bitpaymer, Ryuk, Revil, and Samas. PonyFinal was first detected at the beginning of April.
More Than One Group Of Attackers Are Using PonyFinal
The report highlights that authorship cannot be attributed to a single group of attackers, as several hacker groups are using this same form of ransomware.
Speaking with Cointelegraph, Brett Callow, threat analyst at malware lab Emsisoft, provided the following feedback on PonyFinal:
“Human-operated ransomware such as PonyFinal is not unusual and nor is its delivery method which, according to Microsoft, is ‘thru brute force attacks against a target company’s systems management server.’ Attacks on internet-facing servers are not at all unusual and account for a significant percentage of ransomware incidents. But they’re also mostly preventable as such attacks typically only succeed because of a security weakness or vulnerability.”
Callow adds that companies can significantly reduce the likelihood of being successfully attacked by adhering to best practices: using multi-factor authentication, patching promptly, and disabling PowerShell when possible.
Latest Ransomware Attacks In The Midst Of The Coronavirus Pandemic
Ransomware attacks continue to be carried out in different parts of the world in the midst of the COVID-19 crisis, with many targeting healthcare companies.
Cointelegraph reported on March 30 that operators of Ryuk ransomware continue to target hospitals.
On May 7, hackers reportedly infected the IT infrastructure of the largest private hospital in Europe, Germany-based Fresenius, with a ransomware known as Snake.
Updated: 5-28-2020
Colombia Is the Ransomware Capital of Latin America
A Colombian National Police report revealed that the country is the preferred target for ransomware attacks in Latin America.
A study unveiled on May 28 by the National Police of Colombia shows that ransomware attacks are a rising trend across the country. The report notes that 30% of all ransomware attacks within Latin American have specifically targeted Colombia.
The report, made in alliance with Cisco, McAfee, Microsoft, Absolute, Fortinet, and Claro, states that the threat of ransomware in Colombia is “underestimated.”
The quantity of Colombian attacks are followed by Peru (16%), Mexico (14%), Brazil (11%), and Argentina (9%), with SMEs being the preferred targets of cybercriminals.
The study shows that 83% of companies in the country lack response protocols necessary to handle the violation of information security policies.
Phishing Emails: The Preferred Way To Deliver Ransomware Attacks
The preferred method for attackers continues to be the massive sending of phishing emails. A high percentage of clicks come from victims who open links with ransomware attached.
The main threat is Lockscreen Ransomware, which prevents the targeted system from being use by locking the home screen. It also avoids the protection of antivirus and firewalls.
Other types of attacks include Encryption Ransomware, Master Boot Record Ransomware, Web Server Encryption Ransomware, and Mobile Device Ransomware.
Ransom payments generally range between 0.5 and 5 Bitcoin (BTC), depending on the current price of the cryptocurrency.
Up To $1 Million Ransoms Collected Through 2019
The National Police stated that the criminals collected between 300 million and 5 billion Colombian pesos ($80,300 – $1,134,000) in 2019 through ransomware attacks.
The study also says that the COVID-19 crisis has helped increase the number of ransomware attacks in the country, which is a pattern that has been repeating itself in other countries.
Cointelegraph also reported on March 14 about a report by DomainTools which unveiled new ransomware that took advantage of an Android app to install an attack on consumer devices.
Slovakia-based antivirus software provider, ESET, also discovered a trojan that can steal crypto. It is especially widespread in Latin America.
Updated: 5-30-2020
Congress Fears US Is Losing Battle To Malware And Darkweb Cyberweapons
As COVID-19 has the financial system more internet-dependent than ever, Congress is worried that the United States’ cyber defenses are not up to the current challenge.
In a May 28 virtual roundtable before the congressional Subcommittee on National Security, International Development and Monetary Policy, witnesses and congresspeople alike feared that they are not keeping up with criminals hacking the financial system.
Criminals Have Better Resumes Than Government Agents
One witness, Guillermo Christensen, a partner at law firm Ice Miller, admired the cyber talent operating illegally:
“We are always playing catch up with the criminals. […] It’s very hard to find people who are as qualified as some of these criminal hackers, frankly, to take apart their schemes and trace them.”
Another issue is the overclassification of government information, presenting a barrier to private-sector security efforts. “The information sharing between the private sector and the public sector is very valuable but it could be better,” saft Naftali Harris, co-founder and CEO of SentiLink, an anti-fraud software company.
Fintech’s Vulnerability During The Pandemic
In response to a question from subcommittee chairman Emanuel Cleaver (D-MO) as to the vulnerability of fintech to hacking, cybersecurity strategist Tom Kellermann warned that the current system is vulnerable to new developments and increasingly remote workflows:
“Financial institutions have the best security in the world, but because of telework and because of the customized malware or weaponry that are being developed in the darkweb, primarily the Russian-speaking darkweb. […] They’ve learned ways around the perimeter defense of the network security espoused by the standards of regulators around the world.”
Kellerman continued to explain that telework allows hackers easy access to well-defended financial networks via the worse-defended home systems of executives. He further called out APIs as adding another element of risk:
“The greatest vulnerability of fintech is they build out these APIs that allow them to connect to other financial institutions as well as other fintech vendors. Those APIs themselves are being exploited left and right.”
During the hearing, Chairman Cleaver commented that “It seems that we are losing this battle.” His closing remarks were no more optimistic. “Your comments were very informative but also very scary,” the chairman said.
Cointelegraph has reported previously on the rise in scamming and hacking amid the coronavirus pandemic. Indeed, a number of new threats specifically target hospitals and healthcare facilities.
Updated: 5-31-2020
Ransomware Attack Kidnaps Austrian City
An ongoing ransomware attack targets the public services infrastructure of Weiz.
Malware team, NetWalker, launched a ransomware attack against the Austrian village of Weiz. This attack affected the public service system and leaked some of the stolen data from building applications and inspections.
According to the cybersecurity firm, Panda Security, hackers managed to penetrate the village’s public network through phishing emails related to the COVID-19 crisis.
COVID-19 As Bait To Deploy The Ransomware
The subject of the emails — “information about the coronavirus,” — was used to bait employees of Weiz’s public infrastructure into clicking on malicious links, thus triggering the ransomware.
Panda Security claims that the attack belongs to a relatively new version of a ransomware family, which spreads using VBScripts. If the infection is successful, it spreads throughout the entire Windows network to which the infected machine is connected.
The report details that the ransomware terminates processes and services under Windows, encrypts files on all available disks, and eliminates backups.
Location Of Various Big Companies In Austria
Weiz is a small village that is considered the economic center of the Oststeiermark region, located a few kilometers from the city of Graz.
It is also the place where several big companies, like automaker Magna and construction companies Strobl Construction and Lieb-Bau-Weiz, have established their production plants. This may indicate that the attack was not random, but instead directed to a specific objective.
Netwalker Group recently authored several attacks targeting the healthcare sector across the globe.
Cointelegraph Spanish reported an attack on March 25 which wasperpetrated against hospitals in Spain.
This attack also used phishing emails to deploy ransomware to targeted systems.
Updated: 6-4-2020
Ransomware Strikes Three US Universities
Three US-based universities were targeted by the NetWalker ransomware group over the last seven days.
A ransomware gang claims to have successfully attacked three universities within the last seven days. They say that their latest attack was against the University of California San Francisco, or UCSF, on June 3.
Cointelegraph had access to the evidence published by NetWalker, a group of hackers, on their official dark web blog. In this blog, they claimed to have stolen sensitive data, including student names, social security numbers, and financial information.
NetWalker threatened to leak the data in less than a week if crypto payment in Bitcoin (BTC) is not made. The information is from Michigan State, Columbia College of Chicago, and UCSF.
Educational Services And Ransomware Attacks
As of press time, Michigan State University’s data was also reportedly stolen. The group is also threatening to release student data, according to the countdown displayed on NetWalker’s blog site.
Speaking with Cointelegraph, Brett Callow, threat analyst at malware lab Emsisoft and one of the first experts who spotted the massive attack, says that ransomware attacks in the education sector are an “enormously disruptive and costly problem.”
He relies on the latest Emsisoft’s data, which states that in 2019, at least 89 universities, colleges, and school districts were impacted by ransomware. He suspects that up to 1,233 individual schools were potentially affected.
Callow adds that the trend is continuing into 2020 with at least 30 universities, colleges, and school districts already impacted this year. Regarding the attack on the three US universities, Emsisoft’s threat analyst warned:
“(…) Even if the universities do pay, that will not solve the problem as they will only have a pinky promise.”
University Leading COVID-19-Related Antibody Tests Attacked
UCSF confirmed to Bloomberg that they were the target of an “illegal intrusion,” although they did not provide further details about the attack.
The educational institution is one of the universities leading antibody testing and clinical trials for possible coronavirus treatments.
Callow advises the education sector that systems should be promptly patched, email filtered, PowerShell disabled when not needed, and MFA used everywhere that it can be used. He adds that adhering to well-established best practices can “significantly reduce the likelihood of an organization being successfully attacked.”
The Emsisoft Analyst Adds The Following Regarding The Threat Level Of Recent Ransomware Attacks:
“Every time a ransom is paid, the criminals become more motivated and better resourced. The only way to stop ransomware attacks is to cut off the cash flow, and that means organizations must improve their security so as not to be in the position of needing to pay ransoms.”
Recently, Cointelegraph reported the latest findings of Verizon’s 2020 Data Breach Investigation Report, which revealed that education services worldwide have been witnessing a surge in ransomware attacks in 2020.
Updated: 6-5-2020
The Latest Ransomware Victim Is A NASA Contractor
A DopplePaymer ransomware attack reportedly targeted one of NASA’s IT contractors in the United States.
As SpaceX and NASA celebrated their first human-operated rocket launch on May 30, cybercriminals behind a ransomware known as DopplePaymer launched an attack against one of NASA’s IT contractors.
According to a blog post by the hackers, the gang managed to breach the network of the Maryland-based Digital Management Inc, or DMI. This company provides IT and cyber-security services to several Fortune 100 companies and government agencies.
DopplePaymer hackers leaked almost 20 archive files belonging to NASA through a portal operated by the gang, including HR documents and project plans. Some of the employee details matched with public LinkedIn records.
Ransomware Threatens To Leak Stolen Data
The report claims that DopplePaymer managed to encrypt about 2,853 servers and workstations during the attack. It could not be independently corroborated whether the entire affected infrastructure is related to NASA.
The modus operandi of this ransomware is similar to that perpetrated by Maze or REvil — It threatens to release targeted company data if the ransom is not paid.
Speaking with Cointelegraph, Brenda Ferraro, VP of Third-Party Risk at third-party risk management firm Prevalent, commented on NASA’s ransomware attack:
“NASA’s Third-Party Risk Management program must harmonize both threat intelligence and risk assessments to avoid breach incidents root caused by IT contractors, dark web, ransomware, etc. (…) In fact, if NASA’s program does not incorporate cyber and business intelligence as an integral part of their risk program and invoke continuous monitoring and evaluation as a mandatory risk management practice, IT contractor hygiene vulnerability weaknesses will be found by the adversaries.”
Bolstering Crypto Risk Mitigation
On the role that cryptos continue to play in the increase in ransomware attacks, Ferraro said the following:
“During ransomware attacks, crypto threat intelligence plays a critical role in providing a lens on real-time dark and deep web sourced blind spots such as; hidden websites, handles, IP addresses and in some cases physical locations.
Without in-the-moment crypto intelligence, the victimized networks are open to activity such as ransomware as a service, money laundering services, etc. in blockchain time.”
Aetna’s former CISO also warned about the current large volume of crypto exchange and its role in the ransomware attacks:
“If you do not bolster the adoption of crypto risk mitigation and use continuous threat intelligence monitoring, the trend of ransomware attacks will instigate the crypto’ wild west’ economy, resulting in securing an uncomplicated landscape for the bad actors to access and sell the information.”
Latest Ransomware Attacks By Other Ransomware Gangs
Recently, three US-based universities were targeted by the NetWalker ransomware. Cointelegraph also reported on a ransomware attack perpetrated against Texas-based data center provider, CyrusOne, by the REvil gang.
Updated: 6-6-2020
Another Free Ransomware Decryptor Released
Emsisoft launched a free tool that decrypts files affected by a variant of the Tycoon ransomware attack.
Malware lab, Emsisoft, released a free decryptor tool on June 4. The tool enables victims to recover files encrypted by Tycoon ransomware attacks without needing to pay the ransom.
Researchers from the BlackBerry’s security unit first discovered the ransomware. They stated in TechCrunch that Tycoon uses a Java file format to make it more difficult to detect before deploying its payload that encrypts the files.
How Does Tycoon Work
Speaking With Cointelegraph, Brett Callow, Threat Analyst Of Emsisoft, Said:
“Tycoon is a Java-based, human-operated ransomware that appears to specifically target smaller enterprises and is typically deployed via an attack on RDP. Java-based ransomware is unusual, but certainly not unique. Microsoft warned about another Java-based ransomware strain, PonyFinal, last month.”
On The Tool, Callow Also Clarified Some Of The Limitations Of The Free Tool “Emsisoft Decryptor For RedRum”:
“(…) the tool only works for files encrypted by the original Tycoon variant, not for files encrypted by any subsequent variants. This means it will work for files that have a .RedRum extension, but not for files with .grinch or .thanos extension. Unfortunately, the only way to recover files with those latter extensions is to pay the ransom.”
A Multi-OS Ransomware
BlackBerry’s researchers noted that Tycoon ransomware can run on both Windows and Linux computers, employing the same technique of asking for cryptocurrency payments like Bitcoin (BTC).
The latest findings show that Tycoon infections mostly target educational institutions and software houses. Researchers from BlackBerry believe that the actual number of infections “is likely far higher.”
Furthermore, they warn that newer versions of Tycoon ransomware have been improving its attack power. Previously, decryption tools could be used to recover files for multiple victims, but that is no longer possible.
On June 3, ElevenPaths, the specialized cybersecurity unit of the Spanish telecommunications conglomerate, Telefonica, created a free tool called “VCrypt Decryptor”. This tool aims to recover data encrypted by the VCryptor ransomware amid the international initiative “No More Ransomware.”
Updated: 6-7-2020
Beware Fake Ransomware Decryption Tools
Creators behind Zorab ransomware launched a fake tool that double-encrypts files affected by the attack.
As free ransomware decryptor tools begin to enter the market, a wave of fake software that claims to decrypt ransomware-affected files has begun to proliferate.
According to a report released by Bleeping Computer on June 5, the creators behind Zorab ransomware released a fake STOP Djvu decryptor. Instead of recovering a victim’s data however, this software appears to encrypt their files further with a second ransomware.
When the victim opens one of these tools, the software extracts an executable file called crab.exe. This is the Zorab ransomware itself. Once executed, the tool will encrypt all files present with a .ZRB extension.
Double-encryption Files
Speaking with Cointelegraph, Brett Callow, threat analyst of the malware lab Emsisoft, says that STOP is the most prevalent ransomware by far. He states that it accounts for approximately one-half of all incidents:
“Unfortunately, criminals often create fake versions of popular software in order to spread malware, and they have now created a fake version of our decryptor to do just that. Running the fake tool will not recover data that was encrypted by STOP, it will actually encrypt it for a second time.”
Callow refers to one of several free tools launched recently by Emsisoft. These tools allow people to decrypt files affected by specific ransomware variants.
Emsisoft’s Threat Analyst Issued The Following Warning To The Public:
“This illustrates why people should exercise caution when downloading software and apps and ensure it has come from a reputable and trustworthy source. Similarly, cracks, activators, and keygens should be avoided as these are also frequently used to spread ransomware and other malware.”
Latest Free Ransomware Decryptor Tools Released
Cointelegraph recently conducted extensive coverage on different free ransomware decryptors launched by various tech companies.
On June 3, Spain-based telecommunications conglomerate, Telefónica, released a free tool to recover data encrypted by the VCryptor ransomware.
Emsisoft also launched a free decryptor tool on June 4, which enables victims to recover files encrypted by Tycoon ransomware attacks without needing to pay the ransom.
Updated: 6-7-2020
Singapore Sees 300% Yearly Spike In Q1 Cryptojacking Attacks Amid COVID-19
The first quarter of 2020 saw ransomware attacks targeting devices in Singapore spike by four-fold compared with last year.
Data published by Russian cybersecurity firm Kaspersky indicates that Singapore has seen a significant increase in the prevalence of attempted cryptojacking attacks during the first quarter of 2020.
Kaspersky estimates that 11,700 attacks were attempted on devices located in Singapore from January until March — up from 2,900 as of the first Q1 2019.
Kaspersky asserted that the spike in attacks is the highest percentage increase posted within the South-East Asian region.
Cryptojacking Attacks Up Three-Fold In Singapore
In an interview with Straits Times, Kaspersky’s general manager for South-East Asia, Yeo Siang Tiong, described Singapore’s high-performance internet infrastructure as attracting the operations of malicious cyber actors.
“Cyber criminals use various means to install miner programs on other people’s computers, preferably in bulk, and take all of the profit from cryptocurrency mining without incurring any of the equipment or electricity costs,” said Tiong.
Tiong asserts that the increasing difficulty of mining incentivizes cryptojackers seeking to command a botnet network rather than targeting individual devices, stating:
“It is now no longer profitable to mine cryptocurrency using one’s own equipment and electricity. It is better to resort to hijacking other resources for the mining of cryptocurrency.”
Coronavirus Creates New Opportunities For Hackers
The cybersecurity head at law firm Eversheds Harry Elias, K.K. Lim, attributed the recent increase in cryptojacking attacks to large numbers of individuals working from home, or WFH, amid the COVID-19 pandemic creating lots of low-hanging fruit for attackers.
“We can definitely say that WFH increases the opportunity just like phishing, because some WFH home computers may not update their security updates as it is a general computer used by everyone,” said Lim.
“Practising good basic cyber hygiene like not clicking on unknown links in email, going to official government, commercial and legitimate websites for news and other information, having updated end-point security and constant training for corporates are some effective ways to avoid these crypto miners,” Lim added.
In April, security firm Acronis echoed the assertions of Eversheds and Kaspersky, estimating that the later weeks of March saw a dramatic spike in the number of crypto mining attacks targeting consumers.
Updated: 6-8-2020
Ransom Costs For Stolen Data Rose 200% From 2018 to 2019
On average, ransoms demanded by cryptocurrency ransomware hackers increased by 200% from 2018 to 2019.
According to a report published on June 5 by cybersecurity firm Crypsis Group, the average ransom demanded by cryptocurrency ransomware groups in 2019 reached $115,123.
The median ransom, on the other hand, increased by 300% from 2018’s first quarter to the last quarter to 2019, reaching over $21,700. According to Crypsis Group, ransoms have grown as hackers increasingly target enterprises and select victims who are able to pay higher sums.
Just yesterday, Cointelegraph reported that ST Engineering Aerospace’s United States subsidiary fell victim to a ransomware attack which resulted in the theft of 1.5 terabytes of sensitive data from the firm and its partners.
The highest ransom that Crypsis has seen since 2015 was $5 million, paid by a healthcare organization.
The highest ransom ever demanded was $15 million dollars, after hackers had stolen data from a data center and solutions provider.
The Attack Vectors
Crypsis also reveals that in 50% of ransomware infections, the attack vector was the remote desktop protocol. The report explains that “when enabled, RDP allows users to remotely connect to other Windows-based devices or networks.” When RDP is implemented in inadequate ways it can become an easy attack vector.
The second leading attack vector cited in the report is social engineering, usually email phishing or spearphishing. Social engineering refers to techniques that manipulate people rather than just computers to obtain the desired goal, such as information useful to infect the systems.
Phishing is the practice of sending messages — usually emails — with malicious intent, often including malware as an attachment. While phishing is usually sent en masse to great numbers of people, spearphishing attacks are targeted towards the recipient, with personalized content meant to make the message more convincing.
Updated: 6-9-2020
Ransomware Gangs Are Teaming Up To Form Cartel-Style Structures
The latest moves from ransomware groups suggest that gangs are forging alliances to create a mafia-style structure.
Recent ransomware attacks from well-known cybercriminal groups have been suggesting that gangs are forging cartel-style alliances to pressure their respective victims to pay the ransom requests.
Cointelegraph has obtained access to what seems to be a darknet site that belongs to the Maze group. On the site, Maze has been leaking stolen data beginning sometime after Sunday.
The central feature to highlight is that the gang notes that Ragnar Locker, another ransomware group, provided the info, as the title of the blog post says: “MAZE CARTEL Provided by Ragnar.” Some of the victims listed are United States-based companies.
Speaking with Cointelegraph, Brett Callow, a threat analyst at malware lab Emsisoft, stated that Ragnar Locker’s leak site is currently offline, suggesting that it might have pulled the site permanently and plans to distribute all future leaks via Maze. Still, he clarified that this is not confirmed yet.
Leaking Data Becoming A Pattern In Maze’s Ransomware Attacks
Maze has been leaking stolen data from ransomware attacks against companies in different industries through the group’s darknet website when the victims refuse to pay the ransom.
Cyber intelligence company Kela revealed that at some point in the first week of June, Maze operators added another bunch of data stolen — but from another ransomware gang known as LockBit.
Future Alliances Coming Up Soon?
In statements sent to BleepingComputer on June 3, the Maze group said the following:
“In a few days another group will emerge on our news website, we all see in this cooperation the way leading to mutual beneficial outcome, for both actor groups and companies.”
The average ransom payments requested by the groups exceed $100,000 per incident, often in Bitcoin (BTC) and Monero (XMR). In some reports, victims are said to have paid up to “millions” of dollars.
Callow Commented On The Ragnar Locker Stolen Data Made Available On Maze’s Site:
“Ragnar Locker are likely banking on the Maze group’s name recognition to further pressure companies into meeting their demands. While this is only the second such collaboration that we’re aware of, it’s likely that other groups will join the cartel if they believe it is in their financial interests to do so.”
Recent Maze’s Attacks
The Maze ransomware group has made a number of headlines due to its recent attacks.
Cointelegraph reported on May 6 that the gang infected two U.S.-based plastic surgery studios with ransomware. It subsequently leaked patients’ Social Security numbers and other sensitive information onto the internet.
Maze recently claimed to have hacked a major egg producer, Sparboe.
Updated: 6-10-2020
Alabama City Plans To Pay Ransomware Group Despite Warnings
Florence, AL was targeted by the DoppelPaymer ransomware attack and officials plan to pay the ransom demanded.
A ransomware gang launched an attack on the information technology systems of Florence, Alabama in may. This attack came despite warnings by cybersecurity firms about possible hacker infiltration into the city’s infrastructure.
According to a KrebsOnSecurity report from June 8, city officials intend to pay a ransom of nearly $300,000, citing concerns that failing to do so may result in private citizens having their personal data leaked. If paid, the ransom will be covered in Bitcoin.
DoppelPaymer Group Behind The Ransomware Attack
Wisconsin-based security firm, Hold Security, first alerted the city to the threat DoppelPaymer represented to the city’s IT infrastructure, as well as their 40,000-residents.
Last Friday, Florence Mayor Steve Holt officially confirmed that the city’s email system was hacked.
Although he did not initially acknowledge that it was a ransomware attack, he confirmed via the KrebsOnSecurity report that DoppelPaymer was behind the attack on June 9.
The Mayor confirmed that hackers initially demanded 39 BTC ($378,000). With the help of an external security firm, they managed to reduce the price to 30 BTC ($291,000), with the caveat being that if they do not pay this amount in-full, the hackers will leak the data.
Speaking With Cointelegraph, Brett Callow, Threat Analyst At Malware Lab Emsisoft, Commented:
“Despite being warned that its network had been compromised, Florence was nonetheless hit by ransomware due to the inadequacy of its response to the initial incident. Organizations cannot afford to be sloppy when it comes to remediating incidents. Completely rebuilding the networking is the only sure-fire way to ensure that an incident such as this does not become a ransomware event in which data is encrypted and possibly exfiltrated.”
The Hackers Often Target Cities’ IT Infrastructures
Callow says that the ransomware group has claimed multiple other victims, including the City of Torrance, Visser Precision, and Kimchuk.
DoppelPaymer is known for being one of the ransomware that asks for the most money in its attacks, mainly targeting companies and government offices.
Alex Holden, Chief Information Security Officer Of Hold Security, Told Cointelegraph:
“As we monitor many notorious cyber gangs, ransomware is the most preferred vector of attack because of ease of cashing out – paid by the victims themselves. Also, historically, a significant number of victims do not take alerting seriously and often do not follow the best practices ending up victimized regardless of advanced notice. Plus, the victims are not shy about paying ransom, as it became a “norm” in our society today.”
Recently, the DoppelPaymer gang managed to breach Maryland-based Digital Management Inc’s network. This company provides IT and cyber-security services to several Fortune 100 companies and government agencies, like NASA.
Updated: 6-10-2020
Hackers Increasingly Rely On Trojans To Deploy Ransomware Attacks
Kroll’s Cyber Risk team detected a growing trend in the use of banking trojans to launch ransomware attacks.
A study by risk solutions provider, Kroll, identified a growing trend in the use of Qakbot trojan, or Qbot, to launch email thread hijacking campaigns and to deploy ransomware attacks.
According to the findings in conjunction with analysts from the National Cyber-Forensics and Training Alliance, or NCFTA, cybercriminals seek to steal financial data from multiple industries like media, education, and academia. However, the COVID-19 pandemic has helped the attacks target the healthcare sector as well.
The trojan is reportedly being used as a “point of entry” by the operators behind the ProLock ransomware gang. The report suggests that victims are easy targets due to the sophisticated phishing structures established by the criminals.
Methods Of Attacks Used By The Qakbot Trojan
Qakbot is a banking trojan that has been active for over a decade, says Kroll, and relies on the use of keyloggers, authentication cookie grabbers, brute force attacks, and windows account credential theft, among others.
One of the authors of the research, Laurie Iacono, vice president of Kroll’s cyber risk team, explained the following reasons to Cointelegraph why cybercriminals are relying on trojans like Qakbot to launch ransomware attacks:
“The ultimate reason is to maximize their profits. Within the past 18 months, Kroll has observed multiple cases where a trojan infection is the first step of a multi-phased attack—hackers infect a system, find a way to escalate privileges, conduct reconnaissance, steal credentials (and sometimes sensitive data), and then launch a ransomware attack from an access level where it can do the most damage.
They can make money on the ransom payment and potentially on the sale of stolen data and credentials—plus the stolen data helps force infected companies to pay the ransom.”
Research co-author and vice president of Kroll’s cyber risk department, Cole Manaster, clarified to Cointelegraph that the rise of thread hijacking attacks like the ones deployed by Qakbot shows an evolution. He adds the following:
“Criminals are aware of the increasing cybersecurity training across email users and are producing more sophisticated, and authentic-looking phishing lures.”
COVID-19 Crisis Boosting The Level Of Threat In Cybercrimes
On the other hand, Iacono said that the use of trojans by ransomware is not uncommon and gives an example of the Ryuk attacks that are preceded by the installation of the Emotet trojan, and DoppelPaymer attacks preceded by Trickbot injections.
She cautions that, with more workers at home due to the COVID-19 crisis, they see “an uptick in attacks exploiting vulnerabilities in remote work applications such as the Citrix exploit.”
Cointelegraph reported on May 17 that the gang ProLock is relying on the Qakbot banking trojan to launch the attack and asks the targets for six-figure USD ransoms paid out in Bitcoin (BTC) to decrypt the files.
Updated: 6-11-2020
New Ransomware Uses Sophisticated Evasion Techniques
Recorded Future says that Thanos deploys a particular encryption technique in its attack and offers a revenue-sharing scheme for external hackers.
Cybersecurity firm, Recorded Future, revealed on June 10 that a ransomware attack named “Thanos” has been promoted on a number of darknet hacking forums since February.
According to the report, Recorded Future’s Insikt Group uncovered the new ransomware-as-a-service attack.
“Ransomware-as-a-service” methods consist of allowing external hackers to use the ransomware to attack their targets in exchange for adhering to a revenue-share scheme with the developers by splitting profits of 60% – 70% approximately.
The Major Feature Of Thanos Ransomware
Speaking with Cointelegraph, Lindsay Kaye, director of operational outcomes of Insikt Group at Recorded Future, explains further the encryption’s feature used in the ransomware:
“Thanos does not have any particularly sophisticated or novel characteristics that we were able to identify, but the remarkable feature that Insikt Group found and that spurred this research is the malware’s use of the RIPlace technique in its file encryption process. Previously, the RIPlace technique was only observed in the proof of concept published by Nyotron, but the Thanos ransomware demonstrates an example of a threat actor productizing the technique for use in malware.”
The Thanos ransomware builder allows the operator to customize the software’s ransom note. They can modify the text to ask for any cryptocurrency of their choosing, not just Bitcoin (BTC).
Though it is an advertised possibility, Kaye says that so far, they have not observed the use of Monero with the ransomware.
Encryption’s Level of Strength
The Director Of Operational Outcomes Of Insikt Group At Recorded Future Advised:
“Ransomware attacks, if successful, can be hugely debilitating to companies. Because Thanos by default uses an AES encryption key that is generated at runtime, without the attacker’s private key, recovery of the files is impossible. That said, to minimize the risk of an attack using Thanos, organizations should continue to employ information security best practices for mitigating the threats posed by ransomware.”
Cointelegraph previously reported that DopplePaymer hackers leaked a number of archive files belonging to NASA through a portal operated by the gang, including HR documents and project plans. These files came from Maryland-based Digital Management Inc, or DMI, which is an IT contractor that works with several companies and government entities.
Updated: 6-11-2020
Ransomware Attack Targets Victoria Beckham’s Personal Data
Maze ransomware group threatens to leak stolen data from Threadstone Advisors, LLC.
Ransomware gang, Maze, strikes again. This time, the victim is a US-based independent advisory firm specializing in the consumer and retail sectors. They have a number of big clients including businesswoman and former Spice Girl, Victoria Beckham.
Maze’s official dark web blog lists Threadstone Advisors, LLC as one of their victims following an attack within the last 24 hours.
Threadstone Advisors, LLC worked with Victoria Beckham to establish an investment liaison with NEO investment partners. Among the advisory firm’s clients are Charles S. Cohen, Pittsburgh Brewing Co., and Xcel Brands.
Stolen Data Leak Is “Coming Soon”
As of press time, Maze has leaked information belonging to Threadstone’s managing director, Joshua Goldberg. The group claimed that proof of further stolen data is “coming soon,” according to the announcement.
Such a threat could mean that the company has not paid the ransom demanded by the gang, and there is also no information on how much money in cryptos was requested.
Cointelegraph reached out to representatives from Threadstone Advisors, LLC, but have not yet received a response. We will update this article with comments accordingly.
Brett Callow, Thread Analyst At Malware Lab Emsisoft, Told Cointelegraph:
“The fact that other ransomware groups have adopted Maze’s encrypt-and-exfiltrate double-whammy style of attack likely proves that the strategy works and, consequently, it will probably eventually be adopted by those groups which do not currently steal data.
Of course, the strategy will be more effective in some cases than in others. Companies which hold highly sensitive information relating to their clients – such as an M&A advisory – may be more inclined to pay to prevent their data being posted online than other businesses.”
Ransomware Gangs Are Getting More Aggressive
The cybersecurity expert warns that the tactics employed by ransomware groups like Maze are becoming “ever more extreme”. He states that hackers are weaponizing stolen data via threats against business partners, clients, and to harm companies ’reputations.
Callow Adds The Following:
“This may be a natural evolution, or it may be a response to the Covid-19 pandemic. With so many companies facing financial challenges, fewer may be able or willing to pay ransom demands resulting in the groups seeking to exert additional pressure in an attempt to increase their conversion rate.”
ST Engineering Aerospace’s US subsidiary recently suffered a ransomware attack, reportedly by Maze, that managed to extract about 1.5TB of sensitive data from the firm and its partners.
The gang also claimed to have hacked United States egg producer, Sparboe, in a post on its website. The blog post includes sample data that the group claims was stolen from the company.
Updated: 6-12-2020
Robotics Company Falls Prey To Ransomware Attack
Ransomware gang REvil strikes a US-based robotics firm, leaking their sensitive data on the dark web.
Ransomware gang REvil, known for launching stolen data auctions on the dark web, is now leaking sensitive documents stolen from a US-based robotics company.
According to an official blog post from REvil on June 11, the team has started leaking confidential data belonging to Symbotic LLC. The post noted:
“You do not want to speak with us and you probably think that we will not publish your data. We are already publishing.”
The cybercriminal group stated that they’d created a website and paid for the hosting for a year. They threatened to make the robotics company’s data visible for “a very long time in public.”
Sensitive Data Leaked
Leaked data includes employee names, addresses, SSNs, salary details, non-competition agreements, and more. The group reportedly asked for both Bitcoin (BTC) and Monero (XMR) to cover the ransom payment.
The cybersecurity research team, Cyble, said the attack may have occurred in the first week of June.
Symbotic LLC was founded in 2007. They currently have a workforce of approximately 1,000 employees. They develop software and robotics solutions for supply chain manufacturers, distributors, and retailers.
Ransomware Growing Into “Serious Problem”
Speaking with Cointelegraph, Brett Callow, threat analyst at malware lab Emsisoft, commented:
“Ransomware attacks continue to be a serious problem, and that’s because companies continue to pay ransoms. The only way to stop attacks is to make them unprofitable and that means companies must improve their security so as not to be in the position of needing to pay ransoms. Too often, attacks succeed only because of subpar security, and that needs to change.”
Callow has said that it sounds like the ransomware gang may not be planning to auction the robotics company’s data.
However, that shouldn’t be taken as a 100% confirmed fact. He says that REvil could act unpredictably at any time.
Cointelegraph recently reported that REvil had listed sensitive data from two US-based law firms.
Updated: 6-15-2020
Knoxville Is The Latest American City To Suffer A Ransomware Attack
The city of Knoxville had to shut down its IT infrastructure following a ransomware attack launched by an unknown gang.
An unidentified ransomware gang attacked the city of Knoxville, Tennessee’s IT network, forcing officers to shut down all systems on June 12.
According to local news station WVLT, the attack took place sometime between June 10–11, encrypting all files within the network infrastructure.
The attack forced workstations of the internal IT network to be shut down, which also disconnected internet access from the mayor’s infrastructure, public website, and even the Knoxville court.
The FBI is currently assisting in the investigation, although the identity of the ransomware group behind the attack has not yet been revealed.
The Official Statement From The Knoxville’s Major
Knoxville mayor and former WWE wrestler Glenn Jacobs released a statement via the official Knoxville government Twitter profile:
“Cyber attacks can happen to anyone or any government no matter how good the defense is. In a lot of cases it’s not a matter of ‘if’ but a matter of ‘when.’ Our IT department has been in contact with the city and we stand ready to help if they need it.”
Knoxville joins a long list of cities in the United States that have been targeted by ransomware groups in recent months, along with Atlanta, Baltimore, Denver, New Orleans, and other smaller cities.
Cointelegraph recently reported that the NetWalker ransomware gang had attacked Michigan State University, or MSU. At the time, the gang threatened to leak students’ records and financial documents. However, the university’s officials have said that they will not pay the ransom.
Updated: 6-17-2020
Online Fantasy Sports Company Recognizes Ransomware Attack In SEC Filing
DraftKing reveals that a ransomware attack was behind the latest cybersecurity incident of SBTech.
Fantasy-sports company, DraftKing Inc, recently filed a Form S-1 registration statement with the U.S. Securities and Exchange Commission, or SEC. This form indicates that SBTech, a company DraftKing Inc acquired, was hit by a ransomware attack in March.
According to the registration form, which is required by the SEC before companies may go public on Nasdaq, SBTech, an online gambling technology provider which merged with DraftKing, suffered the cyber attack before the merger finalized on March 27.
The SEC’s Filing Stated:
“On March 27, 2020, SBTech detected a ransomware attack on its network (the“ cybersecurity incident ”). SBTech immediately shut down its data centers. The operation of the sports betting and iGaming services of SBTech’s customers was interrupted as a result of the cybersecurity incident. SBTech informed relevant regulatory authorities and notified affected partners and customers. SBTech believes it is in compliance with applicable regulatory requirements related to the cybersecurity incident.”
Ransomware Gang Not Revealed In The Sec Filing
According to ZDNet, the online betting company had to place $30 million in escrow on April 10 to deal with the cyberattack. At that time, this attack was not yet confirmed as the result of ransomware. The funds in escrow were set aside to cover damage costs and litigation fees.
No additional details were disclosed in the SEC filing.
DraftKing clarified that the interruption to its operations led SBTech to compensate its customers for downtime. They state that this had an immaterial financial impact on SBTech and DraftKings to date.
SBTech’s investigation concluded that the impact of the cybersecurity incident was successfully mitigated. It also included recommendations for security improvements to SBTech’s network and its information technology controls.
Recent Ransomware Incidents
Recently, an Israel-based company reportedly paid $250,000 in Bitcoin (BTC) to a ransomware gang that threatened to shut down its systems.
Cointelegraph reported on June 10 that a ransomware attack named “Thanos” has been promoted on a number of darknet hacking forums since February.
Updated: 6-17-2020
Crypto-Ransomware Attacks Are Spreading Like A Hacking Wildfire
With ransomware attacks up 200% in the last two years, Cointelegraph looks at some of the methods bad actors are employing and how to avoid them.
The last two years have witnessed a hefty uptick in crypto-centric ransomware attacks. Not only are bad actors becoming more refined, but they are facilitating access to other, less sophisticated ones. According to experts, crypto crime of this nature has been especially prevalent amid the coronavirus pandemic. But how does it all connect, and what can the industry do to stamp it out?
As with all groups, the cryptocurrency sector has its portion of bad apples. Since 2018, ransomware attacks worldwide have increased by 200%. To make matters worse, the software required to carry out such attacks is widely available on the darknet.
In Singapore, the situation is arguably at a fever pitch. Instances of so-called “crypto-jacking” — a ransomware method in which criminals commandeer devices to mine cryptocurrency — spiked 300% year-on-year in Q1 2020. Per cybersecurity firm Kaspersky, the increasing difficulty of mining coupled with the subsequent hike in electricity costs is at the root of the problem. As for why Singapore is so disproportionately affected, Kaspersky suggested the country’s high-performance internet may be attracting bad actors.
But this is by no means a localized phenomenon. According to the “2020 Incident Response and Data Breach Report” from cybersecurity firm Crypsis Group, ransomware attacks have more than doubled in the last two years.
It seems COVID-19 has been a boon for cybercriminals. During a recent United States house meeting, the FBI revealed a 75% rise in daily cyber crimes since the onset of the coronavirus. Expert witness Tom Kellermann, head of cybersecurity strategy for VMware, also cited an inconceivable 900% uptick in ransomware attacks between January and May 2020.
Speaking to Cointelegraph, Thomas Glucksmann, vice president of global business development at the blockchain analytics firm Merkle Science, explained that the escalation in ransomware and cryptojacking attacks could be attributed to the exploitation of pandemic-related anxiety through targeted COVID-19 themed campaigns.
“Such campaigns include emails or websites advertising treatments, government information and fake apps which prompt users to download malicious software that infects devices and can be used to compromise data and networks (via ransomware) and computing power (cryptojacking).”
The Finessing Of Ransomware Attacks
Along with an uptick in attacks came refined techniques and modifications. This includes Ryuk and Sodinokibi — also known as “REvil.” These particularly insidious ransomware variants deny users access to their device, system or file until a ransom is paid. Both Ryuk and REvil are designed to prey on enterprise networks. Law firms Fraser, Wheeler & Courtney LLP and Vierra Magen Marcus LLP found this out the hard way.
Both firms were victims of the REvil ransomware attack from the threat group of the same name. On June 6, REvil’s official darknet blog announced the auctioning of over 1.7 TB of data seized from the firms’ databases. The listing was described as containing both private company and client information, including business plans and patent agreements of companies ranging from Asus to LG. The starting bid price of Fraser, Wheeler & Courtney’s data was set at $30,000 — to be paid solely in Bitcoin (BTC). REvil noted that if the price reserve wasn’t met, the files would be publicized nonetheless.
This is not the first time REvil has caught headline news. The group previously struck Grubman Shire Meiselas & Sacks — the law firm connected to music stars such as Madonna, Lady Gaga and Nicki Minaj. However, after failing to extract payment, they seemingly switched up their modus operandi, raising the stakes on their victims via public auctions.
Another ransomware gang, known as “Maze,” took things one step further, targeting the government-affiliated aeronautics firm, ST Engineering Aerospace. Maze plucked around 1.5 TB of data from the organization — 50 GB of which found its way onto the darknet shortly after. One notable aspect of this attack was that the ransomware was initially undetectable. Another particularly nasty and near-imperceptible breed of ransomware, aptly dubbed “STOP,” encrypts the victim’s entire system, demanding payment in return for decryption.
It’s perhaps no surprise, then, that ransomware detection and decryption software are becoming commonplace, offering a means to fight back and decrypt files made inaccessible by attackers.
Nevertheless, bad actors are twisting this to their advantage by disguising ransomware as ransomware decryption software.
Rather than decrypting ransomware-infected files, the fake software encrypts them further, ensuring that victims have no choice but to pay up or face losing data permanently.
Ransomware-As-A-Service
It isn’t just sophisticated cybergangs who have access to these tools, either. To make matters worse, ransomware is openly sold on the darknet. Officially termed ransomware-as-a-service, or RaaS, threat actors are peddling their franchises to less-than-tech-savvy miscreants.
Glucksmann noted that while the majority of RaaS offerings are duds, this new commerce-based criminality is nevertheless aiding the ransomware epidemic: “Not all of this malware for sale is actually usable but the existence of such services shows how malware has become commoditized and such a common threat.” Taking a similar line, blockchain analytics firm Chainalysis went as far as to position RaaS as a reason for the recent rise in attacks. Kim Grauer, head of research at Chainalysis, told Cointelegraph:
“We suspect that the proliferation of Ransomware as a Service (RaaS) is contributing to the increase in ransomware attacks, many attackers who develop ransomware technology now allow less sophisticated attackers to rent access to it, just as a business would pay a monthly fee for software like Google’s G-Suite. The key difference is that the builders of the Ransomware also get a cut of the money from any successful attack.”
Fortunately, law enforcement agencies are starting to gain an edge. According to data from cybersecurity firm Trend Micro, official takedowns of multiple darknet marketplaces have cast doubt in criminal minds. With darknet data in the hands of law enforcement, protecting anonymity stood as a primary concern among criminals — causing darknet sales to drop significantly as a result.
However, Grauer believes the drop still wasn’t big enough as market revenue generated by the darknet has already reached $790 million, adding: “We haven’t quite reached halfway through 2020 yet, but the amount of darknet market revenue is already over half of the 2019 value.”
Are Things Really That Bad?
Cryptocurrencies are often over stigmatized as tools for corruption. This stereotype has dominated the crypto narrative throughout the years, warped as a convenient attack vector for crypto detractors. As evidence suggests, this narrative isn’t altogether accurate.
The industry’s association with unlawful activity started — as everything in crypto has — with Bitcoin. According to Tom Robinson, co-founder and chief scientist of blockchain analytics firm Elliptic, in the early days of crypto, around 2012, criminal activity accounted for over a third of all Bitcoin transactions. This figure has dramatically shifted since, as Robinson told Cointelegraph:
“The absolute amount of criminal usage of crypto might have increased, but the overall use of crypto has increased faster. According to Elliptic figures, back in 2012, 35% of all Bitcoin transactions by value were associated with criminal activity — at that time it was mostly illicit trade on the Silk Road dark market. Today, illicit Bitcoin transactions account for less than 1% of all Bitcoin transactions.”
Still, a report from Ciphertrace suggests that 2020 could become a record year for cryptocurrency-related thefts, hacks and fraud. For Grauer, it’s still far too early to call. “Looking at total illicit activity so far this year, we see it is actually trending low compared to last year,” said Kennedy, adding that, “It’s possible we’ll see a dramatic increase in scamming in the second half of the year.”
Total Share Of Crypto Exchanged By Illicit Entities
Avoiding Ransomware Attacks
So, with ransomware attacks more rampant than ever, there are several methods people can use to avoid getting caught out. “It’s important for people and organizations to stay informed on emerging threats and techniques,” Kennedy explained. “We can help cyber teams quantify and prioritize the threat landscape and identify emerging players and actors dominating the scene.” Providing some practical advice, Glucksmann advocated for a degree of paranoia to any suspicious-looking email, website, app or contact request.
“Ensuring all your personal and company online services are protected with multi-factor authentication can also make it more difficult for a threat actor to obtain your data or cryptocurrency funds even if they are somehow able to compromise your device. For stronger multi-factor authentication set-up I would strongly recommend a hardware token instead of a mobile device.”
“Don’t pay the ransom as this could be deemed illegal by law enforcement in many jurisdictions,” Glucksmann hastened to add.
Updated: 6-19-2020
Ransomware Gang Auctions Off US Healthcare Data For Bitcoin
NetWalker continued to launch ransomware attacks to the healthcare sector during the COVID-19 pandemic.
Crozer-Keystone Health System recently suffered a ransomware attack by the NetWalker ransomware gang. The gang is now auctioning the system’s stolen data through its darknet website. If it is not purchased at auction within six days, the gang has vowed to leak the data.
On June 19, Cointelegraph was able to access the alleged publication. There appeared to be dozens of folders with an undisclosed amount of data, mostly concerning finances, but nothing related to medical records of patients.
The gang claims that Crozer-Keystone Health System failed to pay for the ransom they demanded in Bitcoin (BTC).
Crozer-Keystone is a health system made up of four hospitals. It is based in Delaware County, Pennsylvania, and serves Delaware County, northern Delaware, and parts of western New Jersey.
No Major Details Were Given By The Health System On The Attack
The healthcare system addressed the incident via DataBreaches.net. They did not provide details regarding the ransom amount, or confirm whether patient data was compromised:
“After quickly identifying a recent malware attack, the Crozer-Keystone information technology team took immediate action and began remediating impacted systems. Having isolated the intrusion, we took necessary systems offline to prevent further risk. We completed this work in collaboration with cybersecurity professionals across our healthcare system and are currently conducting a full investigation of the issue.”
Hospitals Attacked During COVID-19 Pandemic
Speaking With Cointelegraph, Brett Callow, Threat Analyst And Ransomware Expert At Malware Lab Emsisoft, Said:
“Attacking a hospital system is a despicable and unconscionable act, especially in the middle of a pandemic. A number of ransomware groups stated they would not attack healthcare providers for the duration of the pandemic and, somewhat surprisingly, they have been good to their word. NetWalker was not one of those groups.”
Callow warned about the dangers of such attacks, noting that they can be extremely disruptive and potentially put lives at risk. He recalled that during previous incidents, hospitals have had to effectively close their doors and reroute emergency patients to other hospitals:
“This is the last thing that’s needed at a time when healthcare services are already stretched to the limit due to Covid-19.”
In 2019, at least 764 US healthcare providers were impacted by ransomware, according to Emsisoft’s own research.
On June 10, Cointelegraph reported that risk solutions provider, Kroll, identified a growing trend in the use of the Qakbot trojan, or Qbot, to launch email thread hijacking campaigns that deploy ransomware attacks.
Updated: 6-24-2020
Millions of Telegram Users’ Data Exposed on Darknet
Telegram’s built-in contact import feature was exploited to leak the personal data of millions of users onto the darknet.
Telegram, a major privacy-focused messaging app, has suffered a data leak that exposed some personal data of its users on the darknet.
A database containing the personal data of millions of Telegram users has been posted on a darknet forum. The issue was first reported by Russian-language tech publication Kod.ru on Tuesday.
According to the report, the database contains phone numbers and unique Telegram user IDs. It remains unclear exactly how many users’ data was leaked while the database file is about 900 megabytes.
About 40% Of Entries In The Database Should Be Relevant
Telegram has reportedly acknowledged the existence of the leaked database to Kod.ru. The database was collected through exploiting Telegram’s built-in contacts import feature at registration, Telegram reportedly said.
Telegram noted that the data in the leaked database is mostly outdated. According to the report, 84% of data entries in the database were collected before mid-2019. As such, at least 60% of the database is outdated, Telegram declared in the report.
Additionally, 70% of leaked accounts came from Iran, while the remaining 30% were based in Russia.
At press time, Telegram has not responded to Cointelegraph’s request for comment. This article will be updated should they respond.
Just The Latest Leak
This is not the first instance of Telegram users’ phone numbers being leaked. In August 2019, Hong Kong activists reported on a vulnerability that exposed their phone numbers, allowing Chinese law enforcement agencies to track protesters’ identities.
In response to the vulnerability, Telegram expanded user privacy tools in September 2019. Specifically, Telegram introduced a feature allowing users to show their phone number to nobody at all. The feature’s description reads:
“If you set Who Can See My Phone Number to ‘Nobody’, a new option will appear below, allowing you to control your visibility for those who already have it. Setting Who Can Find Me By My Number to ‘My Contacts’ will ensure that random users who add your number as a contact are unable to match your profile to that number.”
The report comes soon after Russian authorities lifted the two-year ban on Telegram app in the country.
Updated: 6-24-2020
Celebrities May Have Their Dirty Secrets Exposed If Crypto Ransom Is Unpaid
Ransomware group threatens to auction secrets stolen from a law firm specializing in the entertainment industry.
The REvil ransomware gang says that they will auction over 1TB of data stolen from New York-based entertainment law firm, Grubman Shire Meiselas & Sacks. This data allegedly contains the “dirty” secrets of a number of celebrities. REvil claims that the contents involve sex scandals, drugs, and treachery.
Nicki Minaj, Lebron James, And Mariah Carey Among The Alleged Victims
In a blog post, the ransomware group says they will begin the auction on July 1, noting that the first round will contain information from Nicki Minaj, Mariah Carey, and LeBron James. The price for each dataset is $600,000.
Two days later, REvil plans to auction information belonging to Bad Boy Ent. Hold. Inc, Universal, and MTV. The first has a starting price of $750,000, while the latter sets are to be sold for $1M each.
Alternatively REvil will allow a single entity to purchase the full contents for $42,000,000. The currency requested for the auction is Monero (XMR).
The gang, also known as Sdinokibi, left a warning for law firm head, Allen Grubman:
“Mr. Grubman, you have a chance to stop that, and you know what to do.”
While no further details were provided, REvil says that stolen data also contains cases of “bribery celebrity by Democratic Party, sexual harassment by top politicians, the envy of celebrity for each other.”
“Dirty Secrets” As Bait To Scam People?
Speaking with Cointelegraph, Brett Callow, threat analyst and ransomware expert at malware lab Emsisoft, pointed out:
“As REvil obtained (and published) relating to Lady Gaga, it’s likely that they were able to obtain documents relating to other celebrities too. Whether the documents really do contain details of sex and political scandals is impossible to say.
REvil could simply be making a bogus claim in the hope of upping the amount that people will bid.”
Callow Adds That Parties In This Situation Are In An Unfortunate Position:
“Even if the ransom is paid, they’ll simply receive a pinky promise that the data will not be used or sold – and that pinky promise is being made by a (very) bad faith actor.”
On May 15, REvil also demanded $42 million in cryptocurrency to prevent the exposure of United States President, Donald Trump’s “dirty laundry”.
Updated: 6-25-2020
COVID-19 Ransomware Plagues Canadian Android Users
CryCyptor ransomware poses as a government-backed COVID-19 Android tracing app to deploy its attack.
A new ransomware called CryCryptor is targeting Canadian Android users. It is distributed via multiple websites that pose as portals for a government-backed COVID-19 tracing app.
According to research published by ESET on June 24, CryCryptor appeared shortly after Canada’s government announced a COVID-19 tracing app that utilizes voluntary information submitted by citizens.
Once the victim installs the fake app, the ransomware encrypts all files, leaving a “readme” note with the attacker’s email instead of locking the device. For this particular attack, ransom instructions appear to only be distributed via email.
An Open Source Ransomware
The ransomware’s code is based on an open source project which is available through GitHub. Experts dismiss the claim that this ransomware “project” has research purposes:
“The developers of the open source ransomware, who named it CryDroid, must have known the code would be used for malicious purposes. In an attempt to disguise the project as research, they claim they uploaded the code to the VirusTotal service. While it’s unclear who uploaded the sample, it indeed appeared on VirusTotal the same day the code was published on GitHub.”
ESET analysts have recently created an Android decryption app for victims of CryCryptor. They clarify that it only works with the current version.
On April 28, Cointelegraph reported that cybercriminals have been posing as the FBI in an effort to defraud Android users.
Earlier this year, a study published by the Colombian Chamber of Informatics and Telecommunications revealed that in 2019, 89% of malware on Android in the country included code for crypto mining.
Updated: 6-27-2020
Ransomware Gang Failed To Deploy An Attack Against 30 US Firms
Symantec revealed that a WastedLocker ransomware attack was blocked on time after an early alert by the cybersecurity firm.
Cybersecurity firm Symantec blocked a ransomware attack by a group known for demanding payment in Bitcoin (BTC) directed at 30 U.S.-based firms and Fortune 500 companies.
The announcement published by the cybersecurity firm claims that the Evil Group, the malware gang behind the attacks, targeted the IT infrastructures of the firms. Still, the companies were alerted in time to prevent deployment of the ransomware. The group used the ransomware WastedLocker and managed to breach the security of the victims’ networks and unsuccessfully attempted to laying the ground for staging the attacks.
Gang Asks For Million-Dollar Payments
Cointelegraph reported recently a study made by the cybersecurity firm Fox-IT, a division of NCC Group, warned about the return of Evil Group’s cybercriminal activities, after a short period of going quiet.
The gang is well known for asking its victims to pay million-dollar ransom payments in cryptocurrencies like Bitcoin. There are reports that the group had been asking for a combined total of $10 from an unknown number of U.S. companies that were recently attacked.
Symantec’s Targeted Attack Cloud Analytics team first detected the early stages of WastedLocker attacks by relying on advanced machine learning to spot patterns of activity related to recent targeted attacks.
Evil Group targeted 31 companies in the blocked attack, one of the firms is a U.S.-based subsidiary of an overseas multinational.
Most Affected Sector
Symantec did not identify the intended victims but the cybersecurity firm’s report said the manufacturing sector was most affected, as the gang targeted five organizations related to that industry.
According to Symantec, had the attackers not been disrupted, “successful attacks could have led to millions in damages, downtime, and a possible domino effect on supply chains.”
Evil Group had previously halted its operations until January 2020 due to the indictment of alleged members, Igor Olegovich Turashev and Maksim Viktorovich Yakubets.
Updated: 7-2-2020
Unknown Cybercrime Gang Holds Thousands of Databases For Ransom
MongoDB suffered a “Wiping & Ransom” attack that wiped around 22,900 unsecured databases.
Cross-platform database company, MongoDB, is the latest victim of a cybercriminal attack. This attack has infiltrated 22,900 unsecured databases by wiping their contents. The gang behind the attack has since requested Bitcoin (BTC) payments in exchange for a backup of the data.
According to WeLiveSecurity from the cybersecurity firm ESET, if the ransom isn’t paid in two days, the hacker, or a gang of cybercriminals, threatened to notify authorities in charge of enforcing European Union’s General Data Protection Regulation, or GDPR.
A report published by ZDNet explains that the number of databases compromised in the “Wiping & Ransom” attack account for almost 47% of all the MongoDB’s databases.
Over $3.2 Million In Total Demanded By The Hackers
The hackers used an automated script to scan each database, and left a ransom note demanding 0.015 BTC, or around $140, for each one. The hackers also included a guide which explains to victims how they can purchase the required Bitcoin.
Victor Gevers, A Security Researcher At The GDI Foundation, Said:
“The first few attacks lacked the data-wiping feature. Once the miscreant realized the mistake in their script, they amended it and started wiping the MongoDB databases. Instances of attacks using this particular ransom note have been recorded all the way back to April of this year.”
In total, the hackers are seeking around $3.2M from MongoDB.
In June, ransomware group, REvil, launched a series of attacks that targeted three companies in the U.S. and Canada. They later leaked data from two of the companies and threatened to disclose sensitive data from the third.
Updated: 7-4-2020
The Most Malicious Ransomwares Demanding Crypto To Watch Out For
As tech advances, so too, do the malware attacks. Amid a pandemic, ransomwares are turning to privacy-centric coins to get away with crime.
As interconnectivity turns the world into a global village, cyberattacks are expectedly on the rise. According to reports, the tail end of last year saw a spike in the average amount of payments made to ransomware attackers, as several organizations were forced to pay millions of dollars to have their files released by malware attackers.
Apart from the fact that the current pandemic has left many individuals and corporations vulnerable to attacks, the notion that cryptocurrencies are an anonymous and untraceable payment method has led many ransomware attackers to demand payment in Bitcoin (BTC) and other altcoins.
Just recently, a report published on June 23 by cybersecurity firm Fox-IT revealed a malware group named Evil Corp that has been on a rampage with new ransomware that demands its victims to pay a million dollars in Bitcoin.
The report also reveals that groups such as Evil Corp create ransomware that targets database services, cloud environments and file servers intending to disable or disrupt backup applications of a company’s infrastructure. On June 28, cybersecurity firm Symantec reported blocking a ransomware attack by Evil Corp that targeted about 30 United States firms demanding Bitcoin in payment.
These attempted attacks are just the most recent examples of the escalating threat of ransomware attacks. Below are some of the most malicious ransomware demanding payment in crypto.
WastedLocker
WastedLocker is the latest ransomware created by Evil Corp, a group that has been active since 2007 and is regarded as one of the most lethal cybercrime teams. After the indictment of two alleged members of the group, Igor Turashev and Maksim Yakubets, in connection to the Bugat/Dridex and Zeus banking trojans, Evil Corp reportedly reduced its activity.
However, researchers now believe that as of May 2020, the group has resumed attacks once again, with the WastedLocker malware as its latest creation. The malware has been named “WastedLocker” due to the filename created by the malware, which adds an abbreviation of the victim’s name to the word “wasted.”
By disabling and disrupting backup applications, database services and cloud environments, WastedLocker prevents its victims’ ability to recover their files for a longer period of time, even if there is an offline backup setup. In cases where a company lacks offline backup systems, recovery can be prevented indefinitely.
Researchers, however, note that unlike other ransomware operators that leak victim’s information, Evil Corp has not threatened to publish victims’ information in order to avoid attracting public attention to itself.
DoppelPaymer
DoppelPaymer is ransomware designed to encrypt the files of its target, preventing them from accessing files and subsequently encouraging the victim to pay a ransom to decrypt the files. Used by an eCrime group called INDRIK SPIDER, the DoppelPaymer malware is a form of BitPaymer ransomware and was first discovered in 2019 by CrowdStrike software endpoint protection company.
Recently, the ransomware was used in an attack against the City of Torrance in California. More than 200 GB of data was stolen, with the attackers demanding 100 Bitcoin in ransom.
Other reports reveal that the same malware was used to attack the city of Alabama state’s information technology system. The attackers threatened to publish citizens’ private data online unless they are paid $300,000 in Bitcoin. The attack came after warnings from a cybersecurity firm based in Wisconsin. A cybersecurity specialist analyzing the case mentioned that the attack that had brought down the city’s email system was made possible through the username of a computer belonging to the city’s manager of information systems.
Data from Chainalysis shows that the DoppelPaymer malware is responsible for one of the largest payouts, one of only two to reach the $100,000 mark.
Dridex
According to a report by cybersecurity provider Check Point, the Dridex malware entered the top-10 list of malware for the first time in March 2020 after an initial appearance in 2011. The malware, also known as Bugat and Cridex, specializes in stealing bank credentials using a system of macros on Microsoft Word.
However, new variants of the malware go beyond Microsoft Word and now target the entire Windows platform. Researchers note that the malware can be lucrative for criminals thanks to its sophistication, and is now being used as a ransomware downloader.
Even though last year saw the takedown of a botnet linked to Dridex, experts believe that such successes are often short-lived, as other crime groups can pick up the malware and use it for other attacks. However, the ongoing global pandemic has further escalated the use of malware such as Dridex, easily executed through email phishing attacks, as more people are required to stay and work from home.
Ryuk
Another malware that has resurfaced as a result of the coronavirus pandemic is the Ryuk Ransomware, which is known for targeting hospitals. On March 27, a spokesman of a British-based IT security firm confirmed that despite the global pandemic, Ryuk ransomware is still being used to target hospitals. Like most cyberattacks, the Ryuk malware is distributed via spam emails or geo-based download functions.
The Ryuk malware is a variant of Hermes, which is linked to the SWIFT attack in October 2017. It is believed that the attackers who have been using Ryuk since August have pulled in over 700 Bitcoin across 52 transactions.
Revil
As the ransomware landscape continues to be overcrowded by novel malicious solutions, cybercriminal groups such as the REvil (Sodinokibi) ransomware gang have seemingly evolved with the times with increased sophistication of their operation. The REvil gang operates as a RaaS (Ransomware-as-a-Service) and creates malware strains that it sells to other criminal groups.
A report by security team KPN reveals that the REvil malware has infected more than 150,000 unique computers across the globe. Yet these infections only emerged from a sample of 148 strains of the REvil ransomware. Each strain of the REvil ransomware is deployed according to the infrastructure of the company’s network to increase chances of infection.
Recently, the notorious REvil ransomware gang launched an auction to sell off stolen data from companies unable to pay the ransom with prices starting at $50,000 payable in Monero (XMR). Out of privacy concerns, the REvil gang switched from demanding payment in Bitcoin to Monero, a privacy-centric cryptocurrency.
As one of the most active and aggressive ransomware operators, the REvil gang is primarily targeting corporations, encrypting their files and asking for astronomical fees averaging about $260,000.
PonyFinal
On May 27, Microsoft’s security team revealed in a series of tweets information regarding a new ransomware called “Pony Final,” which uses brute force to get access to its target network infrastructure to deploy ransomware.
Unlike most malware that use phishing links and emails to trick the user into launching the payload, PonyFinal is distributed using a combination of a Java Runtime Environment and MSI files that deliver malware with a payloader that is activated manually by the attacker. Like Ryuk, PonyFinal is mainly being used to attack healthcare institutions amid the COVID-19 crisis.
Declining Payouts
Despite the overall increase in the number of cyberattacks, experts believe there is a decrease in the number of successful attacks, since for most corporations, ransomware attacks amid a global pandemic are proving to be a final stroke, leaving them unable to pay the ransom.
This is evident in a report published by malware lab Emsisoft on April 21, revealing a significant drop in the number of successful ransomware attacks in the U.S. Likewise, a Chainalysis report published in April found a significant decrease in ransomware payments since the coronavirus pandemic intensified in the U.S. and Europe.
So it seems that despite the growing number of attacks, victims are not paying the ransoms, leaving criminal groups like REvil with no other option but to auction out the stolen data. It is also likely that a call for employees to work from home has paradoxically posed a new challenge for hackers. While speaking to Cointelegraph, Emsisoft’s threat analyst Brett Callow stated:
“It’s very obvious to ransomware attackers that they’ve got a potentially valuable target when they hit a corporate endpoint. It may however be less obvious when they hit a personal device that an employee is using while working remotely, and which is only connected to corporate resources on an intermittent basis.”
Updated: 7-9-2020
MIT Crypto Group Researcher Says PoW Attacks Not Always Obvious
James Lovejoy, a research assistant for Massachusetts Institute of Technology, or MIT, crypto and blockchain group the Digital Currency Initiative, explained blockchain attacks might not always be obvious.
Speaking on a Unitize digital conference panel about proof-of-work, or PoW, attacks, James Lovejoy of MIT’s Digital Currency Initiative, or DCI, said 51% attacks might not be evident, despite blockchain’s public nature.
Blockchains do not always show 51% attacks at first glance, Lovejoy explained on the July 9 panel. “You need an active observer to be monitoring the network to check whether or not an attack occurs,” he said.
Lovejoy Has A Blockchain Reorganization Tracker
For his DCI master’s thesis, Lovejoy spun up a blockchain reorganization tracker, or reorg tracker, that examines 51% attacks, he detailed on the panel.
The expert explained recent research shows 51% attacks as more plausible than once thought. He described the viability of such reorganizations across assets in the crypto space, given those assets’ various hash rates, the costs associated with attacks, and other factors.
Victims Take The First Hit Of An Attack
By the time the market discovers foul play on a blockchain without a tracker, people may already have suffered effects. “Up until now we’ve been reliant on victims to tell us about whether they’ve been attacked,” Lovejoy said.
“As you can imagine, if this results in insolvency or a loss of user funds, victims are often not super interested in revealing when an attack has taken place,” he added. Lovejoy also detailed a plethora of other pertinent information and findings during the panel.
Multiple 51% attacks have surfaced in recent years, plaguing projects such as Ethereum ClassicandBitcoin Gold, showing such nefarious behavior as far from impossible.
Updated: 7-16-2020
New Trojan Attack Targets Mac Users To Steal Cryptocurrency
Researchers discovered a new trojan targeted at crypto traders using trading applications on macOS.
A new trojan attack using malware called GMERA is targeting cryptocurrency traders who use trading applications on Apple’s macOS.
The internet security company ESET found that the malware comes integrated into legitimate-looking cryptocurrency trading applications and tries to steal users’ crypto funds from their wallets.
Researchers at another cybersecurity firm Trend Micro first discovered GMERA malware in September 2019, when it was posing as the Mac-specific stock investment application Stockfolio.
Copying The Actual Applications
ESET found the malware operators have integrated GMERA to the original macOS cryptocurrency trading application Kattana. They have also copied the website of the company and are promoting four new copycat applications — Cointrazer, Cupatrade, Licatrade and Trezarus — that come packed with the malware.
The fake websites have a download button which is linked to a ZIP archive containing the trojanized version of the app. According to ESET, these applications have full support for trading functionalities.
“For a person who doesn’t know Kattana, the websites do look legitimate,” wrote the researchers.
The researchers also said that the perpetrators have been directly contacting their targets and “socially engineering them” to download the infected application.
The Malware In A Nutshell
To analyze the malware, ESET researchers tested samples from Licatrade, which they said has minor differences compared to the malware on other applications but still functions the same way.
The trojan installs a shell script on the victim’s computer that gives the operators access to the users’ system through the application. The shell script then allows the attackers to create command-and-control servers, also called C&C or C2, over HTTP between theirs and the victim’s system. These C2 servers help them consistently communicate with the compromised machine.
According to the findings, the GMERA malware steals information such as user names, cryptocurrency wallets, location and screen captures from the users’ system.
ESET, however, said they had reported the issue to Apple and the certificate issued by the company to Licatrade was revoked the same day. They further added the other two certificates used for different applications were already revoked by the time they initiated their analyses.
Updated: 7-23-2020
English Football Club Hit With Multi-Million Dollar Ransomware Attack
Cybersecurity authorities in the UK warned that ransomware could threaten the sports sector.
The UK National Cyber Security Centre released a report on July 23 that discloses a growing trend in ransomware attacks against the sports sector. They noted a recent example in which attackers demanded that an English Football League club, or EFL, pay a multi-million dollar ransom in Bitcoin (BTC).
According to the Cyber Threat to Sports Organizations paper, the unnamed club was targeted by ransomware that crippled their corporate security systems.
The ransom amount requested was 400 BTC ($3.66 million). The club declined to pay, resulting in a loss of their stored data.
The Attack Could Have Had A Great Impact
The study reveals that the attack may have led to significant damages. It notes that the club was unable to use their corporate emails, and the stadium’s CCTV system and turnstiles were non-operational due to the attack.
There is no public information on the attack vector that allowed the criminals to infiltrate their system. One hypothesis is that a phishing email was used to deploy the attack. The systems may also have been accessed through the CCTV system.
The UK cybersecurity authorities disclosed that the attack cost the club “several hundred thousand pounds.”
Ransomware Attacks In The Sports Sector
According to the study, approximately 40% of the attacks on British sports organizations involved malware and a quarter of this involved ransomware.
These attacks have been growing in terms of impact since 2018, with cybercriminals mostly targeting high-value sports entities.
Ransomware attacks worldwide increased by 200% in the same period of time. The software required to carry out such an attack is widely available on the darknet.
Instances of so-called “crypto-jacking” — a ransomware method in which criminals commandeer devices to mine cryptocurrency — spiked in Singapore 300% year-on-year Q1 2020.
Updated: 7-27-2020
Ransomware Victims Are Fighting Back Against Their Attackers And Winning
The initiative launched by Europol has stopped $630M+ in ransomware demands since 2016.
The No More Ransom decryption tool repository, an initiative launched by Europol to combat ransomware attacks, has saved individuals $632 million in ransom demands since 2016.
According to the announcement published by Europol, the repository is celebrating its fourth anniversary. Over the past four years, the repo has gathered over 4.2 million visitors from 188 countries thanks to a compilation of tools from 163 partners.
The initiative’s website lists 100 different tools covering 140 different families of ransomware.
Covering A Wide Range Of Ransomware Decryptors
The project’s largest contributor is the malware lab, Emsisoft, which has contributed 54 tools so far.
Speaking with Cointelegraph, Brett Callow, threat analyst at Emsisoft, said that the project has helped a huge number of people recover their data “without needing to pay the ransom, and that means less money in the pockets of cybercriminals”:
“The project also helps people recover data that would otherwise permanently be lost. The loss of things like wedding photos and videos of babies’ first steps is, obviously, heartbreaking for people, and being able to help them get those things back is an important part of what No More Ransom does.”
On May 12, International crime-fighting organization, Interpol, joined forces with cybersecurity firm, Kaspersky, to launch a campaign called “Anti-Ransomware Day”. The date is set on the third anniversary of the most significant ransomware attack on record, WannaCry.
Updated: 7-30-2020
Hackers Have Been Using Dogecoin To Deploy Malware For 6 Months & No One Noticed
Researchers at Intezer discovered a new malware that relies on the Dogecoin blockchain network to deploy the attack against cloud servers.
A new study indicates that hackers are actively relying on the Dogecoin (DOGE) blockchain to expand a malware payload named “Doki.”
According to cybersecurity researchers at Intezer, Doki is a fully undetected backdoor that abuses the Dogecoin blockchain “in a unique way” in order to generate its C2 domain address and breach cloud servers. It is deployed through a botnet called Ngrok.
These domain addresses are used by the malware to search for additional vulnerable cloud servers within the network of the victim.
Intezer’s Study Explains Further About The Deployment Of The Attack:
“The attacker controls which address the malware will contact by transferring a specific amount of Dogecoin from his or her wallet. Since only the attacker has control over the wallet, only he can control when and how much dogecoin to transfer, and thus switch the domain accordingly.”
Undetected For Over Six Months
Intezer says that using Dogecoin to deploy a crypto-unrelated malware may be “quite resilient” to both law enforcement and security products. That’s why Doki has managed to stay undetected for over six months, despite having been uploaded to the VirusTotal database in January.
The Study Highlights That Such An Attack “Is Very Dangerous”:
“Our evidence shows that it takes only a few hours from when a new misconfigured Docker server is up online to become infected by this campaign.”
Recently, the threat intelligence team at Cisco Systems discovered a new cryptojacking botnet named “Prometei.” This botnet both mines Monero (XMR) and steals data from the targeted system.
Updated: 8-3-2020
Garmin Coming Back Online After Hack — Was $10M Crypto Ransom Paid?
Cybergang Evil Corp hackers reportedly demanded $10M to restore full access to Garmin’s customer support services and navigation solutions.
Multinational tech company Garmin may have paid some or all of a $10 million crypto ransom to hackers who managed to encrypt the firm’s internal network and take down several of its services on July 23.
According to an August 1 report from Lawrence Abrams at Bleeping Computer, Garmin’s IT department used a decryptor to regain access to workstations affected by the initial WastedLocker ransomware attack. The malware took down the company’s customer support, navigation solutions, and other online services.
The news outlet reported that the existence of such a protocol means “Garmin must have paid the ransom to the attackers” as the malware used in the hack has “no known weaknesses in their encryption algorithm.”
“Garmin’s script contains a timestamp of ’07/25/2020′, which indicates that the ransom was paid either on July 24 or July 25,” stated the report.
Evil Corp Responsible
Cointelegraph reported on July 27 that Russian cybergang Evil Corp was responsible for extorting a $10 million crypto ransom from Garmin following the ransomware attack.
Maksim Yakubets, the leader of the cybercriminal group, had previously been indicted by the U.S. Department of Justice in 2019. He was also listed on the FBI’s Most Wanted list with a reward set at $5 million – the highest amount offered by authorities for the arrest of a cybercriminal.
Garmin ‘Returning To Operation’
The technology firm’s most recent tweet on July 27 stated that “many of the systems and services affected by the recent outage, including Garmin Connect, are returning to operation.” An update on the company’s website states Garmin was the “victim of a cyber attack,” but makes no references to any ransom.
Because Evil Corp was officially sanctioned by the U.S. government in 2019, Garmin could face sanctions for admitting it sent any funds to the group. Emisoft threat analyst Brett Callow previously told Cointelegraph that such a payment would “create a legal minefield.”
“Payment may be the only way for a company to avoid a catastrophic loss of data,” said Callow. “But it may be illegal for the company to make that payment.”
Pay Up, Or Else
Other companies targeted by ransomware groups have ended up paying millions in crypto ransom demands rather than risk losing business while computer access is restored or sensitive information is released.
U.S.-based travel firm CWT negotiated with ransomware hackers, haggling on the price of a ransom over a malware attack down from $10 million to $4.5 million in Bitcoin (BTC). The University of California at San Francisco School of Medicine also reportedly paid more than $1 million in crypto as part of a ransom for a June 1 hack.
Updated: 8-3-2020
Travel Management Company CWT Pays $4.5M Bitcoin To Hackers
Ransomware hackers initially demanded $10 million to restore access to travel firm CWT’s computers and delete any stolen data.
U.S.-based corporate travel firm CWT paid $4.5 million in a Bitcoin ransom to hackers who stole sensitive files from the company.
According to a July 31 report from Reuters, representatives from CWT (formerly Carlson Wagonlit Travel) paid ransomware hackers 414 Bitcoin (BTC) on July 27 — roughly $4.5 million at the time — over two transactions. Blockchain data shows the criminals transferred the funds to a different address within an hour.
The attackers said they used Ragnar Locker ransomware to disable access to files on 30,000 computers at the firm and steal sensitive data. They initially demanded $10 million, but accepted less than half after a CWT representative claimed the firm had suffered financial losses during the pandemic.
Ransom Negotiations Visible To All
In an unusual show of seemingly cordial negotiations considering the nature of the crime, a CWT representative and one for the hackers discussed the price of restoring computer access in a publicly accessible online chat group.
The group initially stated such a ransom would probably be “much cheaper” than a lawsuit. In the chat, they even offered a “bonus” of recommendations as to how CWT could improve its security measures if they decided to pay.
According to chat records, some of the ransomware group’s advice included updating passwords every month, having at least three system administrators working at all times, and checking user privileges.
After CWT made the payment, the hackers ended the chat with “it’s a pleasure to work with professionals.”
Easier Just To Pay?
Many businesses and organizations targeted by ransomware groups have ended up paying millions of dollars rather than risk sensitive information being released or face the prospect of not having computer access for an extended period.
The University of California at San Francisco School of Medicine reportedly paid a $1.14 million ransom in crypto to the hackers behind a ransomware attack on June 1. Multinational tech company Garmin also recently received the decryptor to access their files following a massive hack, suggesting the company may have paid all or part of the $10 million initially requested by hackers.
However, not everyone is inclined to give in to the demands of criminals. An unnamed English Football League club refused to pay a $3.6 million ransom requested by hackers who targeted their corporate security systems in July. The club declined to pay, resulting in a huge loss of data.
Updated: 8-4-2020
McAfee Says NetWalker Ransomware Generated $25M Over 4 Months
The millionaire profits put NetWalker as one of the most profitable pieces of ransomware during 2020.
Cybersecurity firm McAfee released a study showing the activities of NetWalker, a ransomware first known as Mailto that was initially discovered in August 2019.
According to the report, the operators of NetWalker have collected over $25 million from ransom payments since March 2020.
From March 1 to July 27, the group collected around 2,795 Bitcoin (BTC), purportedly making it one of the most profitable types of ransomware for cybercriminals.
According to the report, the Bitcoin transactions received by the gang — where the amount is split among several different addresses — reflects that NetWalker is a “ransomware-as-a-service” malware.
Such a maneuver implies that it has generated such a huge amount of money thanks to the affiliate revenue sharing it offers to other operators, McAfee states.
Strengthening Its Capabilities
McAfee notes that NetWalker operators have moved away from using legacy Bitcoin addresses to SegWit addresses, due to its faster transaction times and lower costs, suggesting a sophistication in their modus operandi after becoming a ransomware-as-a-service model.
On March 20, at least two darknet forums saw posts related to the NetWalker actors offering the ransomware with a revenue-sharing scheme to help spread the malware and make it much as profitable as possible.
Speaking To Cointelegraph, Brett Callow, Threat Analyst At Malware Lab Emsisoft, Said:
“NetWalker is a big game hunter and responsible for numerous attacks on larger public sector organizations as well as private sector companies. Working out the amount ransomware groups make is exceptionally difficult and, as McAfee states, the figure of $25 million is almost certainly an underestimate. Globally, companies paid more than $25 billion in ransom demands in 2019.”
The study adds that most of the NetWalker’s targets were based in western European countries and in the United States. The group had previously announced that they won’t target hospitals due to the COVID-19 pandemic, although there have been reports to the contrary.
Crozer-Keystone Health System suffered a ransomware attack by the NetWalker ransomware on June 19. The attackers started to auction the system’s stolen data through its darknet website.
Updated: 8-13-2020
This Ransomware Comes With Its Own Affiliate Program
Crypto crime joins the gig economy.
Avaddon, a new ransomware-as-a-service, or RaaS, protocol, is the latest to jump on the crypto extortion bandwagon. Similar to ransomware from groups like Maze and REvil, the Avaddon project offers revenue-sharing for users who successfully deploy the software on unsuspecting victims.
According to research by the cyber intelligence firm, DomainTools, RaaS development allows hackers to focus their efforts on malware development, rather than finding new places to deploy their attacks. Developers instead rely on third-party individuals who are looking to generate income by launching their own ransomware campaigns.
Speaking with Cointelegraph, Tarik Saleh, senior security engineer and malware researcher at DomainTools, commented on the affiliate scheme used within the ransomware:
“Malware authors are looking to make profits with as low of a risk as possible and the RaaS / affiliate model does just that. Cybercriminals follow tactics and techniques of other successful threat actors, so we can expect the rise of RaaS and affiliate model programs to continue.”
Saleh explains that as of today, there are no publicly available decryptors for Avaddon, aside from the ones provided to victims once the malware’s ransom is paid.
While Bitcoin is the preferred method of payment for this particular ransomware, Saleh has witnessed a change in that trend in recent months.
Citing the recent Twitter hack, he noted that, “We are seeing a shift towards Monero, however, as Bitcoin doesn’t offer the [same] privacy protections and anonymity.”
Saleh believes that the ransomware’s developers are Russian due to the fact that they only sell to Russian language speaking customers on Russian marketplaces.
Russia’s government has “largely turned a blind eye towards taking down cybercriminals that don’t involve Russian assets.” This unspoken arrangement seemingly allows Russian ransomware authors to operate with a very low risk of punishment, Saleh added.
Updated: 8-20-2020
Ransomware Negotiations Revealed: Flattery And Empathy Works
New details reveal the unusual strategies employed by ransomware negotiators in a recent attack on the University of California.
Details of a week-long negotiation between the University of California and a NetWalker ransomware gang have been revealed by Bloomberg.
The University’s School of Medicine was working on a vaccine for Covid-19 in June this year when seven of its servers were locked down by the hackers. Against the advice from FBI, the university took matters into its own hands and conducted private negotiations.
The university negotiator used flattery, appealed to the hackers sense of sympathy and ethics, and managed to reduce the ransom amount from as much as $6M, down to just over $1 million in Bitcoin (BTC) and successfully restored the systems.
Right off the bat, the negotiator ensured they had the hacker’s ‘operator’ on their side, calling for respect from both sides, “I’m willing to work this out with you, but there has to be mutual respect. Don’t you agree?”. Before waiting for a response, they also appealed to the attacker’s pride:
“I have read about you on the internet and know that you are a famous ransomware hacker group and very professional. I know you will honor your word when we agree on a price, right?”
This appeared to work with the operator responding: “We are 100% about respect, and never will we disrespect a client who talk to us with respect.”
Negotiations shifted to feeling out how dedicated each side was, with the negotiator crying poor and stating that all funds had gone into the research with none left to spare.
Calling the apparent bluff, the operator replied that a school who collects over $7 billion in annual revenue should have no trouble paying a few million:
“You need to understand, for you as a big university […] you can collect that money in a couple of hours. You need to take us seriously.”
The first offer by the university was $780,000 and was also scoffed at by the operator. “Keep that $780k to buy McDonalds for all employees. Is very small amount for us,” adding, “I am sorry.”
More Time — For Both Sides
As is typical in ransom situations, the negotiator then asked for two more days in order to allow “the university committee that makes all the decisions” to meet again. The operator agreed on the condition that the $3 million ransom be doubled to $6 million.
A ransomware negotiator from Tel Aviv, Moty Cristal, told Bloomberg the extension might have proved useful for the attackers too, giving them time to identify the value of their stolen data.
The Netwalker Group is a large-scale criminal enterprise and leases its software in a franchise style program. The group posted a recruitment ad in March this year, adding new affiliates to their network.
Getting Personal
At this point, either out of desperation or as a psychological strategy, the negotiator started appealing to the operator’s sympathies. “I haven’t slept in a couple of days because I’m trying to figure this out for you,” they said, “I am being viewed as a failure by everyone here and this is all my fault this is happening.”
“The longer this goes on, the more I hate myself […] All I ask is that you be the only one in my life right now to treat me nice. You’re the only one in the world right now who knows exactly what I’m going through.”
The operator seemed responded: “My friend, your team needs to understand this is not your failure. Every device on the internet is vulnerable.”
Four days into the attack, the negotiator eventually came back with an offer over $1 million, saying they were bending their internal rules to accept an additional $120K donation on the grounds that the negotiations come to a close. They even added a time pressure:
“We normally can’t accept these donations, but we’re willing to make it work only if you agree to end this quickly.”
The university spent 36 hours organising the purchase of 116 Bitcoin ($1.14 million) and sending the funds to the attackers. Two more days were required for the hackers to confirm the deletion of all sensitive data and give access back to the university.
After more than eight days without access, the university successfully gained complete access back to all their servers. However the servers remained offline while they investigated the incident with the FBI and other cybersecurity consultants. In the most recent update on June 26, the university stated that the investigation was still ongoing.
Monero Cryptojacking Malware Targets Higher Education
Guardicore Labs explains that FritzFrog uses a brute-force attack on millions of addresses to gain access to servers.
According to a study published by Guardicore Labs, a malware botnet known as FritzFrog has been deployed to ten millions of IP addresses. The malware has largely targeted governmental offices, educational institutions, medical centers, banks, and telecommunication companies, installing a Monero (XMR) mining app known as XMRig.
Guardicore Labs explains that FritzFrog uses a brute-force attack on millions of addresses to gain access to servers.
That’s where an attacker submitting many passwords or passphrases with the hope of eventually guessing correctly.
After it gets in it proceeds to run a separate process named “libexec” to execute XMRig.
“It has successfully breached over 500 SSH servers, including those of known high-education institutions in the U.S. and Europe, and a railway company.”
The cybersecurity firm said that FritzFrog appears to be a one-of-its-kind malware, and that it was a “complicated task” to track it as the connections were hidden within a peer-to-peer (P2P) network.
Ophir Harpaz, A Researcher At Guardicore Labs, Commented:
“Unlike other P2P botnets, FritzFrog combines a set of properties that makes it unique: it is fileless, as it assembles and executes payloads in-memory. It is more aggressive in its brute-force attempts, yet stays efficient by distributing targets evenly within the network.”
Harpaz recommends choosing strong passwords and using public-key authentication, “which is much safer,” to avoid being attacked successfully by a cryptojacking malware like FritzFrog.
Recently, cybersecurity researchers at Cado Security detected what they believe to be the first-ever stealth crypto mining campaign to steal Amazon Web Services (AWS) credentials, named TeamTNT, which also deploys the XMR mining app.
Updated: 4-18-2021
The Perils Of Suing Crypto Exchanges After Ransomware Attacks Makes Good Case For Hardware Wallets
As seen in the case of AA v. Bitfinex, targeting a crypto exchange over stolen funds is a high-risk, low-reward proposition.
In October 2019, unknown hackers infiltrated a Canadian insurance company by installing the malware BitPaymer, which encrypted the firm’s data and IT systems. The hackers demanded a ransom of $1.2 million be paid in Bitcoin (BTC) in return for the decryption software needed for the firm to regain access to its systems.
The firm’s United Kingdom-based insurer — known only as AA — arranged to pay the BTC ransom, and the firm’s systems were back up and running within a few days. Meanwhile, AA started the process of seeking legal avenues to recover the BTC obtained by the hackers.
It engaged the blockchain investigations firm Chainalysis, whose investigations revealed that 96 of the 109.25 BTC paid had been transferred to a wallet linked to the Bitfinex exchange.
So far, this story is (unfortunately) far from unusual. Bitcoin accounts for the vast majority of ransomware payments due to its anonymity, accessibility (making it easier for victims to pay the ransom) and verifiability of transactions (allowing criminals to confirm once payment has been made).
What is unusual about this story, however, is that it sparked a 14-month-long legal battle between AA and Bitfinex, one that only recently concluded after AA discontinued its claim against Bitfinex in the U.K. High Court.
Having traced the stolen BTC to Bitfinex’s platform — and with the identity of the hackers still unknown — AA started its litigation against Bitfinex in December 2019. Again, this is not unusual: U.K. courts have a wide range of remedies at their disposal to assist victims of fraud in trying to recover their assets.
In instances where banks, exchanges or other intermediaries may find themselves unknowingly receiving or holding misappropriated or stolen assets, victims of fraud have been able to rely on:
Norwich Pharmacal orders, which require a third party to disclose certain information to the applicant that will assist in recovery efforts. In this context, the information would be the identity of the wallet holder to which the BTC was traced, and/or details of any other transactions involving the BTC since receipt by the wallet linked with the exchange.
Freezing orders that prevent defendant fraudsters from dealing with any of their assets until further notice. An exchange notified of a freezing order relating to a client must take steps to freeze the account to prevent the client from withdrawing and dissipating assets.
Where it can be established that the third party holds property that belongs to the fraud claimant, proprietary injunctions can be obtained to prevent the third party from dealing with that particular property. Linked orders are often made to require the subject of a proprietary injunction to disclose information of the Norwich Pharmacal-kind explained above.
Cryptocurrency As Property In The U.K.
The U.K. courts are very familiar with the preceding remedies when involving bank accounts and fiat currency. More recently, the courts have been grappling with how these principles apply to cryptocurrency. However, it is clear that the courts are willing to flexibly apply legal principles, to ensure that these remedies are available to victims trying to recover stolen crypto assets.
In the AA case, Justice Simon Bryan determined — for the first time — that Bitcoin could be classified as property under British law, meaning that he could grant a proprietary injunction in relation to that property.
This seems obvious, but traditionally the law has seen property as something that could either be possessed in a tangible sense or be enforced by a right to sue. Cryptocurrency obviously does not meet either requirement, but the courts have taken a pragmatic approach to ensure that novel intangible assets, like cryptocurrency, are considered property.
This flexible approach meant that AA was able to obtain injunctive relief. Bitfinex duly froze the account and provided AA with information about the identity of the customer who owned the wallet with the stolen BTC.
As it turned out though, the BTC had been transferred again before Bitfinex was contacted by AA’s lawyers, and could not be returned. AA reached a confidential settlement with Bitfinex’s customer (also a defendant to AA’s claim) and then turned its sights on Bitfinex, in an attempt to receive additional compensation.
The insurer raised a number of legal claims against Bitfinex, including the assertion that the exchange received the BTC (or its traceable proceeds) when it was property belonging to AA. As such, AA declared that a legal trust should be imposed, holding Bitfinex accountable to AA for the BTC. It was also argued that Bitfinex was reckless with regards to whether the BTC was lawfully transferred into the relevant wallet.
These are difficult arguments to prove, and after Bitfinex sent out its detailed legal defense and response to AA’s claims, AA ultimately decided to abandon its claims against Bitfinex. But this was not quite the end of the story. Usually, when a claimant abandons its case, the default position is that it must pay all of the defendant’s costs.
However, AA argued that its cost liability should be reduced by 50%, based upon Bitfinex’s supposedly “unreasonable” conduct. The parties fought this out at a High Court hearing in January, culminating in the court deciding there was no unreasonable conduct that would justify any reduction. AA was therefore ordered to pay 100% of Bitfinex’s legal costs, including the costs of its own unsuccessful application to have those costs reduced.
Conclusion
It is understandable that victims of fraud — who may not be able to successfully pursue the actual fraudster — might be tempted to take on a cryptocurrency exchange with deep pockets, perhaps in the simple hope that they can engineer a modest settlement, and avoid the time and cost of complex legal proceedings.
Cyber insurers like AA might calculate that the cost-benefit associated with those steps would be justified. However, exchanges like Bitfinex will continue to defend themselves robustly, particularly when the legal merits of claims are extremely challenging, and ultimately represent an attempt to drag an innocent exchange into the fallout of a cybercrime it had neither knowledge of nor involvement in.
Updated: 6-7-2021
Crypto’s Dark Underbelly Exposed In Ransomware Attack, U.S. Senator Says
U.S senators voiced their opinions on the matter of cryptocurrency’s use in ransomware attacks.
United States lawmakers have deliberated on the prospect of banning cryptocurrencies as a solution to the ransomware attacks that have befallen U.S. institutions in the past month, and opinions appear to be mixed.
The largest fuel pipeline in America was brought to a halt in early May when hackers infected the computer networks of Colonial Pipeline. Food packing company JBS was hit with a similar attack. Colonial Pipeline has since paid a reported $4.4 million in ransom.
Senator Mark Warner addressed the matter during NBC News’ Meet the Press on Sunday, where it was put to him by reporter Chuck Todd that banning cryptocurrencies entirely could curb the growing trend where cyberattackers demand ransom in Bitcoin (BTC) and other cryptocurrencies.
Warner disagreed that crypto should be banned entirely, adding that good things had come out of distributed ledger technology but that its dark underbelly was now being exposed.
“I’ve got a lot of questions about crypto. There were some good things coming out of distributed ledger technology, but we are now seeing some of the dark underbelly […] and that’s why I’m focusing more on transparency,” he said.
Warner claimed certain cryptocurrency “systems” could already be breached by authorities if they so desired. However, he said stopping the technology would simply redirect criminals toward different technologies.
“The truth is there are ways that we can break through some of these systems, but […] if there’s not some transparency of that payment, the bad guys will simply find another way to hide it,” said Warner.
Senator Roy Blunt suggested cryptocurrency shouldn’t be left to run behind the scenes of criminal activities, arguing that cryptocurrency had become the main tool of ransomware attackers, owing to its untraceable nature and ease of use.
“We have a lot of cash requirements in our country, but we haven’t figured out in the country or in the world how to trace cryptocurrency. So, one, fairly easy to do. People almost always pay the ransom. There are very few consequences. And you can’t trace the ransomware — the ransom payment of choice now. And we’ve got to do a better job here,” said Blunt.
Updated: 9-9-2021
South African Justice Department Is Hit by Ransomware Attack
South Africa’s Justice Department said it’s systems have been interrupted by a ransomware attack, the second such assault on a state institution in the past two months.
A breach occurred on Sept. 6 and left all of the department’s information systems encrypted and unavailable, according to a statement sent by WhatsApp on Thursday.
“All electronic services provided by the department are affected,” it said. These include the issuing of letters of authority, bail services, email and the departmental website.
In July, state-owned port and rail company Transnet SOC Ltd.’s systems were taken down by a similar attack.
Updated: 9-17-2021
Senator Lobbies Agencies Over The Use Of Crypto In Ransomware
Senator Hassan wants federal agencies to take more action, while Senator Lummis is more concerned about innovation being stifled.
Some United States senators are ramping up the anti-crypto rhetoric again, urging federal agencies to take action against the illicit use of digital assets.
Senator Maggie Hassan is the latest to raise concerns about the use of cryptocurrency as a means of payment for ransomware attacks.
The Senate Homeland Security and Governmental Affairs Committee member sent a letter on Thursday to several agencies, including the Justice Department, the Department of Homeland Security, the Internal Revenue Service, the Securities and Exchange Commission, and the Treasury Department’s Financial Crimes Enforcement Network.
In it, she aired her concerns, citing a recent case in her home state of New Hampshire where $2.3 million was stolen in a cyberattack in the town of Peterborough before being converted into cryptocurrency.
“The anonymity provided by cryptocurrency has helped facilitate its use by criminals in a myriad of ways. These uses include drug sales over the dark web, payments for ransomware attacks, tax evasion, financing for terrorism and organized crime, money laundering, and more.”
She outlined the difference between centralized exchanges with Know Your Customer requirements and decentralized exchanges and over-the-counter desks without such requirements, adding that more KYC enforcement was needed.
Hassan asked a number of questions about what action agencies were taking to curb the illicit use of cryptocurrencies for ransomware.
Hassan is a member of the Senate Finance Committee alongside Senator Elizabeth Warren, who labeled crypto the “new shadow bank” earlier this month. The committee has jurisdiction over matters relating to taxation and revenues, trade agreements, and tariffs.
Lawmakers on both sides of the aisle have been presenting their arguments for and against cryptocurrencies as regulatory pressure mounts in the United States.
In an interview with Reason Magazine earlier this month, Senator Cynthia Lummis said that her vision was to create a regulatory and statutory framework, adding:
“We want to make sure that Bitcoin, stablecoins, tokens can innovate and that the U.S. dollar can innovate as well and become a digital currency. So there’s going to be formats that people can use that are much more user-friendly than our more old-fashioned forms of currency.”
In early August, senators Ron Wyden, Lummis and Pat Toomey proposed an amendment to the controversial infrastructure bill seeking clearer terminology around the crypto tax provisions to ensure it would not stifle innovation.
However, the bill passed the Senate on Aug. 10, with the language broadly classifying most actors as crypto brokers remaining unchanged. This means that software firms, network validators, stakers and miners may be subject to third-party tax reporting requirements if the bipartisan infrastructure bill passes a final vote on Sept. 27 as scheduled by House Speaker Nancy Pelosi.
Updated: 9-14-2021
Crypto Isn’t The Cause Of Ransomware. It Might Be The Cure
Stamping out cryptocurrency to stall ransomware attacks doesn’t make any sense, says a former U.S. Treasury official.
In the wake of the ransomware attack on Colonial Pipeline, we have witnessed an assault on the payment mechanism, cryptocurrency. A recent New York Times op-ed even went as far as to suggest the use of offensive cyber warfare to disrupt cryptocurrencies like bitcoin.
Earlier this summer, a Wall Street Journal opinion piece titled, “Ban Cryptocurrency to Fight Ransomware,” argued, “We can live in a world with cryptocurrency or a world without ransomware, but we can’t have both.”
At a recent Senate Judiciary Committee hearing, Dick Durbin (D-Ill.), the committee’s chairman, asked, “Cryptocurrency and bitcoin are the coin of the realm when it comes to ransomware. What can we do – what specific laws should we enact in the United States to be responsive to this and diminish the role of cryptocurrency?”
A Department of Justice official responded, “I agree that cryptocurrency has unfortunately fueled this rise of crime. It has two key aspects to it. It’s often anonymous and non-reversible. Once it passed to the criminals, it is very difficult to claw it back.”
Ari Redbord is head of legal and government affairs for TRM Labs, a blockchain intelligence company. Previously, he was an Assistant United States Attorney and senior adviser to the Undersecretary for Terrorism and Financial Intelligence at the United States Treasury Department.
However, the reality is quite the opposite. While cryptocurrency allows ransom payments at the speed of the internet, making it attractive to illicit actors, the blockchain – the open ledger on which crypto lives and moves – allows law enforcement to track and trace the flow of funds in real time, providing unprecedented visibility on financial flows.
For example, in the Colonial Pipeline attack, law enforcement was able to track and ultimately seize the ransom payment. That recovery was possible only because cryptocurrency was the medium of payment. In other words, cryptocurrencies, far from being anonymous, allow law enforcement and regulators visibility on financial transactions in real time. Rather than being the cause of ransomware, crypto could very well be the solution.
In the recent New York Times op-ed, Paul Rosenzweig, former deputy assistant secretary for policy at the Department of Homeland Security, opined that with “alarming regularity, cybercriminals disrupt computer systems controlling important pieces of infrastructure and refuse to restore access until they are paid.”
Rosenzweig is right; cybercriminals, terrorist financiers, weapons proliferators and rogue nation state actors have moved online, launching attacks at unprecedented speed and scale. In the wake of the Colonial Pipeline cyberattack, FBI Director Christopher Wray compared recent cyberattacks to 9/11. As we confront this post-9/11 world, one thing is certain, the battlefield has shifted to the digital space. But law enforcement also has the tools necessary to combat cybercriminals where they live.
The Biden administration has focused its efforts on the need for close interagency and public private coordination. The Department of Justice has ordered U.S. attorney’s offices across the country to coordinate cases involving ransomware and other cyberattacks with a newly created task force, raising these cases to the level of terrorism investigations.
The White House, in a letter to business leaders, provided a playbook of best practices to harden cyber defenses against attacks from malicious actors.
While law enforcement and policy makers are focused on upgrading cyber defense and responsiveness, the sea of critics, instead, focus on cryptocurrency. For example, Rosenzweig argues that cryptocurrency is the root cause of ransomware attacks, allowing cybercriminals to “‘kidnap’ a company from afar and receive payment anonymously and securely.”
How should we neutralize the ransomware threat? He suggests stricter regulation, or if that doesn’t work, the use of offensive cyber warfare to hack and disrupt cryptocurrencies and cryptocurrency exchanges. Not only would that be an attack on the tens of millions of law-abiding Americans who own and use bitcoin and the many legitimate businesses that make up the cryptocurrency industry, but it would be akin to having destroyed the early web in the 1990s because criminals also abused it.
Rosenzweig’s argument, and that of the “ban crypto” set, is predicated on the conclusion that the “[t]he United States does not have a ransomware problem so much as it has an anonymous ransom problem.”
However, that does not take into account the ability of law enforcement, through the use of sophisticated blockchain analytics tools, to trace transactions, and ultimately, through great police work, to identify and potentially seize stolen funds. This type of investigation would not be possible had an illicit actor used another form of payment.
Rosenzweig points to the use of on-chain obfuscation techniques, such as the use of mixers or tumblers – services that combine cryptocurrencies and redistribute them – as an example of the need for additional regulation and something that would “be illegal in the non-virtual world.”
While the use of mixers is, in and of itself, not a crime, the Department of Justice has recently prosecuted and convicted individuals who conspire to launder funds through the use of these mixers. Just like in the off-chain world, you must have the intent to commit a crime. That is also true on-chain.
To be convicted of money laundering, you have to possess the intent to launder the proceeds of illicit activity. In fact, because of the nature of the open ledger, and the use of blockchain analytics, it is far easier to track and trace the flow of funds across the blockchain than it is to track cash flowing through networks of shell companies and hawalas across the globe.
Without question, we need a clear legislative and regulatory framework for cryptocurrency that mitigates the risk from illicit actors, while, at the same time, encourages and promotes innovation. Anti-money laundering and cybersecurity are critical infrastructure for this new financial system – the internet of money.
However, crypto exchanges are already regulated under the same laws as other money service businesses by the Financial Crimes Enforcement Network (FinCEN) and are required to maintain robust risk-based compliance programs, which include transaction monitoring for exposure to terrorist financing, ransomware and other illicit activity.
Cryptocurrency is not the problem. In fact, it could very well be the solution. With the right tools, financial crime investigators are able to trace and track the flow of funds, build out ransomware networks and understand typologies of illicit activity on the blockchain in ways unimaginable in the fiat world.
We don’t talk about banning cash because of money laundering or bulk-cash smuggling. Instead, we focus on thwarting illicit actors behind that activity and hardening our defenses against them. There is one difference, however: In crypto we actually have the tools to follow the money.
Updated: 9-21-2021
Crypto Channels Targeted In Biden’s Fight Against Ransomware
The Biden administration plans a fresh campaign against ransomware attacks through sanctions to cut off criminals’ cryptocurrency pipelines, and it urged companies to report extortion attempts and better protect themselves from them.
Deputy Treasury Secretary Wally Adeyemo told reporters that the sanctions would be imposed on Suex, a cryptocurrency transferring service that’s registered in the Czech Republic. He said Suex had “facilitated transactions involving illicit proceeds for at least eight ransomware variants.”
He said “exchanges like Suex are critical to attackers’ ability to extract profits,” pointing out that this was the first such action by the Office of Foreign Assets Control against a virtual currency exchange.
Both Adeyemo and Deputy National Security Adviser Anne Neuberger, who also briefed reporters in a conference call on Monday evening, underscored the importance of ransomware victims coming forward and vulnerable businesses and organizations taking steps to bolster their security.
Adeyemo announced new Treasury Department guidance that makes “an express statement that the U.S. government strongly discourages the payment of cyber ransoms or extortion demands.”
Neuberger likened companies armoring themselves against cybercrime to motorists and homeowners buying insurance.
“It incentivizes us to drive more safely,” she said. “You get a number of moving violations, your insurance goes up. Get into accidents, it goes up. Similarly, when you look at our home insurance, in order to get home insurance you have to have a smoke detector or have an alarm system.”
“When we look at cybersecurity, what we’re grappling with is what seems to be the lack of incentives for companies to make the investment to modernize their defenses to meet this threat,” Neuberger said.
The actions amount to another foray by the administration after ransomware attacks earlier this year disabled the meat giant JBS SA, which eventually paid an $11 million ransom, paralyzed Colonial Pipeline Co.’s flow of gasoline on the U.S. East Coast and imperiled health care providers in the midst of the coronavirus pandemic.
Since its inception in 2018 as a venue for transferring digital currency and turning it into cash, Suex has moved hundreds of millions of dollars in illicit digital coins, including more than $160 million in Bitcoin alone, according to the cryptocurrency research firm, Chainalysis.
Suex’s addition to the Treasury Specially Designated Nationals and Blocked Persons List prohibits Americans from doing business with it.
Updated: 9-23-2021
Bitcoin.org Goes Offline After Suffering Scam Attack
Bitcoin.org previously fell victim to a DDoS attack in July, with hackers demanding a Bitcoin ransom.
Bitcoin.org, one of the first websites about Bitcoin (BTC), has been hacked by online scammers and down as of the time of writing.
Cobra, Bitcoin.org’s anonymous curator, announced on Sept. 23 that Bitcoin.org was compromised, with hackers managing to put up a scam notice on the site.
“Looks like Bitcoin.org got hacked and the entire site replaced with a scam asking for free Bitcoin. Do not send funds to that address,” Bitcoin developer Matt Corallo reported on Twitter.
Following a query from Corallo, Namecheap temporarily disabled the website. According to Cobra, the Bitcoin.org website “may be down for a few days.”
Prior to Bitcoin.org going offline, users reported that Bitcoin.org was showing a classic fake giveaway announcement, with scammers reportedly managing to collect about $17,000 to their addresses.
https://t.co/Tp6AcXavUW has been breached. Visiting the website displays the classic ‘double your money’ scam. The scammers have profited (as of this writing) roughly $17,000.#Bitcoin pic.twitter.com/BXFMqC61EW
— vx-underground (@vxunderground) September 23, 2021
After disabling the website, Cobra suggested that the hackers exploited a flaw in the DNS, stating that Bitcoin.org’s Cloudflare accounts and servers were not compromised.
https://t.co/OsFgRFRRZb hasn’t been hacked, ever. And then we move to Cloudflare, and two months later we get hacked.
Can you explain where you were routing my traffic too? Because my actual server didn’t get any traffic during hack. @Cloudflare @eastdakota.
— Cøbra (@CobraBitcoin) September 23, 2021
The latest attack comes after Bitcoin.org fell victim of a DDoS attack in early July, alongside a ransom demand for an undisclosed amount of Bitcoin.
The attack came just one week after a court in the United Kingdom ordered the website to stop hosting the Bitcoin white paper, ruling in favor of self-proclaimed Satoshi Nakamoto and Bitcoin SV (BSV) proponent Craig Wright.
Bitcoin.org has been subject to many controversies after Nakamoto left the Bitcoin community in late 2011, leaving the code to Bitcoin developers. The website has since changed hands many times, with Cobra being announced as a co-owner of Bitcoin.org in late 2013.
In May 2020, Bitcoin.com owner and Bitcoin Cash (BCH) advocate, Roger Ver, expressed interest in buying the Bitcoin.org website. Some crypto community members have accused Ver of creating uncertainty over promoting Bitcoin Cash as the “real” Bitcoin.
A month later, Will Binns, one of Bitcoin.org’s overseers, said that he had lost access to the site, pointing to a potential breach.
Bitcoin.org is a landmark crypto website, with its domain name registered back in August 2008, a few months before anonymous Bitcoin creator Satoshi Nakamoto mined the first Bitcoin block in January 2009.
Providing an educational resource about the seminal cryptocurrency, Bitcoin.org is known for hosting the Bitcoin Core, the software used to connect to the Bitcoin network and run a node.
Updated: 9-27-2021
Crypto Guru Pleads Guilty To Advising North Korea On Blockchain Technology
Virgil Griffith was charged with conspiring to violate a federal law prohibiting U.S. citizens from exporting technology to the communist country
As his criminal trial was set to start, a cryptocurrency expert pleaded guilty to conspiring to violating U.S. law by traveling to North Korea to give a presentation on how to use blockchain technology to launder money and evade sanctions.
Virgil Griffith entered the plea in federal court in Manhattan on Monday, before jury selection was to begin in his trial. The former senior researcher for the Ethereum Foundation was arrested in November 2019 after attending a conference in Pyongyang earlier in the year.
A federal grand jury convened by the U.S. attorney’s office for the Southern District of New York indicted Mr. Griffith on one count of allegedly conspiring to violate the International Emergency Economic Powers Act, which prohibits U.S. citizens from exporting goods, services or technology to North Korea.
U.S. District Judge P. Kevin Castel said Mr. Griffith’s sentencing will take place Jan. 18. Mr. Griffith faces up to 20 years in prison.
Brian Klein, a lawyer for Mr. Griffith, said Monday that his client “is sincerely remorseful.”
“Setting aside what happened, he has made important contributions to society that we will raise with the court,” Mr. Klein said. “He also has many wonderful qualities, and no one should define him by this mistake.”
Audrey Strauss, U.S. attorney for the Southern District of New York, said in a statement that Mr. Griffith jeopardized the national security of the U.S.
“As he admitted in court today, Virgil Griffith agreed to help one of our nation’s most dangerous foreign adversaries,” Ms. Strauss said.
The trial was expected to raise questions of free speech. It also was expected to delve into North Korea’s history, culture and relations with the U.S., as well as the prevalence of information about blockchain technology on the internet, according to filings from prosecutors and Mr. Griffith’s lawyers.
While prosecutors say Mr. Griffith provided valuable information at the conference, his lawyers previously said in filings that he didn’t violate the law because he didn’t provide any service to North Korea.
Mr. Griffith, who has a doctorate from the California Institute of Technology in computational and neural systems and has frequently spoken on panels about blockchain technology, gave a talk to about 100 people at the Pyongyang conference, providing basic information that could be found on the internet by anyone, his lawyers previously said.
As such, his talk was protected by the First Amendment, the lawyers said.
Prosecutors said Mr. Griffith conspired to violate the sanctions law by planning with others to give the presentation at the conference without receiving approval from the U.S.
The presentation amounted to services to North Korea, prosecutors said, because it provided valuable information tailored to a North Korean audience.
It emphasized that U.S. or U.N. sanctions couldn’t stop the use of blockchain technology, according to prosecutors.
A criminal complaint says Mr. Griffith, who resided in Singapore, secured from the country’s diplomatic mission in Manhattan a visa to travel to North Korea.
In April 2019, he entered North Korea through China, though he hadn’t obtained approval from the U.S., according to the complaint. Treasury Department and State Department officials had warned him about travel to the country, the complaint says.
Before his arrest, Mr. Griffith told a Federal Bureau of Investigation agent that the North Korean government approved his presentation’s topics in advance of the conference, according to the complaint. He also told the investigator that bitcoin could make North Korea virtually independent from the global banking system, prosecutors said.
The U.S. and the United Nations Security Council have tried to constrain North Korea’s efforts to build its nuclear weapons program by enacting tough sanctions, including bans on trade, finance and weapon sales.
A representative for Mr. Griffith’s employer, the Ethereum Foundation, didn’t respond to a request for comment. The foundation is a nonprofit organization set up to support Ethereum, a popular cryptocurrency platform. Vitalik Buterin, the co-creator of Ethereum, previously said on Twitter that Mr. Griffith went to North Korea without help from the foundation and many counseled against the trip.
Mr. Griffith’s lawyers previously filed a motion to dismiss the indictment based on a disclosure from prosecutors that FBI agents who weren’t part of the investigation accessed data seized from Mr. Griffith’s Twitter and Facebook accounts as part of a search warrant.
The data had been uploaded into an FBI document-review platform developed by Palantir Technologies Inc., prosecutors said, and was marked as either responsive or nonresponsive to the investigation.
Prosecutors said in filings that they believed only their investigative team had access to the material. However, in August, prosecutors said they learned that the documents were accessible by other FBI agents. Some of the data, including material marked as nonresponsive to Mr. Griffith’s case, was accessed by FBI agents in connection with separate investigations, according to prosecutors.
Judge Castel said he would decide on the motion to dismiss after the trial. However, Mr. Griffith’s plea on Monday voided the motion.
Palantir said in a statement that the document-review platform has robust access and security controls.
“The customer also has rigorous protocols established to protect search warrant returns, which, in this case, the end user did not follow,” the statement said.
Updated: 10-2-2021
Russian IT Leader’s Treason Case Shows Cyber Impasse With U.S.
A cybersecurity entrepreneur who pushed for tougher action against hackers is facing as much as 20 years in a Russian prison on treason charges, reflecting the challenges the U.S. faces in reaching a deal with Moscow on reining in online crime.
Ilya Sachkov, the 35-year-old founder of Group-IB who was arrested this week and ordered to be detained until Nov. 27, had spoken critically of the apparent immunity of Russian hackers inside their own country’s borders.
The cybersecurity firm said it’s certain of his innocence and pledged to keep operating as normal. The company moved its headquarters to Singapore in 2019.
President Joe Biden agreed at a June summit with Russian counterpart Vladimir Putin to hold a dialogue on cybersecurity in a bid to halt a spate of hacking linked to crime groups based in Russia. While talks have started, they’ve made little headway, and the malware attacks have continued.
Sachkov worked closely with Russian’s domestic intelligence agency, the Federal Security Service or FSB, as is mandatory for cybersecurity firms of any significant size in Russia, according to three people close to security circles in Moscow.
But his growing effort to commercialize his products abroad and move his business mostly outside of Russia aroused suspicions that he was too independent, two of the people said.
In April, the IT entrepreneur said Group-IB planned to list shares on a foreign exchange, Forbes reported. In 2020, Sachkov said his company was on track to earn half its revenue outside of the former Soviet Union for the first time.
Fluorescent Lamborghini
Sachkov also raised eyebrows in mid-2020 when at a meeting between Prime Minister Mikhail Mishustin and IT executives he said Russian authorities should arrest alleged hacking mastermind Maksim Yakubets if they wanted the sector to thrive.
The FBI has offered a reward of as much as $5 million for Yakubets, who’s accused of targeting Europe and North America with malware.
Even so, the alleged ringleader of the hacking group known as Evil Corp. lives openly in Moscow and has been photographed driving a fluorescent camouflage Lamborghini with a license plate that reads “Thief” in Russian.
Sachkov’s detention may be linked to accusations of providing information on Russian hackers to the U.S., the Kommersant newspaper reported.
While state treason charges mean any trial will be held behind closed doors, Boris Titov, the Kremlin’s business ombudsman, called for transparency in the Sachkov case.
“Otherwise, the sector and its investment attractiveness will be dealt a critical blow,” Titov warned on his Facebook account. “IT will flee the country.”
Dmitry Peskov, Putin’s spokesman, brushed aside such fears. “This has nothing to do with the business and investment climate in our country,” he told reporters on a conference call.
Sachkov’s fate is a reflection of Russia’s determination to tightly control all cybersecurity interaction with the U.S., said Andrei Soldatov, co-author of “The Red Web: The Kremlin’s Wars on the Internet” and co-founder of Agentura.ru, a site that tracks the security services.
“The FSB doesn’t want any even semi-independent players in this field,” he said.
Updated: 10-3-2021
Behind The Crypto Broker Accused of Enabling Ransomware Hackers
A cryptocurrency broker that the Biden administration considers a key cog in the recent ransomware epidemic is legally registered in the Czech Republic but doesn’t appear to have an office there.
It may be operating out of Moscow’s tallest skyscraper despite its not being listed at the address. It earned the distinction last month of being the first crypto exchange to be blacklisted by the U.S. as governments try to stem further attacks.
And while it denies any part in the recent spate of cyber crimes, experts say it’s a prime example of a shadowy corner of the industry that has allowed hackers to thrive by giving them the means to launder millions of dollars in illicit digital proceeds through “nested” middlemen that tap larger exchanges to process transactions.
Suex OTC, a virtual currency exchange, is a transactions platform that allows cryptocurrency traders to buy and sell digital coins.
It is accused by the U.S. of mixing legitimate digital currency trades with illegal transfers from ransomware gangs, allowing them to launder profits from the kind of attacks that have crippled hospitals, businesses, school districts and even a major U.S. fuel pipeline.
The U.S. Treasury Department alleges that Suex has played an integral role helping criminal hackers clean and cash out their loot, mostly Bitcoin paid by ransomware victims, before converting it to a traditional currency.
“There is an illicit underbelly that’s formed in this ecosystem,” said Todd Conklin, counselor to the deputy secretary of the Treasury. “We haven’t yet cleansed the entire ecosystem and we’re definitely continuing to investigate other nested exchanges and mixers, like Suex.”
Since at least 2018, Suex has converted cryptocurrency holdings into cash inside brick-and-mortar offices in Moscow, St. Petersburg and possibly in the Middle East, according to Chainalysis Inc., a blockchain forensics firm specializing in following the movement of digital currencies whose clients have included U.S. federal agencies.
Suex is legally registered in the Czech Republic but apparently doesn’t have an office there, according to Chainalysis. At the official address in a nondescript house in Prague’s old town, there’s a clothing store and antiques shops on the ground floor, and several residential units and a law firm.
The law firm at the address where Suex is registered specializes in incorporation and corporate governance services. A person at the firm who answered a call from Bloomberg denied having any knowledge of Suex and hung up the phone.
The company does appear to be operating from Moscow’s 97-story-high Federation Tower East building, according to Chainalysis. There’s no public directory of tenants at the entrance, and the receptionist bans entry to anyone who hasn’t been invited.
While, per the building’s management, Suex’s name isn’t listed at the address, a company called Art of Web –- which counts Egor Petukhovsky, Suex’s chief executive officer and largest shareholder — is.
Suex’s Petukhovsky didn’t respond to requests for comment. He denied in a recent Facebook post that he or his business helped launder money for hackers and vowed to “firmly defend my name in litigation” in the U.S.
“I believe in independent justice and hope to come back to normal life as soon as possible,” he said. Other Suex officials couldn’t be located for comment.
Permissive Environment
By adding Suex to the Treasury Department’s list of sanctioned entities, U.S. based companies and individuals are prohibited from conducting any transactions with them.
While these sanctions will likely do little to expose Suex to legal authorities half a world away, the Biden administration is hoping it may dissuade U.S.-based ransomware victims from quickly paying ransom to resolve their ordeal.
Brokers like Suex don’t typically build their own software systems to execute cryptocurrency trades. Instead, these operators trade on third-party crypto exchanges.
The Treasury Department declined to identify which exchanges it believes Suex had utilized except to say “several.” Regulators globally have called for tighter enforcement and regulations requiring exchanges to collect data identify their clients.
Suex has so far received at least $160 million in Bitcoin from illicit and high-risk sources since 2018, according to Chainalysis.
If this is correct, that’s about 40% of Suex’s known transaction history linked to the activity of hackers, including nearly $13 million from some of the more infamous ransomware groups: Ryuk and Conti, according to Chainalysis.
Many of the ransomware groups have been traced to Russia and other countries that the U.S. says has provided safe haven for them. At a June summit, President Joe Biden warned Russian President Vladimir Putin about continued attacks, particularly on critical infrastructure.
But the the cyber gangs are still “operating in the permissive environment that they’ve created there,” U.S. Federal Bureau of Investigation Deputy Director Paul Abbate said earlier this month.
High-Value Deals
What’s unclear is the extent to which Suex is aware that it is being used to launder money, if it is simply turning a blind eye to illegal behavior by failing to vet their customers carefully or if the U.S. made a mistake in branding Suex an illicit broker, as its CEO claims.
While the company’s leadership denies any ties to cyber gangs and their illegal activity, Maxim Kurbangaleev, who described himself as Suex’s co-founder on LinkedIn, described how quickly customers can start trading “without the long and tedious sending of documents and passing endless checks.”
The post, which was provided by TRM Labs, a blockchain intelligence firm, has since been removed. It wasn’t clear when Kurbangaleev posted the statement.
Many services that work with exchanges conduct “know-your-customer” checks to verify customer identities; Suex doesn’t, said Ari Redbord, head of legal and government affairs at TRM Labs and a former federal prosecutor and treasury official, who described Suex as a “parasitic exchange.”
“The difference between those and Suex is that Suex is part of a shadow crypto economy that thrives on skipping appropriate compliance controls,” he said, adding that the sanctions against Suex show that “the U.S. government is going to go after the unregulated exchanges.”
Suex largely communicated with its clients via the Telegram app and accepted new customers on a system of referrals from trusted sources, according to TRM.
Transactions were only completed at Suex’s offices, where, one ad bragged, customers would be treated to cookies and tea. Suex “appeared to deal almost exclusively in high-value deals – its minimum acceptable transaction was $10,000,” says TRM.
Then Suex executed clients’ transactions on other exchanges, likely without their knowledge of where Suex was getting the funds.
Warning to Enablers
The U.S. actions against Suex follow other efforts to hold cryptocurrency brokerages accountable for illicit activity.
BTC-e was shuttered in 2017 after the U.S. accused Russian national Alexander Vinnik of supervising a platform that was being used by cyber criminals to move illicit digital proceeds anonymously and without vetting.
BTC-e allegedly handled some Bitcoin traced to the same Russian hacking group implicated in hacking Democratic Party emails ahead of the 2016 presidential election, according to blockchain forensics firm Elliptic.
Vinnik was extradited from Greece to France, where he was sentenced in December to five years in a French prison.
Chainalysis’s data indicates that Suex processed more than $50 million in illicit funds on behalf of BTC-e and its users following the BTC-e takedown, including some transfers as recently as this year.
Law enforcement agencies have long worried that cryptocurrency businesses could be used to launder money and for criminal purposes. But it turns out, most coins can be traced, as all transactions happening outside of centralized exchanges are recorded on digital ledgers, typically called blockchains.
Regulators and law enforcement has been actively using such services to catch bad actors across the globe. Suex was just the latest business to get caught.
Despite Suex’s denial, the Treasury Department’s crackdown should, at least temporarily, narrow the illicit pipeline of digital currency transfers, according to Tom Robinson, co-founder of Elliptic.
“It means one less place for ransomware gangs to cash out their earnings, although there are still plenty of other ways they can still do that,” he said.
“For crypto exchanges, it means that it’s even more critical to ensure that they are not laundering proceeds of crime. They now have the real prospect of being cut off from the mainstream financial system if they are enabling their actors.”
Updated: 10-4-2021
Compounding Problems: $65M More COMP At Risk As Devs Wait For Time-Locked Bug Fix
While Compound’s developers submitted a fix for the protocol’s bug on Thursday, the update won’t take effect until a seven-day time-lock on code updates has passed.
Major decentralized finance (DeFi) money market Compound’s woes are worsening, with nearly $150 million worth of COMP now at risk due to a buggy upgrade to the protocol that went live last week.
On Thursday, Cointelegraph reported that a bug had resulted in between $70 million and $85 million worth of COMP tokens being mistakenly offered to users as rewards after an update intended to fix bugs and “split COMP rewards distribution” went awry.
Despite the reward distribution error being identified quickly, Compound’s week-long delay in enacting new governance measures meant that the error will not be fixed until Thursda.
On Sunday, Compound founder Robert Leshner tweeted that 202,472.5 COMP (worth approximately $65 million) had been placed at risk after the protocol’s drip function was called for the first time in roughly two months.
The drip function makes tokens held in Compound’s Reservoir available to users, with 0.5 COMP being accumulated by the Reservoir per block. Leshner noted that “the majority of COMP reserved for users” is held in the Reservoir.
This brings the total COMP at risk to approximately 490k, of which 136k is still in the Comptroller, and 117k has been returned to the community so far (THANK YOU ).
— Robert Leshner (@rleshner) October 3, 2021
SushiSwap developer Mudit Gupta took to social media to criticize the use of time-locks on governance, asserting that roughly 100 people were aware of the threat posed by the drip function since the bug was discovered on Thursday, but they were unable to act due to the time-delay on updating the protocol.
Gupta also warned of the risks associated with upgradable smart contracts, asserting they are inappropriate for “large [DeFi] primitives.”
This is why timelocks on everything are not always the best option. About a hundred people knew about this possibility since day 1 but their hands were tied due to the timelock.
All of this 68.8m can be drained, not just a quarter if there are malicious actors involved. https://t.co/xB5T1sjUQ8
— Mudit Gupta (@Mudit__Gupta) October 3, 2021
“I’ve come to see upgradability as more of a bug than a feature,” he added.
While Leshner’s tweet revealed that roughly 117,000 COMP worth $37.6 million had been returned to the protocol following the initial incident, Yearn.finance developer Banteg estimated that one-third of the funds that were placed at risk by the drip function had already been claimed by users at roughly 3:30 pm UTC on Sunday.
Banteg tallied the total value of COMP tokens placed at risk by the protocol’s bug to now be $147 million.
Despite the bug’s initial identification causing the price of COMP to quickly crash 3% from $330 to $286 on Thursday, the token quickly recovered and traded above $340 on Saturday, according to CoinGecko.
COMP has shed 7% of its value since tagging a local high of $347.5 on Sunday, last changing hands for $322 at the time of writing.
Updated: 10-6-2021
‘Evolved Apes’ NFT Creator Allegedly Absconds With $2.7 Million
Some members of the NFT project are attempting to continue the development of the game, while efforts are underway to apprehend the alleged culprit.
Investors in Evolved Apes, a recently launched PFP — short for profile picture — nonfungible token (NFT) project, are grappling with the disappearance of the project’s anonymous developer.
Going by the moniker “Evil Ape,” the developer has allegedly lived up to the name by vanishing with 798 Ether (ETH) worth over $2.7 million from the project’s coffers.
The reportedly stolen funds covered both the money realized from the initial minting process and the ETH traded in the secondary sale of the NFTs on the OpenSea marketplace.
Indeed, “Evolved Apes” had been one of the hyped NFT mints recently, with the 10,000-strong collection reportedly selling out in 10 minutes and the floor price rising steadily following the swift sale.
However, the project’s storefront on OpenSea shows a tanked floor price of 0.005 ETH, significantly lower than the original minting cost. The decline in the floor price is no doubt linked to the current rug pull scandal rocking the project.
Apart from allegedly siphoning all the project’s money, Evil Ape also took down the “Evolved Apes’” Twitter account and website.
Before absconding with the $2.7 million, Evil Ape and the project’s creators had promised to ship a blockchain fighting game, a common promise among several avatar-style NFT developers.
Can the rugged apes of #Evolvedapes also get some love? Sure was a bad week for ape-kind #ballerapeclub! We have a new community of volunteers coming together to #fightbackapes and can use any support or expertise https://t.co/pHW23nlbbi
— Fight Back Apes (@FightbackApes) October 4, 2021
Some members of the community have come together to continue the development of the project under the umbrella of “Fight Back Apes.”
The entities behind the new faction say they wish to create a more community-centric operating model for the project, including a multisig wallet, to prevent the repeat of another Evil Ape debacle.
With Evil Ape still receiving the 4% royalties on secondary sales, the current plan is to create a new project that will airdrop new NFTs to current holders.
NFTs have arguably dominated discourse in the crypto space in 2021, with massive platforms such as OpenSea recording massive trading volumes.
Given the popularity of NFTs, it is perhaps unsurprising to see alleged rogue actors like Evil Ape attempting to con unsuspecting victims.
Updated: 10-14-2021
Crypto Adoption In Sights: Regulators And Industry Join To Fight Ransomware
As the crypto industry continues to develop at a rapid pace, so do the ransomware attacks, but regulators now seem ready to step in.
With an increasing number of people forced to work from their homes, data suggests that ransomware attacks are at their all-time highest with the frequency of these incidents increasing by 45% over the course of April 2021 alone. Not only that, some are adamant that the rise in ransomware attacks is closely connected to the meteoric growth of the crypto sector.
Also, in the midst of the recent positive crypto market activity, news of the United States regulators aggressively studying the link between crypto and ransomware seems to be dampening the mood somewhat, especially since various government agencies are seemingly seeing crypto ransomware as a big issue requiring stringent action.
As digital asset adoption continues to spread across the U.S., it appears as though lawmakers are looking to better understand how these offerings can be used for a slew of legal as well as illegal purposes.
For example, the Ransom Disclosure Act, which was introduced by Senator Elizabeth Warren and Representative Deborah Ross on Oct. 5, requires victims of ransomware attacks to disclose information about any ransom payments they may have faced to the Department of Homeland Security (DHS).
The goal here, as per Warren and Ross, is to amass critical data on fiat and cryptocurrency payments, which can eventually be used by relevant regulatory agencies to protect investors from cybercrimes as well as to curb any illicit financial activities taking place in the United States.
Furthermore, the bill also seeks to investigate the direct role of cryptocurrencies in ransomware attacks, an effort that will be helmed by the Department of Homeland Security.
Similarly and just recently, Deputy Attorney General Lisa Monaco revealed that the Justice Department has launched a new initiative dubbed the National Cryptocurrency Enforcement Team that looks to weed out any projects that can allow criminals to launder their crypto proceeds.
“We want to strengthen our capacity to dismantle the financial ecosystem that enables these criminal actors to flourish and to profit from what they’re doing,” Monaco was quoted as saying.
What’s Driving This Wave?
To gain a better understanding of why the U.S. regulators are making such a concerted effort to crack down upon any crypto-related ransomware, Cointelegraph reached out to Kadan Stadelmann, chief technological officer for open-source blockchain solutions provider Komodo.
In his view, one quick look at data available online shows that all kinds — not just crypto — of ransomware attacks are becoming more frequent, adding: “Just look at the statistics. Palo Alto Networks reported last month that the average ransom payment for 2021 is currently around $570,000 — 82% higher than the 2020 average of $312,000. 2020 was also much worse than 2019.” He added:
“To reverse this trend, a more mature regulatory landscape is necessary for the blockchain industry as well as improved cybersecurity as a whole in the next decade.”
When asked about whether major spending on such research activities is warranted, Stadlemann opined that not only should governments be putting more measures in place but they should also allocate additional funds and resources in regard to the same.
On the subject, he went on to state that governments can begin by adopting policies that ensure companies and anyone running critical infrastructure are better prepared for such events: “Together, having both proactive and reactive plans for cybersecurity would certainly reduce the fallout of ransomware attacks.”
Sharing a relatively similar sentiment, Du Jun, co-founder of cryptocurrency exchange Huobi, told Cointelegraph that it is the responsibility of every government to prevent Anti-Money Laundering (AML) as well as Combating the Financing of Terrorism (CFT) within their borders, adding that it is only natural for the U.S. government to have taken the regulatory actions it has to regulate its crypto market. He added:
“It is difficult to deal with cryptocurrencies as a payment method, given the lack of clarity regarding responsibility for AML/CFT compliance and the lack of a central oversight body.
These actions may introduce challenges to crypto businesses but will be good for the ecosystem in the long run, protecting investors from uncertainty and fostering a better business environment.”
Lastly, he opined that in addition to supervision alone, the American government ought to also allocate more resources to encourage the growth of new businesses within this space, making the country more competitive and appealing to crypto enthusiasts.
The Spending Is Justified
Taking a more numbers-oriented approach to the matter, Marie Tatibouet, chief marketing officer for cryptocurrency trading platform Gate.io, told Cointelegraph that in 2020, the total ransom paid by cyberattack victims reached nearly $350 million worth of crypto. With that figure in mind, she added:
“This number is inevitably going to keep increasing year on year. So Warren’s ‘Ransom Disclosure Act’ on paper makes sense. If you are a victim, you must disclose information about ransom payments no later than 48 hours after the payment date.”
That said, she did acknowledge that the primary issue that most people have with the U.S. government is that, of late, Biden and company have been cracking down very hard on the crypto industry via the introduction of the recent infrastructure bill, as well as other sanctions. “So, it is understandable why people have been a little cautious about anything that the government does,” Tatibouet added.
Sergey Zhdanov, chief operating officer for digital currency trading platform EXMO, told Cointelegraph that the measures taken by the U.S. confirm the fact that regulatory authorities are not looking to ban cryptocurrencies (the way China did) but rather want to carve out a way through which digital assets can be incorporated into the traditional financial system.
He Then Went On To State:
“Coming up with new effective methods to stop the illegal use of cryptocurrencies and money laundering is a crucial step that will take the crypto industry to its next level of development.”
Increased Regulations A Win-Win For Everyone?
Hunain Naseer, senior editor for OKEx Insights, told Cointelegraph that the regulatory efforts being initiated globally seek to usher in a level of clarity to this space that can help make it easier for investors to enter this fast-growing space with complete peace of mind. He further expounded on the subject by saying:
“It makes sense to focus on such initiatives that make online interactions and commerce, including cryptocurrency transactions, safer for all. These steps will also contribute toward regulators allowing a wider variety of crypto-based financial products for retail.”
Nischal Shetty, founder of cryptocurrency exchange WazirX, told Cointelegraph that any regulatory steps that seek to track and eliminate criminal activities should always be welcome, especially in an industry as fast-growing as this.
In his view, the rationale behind such movements seems to quite clearly be rooted in governments ultimately wishing to protect consumers without stifling innovation, adding: “For crypto, it’s an even more of a positive sign as this proves that digital asset innovation can thrive while ensuring criminal activities are identified and eliminated.”
Furthermore, On Oct 5. blockchain analytics firm Chainalysis announced that it had facilitated the purchase of cybercrime investigative company Excygent for an undisclosed amount, hinting that the buyout will enable the two firms to work together and “dismantle ransomware operations” that may be active globally.
In the past, Chainalysis has collaborated with Excygent on the seizure of cryptocurrency connected to the now-defunct darknet market Silk Road, as well as in the shutting down of various terrorism and child abuse portals operating online.
In general, crypto native blockchain analytics firms have grown to accrue support not only from the U.S. government but also a number of significant private players, with CipherTrace being bought out by a mainstream entity — in this case like MasterCard — earlier this year.
What Is The Future of Ransomware Crime?
As the crypto landscape continues to evolve and grow, Chainalysis CEO Michael Gronager believes that tracing the flow of ransomware payments on the blockchain will be instrumental for law enforcement agencies to deter, analyze and dismantle any ransomware operations in existence today, as he told Cointelegraph:
“As paradoxical as it seems, it can actually be beneficial to investigators when bad actors choose to use cryptocurrency when committing crimes.”
In this regard, it is pertinent to mention that hackers have become wise to the fact that, contrary to what people keep reiterating like crypto is totally anonymous, it is in fact actually extremely easy to trace individual transactions back to their owners, since all records and transitions are maintained on a blockchain.
Additionally, amid the slew of recent big hack stories such as the ones related to Poly Network and SushiSwap, the interesting thing is that the incidents did not result in the platform or its users losing any money, as companies and regulators stepped in to secure the movement of funds through the blockchains.
And while that may be bad for the notion of decentralization, the fact of the matter remains that the funds are safe.
Gronager further alluded to cases such as NetWalker, a ransomware operator who allegedly targeted hospitals during the pandemic and collected more than $25 million from ransom payments in 2020, as well as Suex OTC, a firm that allegedly allowed hackers to access crypto sent as payment for ransomware attacks, as prime examples of why increased defense against ransomware is needed in this day and age.
Thus, the fact that regulatory agencies are making decisive steps to focus on crypto ransomware-related initiatives, is not unilaterally welcomed by everyone in the crypto industry.
While some believe more can be done to make the digital asset ecosystem safer for newer entrants through the use of regulation, others say that the role of ransomware in crypto is overblown and that tight regulation will stifle freedoms and worsen the image of the industry.
However, most agree that ransomware has no place in the industry and that regulation, if done right, will go a long way toward securing the industry and ensuring long-term prosperity and adoption.
Updated: 10-15-2021
U.S. Treasury Offers Crypto Guidance Amid Ransomware Surge
There was $590 million in suspicious activity related to ransomware in the first six months of 2021, exceeding the entire amount in 2020, when $416 million was reported, according to a report released Friday by the U.S. Treasury Department’s Financial Crimes Enforcement Network.
The average amount of reported ransomware transactions per month in 2021 was $102.3 million, according to the report. If the current trend continues, suspicious activity reports filed in 2021 “are projected to have a higher ransomware-related transaction value than SARs filed in the previous 10 years combined,” according to the report. SARs is shorthand for suspicious activity reports.
U.S. based cybersecurity companies filed most of the SARs related to ransomware while banks and cryptocurrency exchanges filed more than a third of the reports. The reports reflect just how quickly ransomware attacks have grown.
The report offers new insight into the scale of ransomware attacks devastating U.S. businesses and impacting critical infrastructure. A Treasury spokesperson said the SARs don’t represent all ransomware payments.
Reporting ransomware payments to the Treasury via a suspicious activity report is often a requirement of cybersecurity insurance policies, according to a person familiar with the matter.
The Treasury Department also identified 68 ransomware variants, noting that the most commonly reported types were REvil, Conti and DarkSide. Ransomware groups often sell their malware, or variant, to affiliates who then use it to plot attacks, in what is known as ransomware-as-a-service.
REvil, Conti and DarkSide are suspected by cybersecurity firms of being tied to Russia in some way — because they use the Russian language or are suspected of being based there.
The report was filed as the Treasury Department issued guidance to the virtual currency industry to prevent exploitation by entities sanctioned by the U.S. and ransomware groups. It is part of a broader effort by the Biden administration to attempt to curb ransomware attacks. In ransomware attacks, hackers encrypt a victim’s files and promise to unlock them if they are paid a fee.
Among the more notable attacks were those in May on Colonial Pipeline Co. in May that squeezed fuel supplies on the East Coast and on the meatpacker JBS SA.
The Treasury report stated that ransomware actors are increasingly requesting payment in cryptocurrencies like Monero, which are designed to enhance anonymity.
Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,Ultimate Resource For Crypto-Currency,
Related Articles:
Bitcoin Information & Resources (#GotBitcoin?)
Crypto Dusting Attack Affects Nearly 300,000 Addresses (#GotBitcoin?)
A Case For Bitcoin As Recession Hedge In A Diversified Investment Portfolio (#GotBitcoin?)
SEC Guidance Gives Ammo To Lawsuit Claiming XRP Is Unregistered Security (#GotBitcoin?)
15 Countries To Develop Crypto Transaction Tracking System: Report (#GotBitcoin?)
US Department Of Commerce Offering 6-Figure Salary To Crypto Expert (#GotBitcoin?)
Mastercard Is Building A Team To Develop Crypto, Wallet Projects (#GotBitcoin?)
Canadian Bitcoin Educator Scams The Scammer And Donates Proceeds (#GotBitcoin?)
Amazon Wants To Build A Blockchain For Ads, New Job Listing Shows (#GotBitcoin?)
Shield Bitcoin Wallets From Theft Via Time Delay (#GotBitcoin?)
Blockstream Launches Bitcoin Mining Farm With Fidelity As Early Customer (#GotBitcoin?)
Commerzbank Tests Blockchain Machine To Machine Payments With Daimler (#GotBitcoin?)
Man Takes Bitcoin Miner Seller To Tribunal Over Electricity Bill And Wins (#GotBitcoin?)
Bitcoin’s Computing Power Sets Record As Over 100K New Miners Go Online (#GotBitcoin?)
Walmart Coin And Libra Perform Major Public Relations For Bitcoin (#GotBitcoin?)
Judge Says Buying Bitcoin Via Credit Card Not Necessarily A Cash Advance (#GotBitcoin?)
Poll: If You’re A Stockowner Or Crypto-Currency Holder. What Will You Do When The Recession Comes?
1 In 5 Crypto Holders Are Women, New Report Reveals (#GotBitcoin?)
Beating Bakkt, Ledgerx Is First To Launch ‘Physical’ Bitcoin Futures In Us (#GotBitcoin?)
Facebook Warns Investors That Libra Stablecoin May Never Launch (#GotBitcoin?)
Government Money Printing Is ‘Rocket Fuel’ For Bitcoin (#GotBitcoin?)
Bitcoin-Friendly Square Cash App Stock Price Up 56% In 2019 (#GotBitcoin?)
Safeway Shoppers Can Now Get Bitcoin Back As Change At 894 US Stores (#GotBitcoin?)
TD Ameritrade CEO: There’s ‘Heightened Interest Again’ With Bitcoin (#GotBitcoin?)
Venezuela Sets New Bitcoin Volume Record Thanks To 10,000,000% Inflation (#GotBitcoin?)
Newegg Adds Bitcoin Payment Option To 73 More Countries (#GotBitcoin?)
China’s Schizophrenic Relationship With Bitcoin (#GotBitcoin?)
More Companies Build Products Around Crypto Hardware Wallets (#GotBitcoin?)
Bakkt Is Scheduled To Start Testing Its Bitcoin Futures Contracts Today (#GotBitcoin?)
Bitcoin Network Now 8 Times More Powerful Than It Was At $20K Price (#GotBitcoin?)
Crypto Exchange BitMEX Under Investigation By CFTC: Bloomberg (#GotBitcoin?)
“Bitcoin An ‘Unstoppable Force,” Says US Congressman At Crypto Hearing (#GotBitcoin?)
Bitcoin Network Is Moving $3 Billion Daily, Up 210% Since April (#GotBitcoin?)
Cryptocurrency Startups Get Partial Green Light From Washington
Fundstrat’s Tom Lee: Bitcoin Pullback Is Healthy, Fewer Searches Аre Good (#GotBitcoin?)
Bitcoin Lightning Nodes Are Snatching Funds From Bad Actors (#GotBitcoin?)
The Provident Bank Now Offers Deposit Services For Crypto-Related Entities (#GotBitcoin?)
Bitcoin Could Help Stop News Censorship From Space (#GotBitcoin?)
US Sanctions On Iran Crypto Mining — Inevitable Or Impossible? (#GotBitcoin?)
US Lawmaker Reintroduces ‘Safe Harbor’ Crypto Tax Bill In Congress (#GotBitcoin?)
EU Central Bank Won’t Add Bitcoin To Reserves — Says It’s Not A Currency (#GotBitcoin?)
The Miami Dolphins Now Accept Bitcoin And Litecoin Crypt-Currency Payments (#GotBitcoin?)
Trump Bashes Bitcoin And Alt-Right Is Mad As Hell (#GotBitcoin?)
Goldman Sachs Ramps Up Development Of New Secret Crypto Project (#GotBitcoin?)
Blockchain And AI Bond, Explained (#GotBitcoin?)
Grayscale Bitcoin Trust Outperformed Indexes In First Half Of 2019 (#GotBitcoin?)
XRP Is The Worst Performing Major Crypto Of 2019 (GotBitcoin?)
Bitcoin Back Near $12K As BTC Shorters Lose $44 Million In One Morning (#GotBitcoin?)
As Deutsche Bank Axes 18K Jobs, Bitcoin Offers A ‘Plan ฿”: VanEck Exec (#GotBitcoin?)
Argentina Drives Global LocalBitcoins Volume To Highest Since November (#GotBitcoin?)
‘I Would Buy’ Bitcoin If Growth Continues — Investment Legend Mobius (#GotBitcoin?)
Lawmakers Push For New Bitcoin Rules (#GotBitcoin?)
Facebook’s Libra Is Bad For African Americans (#GotBitcoin?)
Crypto Firm Charity Announces Alliance To Support Feminine Health (#GotBitcoin?)
Canadian Startup Wants To Upgrade Millions Of ATMs To Sell Bitcoin (#GotBitcoin?)
Trump Says US ‘Should Match’ China’s Money Printing Game (#GotBitcoin?)
Casa Launches Lightning Node Mobile App For Bitcoin Newbies (#GotBitcoin?)
Bitcoin Rally Fuels Market In Crypto Derivatives (#GotBitcoin?)
World’s First Zero-Fiat ‘Bitcoin Bond’ Now Available On Bloomberg Terminal (#GotBitcoin?)
Buying Bitcoin Has Been Profitable 98.2% Of The Days Since Creation (#GotBitcoin?)
Another Crypto Exchange Receives License For Crypto Futures
From ‘Ponzi’ To ‘We’re Working On It’ — BIS Chief Reverses Stance On Crypto (#GotBitcoin?)
These Are The Cities Googling ‘Bitcoin’ As Interest Hits 17-Month High (#GotBitcoin?)
Venezuelan Explains How Bitcoin Saves His Family (#GotBitcoin?)
Quantum Computing Vs. Blockchain: Impact On Cryptography
This Fund Is Riding Bitcoin To Top (#GotBitcoin?)
Bitcoin’s Surge Leaves Smaller Digital Currencies In The Dust (#GotBitcoin?)
Bitcoin Exchange Hits $1 Trillion In Trading Volume (#GotBitcoin?)
Bitcoin Breaks $200 Billion Market Cap For The First Time In 17 Months (#GotBitcoin?)
You Can Now Make State Tax Payments In Bitcoin (#GotBitcoin?)
Religious Organizations Make Ideal Places To Mine Bitcoin (#GotBitcoin?)
Goldman Sacs And JP Morgan Chase Finally Concede To Crypto-Currencies (#GotBitcoin?)
Bitcoin Heading For Fifth Month Of Gains Despite Price Correction (#GotBitcoin?)
Breez Reveals Lightning-Powered Bitcoin Payments App For IPhone (#GotBitcoin?)
Big Four Auditing Firm PwC Releases Cryptocurrency Auditing Software (#GotBitcoin?)
Amazon-Owned Twitch Quietly Brings Back Bitcoin Payments (#GotBitcoin?)
JPMorgan Will Pilot ‘JPM Coin’ Stablecoin By End Of 2019: Report (#GotBitcoin?)
Is There A Big Short In Bitcoin? (#GotBitcoin?)
Coinbase Hit With Outage As Bitcoin Price Drops $1.8K In 15 Minutes
Samourai Wallet Releases Privacy-Enhancing CoinJoin Feature (#GotBitcoin?)
There Are Now More Than 5,000 Bitcoin ATMs Around The World (#GotBitcoin?)
You Can Now Get Bitcoin Rewards When Booking At Hotels.Com (#GotBitcoin?)
North America’s Largest Solar Bitcoin Mining Farm Coming To California (#GotBitcoin?)
Bitcoin On Track For Best Second Quarter Price Gain On Record (#GotBitcoin?)
Bitcoin Hash Rate Climbs To New Record High Boosting Network Security (#GotBitcoin?)
Bitcoin Exceeds 1Million Active Addresses While Coinbase Custodies $1.3B In Assets
Why Bitcoin’s Price Suddenly Surged Back $5K (#GotBitcoin?)
Zebpay Becomes First Exchange To Add Lightning Payments For All Users (#GotBitcoin?)
Coinbase’s New Customer Incentive: Interest Payments, With A Crypto Twist (#GotBitcoin?)
The Best Bitcoin Debit (Cashback) Cards Of 2019 (#GotBitcoin?)
Real Estate Brokerages Now Accepting Bitcoin (#GotBitcoin?)
Ernst & Young Introduces Tax Tool For Reporting Cryptocurrencies (#GotBitcoin?)
Recession Is Looming, or Not. Here’s How To Know (#GotBitcoin?)
How Will Bitcoin Behave During A Recession? (#GotBitcoin?)
Many U.S. Financial Officers Think a Recession Will Hit Next Year (#GotBitcoin?)
Definite Signs of An Imminent Recession (#GotBitcoin?)
What A Recession Could Mean for Women’s Unemployment (#GotBitcoin?)
Investors Run Out of Options As Bitcoin, Stocks, Bonds, Oil Cave To Recession Fears (#GotBitcoin?)
Goldman Is Looking To Reduce “Marcus” Lending Goal On Credit (Recession) Caution (#GotBitcoin?)

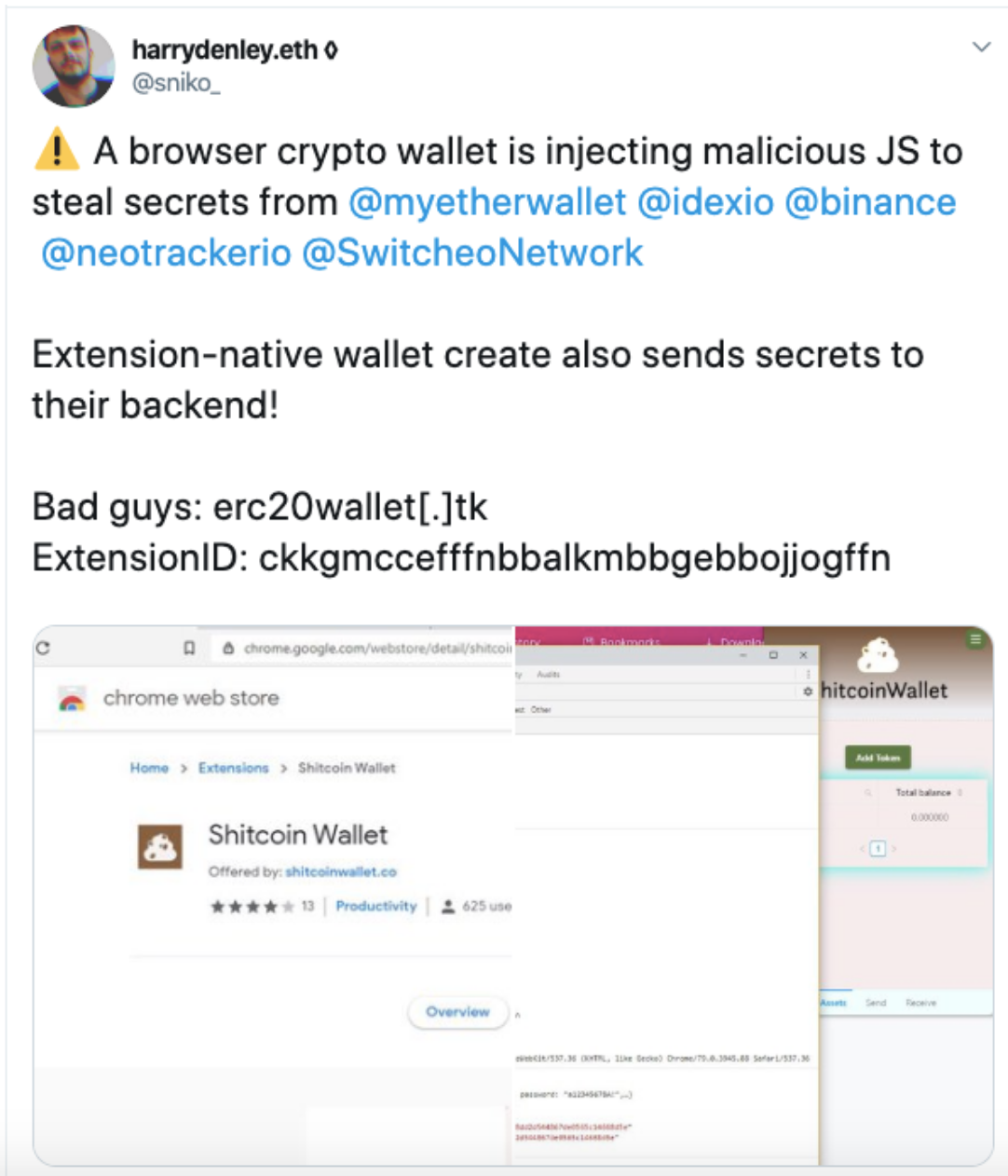
Leave a Reply
You must be logged in to post a comment.