Who’s Watching Who? gSpy vs. iSpy
Randi Zuckerberg, sister of Mark, thinks she’s got problems? Who’s Watching Who? gSpy vs. iSpy
Well, over a few hours around town that day I counted 57 cameras–at traffic lights, various stores and the bank–and my phone told me I switched between eight different cellphone towers. We are all being watched, whether we like it or not.
So who’s winning? It is a battle between you and the government–like Mad Magazine’s Spy vs. Spy comic, but it’s gSpy vs. iSpy.
Related:
Citizen Surveillance Is Playing A Major Role In Criminal Investigations
Ultimate Resource On “Havana Syndrome” Including New Cases of The Mysterious Illness
Harvard Chemical Biology Department Chair Accused Of Selling Covid19 To Wuhan University
Pentagon Sees Giant Cargo Cranes As Possible Chinese Spying Tools
US. Can Learn From China’s Spot-The-Spy Program
Apple, Google Forced To Give Governments User “Push Notifications” Data
America’s Spies Are Losing Their Edge
Vast Troves of Classified Info Undermine National Security, Spy Chief Says
Pentagon Being Investigated For One Of The Most Dangerous Intelligence Breaches In Decades
Ex-CIA Engineer Goes On Trial For Massive Leak
Ex-Intelligence Analyst Charged With Leaking Classified Information
CFPB (Idiots) Says Staffer Sent 250,000 Consumers’ Data To Personal Account
There are thousands of toll booths at bridges and turnpikes across America recording your license plate. There are 4,214 red-light cameras and 761 speed-trap cameras around the country. Add 494,151 cell towers and 400,000 ATMs that record video of your transactions.
New York City alone has 2,400 official surveillance cameras and recently hired Microsoft to monitor real-time feeds as part of the Orwellian-named Domain Awareness System.
And that is nothing compared with England, where over four million surveillance cameras record the average Londoner 300 times a day.
Popular Mechanics magazine estimates that there are some 30 million commercial surveillance cameras in the U.S. logging billions of hours of video a week. I guarantee that you’re in hundreds if not thousands of these.
In the year 1984, we only had lame amber-screened PCs running Lotus 123. Now, 64 years after George Orwell sent “1984” to his publisher, we have cheap video cams and wireless links and terabyte drives and Big Brother is finally watching.
So gSpy Is Winning, Right?
Not so fast. We are watching back. I know the precise number of red-light cameras because a website (poi-factory.com) crowdsources their locations and updates them daily for download to GPS devices. And 30 million surveillance cameras are a pittance compared with the 327 million cellphones in use across America, almost all of them with video cameras built in.
How do you think the “Don’t tase me, bro” guy protesting a 2007 speech by John Kerry ever got famous? Last year, when cops at the University of California at Davis were caught on video pepper-spraying protesters, they had to pay $30,000 each to 21 students to settle. A man arrested for blocking traffic at an Occupy Wall Street protest (who was there to defend police tactics, oddly) was acquitted when smartphone photos and video showed protesters on the sidewalk, not the street. Six members of the 2004 St. John’s basketball team had rape charges against them dropped when a video of the accuser’s extortion demands was recorded on a player’s cellphone.
Zapruder, Rodney King, the young Iranian Neda Agha-Soltan’s death by gunshot after her country’s rigged 2009 election. In America and increasingly across the world, iSpies are watching, too.
Both sides are getting more sophisticated. Snowboarders mount GoPro Hero cameras to their helmets to record up to eight hours of their exploits. So-called lifeloggers pin small, $199 “Memoto” cameras to their shirts and snap a photo every 30 seconds. With cheaper data storage, it is easy to envision iSpies logging audio, GPS and eventually video of our lives.
But gSpy is going further. Already a third of large U.S. police forces equip patrol cars with automatic license plate-readers that can check 1,000 plates per hour looking for scofflaws. Better pay those parking tickets because this system sure beats a broken tail light as an excuse to pull you over. U.S. Border Patrol already uses iris-recognition technology, with facial-recognition in the works, if not already deployed. How long until police identify 1,000 faces per hour walking around the streets of New York?
In September, Facebook turned off its facial-recognition technology world-wide after complaints from Ireland’s Data Protection Commission. I hope they turn it back on, as it is one of the few iSpy tools ahead of gSpy deployment.
The government has easy access to our tax information, stock trades, phone bills, medical records and credit-card spending, and it is just getting started. In Bluffdale, Utah, according to Wired magazine, the National Security Agency is building a $2 billion, one-million-square-foot facility with the capacity to consume $40 million of electricity a year, rivaling Google ‘s biggest data centers.
Some estimate the facility will be capable of storing five zettabytes of data. It goes tera, peta, exa, then zetta–so that’s like five billion terabyte drives, or more than enough to store every email, cellphone call, Google search and surveillance-camera video for a long time to come. Companies like Palantir Technologies (co-founded by early Facebook investor Peter Thiel) exist to help the government find terrorists and Wall Street firms find financial fraud.
As with all technology, these tools will eventually be available to the public. Internet users created and stored 2.8 zettabytes in 2012. Facebook has a billion users. There are over 425 million Gmail accounts, which for most of us are personal records databases. But they’re vulnerable. We know from the takedown of former Gen. David Petraeus
that some smart legwork by the FBI (in this case matching hotel Wi-Fi tags and the travel schedule of biographer Paula Broadwell can open up that database to prying eyes. Google has accused China of cracking into Gmail accounts.
Google gets over 15,000 criminal investigation requests from the U.S. government each year, and the company says it complies 90% of the time. The Senate last week had a chance to block the feds from being able to read any domestic emails without a warrant–which would put some restraint on gSpy–but lawmakers passed it up. Google’s Eric Schmidt said in 2009, “If you have something that you don’t want anyone to know, maybe you shouldn’t be doing it in the first place.” Thanks, Eric.
From governments to individuals, the amount of information captured and stored is growing exponentially. Like it or not, a truism of digital technology is that if information is stored, it will get out. Mr. Schmidt is right. It doesn’t matter whether an iSpy friend of Randi Zuckerberg tweets it or a future WikiLeaks pulls it out of the data center at Bluffdale and posts it for all to view.
Gen. Petraeus knows it. Politicians yapping about “clinging to guns” or “the 47%” know it. Information wants to be free and will be. Plan for it. I’m paying my parking tickets this week.
Updated: 6-29-2023
Police Are Requesting Self-Driving Car Footage For Video Evidence
San Francisco police request driverless car footage from Waymo and Cruise to solve crimes from robberies to murders.
In December 2021, San Francisco police were working to solve the murder of an Uber driver. As detectives reviewed local surveillance footage, they zeroed in on a gray Dodge Charger they believed the shooter was driving. They also noticed a fleet of Waymo’s self-driving cars, covered with cameras and sensors, happen to drive by around the same time.
Recognizing the convenient trove of potential evidence, Sergeant Phillip Gordon drafted a search warrant to Alphabet Inc.’s Waymo, demanding hours of footage that the SUVs had captured the morning the shooting took place.
“I believe that there is probable cause that the Waymo vehicles driving around the area have video surveillance of the suspect vehicle, suspects, crime scene, and possibly the victims in this case,” Gordon wrote in the application for the warrant to Google’s sister company. A judge quickly authorized it, and Waymo provided footage.
As self-driving cars become a fixture in major American cities like San Francisco, Phoenix and Los Angeles, police are increasingly relying on their camera recordings to try to solve cases.
In Waymo’s main markets, San Francisco and Arizona’s Maricopa County, Bloomberg found nine search warrants that had been issued for the company’s footage, plus another that had been sent to rival autonomous driving firm Cruise. More warrants may have been issued under seal.
The footage presents new avenues for police to investigate serious crimes, as they did in the murder of the Uber driver, Ahmed Yusufi, who was killed between shifts.
Yet privacy advocates say it is crucial to consider the implications of handing police another tool for surveillance, especially as Waymo and Cruise accelerate expansion to more cities.
In the Phoenix area, Waymo has a partnership with Uber for people to eventually request driverless rides through that familiar app; it has also announced plans to test its service in Austin, where Cruise already operates.
While security cameras are commonplace in American cities, self-driving cars represent a new level of access for law enforcement — and a new method for encroachment on privacy, advocates say.
Crisscrossing the city on their routes, self-driving cars capture a wider swath of footage. And it’s easier for law enforcement to turn to one company with a large repository of videos and a dedicated response team than to reach out to all the businesses in a neighborhood with security systems.
“We’ve known for a long time that they are essentially surveillance cameras on wheels,” said Chris Gilliard, a fellow at the Social Science Research Council.
“We’re supposed to be able to go about our business in our day-to-day lives without being surveilled unless we are suspected of a crime, and each little bit of this technology strips away that ability.”
Waymo said it occasionally receives requests from local police in markets where it operates and generally requires law enforcement to provide a warrant or court order.
“We carefully review each request to make sure it satisfies applicable laws and has a valid legal process,” Waymo said. “If a request is overbroad (asks for too much information), we try to narrow it, and in some cases we object to producing any information at all.”
Cruise said it also strives to provide the minimum amount of data necessary to satisfy requests from law enforcement.
“Privacy is extremely important to us, which is why we disclose relevant data only in response to legal processes or exigent circumstances, where we can help a person who is in imminent danger,” Cruise said in a statement.
Waymo emerged from the labs of Google, whose rich user data creates opportunities for law enforcement at every turn. In one hit-and-run case in San Francisco, police learned Waymo had passed by the crime scene while reviewing footage from a Nest home surveillance camera, presenting yet another connection with Google, which bought the smart-home hardware maker in 2014.
Privacy advocates are particularly concerned about the evidence that police can glean from the so-called internet of things, the growing landscape of connected devices such as doorbells and home security cameras that collect vast amounts of data.
Amazon’s Ring doorbells have found a following with both consumers and law enforcement; thousands of agencies subscribe to its Neighbors app, where camera owners voluntarily upload footage.
Last year, Amazon revealed that it had shared footage in emergencies without owners’ permission, sparking criticism from lawmakers. Amid the controversy over Ring’s data collection, Amazon has begun offering end-to-end encryption of the videos and has asked cops to request footage publicly in the Neighbors app.
While self-driving services like Waymo and Cruise have yet to achieve the same level of market penetration as Ring, the wide range of video they capture while completing their routes presents other opportunities.
In addition to the San Francisco homicide, Bloomberg’s review of court documents shows police have sought footage from Waymo and Cruise to help solve hit-and-runs, burglaries, aggravated assaults, a fatal collision and an attempted kidnapping.
In all cases reviewed by Bloomberg, court records show that police collected footage from Cruise and Waymo shortly after obtaining a warrant.
In several cases, Bloomberg could not determine whether the recordings had been used in the resulting prosecutions; in a few of the cases, law enforcement and attorneys said the footage had not played a part, or was only a formality.
However, video evidence has become a lynchpin of criminal cases, meaning it’s likely only a matter of time.
In markets where Waymo and Cruise operate, police departments have alerted their detectives to the investigative opportunities that the vehicles present. A San Francisco Police Department training document obtained by Vice instructed detectives of the vehicles’ “potential to help with investigative leads.”
Waymo said it responds to law enforcement requests with footage that blurs license plates and faces “in order to protect the privacy of bystanders who may appear in the imagery that’s requested by the warrant.” But San Francisco police seem to be trying to find a way around that.
Two of the warrants reviewed by Bloomberg, which were obtained in burglary cases, noted Waymo’s practice of “fogging” footage and requested “a true and accurate depiction of the vehicle’s recordings.”
Comprehensive privacy legislation, which has languished for years in the US, is ultimately the only thing that can thwart overly broad requests from police, experts say.
“With the lack of consumer privacy protections that we have in the US right now, companies are able to collect as much information as humanly possible,” said Matthew Guariglia, a policy analyst at the Electronic Frontier Foundation, adding that police are then able to capitalize on the trove of data.
Police who have obtained footage from self-driving cars say they view it as a tool to be used judiciously — and that the evidence can be used not just to build cases, but to exonerate suspects.
Last year, a teen in Mesa, Arizona, said she was trying to hop into a Waymo she had hailed when her cell phone, which riders use to enter the vehicle, ran out of battery.
She claimed a man offered to help her charge her phone and then attempted to force her into his vehicle. Bystanders intervened. All the while, Waymo was recording.
When Mesa Detective Trisha Jackson received the report, she recalled a flyer she had received from her department when self-driving cars became more prevalent in the area about the opportunities that footage from the vehicles could create for cops.
She reached out to the company, which she said offered guidance on the warrant process. But when Waymo ultimately produced the footage, it contradicted the teen’s account. Jackson saw no evidence of a crime.
Jackson said reviewing the Waymo footage enabled her to close the case more quickly, saving police resources.
“We were able to contact the company and get the search warrant done, and they were able to give us exactly what we had asked for in a timely manner,” she said.
Last year, San Francisco police obtained a search warrant for Waymo footage to try to solve a spate of residential burglaries. John McCammon, whose apartment was among those burglarized, says he has mixed feelings about police seeking such evidence.
He’s wary of handing police a new tool, especially in San Francisco, where the police department has made headlines for its proposal to use robots and other high-tech investigative techniques.
When a Bloomberg reporter informed McCammon that Waymo had witnessed the crime, he wasn’t surprised. The vehicles are such a regular presence on his street that he has considered writing to the local government to complain.
He said Waymo’s assistance in his case was unlikely to change his opinion of the self-driving service, which he has already written off as a “constant irritant.” Local officials are often responding to complaints about Waymo and Cruise vehicles blocking roads when their software is confused by construction, parades and crime scene barricades.
And the footage isn’t always helpful. In the case of the Uber driver who was shot, San Francisco police arrested Clifford Stokes, who was convicted of murdering Yusufi earlier this year.
Yusufi had worked as an interpreter for the American military during the war in Afghanistan, and after settling in California, he supported himself by working as an Uber driver, according to local media reports. He was killed in a botched armed robbery in between shifts.
A lawyer involved in the case said though police did obtain the Waymo video, it was not ultimately used in the prosecution of Stokes, as Waymo had not actually filmed the Dodge Charger. Still, such cases are a reminder of the new frontier that self-driving cars open up for law enforcement, privacy advocates say.
Police tapped Waymo for the footage in that murder case just a few months after the company began testing its self-driving service with members of the public in San Francisco.
“Whenever you have a company that collects a large amount of data on individuals, the police are eventually going to come knocking on their door hoping to make that data their evidence,” Guariglia said.
Spy Fears Over A Chinese Corn Mill Led Biden To Tighten US Investment Curbs
Rising US hostility toward China surfaces in Middle America.
Presidents Joe Biden and Xi Jinping are trying to ease tensions and calm trade fights between the world’s top economies. The collapse of a project in the American heartland shows just how deep a chill has set in.
Biden dispatched Secretary of State Antony Blinken for a visit to Beijing and a meeting with Xi last week, and Treasury Secretary Janet Yellen is planning her own visit in July, according to people familiar with the matter.
But Biden’s gestures are accompanied by a souring national mood on China. Underneath the pomp of top-tier visits by US officials, there is growing resentment among ordinary Americans and state and local politicians toward Chinese attempts at US investment.
There’s no clearer example of the grassroots shift in sentiment than in Grand Forks, North Dakota, where a failed agricultural complex led to new proposals at both the federal and state level to restrict China-linked development.
The city this year abandoned a project that, just two years earlier, it had aggressively sought as an economic bonanza: a $700 million corn mill that would have risen from rich farmland on the outskirts of the community.
The mill faced a groundswell of opposition, especially regarding its owner: a Chinese company, Fufeng Group.
The saga touched off a battle emblematic of growing US angst about Chinese investment. It combined swirling local concerns, opaque federal rules, saber-rattling politicians and potential loopholes in security laws, ultimately concluding with an unusual public warning from the Air Force that the corn mill posed a national security threat.
The ripples reached beyond Grand Forks, as Biden’s administration in May quietly moved to tighten scrutiny of foreign property purchases near the city’s Air Force base and other military facilities.
The abandoned corn mill also illustrates a political shift. Politicians who once backed the project— including North Dakota’s governor, Doug Burgum, a Republican running for president — now oppose it.
Some Republican-led states, including Burgum’s, seek to restrict or outright ban Chinese property purchases. The mayor of Grand Forks, Brandon Bochenski, says cities like his shouldn’t be left to determine foreign investment policy.
“Until there is an actual strategy, I don’t see how you can have really any investment from China — whether it’s ag, or tech, or anything,” Bochenski said in an interview in a city building that once housed the local newspaper.
“Right now, I think that’s the problem,” he said. “There’s no clear direction from the federal government.”
`Great Day for Grand Forks’
Fufeng Group’s corn mill once looked like an economic prize. It promised hundreds of jobs and enough corn products to fill 180 train cars a week. Grand Forks won the project over about two dozen other Midwest locations.
A $700 Million Corn Mill That Raised US Suspicions
Beijing-based Fufeng Group sought to build a wet corn mill 12 miles from a US air base.
Fufeng Group, founded in 1999 and listed on the Hong Kong stock exchange, is the world’s largest manufacturer of the common food additives monosodium glutamate and xanthan gum, according to its website. Its investors include Treetop Asset Management, Blackrock Inc. and the Vanguard Group.
The company’s US representatives declined interview requests but said in written responses to questions that it “does not pose a national security threat.”
“Our plant is designed to mill corn and make livestock feed ingredients,” the company’s spokespeople said. “Neither the US company nor the Fufeng Group have any ties to any government, political party, or official.”
Fufeng’s US subsidiary sought in the spring of 2020 to build its first US wet corn mill. The endeavor was dubbed “Project Peony,” after a flower popular in both China and the US. Grand Forks officials were jubilant when the company notified them they’d won.
“Great Day for Grand Forks, Great Day for North Dakota!” Keith Lund, who leads the city’s economic development agency, wrote in an email.
Local opposition focused at first on concerns such as pollution, subsidies and land use, but soon shifted to the mill’s ownership.
“Larger and louder than all of the other concerns was a fear of Communist China,” said Katie Dachtler, the only member of the city council to initially vote against the project, who has since left office. “And we can’t talk about the Chinese without them being ‘communists.'”
People in Grand Forks who opposed the project from the start say their political leaders should have seen the trouble coming.
“You come here because you can get away with stuff,” said Frank Matejcek, a farmer who lives just outside the city.
“Everyone kept saying they would do due diligence, and look into this, and the company had been vetted and all this stuff, when actually none of this was happening,’’ he said.
Fufeng Fighters
The city and Fufeng signed a deal in May 2022. But as complaints mounted, city leaders grappled for a clear answer about whether the mill could be a front for Chinese spies.
City and state officials, including its two senators and the governor, requested a review by the Committee on Foreign Investment in the US, or CFIUS, a secretive panel led by Yellen.
It would not have been Grand Forks’s first experience doing business with China. Cirrus Aircraft Corp., which operates a factory in the city, is owned by a Chinese government-controlled firm, China Aviation Industry General Aircraft. Cirrus’s purchase by CAIGA in 2011 was subject to a CFIUS review, which yielded an agreement allowing the government to closely monitor the business’s operations.
But CFIUS told state and local officials it didn’t have jurisdiction over the mill. Building the project on land Fufeng had already bought — for $26,000 an acre, according to its opponents, a price they regarded as suspiciously inflated — wasn’t considered an acquisition, and the property wasn’t close enough to the base to trigger a probe, under rules in effect at the time.
“If a wet corn-milling plant run by Fufeng isn’t under CFIUS jurisdiction, then CFIUS has a problem,” said Kelly Armstrong, the state’s lone House member.
The Air Force would have its own say. In January, the service’s assistant secretary, Andrew Hunter, wrote to the state’s two senators, Kevin Cramer and John Hoeven.
The Air Force’s “unambiguous” view, Hunter wrote, was that the mill posed “a significant threat to national security, with both near- and long-term risks.”
The one-page letter didn’t elaborate. But political support evaporated, and the city council voted Feb. 6 to end the project — two days after President Joe Biden ordered an alleged Chinese surveillance balloon shot down after it floated across the country.
Spokespeople for the Air Force and the Grand Forks base declined further comment.
Cramer, who received a classified briefing on the project in December, said he has little doubt about Fufeng’s motive.
“It was highly likely that the investment was made to take advantage of its proximity of the Air Force base,” the senator said in an interview.
Local opponents — who call themselves the Fufeng Fighters, a play on the name of the rock band Foo Fighters — say the federal government should have been more involved from the start.
“It’s easy to see how there needs to be more federal scrutiny,” said Ben Grzadzielewski, a contractor who organized a petition over a range of concerns, including the mill’s environmental impact and public subsidies. “Because at a local level, it’s pretty easy to convince them of how great things are, and get them to run with it.”
Burgum Reversal
Burgum, the governor who helped woo Fufeng to North Dakota, “initially expressed support for the value that a wet corn mill would add for the area’s corn growers and the economic benefits to the region,” his spokesman Mike Nowatzki said in a statement.
But he said the governor “urged an expedited review of the land purchase and shared our U.S. senators’ concerns about the project several months” before it was canceled.
The project’s demise has been felt far beyond Grand Forks.
The Treasury Department in May proposed adding the Grand Forks base and seven others to a list of military facilities around which foreign investment within 100 miles triggers a CFIUS review.
Sensitive Real Estate
The Biden administration added Grand Forks AFB and seven other installations to a list of bases where nearby foreign property purchases can trigger federal review.
The North Dakota saga ended hopes of reviving plans by Chinese state-owned food processor Cofco Corp. to purchase an interest in a Cargill Inc. and CHS Inc. shipping terminal, according to a person familiar with the proposed transaction.
North Dakota passed a law this year banning foreign purchases of agricultural land, except by Canadians. A similar bill in Texas passed the state’s Senate but died in the House. Florida’s government has been sued over a law it adopted earlier this year banning all property purchases by Chinese nationals.
Fufeng still owns its Grand Forks land but is seeking “alternative options.” The US political climate is working against it.
Bob Scott, the mayor of Sioux City, Iowa, another city Fufeng considered, said in an interview that there’s no longer any interest. “Following that, up in North Dakota, they’re going to have a very, very difficult time getting a community,” he said.
Updated: 6-30-2023
US Spies Issue Warnings Over Risks of Doing Business In China
US intelligence officials renewed warnings for American companies doing business in China, citing an update to a counterespionage law that’s due to take effect in the next day.
A bulletin issued by the National Counterintelligence and Security Center on Friday warns executives that an update to China’s counterespionage law, which comes into effect on July 1, has the “potential to create legal risks or uncertainty” for companies doing business in China.
It adds that the law broadens the scope of China’s espionage law and expands Beijing’s official definition of espionage. “Any documents, data, materials, or items” could be considered relevant to the law due to its “ambiguities,” the bulletin says.
The revisions to China’s counterespionage law have raised further concerns for US companies, which already find themselves in caught in the middle of an increasingly fraught US-China relationship.
The law is just one of a slew of measures taken by President Xi Jinping to strengthen state power and clamp down on foreign influence.
Earlier this year, authorities in China questioned staff at the China offices of US consultancy Bain & Company. Officials also raided
the Beijing office of New York-based due diligence firm Mintz Group and detained five of its Chinese employees. China’s foreign ministry put out a short statement saying Mintz was suspected of illegal business operations, while separately stating that it wasn’t aware of any raid at Bain’s Shanghai office.
The bulletin also draws attention to other pieces of Chinese legislation, including the 2021 Cyber Vulnerability Reporting Law, which it says could provide Beijing with the “opportunity to exploit system flaws before cyber vulnerabilities are publicly known.”
It also discusses the 2017 National Intelligence Law, which it says may force locally employed Chinese nationals working at US companies to assist in intelligence efforts for Beijing.
Updated: 7-17-2023
Inside Russia’s Spy Unit Targeting Americans
This transcript was prepared by a transcription service. This version may not be in its final form and may be updated.
Peter Zwack: My name is Peter Zwack, retired US Army Brigadier General. I was in Moscow serving as our senior U.S. Defense Attaché.
Kate Linebaugh: Peter served in Moscow from 2012 to 2014, and during that time he noticed some strange things, like the time he was driving and saw someone tailing his car from above.
Peter Zwack: We had a helicopter just there hovering for a while as we were driving along.
Kate Linebaugh: Sometimes his family would come home and just sense that something was off.
Peter Zwack: There would just be strange signs that somebody had been in your apartment. My son lost his watch or thought his watch would move, and then one day, a week or two later, the watch was sitting there on the floor, just odd, clothing moved. And it’s kind of a tap on the shoulder that we know you’re here.
Kate Linebaugh: A tap on the shoulder from Russia’s spy network.
Peter Zwack: You have to make the assumption when you’re in Moscow that you are under surveillance and you’re being followed one way or the other.
Kate Linebaugh: Peter is one of many Americans who said they’ve experienced unsettling things in Russia. Americans, including our colleague, Evan Gershkovich, who was followed by several Russian security officers. Earlier this year, Evan was arrested on espionage charges, charges that he and the Wall Street Journal vehemently deny. Now, after months of reporting, the Journal has uncovered that one secret unit in Russia’s powerful spy agency is behind it all. Welcome to the Journal, our show about money, business, and power. I’m Kate Linebaugh. It’s Monday, July 17th. Coming up on the show, the secretive Russian security force targeting Americans. On March 29th, Wall Street Journal reporter Evan Gershkovich was on a reporting trip outside of Moscow when he was arrested. When they first heard the news, our colleagues, Joe Parkinson and Drew Hinshaw, had a lot of questions.
Drew Hinshaw: Almost immediately after, Joe and I started to think about, “Well, who took him?”
Joe Parkinson: And that’s a very simple question, but it led us on this very, very complicated transnational journey where the simple question actually revealed this much bigger truth about not just one of the most opaque corners of the Russian security services but also the power that this particular unit has inside Putin’s Russia today.
Kate Linebaugh: Joe and Drew’s reporting journey took them across Europe and the US. They interviewed dozens of senior diplomats and security officials, former Russian intelligence officers, Americans who’d previously been jailed in Russia and their families, as well as independent Russian Journalists and security analysts who fled the country. They also drew information from public court proceedings as well as reviewed leaked Russian intelligence memos.
Drew Hinshaw: And we spoke with former American officials and current American officials who had the unpleasant life of being based in Moscow or traveling to Moscow and being subject to spycraft and harassment.
Kate Linebaugh: They heard stories about intimidation tactics that at times sounded like juvenile pranks, like the kind Peter described.
Joe Parkinson: The bookcases have been moved around. People will come home; the car keys are missing, the jewelry is missing. Another thing they do is leave a calling card, which is a lit cigarette or a stubbed-out cigarette, on a toilet seat.
Kate Linebaugh: Other times, these calling cards were nasty.
Drew Hinshaw: An American official visiting Moscow came back to his hotel room and found someone had defecated in his suitcase.
Kate Linebaugh: Ew. Some were unsettling.
Joe Parkinson: They also liked to slash the tires of cars that are parked around the embassy or the residences of diplomats.
Drew Hinshaw: They’ve followed an ambassador’s young children to things like soccer practice and into a McDonald’s.
Kate Linebaugh: And sometimes the stories were downright scary.
Drew Hinshaw: Someone working in the Defense Attaché’s office came home and found his dog dead in what appeared to be a poisoning.
Kate Linebaugh: Joe and Drew suspected that behind many of these antics was Russia’s main security service, the FSB, which had replaced the old Soviet-era KGB. So they started to talk with their sources about what exactly was going on inside the agency.
Joe Parkinson: As we were plunging into this huge, opaque, deliberately secretive institution, which is the FSB, we tried, first of all, to map what the different directorates were because the FSB is very, very complicated, structured into these directorates, inside these directorates, all these smaller subdivisions.
Kate Linebaugh: And then they got a tip, a potential name for the unit.
Joe Parkinson: And one of the former US ambassadors that we spoke to said, “Well, the subdivision of the unit that’s responsible for following Americans has always been DKRO.”
Kate Linebaugh: DKRO, or the DKRO, for the Department for Counterintelligence Operations. Joe and Drew now had something to go on. The problem was they could scarcely find anything about it.
Drew Hinshaw: Well, I think at one point I Googled them, and there’s like 35 Google results, and most of them were just random. If you Google four random letters, some weird stuff comes up.
Joe Parkinson: Do you know that the Wikipedia page for DKRO was created after our story was written?
Kate Linebaugh: I did not know that. So what is DKRO?
Drew Hinshaw: DKRO is the counterintelligence arm of the FSB. They’re responsible for monitoring foreigners in Russia. So if you visit Russia, there’s a good chance they would be monitoring you. And its first section, DKRO-1, is the subdivision responsible for following Americans and Canadians.
Kate Linebaugh: Those slash tires, the dead dog, Peter’s car being trailed by a low-flying helicopter, US officials have chalked it up to DKRO, though it’s impossible to know whether DKRO is behind every such incident. The unit makes no public statements. And in the course of your reporting, you spoke with so many people; what did they tell you was the goal of all of this?
Drew Hinshaw: They said the goal is to stifle any American diplomats movements in Russia, to keep them inside the embassy walls, have them put their heads down, and do nothing during their two or three years they’re base there.
Joe Parkinson: Many people who worked in that embassy over the last 10 years did say that the Russians’ tactics were incredibly effective.
Kate Linebaugh: Neither the FSB nor the Kremlin responded to written questions. The State Department and the US Embassy in Moscow declined to comment, as did Evan’s lawyers in Russia. The modern-day FSB traces its roots to the fall of the Soviet Union in 1991.
Drew Hinshaw: Every pillar of Soviet society collapsed. But there was one thing that survived, and that was the spy agencies.
Kate Linebaugh: Out of the ashes of the KGB came the FSB, and its expanding role in Russian life was helped by one person in particular, Vladimir Putin.
Joe Parkinson: This is a man who wanted to join the KGB since he was a teenager. He famously walked into the KGB office in St. Petersburg through the front door and asked if he could join, which is a very unusual way of being recruited. They told him to go off to university and study, and maybe then he could be hired.
Kate Linebaugh: The young Putin did return after graduating, and he had big ambitions. Around this time, Drew says a new Russia was emerging.
Drew Hinshaw: There’s this huge 1990s influx of American investors, reporters, visitors. There’s a McDonald’s in Moscow. Russia is now open.
Kate Linebaugh: In 1998, Putin became the head of the FSB, and then in 2000, he became President of Russia. Under his leadership, the security services role has expanded; some security analysts now call Russia a counterintelligence state, with the FSB controlling many aspects of Russian life. And one arm of the FSB that’s grown is DKRO.
Joe Parkinson: People that we spoke to said that DKRO’s operations essentially ebb and flow with the policy inside the Kremlin. However, as Russia and Putin’s Russia has become more and more insular in the last 20 years, as Putin himself has become more paranoid, DKRO has become an expression of that.
Kate Linebaugh: Isn’t this just what countries do, everybody’s spying on everybody?
Joe Parkinson: It’s definitely the case that intelligence services exist for a reason. Countries are spying on each other, enemies, friends, all of these institutions are trying to gather information, but there is something everyone who has served in Moscow says, and that is that it is qualitatively different. It is much, much more hostile.
Kate Linebaugh: And this more hostile posturing would have big consequences for foreign journalists, journalists like Evan Gershkovich. That’s next. Drew says Evan’s detention in March doesn’t seem to have been his first brush with DKRO agents.
Drew Hinshaw: Evan had had these bizarre experiences where, on one assignment, Evan was followed by several Russian security officers, at least one of whom had his camera out and was recording his movements.
Kate Linebaugh: After the invasion of Ukraine, Evan began investigating the expanding role the security services played in Russia. He and some colleagues reported that the FSB had mainly planned the invasion, not the military. But as the war dragged on and began to flounder, the FSB came under pressure from President Putin.
Drew Hinshaw: He publicly berated his spy agencies several times, saying that they needed to kick up their work. At one point, he says, quote, “You need to significantly improve your work.”
Vladimir Putin: (Russian)
Kate Linebaugh: Soon after, US officials noticed an uptick in aggressive actions toward the few Americans still in Russia.
Drew Hinshaw: And around that time, Evan, among many other reporters, started to notice that they were being followed by what we now understand to be DKRO.
Kate Linebaugh: While awaiting trial, Evan is being held in Russia’s Lefortovo prison, the same prison where former US Marine Paul Whelan was once held. Whelan is now serving a 16-year sentence on spying charges. The US State Department has deemed Whelan and Evan as wrongfully detained. Since Evan’s arrest, another American has been picked up by security services in Russia. Last month, a former US paratrooper and musician named Travis Michael Leek was detained on drug charges, which he denies. In recent years, Russia and the US have engaged in several prisoner swaps, including for Britney Griner, and last week President Biden said he is, quote, “serious about a prisoner exchange for Evan.”
Drew Hinshaw: So clearly, this continues. Evan is neither the first nor the last attempt by Russia to use human beings as bargaining chips in this conflict with America.
Kate Linebaugh: Joe and Drew say that their reporting showed Putin knew about the operation to arrest Evan.
Joe Parkinson: While we don’t know and we perhaps will never know whether Putin himself ordered Evan to be arrested, we do know a proposal for this operation reached his desk before March 29th, when Evan was taken. We do know from speaking to people who are familiar with the situation that, after the arrest, Putin was briefed by Vladislav Menshchikov, who is in charge of counterintelligence at the FSB. And we do know that he asked how the operation went. He wanted details on the operation.
Kate Linebaugh: What does this ramp up of surveillance of Westerners in Russia tell us about Putin?
Drew Hinshaw: The thing I was struck with is just how much Russia is a country run by the spy chief. Putin was the FSB director, and he runs the country exactly the way you would imagine an FSB director surrounded by paranoid former and current spies would.
Joe Parkinson: Yes, it’s a mentality that’s paranoid. Yes, it’s a mentality that is very, very suspicious of the West, but it also shows that he’s still very interested in operations that you would think someone like him perhaps wouldn’t have the time or the inclination to be following on a granular level. So it really is someone who’s still following the minutiae and someone who’s still running the entire country, not just as if he’s the president but as if he’s also head of the security services.
Kate Linebaugh: That’s all for today, Monday, July 17th. The Journal is a co-production of Gimlet and the Wall Street Journal. Also, if you haven’t listened to our recent series, With Great Power: The Rise of Superhero Cinema, go back and check it out. It’s in your feed. Thanks for listening. See you tomorrow.
Updated: 8-10-2023
To Battle New Threats, Spy Agencies To Share More Intelligence With Private Sector
Pandemics, cyberattacks and supply-chain disruptions are pushing government to work more with outside groups.
WASHINGTON—U.S. spy agencies will share more intelligence with U.S. companies, nongovernmental organizations and academia under a new strategy released this week that acknowledges concerns over new threats, such as another pandemic and increasing cyberattacks.
The National Intelligence Strategy, which sets broad goals for the sprawling U.S. intelligence community, says that spy agencies must reach beyond the traditional walls of secrecy and partner with outside groups to detect and deter supply-chain disruptions, infectious diseases and other growing transnational threats.
The intelligence community “must rethink its approach to exchanging information and insights,” the strategy says.
The U.S. government in recent years has begun sharing vast amounts of cyber-threat intelligence with U.S. companies, utilities and others who are often the main targets of foreign hackers, as well as information on foreign-influence operations with social-media companies.
The last National Intelligence Strategy was released in 2019 under the Trump administration, before the Covid-19 pandemic and Russia’s invasion of Ukraine.
“There’s so much that’s changed in the threat landscape, and in the world that we’re operating in today,” Director of National Intelligence Avril Haines said in an interview.
She sketched out a broader, more institutionalized information exchange on a wider array of topics with the private sector, ranging from academia to local governments.
Illustrating the changing threats, a senior U.S. official said that the daily intelligence briefing prepared for President Biden and his top advisers—once dominated by terrorism and the Middle East—now regularly covers topics as varied as China’s artificial-intelligence work, the geopolitical impacts of climate change, and semiconductor chips.
The new strategy is meant to guide 18 U.S. intelligence agencies with an annual budget of about $90 billion whose work Haines coordinates.
The 16-page document, which contains no budget or program details, also says spy agencies must support the U.S. in its competition with authoritarian governments such as China and Russia, particularly in technological arenas.
On transnational threats such as financial crises, narcotics trafficking, supply-chain disruption and infectious diseases, the document calls on intelligence agencies to strengthen their internal capabilities to warn U.S. policymakers of looming threats.
A report last year by the House Intelligence Committee, at the time led by Democratic Rep. Adam Schiff, concluded that three years after the Covid-19 pandemic began, U.S. intelligence agencies still hadn’t made the changes needed to provide better warnings of future global health crises.
Haines said that the intelligence community has strengthened its focus on global health. Her office, she said, now has a senior official whose responsibilities include coordinating intelligence work on global health issues, has invested more resources and has strengthened outreach to organizations such as the Centers for Disease Control and Prevention.
But the government, she said, also needs to rely on outside experts. Haines’ office brought in scientists and other specialists outside the government to help investigate the origins of the Covid pandemic and the health incidents affecting U.S. personnel abroad known as Havana Syndrome.
Such exchanges can be tricky. Many academics don’t want to be associated publicly with the intelligence community, said Haines, who has resisted efforts by Republican lawmakers to disclose the names of those consulted on the Covid question.
The emphasis on greater intelligence sharing is part of a broader trend toward declassification that the Biden administration has pursued. The United States has released unprecedented levels of formerly secret intelligence to warn of Russia’s plans in Ukraine and its quest for weapons from China, Iran and North Korea.
Updated: 10-13-2023
How Ads On Your Phone Can Aid Government Surveillance
Federal agencies buy bulk data, collected from ads you might never see, that can yield valuable information about you.
Technology embedded in our phones and computers to serve up ads can also end up serving government surveillance.
Information from mobile-phone apps and advertising networks paints a richly detailed portrait of the online activities of billions of devices. The logs and technical information generate valuable cybersecurity data that governments around the world are eager to obtain.
When combined with classified data in government hands, it can yield an even more detailed picture of an individual’s behaviors both online and in the real world.
A recent U.S. intelligence-community report said the data collected by consumer technologies expose sensitive information on everyone “in a way that far fewer Americans seem to understand, and even fewer of them can avoid.”
The Wall Street Journal identified a network of brokers and advertising exchanges whose data was flowing from apps to Defense Department and intelligence agencies through a company called Near Intelligence.
This graphic puts those specific examples in the context of how such commercially available information—bought, sold or captured by dozens of entities—can end up in the hands of intermediaries with ties to governments.
When you open an ad-supported app on your phone, your information is fed into a data stream that passes through many hands and has ended up in those of government agencies.
The moment before an app serves you an ad, thousands of advertisers compete for it to be their ad. While only one of the advertisers wins the spot, all the other advertisers in the bidding process are given access to information about your device.
Here’s an example of what that data looks like.
One of these apps collecting such data is Life 360, a family safety app, which generates a particularly rich set of information about the movement of devices. Until earlier this year, through brokers including Near Intelligence, some of that data ultimately ended up in the hands of government contractors.
A spokesman for Life360 said it has exited the data-brokerage business, adding that any sale of its data to government agencies violated its terms of service.
Mobile-phone information is collected by data brokers who are part of advertising exchanges and who repackage it for sale to their own customers. One such broker, Near Intelligence, had links to government contractors and used data from exchanges OpenX, Smaato and AdColony.
Those exchanges said they suspended data brokers who had violated their terms by collecting and reselling their data.
Additionally, some apps sell geolocation and other technical information about a device directly to data brokers. Mobfox and Tamoco, two brokers that sold such data to Near, didn’t respond to requests for comment.
Another broker, SafeGraph, no longer sells data on people, a company spokesman said.
Data brokers sell data to each other. The Journal was able to trace flows of ad data from the data providers and ad networks as named in the graphic to one such company, Near Intelligence, that sold it on to others.
Until earlier this year, Near had several clients that were government contractors, according to people familiar with the matter. Its clients’ national-security contracts began with UberMedia, a U.S. company Near bought in 2021, according to the people and documents.
These contractors and pass-through entities then provide the cyber data to the U.S. government, where it may be used for cybersecurity, counterterrorism, counterintelligence and public safety.
Near Intelligence, based in India with offices in the U.S. and France, was until earlier this year obtaining data from other brokers and advertising networks.
It had several contracts with government contractors that were then passing that data to U.S. intelligence agencies and military commands, according to people familiar with the matter and documents reviewed by the Journal.
Near was surreptitiously obtaining data from numerous advertising exchanges, the people said, and claimed to have data about more than a billion devices. When contacted by the Journal, several ad exchanges said they have cut Near off for violations of their terms of service.
The exchanges told the Journal that their data is meant to help target ads, not for other purposes.
Privacy, legal and compliance specialists inside Near warned the company’s leadership that it didn’t have permission to save real-time bidding data and resell it this way, especially in the wake of tough new European privacy standards that came into place in 2018, the people said.
Those specialists also warned the company that indirect sales to intelligence-community clients were a reputational risk. Near’s leadership didn’t act on those warnings, the people said.
In an email viewed by the Journal, Near’s general counsel and chief privacy officer, Jay Angelo, wrote to CEO Anil Mathews that the company was facing three privacy problems.
“We sell geolocation data for which we do not have consent to do so…we sell/share device ID data for which we do not have consent to do so [and] we sell data outside the EU for which we do not have consent to do so.”
In another message, Angelo called the transfer of European Union data a “massive illegal data dump,” adding that the U.S. federal government “gets our illegal EU data twice per day.”
A spokesman for Near didn’t respond to questions about the messages. The company last week told the Securities and Exchange Commission that Mathews and several other executives had been placed on administrative leave while the board investigates allegations of financial wrongdoing.
The spokesman didn’t say whether the matter was related to Near’s sale of ad-tech data to government contractors.
In a statement, Angelo said Near had over the past year “taken deliberate measures to safeguard privacy,” including ending customer relationships that were inconsistent with its values, which forbid Near’s data from being used for law enforcement, tracking or surveilling. Near didn’t make him available for an interview.
“We are continuously improving our systems for preventing misuse of our data by customers,” Near said in a statement.
Other brokers that compete with Near also have done robust business with government contractors, the Journal has previously reported.
Many Near staff were told that the agreements with government contractors were for “humanitarian purposes,” people said. Advertising exchanges it worked with told the Journal they had no knowledge of Near asking permission to license their data to a government entity, which wasn’t allowed under their agreements with the company.
In another instance, Near contracted with a government-linked client, nContext, that described itself as a digital-marketing company, highlighting commercial work on its website for clients such as a Philadelphia cultural center and New York City’s 92nd Street Y.
Corporate ownership records show nContext is a wholly owned subsidiary of defense contractor Sierra Nevada. Federal contracting records show that nContext is a subcontractor on several large intelligence and defense data contracts.
The Defense Counterintelligence Security Agency, part of the Defense Department, confirmed it signed a contract with Sierra Nevada in 2020 in an effort “to better analyze publicly available data and government information to identify cyber threats to cleared contractors.”
A pilot program the following year included ad data supplied by nContext but was discontinued, a spokeswoman said, adding: “DCSA did not collect any information that would identify people.”
Sierra Nevada and nContext didn’t respond to requests for comment. Another government contractor that was licensing Near’s data, Aelius, also didn’t respond to requests for comment.
The National Geospatial-Intelligence Agency, also part of the Defense Department, lawfully procured data and services from commercial vendors to support a “wide variety of missions” including foreign intelligence, humanitarian assistance and navigational safety, a spokeswoman said, and an Air Force spokeswoman said cyber and intelligence personnel use publicly available information “in an ethical and legal manner to understand an-ever changing data landscape that could be used by foreign malicious cyber actors to erode U.S. national security.”
The National Security Agency declined to comment. The Defense Department declined to comment on the contract with Joint Special Operations Command.
The U.S. has no comprehensive national privacy law, and therefore no outright prohibition on the collection and resale of such data to private- or public-sector entities.
While such contracts for commercially available information are generally unclassified and require no special authority, its use by U.S. agencies for national-security purposes was until recently a closely held secret.
The U.S. intelligence-community report, made public in June and produced by the Office of the Director of National Intelligence, said there is commercially available information “on nearly everyone that is of a type and level of sensitivity that historically could have been obtained” through targeted collection methods such as wiretaps, cyber espionage or physical surveillance.
Now ODNI is completing a framework to govern U.S. intelligence agencies’ use of such information, said spokeswoman Nicole de Haay.
“We will publicly share as much of this framework as possible,” she said.
Updated: 12-16-2023
AI Is Replacing 007 In The Espionage Arms Race
A conversation with Harvard’s Calder Walton about spies, lies and big data.
Folks who think about such things tend to look at the great espionage battle between the US and the Soviet Union as covering the four decades of the Cold War — the heady days of the Rosenbergs, the Wall, the Cuban Missiles and the owlish George Smiley.
But in truth, as Calder Walton reminds us in his remarkable new book Spies: The Epic Intelligence War Between East and West, a struggle that began after the Russian Revolution in 1917 is with us to this day.
Walton obsessively and entertainingly documents this century of the clandestine warfare, and reminds us that this contest didn’t waver during the brief enemy-of-my-enemy Alliance during World War II or in the immediate aftermath of the Soviet collapse, a period “Slow Horses” author Mick Herron memorably calls “the blissful break when the world seemed a safer place, between the end of the Cold War and about ten minutes later.”
Walton, a Brit who was born in the US, is the assistant director of the Harvard Belfer Center’s Applied History Project and Intelligence Project and a self-proclaimed “recovering barrister.” He is also quite fortunate:
While a graduate student at Cambridge University, he was selected to help research the official history of the British Security Service, or MI5.
We recently had a long discussion on how the lessons of that first Cold War can be applied (and misapplied) to the new one the US faces against China and its junior partner in Moscow. Below is a lightly edited transcript of the first part of that conversation. The second will follow in a future installment.
Tobin Harshaw: We of course need to talk about weighty geopolitical issues eventually, but let’s start with the fun stuff: How did you end up taking part in the official MI5 history?
Calder Walton: Right place, right time. My Ph.D. adviser at Cambridge University, Christopher Andrew, was selected as MI5’s authorized historian. And he said, hey, do you want to do some part-time research at the archives in MI5’s headquarters? It was too much of an opportunity to pass up.
TH: Indeed. What were those archives like? Or is it one of those “I could tell you but then I’d have to kill you” situations?
CW: If only! More Agatha Christie than 007, but it was certainly exciting. With British historic records, you open the file and it just tells the story of the person or the thing under investigation. For good and bad.
And it’s all meticulously a John le Carré-type affair: women typing up tapped telephone calls, bugged conversations, and so on.
And so the files invariably spill out compelling narratives of the people under investigation. Little wonder that some of the best espionage writers, like Graham Greene and le Carré, were British intelligence officers. They knew the land.
TH: How has the CIA done in comparison?
CW: The CIA is the world’s preeminent intelligence agency, but they’ve got some work to do in terms of releasing user-friendly dossiers. The declassified records on their website are difficult to use, and while you can find individual reports, they’re snippets; it’s not like with MI5, where you open a dossier, which tells a story.
TH: You write that even with its dwindling global influence and military since World War II, the UK has stayed in the geopolitical game because of the intelligence services. Is it just James Bond?
CW: Some of this is certainly explained by the James Bond effect — a first-class reputation — so the UK punches way above its weight. But I think it’s also down to genuine expertise, especially in areas like codebreaking. After all, the British essentially did the unthinkable in the Second World War.
TH: Bletchley and the Enigma machine.
CW: Right. And in the postwar years, the UK made itself indispensable to the US in terms of collection capabilities and decryption.
The US didn’t much like British colonialism, for obvious reasons, but Washington realized that having signals interception bases in Hong Kong, in Singapore, Cyprus, East Africa, in West Africa were incredibly useful in the context of the Cold War.
Britain’s declining empire became invaluable for the US.
The relationship was so intertwined that in the early 2000s, the UK’s signals intelligence agency, GCHQ, and the US National Security Agency acted as backup for each other. If NSA went down, a massive power cut or whatever, everything would just go over to GCHQ, and vice-versa. In the history of intel, there’s nothing else like that.
TH: So the whole le Carré thing about UK spies hating the “the cousins” at the CIA isn’t entirely true?
CW: The world of le Carré lies more with human intelligence, so MI6 rather than GCHQ. I was born in the US, and le Carré’s anti-Americanism does get tiresome pretty quickly. But yes, in reality there’s a love-hate, and that even shows up in the records. America’s got more resources, they’ve got more money. Begrudging respect and jealousy.
TH: I’ve heard from many people how high-quality British intelligence was in preparing for Russia’s invasion of Ukraine.
CW: That’s been borne out by a UK Parliamentary Intelligence Security Committee report published just a couple of days ago. In particular, GCHQ’s intelligence collection on Russian targets showed unambiguously that Putin’s buildup wasn’t a masking or just a show of force — that they actually meant what they were doing.
Do you remember the stories of Russian surgeons being brought toward the front line? This wouldn’t happen if it was just an exercise. And reading between the lines, GCHQ was all over that.
The British and the US worked together to declassify for the public intelligence on Putin’s war plans. This was not unprecedented — the US declassified intelligence during the Cuban Missile Crisis, for example. But on Ukraine, they did so in a striking way, in near-real time. It was a real game changer.
TH: Which brings us to open-source intel.
CW: Yes. What was available commercially gave the intelligence communities on both sides of the Atlantic the ability to say: We can get that information out without betraying our intelligence sources and methods.
TH: In the book, you say that during the Cold War, about 80% of US intelligence was derived from clandestine collection, and just 20% from open sources. But now it’s flipped to 80-20 the other way?
CW: Yes. There will continue to be a narrow but very deep margin of what intelligence communities can do in the traditional, clandestine, sense. A well-placed source in the Kremlin, in Beijing, etc.
But so much is now available through open sources that Western services are struggling to figure out what their role is in this changed world. Is it to try to do everything, or are they just going to be more conservative and concentrate on what open source cannot deliver?
Whatever happens, the age of a traditional secret service is over.
TH: Meanwhile, China’s hoovering everything up.
Collect, collect, collect. That’s their strategy. What they’re going to do with all of that is anyone’s guess. The intelligence struggle between China and the West is built around a race for machine learning, artificial intelligence, and quantum computing — it’s a race to process data.
Whoever masters AI will be able to master the data that’s been collected. And in the West, it will not be governments to do that. It will be the private sector. We’re thus at this watershed moment of redefining the nature of intelligence and national security. Intelligence communities are by necessity having to bridge gaps with the private sector. Quite how that will come out is anyone’s guess.
I’d be hugely in favor of the US intelligence community setting up a single open-source intelligence agency, and having it collaborate with all the clandestine agencies, rather than each individual agency trying to do open source itself.
TH: Is there a Cold War model for that?
CW: There is not. Although I argue in “Spies” that we are in a new Cold War, I think it’s important not to be shackled by the old Cold War, being stuck in the past.
That said, there are precedents for using open source effectively. The CIA’s Foreign Broadcast Information Service for example, which trawled through Soviet state media.
TH: That did really good work exposing Soviet propaganda efforts, like what the Kremlin made up about America cooking up AIDS in a lab. But now we didn’t respond nearly as well to the Covid misinformation that came out of China, for example.
CW: Looking at it from a historical perspective, it’s the same bloody conspiracy theory. The CCP is alleging that Covid was designed and let loose in the same lab in Maryland where the Soviets said AIDS was created. What’s old is new again.
TH: So why can’t we respond successfully today?
CW: First of all, it was a simpler time in the analog pre-digital era.
TH: Now we have social media.
CW: Exactly. Consider the mechanics of how Soviet intelligence spread disinformation: The story goes out in an obscure journal, a couple of months later it gets picked up more broadly — trickle, trickle, trickle — then some “useful idiots” in the West repackage it. It’s all very slow, and the Kremlin didn’t know whether a fabricated story was going to take off.
But now, obviously, everything travels at the speed of light. It’s easier, cheaper, quicker to spread disinformation than ever before. But it’s also more difficult for the authoring state to control the narrative. Once it’s out, where does it end up?
TH: In terms of open source and AI, you say we need to have public-private cooperation. But, as in the Cold War, I would imagine we need think tanks and universities as well.
CW: A bridge, yes.
TH: Whereas the Chinese are going to go about this the Chinese way, through centralized control. We like our model. We think it always wins in the end.
CW: That’s right.
TH: Should we have that much confidence today?
CW: Well, democracies have stood the test of time so far. Democracy is the least bad form of government compared to every other, to paraphrase Churchill. As for our model, do you mean our Western way of life, or just in terms of information warfare?
TH: Both. But in terms of us looking at national security in general, there’s a role for the federal government, there’s a role for universities, there’s a role for Silicon Valley today. It’s a collaborative Western-style effort as opposed to being a centralized one.
CW: Absolutely. I think we will prevail. I have full confidence in it. But we’ve got our work cut out for us.
Updated: 12-25-2023
China Is Stealing AI Secrets To Turbocharge Spying, U.S. Says
U.S. officials are worried about hacking and insider theft of AI secrets, which China has denied.
On a July day in 2018, Xiaolang Zhang headed to the San Jose, Calif., airport to board a flight to Beijing. He had passed the checkpoint at Terminal B when his journey was abruptly cut short by federal agents.
After a tipoff by Apple’s security team, the former Apple employee was arrested and charged with stealing trade secrets related to the company’s autonomous-driving program.
It was a skirmish in a continuing shadow war between the U.S. and China for supremacy in artificial intelligence. The two rivals are seeking any advantage to jump ahead in mastering a technology with the potential to reshape economies, geopolitics and war.
Artificial intelligence has been on the Federal Bureau of Investigation’s list of critical U.S. technologies to protect, just as China placed it on a list of technologies it wanted its scientists to achieve breakthroughs on by 2025. China’s AI capabilities are already believed to be formidable, but U.S. intelligence authorities have lately made new warnings beyond the threat of intellectual-property theft.
Instead of just stealing trade secrets, the FBI and other agencies believe China could use AI to gather and stockpile data on Americans at a scale that was never before possible.
China has been linked to a number of significant thefts of personal data over the years, and artificial intelligence could be used as an “amplifier” to support further hacking operations, FBI Director Christopher Wray said, speaking at a press conference in Silicon Valley earlier this year.
“Now they are working to use AI to improve their already-massive hacking operations using our own technology against us,” Wray said.
China has denied engaging in hacking into U.S. networks. Chinese Foreign Ministry spokesman Wang Wenbin said this summer that the U.S. was the “biggest hacking empire and global cyber thief” in the world, in response to allegations that Beijing had hacked into the unclassified email systems of several top-level Biden administration officials.
A spokesman at the Chinese Embassy in Washington didn’t respond to requests for comment.
In recent years, the FBI’s interest in protecting American innovations in the area has more squarely targeted manufacturers of chips powerful enough to process artificial-intelligence programs, rather than on artificial-intelligence companies themselves.
Even if insiders or hackers were able to steal algorithms underpinning an advanced system today, that system could be obsolete and overtaken by larger advancements by other engineers in six months, several former U.S. officials said.
In 2022, the chip-manufacturing technology supplier Applied Materials sued a China-owned rival, Mattson Technology, alleging that a former Applied engineer stole trade secrets from Applied before leaving for Mattson.
The case attracted the interest of federal prosecutors, although no criminal charges have been filed, according to people familiar with the matter.
Mattson hasn’t been contacted by any federal agency over the matter, and there is no evidence that any Applied information taken was ever used by Mattson, a company spokesman said.
Mattson, based in Fremont, Calif., was acquired in 2016 by an investment arm of the city of Beijing, which currently owns about 45% of the company, the spokesman said.
The case remains in litigation. In November, Mattson sued Applied, claiming that engineers at Applied had applied for patents using intellectual property developed while they were working at Mattson.
Fears of how China could use AI have grown so acute over the past year that the FBI director and leaders of other Western intelligence agencies met in October with technology leaders in the field to discuss the issue.
Makers of AI technology are concerned about their secrets making their way to China, too, according to executives at these companies.
Recently, OpenAI reached out to the FBI after a forensic investigation of a former employee’s laptop raised suspicions that the employee had taken company secrets to China, according to people familiar with the company. The employee was later exonerated, according to a person familiar with the matter.
U.S. intelligence analysts have worried for years about the long-tail espionage dividends that China is believed to be reaping from amassing enormous troves of hacked personal information belonging to American officials and business executives.
Over the past decade, Beijing has been linked to the hacks of hundreds of millions of customer records from Marriott International, the credit agency Equifax and the health insurer Anthem (now known as Elevance Health), among others, as well as more than 20 million personnel files on current and former U.S. government workers and their families from the Office of Personnel Management.
The heists were so huge and frequent that Hillary Clinton, then a Democratic presidential candidate, accused China of “trying to hack into everything that doesn’t move.” China has denied responsibility for each of those heists.
China was so good at stealing private information—billions of pieces of data in all, according to U.S. officials, criminal indictments and cyber-threat researchers—that its hackers had likely collected too much of a good thing: an informational treasure trove so vast that humans would be incapable of locating the right patterns.
Artificial intelligence, however, would have no such limitations.
Microsoft believes China is already using its AI capabilities to comb these vast data sets, said Brad Smith, the company’s president, in an interview with The Wall Street Journal.
“Initially the big question was did anyone, including the Chinese, have the capacity to use machine learning and fundamentally AI to federate these data sets and then use them for targeting,” he said. “In the last two years we’ve seen evidence that that, in fact, has happened.”
Smith cited the 2021 China-linked attack on tens of thousands of servers running Microsoft’s email software as an example. “We saw clear indications of very specific targeting,” he said.
“I think we should assume that AI will be used to continue to refine and improve targeting, among other things.” Smith didn’t address the issue of AI technology being stolen by China.
In the 2018 case, the former Apple employee Zhang pleaded guilty to stealing trade secrets and is set to be sentenced in February. His plea agreement is under seal. Apple declined to comment.
U.S. authorities believe Chinese intelligence operatives are correlating sensitive information across the databases they have stolen over the years from OPM, health insurers and banks—including fingerprints, foreign contacts, financial debts and personal medical records—to locate and track undercover U.S. spies and pinpoint officials with security clearances.
Passport information stolen in the Marriott hack could help spies monitor a government official’s travel, for example, counterintelligence analysts have said.
“China can harness AI to build a dossier on virtually every American, with details ranging from their health records to credit cards and from passport numbers to the names and addresses of their parents and children,” said Glenn Gerstell, a former general counsel at the National Security Agency.
“Take those dossiers and add a few hundred thousand hackers working for the Chinese government, and we’ve got a scary potential national security threat.”
Although executives including Smith are concerned by the weaponization of AI, they point out that this technology can be used to spot and mitigate attacks, too.
“We believe that if we do our work well and we’re determined to do our work well, we can use AI as a more potent defensive shield than it can be used as an offensive weapon,” Smith said. “And that’s what we need to do.”
Updated: 1-29-2024
There’s So Much Data Even Spies Are Struggling To Find Secrets
Scouring open-source intelligence may not have the same cachet as undercover work, but it’s become a new priority for the US intelligence agencies.
Spying used to be all about secrets. Increasingly, it’s about what’s hiding in plain sight.
A staggering amount of data, from Facebook posts and YouTube clips to location pings from mobile phones and car apps, sits in the open internet, available to anyone who looks. US intelligence agencies have struggled for years to tap into such data, which they refer to as open-source intelligence, or OSINT. But that’s starting to change.
In October the Office of the Director of National Intelligence, which oversees all the nation’s intelligence agencies, brought in longtime analyst and cyber expert Jason Barrett to help with the US intelligence community’s approach to OSINT.
His immediate task will be to help develop the intelligence community’s national OSINT strategy, which will focus on coordination, data acquisition and the development of tools to improve its approach to this type of intelligence work. ODNI expects to implement the plan in the coming months, according to a spokesperson.
Barrett’s appointment, which hasn’t previously been reported publicly, comes after more than a year of work on the strategy led by the Central Intelligence Agency, which has for years headed up the government’s efforts on OSINT.
The challenge with other forms of intelligence-gathering, such as electronic surveillance or human intelligence, can be secretly collecting enough information in the first place. With OSINT, the issue is sifting useful insights out of the unthinkable amount of information available digitally.
“Our greatest weakness in OSINT has been the vast scale of how much we collect,” says Randy Nixon, director of the CIA’s Open Source Enterprise division.
Nixon’s office has developed a tool similar to ChatGPT that uses artificial intelligence to sift the ever-growing flood of data. Now available to thousands of users within the federal government, the tool points analysts to the most important information and auto-summarizes content.
Government task forces have warned since the 1990s that the US was at risk of falling behind on OSINT. But the federal intelligence community has generally prioritized information it gathers itself, stymying progress.
“You build your career on the idea that you have to obtain information covertly,” says Senator Mark Warner, the Virginia Democrat who chairs the chamber’s Intelligence Committee. “It’s a mindset change to say, ‘OK, no, I think we can learn just as much from open-source information.’”
Failing to develop new capabilities for using open data could be costly and even dangerous, say US policymakers and intelligence experts. OSINT is especially important when it comes to gathering information about the Chinese government, whose political system is highly compartmentalized and difficult to penetrate with human agents.
Michael Morell, who served two stints as acting director of the CIA during the Obama administration, says identifying and making more open-source information available to analysts would significantly improve the performance of the US intelligence community.
The government is already working on OSINT. It used publicly available company records, procurement documents and satellite imagery to identify targets to sanction over alleged human rights abuses in Xinjiang, a territory in northwest China, according to a person familiar with the matter, who asked not to be identified discussing sensitive matters.
The Department of State’s Bureau of Intelligence and Research also used open-source methods to help identify the manufacturers of the Chinese spy balloon that traversed the continental US in early 2023, the person says.
By its nature, OSINT is also useful for groups beyond traditional intelligence agencies. In the months before Russia invaded Ukraine reporters and think tank analysts were able to verify claims of a Russian troop buildup using commercial satellite imagery, helping the Biden administration convince the American public that its warnings over Russia’s plans to invade Ukraine were credible.
Hamas has relied on television footage and social media posts to glean insights into the Israel Defense Forces’ weaponry, drills and training, according to a May 2023 study in the journal Intelligence and National Security.
Houthi rebels have used Google searches and commercial shipping data to pinpoint vessels to attack, according to a person familiar with the situation.
US officials say they believe China is supplementing its ability to track American naval operations by monitoring thousands of individual sailors’ social media accounts, according to another person. Both sources asked to remain anonymous to discuss sensitive issues.
Despite some progress, multiple senior US policymakers describe the community’s open-source efforts as insufficient. “I’d give the intelligence community a ‘D’ when it comes to its performance at open source,” says Ellen McCarthy, who was head of the State Department’s Bureau of Intelligence and Research from 2019 to 2021.
“At the State Department, I saw policymakers going more and more to the private sector to get what they needed.”
Part of the tradecraft of this kind of intelligence-gathering is doing it in such a way that targets of surveillance don’t realize what’s going on. If another government or organization realizes how the information it’s making public is contributing to US intelligence, they might find a way to stop oversharing.
The potentially invasive nature of the work unnerves civil liberties advocates. US Senator Ron Wyden, a Democrat from Oregon, in December temporarily blocked the nomination of the next director of the National Security Agency until the agency disclosed to him whether it buys Americans’ location and web-browsing data from commercial data brokers.
In a letter to Wyden, the NSA said it acquires various types of commercially available information, which may include “information associated with electronic devices” but doesn’t include location data for phones known to be used inside the country.
The government itself can be wary about some of the tools used to collect OSINT. At the CIA, for example, Russia analysts aren’t allowed to use their desktop computers to access the social media app Telegram, which is popular among Russian military bloggers.
The analysts are also barred from bringing personal devices into the workplace, forcing them to leave CIA premises when they want to access the app, according to people familiar with the situation, who requested anonymity to discuss CIA operations.
Coordination has also been a challenge. Different agencies gather data on their own, without necessarily sharing who’s collecting what or tagging data in a way that allows them to combine their work and to have people with various levels of security clearance gain access to it.
Rules regarding the collection and sharing of intelligence vary by agency, as does the definition of what even counts as OSINT. ODNI is set to issue revised definitions, as well as guidance on how it will treat commercially available information such as cellphone or web-browsing data.
(Bloomberg reported on Jan. 23 that the Biden administration is preparing an executive order to limit or prevent foreign adversaries from accessing personal data about Americans through legal means, such as purchasing it through data brokers.)
Power struggles within the intelligence community have also slowed progress on OSINT, critics say. “Everybody’s so focused on controlling it, there’s actually no one leading it,” says Eliot Jardines, who oversaw the Open Source Center within ODNI before it was absorbed into the CIA in 2015.
As it stands, various parts of the intelligence community are pursuing their own operations. The National Geospatial-Intelligence Agency, which analyzes imagery from spy satellites, started an open-source project called Tearline in 2017 that works with universities and nonprofits on projects such as tracking the expansion of China’s “Belt and Road” initiative.
Tearline’s creator, Chris Rasmussen, argues for a standalone OSINT agency that’s separate from the existing US intelligence community. He also wants OSINT reports to be delivered directly to policymakers’ phones every morning—akin to the president’s daily brief, but without classified information.
The potential of this kind of information won’t be truly realized until the process of gathering, analyzing and sharing OSINT is seen as something that stands on its own merits, he says, and “not just a supplement.”
Updated: 2-7-2024
Chinese Hackers Embedded In US Networks For At Least Five Years
The Chinese state-sponsored hacking group known as Volt Typhoon has been living in the networks of some critical industries for “at least five years,” according to a joint cybersecurity advisory issued by the US and its allies on Wednesday.
The compromised environments are in the continental US and elsewhere, including Guam, the advisory said. It was published by US agencies and their security counterparts in Australia, Canada, the UK and New Zealand.
The report comes a week after US officials announced an operation to disrupt Volt Typhoon by deleting malware from thousands of internet-connected devices the group had hijacked to gain access to the networks in critical parts of the economy.
Among the sectors targeted were communications, energy, transportation and water systems.
Addressing Congress last week, FBI Director Christopher Wray said China’s hackers were “positioning on American infrastructure in preparation to wreak havoc and cause real-world harm to American citizens and communities, if or when China decides the time has come to strike.”
Volt Typhoon uses techniques that have also been put into practice by Russian-affiliated hackers, the report noted. Those include “living off the land,” in which hackers put in place existing tools to stay under the radar.
Even for organizations adopting best practices, distinguishing malicious activity from legitimate behavior is a challenge, the report said. Details of the report were previously published by CNN.
Updated: 3-8-2024
U.S. Spy Agencies Know Your Secrets. They Bought Them
Commercial data brokers are providing the government with personal information that might otherwise require search warrants. Should that be allowed?
Last November, Michael Morell, a former deputy director of the Central Intelligence Agency, hinted at a big change in how the agency now operates. “The information that is available commercially would kind of knock your socks off,” Morell said in an appearance on the NatSecTech podcast.
“If we collected it using traditional intelligence methods, it would be top secret-sensitive. And you wouldn’t put it in a database, you’d keep it in a safe.”
In recent years, U.S. intelligence agencies, the military and even local police departments have gained access to enormous amounts of data through shadowy arrangements with brokers and aggregators.
Everything from basic biographical information to consumer preferences to precise hour-by-hour movements can be obtained by government agencies without a warrant.
Most of this data is first collected by commercial entities as part of doing business. Companies acquire consumer names and addresses to ship goods and sell services.
They acquire consumer preference data from loyalty programs, purchase history or online search queries. They get geolocation data when they build mobile apps or install roadside safety systems in cars.
But once consumers agree to share information with a corporation, they have no way to monitor what happens to it after it is collected. Many corporations have relationships with data brokers and sell or trade information about their customers.
And governments have come to realize that such corporate data not only offers a rich trove of valuable information but is available for sale in bulk.
Immigration and Customs Enforcement has used address data sold by utility companies to track down undocumented immigrants. The Secret Service has used geolocation data to fight credit card fraud, while the Drug Enforcement Administration has used it to try to find a kidnapping victim in Mexico.
A Department of Homeland Security document revealed that the agency used purchased location data from mobile phones to “identify specific stash houses, suspicious trucking firms in North Carolina, links to Native American Reservations in Arizona, connections in Mexico and Central America which were not known and possible [accomplices] and international links to MS- 13 gang homicides.”
And one government contractor, as part of a counterintelligence demonstration, used data from the gay-themed dating site Grindr to identify federal employees having sexual liaisons on the clock.
Whatever the U.S. can do with commercial data, foreign governments can do too. Last week, President Biden signed an executive order to prevent certain adversary countries, especially China and Russia, from buying bulk commercial data sets about Americans, including genetic information and personal movement information.
But the order didn’t address the issue of how the U.S. government itself uses commercial data to get around constitutional protections for civil liberties.
That issue is now before Congress as lawmakers consider reauthorizing a key surveillance law, prompting a debate over whether it’s appropriate for government and corporate power to become so intertwined.
In January 2022, a group of advisers convened by the U.S. Director of National Intelligence issued a report on the changing nature of intelligence.
The report, withheld from the public for nearly a year and a half, concluded that “Today, in a way that [few] Americans seem to understand, and even fewer of them can avoid,” governments can purchase “information on nearly everyone that is of a type and level of sensitivity that historically could have been obtained, if at all, only through targeted (and predicated) collection.”
Earlier generations of data brokers vacuumed up information from public records like driver’s licenses and marriage certificates. But today’s internet-enabled consumer technology makes it possible to acquire previously unimaginable kinds of data.
Phone apps scan the signal environment around your phone and report back, hourly, about the cell towers, wireless earbuds, Bluetooth speakers and Wi-Fi routers that it encounters.
The National Security Agency recently acknowledged buying internet browsing data from private brokers, and several sources have told me about programs allowing the U.S. to buy access to foreign cell phone networks.
Those arrangements are cloaked in secrecy, but the data would allow the U.S. to see who hundreds of millions of people around the world are calling.
Car companies, roadside assistance services and satellite radio companies also collect geolocation data and sell it to brokers, who then resell it to government entities. Even tires can be a vector for surveillance. That little computer readout on your car that tells you the tire pressure is 42 PSI?
It operates through a wireless signal from a tiny sensor, and government agencies and private companies have figured out how to use such signals to track people.
While it’s unclear how far that capability has penetrated into mass surveillance technology, one Utah company called Blyncsy has put up sensors that collect tire pressure identifiers—data meant to be used for anonymized traffic analysis by highway departments and transportation planners.
Blyncsy’s CEO Mark Pittman said in an email that the company has not sold its sensors to police or national security entities and has recently discontinued the product.
It’s legal for the government to use commercial data in intelligence programs because data brokers have either gotten the consent of consumers to collect their information or have stripped the data of any details that could be traced back to an individual. Much commercially available data doesn’t contain explicit personal information.
But the truth is that there are ways to identify people in nearly all anonymized data sets. If you can associate a phone, a computer or a car tire with a daily pattern of behavior or a residential address, it can usually be associated with an individual.
And while consumers have technically consented to the acquisition of their personal data by large corporations, most aren’t aware that their data is also flowing to the government, which disguises its purchases of data by working with contractors.
One giant defense contractor, Sierra Nevada, set up a marketing company called nContext which is acquiring huge amounts of advertising data from commercial providers. Sierra Nevada and nContext did not respond to a request for comment.
Big data brokers that have reams of consumer information, like LexisNexis and Thomson Reuters, market products to government entities, as do smaller niche players. Companies like Babel Street, Shadowdragon, Flashpoint and Cobwebs have sprung up to sell insights into what happens on social media or other web forums.
Location data brokers like Venntel and Safegraph have provided data on the movement of mobile phones.
“Government agencies rely on mobility and location analytics to properly allocate resources and inform critical decisions, including combating human and sex trafficking, identifying food or health deserts, improving infrastructure planning and informing natural disaster preparedness and response,” said Jason Sarfati, chief privacy officer of Venntel, in a statement.
“Agencies use this data within their approved scope of responsibility and in compliance with the laws under which they were formed.”
A group of U.S. lawmakers is trying to stop the government from buying commercial data without court authorization by inserting a provision to that effect in a spy law, FISA Section 702, that Congress needs to reauthorize by April 19.
The proposal would ban U.S. government agencies from buying data on Americans but would allow law-enforcement agencies and the intelligence community to continue buying data on foreigners.
The effort scrambles the usual partisan lines, with support from Republican firebrands like Jim Jordan of Ohio and Andy Biggs of Arizona, as well as liberal Democrats like Ron Wyden of Oregon and Pramila Jayapal of Washington.
But the Biden administration has been lobbying Capitol Hill against the provision. “I would not compare the way that our government uses data to the way that countries of concern are using data,” an administration official said last month on a conference call with reporters announcing Biden’s executive order.
In a bid to convince fellow Democrats to vote against the proposal, Rep. Jim Himes of Connecticut, the top Democrat on the House Intelligence Committee, said that the proposal to ban the purchase of data “would undermine some of the most fundamental and important activities of the intelligence community and law enforcement.”
House Speaker Mike Johnson, a Republican, pulled the reauthorization bill for the spy law from the floor in February over concerns from intelligence agencies and their allies in Congress, in part because of the proposed restrictions on using commercial data.
Many in the national security establishment think that it makes no sense to ban the government from acquiring data that everyone from the Chinese government to Home Depot can buy on the open market. The data is valuable—in some cases, so valuable that the government won’t even discuss what it’s buying.
“Picture getting a suspect’s phone, then in the extraction [of data] being able to see everyplace they’d been in the last 18 months plotted on a map you filter by date ranges,” wrote one Maryland state trooper in an email obtained under public records laws. “The success lies in the secrecy.”
For spies and police officers alike, it is better for people to remain in the dark about what happens to the data generated by their daily activities—because if it were widely known how much data is collected and who buys it, it wouldn’t be such a powerful tool.
Criminals might change their behavior. Foreign officials might realize they’re being surveilled. Consumers might be more reluctant to uncritically click “I accept” on the terms of service when downloading free apps.
And the American public might finally demand that, after decades of inaction, their lawmakers finally do something about unrestrained data collection.
Updated: 4-12-2024
House Passes Controversial Spying Bill As Speaker Johnson Overcomes GOP Objections
Measure extending foreign surveillance program for two years now heads to the Senate.
WASHINGTON—The House passed legislation Friday to renew a controversial national-security spying power, as House Speaker Mike Johnson (R., La.) overcame a last-minute intervention from former President Donald Trump and a down-to-the wire dispute over Americans’ privacy.
The bill extending the foreign surveillance program was approved 273-147, capping a bitter, yearlong fight in the chamber that had aligned some conservatives and progressives in seeking more privacy protections against congressional leadership and the Biden administration, which warned that deep changes to the law could put American lives in danger.
The legislation, which will expire next week unless renewed, now heads to the Senate, where it is expected to pass, and President Biden backs the measure.
It would renew Section 702 of the Foreign Intelligence Surveillance Act for just two years instead of the five sought by Johnson earlier in the week, a compromise designed to placate Trump and his allies.
Trump had urged members to “KILL FISA” in a social-media post Wednesday, and holdout Republicans then blocked the bill from proceeding, forcing leaders to scramble to rework the proposal.
The setback also underscored the precarious state of Johnson’s leadership in the House, where his party has a narrow 218-213 majority and Rep. Marjorie Taylor Greene (R., Ga.) is poised to try to oust him from the speakership.
Senior Biden administration officials say Section 702 is the most important surveillance tool at their disposal and is prodigious in generating intelligence used to thwart terror plots, fend off hackers and track spies.
But the law’s critics for years have viewed it skeptically and have raised particular issues with how it allows the collection of some Americans’ communications without a warrant, such as when they communicate with a foreign surveillance target.
While dozens of mostly minor changes geared at safeguarding privacy were included, an amendment to add a warrant requirement failed Friday in a nail biter of a vote, with 212 in favor and 212 against.
Members of both parties were riveted to the vote tally in the crowded chamber, with Republican conservatives cheering progressive Democrats, their allies on this matter, as they hurried to cast votes in favor in the final minutes.
The warrant requirement was opposed by the Biden administration and security hawks, who called it a poison pill.
Senior Biden officials, including national security adviser Jake Sullivan and Attorney General Merrick Garland, placed calls Friday morning to House members urging them to vote down the warrant amendment, according to people familiar with the matter.
“If this becomes law, we will be blind” to recruitment efforts in the U.S. by terror groups, said Rep. Mike Turner (R., Ohio), who vigorously opposed the warrant amendment. Turner is the chairman of the House Intelligence Committee and a key architect of the FISA package.
He let out a celebratory whoop when the warrant amendment failed, and pumped his fist.
Rep. Thomas Massie (R., Ky.), who supported the warrant amendment as critical to protecting Americans’ constitutional rights, laid the blame for its failure on Johnson, who was a crucial “no.”
“It was the deciding vote,” Massie said. “This would have been a good time for him to stay off the board, frankly.”
Judiciary Committee Chairman Jim Jordan (R., Ohio,), whose panel authored the provision, said: “It’s not complicated. If you want to spy on American citizens, you need to get a warrant.”
The bill’s backers touted the overall package as the most sweeping reform package to FISA since its creation in 1978.
Among other changes, the bill sharply reduces the amount of Federal Bureau of Investigation personnel who can conduct U.S. searches, creates criminal penalties for abuse, bars the FBI from searching the database solely for evidence of a crime rather than a national-security purpose, mandates more auditing of the program, and codifies other changes already internally adopted at the FBI.
Section 702 grants the National Security Agency broad authority to collect electronic communications from U.S. technology firms to hunt for national-security threats living overseas and share those intercepts with other intelligence agencies.
Though it targets foreign suspects believed to be on foreign soil, it sweeps up an unknown amount of communications belonging to Americans, such as when they text or call a foreigner who is under surveillance.
Skeptics say that arrangement amounts to backdoor searches of Americans who have repeatedly been improperly viewed by FBI analysts, including disclosures last year that the power was used to monitor George Floyd protesters, participants in the Jan. 6, 2021, riot at the U.S. Capitol, 19,000 donors to a congressional campaign, and a sitting U.S. senator.
Friday’s vote was a much-needed win for Johnson, who has struggled to navigate a way forward on other matters including Ukraine while presiding over a fractious and narrow Republican majority.
He had previously attempted three separate times to advance FISA legislation only to be forced back to the drawing board or punt, as he did in December when Congress passed an extension only for 3½ months.
The fourth time was a charm.
In shortening the renewal time frame, lawmakers appeared to be giving Trump the opportunity to seek further changes to the law should he be elected in November.
The former president has long nursed grievances against FISA and has erroneously suggested Section 702 has been used to spy on him and his campaign.
A different, more traditional part of FISA was used by the Federal Bureau of Investigation during its Russia investigation to obtain a wiretap on 2016 campaign staffer Carter Page, in a process the Justice Department inspector general later excoriated as riddled with mistakes.
“We wanted to give Trump an at-bat to tackle FISA,” said Rep. Matt Gaetz (R., Fla.), a critic of the law who pushed for a warrant requirement. “That was a principal objective.”
At a press conference late Friday with Johnson, Trump said he was “not a big fan of FISA” but credited the House with adding “a lot of checks and balances,” softening his rhetoric from earlier in the week.
He spoke approvingly of the two-year extension, noting the next deadline would fall within his next administration should he defeat Biden.
Former intelligence officials said Friday after the vote it may be even harder to defeat a warrant requirement in two years if Trump is elected in November to a second term.
Given Trump’s criticism of FISA, the two-year extension “seems like a threat to the authority’s unique value rather than a promise to reassess concerns in a meaningful way,” said Vanessa Le, a former intelligence community lawyer and Senate Intelligence Committee staffer who worked on FISA.
As president, Trump signed a renewal of Section 702 into law in 2018. His administration had unsuccessfully sought a permanent renewal of it from Congress, arguing that intelligence agencies needed stability for such a vital surveillance program.
Even if the Senate unexpectedly fails to pass the House’s bill, the spying program could continue for an additional year because of how and when the secretive court that oversees FISA grants annual approval for the categories of intelligence collection allowed under Section 702.
Those annual certifications were granted by the FISA Court earlier this month.
Such a scenario could invite a wave of lawsuits challenging the program, including potentially from U.S. technology companies who are compelled to cooperate.
In an April 5 letter to congressional leadership, senior Biden administration officials warned that those certifications weren’t a guarantee against disruptions to intelligence collection.
Amendments passed on Friday that expand the scope of spying allowed under Section 702 to include more leeway in targeting international narcotic trafficking operations and to allow the program to be tapped to vet foreigners entering the U.S. for possible terrorist ties. Civil libertarians generally opposed these measures.
Another amendment to codify a prohibition against a type of surveillance known as “about collection” also passed. The NSA halted in 2017 the once-secret practice, which allowed it to collect without a warrant the communications of Americans who mentioned—or talked about—a foreign intelligence target in their messages or phone calls.
“This legislation contains the most significant reforms to Section 702 ever,” said Rep. Jim Himes (D., Conn.), the top Democrat on the House Intelligence Committee and a key architect of the legislation, who opposed the warrant rule.
“This bill puts in place protections to make sure the abuses of the past do not continue into the future.”
Updated: 4-15-2024
Research For Sale: How Chinese Money Flows To American Universities
Contracts were valued at $2.32 billion between 2012 and 2024, amid concerns in Congress that the academic ties could pose a national-security risk.
Chinese companies are feeling a cold shoulder in the U.S.—except at universities, where they are welcomed as customers.
American universities sign contracts around the world to sell their research and training expertise, and some of their most lucrative agreements have been with companies based in China.
The decadeslong trade thrives despite a deepening U.S.-China rivalry and rising sensitivities about Beijing’s influence on American campuses.
Nearly 200 U.S. colleges and universities held contracts with Chinese businesses, valued at $2.32 billion, between 2012 and 2024, according to a review by The Wall Street Journal of disclosures made to the Education Department. The Journal tallied roughly 2,900 contracts.
The extensive trade in American expertise presents a quandary for universities and policymakers in Washington: Where’s the line between fostering academic research and empowering a U.S. rival?
“It seems clear that when the Chinese contract with U.S. universities they are getting a capability they can’t get anywhere else,” said Daniel Currell, a Trump administration Education Department official who has tracked foreign influence in higher education.
“The big question is, what [contracts] should be legal, what should be legal and disclosable, and what should be illegal?” he added.
In some cases, an American university whose identity is tied to a bedrock local industry—think cars and the University of Michigan, or the University of Florida and citrus—does research on behalf of a Chinese challenger in that same sector.
All three of China’s major government-owned oil companies have funded contracts for $100,000 or more at the University of Texas at Austin, which the school describes only as “research activity.”
U.S. universities earn money from virtually every nation in the form of tuition, gifts and contracts. In the Journal analysis, Qatar provided more non-tuition money into U.S. universities than any other country, followed by the U.K., Germany and China.
Gifts draw more publicity because they are often large-dollar amounts from individuals that confer, say, naming rights for new buildings. But overall, the contract world involves far more money.
The Journal found that the aggregate value of university contracts attributed to China over roughly the past decade was 2.5 times reported Chinese donations, in line with the flows from other countries.
China remains the largest source of foreign students on American campuses and their spending, including tuition, is a far bigger share of most university budgets than contracts and gifts.
Universities are required to report any foreign gift or contract worth $250,000 or more to the Education Department, though the rule historically wasn’t vigorously enforced and the agency has alleged billions have gone unreported. Journal reporting also found instances of double-counting and other data errors.
Calls are growing on Capitol Hill to vet Chinese contracts with U.S. schools for national-security risks.
Aiding U.S Rivals
The Journal made public-records requests to major public universities in all 50 states for details of their contracts with entities in China.
The disclosures reveal how contracts cut across industries where Beijing has subsidized and otherwise supported Chinese enterprises, from medicine and agriculture to manufacturing and even the arts.
Schools say the practice of matching Chinese funding with American expertise often serves the public good, like developing new cancer treatments. Yet, to critics, the Communist Party’s control over China’s business sector can taint even those pursuits.
That’s the conundrum facing the U.S. universities that have entered contracts with Shanghai-based WuXi AppTec. Known in China as the Huawei Technologies of pharma, AppTec is a biotech conglomerate globally recognized for medical breakthroughs and manufacturing therapies approved by the Food and Drug Administration.
But like Huawei, China’s now-blacklisted maker of advanced telecommunications gear, it is now dogged by concerns in Washington its innovations could be abused by Beijing.
Both AppTec and Huawei have had contracts with U.S. universities, the Journal found. The companies say they are private enterprises and reject suggestions they take directions from China’s government or pose national-security risks to the U.S.
The University of Arizona valued three AppTec contracts it reported for 2022 collectively around $1.5 million.
Among them is an agreement in which a services arm of AppTec, on behalf of another Chinese drugmaker, agreed to pay the university’s hospital $36,977 for each subject enrolled in trials of a drug designed to treat tumors.
The medicine has FDA approval for treatment during the trial of certain rare cancers.
Now, out of concern Beijing could harness commercial biological discoveries for military purposes, members of Congress want the government to classify AppTec an “adversary biotech company of concern,” which would make it virtually untouchable as a partner for U.S. organizations that get federal dollars, including many hospitals and universities.
“WuXi AppTec and [its sister company] WuXi Biologics are rapidly becoming a global pharmaceutical and research-services giant that threatens U.S. intellectual property and national security,” read a February letter signed by four members of a House committee on China to U.S. government agencies requesting the new classification.
AppTec said the legislative effort targeting it is “misguided” and “without a fair and transparent review of the facts.” Arizona spokeswoman Pam Scott said by email, “We have not been notified of any security concerns.”
Calling CFIUS
In early 2018, the University of Washington announced that it would create one of the world’s first academic centers dedicated to virtual and augmented reality. The university credited the center’s $6 million funding equally to Facebook, Google and Huawei.
After the Trump White House made it illegal for Americans to do many types of business with Huawei in May 2019, the university announced that federal regulations meant it could no longer enter into transactions with the Chinese company.
The school reported over $5.5 million from Huawei across the years 2018, 2019 and 2021, and a spokesman said the latter entry represented a final payment in a contract that began before 2019.
A Huawei logo appears in a welcome video on the homepage of the university’s Reality Lab, which the spokesman said is an “accurate and transparent” acknowledgement of Huawei’s founding participation in the lab.
Huawei didn’t respond to questions about its contracts at U.S. universities, including Washington.
“There has not until recently been much concern about what’s going on at universities,” said Aaron Friedberg, a U.S.-China Economic and Security Review Commission member.
The commission, which advises Congress, now urges legislation to treat Chinese contracts with universities like foreign-funded acquisitions, subject to national-security screening through an interagency panel known as the Committee on Foreign Investment in the United States, or Cfius.
The concern, Friedberg said, is that contracts represent “just one of the many avenues of access into our R&D technology establishment.”
Pilot Program
A number of contracts identified by the Journal provided China with specialized training it lacks.
For instance, China has few small planes or public airstrips needed for pilot training, so for over a decade major Chinese airlines such as Air China paid the University of North Dakota millions annually to get their recruits licensed to fly.
Between October 2018 and July 2022 alone, North Dakota records detail contracts worth over $37 million from four Chinese carriers.
Student pilots at North Dakota’s aerospace academy racked up their required 250 flight training hours from airstrips a few miles from Grand Forks Air Force Base, a control center for military drones and satellites.
North Dakota declined to discuss its work with China’s airlines, though university publications have said some 30% of Air China pilots trained there and that their presence was a financial shot in the arm for the capital-intensive aerospace school. The Chinese airlines didn’t respond to questions.
Among foreign funders of U.S. schools, China raises particular complications, says Ian Oxnevad, a senior fellow at the National Association of Scholars, who argues U.S. universities don’t need China’s money and should be alert that its military can make use of seemingly civilian commercial applications.
“There’s an ethical imperative to research,” he said.
For years, a prominent type of university contract involved Chinese-language training on U.S. campuses under the rubric Confucius Institutes, such as the around-$540,000 reported by the University of Oklahoma for 2019.
After evidence piled up of the Beijing-funded institutes’ close ties to China’s diplomatic missions, most closed, including Oklahoma’s.
Some of the biggest-value China contracts feature franchise-type arrangements for overseas satellite campuses. New York University, which the Education Department database shows has been the largest single recipient of Chinese funding, reported two contracts totalling over $46.5 million for 2021 alone for its Shanghai branch.
The Juilliard School has disclosed over $133 million in such funding over more than a decade for its Tianjin Juilliard School near Beijing, appointed with some 120 Steinway pianos.
Motor City
Successive American administrations have accused the Chinese Communist Party of treating U.S. campuses as beachheads to further its agenda. The Federal Bureau of Investigation and other agencies warn that China’s state has encouraged theft of technological secrets at universities, spread pro-Beijing propaganda, stifled campus debate and harassed students.
Beijing dismisses such characterizations. Its officials say ethnic Chinese students and professors have been unfairly targeted in the U.S., including on American campuses, and urged the U.S. to be mindful of its reputation for academic freedom.
The Chinese Embassy in Washington didn’t respond to detailed questions about the university contracts.
In the shadow of Detroit’s auto industry, the University of Michigan said it has had around $1 million in contracts from DiDi Global, a Chinese ride-sharing company built on government money that forced Uber out of the market.
The university said DiDi funding supported a range of engineering research, from evaluating devices for monitoring a driver’s health and operational safety to using a vehicle fleet to track air pollution, including eight peer-reviewed scientific papers that made the findings public.
One study, based on a year’s worth of data from DiDi, examined how empty cabs affect overall traffic.
“International engagement is a foundational element of successful research,” university spokesman Rick Fitzgerald said in a statement.
Among the arrangements disclosed by the University of Minnesota to the Journal, a pair of small Chinese equipment makers have paid $50,000 annually for membership in its Center for Filtration Research alongside industry titans such as 3M and Boeing.
When one of the Chinese members, Guangxi Watyuan Filtration System, launched an initial public offering, it told investors the Minnesota connection allowed it to “enjoy the latest achievements of world-class R&D institutions in the filter industry.”
Minnesota, like many schools, said any research generated from a Chinese contract is made public.
Orange Pickle
Florida oranges long ago got squeezed out of the Chinese market by aggressive Chinese growers and protectionist policies such as a 56% import tariff. Yet China does have a taste for Florida’s orange know-how.
Anxious about a tree infection called greening that makes fruit taste acidic, scientists in China turned to the University of Florida, which has researched citrus diseases for more than a century.
A disclosure from the school showed that contracts worth about $1.8 million with China’s Institute of Navel Orange at Gannan Normal University supported work by a Florida authority on tree genetics who has made advances against citrus diseases, Nian Wang.
University spokeswoman Chris Vivian said the contracts reflect the university’s responsibilities to the agricultural community.
The university’s work studies wild citrus germplasms in China that are resistant and tolerant of greening, and local collaboration is necessary because under Chinese law that material can’t be shipped overseas, she said.
Wang declined to comment. Emails to several people at China’s orange institute went unanswered.
Florida orange grower Dan Richey, president of Vero Beach, Fla.-based Riverfront Packing, stresses that the global citrus industry is desperate for a greening cure, but also says the university’s deal smacks of a potential Chinese “intellectual-property grab.”
Almost 25 years ago, Richey toted a crate of Florida oranges to Beijing amid hopes its market would open up to U.S. growers, only to see the opportunity fizzle. He says he remains distrustful of Chinese intentions.
Future Florida-China collaborations are now in doubt after Gov. Ron DeSantis last year signed a law that could bar state-funded universities from entering contracts with partners from China, Russia, Iran and four other nations.
The governor’s office said he aimed “to root out Chinese influence in Florida’s education system.” The university declined to comment on the law or address its impact on the orange research.
Updated: 4-22-2024
Three Suspected Spies For China Detained In Germany
Dismantling of alleged military-technology spy cell comes as Berlin seeks to re-engage with Beijing.
Germany has detained three people suspected of spying for China on sensitive military technology, underlining the limits of Berlin’s efforts to re-engage with Beijing to boost its stagnating economy.
Germany’s General Federal Prosecutor’s Office said the two men and one woman, all German nationals, had obtained valuable information and dual-use hardware on behalf of the Ministry of State Security, the Chinese intelligence agency, since at least June 2022 and transferred it to China.
The suspected cell was led by a man identified as Thomas R., who was in direct contact with an MSS handler in China, the prosecutors said. The other suspects, a married couple identified as Ina F. and Herwig F., helped obtain the information and equipment using a Düsseldorf-based company they managed.
The suspects’ lawyers couldn’t immediately be reached for comment. China’s Foreign Ministry didn’t immediately respond to a request for comment.
The announcement of the arrests comes days after German Chancellor Olaf Scholz, flanked by a large business delegation, returned from a three-day tour of China aimed at re-engaging with Chinese leader Xi Jinping and bolstering trade between the two countries.
Germany, China’s largest trade partner in Europe, adopted a more skeptical stance toward China shortly after Scholz’s 2021 election. The country’s first China strategy document, unveiled last year, described Beijing as a partner, competitor and systemic rival and urged German businesses to reduce their dependence on China.
In recent months, however, Berlin has softened its stance in an effort to support its ailing export-oriented economy, persuade Beijing to lean on Moscow to end its war in Ukraine, and offset potential new U.S. import tariffs should Donald Trump be re-elected president in November, according to German officials.
Scholz’s visit to China last week was his third meeting with Xi in as many years.
Prosecutors said Ina F. and Herwig F., under instructions from Thomas R., had signed a cooperation agreement with a German university commissioning a study on the current state of machine parts that, among other applications, can be used in the production of powerful engines for military ships.
The study was commissioned on behalf of a Chinese contract partner that acted as a front for the MSS agent, and it was paid by the Chinese state, the prosecutors said.
Shortly before being detained, the three suspects were negotiating a new research project that could have been of use to China’s navy buildup, the prosecutors said.
In addition, the suspects are alleged to have acquired a special laser and shipped it to China without the required authorization, the prosecutors said, citing an investigation by Germany’s domestic intelligence agency. The funds to buy the dual-use laser were provided by the MSS, they added.
As an engineering powerhouse and the world’s fifth-largest weapons exporter, according to the Stockholm International Peace Research Institute, Germany has been a target of espionage, especially of the industrial kind, by the likes of Russia, Iran, China and others.
Yet the arrest of spies associated with China has been relatively rare and Beijing’s interest was until recently thought to be focused on the acquisition of commercial secrets, such as the equipment and know-how needed for the manufacture of high-end semiconductors.
China has a history of tapping Western research institutions for expertise useful to its military buildup without necessarily resorting to espionage, said Mareike Ohlberg, senior fellow at the Indo-Pacific program of the German Marshall Fund in Berlin.
The German case suggests heightened Western vigilance is making it harder to do this openly, she said.
“There was a real surge in awareness among research institutions after the Russian invasion of Ukraine,” she said, adding that universities, in particular, had become more careful in vetting the Chinese partners they work with for potential links with the Chinese military.
Germany has detained a string of suspected Russia spies in recent years, including an alleged cell that prosecutors said last week was planning to sabotage U.S. and German military installations in Germany.
Separately, in the U.K., the Crown Prosecution Service said it had authorized police to charge two men identified as Christopher Berry, 32, and Christopher Cash, 29, with spying for China.
Cash had worked as a parliamentary researcher and was a member of the China Research Group, founded by Conservative lawmakers wary of Beijing’s growing influence.
Neither of the men could be reached for comment. Lawyers who have previously represented Cash didn’t immediately comment.
Both men are accused of breaking the Official Secrets Act by obtaining notes, documents or information which were calculated or intended to be, directly or indirectly, useful to the enemy.
Berry is alleged to have done so between the end of December 2021 and early February last year, while the allegations against Cash relate to the year beginning Jan. 20, 2022.
Nick Price, head of the CPS special crime and counter terrorism division, said the two men would be charged with providing prejudicial information to a foreign state and were set to appear in court Friday.
In a statement released by his lawyer in September, Cash denied he was a spy and said he was “completely innocent.”
Successive U.K. spy chiefs have warned that China’s spy apparatus presents a U.K. national security threat and is more effective than Russia’s by orders of magnitude.
The head of MI5, Britain’s domestic-intelligence security operation, has warned companies that China is routinely stealing their intellectual property. A government foreign-policy paper released last year defines China as “an epoch-defining challenge” to the international order.
The China Research Group, of which Cash was a member, was founded in 2020 by Conservative Party members of Parliament concerned about Beijing’s influence on British politics. The Chinese government in 2021 banned some members of the group from entering China, saying they spread lies about the country.
Updated: 5-8-2024
U.K. Expels Russian Diplomat It Says Is A Spy
Move to kick out defense attaché is latest spat in broader spying cold war that pits Europe against Russia.
LONDON—The U.K. government Wednesday launched its latest salvo against Russia’s intelligence service, expelling the serving Russian defense attaché on allegations of spying and removing diplomatic protection from several Russian government-owned properties that it said were being used for intelligence gathering.
The move is a retaliation against what the U.K. government called a “pattern of malign activity” by Russia in the past year, including allegedly orchestrating an arson attack on a Ukrainian-linked business in east London and hiring six U.K.-based Bulgarians as part of an alleged Kremlin plot to abduct individuals.
“Since the illegal invasion of Ukraine, Russia’s attempts to undermine U.K. and European security have become increasingly brazen,” said Foreign Secretary David Cameron.
The expulsion and public shaming are the latest chapter in a new cold war between most of Europe and Russia following the Ukraine invasion, amid fears that Russia is expanding its attempts to choke off support for Ukraine.
NATO recently said it was “deeply concerned” by Russian hostile state activity in countries including Estonia, Germany, Latvia, Lithuania and Poland.
These hybrid campaigns included sabotage, acts of violence, cyberattacks and disinformation, the security alliance said last week.
Weeks earlier, Germany detained two dual German-Russian nationals on suspicion of gathering evidence on industrial and military installations.
Part of the measures the U.K. announced on Wednesday include imposing new restrictions on Russian diplomatic visas, capping the length of time Russian diplomats can spend in Britain. U.K. officials didn’t give details as to what the time limit would be.
The government also stripped diplomatic protection from several Russian properties in the U.K., arguing they were being used for spying.
Among the properties is Seacox Heath, a mansion in Sussex owned by the Russian government and used as a weekend retreat by diplomatic staff.
Buildings that are deemed diplomatic premises cannot normally be searched by police without the permission of the country’s ambassador. Those buildings no longer have that protection, the government said.
The war in Ukraine had already decimated the Russian diplomatic spy corps. After the invasion, more than 400 Russian intelligence officers operating under diplomatic cover were expelled across Europe, according to an assessment by MI6 chief Richard Moore in 2022.
He estimated the expulsions had cut Russia’s ability to spy in Europe by about half.
Britain in particular took a hard line on Russian diplomats, ejecting over 20 after it accused the Kremlin of poisoning a former spy on U.K. soil in 2018. Russia responded by ejecting a similar number of British diplomats.
Britain has since then rejected around 100 diplomatic visas to Russia to stop it rebuilding its spy ranks. Following the latest expulsion, U.K. officials expect a tit-for-tat response from Russia.
Despite the expulsions, Russia has continued to allegedly cause trouble, often hiring foreign proxies to undertake work on the intelligence service’s behalf.
Last week, a British man who allegedly conducted the arson attack on the Ukrainian-linked business in London was charged under U.K. national-security laws with being a Russian operative.
There is also a continuing court case against six Bulgarians who were allegedly hired by Russia to collect information “intended to be directly or indirectly useful to an enemy” between 2020 and 2023.
The spy cell was allegedly run by Jan Marsalek, a former fintech executive wanted in Germany for a 1.9 billion euro fraud who fled to Russia.
Recently, the Russian government said it summoned British Ambassador Nigel Casey after Cameron said Ukraine “has the right” to launch attacks inside Russia with British-made weapons.
Britain’s response to the Russian covert activity has been to name and shame in the hope it can deter the Kremlin. Late last year the U.K. said Russia was behind a global hacking campaign over the past eight years that targeted British lawmakers, journalists and civil society organizations.
These included targeting U.K. parliamentarians through spear-phishing attacks—emails designed to extract sensitive information—and leaking confidential U.K.-U.S. trade documents in 2019.
Updated: 5-13-2024
U.K. Charges Three With Spying Linked To Hong Kong
British authorities continue effort to crack down on Chinese intelligence gathering.
LONDON—U.K. police charged three men on Monday, including a U.K. Border Force official and a former Royal Marines commando, with allegedly helping Hong Kong’s intelligence services spy on dissidents based in Britain.
The prosecution is one of the most high-profile efforts by British authorities to curtail alleged Chinese spying on U.K. soil, with a trial that is expected to shine a light on the lengths the Chinese state goes to pursue members of its diaspora.
Chi Leung Wai, 38 years old, Matthew Trickett, 37, and Chung Biu Yuen, 63, appeared in a London court wearing gray prison-issued clothing after being arrested this month under the U.K.’s National Security Act for allegedly assisting a foreign intelligence service.
The charges include aiding a hostile state and forcing entry into a U.K. address. The men confirmed their names and ages but didn’t enter pleas.
The Chinese Embassy denounced the charges as a “malicious fabrication.”
Western governments have become increasingly concerned about Beijing’s sprawling attempts to gather intelligence, including by hacking and spying. Germany arrested four people last month, including a far-right politician’s parliamentary assistant, on suspicion of spying for China.
A British parliamentary researcher was arrested last year and formally charged in April with spying for China and is due to face trial next year. In January, Beijing said it had arrested an alleged British spy.
Yuen is a retired Hong Kong police officer who is listed as an office manager at the Hong Kong Economic Trade Office in London, a government agency that promotes overseas investment in the former British colony.
Wai works at Heathrow Airport for the U.K. Border Force, which oversees immigration and customs controls, and is listed online as the founder of a consulting firm called D5 Security. Trickett, a British national, advertises himself on LinkedIn as a security specialist who previously served as a Royal Marines Commando.
The three were released on bail ahead of another court hearing later this month. British counterterrorism police said seven more men and one woman were detained but then released without charges. Most were detained in Yorkshire, in northern England.
British officials have previously warned that the Chinese state was keeping tabs on the large number of Hongkongers who had fled to the U.K. following the Chinese imposition of a security law in 2020 aimed at stifling mass protests that had swept Hong Kong.
The security law permitted China’s state security apparatus to operate openly in the city after years of doing so covertly.
The British government said the security law violated Hong Kong’s judicial independence from Beijing—which was supposed to last until 2047 as part of the British handover and withdrawal of the last British governor in 1997.
In response, the U.K. opened a special five-year visa route to allow up to 4 million Hong Kongers to enter the country. So far over 150,000 people have come over to live in the U.K. on those visas, according to the U.K. Home Office.
After the security law was implemented, the Hong Kong police set up a national security department that former officials said would likely be similar to the so-called Special Branch, the unit of the police force during British rule tasked with collecting intelligence and monitoring perceived threats of subversion.
Much of the operations of the national security department have been secret, but it has publicly targeted activists outside of Hong Kong in addition to people in the city.
Last year the department announced rewards of 1 million Hong Kong dollars, equivalent to about $128,000, for help in capturing 13 activists overseas, more than double the bounties offered for alleged murderers.
Those bounties stirred criticism from countries where the activists now live, including the U.K., U.S. and Australia. The activists targeted in the U.K. included Simon Cheng, a former employee of the British Consulate in Hong Kong, and Mung Siu-tat, a former union official.
Police in Hong Kong arrested people accused of raising money to help suspects overseas wanted for alleged national security violations.
The U.K. Parliament’s intelligence committee has previously warned about “Operation Fox Hunt,” in which the Chinese government forces the repatriation of opposition figures living abroad. According to a recent report by the U.K. Parliament’s Intelligence and Security Committee, China is known to have “conducted coerced repatriations of economic fugitives from the U.K. and kidnapping of dual nationals overseas.”
Updated: 5-15-20-24
The Misfits Russia Is Recruiting To Spy On The West
Young people hired in Poland, seeing chance for ’easy money,’ take part in Russian sabotage in Europe.
WARSAW—Low on cash and out of his most recent minimum-wage job, Ukrainian refugee Maxim Leha, then 22, had just found a new way to make ends meet in his newly adopted home of Poland.
The job advertised on the Telegram messaging app in early 2023 didn’t appear to demand much: Spray-paint graffiti on remote fences and highway underpasses for $7 a pop. When Leha answered, a man who identified himself as Andrzej wrote back.
Within days, Andrzej had upped the ante: Leha was fixing cameras along railroad lines carrying Western military aid to neighboring Ukraine.
Weeks later, Leha and 15 others were arrested in the biggest publicized spy case in Poland’s history. Andrzej, it turned out, was a front for a Russian intelligence unit that was recruiting people such as Leha—drifters looking to make a quick buck—for spying and espionage jobs since late 2022.
Late last year, Leha received a six-year sentence on espionage charges, after a trial in which he was painted as a ringleader.
“It was easy money,” Leha recently said from a jail in the Polish city of Lublin, his lanky frame under the red jumpsuit given to detainees considered most dangerous.
It is unclear whether the information provided by Leha and the other recruits directly led to Russian strikes on the shipments of Western weapons that have regularly transited into Ukraine since Russia’s February 2022 invasion.
But Western officials say Russia has successfully combined camera footage with more sophisticated efforts such as satellite surveillance to trace shipments of hardware and ammunition from Poland and elsewhere to secret warehouses in Ukraine, where they have been hit by drones and guided missiles.
“These cheap and seemingly bumbling efforts are nothing to be sneered at,” a senior Western military intelligence official said. “They are part of a large toolbox of intelligence gathering that has helped Russia destroy key materiel with minimum investment.”
A Low-Risk Strategy
The case of the Polish spy ring opens a window onto Moscow’s renewed efforts to boost its espionage capabilities in Europe as the Kremlin is settling into a long confrontation with the West. Part of their network was hit when more than 600 Russian diplomats were expelled in the wake of the 2022 invasion.
The U.K. has said that two thirds of those expelled from Europe were likely spies.
Now Russia is using chat platforms such as Telegram to recruit young, marginalized people, often immigrants and mostly men, to undertake mundane yet damaging acts of spying and sabotage.
The approach—low-cost and low-risk for Moscow’s spy services—allows Russia to stoke anti-Western sentiment and reap potentially important intelligence while letting their recruits take the fall.
“Now they are trying to reconstruct their capabilities,” said Jacek Dobrzynski, spokesman for Poland’s special services coordination.
Recent weeks have seen a spate of similar spy cases. The North Atlantic Treaty Organization this month called out “an intensifying campaign of activities which Russia continues to carry out across the Euro-Atlantic area.”
British police arrested five men in April for burning down a warehouse connected with Ukraine and helping Russia identify other possible sabotage targets. That followed the arrest last year of Bulgarian spies allegedly surveilling U.K. military installations.
A few weeks ago, authorities in Germany arrested two German-Russian nationals accused of passing on photographs and videos of military infrastructure.
Western security officials suspect Russia is responsible for the destruction of undersea internet cables and natural-gas pipelines, attacks on railroads and plans to strike military compounds.
The Kremlin denied it was behind the incidents.
“We constantly hear unfounded and unsubstantiated accusations against us,” said Kremlin spokesman Dmitry Peskov. “We reject them.”
A New Recruit
This account of the Polish case, assembled from hundreds of pages of documents from the investigation and an interview with Leha, offers a rare window into Russia’s new campaign.
Leha crossed the border into Poland in late 2021, five months before the Russian invasion. He found work as a supermarket cashier, but soon looked for easier ways of making quick cash.
After a short stint driving undocumented migrants through Hungary, a job he found on Telegram that earned him three months in a Hungarian jail, he came across Andrzej’s ad.
Leha said he suspected he was part of a Russian intelligence effort. But he had a rudimentary education and a growing criminal record, and the cash helped him ignore qualms about betraying his homeland.
Andrzej paid Leha to spray slogans such as “Stop NATO” hundreds of times. After each job, Andrzej paid him in bitcoin or Ethereum.
Soon Andrzej had a bigger job: Start a fire near a Ukrainian transport company in Poland’s eastern city of Biala Podlaska. But when Leha arrived at the site, he recalled his father’s advice not to “build his happiness on someone else’s misfortune.”
Instead, he rubbed charcoal on the fence to make it appear damaged by fire, took a photo and sent it to Andrzej.
As the requests piled up, Andrzej promised Leha a car and transferred several hundred dollars in cryptocurrency that Leha used to buy a Mazda 6 GG.
Andrzej remained a cipher. He spoke with Leha in both Russian and Ukrainian, but Leha assumed he was Ukrainian from his colloquial use of the language. During phone calls, Leha gleaned that Andrzej was two hours ahead of Poland, placing him in the Moscow time zone.
When Leha said he wanted to meet and asked what he looked like, Andrzej shot back: “Like your new car.”
When he asked if he was helping the Russians, Andrzej replied, “It’s a Polish thing.”
“And what is it in reality?” Leha responded.
“It is an international thing,” he wrote back. “The goal is to show that people are bored with this war and cause a major resonance within the society.”
Watching The Trains
Meanwhile, Andrzej was recruiting other young immigrants in Poland.
One was Maxim Sergeyev, a 20-year-old who had come from a town from outside Moscow to play hockey for the local Zaglebie Sosnowiec hockey team. People who knew him said he had learned almost flawless Polish and had befriended most of the team since he arrived in 2021.
When Russia invaded Ukraine the next year, he signed a statement disavowing the war.
Like many young hockey players in Poland, Sergeyev was chronically short of cash. A job as a food courier ended in a bike accident.
When he was arrested several months later, police found a group chat with Andrzej and dozens of pictures and videos on his cellphone of two major Warsaw train stations, cities in eastern Poland and the Malhowice-Nizankowice border crossing.
Andrzej also recruited a female student from Belarus and a teen from Ukraine. Another member of the ring, Oleksii Pronkin, a young Ukrainian, was tasked with collecting photos of the Polish Naval Academy in the coastal city of Gdynia and a nearby naval base on the Baltic Sea.
He also sent Andrzej pictures of a commercial port terminal and a nearby ammunition depot. In December, Pronkin was sentenced to two years and two months in prison on charges of espionage and belonging to a criminal group.
Almost everyone who answered the job advertisement first talked with Andrzej, who would guide them through their tasks or pass them off to someone else.
Some of those who spoke with Andrzej said he sounded young; others described him as middle-aged and with a deep voice. In the end, it was never clear if he was the same person or a group of Russian intelligence officers handling the group.
For Leha’s last job, Andrzej paired him with Artem Averba, a 19-year-old Ukrainian refugee. He told them to set up cameras along the train routes carrying Western military aid into Ukraine.
To introduce the two, Andrzej set up a group Telegram chat named “Grand Theft Auto: San Andreas” in late February 2023.
“Just so we’re all on the same page and that there’s no confusion among you guys,” Andrzej wrote.
The young men picked their own code names. Leha was Karim. Averba chose Erewan, or Yerevan, in English. Andrzej dropped location pins where they were meant to place the solar-powered cameras along Poland’s eastern border with Ukraine.
While on the road, Leha said he felt uneasy with Averba, driving silently while the teen spoke nonstop.
First they stopped at Jasionka, the airport outside of Rzeszow and the transit point for much of the U.S. aid bound for Ukraine. In the forest outside the airfield, Leha attached a camera to a tree with duct tape, its lens facing the runway.
Averba later told police that he stayed in the car, while Leha did the work.
A few miles further east, they fixed another camera on the train tracks between Rzeszow and the Medyka border crossing “to record military aid going to Ukraine,” Averba said later in an interrogation.
The two then shared the camera’s account data with Andrzej over a shared MyHome app, giving all three access to watch the footage in real time.
Driving back to Warsaw, Leha said he felt increasingly uneasy and considered quitting.
“But I didn’t tell the other guys, I didn’t trust them,” Leha, now 23, said in the Lublin jail.
On his last trip on March 3, to set up cameras around the city of Kazimierz Dolny, he parked his Mazda near the city’s old Jewish cemetery. As he was walking back to his car, at least seven counterintelligence officers swooped in and detained him.
Of the 16 arrested, 14 have reached plea deals, confessing to espionage charges in exchange for prison sentences from nine months to six years. One was placed in a correctional facility for minors.
Leha refused the plea bargain in hopes of getting a lighter sentence for what he calls his cooperation with authorities. The first hearing of his appeal is planned for next week.
When asked whether he felt remorse for working for the Russians, he stayed quiet for a moment and then said flatly: “I feel very badly about what I have done.”
“I don’t think it is fair I was painted as the head of the operation. I think they needed a scapegoat,” he added.
As he was led back by officers in riot gear to a tiny jail cell that he now shares with a convicted murderer, a guard on the other side of the glass said: “Nobody likes a traitor.”
Updated: 5-17-2024
Biden Order To Halt China-Tied Bitcoin Mine Beside Nuke Base Came As U.S. Firm Just Bought It
President Biden’s emergency order to halt the Chinese-tied mining on the doorstep of a nuclear-missile base hit days after mining giant CleanSpark struck a deal to buy the property.
* CleanSpark had just finished hailing the benefits of its purchase of a Wyoming crypto-mining site when the White House declared that the current operation was a national security threat that must be halted.
* The company says it was unaware of the order before buying the properties but intends to move forward with the acquisition.
* Order would mark first “the first presidential prohibition relying on the expanded authority over real estate transactions granted to CFIUS and the president.”
An American bitcoin mining company, CleanSpark (CLSK), got caught up in the U.S.-China political war after buying mining sites in Wyoming within close proximity of a U.S. nuclear missile base from MineOne, a company with Chinese ties.
On Monday, President Joe Biden ordered a bitcoin mining facility near Warren Air Force Base in Wyoming to stop operations, citing a threat to national security as it uses foreign-sourced technology.
The order said that MineOne is majority-owned by Chinese nationals, and all mining equipment on the property must be removed from within a mile of the military facility in Cheyenne, which houses Minuteman III intercontinental ballistic missiles (ICBMs).
While this may not be a surprising move in itself, the timing stands out, as MineOne sold the sites to CleanSpark less than a week prior to the order.
On May 9, CleanSpark said it was buying two mining sites for nearly $19 million in cash, with a 45-day closing, without naming a specific seller.
The miner said it will deploy China-based Bitmain’s latest generation mining machine, noting that it plans to expand the sites by an additional 55 megawatts (MW) from 75MW.
A spokesperson for CleanSpark said the company was unaware of the order prior to buying the mining sites but acknowledged the concerns in the executive order and intends to press forward with the deal.
“The executive order and the involvement of CFIUS, both of which we were unaware of before signing the deal, has added an unexpected layer to the closing process, but we are working through these developments toward a satisfactory closing,” the spokesperson told CoinDesk in a statement.
“We respect the oversight process and are dedicated to ensuring that our operations bolster national security and benefit economic development, particularly in Wyoming, a state that has been at the forefront of developing and nurturing a pro-Bitcoin environment,” the statement said.
Neither MineOne nor lawyers at Loeb & Loeb who handled the property deal for the company responded to requests for comment.
The details of the $19 million deal, though, were fully described in filings to the Securities and Exchange Commission (SEC) from CleanSpark. The purchase was highly dependent on the securing of massive amounts of energy required to run the business.
The larger of the two properties is about 4,000 feet from the closest edge of Warren Air Force Base.
From MineOne, the sale agreement was signed by Jiaming Li, identified as the company’s director. Li, who couldn’t be reached by CoinDesk for comment, has also been president of China Xiangtai Food Co., a partner in TCC Capital and reportedly managed almost $12 billion in assets at Sinatay Insurance Co.
He has a doctorate in economics from Fordham University, according to past press releases. Li was also briefly the president of Bit Origin Ltd., a MineOne investor and a company that was reported to have garnered similar scrutiny previously from Washington.
Due Diligence
The SEC-disclosed contract with CleanSpark outlined a due diligence period extending 15 days from the May 8 date the deal was signed, and the purchase could be scrapped if MineOne didn’t satisfy several conditions, including “government compliance matters.”
“I have been deeply involved in National Security affairs for nearly four decades, and am well aware of the potential risks of many different types of encroachment on important defense infrastructure,” said Tom Wood, a CleanSpark board member who once served in senior U.S. Navy roles and as a military analyst, in a statement.
“The presence of a CCP-owned data processing facility near a facility like Warren which houses a portion of the nation’s ICBM force is legitimate cause for concern as noted by the president’s order.”
He said he’s familiar with the CFIUS process, calling it “impartial, data-driven and non-arbitrary,” and he said that if the U.S. mining business can address the concerns in the order, “I would consider this a significant win-win for the United States and for CleanSpark.”
This use of Committee on Foreign Investment in the United States (CFIUS) powers to shut down the acquisition by owners tied to China marked the eighth time the president has used the authority – seven of which involved China, according to lawyers at Hogan Lovells who specialize in this issue.
Anne Salladin and Brian Curran said in an emailed analysis that this was “the first presidential prohibition relying on the expanded authority over real estate transactions granted to CFIUS and the president under the Foreign Investment Risk Review Modernization Act of 2018.”
Updated: 6-3-2024
China Accuses U.K. of Recruiting Couple As Spies
Ministry of State Security says the couple gathered sensitive information on behalf of MI6.
SINGAPORE—China accused British intelligence of recruiting a Chinese couple as well-placed spies in key state agencies, delivering Beijing’s latest response in a simmering row with the West over espionage.
In a social-media post published Monday, China’s Ministry of State Security said authorities are investigating the couple, a man surnamed Wang and a woman surnamed Zhou, for allegedly gathering sensitive information on behalf of MI6, the U.K. foreign-intelligence agency.
The allegation marked the latest in a series of MSS disclosures of espionage probes involving Western intelligence services. China’s main civilian spy agency started using social media last year to raise public awareness about national security and warn against foreign spying.
According to the MSS account, MI6 approached Wang after he applied to study in the U.K. in 2015 because he was working at a central-level government agency in a role with access to secrets.
The British then recruited Wang to gather intelligence in China and had him persuade his wife—who was working at what the MSS called a “critical unit”—into spying for MI6 as well.
The probe against Wang and Zhou meant “uprooting a major ‘nail’ that the British had implanted within” the Chinese government, the MSS said. It didn’t provide additional information about the couple, or the agencies they worked for.
U.K. authorities declined to comment on the allegations.
The disclosure comes amid rising rancor between China and the West over alleged espionage. Such tensions have manifested themselves in public warnings about cyberattacks, spying and other forms of intelligence gathering, as well as high-profile arrests of alleged spies.
In April, Germany arrested four people, including a far-right politician’s parliamentary assistant, on suspicion of spying for China.
U.K. authorities also charged two men with allegedly spying for Beijing, including a former parliamentary researcher first arrested last year. Last month, British police charged three more men—including a U.K. Border Force official and a former Royal Marines commando—with allegedly helping Hong Kong’s intelligence services spy on U.K.-based dissidents.
The former marine was later found dead in a park.
Washington has also stepped up warnings against Chinese espionage, describing Beijing as a major source of spying and cyber threats against the U.S.
In February, Federal Bureau of Investigation Director Christopher Wray said Beijing’s efforts to covertly plant offensive malware inside critical-infrastructure networks is at “a scale greater than we’d seen before.”
Beijing, for its part, has waged a publicity campaign to urge officials and ordinary citizens to stay vigilant against efforts to steal state secrets. The once-secretive MSS launched a social-media account last summer, publicizing cases of alleged spying directed by the U.S. Central Intelligence Agency and MI6.
In January it said it had detained an alleged spy working for Britain, a “third country” national surnamed Huang, who Chinese authorities believe was directed by MI6 to enter China as a representative of a consulting agency and send back intelligence.
In the latest disclosure, the MSS said British intelligence started targeting Wang after he applied for a China-U.K. exchange program. MI6 allegedly arranged a speedy approval for Wang’s application and after his arrival sent people to cultivate him by taking him out for meals and sightseeing.
The MSS said Wang’s handlers then offered generous pay to entice him into taking on part-time consulting work, which involved looking into internal matters at a “central-level state agency.”
It said MI6 personnel then directly approached Wang, offered more money to recruit him as a spy, gave him “professional espionage training” and sent him back to China.
MI6 later asked Wang to recruit his wife, Zhou, in return for doubling his remuneration. Wang initially hesitated but eventually pushed Zhou into agreeing to spy for the British, according to the MSS.
Updated: 6-17-2024
The Russian Spies Next Door
Posing as Argentine immigrants in Slovenia, the quiet married couple were in fact part of Putin’s aggressive effort to seed the West with ‘illegal’ intelligence operatives, say authorities.
LJUBLJANA, Slovenia—The young Argentine couple in the pastel-colored house lived a seemingly ordinary suburban life, driving around this sleepy European capital in a white Kia Ceed sedan, always paying their taxes on time and never so much as getting a parking ticket.
Maria Rosa Mayer Muños ran an online art gallery, telling acquaintances she’d left Argentina after being robbed in Buenos Aires by an armed gang at a red light. Her husband, Ludwig Gisch, ran an IT startup.
Described by neighbors in their middle-class district of Črnuče as “normal” and “quiet,” the husband and wife appeared to be global citizens: switching from English and German with friends to accentless Spanish with their son and daughter, who attended the British International School.
Yet almost everything about the family from number 35 Primožičeva street was a carefully constructed lie, according to Slovenian and Western intelligence officials.
Gisch’s real name is Artem Viktorovich Dultsev, born in the Russian autonomous republic of Bashkortostan and an elite officer in Russia’s foreign intelligence service, the SVR, according to the officials and court documents.
Mayer Muños is Anna Valerevna Dultseva, a more senior SVR officer than her partner, from Nizhny Novgorod. The couple’s computers contained hardware to communicate securely to handlers in Moscow that was so encrypted neither Slovenian nor U.S. technicians could crack it.
In a secret compartment inside their refrigerator, they kept hundreds of thousands of euros in crisp bank notes.
Now, a classified trial is expected to deliver its first judgment in the coming weeks on the couple charged with conducting espionage as “illegals,” or deep-penetration agents—two crucial cogs in Vladimir Putin’s fast-expanding shadow war with the West.
Officials say that before they were arrested in December 2022, the pair used Slovenia, a North Atlantic Treaty Organization and European Union member state of just two million people, as a base to travel to nearby Italy, Croatia and across Europe to pay sources and communicate orders from Moscow.
The bucolic Alpine country of lakes and mountains—and birthplace of Melania Trump—was a perfect choice to conduct operations, with visa-free access across much of Europe and a limited counterintelligence capacity.
They had even trained their two young children, Slovenian officials say, telling them that one day their mom and dad may be captured.
Shortly after Mayer Muños and Gisch were arrested in a dawn raid by Slovenia’s security services, another pair of suspected Russian illegals—a woman and man carrying Greek and Brazilian passports—abruptly left their lives in Athens and Rio de Janeiro, abandoning businesses and romantic partners who had no idea of their real identity.
The pair carried passports identifying them as Maria Tsalla and Ludwig Campos Wittich. In fact, they were married Russian intelligence officers still building out their legend—a spy’s fake background story—separately in Greece and Brazil, a process Western intelligence agencies estimate costs millions of dollars per person.
They were called back to Moscow by handlers fearing the collapse of a network after the Slovenia arrests, officials said.
Other suspected Russian illegals have been exposed across Europe since the Ukraine invasion, from the Netherlands and Norway to the Czech Republic and Bulgaria—the biggest unmasking of deep-penetration agents since the FBI’s 2010 “Operation Ghost Stories” that nabbed 10 Russian spies in America.
Now locked in a Slovenian prison, their children housed with a foster family, the faux-Argentine couple is also a possible component in any prisoner swaps agreed with Russia, including those that may involve jailed Americans Paul Whelan and Wall Street Journal reporter Evan Gershkovich, according to senior Slovenian and U.S. officials.
The Kremlin has already expressed interest in getting them back in talks handled by Putin’s longtime close ally, Nikolai Patrushev, according to people familiar with the situation.
Neither the Kremlin nor the SVR responded to requests for comment.
The case—being investigated by Slovenian and Western officials at the highest levels of secrecy, with the court proceedings and all materials highly classified—reveals a rare insight into one of the most secretive and prized parts of Russia’s spy machine.
Unlike most spies, illegals don’t pose as diplomats but usually as people unconnected to Russia.
They spend years burrowing themselves deep into their target region, creating a spider web of information sources, identifying candidates for recruitment—“talent spotting”—and taking on assignments as a cutout for spies under diplomatic cover, who tend to be under close surveillance by their host countries.
Created in the early days of the Soviet Union and dramatized in the TV show “The Americans,” a previous generation of Russian illegals in the 1940s had played a key role in stealing American atomic secrets.
Stalin, who saw the illegals as a crucial tool for influencing the policies of adversaries and gathering intelligence on potential threats, created specialized training programs and deployed them in strategic Western capitals.
The program has been reinvigorated by Putin, who allegedly worked with illegals during his time as a KGB officer in East Germany and has sung patriotic Soviet songs with agents caught in the U.S. and returned to Moscow in prisoner swaps.
“These are special people, of special quality, of special convictions, of a special character,” he said about illegal spies in a 2017 interview with state television.
It is highly likely that Putin receives personal briefings on illegals’ exploits around the world, said Dan Hoffman, a former CIA station chief in Moscow.
In the “Operation Ghost Stories” case, the FBI said Russian illegals spent years establishing a seemingly normal existence in the U.S.: They married, bought homes, raised families, and integrated into American society. One of them studied at Harvard and another earned two master’s degrees from Seton Hall University. Two others worked in real estate.
But beneath the surface, they were actively gathering intelligence and transmitting it back to Moscow, while also seeking individuals who could be recruited as future agents.
One of them infiltrated a well-connected consulting firm with offices in Manhattan and Washington, D.C., by working as the company’s in-house computer expert, the Journal has reported.
Others were even cultivating their own American-born or -raised children as agents with even deeper cover that would be more likely to pass a U.S. government background check.
Deep-cover agents face greater risks than embassy-based operatives who work with the protection of diplomatic immunity and are often discreetly deported if caught. Illegals are likely to be handed lengthy prison sentences, meaning a yearslong wait to be released or exchanged in a prisoner swap.
These shapeshifting spies are now becoming a more important tool for the Kremlin after some 700 suspected Russian intelligence officers operating under diplomatic cover were expelled worldwide in the aftermath of the Ukraine invasion.
The Czech government recently proposed that all Russian embassy workers in the EU should be restricted from moving freely inside the border-free travel zone in Europe, which would make it more difficult for spies under diplomatic cover to liaise with illegals abroad.
NATO secretary-general Jens Stoltenberg said on Thursday that plans were being drawn up to tighten restrictions on the movement of Russian intelligence personnel in Europe.
“Illegals are again growing in significance for Moscow, especially as the line between espionage and war is becoming almost nonexistent,” said Andrei Soldatov, a Russian security expert who has spent years studying Moscow’s spy networks.
Slovenian officials said that they suspect that an unusual influx of Russian students enrolling in the country’s universities in the past two years, many of whom are in their 40s and 50s, could be cover for more Russian agents.
In March, the government deported at least eight Russian students for disseminating pro-Kremlin propaganda and impersonating Slovenians online, according to Slovenian security officials.
The same month a Russian military attaché Sergei Lemeshev was declared persona non grata after he was discovered running a disinformation operation that involved paying “hundreds of sources” to publish pro-Moscow talking points.
To untangle the truth about the quiet couple who immersed themselves in new roles as an ordinary expat family while leading double lives as Russian spies, the Journal talked to their friends and neighbors; Slovenian, Western and Latin American officials; and reviewed hundreds of sealed documents, including birth and marriage certificates, flight records, Interpol notices and Argentine court records.
Along the way reporters found a complex web of lies, from fraudulent documents to the theft of an identity of an infant who died in a small Greek village more than 30 years ago.
“We know they were important, serious agents,” said Vojko Volk, Slovenia’s state secretary for international affairs and national and international security. “It’s like ‘The Americans,’ except in Slovenia.”
Building A Legend
The cover story begins with a 2012 bus journey across Uruguay’s border with Argentina, where the couple began a decadelong effort to build an entirely false identity.
A cache of sealed Argentine court documents shows Gisch entering the country on a tourist visa from Uruguay and Mayer Muños arriving shortly after from Mexico. The couple then almost immediately began gathering documents—many of them fraudulent—to obtain citizenship.
Gisch claimed he was an Austrian citizen born in Namibia to an Argentine mother, which gave him a fast track toward citizenship. Mayer Muños claimed she was Mexican and submitted a birth certificate saying she was born in Greece.
The couple moved to the Argentine capital and began building out their legend: living in the middle class neighborhood of Belgrano and attracting little attention among the 146 apartments in their building. Mayer Muños attended a public relations class, graduating with top grades.
Gisch opened accounts with Banco Galicia and Banco Macro. Neighbors and locals described them as a shy couple who didn’t attend the building’s tenant meetings.
The concierge saw them come and go at routine times, with Gisch often wearing a tie. In 2012, Gisch applied for Argentine citizenship, with Mayer Muños applying a year later. In 2013, the couple welcomed a daughter, Sophie.
“They were very polite, respectful,” said the owner of a nearby deli, Jamonería del Virrey, where the couple would buy raw ham and cheese. “They always paid in cash.”
Mayer Muños was granted citizenship in November 2014 and a son, Daniel arrived the following August.
A month later, the couple married in their local registry office in a small ceremony witnessed by two Colombian citizens. Gisch was listed as a merchant, Mayer Muños as an events organizer.
Slovenian officials and Argentine court and Interpol documents reviewed by the Journal show the couple’s names were Artem Dultsev and Anna Dultseva, suggesting they had married in Russia before they arrived in Argentina.
Illegals are often sent abroad as couples, sometimes after an arranged marriage during their training in Russia, espionage experts say.
A year after their Argentine nuptials, an amendment was made in the marriage certificate, changing Mayer Muños’ mother’s nationality from Austrian to Mexican. The family were set to move to Europe, where background checks by Austria’s government could reveal a hole in their story.
As they prepared to leave, Gisch drained his Banco Galicia account, the final statement showing a balance of 18,784 Argentine pesos, only $21.
The family landed in Slovenia—a country roughly the size of New Jersey—on tourist visas in the summer of 2017, for the next act of their double lives, this time in the European Union.
Gisch established DSM&IT, an online IT business selling domain names and cloud hosting. The company had three followers on X, including the account of his wife’s business, Art Gallery 5’14, an online company buying and selling mostly modern art.
The gallery claimed to work with 90 artists and had prolific social-media accounts posting images almost daily. Gisch would ride his bike the short distance from the Črnuče neighborhood into downtown Ljubljana, while his wife would drive the family car.
In 2019 they received Slovenian residence permits, putting them on a path to citizenship.
Mayer Muños was using Ljubljana as a base to travel across Europe, posting pictures of art fairs and exhibitions in places like Zagreb and Edinburgh. A photo from the 2019 Art Fair Zagreb shows her adjusting paintings next to a step ladder, her face not visible.
In 2020, the 5’14 gallery organized an online photo competition, Life in Quarantine, with a €500 cash award.
None of the hundreds of photos shared on their social-media accounts showed a clear picture of Mayer Muños or Gisch, but one image posted on Facebook in December 2020, the height of the pandemic, appears to be taken at the front gate of the family home, showing four face masks dangling from a washing line.
“She was always in a good mood and joyful, and had lots of fun together with other artists,” said Marko Milić, a fine art photographer from Croatia who had met Mayer Muños at a Zagreb art fair.
Both companies appeared designed to attract little attention. They were registered in a nondescript building on Ljubljana’s outskirts along with dozens of other foreign companies such as translators, accountants and financial advisers.
The couple filed annual tax returns and paid promptly, according to Slovenian corporate records. Art Gallery 5’14 claimed in 2021 to have €25,220 in revenues, while the IT company reported €43,785. Neither received public funding or had dealings with entities within tax havens, which could have raised suspicions of Slovenian authorities.
At their two-story home, the couple spoke Spanish with their son and daughter, neighbors said. Majda Kvas, 93 years old, said she never saw any visitors, but remembers them having at least two family picnics in the garden. “They kept to themselves,” she said. “They were quiet, they wouldn’t even say hello.”
They weren’t quiet enough.
On Feb. 24, 2022—the same day that Putin began his invasion of Ukraine—the couple were back in Argentina, applying for an express processing of a new, or clean, passport, before immediately returning to Slovenia via Frankfurt.
A few months later, Slovenia’s spy agency, SOVA, or “Owl,” got a tip from an allied agency: They should look into Gisch and Mayer Muños.
‘A puzzle’
Slovenia’s top security officials called allies, who began working in a multinational cell to retrace their movements in Ljubljana, Buenos Aires and across Europe. “We worked together in the utmost secrecy,” said Volk, the state secretary. “It was a puzzle.”
Investigators set up wiretaps, collecting text messages and other data from the couple, which showed them meeting sources in European countries. Slovenian officials could see their companies were fronts, financed by cash collected from their handlers and money from prepaid cards as well as transactions between the two firms to give the impression of cash flow.
In Argentina, police visited the town Gisch had listed on his passport application and found he had never lived there. At the addresses given by the Colombians who witnessed the couple’s wedding, nobody had heard of them. Slovenia requested the fingerprints of Artem Dultsev and Anna Dultseva from Interpol, then sent them to Argentina to compare with Gisch and Mayer Muños. They matched.
More concerning was that the couple had also begun spying in Slovenia: targeting the Agency for the Cooperation of Energy Regulators, or ACER, the only significant EU body based in Ljubljana which coordinates regulatory actions among the bloc on electricity and natural gas.
The agency, whose headquarters is located around five miles from the couple’s home, raised its profile after the Ukraine invasion as energy became an especially acute topic for the continent and Russia used its gas supply to squeeze European industry. ACER didn’t respond to a request for comment.
The Slovenians and their allies realized the couple were no longer just creating their back story. “They had been awoken,” Volk said.
On Dec. 5, 2022, masked police in tactical gear arrived after midnight, jumped the family’s fence and positioned themselves outside the windows. When the couple raised the shutters, the officers burst in and arrested them.
Gisch and Mayer Muños refused to divulge any information to the investigators after their arrest, according to a former official. Their two children—now aged 8 and 11, according to the Argentine court documents—were placed in the care of the state and moved to another school.
They are allowed regular visits to their parents in prison.
Shortly after the arrest, Russia established contact, acknowledging the couple worked for the SVR and saying it wanted them back. Slovenia was eager to quickly trade and to avoid antagonizing the Kremlin, but a deal couldn’t be reached.
Slovenian officials had “prayed to get rid of them,” one senior official said.
Mayer Muños and Gisch refused to talk, but Slovenia and its allies were learning more about their activities and other potentially connected agents.
When Maria Tsalla fled Greece shortly after the arrests, Greek authorities discovered she had registered her birth on the island of Evia, claiming the identity of an infant who was listed as dying in 1991.
Authorities could see the handwritten registry had been altered—a clue to her deception—and that Tsalla had been trying to replace it with a new registration in the Athens suburb of Marousi, one of the first municipalities to digitize records.
Tsalla left behind a boyfriend in Athens who allegedly had no idea she wasn’t from Greece. Greek authorities discovered she was in fact married to another Russian illegal, Campos Wittich, who had lived for some two years in Rio de Janeiro with his Brazilian girlfriend—a veterinarian who worked for the country’s ministry of agriculture.
She helped coordinate the social media search for him when he disappeared—only to learn that he was working undercover for Russian intelligence.
Gisch and Mayer Muños have now served more than 18 months in a Slovenian prison. Slovenia’s espionage laws allow for a maximum eight-year sentence, and officials say the couple could be freed after four for good behavior.
“They were long-term illegals,” said Janez Stusek, SOVA chief until the middle of 2022, several months before the couple’s arrest. “They had a long-term mission trying to infiltrate Slovenia as an entering point into Europe.”
On 35 Primožičeva street, a new couple has moved in. Two bikes are parked on the porch and two children’s badminton rackets are hung on the veranda. Efforts to reach them were unsuccessful, and the owners of the house declined to comment. The new couple, officials and neighbors said, are also Russian.
Updated: 6-28-2024
A Den of Spies: Vienna Emerges As Hub For Russian Espionage
Moscow allegedly plotted to kill an investigative journalist in Austria. Now his home is protected by officers with submachine guns.
VIENNA—Inside a stately art nouveau building in central Vienna, special-forces officers armed with submachine guns guard the home of Christo Grozev, an investigative journalist whose Academy Award-winning documentary exposed the Kremlin’s attempt to kill opposition leader Alexei Navalny.
Two years ago, Austrian intelligence and U.S. law enforcement warned Grozev that Russian President Vladimir Putin’s spies were plotting to kill him.
After living with his family for two decades in Austria, the Bulgaria-born Grozev fled to the U.S. in 2023.
Now, when he returns to visit his family, who remained behind in Vienna, he receives a degree of state protection that rivals that of Austria’s chancellor, officials say.
The failed murder plot is one of a series of incidents that show how Vienna has emerged as Russia’s new espionage hub in Europe after capitals there expelled 600 spies posing as diplomats in the wake of the invasion of Ukraine.
Dozens of these spies have since resurfaced in Austria, intelligence officials there say. In the past two years, the number of Russian state employees in Austria swelled to over 500 from 300 to 400, over a half of whom are diplomats and administrators, according to intelligence officials.
Up to a half of them operate as spies, Austrian intelligence officials estimate.
Last year, neighboring Germany closed the Russian consulate in Munich, which German officials said was hosting a number of spies. The Russian staff simply relocated to Salzburg, an Austrian city across the border to the east, Austrian intelligence officials say.
Vienna is now a base for Russian clandestine operations, including financing and logistical support for murder, sabotage and recruitment across Europe, as well as industrial espionage and influence operations, according to over a dozen Austrian, European and U.S. intelligence and government officials.
The Russian Embassy in Washington didn’t respond to a request for comment.
Russian diplomats and support staff operate in Vienna from over 40 properties owned by Moscow and people or companies linked to the Russian state. Surveillance equipment has sprouted up on the roofs of such properties, some used to tap satellite telecommunications.
An Austrian Interior Ministry spokesman said that Austria is one of the safest countries due to its well-functioning security agencies.
The spokesman said that the country’s intelligence agency is aware that Austria has become a target for Russian espionage and influence operations and that the agency counters threats from state actors within its legal limits.
During the Cold War, the city was a notorious international spying hub, as immortalized in the Hollywood classic, “The Third Man.” Espionage is legal in Austria, which is a member of the European Union, as long as it isn’t directed against Austria itself.
A neutral country outside military alliances, Austria hosts international organizations, including United Nations agencies and the Organization of the Petroleum Exporting Countries, some of which have long had spies in their delegations, according to multiple Austrian and foreign officials.
Russian influence runs deep in Austria, dating back to when Moscow was an occupying power of the country after World War II.

For instance, in 2018, photos of Putin dancing with Austrian Foreign Minister Karin Kneissl at her wedding caused an uproar. The Foreign Ministry is in charge of approving diplomats’ accreditations—as well as expelling them.
In 2023, Kneissl moved to Russia, where she runs a think tank. The Russian air force helped move her household, including her ponies.
Vienna-based Russian operatives are suspected of helping with the recruiting and financing of Russian operations such as tracking Western arms shipments to Kyiv in Poland and killing a Russian military helicopter pilot who defected to Ukraine and was living in Spain, Western security officials say.
The killers, who shot the man five times and then ran him over with an SUV, were criminals paid with cash provided by Russian state employees from Vienna, these officials say.
“We are now becoming a liability for our neighbors because Russia is using us as an operational base,” a senior Austrian intelligence official said.

Russia sends large volumes of cash into neighboring countries such as Lithuania by road, an Austrian intelligence official said. From there, Austria-based diplomats ferry it across Europe, often in diplomatic pouches that can’t be checked by police.
Now, other EU nations are considering a Czech proposal for a ban on Russian diplomats traveling outside the country where they are posted.
“If these diplomats want to work in Vienna, then that is perfectly fine…but I see no reason why they should have free access to the Czech Republic,” Czech Foreign Minister Jan Lipavský said, claiming that Russian diplomats engage in nefarious activities.
Russian or Russian-paid saboteurs were found by Czech police and prosecutors to be behind a number of attacks on ammunitions factories and civilian targets.
The Austrian government must end its “extremely dangerous inaction” on Russia spying, which is “weakening efforts to curb Russian influence in Europe,” said Stephanie Krisper, an Austrian opposition legislator who sits on the committee scrutinizing intelligence operations.
Russia is rebuilding its spying network by recruiting civilians, organized-crime figures, hackers and private detectives for attacks on and surveillance of critical infrastructure and other operations across the continent.
“Russian intelligence is now like an octopus using every tentacle at its disposal, and the head is currently in central Europe,” a European intelligence officer said.
The U.S. also keeps a large spying contingent in Austria, which is the seat of the Central Intelligence Agency’s regional center overseeing activities in Eastern Europe and the Balkans.
Some U.S. officials believe that Russia grew bolder in recent years and began targeting American personnel. In 2021, 20 U.S. Embassy staff, including CIA officers, based in Vienna became ill with a mysterious condition known as the Havana Syndrome, according to several U.S. and Austrian officials.
The Russians possibly used acoustic or “directed energy” weapons against the U.S. personnel, said Amb. John Bolton, former President Donald Trump’s national security adviser from 2018 to 2019, when some of the reported Havana Syndrome incidents occurred in various countries.
The inability of the U.S. to protect personnel from the attacks “means that the Russians or whoever is doing it are way ahead of us,” he said.
In 2023, the U.S. intelligence community said there was no evidence that a foreign adversary had used any such weapon.
Austria’s intelligence service itself has allegedly been penetrated by Russian spies. Earlier this year, Egisto Ott, a senior undercover operations official, was arrested on various charges including accusations of spying for Russia. Ott’s lawyer Jürgen Stephan Mertens didn’t respond to a request for comment.
Mertens told Austrian media that the accusations against Ott were unfounded and lacking solid evidence. In an interview with The Wall Street Journal before his arrest, Ott denied he was a Russian spy.
The agency’s former head of operations Martin Weiss, also suspected by Austrian investigators of being a Russian spy, fled to Dubai in 2021. Austria is seeking his extradition for a number of accusations, including some related to the Grozev case, such as using Ott to obtain the journalist’s personal details.
Weiss didn’t respond to requests for comment.
Both men worked for Jan Marsalek, the Austria-born former chief operating officer of fintech group Wirecard, which collapsed in a major fraud case in 2020.
Marsalek, who fled to Moscow to avoid arrest, has been working for Russian intelligence for over a decade and now holds a senior role with the FSB, Russia’s main intelligence service, according to European officials.
Marsalek coordinated at least one team that participated in the plot against Grozev, according to legal documents.
Moreover, Austrian authorities have accused Ott in their arrest warrant, seen by the Journal, of using his intelligence connections to obtain Grozev’s address and passing it on to Marsalek and to Russian agents.
A team coordinated by Marsalek then began following Grozev. They stole electronic equipment including laptops from his homes in Vienna and Bulgaria, according to investigators in several European countries. The goal was to capture and kill him, say investigators.
Several people involved in the plot have since been arrested. One was identified after Grozev’s teenage daughter took a picture in 2022 of a man loitering outside a cafe where she was lunching with her father.
After the plot was discovered, the new head of the Austrian intelligence agency, Omar Haijawi-Pirchner, who has been cleansing the body of suspected Russian sympathizers, personally vouched for the security of the Grozevs.
Russian spies have photographed the Grozevs’ security team in an attempt to establish their identities, according to Austrian intelligence officials.
On Tuesday, Grozev said the Austrian government must do more to curb Russian espionage, saying it had penetrated Austrian institutions and its business community.
“Austria only has the counterespionage infrastructure of a very small country, although given the concentration of spies and its importance as a hub for intelligence services, it should have that of a much larger country,” he said in the presence of armed guards.
In the wake of the investigation, Austria’s justice minister has said he wants to change the law that allows for spying.
In the past two years. Haijawi-Pirchner, a former police officer without prior links to the agency, successfully pushed for the expulsion of 11 Russian spies accredited as diplomats, according to several Austrian officials.
He has asked for the expulsion of over a dozen other Russian diplomats, but the government has yet to react, two officials said.
Some Western intelligence agencies that had curbed their cooperation with Vienna during the recent scandals said they had re-established some intelligence sharing with Austria after Haijawi-Pirchner purged the service of Russian influence.
A spokeswoman for the Austrian Foreign Ministry said it supports requests to expel all diplomats who violate laws and regulations when firm evidence is presented. The Chancellery didn’t respond to a request for comment.
The scandals are sparking a reassessment of Austria’s ties to Russia—potentially to the benefit of the U.S.
The U.S. had already sought to pull Austria away from Russia in recent years, said Trevor Traina, U.S. ambassador to Vienna between 2018 and 2021.
He said he persuaded his hosts to expel a Russian spy accredited as a diplomat, at the time viewed as a great success for U.S. policy.
Then last year, the U.S. grew alarmed at a plan by Austria’s Raiffeisen Bank International to compensate Putin ally Oleg Deripaska for a $1.6 billion stake in a local construction company that was frozen due to U.S. sanctions against the oligarch. Raiffeisen has come under fire for being the biggest Western bank still operating in Russia.
Secretary of State Antony Blinken asked Austrian Chancellor Karl Nehammer to block the plan, according to officials familiar with the talks. The Austrian government scuttled the deal.
Updated: 7-2-2024
Satellite Images Show Expansion of Suspected Chinese Spy Bases In Cuba
Analysts identified four electronic eavesdropping stations, including a previously unreported site near a U.S. naval base.
WASHINGTON—Images captured from space show the growth of Cuba’s electronic eavesdropping stations that are believed to be linked to China, including new construction at a previously unreported site about 70 miles from the U.S. naval base at Guantanamo Bay, according to a new report.
The study from the Center for Strategic and International Studies, a Washington-based think tank, follows reporting last year by The Wall Street Journal that China and Cuba were negotiating closer defense and intelligence ties, including establishing a new joint military training facility on the island and an eavesdropping facility.
At the time, the Journal reported that Cuba and China were already jointly operating eavesdropping stations on the island, according to U.S. officials, who didn’t disclose their locations. It couldn’t be determined which, if any, of those are included in the sites covered by the CSIS report.
The concern about the stations, former officials and analysts say, is that China is using Cuba’s geographical proximity to the southeastern U.S. to scoop up sensitive electronic communications from American military bases, space-launch facilities, and military and commercial shipping.
Chinese facilities on the island “could also bolster China’s use of telecommunications networks to spy on U.S. citizens,” said Leland Lazarus, an expert on China-Latin America relations at Florida International University.
The White House and the Office of the Director of National Intelligence declined to comment.
Authors of the CSIS report, after analyzing years’ worth of satellite imagery, found that Cuba has significantly upgraded and expanded its electronic spying facilities in recent years and pinpointed four sites—at Bejucal, El Salao, Wajay and Calabazar.
While some of the sites described by CSIS, such as the one at Bejucal, have previously been identified as listening posts, the satellite imagery provides new details about their capabilities, growth over the years and likely links with China.
“These are active locations with an evolving mission set,” said Matthew Funaiole, a senior follow at CSIS and the report’s chief author.
The report comes amid growing concerns about Great Power competition in the Caribbean and elsewhere in Latin America, where Washington for decades has tried to prevent rivals from gaining military and economic advantage.
China is building a megaport on Peru’s Pacific coast. Russia, meanwhile, recently sent a nuclear-powered submarine, capable of firing Kalibr cruise missiles, and a frigate to Cuba’s Havana harbor.
In its annual threat assessment released in February, the U.S. intelligence community said publicly for the first time that China is pursuing military facilities in Cuba, without providing details.
Chinese officials stress that the U.S. has a vast global network of military bases and listening posts. “The U.S. is no doubt the leading power in terms of eavesdropping and does not even spare its Allies,” Liu Pengyu, a spokesman for China’s embassy in Washington, wrote in a statement. “The U.S. side has repeatedly hyped up China’s establishment of spy bases or conducting surveillance activities in Cuba.”
Cuba’s embassy didn’t respond to a request for comment.
The report says that two of the sites near Havana—Bejucal and Calabazar—contain large dish antennas that appear designed to monitor and communicate with satellites. The report notes that while Cuba doesn’t have any satellites, the antennas would be useful for China, which does have a substantial space program.
The newest dish antenna was installed at Bejucal in January, said the report, which found that and other infrastructure upgrades at the sites over the last decade.
The most recent of the four sites, still being built and not previously known publicly, is at El Salao, outside the city of Santiago de Cuba in the eastern part of the country and not far from the U.S. naval base at Guantanamo.
Construction there began in 2021, and the site appears designed to hold a large formation of antennas known as a circularly disposed antenna array, which can be used to find and intercept electronic signals, the report said.
The site, when completed, could potentially monitor communications and other electronic signals coming from the Guantanamo base, said Funaiole.
The U.S. and Russia have largely abandoned this sort of antenna array in favor of newer technologies, but China has been building them at several militarized outposts in the South China Sea, he said.
During the Cold War, the Soviet Union operated its largest overseas site for electronic spying, known as signals intelligence, at Lourdes, just outside Havana. The site, which reportedly hosted hundreds of Soviet, Cuban and other Eastern-bloc intelligence officers, closed down after 2001, and its current status isn’t clear.
China has played a larger role on the island in more recent years, and according to a White House statement last year, conducted an upgrade of its intelligence collection facilities in Cuba in 2019.
Related Articles:
Apple Sues NSO Group To Curb The Abuse Of State-Sponsored Spyware
Massive Encrypted Cellphone Hack Gave Police A Window On Cocaine, Cash And Killers
GoDaddy Breached – Plaintext Passwords – 1.2M Affected!!
Amazon’s Twitch Hack Shows Top Gamers Rake In Six-Figure Payouts
The Mercenary Threat of U.S. Hackers-for-Hire
A Hospital Hit By Hackers, A Baby In Distress: The Case Of The First Alleged Ransomware Death
Google’s Chrome Browser Is Under Active Attack, Patch Now!!!!
How Hackers Use Our Brains Against Us And How We Can Fight Back
AT&T 5G Upgrade Risks Silencing Home Alarms Reliant On Old Tech
Coinbase Users Angry With Customer Support After Funds Disappear From Accounts
Apple Cyber Flaw Allows Silent iPhone Hack Through iMessage
Biden Urges CEOs To Improve U.S. Cybersecurity After Attacks
How Hackers Hammered Australia After China Ties Turned Sour
Electric Vehicle Infrastructure Push Brings Cyber Concerns
Hacker Claims To Steal Data Of 100 Million T-Mobile Customers
Accenture Confirms Hack After LockBit Ransomware Data Leak Threats
CIA Weighs Creating Special China Unit In Bid To Out-Spy Beijing
Israel’s Mossad Intelligence Agency Is Seeking To Hire A Crypto Expert
US Taps Amazon, Google, Microsoft, Others To Help Fight Ransomware, Cyber Threats
US Drops Visa Fraud Cases Against Five Chinese Researchers
Want To Invest In Cybersecurity? Here Are Some ETFs To Consider
How To Protect Your Online Privacy While Working From Home
What Hackers Can Learn About You From Your Social-Media Profile
Biden Administration Blames Hackers Tied To China For Microsoft CyberAttack Spree
US Fights Ransomware With Crypto Tracing, $10 Million Bounties
Faces Are The Next Target For Fraudsters
Russia ‘Cozy Bear’ Breached GOP As Ransomware Attack Hit
Advertising Company Will Use Its Billboards To Track Passing Cellphones
REvil Ransomware Hits 200 Companies In MSP Supply-Chain Attack
What It Will Take To Protect Cities Against Cyber Threats
Home Security Company ADT Betting On Google Partnership To Build Revenue
Carnegie Cyber Kids Academy. World’s Most Prestigious Cyber Defense Training Facility
How To Opt Out Of Amazon’s Bandwidth-Sharing Sidewalk Network
Carnival Discloses Breach of Personal Data On Guests And Crew
UK Cyber Chief Cameron Says Ransomware Key Online Threat
The FBI Secretly Ran The Anom Messaging Platform, Yielding Hundreds Of Arrests In Global Sting
Federal Reserve Hacked More Than 50 Times In 4 Years
All of JBS’s US Beef Plants Were Forced Shut By Cyberattack
It Wasn’t Until Anonymous Payment Systems That Ransomware Became A Problem
A New Ransomware Enters The Fray: Epsilon Red
This Massive Phishing Campaign Delivers Password-Stealing Malware Disguised As Ransomware
Biden Proposes Billions For Cybersecurity After Wave of Attacks
Mobile Crypto ‘Mining’ App Possibly Connected To Personal Data Leak
Ireland Confirms Second Cyber Attack On Health System
US Unveils Plan To Protect Power Grid From Foreign Hackers
Hackers Breach Thousands of Security Cameras, Exposing Tesla, Jails, Hospitals
A Hacker Was Selling A Cybersecurity Exploit As An NFT. Then OpenSea Stepped In
Clubhouse And Its Privacy & Security Risk
Using Google’s ‘Incognito’ Mode Fails To Prevent Tracking
Kia Motors America Victim of Ransomware Attack Demanding $20M In Bitcoin, Report Claims
The Long Hack: How China Exploited A U.S. Tech Supplier
Clubhouse Users’ Raw Audio May Be Exposed To Chinese Partner
Hacker Changed Chemical Level In Florida City’s Water System
UK Merger Watchdog Suffers 150 Data Breaches In Two Years
KeepChange Foils Bitcoin Theft But Loses User Data In Sunday Breach
Hacker Refuses To Hand Police Password For Seized Wallet With $6.5M In Bitcoin
SonicWall Says It Was Victim of ‘Sophisticated’ Hack
Tor Project’s Crypto Donations Increased 23% In 2020
Armed Robbers Steal $450K From Hong Kong Crypto Trader
Is Your iPhone Passcode Off Limits To The Law? Supreme Court Ruling Sought
Researchers Warn 3 Apps Have Been Stealing Crypto Undetected For A Year
Ways To Prevent Phishing Scams In 2020
The Pandemic Turbocharged Online Privacy Concerns
US Treasury Breached By Foreign-Backed Hackers
FireEye Hack Portends A Scary Era Of Cyber-Insecurity
How FinCEN Became A Honeypot For Sensitive Personal Data
Apple And Google To Stop X-Mode From Collecting Location Data From Users’ Phones
Surge In Physical Threats During Pandemic Complicates Employee Security Efforts
Imagine A Nutrition Label—for Cybersecurity
Cybercriminals Attack GoDaddy-based Cryptocurrency Platforms
Biden Team Lacks Full U.S. Cybersecurity Support In Transition Fracas
Nasdaq To Buy Anti-Financial Crime Firm Verafin For $2.75 Billion
Mysterious Software Bugs Were Used To Hack iPhones and Android Phones and No One Will Talk About It
Dark Web Hackers Say They Hold Keys To 10,000 Robinhood Accounts #GotBitcoin
Hackers Steal $2.3 Million From Trump Wisconsin Campaign Account
Crypto Scammers Deface Trump Campaign Website One Week From Elections
Telecoms Protocol From 1975 Exploited To Target 20 Crypto Executives
With Traders Far From Offices, Banks Bring Surveillance To Homes
A Millionaire Hacker’s Lessons For Corporate America
Container Shipping Line CMA CGM Says Data Possibly Stolen In Cyberattack
Major Hospital System Hit With Cyberattack, Potentially Largest In U.S. History
Hacker Releases Information On Las Vegas-Area Students After Officials Don’t Pay Ransom
Russian Troll Farms Posing As African-American Support For Donald Trump
US Moves To Seize Cryptocurrency Accounts Linked To North Korean Heists
These Illicit SIM Cards Are Making Hacks Like Twitter’s Easier
Uber Exec Allegedly Concealed 2016 Hack With $100K BTC ‘Bug Bounty’ Pay-Off
Senate Panel’s Russia Probe Found Counterintelligence Risks In Trump’s 2016 Campaign
Bockchain Based Surveillance Camera Technology Detects Crime In Real-Time
Facebook Offers Money To Reel In TikTok Creators
How A Facebook Employee Helped Trump Win—But Switched Sides For 2020
Facebook Rebuffs Barr, Moves Ahead on Messaging Encryption
Facebook Ad Rates Fall As Coronavirus Undermines Ad Spending
Facebook Labels Trump Posts On Grounds That He’s Inciting Violence
Crypto Prediction Markets Face Competition From Facebook ‘Forecasts’ (#GotBitcoin?)
Coronavirus Is The Pin That Burst Facebook And Google Online Ads Business Bubble
OpenLibra Plans To Launch Permissionless Fork Of Facebook’s Stablecoin (#GotBitcoin?)
Facebook Warns Investors That Libra Stablecoin May Never Launch (#GotBitcoin?)
FTC Approves Roughly $5 Billion Facebook Settlement (#GotBitcoin?)
How Facebook Coin’s Big Corporate Backers Will Profit From Crypto
Facebook’s Libra Is Bad For African Americans (#GotBitcoin?)
A Monumental Fight Over Facebook’s Cryptocurrency Is Coming (#GotBitcoin?)
Alert! 540 Million Facebook Users’ Data Exposed On Amazon Servers (#GotBitcoin?)
Facebook Bug Potentially Exposed Unshared Photos of Up 6.8 Million Users (#GotBitcoin?)
Facebook Says Millions of Users’ Passwords Were Improperly Stored in Internal Systems (#GotBitcoin?)
Advertisers Allege Facebook Failed to Disclose Key Metric Error For More Than A Year (#GotBitcoin?)
Ad Agency CEO Calls On Marketers To Take Collective Stand Against Facebook (#GotBitcoin?)
Thieves Can Now Nab Your Data In A Few Minutes For A Few Bucks (#GotBitcoin?)
New Crypto Mining Malware Beapy Uses Leaked NSA Hacking Tools: Symantec Research (#GotBitcoin?)
Equifax, FICO Team Up To Sell Your Financial Data To Banks (#GotBitcoin?)
Cyber-Security Alert!: FEMA Leaked Data Of 2.3 Million Disaster Survivors (#GotBitcoin?)
DMV Hacked! Your Personal Records Are Now Being Transmitted To Croatia (#GotBitcoin?)
Lithuanian Man Pleads Guilty In $100 Million Fraud Against Google, Facebook (#GotBitcoin?)
Hack Alert! Buca Di Beppo, Owned By Earl Enterprises Suffers Data Breach Of 2M Cards (#GotBitcoin?)
SEC Hack Proves Bitcoin Has Better Data Security (#GotBitcoin?)
Maxine Waters (D., Calif.) Rises As Banking Industry’s Overseer (#GotBitcoin?)
Your Questions And Comments Are Greatly Appreciated.
Monty H. & Carolyn A.
Who’s Watching Who? gSpy vs. iSpy,Who’s Watching Who? gSpy vs. iSpy,Who’s Watching Who? gSpy vs. iSpy,Who’s Watching Who? gSpy vs. iSpy,Who’s Watching Who? gSpy vs. iSpy,Who’s Watching Who? gSpy vs. iSpy,Who’s Watching Who? gSpy vs. iSpy,Who’s Watching Who? gSpy vs. iSpy,Who’s Watching Who? gSpy vs. iSpy,Who’s Watching Who? gSpy vs. iSpy,Who’s Watching Who? gSpy vs. iSpy,Who’s Watching Who? gSpy vs. iSpy,Who’s Watching Who? gSpy vs. iSpy,
Go back









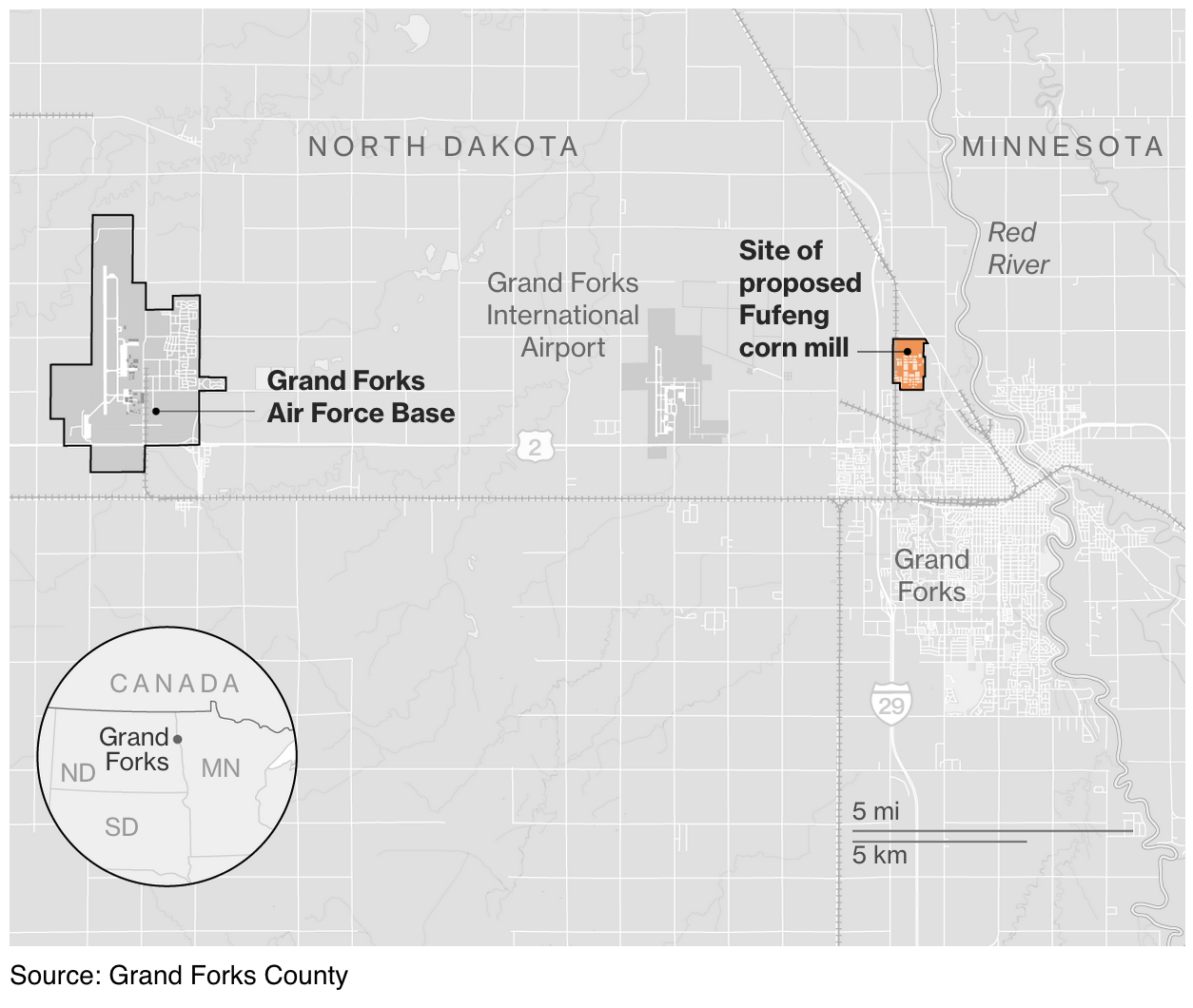




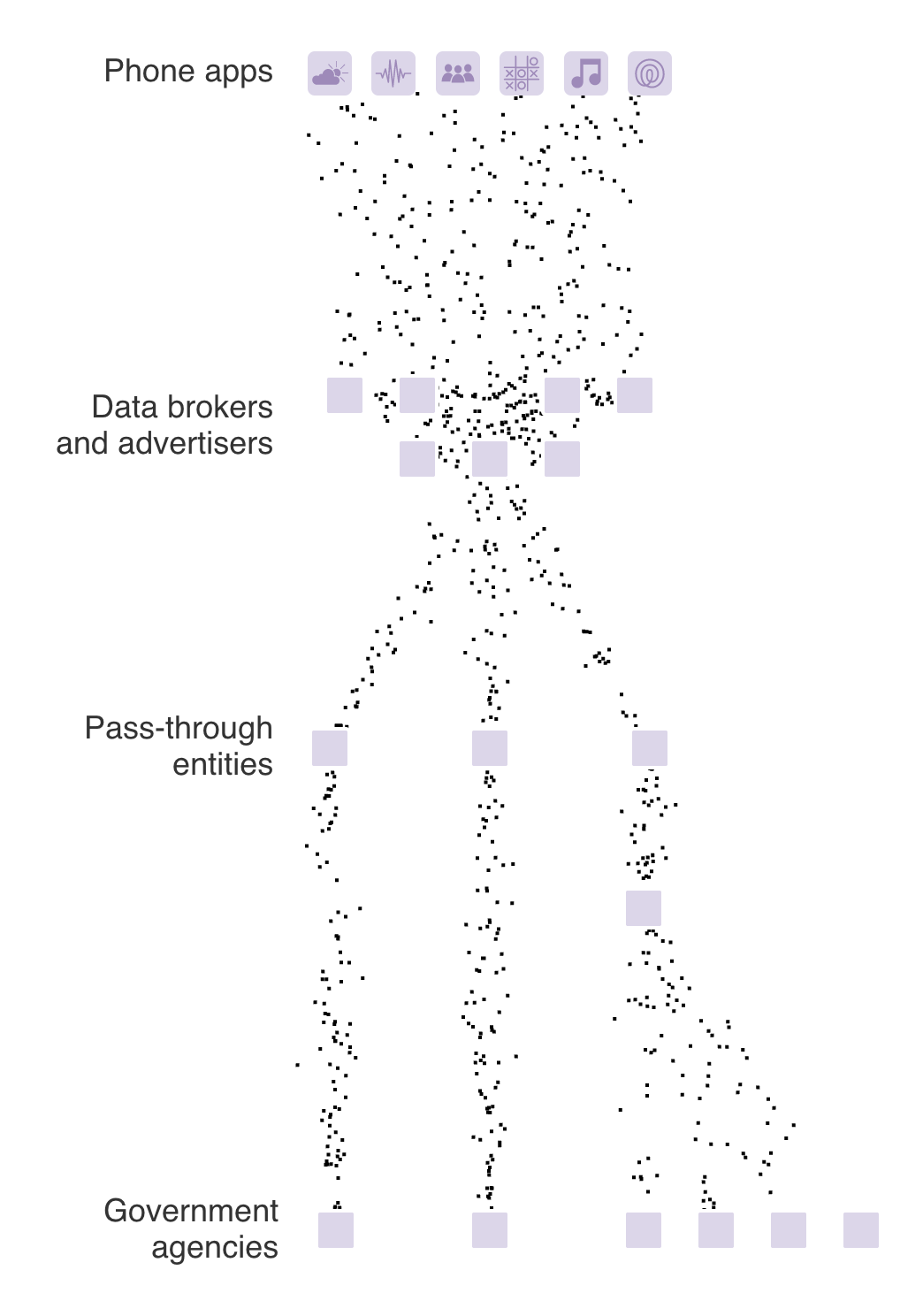
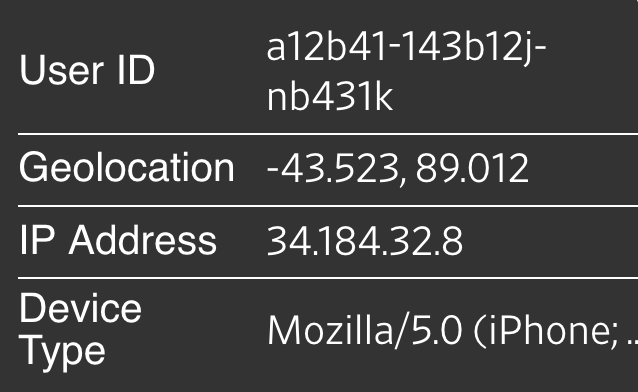
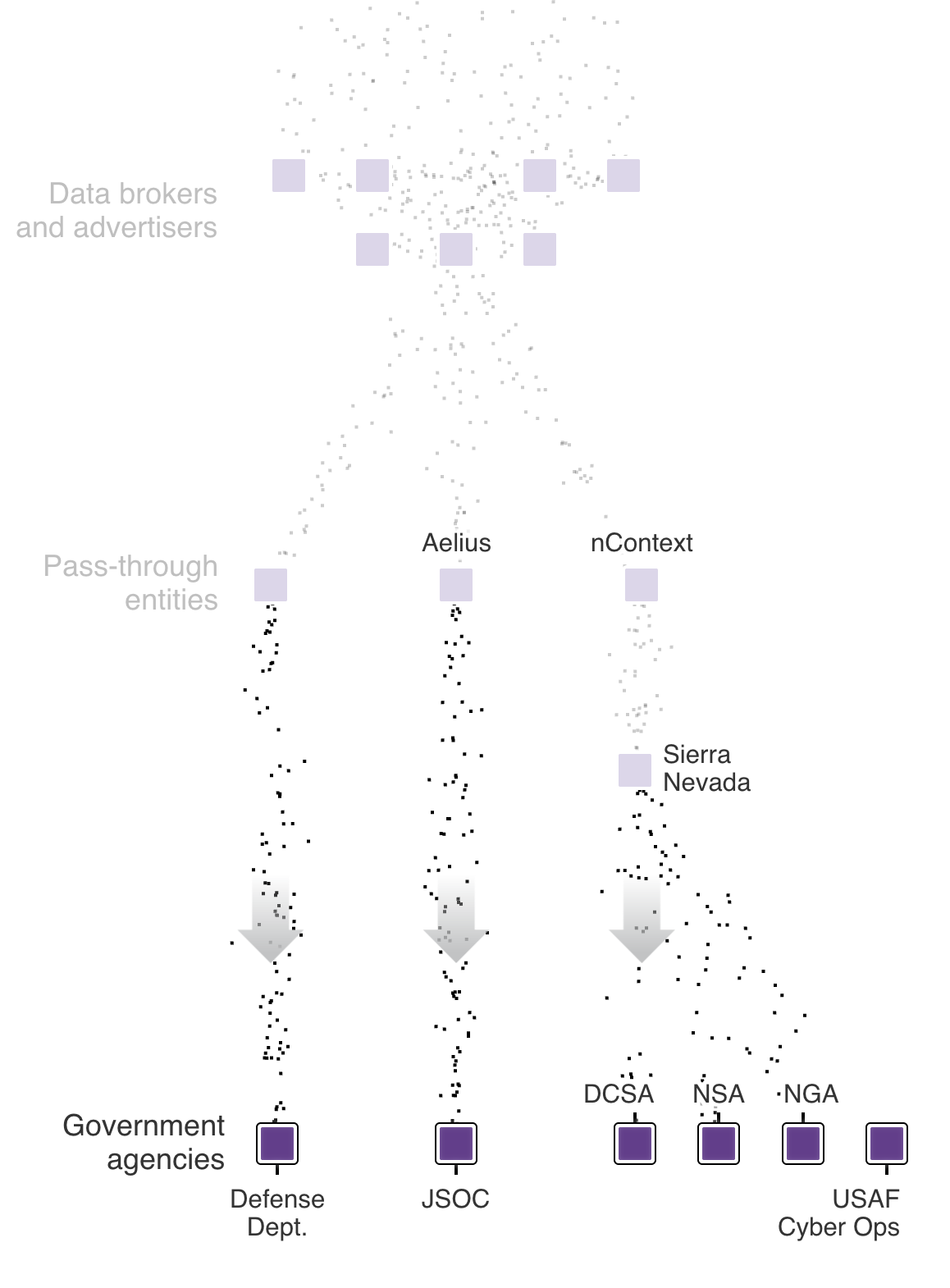










































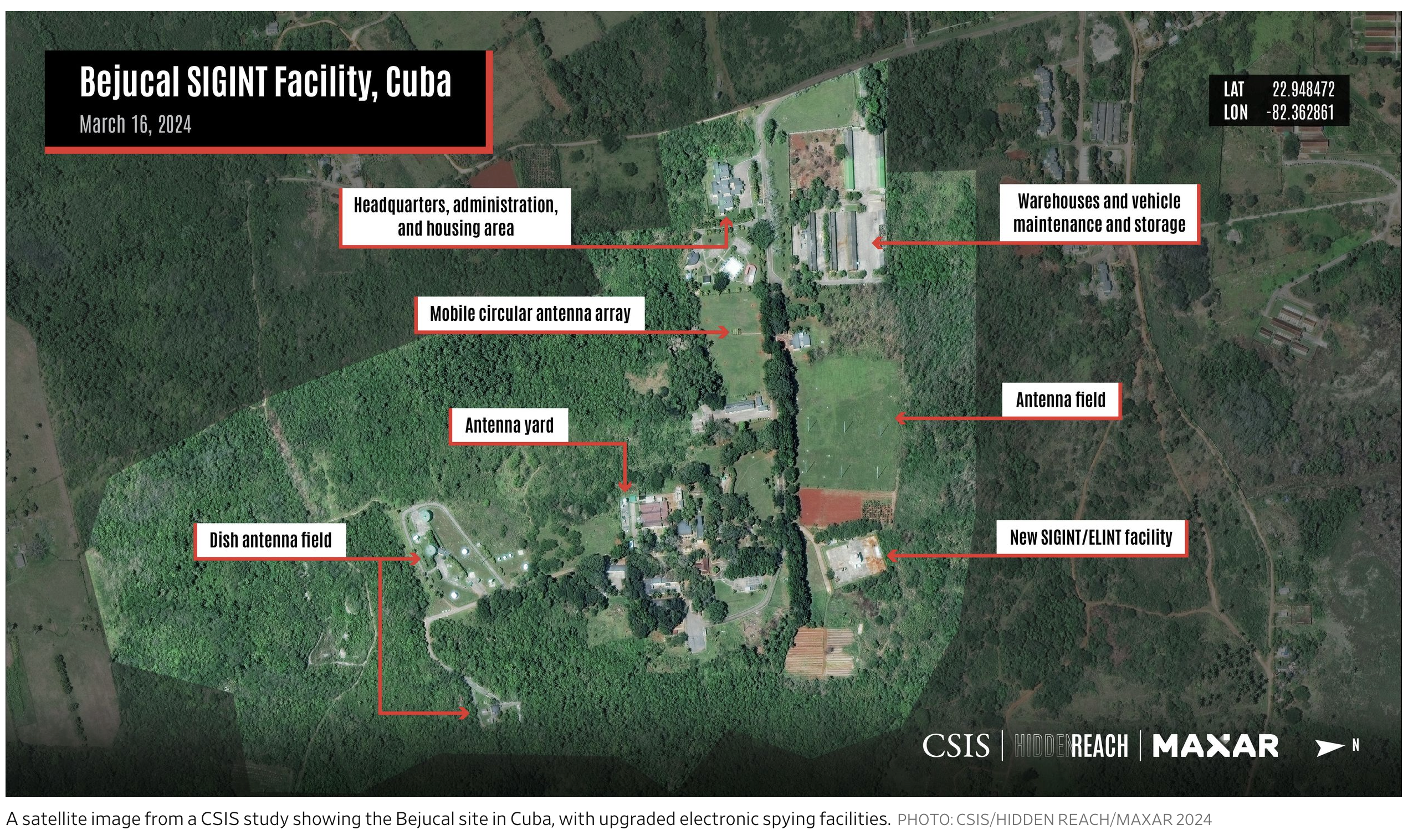


Leave a Reply
You must be logged in to post a comment.