Thieves Can Now Nab Your Data In A Few Minutes For A Few Bucks (#GotBitcoin?)
‘If someone wants to find my Social Security number, it will take them exactly $3 and five minutes,’ a data security specialist said.
As investigators work to assess who hacked Marriott International Inc. and the extent of the damage, one place they are hunting is the shadowy digital bazaars where thieves and spies trade stolen personal data.
A seemingly endless string of breaches have hit big companies and their users in recent years: 500 million potential victims at Marriott’s Starwood properties; 117 million users in the 2012 hack of LinkedIn; three billion at Yahoo in 2013. Often, these attacks fuel a black market awash in pilfered data bought, sold and repackaged for criminal uses.
So much stolen data is available on the dark web, people shouldn’t worry whether their information has been swiped, said Elvis Chan, a supervisory special agent with the Federal Bureau of Investigation who investigates cyber intrusions. “Every American person should assume all of their data is out there,” he said.
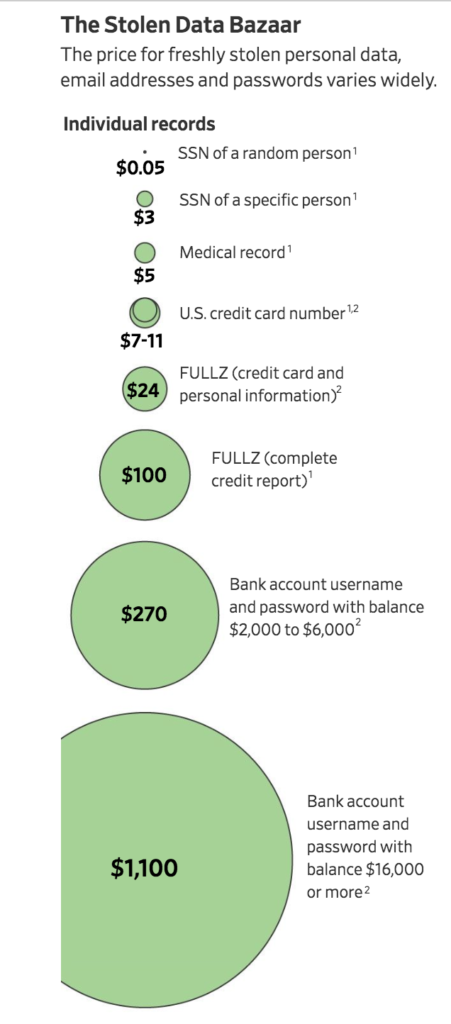
The pipeline for personal information has made it cheap and easy to get. The asking price for a single piece of data, such as a credit-card number, webmail password or Social Security number can be just a few dollars.
“If someone wants to find my Social Security number, it will take them exactly $3 and five minutes,” said Andrei Barysevich, who works for the online investigation firm Recorded Future Inc.
Data thieves historically have focused on passwords and payment-card information. But the Marriott breach and an attack on Equifax Inc. threw a spotlight on other kinds of vital information—Social Security and passport numbers—that can be used in identity theft. New sellers of stolen data are “popping up on a weekly basis,” Mr. Barysevich said.
The stolen information is spread across a dizzying array of black-market websites and discussion forums, where it is packaged, processed and sold in bulk for hard-to-trace digital currencies such as bitcoin. Many sellers aren’t trustworthy and prices can range wildly, but the marketplace is growing, fed by abundant supply. The security firm Risk Based Security Inc. estimates more than 24 billion credentials all told have been stolen or exposed.
Not everyone whose data is swiped in a breach ends up an identity-theft victim. Still, Javelin Strategy & Research pegs losses from identity theft at $16.8 billion last year. The average victim loses $776 and spends 20 hours setting things straight, Javelin estimated.
In the aftermath of big breaches like Marriott’s, investigators scour criminal marketplaces for clues. If a large number of credit-card numbers used at a particular hotel chain pop up, for example, that is a possible sign that criminals, and not nation-state hackers, were behind the hack.
With the Marriott breach and Equifax attack, which was disclosed last year and affected 148 million people, sellers haven’t yet appeared—which could indicate foreign governments are behind those two break-ins.
Alex Holden, chief information security officer of Hold Security LLC, said a recent investigation found hackers last month offering to produce fake passport and identification cards based on data in a cache of 4,600 purloined documents. By using image-editing software to marry photos with the stolen data, hackers were producing fake IDs that could be used to gain access to online accounts, he said.
Providers of online accounts sometimes will reset a password for someone if that person can produce a passport, he said.
Fake passports are only one of many products made from stolen consumer information. Criminals also assemble comprehensive victim files called “fullz”—internet slang for a full listing of someone’s data—that sell for about $100 each, Mr. Barysevich said. Fullz can include a victim’s date of birth, Social Security number, telephone number, driver’s license number, banking information and more.
This type of information is feeding a new form of fraud known as SIM hijacking, in which criminals use stolen data to persuade mobile-phone operators they are legitimate customers who have lost their phones and are in need of a new SIM card. When the new SIM card is activated, criminals gain control of the victim’s phone number and quickly use it to reset online passwords and empty bank accounts.
For accounts that require only a user name and password, hackers turn to free downloadable tools such as Sentry MBA or Hitman, known as credential stuffers. The software takes a bulk list of email addresses and passwords stolen from a site and tries, through a network of computers, to use them one by one to log into different websites. Stolen email addresses and passwords from LinkedIn, for example, could be tried against Amazon. Up to 2% of passwords found on any one site work elsewhere, according to the security company SpyCloud Inc. That can turn a single $100 record into a valuable skeleton key for a buyer.
There are criminal tutorials for sale for neophyte thieves. For $300, a would-be hacker can buy a “Bank Account Takeover Guide” for step-by-step instructions on how to use fullz information to obtain a bank loan. Lower-cost guides can go for $50, Mr. Barysevich said.
Corporate data commands a premium. Login information for specific company email addresses on a variety of forums, for example, sells for $400 to $500, said Corey Milligan, a researcher with the security-service provider Armor Defense Inc.
Access to an online bank account, which gives a hacker a way to siphon cash directly from a victim, is worth more. And the more money in the account, the more it is worth. For the keys to a banking account with $15,000 in cash, hackers can charge as much as $1,000, according to research firms that track such activity.
HOW TO PROTECT YOUR DATA
There are simple steps people can take to make life more difficult for online thieves, researchers say.
- Make sure email and other important accounts use two-factor authentication. Typically, this means you get a text or app message on your phone asking for approval when you try to login from a new device.
- Get a password manager for your online accounts, make your passwords complex and never reuse them.
- Make sure you have an account registered with the Internal Revenue Service and Social Security Administration. If you register first, it makes it hard for crooks to do so in your name.
- Consider a free credit freeze. This makes it harder for anyone–you or the hackers–to apply for credit in your name.
Related Article:
Marriott Says Up To 500 Million Breach Also Includes Trump Hotels (#GotBitcoin?)
Your questions and comments are greatly appreciated.
Monty H. & Carolyn A.
Go back
Leave a Reply
You must be logged in to post a comment.