New Crypto Mining Malware Beapy Uses Leaked NSA Hacking Tools: Symantec Research (#GotBitcoin?)
American software security firm Symantec found a spike in a new crypto mining malware that mainly targets enterprises, TechCrunch reports on April 25. New Crypto Mining Malware Beapy Uses Leaked NSA Hacking Tools: Symantec Research (#GotBitcoin?)
So, the NSA is actually spreading or contributing to the exchange hacking, mining malware and overall cyber-crime sprees we’re facing. Hahahah, Monty
The new cryptojacking malware, dubbed Beapy, uses the leaked United States National Security Agency (NSA) hacking tools to spread throughout corporate networks to generate big sums of money from a large amount of computers, the report notes.
First spotted in January 2019, Beapy reportedly surged to over 12,000 unique infection across 732 organizations since March, with more than 80% of infections located in China.
As found by researchers, Beapy malware is reportedly spread through malicious emails. Once opened, malware drops the NSA-developed DoublePulsar malware and uses NSA’s EternalBlue exploit, the same exploits that helped spread the WannaCry ransomware in 2017. According to the report, Beapy also uses Mimikatz, an open-source credential stealer, to collect and use passwords from infected computers to navigate its way across the network.
According to TechCrunch, cryptojacking has seen a decline in recent months, partially due to the recent shutdown of Coinhive, a popular web-based online mining tool. However, file-based cryptojacking such as Beapy is reportedly much more efficient and faster, which allows hackers to make more money.
As such, in a single month, file-based mining can generate up to $750,000, compared to just $30,000 from a browser-based mining activity, Symantec researchers said.
As recently reported, crypto mining is one of the most observed objectives of hackers attacking businesses’ cloud infrastructures, with organizations of all sizes continuing to face major crypto mining attacks despite the bear market.
Recently, a federal jury convicted two Romanian alleged cybercriminals for spreading malware to steal users credentials and illicitly mine cryptocurrency.
3-20-2017
Leaked NSA Hacking Tools Find Their Way Onto The Dark Web
Underground hackers are now sharing, promoting and working to adopt executable computer code evident in NSA documents that were published last week by the Shadow Brokers, private sector intelligence analysts tell CyberScoop.
Tutorials on how to utilize some of the tools began appearing the same day the NSA documents were originally published, according to researchers at Israel-based dark web intelligence firm SenseCy. Forum members have shown a particular interest in a leaked framework similar to Metasploit that’s unique to the NSA called Fuzzbunch.
SenseCy, a firm focused on the dark web staffed by former intelligence officials, identified a series of conversations occurring in a hidden Russian cybercrime forum discussing how members could exploit a bug in Windows Server Message Block, a network file sharing protocol.
“Hackers [have] shared the leaked [NSA] information on various platforms, including explanations [for how to use the tools] published by Russian-language blogs,” said SenseCy Director Gilles Perez. “We identified [one] discussion dealing with the SMB exploit [ETERNALBLUE], where hackers expressed interest in its exploitation and share instruction on how to do so.”
Perez declined to name the dark web forums surveilled by SenseCy, but provided CyberScoop with screenshots of conversations between members discussing the matter in discussion boards — “We can never provide the names of the forums as that could jeopardize our operations,” he wrote in an email.
One of the powerful tools shared by the Shadow Brokers last week, and addressed by a March Microsoft security update, is codenamed ETERNALBLUE in the leaked documents — it is also referred to as vulnerability MS17-010 by Microsoft.
ETERNALBLUE allows for an attacker to remotely cause older versions of Windows to execute code.
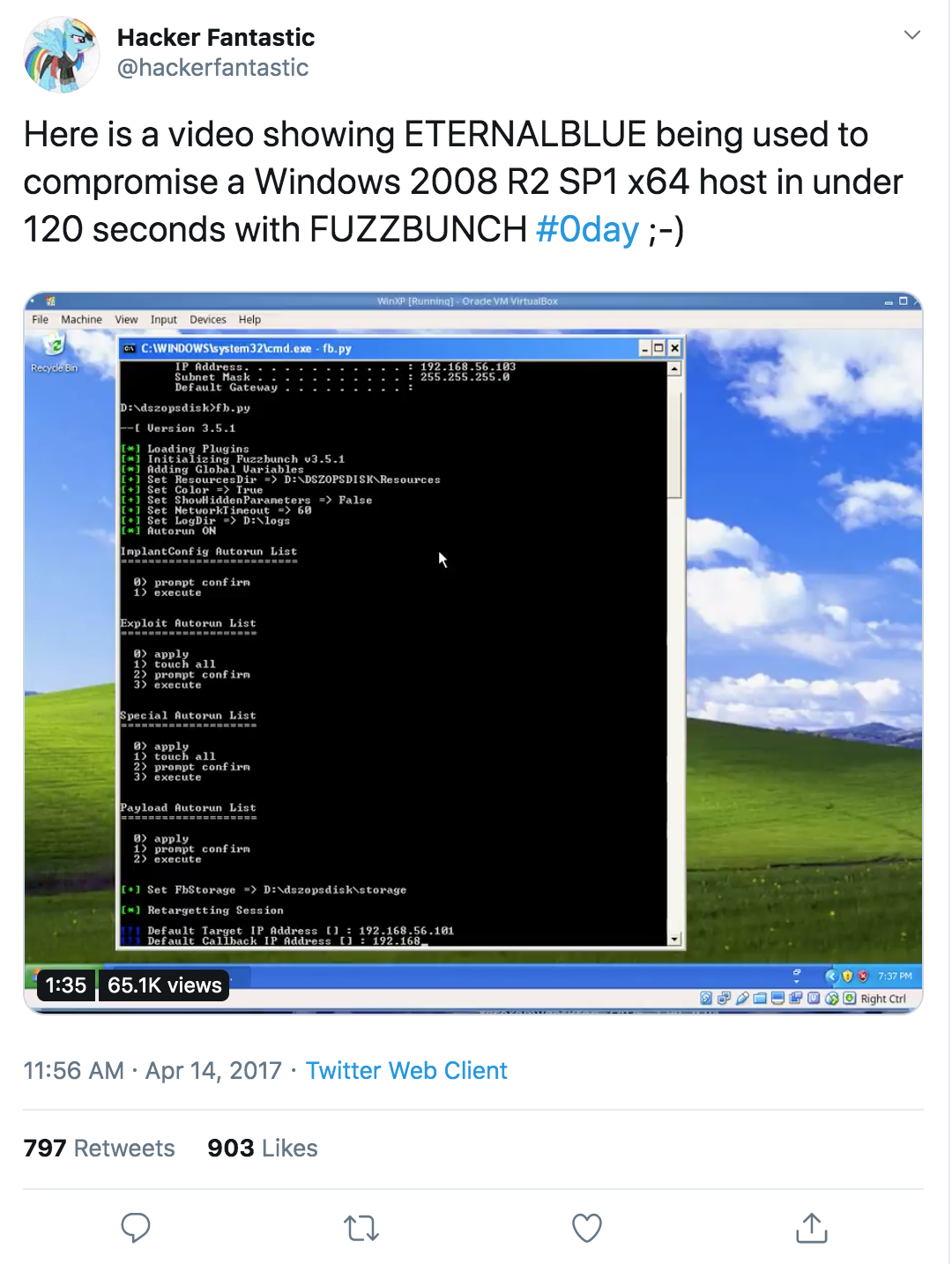
Security researcher Matthew Hickey was able to show in a video that ETERNALBLUE is effective against machines running Windows Server 2008 R2 SP1, an old but popular version of Windows Server.
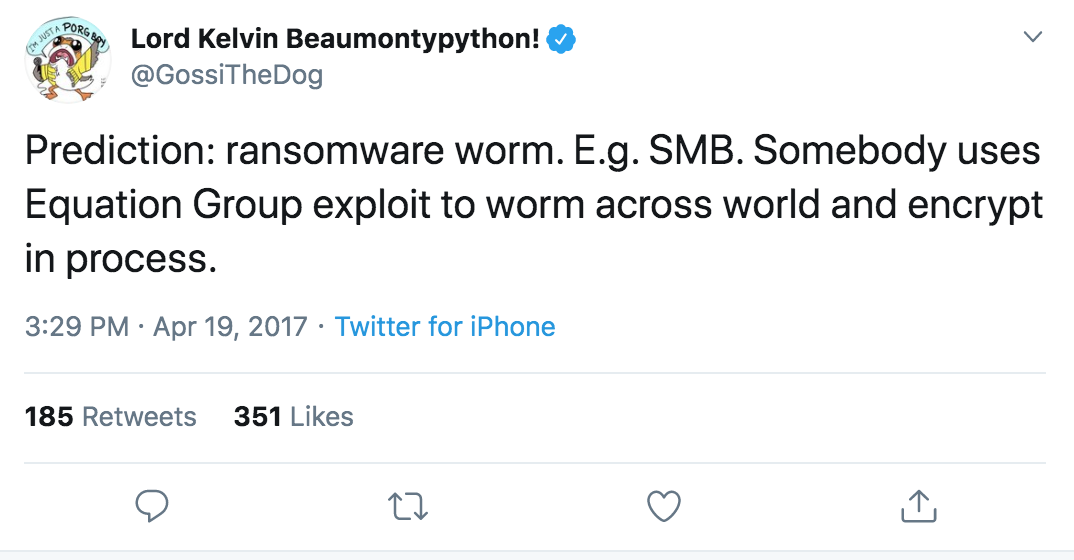
SenseCy researchers told CyberScoop they’ve already seen cybercriminals attempt to utilize the MS17-010 vulnerability in ransomeware-style attacks.
“We are now seeing a trend, that most likely will gain momentum in the following weeks, of infecting Windows servers with Ransomware utilizing the [NSA] leaked exploits,” Gilles said.
Some security researchers believe that exploiting MS17-010 will become popular amongst cybercrime gangs because it allows for a more damaging ransomware infection.
Researchers at cyber intelligence firm Recorded Future told CyberScoop that they too have spotted separate discussions in several Russian and Chinese hacker forums in which users successfully reversed engineered some of the Windows tools and were openly sharing their findings.
“The surprising recent release — one of the most comprehensive and up to date — of hacking tools and exploits by the notorious Shadow Brokers group stirred up great interest among Russian-speaking cyber criminals,” said Andrei Barysevich, Recorded Future’s director of advanced collection. “Only three days after the data was leaked, we identified a discussion among members of an elite dark web community sharing expertise in weaponizing the EternalBlue exploit as well as the DoublePulsar kernel payload.”
He added, “considering that Microsoft patched the EternalBlue vulnerability as recently as March 14, the number of potentially affected systems could still be tremendous.”
Recorded Future similarly declined to name the forums where they discovered this content.
“[In the Chinese forum], they were particularly interested in the exploit framework (named FUZZBUNCH), the SMB malware (ETERNALBLUE) and privilege escalation tool (ETERNALROMANCE),” members of Recorded Future’s research team wrote in an email. “Actors were focused on the unique trigger point for [ETERNALBLUE] and some claimed that the patches for CVE-2017-0143 through -0148 were insufficient because they did not address the base code weaknesses.”
These discussions indicate that there’s broad interest in the unique malware triggers published by the Shadow Brokers and a belief that the underlying vulnerabilities being exploited had not been completely mitigated by Microsoft’s patches, according to Recorded Future. “These two factors combine to increase the risk that malicious Chinese actors may reuse or repurpose this malware in the future,” a spokesperson explained.

Most of the exploits and implants mentioned in the latest release are designed to exploit software vulnerabilities apparent in older Microsoft products, including Office and various operating systems. The technology giant stated in a blog post over the weekend that it had patched most of the exploits. Discontinued, end of life version of Windows, such as XP and 2003, remain vulnerable as they did not receive a security patch.
More than 65 percent of desktop computers connected to the internet last month ran on older versions of Windows like Vista, according to estimates from the tracking firm Net Market Share.
While many of the Microsoft Windows-specific exploits contain remote code execution vulnerabilities, they need to be deployed against a host in order to be successful. In other words, a connection to the organization must already be established for many of these exploits to work — as port 445, which is used in Microsoft’s SMB, is typically blocked internet-wide.
Microsoft declined to answer questions pertaining to how the company originally became aware of the aforementioned vulnerabilities, which were supposedly once exploited by the NSA.
Though it remains unclear whether anyone has been able to successfully leverage any of the leaked hacking tools to launch their own computer intrusion, security researchers fully expect and are preparing for a barrage of new attacks supported by NSA’s quality engineering.
“Even though the vulnerabilities released were patched, we feel confident that it will only be a matter of time before we see exploitation in the wild,” said Cylance Chief Research Officer Jon Miller. “The scale will be on par with any other known and patched vulnerability. Only those that aren’t judicious in patching their systems will be affected, mitigating the risk that comes from a true zero-day.”
Liam O’Murchu, the director of Symantec’s security technology and response group, said he expects it will take a “little longer” for attackers to begin incorporating the leaked tools into their own attacks.
“From a defensive perspective, one of the main problems is the volume of data released,” said O’Murchu. “We need to analyze all the files to understand how they could be changed or used to fit in with current cybercrime attacks … with ~7000 files disclosed, it is very resource intensive to understand all of the tools, the full capabilities and how they can be used. That is what we are working on now.”
A cohort of independent researchers and security firms are finding new capabilities and targeted software vulnerabilities hidden in the massive trove of documents on a near daily basis since Friday’s release.
“We have only begun to scratch the surface on these tools and now that they are out there it’s important we can analyze them to determine servers that are impacted as well as what steps can be taken to protect against them,” Hickey wrote in a blog post, Wednesday.

“The tools are released in binary format and as reverse engineering efforts are underway. We will likely discover more interesting features about the attacks,” wrote Hickey. “We are under no illusion that such a huge data trove will not be completely analyzed in its first few days of discovery and neither should you.”
Updated: 10-30-2019
New Web App Scans GitHub For Secrets Like Crypto Keys And Passwords
A new web app, called “Shhgit”, will scan the web-based GitHub code repository and search for sensitive secrets, such as private crypto keys.
Scanning For Private Crypto Keys And Passwords
On Oct. 17, programmer and security expert Paul Price introduced his new tool, Shhgit. Shhgit scans for secrets across public code repositories that sometimes end up in the hands of bad actors and ultimately have the potential to cause significant data breaches.
Price said that finding these potentially harmful secrets across GitHub is nothing new. According to the programmer, there are tons of open-source tools available, such as gitrob and truggleHog, which all dig into “commit history to find secret tokens from specific repositories, users or organisations.”
Price added that software developers, who sometimes unwillingly leak secrets across public code repositories, should ensure secrets don’t end up in their code base in the first place. At a minimum, Price said, “config files should be encrypted with a environment-based key.”
Although scanning for secrets in public code repositories has existed since the launch of GitHub, some recent data breaches, such as the Capital One hack that left the personal data of over 100 million individuals exposed, show severe implications of faulty security that can lead to reputational damage and huge fines.
Price states that his tool can help in finding any secrets accidentally committed in real time, which should give developers the time to delete any sensitive information before hackers can have a field day with anybody’s private information.
Bitcoin Has Never Been Hacked
In July, Paige Thompson allegedly stole the confidential data for around 106 million Capital One customers’ accounts and credit card applications. The hacker allegedly gained access to 140,000 Social Security numbers, 1 million Canadian Social Insurance numbers and 80,000 bank account numbers, as well as data pertaining to customers’ credit scores, credit limits and balances.
Updated: 11-4-2019
Crypto Under Attack: The Five Worst Hacks That Shook the Crypto World
In tandem with improvements in technology and security, hackers have started getting more creative with the scams and hacks they carry out. You could be one click away from malware, causing harm to your files and crypto assets.
If you’re on a network that is used by billions of people every day, then I would like to burst the bubble and tell you that no matter what, you are prone to hacking. Hacking is the act of gaining unauthorized access to someone’s system to steal their data and files or corrupt their system. This process is done by repeatedly cracking codes and passwords, eventually giving access to the systems.
Cryptocurrencies were first introduced in 2009 with the launch of Bitcoin (BTC), and since then, many other digital currencies — or altcoins — have also surfaced. Cryptocurrency is an asset that is available on a blockchain-based network and works as a medium of exchange. With their entire presence only existing online, cryptocurrencies are prone to hacking as well, and over the years, we have seen several cryptocurrency hacks and scams take place.
Even though hacking is illegal and of course looked down upon, we can’t ignore the impressive effort, depth of knowledge, courage and level of creativity necessary to pull off such a task. Here is a list of the five greatest hacks of all time.
Nicehash Hack, Professional Attack, $64 Million Stolen
Slovenian-based Bitcoin mining marketplace, NiceHash, was launched in 2014. In just three years, so-called “cloud mining” — i.e., a web platform where people buy and sell processing power needed to mine Bitcoin — was poorly wounded: A hacker stole approximately 4,700 Bitcoins, which was worth about $64 million at the time of the hack in December 2017, when the leading cryptocurrency’s price was hitting record highs around $20,000 per coin. The platform called the security breach a highly skilled and organized attack that was carried out with sophisticated social engineering.
The damage inflicted by the hacker on the platform was so significant that the exchange suspended all its operations for 24 hours to conduct the investigation. The mining exchange’s official press release statement also recommended its users change their online passwords.
In an effort to save its reputation, NiceHash started a repayment program to return digital currency to those users who had been affected by the infamous hack. Started back in February 2018, the repayment program is still ongoing, and the next, 22nd reimbursement is scheduled for Nov. 4, 2019, meaning that 81% of all stolen funds will have been returned to the platform’s users.
Bitpoint Exchange Hacked, Wallet Attack, $28 Million Stolen
In July, cryptocurrency exchange Bitpoint revealed that about 55,000 users became the target of a $27.9 million hack. Bitpoint’s president, Genki Oda, stated that out of the crypto stolen, $19 million belonged to customers, whereas the remaining amount, $8.9 million, was the company holdings.
In the theft, the hot wallets of customers were attacked. Not only this, however, as the hacker also used Bitpoint’s software to steal an additional $2.3 million from overseas exchanges. The stolen funds have not been recovered yet, and the exchange is trying to find the person or group responsible for this theft through an investigation.
Bitpoint received a business improvement order from Japan’s Financial Services Agency in June 2018.
The FSA did this to make sure that the exchange upgrade its system to secure the funds and also to match up with the FSA’s Anti-Money Laundering and Know Your Customer requirements.
The exchange has a total userbase of 110,000, and theft on half of them raises questions regarding security levels of the exchange.
Bittrex Delists Bitcoin Gold, Series Of Hacks, $18 Million Lost
Launched in 2013, Bittrex is a United States-based cryptocurrency exchange with a team of 49 members. Recently, the exchange decided to delist Bitcoin Gold (BTG) from its platform after a hack.
A series of hacking attacks on the exchange led to the loss of over $18 million in funds from the exchange. Back in May 2018, hackers took control of more than 51% of the overall hash power of Bitcoin Gold, more than 388,000 BTG.
A method called “double-spending” was used by hackers to trick the exchange into transferring double the amount of coins than needed. The exact amount of Bitcoin Gold stolen from Bittrex was not mentioned, but Bittrex had reportedly requested more than 12,000 BTG (worth around $255,000) as a compensation from Bitcoin Gold.
These hacks have damaged the reputation of Bitcoin Gold: Earlier, BTG worth $3.3 million was stolen after hackers tricked users into downloading a fake wallet. These hacks have declined BTG’s rank in the crypto market, as it is currently ranked 43rd, according to Coin360.
Apple MacOS Hack, Corporation Hack, Malware Attack
North Korea is known for its notorious acts, as it continues to exploit the crypto market with illegal activities and constant attempts of hacking various systems. In recent news, hackers sponsored by North Korea, disguised under the so-called Lazarus Group, tried to hack into Macs via fake cryptocurrency software.
The U.S. government and numerous other cybersecurity companies have claimed that the Lazarus Group is an organization sponsored by North Korea. The group tried to hack Apple’s macOS by creating a fake company with an official website and wrote an open-source code for a cryptocurrency trading app that was uploaded on GitHub.
Within this code was a piece of malware that, when downloaded, would attack Apple computers and give the hacker access to do anything on the system. According to a United Nations report, North Korea has made about $2 billion by hacking various traditional exchanges and banks.
Apple products are known for their security and functionality, and the company even claims that Apple products cannot be hacked or manipulated.
The Infamous Mt. Gox Hack, $460 Million Stolen
Mt. Gox, was leading the crypto exchange market in 2013, with over 70% of the world’s Bitcoin exchanges taking place on its platform. Mt. Gox was first struck was in 2011, when 80,000 BTC was stolen from the exchange’s founder, Jeb McCaleb, who was in the process of selling the exchange to Mark Karpeles. Shortly after, a hacker was able to get into McCaleb’s account, which still had admin access, and artificially dropped the price of Bitcoin from around $17 to just about $0.01, allowing for about 2,000 BTC to be bought and transferred out of the exchange before the attack was noticed and resolved.
The most significant attack, however, occurred over a number of years — 2011 to 2014, when it finally came to light that the exchanges cold wallets were virtually empty. During that time, 850,000 Bitcoins were stolen from the exchange, 750,000 Bitcoins of which were owned by users, while the rest were the exchange’s. The value of the stolen Bitcoins at the time was $460 million, making it the most significant amount of Bitcoins ever stolen.
Mark Karpeles, who was the head of Mt. Gox, went on trial in Japan. After such a colossal failure of Mt. Gox as a crypto exchange platform, the rules and regulations related to cryptocurrencies were changed in the country.
In 2014, Mt. Gox was forced to file for bankruptcy and was forced to shutdown.
During the investigation, 200,000 Bitcoin were discovered, but these Bitcoin have not yet been distributed among users as compensation.
There is a lot of complexity with Mt Gox, so it is hard to cover it in only 3-4 paragraphs.
Conclusion
Cryptocurrency assets are a modern form of investments by many people, as they have moved from traditional investments like real estate and gold. But with the ease of online transactions comes the risk of getting attacked by hackers and malware. It is essential to use proper software that provide two-factor authentication service, such as Google Authenticator, and other services like email verification or IP address tracking.
Updated: 12-19-2019
Hashpower Broker NiceHash Can’t Promise To Fully Reimburse Hack Losses
The hashpower rental marketplace NiceHash, which was hacked in Dec. 2017, says it may not be able to fulfill its pledge to fully reimburse affected users.
In a blog post published on Dec. 18, NiceHash said its repayment program would be frozen at its current level of 82% successful reimbursement and that its promise to repay 100% of lost funds will not be realized “in the foreseeable future.”
No Time Estimates For Possible Eventual Repayment
Established in 2014, NiceHash is a marketplace that brokers between miners and investors, allowing owners of mining hardware to rent out their hash power to interested parties.
In Dec. 2017, the service lost over $60 million in Bitcoin (BTC) in a major hack. It subsequently pledged to fully reimburse affected users, launching a repayment program in Feb. 2018.
According to NiceHash, 82% of lost funds have by now been successfully reimbursed, yet despite having been committed to periodically repay the outstanding balance, the company now says it cannot uphold this commitment:
“We have been repaying the old balance to our users through our fees and thus cutting our income. Our income and thus Repayment program assets are subject to taxation. The current state of the Repayment program is at 100,04% of the original loss value in our accounting books.”
NiceCash adds that the decision was taken in order to allow it to stay in business with enough cash flow for the future development of its services.
The company says it will continue with the legal procedures tied to the repayment program and that should the market see “a positive development” in 2020, it will resume its reimbursement efforts.
All information regarding the repayment program will meanwhile remain visible in users’ wallets, but as of now, the firm says it is unable to give any time estimates for possible eventual reimbursement.
Easy Access Mining
This spring, as part of an overview of students’ crypto mining, Cointelegraph reported on the popularity of Nicehash and similar services that offer a low-barrier entry point to mining for those without access to sophisticated hardware.
Notwithstanding his access to “free” (campus) electricity, one interviewee — a University of Mississippi pharmaceutical sciences student — nonetheless told Cointelegraph he had eventually been forced to abandon mining because of the continuously high strain on processing power and “overinflated” GPU prices.
New Crypto Mining Malware,New Crypto Mining Malware,New Crypto Mining Malware,New Crypto Mining Malware,New Crypto Mining Malware,New Crypto Mining Malware,New Crypto Mining Malware,New Crypto Mining MalwareNew Crypto Mining Malware,New Crypto Mining Malware,New Crypto Mining Malware
Related Articles:
Cyber-Security Alert!: FEMA Leaked Data Of 2.3 Million Disaster Survivors (#GotBitcoin?)
DMV Hacked! Your Personal Records Are Now Being Transmitted To Croatia (#GotBitcoin?)
Alert! 540 Million Facebook Users’ Data Exposed On Amazon Servers (#GotBitcoin?)
Facebook Says Millions of Users’ Passwords Were Improperly Stored in Internal Systems (#GotBitcoin?)
Facebook Bug Potentially Exposed Unshared Photos of Up 6.8 Million Users (#GotBitcoin?)
Lithuanian Man Pleads Guilty In $100 Million Fraud Against Google, Facebook (#GotBitcoin?)
Ad Agency CEO Calls On Marketers To Take Collective Stand Against Facebook (#GotBitcoin?)
Advertisers Allege Facebook Failed to Disclose Key Metric Error For More Than A Year (#GotBitcoin?)
Hack Alert! Buca Di Beppo, Owned By Earl Enterprises Suffers Data Breach Of 2M Cards (#GotBitcoin?)
Equifax, FICO Team Up To Sell Your Financial Data To Banks (#GotBitcoin?)
SEC Hack Proves Bitcoin Has Better Data Security (#GotBitcoin?)
Thieves Can Now Nab Your Data In A Few Minutes For A Few Bucks (#GotBitcoin?)
Maxine Waters (D., Calif.) Rises As Banking Industry’s Overseer (#GotBitcoin?)

Leave a Reply
You must be logged in to post a comment.