Maintain Your Privacy And Security During A Protest (#GotBitcoin?)
In the Interest of Free Speech and using your Right to Protest, it is important to understand that participating in these events can lead to active tracking, and data pulling by government organizations. Maintain Your Privacy And Security During A Protest (#GotBitcoin?)
The past has shown that this data is easily tracked and your location ceases to be a private thing. The act of protesting is to enact a right to free speech and assembly, since when does this mean a right to being tracked as well?
Associated Resources:
Blockchain Technology Counters US Anti-Message Encryption Bill, AKA EARN IT Act (#GotBitcoin?)
Cryptocurrency Technology Finds New Use Tackling Coronavirus
Here Are Some Steps That We Have Gathered To Protect You If And When You Choose To Publicly Take To The Streets:
- If you are going to carry your phone with you, turn off your GPS, WiFi, and Bluetooth. All three of these can be used against you to locate your phone because they emit a signal while on. Turning off should be a daily practice already, but if it’s not, start now.
- Store your phone in our Mobile-Blok Pouch , this allows your phone to be completely untraceable. Blocking all signals going in or out, and allowing access to your device when you feel safe to again. Know that your location and data are going to be safe and secure while you are out there practicing your rights.
- Many outlets recommend airplane mode, but your phone can still be traced in this mode. This may turn off cellular, but that does not mean GPS or Bluetooth is turned off.
- Turn Off Face ID or Touch ID. A more forceful law enforcement member could place the phone in front of your face or your finger on the bottom. What was designed to help us, hurts us in this instance.
- Use secure messaging services. Applications such as Signal can ensure that your messages are only seen for a short period of time by the other party. This will allow you to go that extra step when you are unsure of how the other party is approaching their security.
In the last few weeks, we have been heavy on how COVID-19 and Contact Tracing could forever change our privacy and its relationship with modern technology.
This is not something to take lightly, as Government-mandated tracking is a scary thought for us and many other folks.
What if you found out that the application you downloaded to help get your morning coffee was also tracking you? Check out this recent finding that Tim Horton’s was tracking each of their users every few minutes to see if they were visiting competitors.
We hear about companies using our data all the time, but putting a face to the name makes it that much more real.
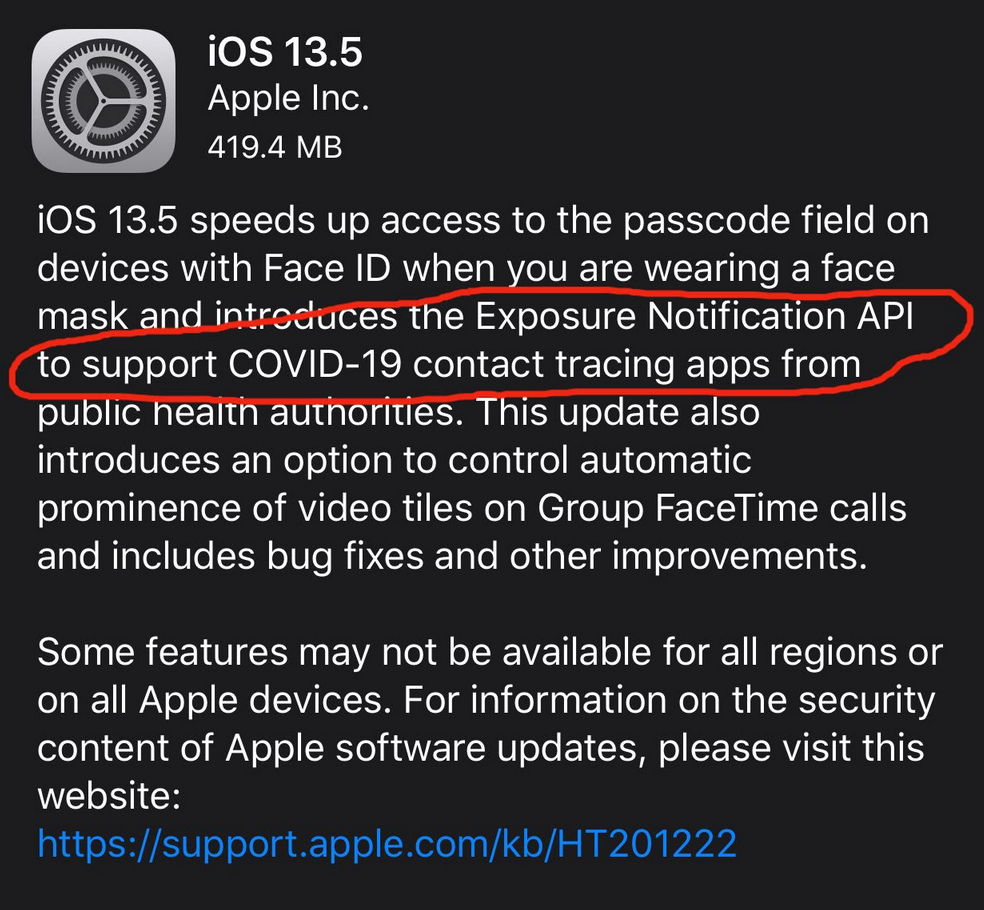
What We Have Been Dreading Has Arrived!
Apple officially launched contact tracing for all Apple devices in the latest update. As specified in the update specifics, there is new background software that allows contact tracing apps to track your location and who you’ve been around via Bluetooth.
This data is then uploaded anonymously centrally to a database to be sorted through, with the selected people being notified. Doesn’t a central database of all our whereabouts sound scary?
Multiple countries and specific states have moved forward on either their own applications or requirements of existing ones for employment and entry. This is being rolled out in phone-based applications and in more extreme cases, ankle monitors.
Many countries are requiring forced quarantine at entry, with the potential to be tracked by local police, and if you break this, you are subject to being apprehended.
We’ve been talking about this for weeks, but the reality is now. This is a big step towards infringing on our civil liberties during and after the pandemic.
Updated: 6-14-2020
How Political Groups Are Harvesting Data From Protesters
Voting and advocacy groups track cellphones of participants and send messages; the tactics are ‘deeply spooky yet extremely helpful,’ says one user.
The protests continuing around the country are historic displays of social action. For political operatives, the mass gatherings are also a unique opportunity to harvest data on potential voters.
Advocacy and voter-registration groups are gathering a trove of data from protests by tracking the cellphones of participants and sending them messages about registering to vote or taking other actions. The tactics, which one user called “deeply spooky yet extremely helpful” are the latest example of ways political groups are using cellphone data to target voters.
Tracking individuals through location data gathered by apps on their phones, often referred to as geofencing, has been used by businesses for years and has more recently caught on among political groups. That data allows firms to reach people’s phones with ads or other messaging—in real-time or later—without identifying individuals, proponents say.
Political groups say the protests following the killing of George Floyd while in police custody, along with earlier lockdown protests, are opening up fresh opportunities to reach people who may not be registered to vote or weren’t previously politically active.
“When these protests emerged, it was eye-opening for folks to understand, wow, people are gathering again,” said Quentin James, founder and president of the Collective, which works to elect African-Americans. Mr. James’s group is using the data gathered to target voter-registration messages to people who have been at protest locations. “We want to make sure we’re using all available tools in our toolbox to make sure we’re reaching the right people.”
Reaching those individuals is especially critical, groups say, since in-person voter registration drives were halted by coronavirus. Plus, with Americans staying home for the past few months to prevent the virus’s spread, organizations have little other recent data about people’s movements.
Geofencing has become increasingly common in politics, and was expected to play a big role in the 2020 election even before a pandemic and social unrest upended the campaign season.
Some argue that collecting protesters’ location data is akin to surveillance.
X-Mode Social Inc., which collects location data from software built into about 300 apps, has rejected requests for data on phones in protest locations, according to Joshua Anton, its chief executive. Mr. Anton wrote on LinkedIn last week that X-Mode believes in “withholding [data] from use cases we believe could bring harm,” also citing its decision not to monitor religious institutions or elections. He asked peer firms “to protect the data of those fighting against racial inequality.”
The protests continuing around the country are historic displays of social action. For political operatives, the mass gatherings are also a unique opportunity to harvest data on potential voters.
Advocacy and voter-registration groups are gathering a trove of data from protests by tracking the cellphones of participants and sending them messages about registering to vote or taking other actions. The tactics, which one user called “deeply spooky yet extremely helpful” are the latest example of ways political groups are using cellphone data to target voters.
Tracking individuals through location data gathered by apps on their phones, often referred to as geofencing, has been used by businesses for years and has more recently caught on among political groups. That data allows firms to reach people’s phones with ads or other messaging—in real-time or later—without identifying individuals, proponents say.
Political groups say the protests following the killing of George Floyd while in police custody, along with earlier lockdown protests, are opening up fresh opportunities to reach people who may not be registered to vote or weren’t previously politically active.
“When these protests emerged, it was eye-opening for folks to understand, wow, people are gathering again,” said Quentin James, founder and president of the Collective, which works to elect African-Americans. Mr. James’s group is using the data gathered to target voter-registration messages to people who have been at protest locations. “We want to make sure we’re using all available tools in our toolbox to make sure we’re reaching the right people.”
Reaching those individuals is especially critical, groups say, since in-person voter registration drives were halted by coronavirus. Plus, with Americans staying home for the past few months to prevent the virus’s spread, organizations have little other recent data about people’s movements.
Geofencing has become increasingly common in politics, and was expected to play a big role in the 2020 election even before a pandemic and social unrest upended the campaign season.
Some argue that collecting protesters’ location data is akin to surveillance.
X-Mode Social Inc., which collects location data from software built into about 300 apps, has rejected requests for data on phones in protest locations, according to Joshua Anton, its chief executive. Mr. Anton wrote on LinkedIn last week that X-Mode believes in “withholding [data] from use cases we believe could bring harm,” also citing its decision not to monitor religious institutions or elections. He asked peer firms “to protect the data of those fighting against racial inequality.”
Keith Chen, a behavioral economics professor at University of California, Los Angeles, who has used cellphone data in his research, said such data can be useful. But given the lack of rules around informed consent—protesters may not even know their data is being used—he said there is little to protect others from using data to identify individual protesters.
“To the degree that this becomes very common, I do worry that it starts to put a chill on people’s willingness to peaceably assemble,” said Mr. Chen of the protest data gathering.
Privacy experts suggest those who don’t want to be tracked can turn off location services on their phones or adjust app location privileges in cellphone settings.
IQM Corp., a political ad-tech firm, has received a number of requests from PACs and advocacy groups to geofence recent protests, said Kris Qiu, the company’s co-founder and chief operating officer. Mr. Qiu said both liberal and conservative groups have contacted him.
It couldn’t be determined whether political campaigns have sought to use recent protester data to target messages.
Democratic voter-registration outfit Field Team 6 is using Facebook Inc. advertising tools to direct ads to users within a specific geographic area of recent protests, said founder Jason Berlin. The group switched to digital earlier this year after coronavirus halted its voter-registration efforts at grocery stores, college campuses and other physical locations.
Mr. Berlin’s group targeted voter-registration ads to Facebook users whose cellphones were present in the areas of demonstrations in Detroit, Houston, Raleigh and Tallahassee, cities located in battleground states the group is focused on for the November presidential and Senate races.
“It’s deeply spooky yet extremely helpful,” Mr. Berlin said. “We’re actively looking at where the protests are popping up and then readjusting our targets.”
Shomik Dutta, a former Obama aide and co-founder of Higher Ground Labs, a progressive political tech incubator, said he would encourage Democrats to use geofencing to reach more voters, but said it is important that companies operate legally and obey privacy laws.
He noted that Republicans are using geofencing to their advantage, such as the Trump campaign’s data-gathering efforts to better reach voters at rallies and other events.
The Collective worked with VoteMAP, a technology firm specializing in audience creation and mobile outreach for progressives, to collect location data up to a mile around protests in Columbus, Milwaukee, Minneapolis and Washington, D.C., between May 29 and May 31, said Jeremy Fair, co-founder of VoteMAP, which is owned by technology firm Datum Tech Inc.
In efforts to better understand where the mobile-phone users are based, VoteMAP examined device location 48 hours before the protest and 48 hours after, Mr. Fair said. VoteMAP worked with at least one other client, progressive group the Committee to Protect Medicare and Affordable Care, to gather location data from cellphone users at lockdown protests several weeks ago in attempts to determine the potential spread of coronavirus from users gathering at the demonstrations.
Mr. Fair said VoteMAP accesses and aggregates data from thousands of apps that may include gaming, entertainment and weather. VoteMAP says the app publishers are responsible for terms and compliance with necessary laws and privacy practices.
In the past two weeks, VoteMAP has served ads to more than 14,000 mobile devices believed to be in protest areas. “Let’s keep the same energy in November…at the ballot box…Vote Black voices and representation in power,” flashes the Collective’s ad on three different slides, with the last including a link to register to vote, according to images of the ad reviewed by The Wall Street Journal.
The Collective’s Mr. James said its “Vote to Live” campaign will run through September and aims to register 250,000 black Americans. Former New York City Mayor Michael Bloomberg donated $2 million in March to the Collective’s efforts to register more black voters.
“We never had the funding and the resources to really engage in these types of techniques before,” The Collective’s Mr. James said.
Updated: 6-17-2020
Decentralized Tech Can Protect Activists From Social Media Crackdowns
As protests against police brutality continue in the U.S., privacy advocates warn of the risks posed by centralized social media platforms.
The protests in the United States against police brutality and systemic racism sparked by the murder of George Floyd by former Minneapolis police officer Derek Chauvin on May 25 are showing no signs of stopping.
Rallies and marches have continued in many cities for three weeks now, with events organized in all 50 states as well as in at least 40 countries around the world. Another killing of an African American man in Atlanta, Rayshard Brooks — who was shot in the back twice while fleeing police — has only fed more fuel to the fire.
Most events have been organized and promoted using centralized, corporate-owned social media platforms such as Facebook, Instagram and Twitter. The ease of communication and ability to connect with one another that these large platforms provide have been a major driving force in enabling the activists to mobilize quickly and successfully.
As cities and states begin to unveil policing reforms in response to the widespread protests, with the Minneapolis City Council going so far as voting to disband its police department, privacy advocates have argued that those who are serious about resisting censorship and government surveillance should be wary of centralized platforms because they are controlled, for-profit entities and are subject to coercion from governments. Instead, they point to decentralized technologies and platforms as having the potential to be a safer way for activists to communicate.
Centralized Social Media Presents Risks
As of 2019, an estimated 72% of all U.S. adults use social media, and given the coronavirus-related lockdown, people have been more connected than ever.
Organizers of the Black Lives Matter movement have relied on Instagram’s “stories” feature to notify protest attendees of location changes, while police scanner apps were downloaded during the initial days of the protests by hundreds of thousands of people, many of whom have taken to Twitter to assume “scanner duty” and broadcast the movements of police officers for protesters.
These platforms give activists and dissidents an unprecedented ability to communicate and organize, but they are run by for-profit corporations that are ultimately beholden to shareholders and governments. This, privacy advocates argue, represents a fundamental flaw in their ability to be secure and resistant to censorship.
Matthew Hodgson, a technical co-founder of the decentralized Matrix communications protocol, told Cointelegraph that these platforms do not serve end users because their business models are to present regular users with ads. In order to best deliver ads, they collect large amounts of user data that accumulates and is at risk of being abused.
Since social media companies are also privately owned entities, they can revoke a user’s access to their platforms for any reason, especially if they are seen as too controversial or “non-mainstream,” pointed out Bruce Schneier, a security technologist and author. Those decisions affect speech, assembly and the ability to organize, he said, adding: “That’s a very dangerous kind of system to pin democracy on.”
Oftentimes, the decision to remove a user or their content is typically made by underpaid content moderators in developing countries or by an algorithm, rather than a company’s leadership. Cointelegraph itself recently found its recent Bitcoin (BTC) halving event canceled by YouTube mid-livestream for being “harmful content.”
Sharon Bradford Franklin, policy director of the New America’s Open Technology Institute think tank, told Cointelegraph that algorithmic decisions often result in “discriminatory targeting of messages, amplification of harmful content, or silencing of marginalized communities,” and that platforms have a responsibility to “take steps to audit and modify their algorithms, and avoid suppressing protest movements.”
Centralized Companies Are Beholden To Governments
Shareholders are not the only group that corporations must answer to. These global organizations are also required to follow the laws of the nations in which they operate and can face intense pressure to censor content governments deem subversive. The messaging app Telegram has been banned in Russia since 2018, China’s “Great Firewall” blocks access to thousands of websites, and even the video conferencing platform Zoom admitted to deactivating U.S.-based accounts on behalf of the Chinese government.
As suggested by President Donald Trump on May 27, the U.S. government can implement a similar approach and ban specific apps or websites that are used by activists to dissent and organize protests. Trump then acted on the suggestion by signing an executive order seeking to remove existing protections that shield social media companies from lawsuits.
Luke Stokes, managing director for the foundation for interwallet operability and a witness for the Hive blockchain — a decentralized social network — told Cointelegraph that as the U.S. has gotten away with doing many things never thought possible, it would not surprise him if the nation’s government took intentional action to censor online platforms. However, doing so would be a slippery slope toward the erosion of citizens’ rights, he explained:
“Any form of restricting freedom of speech is dangerous because it is the right that enables us to communicate the reality of every other right. When those with a monopoly on the initiation of force control the narrative, that is a very dangerous thing for a free people.”
According to Franklin, however, the even bigger risk is that officials might try to ban end-to-end encryption and force tech companies to weaken the security of their products. Franklin was referring to Republican Senator Lindsay Graham’s introduction of the Eliminating Abusive and Rampant Neglect of Interactive Technologies Act, otherwise known as the EARN IT Act, which would effectively ban the use of end-to-end encryption by stripping legal protections from companies that do not comply with a list of government-approved best practices. Yet to be determined, these guidelines are widely expected to include government access to the content of all messages. Franklin told Cointelegraph:
“End-to-end encryption is vital to the ability of activists and ordinary people alike to communicate securely. Particularly as our country confronts police violence and pervasive surveillance, it is critical that people are able to express themselves safely and securely.”
While the bulk of organizing has remained public on unencrypted social media platforms, the number of new users downloading the encrypted messaging app Signal has skyrocketed by 259% since the start of the protests. The security-focused app uses end-to-end encryption to protect messages and phone calls, and has long been a favorite of whistleblower Edward Snowden.
However, apps such as Signal that are centrally owned may not be as reliable as some hope. Signal has stated that if the EARN IT Act is signed into law, “it would not be possible for a small nonprofit like Signal to continue to operate within the United States.”
Decentralized Platforms May Provide A Solution
Advocates of decentralization argue that the solution to the issue of profit-driven, algorithmic or government-imposed censorship of activists on centralized platforms lies in embracing decentralized alternatives. Indeed, there have been use cases of social movements using decentralized technology to organize.
In Hong Kong, protesters have been using the app Bridgefy to communicate via Bluetooth-based mesh networks that send messages offline, bypassing the Great Firewall and reducing the risk of being shut down. Peer-to-peer mesh networks are composed of individual nodes that all connect into a “mesh.” If one node is not directly connected to another, messages will hop from node to node until they reach their intended targets.
In Spain, the Catalan separatist group Tsunami Democratic developed an app built on top of the free software Retroshare, which allows it to create a private, encrypted, peer-to-peer network. New users must scan a QR code of a user that has already joined the network in order to access it. Once instructed, users provide their general geographic location so that they can be activated for regional activities.
Hodgson believes that decentralized communications platforms have the ability to change the way in which social movements are organized. The Matrix communications protocol that he helped develop was designed specifically to be censorship-resistant and give as much privacy and control to each group of users as possible. Hodgson told Cointelegraph:
“It is vital for social movements to be able to communicate privately and without leaving a metadata footprint, otherwise you are simply accumulating data in a centralised messaging service which could be abused, deliberately or otherwise, by that centralised service or the jurisdiction under which they operate.”
According to Stokes, in order to be truly censorship-resistant, a communications platform must not only have decentralized hardware but also be decentrally governed, “if there’s a single point of failure a government or powerful entity can shut down or censor, then it is not a resilient or censorship resistant system,” he said. Stokes believes that decentrally governed blockchain-based platforms have the potential to be the most resilient:
“It’s the individuals participating in governance according to the consensus algorithm that give a blockchain censorship resistance. Those could be miners in PoW, stakers in PoS, or voters/stakers in DPoS.”
Decentralized Tech For The Bad
There have certainly been a number of instances in which criminal or terrorist groups have used encrypted and/or decentralized technology to facilitate their activities. In 2008, an al-Qaeda-linked group released an app called “Mujahideen Secrets 2” — an update of the original app released in 2007 — which promised to be “the first Islamic program for secure communications through networks with the highest technical level of encoding.”
In an even more complex operation, the Zeta drug cartel in Mexico kidnapped and enslaved engineers in order to build a do-it-yourself, encrypted, decentralized radio network that relied on hundreds of antennas, signal relay stations and solar power. Most malicious actors, however, opt for existing technologies such as the anonymity-centric Tor browser to host illicit sites on the darknet, often financed through cryptocurrency payments in BTC, Ether (ETH) or Monero (XMR).
The Islamic State group has also experimented with several decentralized platforms including Riot.im, a free, open-source messaging app based on the Matrix protocol that boasts complete privacy. Hodgson — who is also CEO of New Vector, the developing company of Riot.im — said that while it is impossible to stop bad people from using open networks, developers can create tools that allow users to curate content for themselves and filter out anything considered to be bad. He added that the Matrix community is actively building tools into the protocol to facilitate the process.
Everything in society, including “infrastructure, […] airplanes, cars, restaurants, telephones,” can be used for either good or bad, argued Schneier, but “the reason society works is that there are way more good people than bad people.” He added that even though privacy-focused technology can be used for nefarious purposes, nations are safer when everyone is secure than when everyone has the same central vulnerabilities.
Technology Is Not A Panacea
While technology may have the ability to allow activists to organize securely and away from the prying eyes of corporations and governments, decentralized and privacy-focused apps should not be considered panaceas. Movements for social change, at their core, revolve around the organization of people. Ross Schulman, the senior policy counsel and senior technologist of New America’s Open Technology Institute, told Cointelegraph:
“To the extent that these technologies [P2P and decentralized apps] enable greater abilities for direct and protected communications between people and provide the infrastructure for growing and managing communities, there is the potential for them to influence how social movements grow and spread. With that said, the hard part of organizing is always in the connections that we build with our neighbors in our communities and no technology can replace that if it is missing.”
If civil liberties were to deteriorate to the point where activists could longer organize via centralized platforms without the threat of arrest or death, whether the apps and protocols are centralized or decentralized may not make as big of a difference as some might think. According to Schneier, no piece of software will ever truly protect one against government oppression. “Computer security’s not going to save you,” he said. “If we actually move into that level of police state, the app will only save you in the movies.”
Updated: 9-11-2020
An Application Is No Longer Needed For Contact Tracing, How Are You Responding?
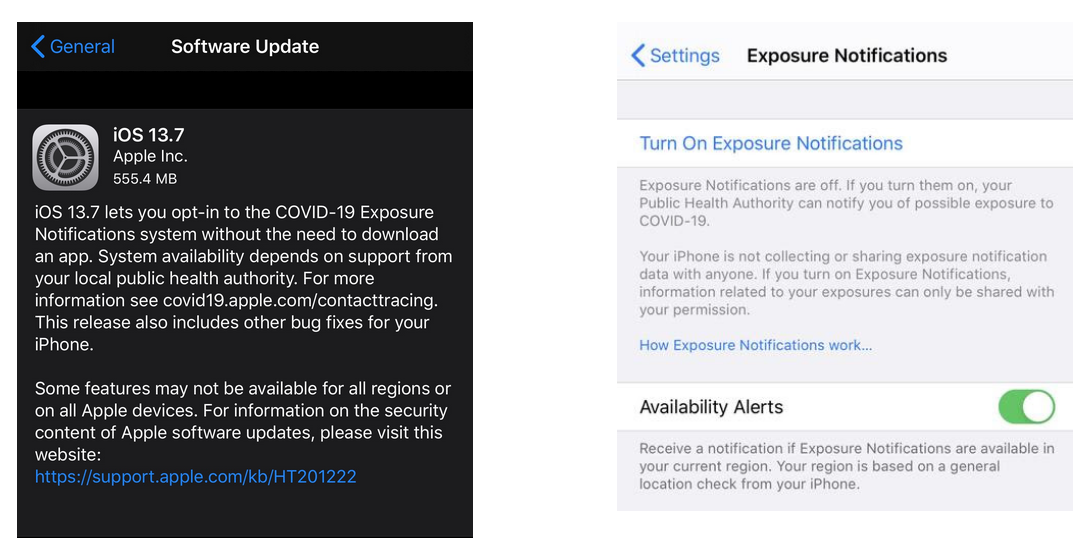
Last week, Apple made the next step in universal Contact Tracing.
They removed the need for a standalone contact tracing application and installed the API and capabilities to everyone that chose to update their phone.
This is an unprecedented step when it comes to everyone’s personal privacy. As well as a further step to policies that may not be reversed in the future post-pandemic.
Presently, this is turned off when installed but how can we be sure? Is there a secret backdoor that allows this to be turned on without our knowledge?
“Anonymous” GPS data sets are not as secure as they are made out to be, so what are you doing?
We’ve been long time advocates of daily use of our Mobile-Blok Pouch, but the time is now to act before your privacy completely disappears.
Related Articles:
Borrower, Beware: Credit-Card Fraud Attempts Rise During The Coronavirus Crisis
Report Says Chinese And Iranian Hackers Seek To Steal Coronavirus Research
28,000 GoDaddy Hosting Accounts Compromised
Some States Dabble In Online Voting, Weighing Pandemic Against Cybersecurity Concerns
Antonopoulos: Chainalysis Is Helping World’s Worst Dictators & Regimes (#GotBitcoin?)
Survey Shows Many BTC Holders Use Hardware Wallet, Have Backup Keys (#GotBitcoin?)
Blockfolio Quietly Patches Years-Old Security Hole That Exposed Source Code (#GotBitcoin?)
Apple iPhone May Be Vulnerable To Email (Mail) Hack
Gates Foundation, WHO And Wuhan Institute of Virology All Hacked!
Google Hack Requires That You Updated Chrome Browser Now To Version: 81.0.4044.113
Privacy-Oriented Browsers Gain Traction (#GotBitcoin?)
Can Blockchain Technology Counter US Anti-Message Encryption Bill? (#GotBitcoin?)
Chinese Military Turns To U.S. University To Conduct Covert Research
CIA Has Had Keys To Global Communication Encryption Since WWII
Hostile Spies Target U.S. With Cyber, Encryption, Big Data, Report Finds
Hackers Stole And Encrypted Data of 5 U.S. Law Firms, Demand 2 Crypto Ransoms
Ex-CIA Engineer Goes On Trial For Massive Leak
Multi One Password (Portable App)
After He Fell For A $40K Phone Scam, His Bank Offered To Help—If He Stayed Quiet (#GotBitcoin?)
Your PGP Key? Make Sure It’s Up To Date
Bezos’ Phone Allegedly Hacked By Account Associated With Crown Prince
Major Companies Shared Vulnerability Used In Travelex Cyberattack (#GotBitcoin?)
Microsoft Releases Patch To Patch Windows Flaw Detected By NSA
VPN Tier List 2020 (Comparison Table)
SEC Market-Surveillance Project Hits Snag Over Hacker Fears
Inside China’s Major US Corporate Hack
Twitter Bug Exposed Millions of User Phone Numbers
U.S. Cyber Officials Give Holiday Shopping Advice For Consumers
Is Cayla The Toy Doll A Domestic Spy?
Google’s “Project Nightingale” Faces Government Inquiry Over Patient Privacy.
Which Password Managers Have Been Hacked?
DNS Over HTTPS Increases User Privacy And Security By Preventing Eavesdropping And Manipulation
Russia Steps Up Efforts To Shield Its Hackers From Extradition To U.S.
Barr Revives Debate Over ‘Warrant-Proof’ Encryption (#GotBitcoin?)
Should Consumers Be Able To Sell Their Own Personal Data?
Doordash Says Security Breach Affected Millions Of People (#GotBitcoin?)
Fraudsters Used AI To Mimic CEO’s Voice In Unusual Cybercrime Case (#GotBitcoin?)
Pearson Hack Exposed Details on Thousands of U.S. Students (#GotBitcoin?)
Cyber Hack Got Access To Over 700,000 IRS Accounts (#GotBitcoin?)
Take A Road Trip With Hotel Hackers (#GotBitcoin?)
Hackers Target Loyalty Rewards Programs (#GotBitcoin?)
Taxpayer Money Finances IRS “Star Trek” Parody (#GotBitcoin?)
IRS Fails To Prevent $1.6 Billion In Tax Identity Theft (#GotBitcoin?)
IRS Workers Who Failed To Pay Taxes Got Bonuses (#GotBitcoin?)
Trump DOJ Declines To Charge Lois Lerner In IRS Scandal (#GotBitcoin?)
DMV Hacked! Your Personal Records Are Now Being Transmitted To Croatia (#GotBitcoin?)
Poor Cyber Practices Plague The Pentagon (#GotBitcoin?)
Tensions Flare As Hackers Root Out Flaws In Voting Machines (#GotBitcoin?)
Overseas Traders Face Charges For Hacking SEC’s Public Filings Site (#GotBitcoin?)
Group Hacks FBI Websites, Posts Personal Info On Agents. Trump Can’t Protect You! (#GotBitcoin?)
SEC Hack Proves Bitcoin Has Better Data Security (#GotBitcoin?)
Your Questions And Comments Are Greatly Appreciated.
Monty H. & Carolyn A.
Go back


Leave a Reply
You must be logged in to post a comment.