Online Privacy Tools And Tips

Moxie Marlinspike : The Coder Who Created Encrypted Tools That The NSA/FBI Can’t Crack. Online Privacy Tools and Tips

In the past decade, Moxie Marlinspike has squatted on an abandoned island, toured the U.S. by hopping trains, he says, and earned the enmity of government officials for writing software.
Mr. Marlinspike created an encryption program that scrambles messages until they reach the intended reader. It’s so simple that Facebook Inc.’s WhatsApp made it a standard feature for many of the app’s 800 million users.
Related:
RollingStone Report: FBI Can Get Your WhatsApp Data in Real Time
Thought Leaders In Crypto-Currency Privacy Space Talk About The Next Century of Money (#GotBitcoin)
Researchers Use GPU Fingerprinting To Track Users Online
Ultimate Resource On Private Blockchain Brave Browser
How To Protect Your Online Privacy While Working From Home
The Pandemic Turbocharged Online Privacy Concerns
California Lawmaker Says National Privacy Law Is a Priority
How To Turn On Advanced Data Protection For iCloud
The software is effective enough to alarm governments. Earlier this year, shortly after WhatsApp adopted it, British Prime Minister David Cameron called protected-messaging apps a “safe space” for terrorists. The following week, President Barack Obama called them “a problem.”
That makes the lanky, dreadlocked and intensely private coder a central figure in an escalating debate about government and commercial surveillance. In a research paper released Tuesday, 15 prominent technologists cited three programs relying on Mr. Marlinspike’s code as options for shielding communications.
His encrypted texting and calling app, Signal , has come up in White House meetings, says an attendee. Speaking via video link last year as part of a panel on surveillance, former National Security Agency contractor Edward Snowden, who leaked troves of U.S. spying secrets, urged listeners to use “anything” that Mr. Marlinspike releases.
That endorsement was “a little bit terrifying,” Mr. Marlinspike says. But he says he sees an opening, following Mr. Snowden’s revelations, to demystify, and simplify, encryption, so more people use it. He finds most privacy software too complicated for most users.
The former teenage hacker studies popular apps like Snapchat and Facebook Messenger, trying to understand their mass appeal. He says he wants to build simple, “frictionless” apps, adopting a Silicon Valley buzzword for “easy to use.”
“I really started thinking about, ‘How do I be more in touch with reality?’ ” he says.
Those who know him say he has both the will and the technical chops to popularize complex technology.
A few years ago, Matthew Green, a cryptographer and professor at Johns Hopkins University, unleashed his students on Mr. Marlinspike’s code. To Prof. Green’s surprise, they didn’t find any errors. He compared the experience to working with a home contractor who made “every single corner perfectly squared.”
During chats about surveillance and security, Mr. Marlinspike also won over Morgan Marquis-Boire, a researcher who has worked on security for Google Inc. In a fellowship recommendation for Mr. Marlinspike, Mr. Marquis-Boire wrote, “There are very few people who write privacy tools that I trust, and Moxie is one of them.”
Mr. Marlinspike says it is more important that users trust his software than trust him. “It’s easier to trust that I haven’t made mistakes,” he says.
Even by the standards of privacy activists, Mr. Marlinspike is unusually secretive about himself. He won’t give his age, except to say he is “in his 30s.” In an interview, he wouldn’t say whether Moxie Marlinspike was his birth name. In an 2011 online interview with the website Slashdot , however, he wrote, “the name my parents put on my birth certificate is ‘Matthew.’ ” Friends and former associates say they know him only as Moxie.
Consumer encryption tools like Mr. Marlinspike’s have been around since the early 1990s, but most are so cumbersome that few people use them. A popular email-encryption program, PGP , or Pretty Good Privacy , requires users to swap a series of thousands of random letters and numbers with anyone they wish to contact. Sending a message requires several clicks, a password, and sometimes, copying and pasting.
A young Mr. Marlinspike once thought users would eventually adopt such tools. “That hasn’t really worked out,” he says now.
Phil Zimmermann, who invented PGP, says he rarely uses it because “it doesn’t seem to work well on the current version of MacIntosh.”
Such headaches have limited the use of encryption to a level law enforcement has mostly learned to live with. Big technology companies like Google, Microsoft Corp. and Yahoo Inc. usually maintain access to customer messages and provide user emails and contact information to authorities when faced with a court order, even if they oppose it. Consumer services like these typically haven’t had strong encryption.
Adding easy-to-use encryption that companies can’t unscramble to products used by millions changes that calculus. After Apple Inc. tweaked its iPhone software so that the company could no longer unlock phones for police, the director of the Federal Bureau of Investigation accused Apple of aiding criminals. Apple Chief Executive Tim Cook counters that he is defending user privacy.
The incident sparked a continuing war of words between Silicon Valley and Washington.
“Encryption has moved from something that is available to something that is the default,” FBI Director James Comey told a congressional panel Wednesday. “This is a world that in some ways is wonderful and in some ways has serious public-safety ramifications.”
Technology companies, once cozy with Washington, sound increasingly like Mr. Marlinspike. Apple, Facebook, Google and others are resisting efforts to give the government access to encrypted communications.
Last fall, WhatsApp added Mr. Marlinspike’s encryption scheme to text messages between users with Android smartphones, but there is no easy way to verify that the encryption software is actually turned on. The app maker, acquired by Facebook for $22 billion last year, plans to extend encryption to images and iPhone messages, a person familiar with the project said.
Behind the clash lurks this reality: Even if the big tech companies come around, there are others like Mr. Marlinspike who will pick fights with code.
Mr. Marlinspike argues for safe spaces online. His personal Web address is thoughtcrime.org , a reference to George Orwell’s “1984.”
As a teenager, Mr. Marlinspike says, he was more interested in breaking software than creating it. He turned to protecting data as he grew more concerned about surveillance.
He moved to San Francisco in the late 1990s and worked for several technology companies before the dot-com bust, including business-software maker BEA Systems Inc . Since then, he often has lived on the edge of the Bay Area’s tech-wonk scene.
During the mid-2000s, he and three friends refurbished a derelict sailboat and spent summers being blown around the Bahamas, without a backup motor, as depicted in a home movie Mr. Marlinspike posted online.
In 2010, Mr. Marlinspike’s company, Whisper Systems , released an encryption app, TextSecure . Twitter Inc. bought Whisper Systems for an undisclosed sum in 2011 primarily so that Mr. Marlinspike could help the then-startup improve its security, two people familiar with the transaction said. He worked to bolster privacy technology for the social-media firm, leaving in 2013.
Around that time, the State Department was looking to use technology to support pro-democracy movements overseas. Mr. Marlinspike’s work caught the attention of Ian Schuler, manager of the department’s Internet freedom programs. Encrypted messaging was viewed as a way for dissidents to get around repressive regimes.
With help from Mr. Schuler, Radio Free Asia’s Open Technology Fund, which is funded by the government and has a relationship with the State Department, granted Mr. Marlinspike more than $1.3 million between 2013 and 2014, according to the fund’s website.
Mr. Marlinspike was hardly a conventional Washington player. He and a government official missed meeting one another at a San Francisco burrito joint because the visitor assumed the dreadlocked Mr. Marlinspike couldn’t be the person he was there to see, Messrs. Schuler and Marlinspike said.
Mr. Marlinspike now runs a new firm, Open Whisper Systems , from a low-rent workspace in San Francisco’s Mission District. He has received other grants but says he isn’t interested in venture capital, partly because he would have to promise returns to investors.
His latest app, Signal , promises users secure text messages and voice calls. He acknowledges that it still has some kinks. Calls can drop if a user receives a traditional phone call while on an encrypted call. Mr. Marlinspike won’t disclose how many people use the app.
He still has work to do if he wants typical users to adopt encrypted communications.
But its minimalist blue-and-white design looks like something that could have emerged from Facebook.
Mr. Marlinspike says the San Francisco Police Department called last year to ask whether the app was secure enough for its officers to use. A spokesman for the department said it “did look at this vendor.”
Apple’s Private Relay: Better Than A VPN?
VPN Tier List (Comparison Table)
Welcome to Our VPN Tier list website. This website will help you improve your online privacy, security, and anonymity. VPN Tier List (Comparison Table)
VPN Tier List (Comparison Table)
(Click VPN To Visit Site, Or Number To Visit Youtube Review)
TIER 1 (God Tier): TorGuard VPN (4.91), AirVPN (4.0)
TIER 2 (Strong Tier): ExpressVPN (3.83), Windscribe (3.75), VyprVPN (3.70), iBVPN (3.62), VPNArea (3.62), PureVPN (3.58), CactusVPN (3.58), VPN.AC(3.54), VPN Unlimited (3.50), FrootVPN (3.50), iVPN (3.50), MullvadVPN (3.33), VPNCity (3.29), IPVanish (3.25), ZoogVPN (3.20), PrivateVPN (3.16), HotSpot Shield VPN (3.16), Perfect Privacy VPN(3.12), UltraVPN (3.12), FastestVPN (3.08), VeePN (3.0), Ivacy VPN (3.0)
TIER 3 (Below Average Tier): Avast SecureLine VPN (2.91), SaferVPN(2.91), Private Internet Access (2.91), F-Secure FreedomVPN (2.83), Astrill VPN (2.79), TunnelBear VPN (2.75), oVPN (2.75), NordVPN (2.75), SlickVPN (2.66), Norton Secure VPN (2.58), Unlocator VPN (2.33), Zenmate VPN (2.29), VPNGate (2.29), HideMyAss VPN (2.29), Cyberghost (2.16), Surfshark VPN (2.08), TurboVPN (2.00)
TIER 4 (Weak Tier): Freedom IP VPN (1.87), Ghostery Midnight VPN (1.83), ProtonVPN (1.37), X-VPN (.85)
Other Recommended Services:
What Antivirus does Tom Spark use? This question and many others can be answered here. It can be hard to find honest good reviews online and good products. Here are some of my favorite products I personally can vouch for either through my own extended use or reviews.
Best Private Browser: Brave Browser (Review)
* Privacy-Oriented Browsers Gain Traction
Best Antivirus Program: MalwareBytes (Review)
Best Encrypted Email Provider: PrivateMail (Review)
Best Password Manager: LastPass (Review)
Best Web host Provider: Siteground (Review soon)
Updated: 7-23-2021
What Keeps People From Using Password Managers?
Cybersecurity experts say they will make our online accounts more secure. But the usual methods of persuasion don’t work.
Many of us are vulnerable to hackers and eager to secure our online accounts, but lots of us also refuse to use an obvious solution: password managers.
Why? Our research has found that the typical reassurances and promises about password managers just don’t work. Fortunately, our research also suggests there are strategies that can persuade people to get past the psychological barriers and keep their data safe.
For the unfamiliar, a password manager stores your passwords securely and lets you access them with just one master password. Some password managers will fill in your password for you when you go to a website where you already have an account, and some will generate a strong password on your behalf.
Not So Simple
In a study I conducted with my Ph.D. student Norah Alkaldi, we found that the two most common methods of persuasion were ineffective in getting people to adopt password managers. The first is the “push” approach—the idea that by showing people the dangers of using simple passwords, recording passwords on their computer or using the same passwords at different sites, we would push them to adopt a safer approach. Users, we found, don’t respond to the push strategy.
The other, “pull,” approach—focusing on the positives of password managers—didn’t deliver any better results.
With neither push nor pull nor their combination working, it isn’t surprising that only 10% of users have adopted password managers. It is as if there is a glass ceiling preventing password-manager usage across the population.
We wanted to find out why. We discovered two types of “mooring factors” that keep people from changing their behavior. They are seldom addressed when people are trying to persuade others to use password managers, but they have a powerful impact.
First, there was the effort required to enter all your passwords into the password manager. Many people have some of their passwords stored in their browsers, others written down somewhere and yet more memorized.
The second type of mooring factor involves concerns. People don’t trust the developer of the password manager: Why, they wonder, should they give the keys to their online world to a password-management company that they neither know nor trust?
People also fear they will lose all their passwords if they forget their master password. (My father dubbed those concerns about personal limitations “forgettories” after forgetting passwords of his own.)
Getting Unmoored
All are valid concerns that are easily addressed.
First, the effort of migrating account credentials to the password manager should be acknowledged. Developers should focus their attention on easing the password-manager setup process as much as possible, perhaps importing people’s passwords from their browsers or from other repositories such as spreadsheets.
Second, when it comes to not trusting the password-management company, people should be reminded that these companies are in the business of storing passwords securely. They cannot afford to store passwords insecurely, because their entire business is built on the trust that comes from doing this well.
To that end, the source code of a password manager could be open and available to anyone to examine. Even though the average user couldn’t understand the code, influential experts could—and spread the word about the safety of using the password manager.
Some password managers permit access via a fingerprint or face biometric. Other password managers can ease users’ concerns about forgetting the master password by encouraging them to write down that password on a piece of paper and store it in a locked drawer or safe at home. Online hackers won’t be able to get hold of it, and users can refer to it whenever they need to.
Then when users know they won’t forget it any more, they can feel comfortable destroying the record. Or they can leave it there so that if anything happens to them, their nearest and dearest will be able to close all their accounts and not have to struggle with online companies and have to provide legal certificates to tie up all the loose ends.
Users can also be encouraged to use a memory from childhood as a password—early teens are best. All humans have a memory bubble from that stage of their lives, and these memories will endure throughout adulthood. They are also probably not in any online database. So, for example, you can use a telephone number your parents had when you were young. You could also use an old address.
So, if you lived at 3279 Dipdale Road when you were 10 years old, your password could be “3279 Dipdale Road aged 10.” Unless you’re still living there, in which case you might use the name of your 4th-grade teacher, the one who made you read that boring book: “Miss Amy’s Boring Book” or “Mrs. Mellville-Smith hated chewing gum.” The funnier you make the password, the more likely you are to remember it.
Those promoting password managers are currently relying on suboptimal strategies to encourage adoption. If we continue to do this, the glass ceiling will remain in place, uncracked. Improving adoption is a simple matter of explicitly addressing the mooring factors and raising awareness of the advantages of password managers and the risk of not using them. It is not that hard to do.
Internet History Privacy Software
When you surf the web, your computer stores tons of data about where you have been on the internet, what you have been doing and what information you have entered when surfing the web. Over time, this information builds up on your computer. If someone gains access to your computer, something that is common and easy to do, they will have a treasure trove of personal data that could cause you serious problems. Things like credit card information, bank account information, passwords, social security numbers, all are likely to be accessed by these kinds of hackers.
To prevent this, you need to regularly remove this information from your computer so that it does not pile up like a digital fire hazard. Here are some of the top rated privacy software products to help with this.
Webroot Window Washer – (all prices are estimated) – Removes unnecessary files, cleans up internet use, overwrites files to truly delete them, frees up computer space.
Cyber Scrub Privacy Suite – Frees up disk space, cleans up internet history, erases Vista shadow copies, uses 256 bit encryption, protects emails and chats, overwrites deleted files.
Portable Firefox – Free – Keep your browser on a flash drive. Minimizes information stored and shared, doesn’t put information on the PC at the same risk, portable for use on multiple computers.
Process Explorer – Malware Elimination: Windows Task Manager On Steroids!
AntiVirus Privacy Software:
Sometimes just removing information from your PC isn’t enough. Often times a computer virus will cause your computer to collect and transmit data surreptitiously. To prevent the most common viruses, use a good anti virus software like these.
Norton – Standard anti-virus PC protection from one of the most trusted names in anti-virus.
McAfee – Standard anti-virus PC protection from one of the most trusted names in anti-virus.
AVG – Free – Standard anti-virus protection, although less robust than the paid version, from a trusted name in free anti-virus protection.
Email Privacy:
Email is one of the most notoriously unprotected forms of communication. Not only is it possible to collect and analyze all plain text emails (that is emails that you have not taken steps to encrypt), but it is extremely easy for oppressive governments, identity thieves and hackers to get the contents of emails. To prevent intrusion by oppressive governments and unscrupulous identity thieves, use email encryption services.
BitMessage – (Free) – Protect the security of your emails. (No Security Audit As of 8-19-2013)
BM-2D8imU27HR8oKxV8EyDKrT3wD6brXU76VX
Send me a “Hello” or “test” message.
KryptoKit : Easy-to-Use, In-Browser Bitcoin and Messaging for the Masses
PGP – (Lifetime) – Protect the security of your emails.
Hushmail – Free – Encrypt your emails as they bounce around the internet, or, if emailing another Hushmail user, completely protect messages from just about all but warrant searches.
Encryption:
Whether it is business data that needs to be protected from competitors, or private communications with your attorney, or just keeping files on your laptop, like banking information, tax information, or other files that you don’t want compromised in case your laptop gets lost or stolen, you need to encrypt at least some of your files. Here is some great privacy software for doing that.
Once you accept these facts, it’s easy to see that you should use encryption to protect your important data and communications. But surely encrypting something like “yay :)” is overkill, right? The catch here is that encryption is most effective when everyone uses it all the time. Otherwise the encrypted stuff sticks out like a sore thumb, announcing to all the world that this data is special and secret. So even if you have nothing to hide, using encryption as part of your regular routine will help protect you when you really need it, not to mention helping to protect others who really need it.
The problem is, the barrier to entry has traditionally been fairly high. Access to modern encryption used to be restricted to government agencies. This is now changing as more and more people pick up on PGP for email and HTTPS for the web.
Telegram: Messages are heavily encrypted and can self-destruct. Open API and protocol free for everyone. Distributed servers are spread worldwide for security and speed. (For Android/iPhone)
Is Telegram Secure?
One look at the section on security from Telegram’s dedicated Wikipedia page will give you the answer to these questions, and the answer is no. In fact, Telegram’s security model has been heavily criticized by cryptography experts over the years.
Some of the main issues cited by the Wiki include not making E2E encryption the default for all chats, as well as storing media, messages, and contacts in the same place as decryption keys. The app’s proprietary MTProto Mobile Protocol has also been decried for containing unapproved and homebrewed cryptography that could potentially endanger the personally identifiable information stored on the platform.
Telegram’s claim to fame that it is more secure than other mass-market instant messaging apps such as WhatsApp has been disproved by professionals in the field. As stated above, WhatsApp encrypts all traffic end-to-end by default and operates within the boundaries of the expert-reviewed and approved Signal Protocol. Telegram, as we’ve discussed, attains neither.
In addition to this, researchers from Aarhus University in Denmark demonstrated in 2015 that Telegram does not achieve authenticated encryption or indistinguishability under chosen-ciphertext attack. Pavel Durov has defended the app publicly on numerous occasions, but reproach still arose regularly.
Telegram Security Breaches
This being said, is Telegram secure in the face of cyberattacks at least? The answer is still no. In fact, the app has fallen victim to plenty of breaches in recent years, the most notable of which I will briefly enumerate below.
On June 13, 2019, during the Hong Kong protests, Telegram suffered a denial-of-service attack performed by IP addresses linked to mainland China.
On March 30, 2020, a public ElasticSearch database containing the information of 42 million Iranian Telegram users was found on the Web. The app has been completely banned in the country since May 2018. This was just one of the numerous security breaches involving Iran on Telegram.
On October 19, 2020, hackers with access to the Signaling System 7, or SS7 for short, gained access to Telegram messenger. SS7 is used for linking mobile networks across the globe.
Minimizing The Cybersecurity Risks Associated With Telegram
To sum up the discussion thus far, Telegram is an instant messaging app that employs a custom encryption protocol known as MTProto. This has been heavily criticized by some experts over time, among other questionable approaches the app has taken. Plus, Telegram is no stranger to security breaches, especially over the last year or so.
However, there are many reasons you might still want to use it. Although E2E encryption is not its default, having the option to choose between regular and secret chats has a certain charm. And it’s not as if the alternative doesn’t exist at all.
Furthermore, Telegram is GDPR-compliant and supports two-step authentication. Its custom protocol recommends it as a favorite among tech enthusiasts thanks to its open-source model. Plus, you can add your own stickers. All in all, I’m not saying you should skip out on it entirely. Nevertheless, if you do choose to communicate on it, here are a few things you should consider from case to case.
KryptoKit: Easy-to-Use, In-Browser Bitcoin and Messaging for the Masses
Encryptfree – Free – (Extremely easy to use) Allows you to encrypt your data and your communications.
GnuPG – Free (Requires some skill to use) – Allows you to encrypt your data and your communications.
TrueCrypt – The development of TrueCrypt was discontinued back in 2014 and has subsequently not been maintained. A number of security flaws have been uncovered and as a result we are reaching out to people to highlight a list of alternatives.
KeyScrambler Personal – Free – Keeps your keystrokes from being logged by keyloggers.
Silent Phone: Encrypted voice and video calls on mobile devices. Currently available for iOS and Android, it can be used with Wi-Fi, EDGE, 3G or 4G cellular anywhere in the world.
Silent Text: Encrypted text messaging with attachments and “Burn Notice” feature for permanently deleting messages from device registries. Currently available for iOS with Android version under development.
Silent Mail: Encrypted e-mail on Silent Circle’s private, secure network through unique silentcircle.com e-mail accounts with up to 1 Gigabyte (GB) of encrypted mailbox space. Compatible with popular e-mail client software.
Silent Eyes: Encrypted video and voice teleconferencing from laptops and business conference systems through Silent Circle’s custom HD network. Compatible with Silent Phone. Currently available for Windows.
“there exists no method of verifying the effective security properties of Silent Circle, or to verify if, at all, the application does anything more or less than what it says it does. […] Silent Circle promises encryption and yet offers no method to verify the security, integrity and reliability of their claims.” Monty
Cryptocat Alternatives: Free open source software that aims to provide an open, accessible Instant Messaging environment that encrypts your conversations and works right in your browser.
Wickr: The app (not open source) sends messages, photos (and soon videos) that will eventually be erased. Wickr allows users to choose how long they want their digital missives to last: as short as one second, and as long as 5 days, 23 hours, 59 minutes and 59 seconds.
Bitmsg.me – Free – (Extremely easy to use) Allows you to encrypt your online communications. Send me a “Hello” or “test” message: BM-2DBubtaAq4Mz2DJxKcXwkmW2aWAsuzTmhB
BitMessage – (Free) – Protect the security of your emails.
BM-2D8imU27HR8oKxV8EyDKrT3wD6brXU76VX
Send me a “Hello” or “test” message.
Internet Use Itself:
Your IP address says a lot about you, your location, etc. and can be used to identify you personally. It can also be used to track you around the internet to figure out what you are doing, even if you have used other software to prevent your internet history from popping up. Plus, oppressive governments can just ask your ISP where you have been on the internet. If you don’t want this to happen, you should turn your web surfing into anonymous browsing with these tools.
Speedcheck.org – This free tool lets you test your internet connection. This is especially helpful if you want to stream a movie or play a game. This way you can always see if your connection is fast enough.
Unstoppable Domains – Allows you to have uncensorable websites, decentralized website hosting, replace long crypto wallet addresses with a simple, human-readable one and more
DropBox – Free – Cloud based file storage. No need to access files from any particular computer that might be compromised to track you. It is encrypted and you can upload files encrypted yourself for double the pleasure and double the fun of encryption. Paid services offer more storage.
IdentityCloaker – Makes anonymous browsing automatic and easy. Allows you to choose from several countries to base your anonymous browsing so you can watch the BBC from outside of England or watch Hulu from outside of the US.
Online Security Tools and the Advantages of Using Them
Cryptohippie – Gives you access to their secure encrypted Virtual Private Network (VPN) to do anonymous browsing, even from public WiFi hotspots, hotels and other public places.
Proxify – Free – Anonymous web proxy. Free but can be slow and limited functionality of some sites.
Tor – Free – Onion router which bounces your web traffic around through different servers to make it very difficult to trace your internet use to your IP address.
FireEye: The leader in next generation threat protection, stopping advanced malware, zero-day, and targeted APT attacks that bypass traditional defenses.
Password Management Privacy Software:
No matter how secure your networks, encryption, anti-virus and computer habits, the weakest point of all security systems is the password. Good password habits go a long way, but with increasing computing power, it is becoming increasingly easy to break simple passwords by brute force. Using password generators helps you keep track of more passwords and make those passwords more complex to prevent brute force attacks.
Multi One Password (Portable App) – A portable app that allows you to generate, store, and password-protect unique passwords for all of your accounts with one password. The only safe Password Manager that does not store users encrypted\hashed passwords neither locally in the users computers nor in the Cloud, is “Multi One Password”!
Free Password Generator – Use the this free Password Generator to create highly secure passwords that are difficult to crack or guess. Just select the criteria for the passwords you need, and click “Generate Password(s)”. Remember, the more options you choose, the more secure the passwords will be.
KeePass – Free – Keeps track of all of your passwords. You only have to remember one password to unlock the secure database where they are stored.
RoboForm – A lot like KeePass except it enters your passwords automatically. This can be very helpful when your strong passwords are long, complicated and easy to misspell.
Free – Encrypted Calls And Text Messages for Android
MaskMe: Create And Manage Secure Passwords, And Mask Your Email, Phone, And Credit Card As You Browse And Shop On The Web.
DuckDuckGo: DuckDuckGo is an Internet search engine that emphasizes protecting searchers’ privacy and avoiding the filter bubble of personalized search results.
Updated: 7-25-2021
The Key To Getting People To Be Safer Online: Make The Appeals More Personal
The nudges we currently use to prod people to use stronger passwords are aimed at the ‘average’ user. But few people are average.
Many of us know that strong passwords are crucial protection against hackers, yet many people still routinely use weak ones. So, how can they be encouraged to create stronger passwords? Our research suggests the answer is to make the appeal more personal.
Consider password meters, a common way to nudge people toward stronger passwords. They do some good, but they can’t help every individual choose their strongest password, because they are designed with the average user in mind, not taking into account differences in people’s personal traits and tendencies.
Yet few people are “average.” People who are good with numbers, for example, might be more motivated by being shown how long it would take a hacker to crack their password, rather than a simple “weak” to “strong” scale. Others might respond best to seeing how strong their password is compared with other people’s. We found that the most effective password nudges are targeted with differences like these in mind.
In our study, the effect of personalization was even larger than we had expected: When participants were given a password nudge tailored to their individual traits and tendencies, the passwords they created would have taken attackers about four times more resources and time to crack than passwords created by others who received a nudge that wasn’t personalized. And they were more than 10 times harder to crack than those of participants who weren’t nudged in any way.
We also found that personalized nudges didn’t have the undesired consequence of people creating passwords too strong for them to remember. Those who received personalized nudges were as likely as the other participants to remember their passwords when asked to do so in a follow-up study.
In our experiments, we had participants complete a large battery of questionnaires that measured various traits, including things like how much they consider future consequences, their style of decision making and how well they deal with numbers.
We then nudged each participant in different ways to encourage them to pick the strongest password they could. These nudges included standard-looking password meters, but also nudges designed to appeal to particular personal traits.
The results showed us which nudges worked best for which profiles of individual traits and tendencies. Next, to test those conclusions, we worked with a fresh sample of participants who received only one kind of nudge each. When we gave individuals a personalized nudge based on their profile, it increased the strength of the password they chose, compared with those who were shown either the nudge that had been found best on average or one chosen at random.
Identifying the power of personalized nudges is one step toward broader use of strong passwords. Now, for businesses, governments and other organizations that want to personalize their password nudges, the hard part will be figuring out how to gather the information needed to develop individual profiles while respecting people’s privacy.
Updated: 9-15-2021
Microsoft Rolls Out Passwordless Login For All Microsoft Accounts
Microsoft is rolling out passwordless login support over the coming weeks, allowing customers to sign in to Microsoft accounts without using a password.
The company first allowed commercial customers to rollout passwordless authentication in their environments in March after a breakthrough year in 2020 when Microsoft reported that over 150 million users were logging into their Azure Active Directory and Microsoft accounts without using a password.
Rolling Out To All Microsoft Accounts
Starting today, Redmond announced that users are no longer required to have a password on their accounts.
Instead, they can choose between the Microsoft Authenticator app, Windows Hello, a security key, or phone/email verification codes to log into Microsoft Edge or Microsoft 365 apps and services.
“Now you can remove the password from your Microsoft account and sign in using passwordless methods like Windows Hello, the Microsoft Authenticator mobile app or a verification code sent to your phone or email,” said Liat Ben-Zur, Microsoft Corporate Vice President.
“This feature will help to protect your Microsoft account from identity attacks like phishing while providing even easier access to the best apps and services like Microsoft 365, Microsoft Teams, Outlook, OneDrive, Family Safety, Microsoft Edge and more.”
As Microsoft Corporate Vice President for Security, Compliance, and Identity Vasu Jakkal added, threat actors use weak passwords as the initial attack vector in most attacks across enterprise and consumer accounts. Microsoft detects 579 password attacks every second, with a total of 18 billion incidents each year.
“One of our recent surveys found that 15 percent of people use their pets’ names for password inspiration. Other common answers included family names and important dates like birthdays,” Jakkal said.
“We also found 1 in 10 people admitted reusing passwords across sites, and 40 percent say they’ve used a formula for their passwords, like Fall2021, which eventually becomes Winter2021 or Spring2022.”
How To Go Passwordless Right Now
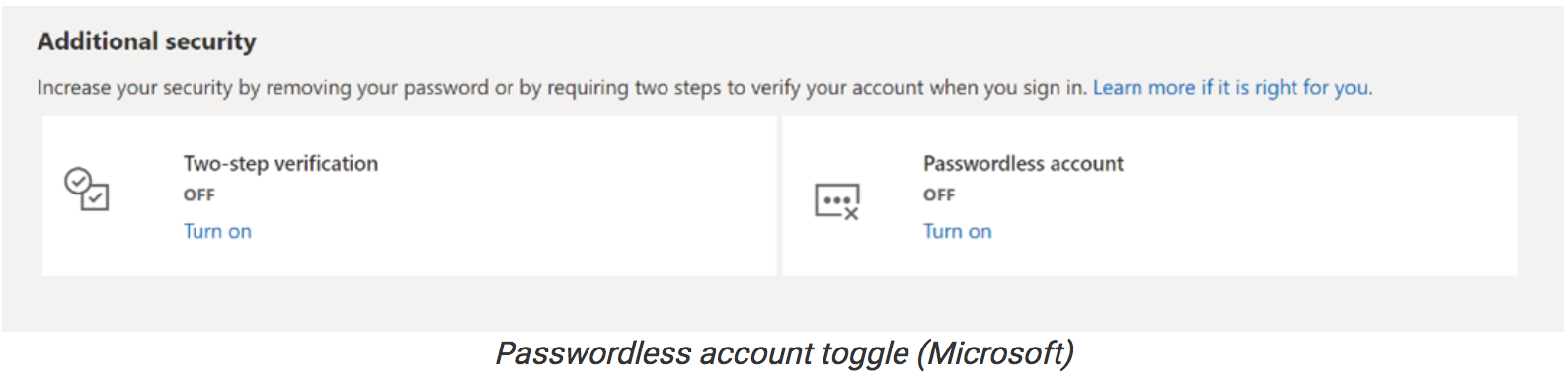
To start logging in to your Microsoft account without a password, you first need to install the Microsoft Authenticator app and link it to your personal Microsoft account.
Next, you have to go to your Microsoft account page, sign in, and turn on the ‘Passwordless Account” under Advanced Security Options > Additional Security Options.
The last steps require you to follow the on-screen prompts and approve the notification displayed by the Authenticator app.
More info on using a passwordless method to sign in to your account is available on Microsoft’s support website.
“Passwordless solutions such as Windows Hello, the Microsoft Authenticator app, SMS or Email codes, and physical security keys provide a more secure and convenient sign-in method,” Microsoft explains.
“While passwords can be guessed, stolen, or phished, only you can provide fingerprint authentication, or provide the right response on your mobile at the right time.”
Updated: 8-25-2022
World’s Most Popular Password Manager Says It Was Hacked
* LastPass Says That Source Code And Technical Info Was Stolen
* No Indication That Passwords Were Stolen, Investigation Finds
LastPass, a password manager used by more than 33 million people around the world, said a hacker recently stole source code and proprietary information after breaking into its systems.
The company doesn’t believe any passwords were taken as part of the breach and users shouldn’t have to take action to secure their accounts, according to a blog post on Thursday.
An investigation determined that an “unauthorized party” cracked into its developer environment, which is the software that employees use to build and maintain LastPass’s product. The perpetrators were able to gain access through a single compromised developer’s account, the company said.
We recently detected unusual activity within portions of the LastPass development environment and have initiated an investigation and deployed containment measures. We have no evidence that this involved any access to customer data. More info: https://t.co/cV8atRsv6d pic.twitter.com/HtPLvK0uEC
— LastPass (@LastPass) August 25, 2022
The attack struck a company that generates and stores hard-to-crack, auto-generated passwords for multiple accounts, like Netflix or Gmail, on behalf of its users — without the need to manually enter credentials. LastPass lists Patagonia, Yelp Inc. and State Farm as customers on its website.
Cybersecurity website Bleeping Computer reported that it had asked LastPass about the breach two weeks ago.
Allan Liska, an analyst on the Computer Security Incident Response Team at cybersecurity company Recorded Future, said he was impressed with the “speedy notification” from LastPass.
“While two weeks might seem like a long time to some, it can take a while for incident response teams to fully assess and report on a situation,” he said. “it will take time to fully determine the extent of any damage that may have been as result of the breach. However, for now it appears to not be client-impacting.”
LastPass didn’t immediately respond to a request for further comment.
There was speculation on social media that hackers may be able to access the keys to password vaults after stealing source code and proprietary information.
“It is unlikely that the stolen source code will give the criminals access to customer passwords,” Liska said.
Updated: 12-22-2022
LastPass Says Hackers Stole Customer Data, Encrypted Passwords
* LastPass Says Passwords Difficult For Hackers To Decrypt
* Company Warns Customers Of Phishing, Social Engineering
LastPass, a password management service, announced on Thursday that hackers stole encrypted copies of customer passwords and other sensitive data such as billing addresses, phone numbers and IP addresses.
The announcement is the latest update from a breach that occurred in August. At that time, the company said they had seen no evidence that the hackers had access to customer data or encrypted password vaults.
But the company’s statement on Thursday said that source code and technical information that were stolen as part of that hack was used to target another employee. The hackers were then able to obtain credentials and keys to access and decrypt data stored on a third-party cloud storage space.
They were able to copy such things as basic customer account information, including email addresses and the IP addresses from which customers accessed LastPass, and “fully-encrypted sensitive fields such as website usernames and passwords, secure notes and form-filled data.”
Password managers are a way for customers to store usernames and passwords in one place and can be accessed using a master password that a customer creates. The master password isn’t known to LastPass nor is stored or maintained by the company, it said in its statement.
The other encrypted data can only be decrypted “with a unique encryption key derived from each user’s master password,” the company said.
Nonetheless, LastPass warned customers that they could be targeted for social engineering, phishing attempts or other methods.
“The threat actor may attempt to use brute force to guess your master password and decrypt the copies of vault data they took,” the company said in a statement. “Because of the hashing and encryption methods we use to protect our customers, it would be extremely difficult to attempt to brute force guess master passwords for those customers who follow our password best practices.”
For those who follow LastPass’s password guidance, “it would take millions of years to guess your master password using generally available password-cracking technology,” the company said.
A representative for LastPass didn’t respond to messages seeking comment.
The company said that it has hired cybersecurity firm Mandiant to investigate the breach. It also said that it is rebuilding its entire development environment from scratch, an indication that hackers had thoroughly comprised the company’s sensitive systems.
LastPass said that its investigation is ongoing, and that it has notified law enforcement and “relevant regulatory authorities.”
Related Articles:
VPN Tier List 2020 (Comparison Table)
Inside China’s Major US Corporate Hack
Twitter Bug Exposed Millions of User Phone Numbers
U.S. Cyber Officials Give Holiday Shopping Advice For Consumers
Is Cayla The Toy Doll A Domestic Spy?
Google’s “Project Nightingale” Faces Government Inquiry Over Patient Privacy.
Which Password Managers Have Been Hacked?
DNS Over HTTPS Increases User Privacy And Security By Preventing Eavesdropping And Manipulation
Russia Steps Up Efforts To Shield Its Hackers From Extradition To U.S.
Barr Revives Debate Over ‘Warrant-Proof’ Encryption (#GotBitcoin?)
Should Consumers Be Able To Sell Their Own Personal Data?
Doordash Says Security Breach Affected Millions Of People (#GotBitcoin?)
Fraudsters Used AI To Mimic CEO’s Voice In Unusual Cybercrime Case (#GotBitcoin?)
Pearson Hack Exposed Details on Thousands of U.S. Students (#GotBitcoin?)
Cyber Hack Got Access To Over 700,000 IRS Accounts (#GotBitcoin?)
Take A Road Trip With Hotel Hackers (#GotBitcoin?)
Hackers Target Loyalty Rewards Programs (#GotBitcoin?)
Taxpayer Money Finances IRS “Star Trek” Parody (#GotBitcoin?)
IRS Fails To Prevent $1.6 Billion In Tax Identity Theft (#GotBitcoin?)
IRS Workers Who Failed To Pay Taxes Got Bonuses (#GotBitcoin?)
Trump DOJ Declines To Charge Lois Lerner In IRS Scandal (#GotBitcoin?)
DMV Hacked! Your Personal Records Are Now Being Transmitted To Croatia (#GotBitcoin?)
Poor Cyber Practices Plague The Pentagon (#GotBitcoin?)
Tensions Flare As Hackers Root Out Flaws In Voting Machines (#GotBitcoin?)
Overseas Traders Face Charges For Hacking SEC’s Public Filings Site (#GotBitcoin?)
Group Hacks FBI Websites, Posts Personal Info On Agents. Trump Can’t Protect You! (#GotBitcoin?)
SEC Hack Proves Bitcoin Has Better Data Security (#GotBitcoin?)

Leave a Reply
You must be logged in to post a comment.