DNS Over HTTPS Increases User Privacy And Security By Preventing Eavesdropping And Manipulation
DNS over HTTPS (DoH) is a protocol for performing remote Domain Name System (DNS) resolution via the HTTPS protocol. DNS Over HTTPS Increases User Privacy And Security By Preventing Eavesdropping And Manipulation
A goal of the method is to increase user privacy and security by preventing eavesdropping and manipulation of DNS data by man-in-the-middle attacks by using the HTTPS protocol to encrypt the data between the DoH client and the DoH-based DNS resolver.
Encryption by itself does not protect privacy, encryption is simply a method to obfuscate the data. As of March 2018, Google and the Mozilla Foundation started testing versions of DNS over HTTPS.
In addition to improving security, another goal of DNS over HTTPS is to improve performance: testing of ISP DNS resolvers has shown that many often have slow response times, a problem that is exacerbated by the need to potentially have to resolve many hostnames when loading a single web page.
Technical Detail
DoH is a proposed standard, published as RFC 8484 (October 2018) by the IETF. It uses HTTP/2 and HTTPS, and supports the wire format DNS response data, as returned in existing UDP responses, in an HTTPS payload with the MIME type application/dns-message. If HTTP/2 is used, the server may also use HTTP/2 server push to send values that it anticipates the client may find useful in advance.
DoH is a work in progress. Even though the IETF has published RFC 8484 as a proposed standard and companies are experimenting with it, the IETF has yet to determine how it should best be implemented. The IETF is evaluating a number of approaches for how to best deploy DoH and is looking to stand up a working group, Applications Doing DNS (ADD), to do this work and develop a consensus. In addition, other industry working groups such as the Encrypted DNS Deployment Initiative, have been formed to “define and adopt DNS encryption technologies in a manner that ensures the continued high performance, resiliency, stability and security of the Internet’s critical namespace and name resolution services, as well as ensuring the continued unimpaired functionality of security protections, parental controls, and other services that depend upon the DNS”.
Many Issues With How To Properly Deploy DoH Are Still Being Resolved By The Internet Community Including But Not Limited To:
* Parental Controls And Content Filters
* Split DNS In Enterprises
* CDN Localization
* Interoperability With 5G Networks
* Deployment Scenarios
DoH is used for recursive DNS resolution by DNS resolvers. Resolvers (DoH clients) must have access to a DoH server hosting a query endpoint.
DoH Lacks Native Support In Operating Systems. Thus, A User Wishing To Use It Must Install Additional Software. Three Usage Scenarios Are Common:
Using a DoH implementation within an application: Some browsers have a built-in DoH implementation and can thus perform queries by bypassing the operating system’s DNS functionality. A drawback is that an application may not inform the user if it skips DoH querying, either by misconfiguration or lack of support for DoH.
Installing a DoH proxy on the name server in the local network: In this scenario client systems continue to use traditional (port 53 or 853) DNS to query the name server in the local network, which will then gather the necessary replies via DoH by reaching DoH-servers in the Internet. This method is transparent to the end user.
Installing a DoH proxy on a local system: In this scenario, operating systems are configured to query a locally running DoH proxy. In contrast to the previously mentioned method, the proxy needs to be installed on each system wishing to use DoH, which might require a lot of effort in larger environments.
Installing A DoH Resolving Plugin For The Operating System
In all of these scenarios, the DoH client does not directly query any authoritative name servers. Instead, the client relies on the DoH server using traditional (port 53 or 853) queries to finally reach authoritative servers. Thus DoH does not qualify as an end-to-end encrypted protocol, only hop-to-hop encrypted and only if DNS over TLS is used consistently.
Public DNS Servers Using DoH
DNS over HTTPS server implementations are already available free of charge by some public DNS providers. See public recursive name server for an overview.
How To Enable And Test Doh In Chrome
To enable DoH support in Chrome, users would have to use a so-called command-line argument (or command-line flag), which is a set of additional instructions that are passed to the Chrome executable at start-up, to enable in-dev features.
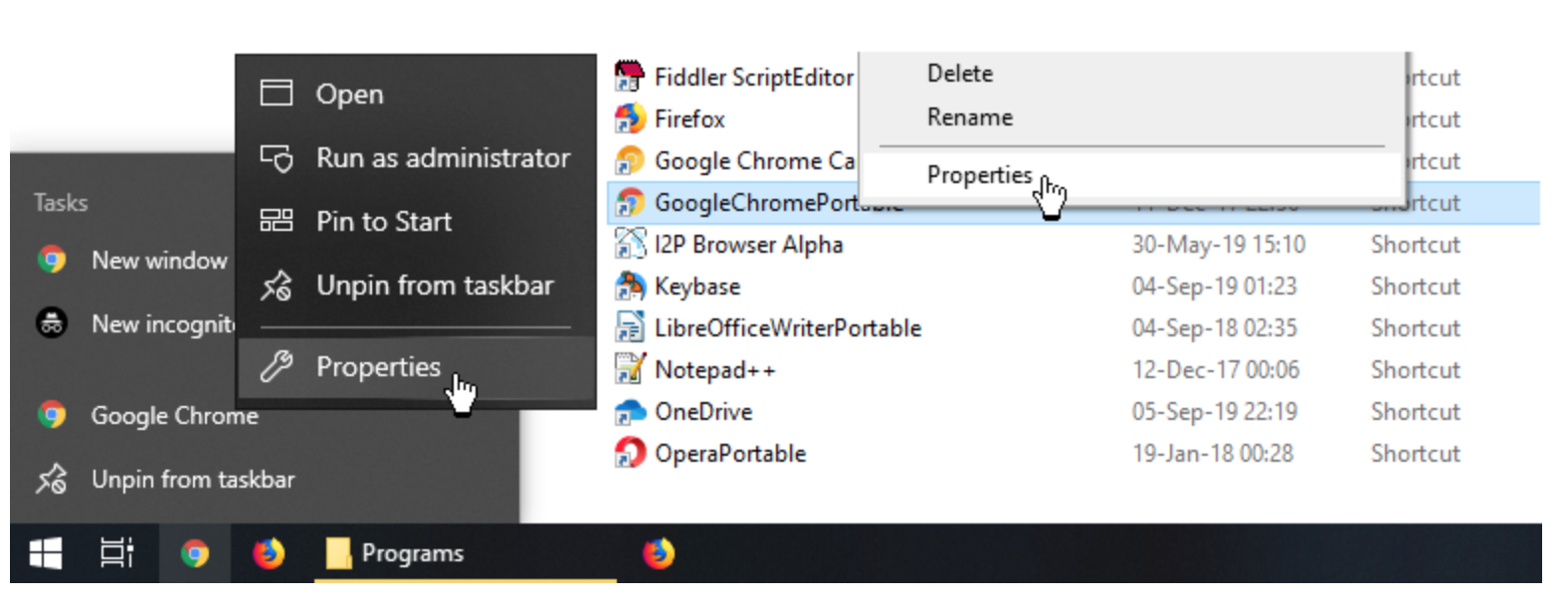
Step 1: Find your Chrome shortcut. This may be on your taskbar, desktop, start menu, or somewhere else on your file system.
Step 2: Right-click on the Chrome shortcut and select the Properties option.
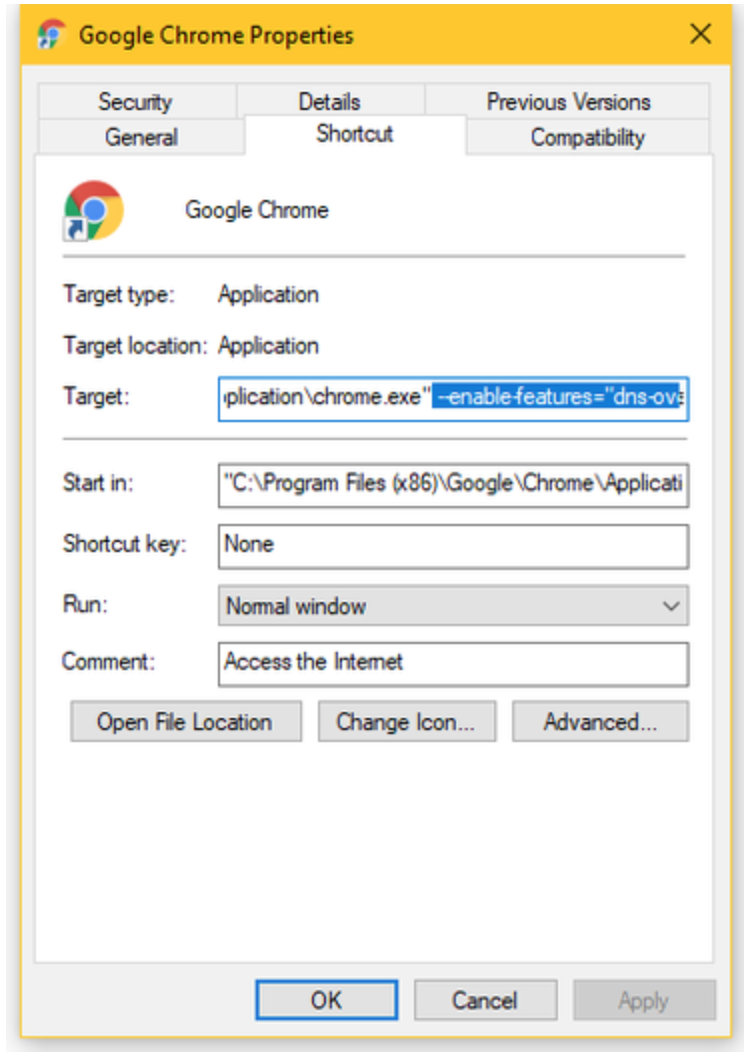
Step 3: In the Target field, add the following text at the end of the shortcut path and hit Save. [Source]
–enable-features=”dns-over-https<DoHTrial” –force-fieldtrials=”DoHTrial/Group1″ –force-fieldtrial-params=”DoHTrial.Group1:server/https%3A%2F%2F1.1.1.1%2Fdns-query/method/POST
The above text will configure Chrome to use the Cloudflare DoH server. Users can select any other DoH server from this list.
Step 4: If Chrome is already running, restart it. Otherwise, start Chrome.
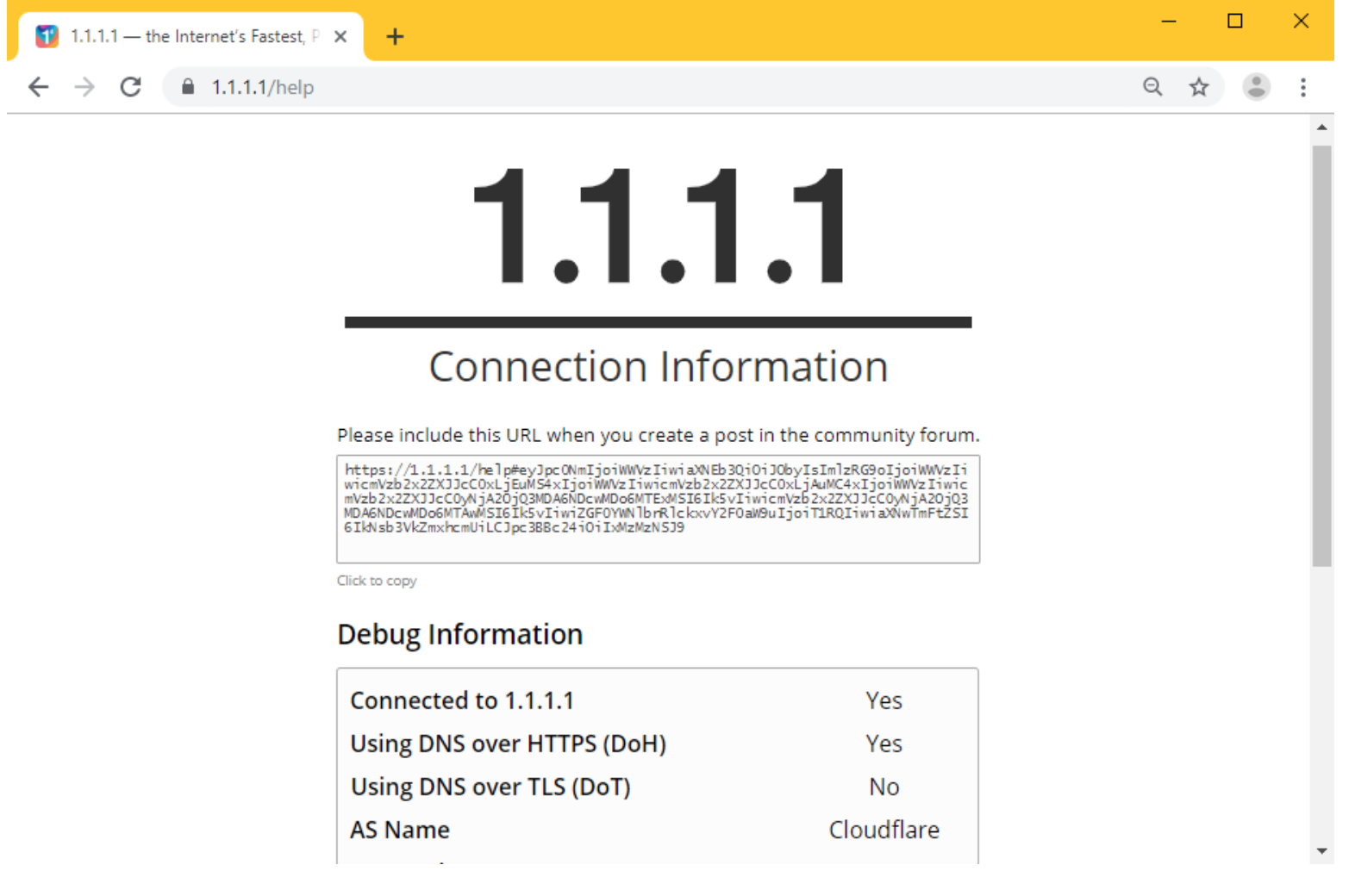
Step 5: To test if DoH support is working in Chrome, access https://1.1.1.1/help. On the right of “Using DNS over HTTPS (DoH)” the site should return “Yes.”
Client Support
- AdGuard for Android, AdGuard for iOS and AdGuard Home
- Cloudflare 1.1.1.1 client app for Android and iOS.
- Cloudflare resolver for Linux, MacOS and Windows.
- cURL since 7.62.0.
- DNSCrypt-proxy — Local DNS → DNS over HTTPS proxy.
- DNSP — Versatile DNSProxy. DoH server (C) and client (PHP) implementation.
- doh-php-client — PHP Implementation.
- Firefox since Version 62 and later— Browser support.
- Intra — an Android application by Jigsaw to route your DNS queries to a DNS-over-HTTPS server of your choice.
- nss-tls — a DoH-based resolver plugin for glibc.
- Technitium DNS Client — C# .NET cross-platform implementation.
- NextDNS client apps.
- Nebulo – DNS over HTTPS/TLS – for Android.
Criticism
The Internet Watch Foundation and the Internet Service Providers Association (ISPA)—a trade association representing UK ISPs—criticized Mozilla, developers of the widely-used Firefox Web browser, and Google—for supporting DoH, as they believe that it will undermine web blocking programs in the country, including ISP default filtering of adult content, and mandatory court-ordered filtering of copyright violations. The ISPA nominated Mozilla for its “Internet Villain” award for 2019 (alongside the EU Directive on Copyright in the Digital Single Market, and Donald Trump), “for their proposed approach to introduce DNS-over-HTTPS in such a way as to bypass UK filtering obligations and parental controls, undermining internet safety standards in the UK.” Mozilla responded to the allegations by the ISPA, arguing that it would not prevent filtering, and that they were “surprised and disappointed that an industry association for ISPs decided to misrepresent an improvement to decades-old internet infrastructure”. In response to the criticism, the ISPA apologized and withdrew the nomination. Mozilla subsequently stated that DoH will not be used by default in the UK market until further discussion with relevant stakeholders, but stated that it “would offer real security benefits to UK citizens”.
OpenBSD has disabled DoH by default in their builds of Firefox, citing its decision to rely on a CloudFlare server by default for DoH service as a disrespect of operating system configuration, and having potential privacy issues. DNS Over HTTPS Increases,DNS Over HTTPS Increases,DNS Over HTTPS Increases,DNS Over HTTPS Increases,DNS Over HTTPS Increases,DNS Over HTTPS Increases,DNS Over HTTPS Increases,DNS Over HTTPS Increases,DNS Over HTTPS Increases,DNS Over HTTPS Increases
References
- ^ Jump up to:a b c Chirgwin, Richard (14 Dec 2017). “IETF protects privacy and helps net neutrality with DNS over HTTPS”. The Register. Retrieved 2018-03-21.
- ^ “DNS-over-HTTPS | Public DNS | Google Developers”. Google Developers. Retrieved 2018-03-21.
- ^ Cimpanu, Catalin (2018-03-20). “Mozilla Is Testing “DNS over HTTPS” Support in Firefox”. BleepingComputer. Retrieved 2018-03-21.
- ^ Hoffman, P; McManus, P. “RFC 8484 – DNS Queries over HTTPS”. datatracker.ietf.org. Retrieved 2018-05-20.
- ^ Jump up to:a b Hoffman, P; McManus, P. “draft-ietf-doh-dns-over-https-08 – DNS Queries over HTTPS”. datatracker.ietf.org. Retrieved 2018-05-20.
- ^ “Experimenting with same-provider DNS-over-HTTPS upgrade”. Chromium Blog. Retrieved 2019-09-13.
- ^ Deckelmann, Selena. “What’s next in making Encrypted DNS-over-HTTPS the Default”. Future Releases. Retrieved 2019-09-13.
- ^ “About”. Encrypted DNS Deployment Initiative. Retrieved 2019-09-13.
- ^ “DNS over HTTPS Implementations”. 2018-04-27. Retrieved 2018-04-27.
- ^ Brinkmann, Martin (2019-03-21). “AdGuard 3.0 for Android: Redesign, Stealth Mode, Custom Filter Lists”. Ghacks Technology News. Retrieved 2019-08-02.
- ^ Orr, Andrew (2019-07-13). “AdGuard 3 Brings DNS Privacy, 250,000 Filter Rules, Premium Features”. The Mac Observer, Inc. Retrieved 2019-08-02.
- ^ Davenport, Corbin (2018-12-29). “AdGuard officially releases its own DNS service, and it works with Android Pie”. Android Police. Illogical Robot LLC. Retrieved 2019-08-01.
- ^ Cimpanu, Catalin. “Cloudflare launches Android and iOS apps for its 1.1.1.1 service”. ZDNet. Retrieved 2018-12-13.
- ^ “DNS over HTTPS”. Argo Tunnel. Cloudflare. Retrieved 20 July2019.
- ^ “DoH in curl”.
- ^ “DNSCrypt-proxy v2.0”. 2019-08-05.
- ^ “DNSP”. 2019-07-22.
- ^ “DNS over HTTPS PHP Client”. 2019-08-03.
- ^ “Trusted Recursive Resolver”. Mozilla. 15 September 2019. Archived from the original (html) on 12 September 2019. Retrieved 15 September 2019.
All preferences for the DNS-over-HTTPS functionality in Firefox are located under the `network.trr` prefix (TRR == Trusted Recursive Resolver). The support for these were added in Firefox 62.
- ^ “Improving DNS Privacy in Firefox”.
- ^ “Intra on Play Store”.
- ^ “GitHub – dimkr/NSS-TLS: A DNS over HTTPS resolver for glibc”. 2019-08-02.
- ^ “DNS over HTTPS C# Client”. 2019-07-18.
- ^ “nextdns”. www.nextdns.io. Retrieved 2019-07-13.
- ^ “Nebulo – DNS over HTTPS/TLS – Apps on Google Play”.
- ^ Cimpanu, Catalin. “UK ISP group names Mozilla ‘Internet Villain’ for supporting ‘DNS-over-HTTPS‘“. ZDNet. Retrieved 2019-07-05.
- ^ “Internet group brands Mozilla ‘internet villain’ for supporting DNS privacy feature”. TechCrunch. Retrieved 2019-07-19.
- ^ “British ISPs fight to make the web LESS secure”. IT PRO. Retrieved 2019-09-14.
- ^ Patrawala, Fatema (2019-07-11). “ISPA nominated Mozilla in the “Internet Villain” category for DNS over HTTPs push, withdrew nominations and category after community backlash”. Packt Hub. Retrieved 2019-09-14.
- ^ Hern, Alex (2019-09-24). “Firefox: ‘no UK plans’ to make encrypted browser tool its default”. The Guardian. ISSN 0261-3077. Retrieved 2019-09-29.
- ^ “Google Unveils DNS-over-HTTPS (DoH) Plan, Mozilla’s Faces Criticism”. BleepingComputer. Retrieved 2019-09-14.
Related Articles:
Russia Steps Up Efforts To Shield Its Hackers From Extradition To U.S.
Barr Revives Debate Over ‘Warrant-Proof’ Encryption (#GotBitcoin?)
Should Consumers Be Able To Sell Their Own Personal Data?
Doordash Says Security Breach Affected Millions Of People (#GotBitcoin?)
Fraudsters Used AI To Mimic CEO’s Voice In Unusual Cybercrime Case (#GotBitcoin?)
Pearson Hack Exposed Details on Thousands of U.S. Students (#GotBitcoin?)
Cyber Hack Got Access To Over 700,000 IRS Accounts (#GotBitcoin?)
Take A Road Trip With Hotel Hackers (#GotBitcoin?)
Hackers Target Loyalty Rewards Programs (#GotBitcoin?)
Taxpayer Money Finances IRS “Star Trek” Parody (#GotBitcoin?)
IRS Fails To Prevent $1.6 Billion In Tax Identity Theft (#GotBitcoin?)
IRS Workers Who Failed To Pay Taxes Got Bonuses (#GotBitcoin?)
Trump DOJ Declines To Charge Lois Lerner In IRS Scandal (#GotBitcoin?)
DMV Hacked! Your Personal Records Are Now Being Transmitted To Croatia (#GotBitcoin?)
Poor Cyber Practices Plague The Pentagon (#GotBitcoin?)
Tensions Flare As Hackers Root Out Flaws In Voting Machines (#GotBitcoin?)
Overseas Traders Face Charges For Hacking SEC’s Public Filings Site (#GotBitcoin?)
Group Hacks FBI Websites, Posts Personal Info On Agents. Trump Can’t Protect You! (#GotBitcoin?)
SEC Hack Proves Bitcoin Has Better Data Security (#GotBitcoin?)

Leave a Reply
You must be logged in to post a comment.