Cyber-Security
PG&E Identified As Utility That Lost Control of Confidential Information
As a result of 2016 failure, 30,000 records about PG&E’s cyber assets were exposed on the internet. PG&E Identified As Utility That Lost Control of Confidential Information San Francisco-based PG&E Corp. was identified Friday as the large utility that authorities had fined in May for losing control of a database with…

Trump Unleashes U.S. Use of CyberWeapons (#GotBitcoin?)
The Trump administration’s move to loosen rules of engagement for U.S. cyberattacks has prompted questions about how the military will carry out offensive digital strikes, and whether hostilities with foreign adversaries will rapidly escalate. Trump Unleashes U.S. Use of CyberWeapons ‘The devil is in the details,’ says Trump’s former homeland security…

Tensions Flare As Hackers Root Out Flaws In Voting Machines (#GotBitcoin?)
Defcon hack-a-thon conference aims to help test election security, but makers of voting equipment raise doubts. Tensions Flare As Hackers Root Out Flaws In Voting Machines (#GotBitcoin?) Hackers at the Defcon computer security conference believe they can help prevent manipulation of U.S. elections. Some election officials and makers of voting…

Next Target For Hackers In 2024 Is Your Brain
(1). Hacking Our Brains Via Our Sense of Smell: Next Target For Hackers In 2024 Is Your Brain “Mind your wants 'cause there's someone that wants your mind”, George Clinton Ilana Hairston is a psychologist at The Academic College of Tel-Aviv Yaffo in Israel. She studies how the brain works when…

Next Major Target For Hackers In 2023-24 Medical Data And Wireless Medical Devices
Next Great Target For Hackers And Digital Troublemakers In 2023-24 Is Health Care Records And Wireless Medical Devices. Next Major Target For Hackers In 2023-24 Medical Data And Wireless Medical Devices Hospitals Have Weak Security For Mobile Devices [embed]https://www.youtube.com/watch?v=R7wz6RxcjDE&list=PLU1KxUVqGmaOU_q55fcRJoahAQ3lKH-9U[/embed] Many health-care organizations fail to protect patient information residing on personal…

Online Privacy Tools And Tips
Moxie Marlinspike : The Coder Who Created Encrypted Tools That The NSA/FBI Can't Crack. Online Privacy Tools and Tips [embed]https://youtu.be/tOMiAeRwpPA?list=PLU1KxUVqGmaOdU83GF23I3uwim_NFkzLW[/embed] In the past decade, Moxie Marlinspike has squatted on an abandoned island, toured the U.S. by hopping trains, he says, and earned the enmity of government officials for writing software. [embed]https://www.youtube.com/watch?v=pURzvhYQ2FQ&list=PLt3zZ-N423gVst3WSgHXHRQYzgpmUkBUN[/embed] Mr. Marlinspike created…

Bionic Eyes Seen As The Perfect Spy Tool
It's very exciting and it's very cool! The technology tested to date lets the wearer primarily see in black and white. It is most useful for seeing sharp contrasts, such as the painted white line of a crosswalk on a dark road. But scientists hope that they can improve the…

Who’s Watching Who? gSpy vs. iSpy
Randi Zuckerberg, sister of Mark, thinks she's got problems? Last week she complained that a family photo posted to Facebook had been circulated on Twitter without her authorization. Who's Watching Who? gSpy vs. iSpy Well, over a few hours around town that day I counted 57 cameras–at traffic lights, various stores and…
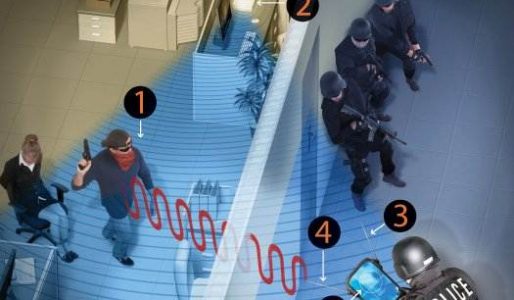
A Device That Can See Through Walls Using Your Wi-Fi Router
The Wi-Fi radio signals found in most homes can now be used to pinpoint your movement, when they are sniffed by a system being developed by researchers in London. A Device That Can See Through Walls Using Your Wi-Fi Router Kevin Chetty of University College London's Department of Security…

How To Stop Flame and Stuxnet (Super-Malware) Dead in Their Tracks
A new plug-and-play device for factories and power plants could stop malicious code from triggering a major malfunction, or worse. How To Stop Flame and Stuxnet (Super-Malware) Dead in Their Tracks Let me introduce you to Norm. "Norm!" No, not George Wendt. Norman is an IT security company based in Norway that's selling…

How to Track a Cell Phone Even When It’s Not Being Used
The U.S. Department of Justice now says its use of a cellphone-tracking device in a controversial Arizona case could be considered a "search" under the Fourth Amendment, a tactical move legal experts say is designed to protect the secrecy of the new cell phone locators. How to Track a Cell Phone…

Phishing/Scamming: Why You Shouldn’t Take The Bait!
Phishing/Scamming One of the primary reasons for the severe increase in phishing/scamming among and individuals and smaller organizations is that online criminals believe these institutions and people do not possess the resources, knowledge or employees to protect themselves or respond to a phishing/scamming attack. Many of the larger banks, retailers…
