What You Can Learn From The Best Hackers And Spies (#GotBitcoin?)
When my nanny sends me a photo of my 18-month-old son busy at play, my immediate thought: He’s a genius. What You Can Learn From The Best Hackers And Spies (#GotBitcoin?)
When a hacker sent me a photo of my son, after breaking into the baby monitor on my Wi-Fi network, my thought: I’m an idiot.
To be fair, I gave Alexander Heid, a certified ethical hacker and chief research and development officer at security firm Security Scorecard, free rein to try to break into all my cameras. Still, that’s no excuse for me not changing the default password.
We’re putting cameras in more and more places, yet more and more people are putting tape over their computer webcams because they fear who may be looking.
How secure are these tiny eyes into our private lives? The bad news is, it was possible for Mr. Heid to get into my Windows 10 laptop’s webcam and, from there, my entire home network. He also eventually cracked my MacBook Air. The good news is that both operating systems were initially able to thwart the hacker. It took me performing some intentionally careless things for him to “succeed.”
If you’re on guard and aware that people are out there trying to trick you to let down your defenses, and you follow some basic practices, you can make it much more difficult for the bad guys to get to you.
Mr. Heid employed off-the-shelf hacking tools often used by security professionals to find network and device vulnerabilities. With more time and resources, however, he says he could have better concealed the attacks. Even so, they highlighted some key human vulnerabilities. While I expected the phishing emails, and played along with them, his requests were all fairly simple user actions or settings adjustments that we might encounter in our daily use over months or even years.
When Mr. Heid got into my system, he got a glimpse of my digital body—my passwords, emails, personal info. And the truth is, most hackers are more interested in our bank info than our birthday suits. Various security experts told me while webcam hacks happen, notably to women or children, they’re not as common as other threats.
Here’s What I Learned Along The Way About How To Play Things Safer
Getting My Attention
In a recent tweet, I announced I was looking to hire a new video producer. Mr. Heid decided that was his attack vector. He got together everything needed for “Rutiger Watkins” to apply for the job: a coherent intro email with a résumé attached and a link to a video reel. Of course, the reel was actually a file containing malware, and the résumé was a Word doc that had the instructions for executing it. (A similar fake-résumé tactic was recently used by Russian hackers.)

Sure, I was in on it, but spear-phishing—the practice of targeting individuals by leveraging public information and posing as a known or trustworthy sender—is getting increasingly popular. “Most people can fall for some social-engineering attack,” says Jack Koziol, the chief executive of InfoSec Institute. “It’s becoming easier and easier to trick a person to just click on a link.” There’s also an abundance of information about us now on the internet, too.
What you can do: We’re the weakest part of our own digital security. We’re busy, we click things, we ignore warning signs. Be suspicious of even the most routine digital communications. Pay attention to those email warnings. I didn’t receive a phishing warning in Gmail when I got the fake job application, but the email did have a big yellow warning about being unable to scan the encrypted attachment for viruses. (Gmail has three classes of security notifications that differ in size and color based on the anticipated threat level.)
Getting Into Windows
When I opened the attached Word doc, Microsoft ’s built-in, free anti-virus software, Windows Defender, immediately flagged it. When I clicked the link to the “reel,” the file that began downloading was identified as a virus and deleted. The system worked, but I wanted to see what would happen if I were someone who didn’t have anti-virus turned on in the first place, or who turned it off because it got annoying.
I went into Windows settings and disabled real-time virus protection. I was able to download the “reel” without issue. But when I double-clicked the document, Microsoft Word opened it in a protected view. I intentionally dismissed the warning sign and enabled editing of the document.

Once the two files were activated, Mr. Heid was able to fire up my webcam within 15 minutes. There I was, no makeup on and thankfully not picking my nose. The HP’s indicator light went on when he first reached the camera, but everything on the laptop’s desktop remained as is. He set it to snap photos every few seconds and was even able to tap into my mic and hear the commotion in my home. Some of HP’s newest laptops have a physical webcam kill switch that disconnects the camera’s power supply.
Microsoft patched this Microsoft Office vulnerability in April 2017, which is why Mr. Heid had to use a second file to successfully infect the updated machine, says Tanmay Ganacharya, Microsoft’s general manager of Windows Defender, in an email. The key weakness was in my own actions. “If security features are deliberately disabled and warnings are not heeded, technology becomes limited in how well it can protect users,” he says.
What you can do: Windows users should make sure Windows Defender or other name-brand anti-virus is always up and running. For users who don’t want to worry every time they download something, Mr. Ganacharya recommends putting Windows 10 in S Mode, which only runs apps that have been approved by Microsoft. It also helps to view documents in the cloud, for instance in Office Online or Google Docs, where any malware won’t touch your machine.
Getting Into The Mac
Hacking a 2015 MacBook Air running the latest MacOS version, Mojave, also required a multistep process (and some missteps by the “victim”). This time the malware was embedded in an .odt document, an open-source file format.
To open it, I downloaded LibreOffice. The free version of the popular open-source office suite isn’t in the Mac App Store, however, so I had to disable the Mac security setting that prevents unverified developer software installation. This is something that comes up often when downloading the many popular apps that aren’t in the App Store. (I could have paid $14 for a version in the App Store, however.)
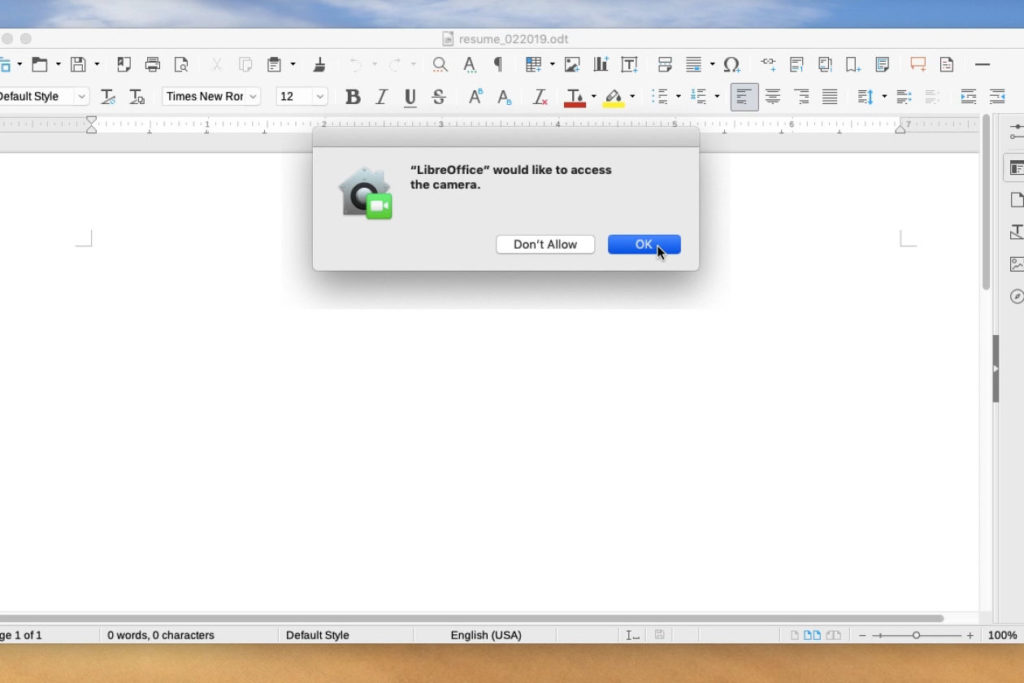
Once I installed LibreOffice, I turned off its macro security setting, per the hacker’s instructions. There are scenarios where you might do this—say, for instance, because your company used a specially designed inventory spreadsheet or sales form—but for most people, it’s a bad idea.
“Setting macro security to low is like jumping from the 10th floor hoping to land on a soft surface. Chances to survive are close to zero,” says Italo Vignoli, a founder of The Document Foundation, which oversees LibreOffice.
Whenever the security scenario slacked even a bit, the hacker was able to gain an advantage. Before snapping a few shots of me sitting in a Starbucks , he downloaded some files he needed to access the camera. I did get a pop-up asking for camera access, and I clicked OK, like we might do when we’re in a rush. Because Mr. Heid was only snapping stills, the webcam LED only lit up for a second.
“Apple has built security features into MacOS to protect users from mistakenly downloading unsafe software,” said an Apple spokesman in a statement. “We recommend downloading software only from the Mac App Store or trusted members of the Apple Developer Program and never opening files from unknown or untrusted sources.” The company also stresses the importance of paying attention to warnings.
What you can do: Installing those nagging security and OS updates are a must—on your phone, laptop, router, thermostat, really anything that connects to the internet. They include the latest attempts to patch the holes that hackers use to get in. Mac users should install Malwarebytes or other malware-fighting software—and don’t turn off any security features just because someone asks you to.
And yes, my laptop now also has a sliding webcam cover, though a piece of tape or Post-it will do.

What about the cameras on our phones? While it’s possible to hack a smartphone, it’s harder. “Many vendors are doing an excellent job securing phones,” says Dave Lewis, advisory chief information security officer at Cisco subsidiary Duo Security. Various security experts I spoke to highlighted the strong security of Apple’s iOS. Android is considered a more likely target but Google has made security improvements over the last few years. Plus, phone cameras aren’t exactly revealing. A hacker could get some great shots of my ceiling right now.
Getting Into Everything Else
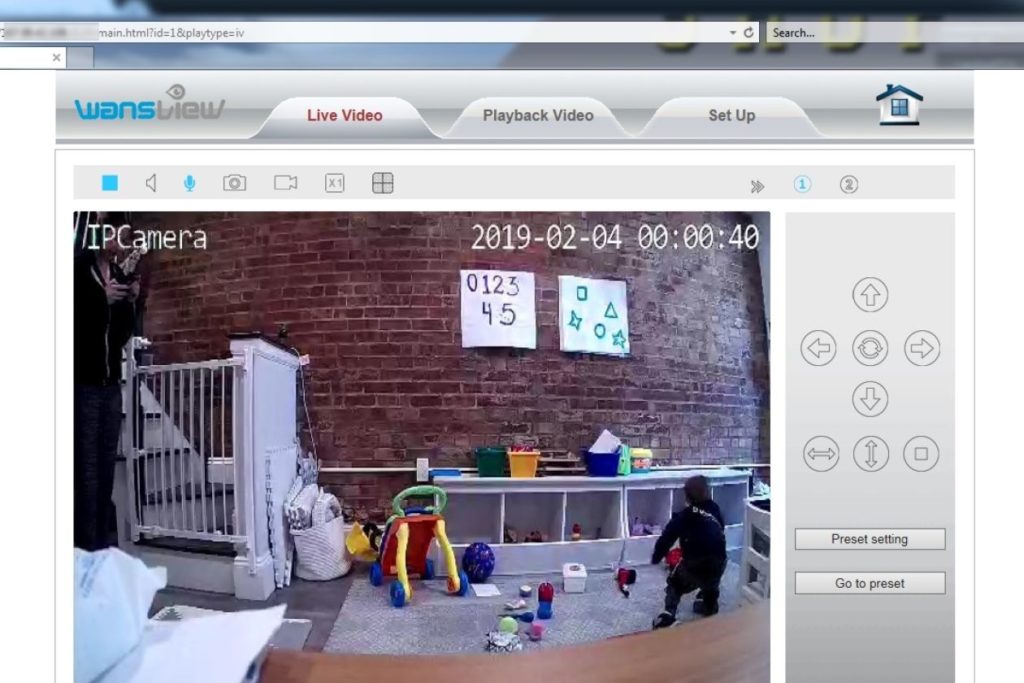
When connected to the Windows laptop, Mr. Heid was able to scan for other devices on my home Wi-Fi network. He quickly found two cameras: a Nest Camera and a Wansview 1080p connected baby monitor that I bought for this column along with the laptops.
From this point on, getting into the baby monitor didn’t even require hacking. He went to its IP address, searched Google for the default username and password and typed it in to the camera’s web portal. He had a nice stream of my son’s playroom—my son included.

When I configured the camera with Wansview’s iPhone app, it wouldn’t allow me to change the default credentials. If you want to change the password, you have to go back into the settings of the app and change it later.
While this was a result of bad password hygiene, various security experts told me that IP web cameras have some of the poorest security. They pointed out a site where you can view webcam streams from inside homes of oblivious users.
The setup process requires default settings for technical reasons, said Una Tan, a Wansview representative, who also stressed the importance of changing the password (after setup) and keeping your home network secure.
The cloud-based Nest camera is managed through a Nest account, which is safer because it requires you to create a password, has other security features and is protected by parent-company Alphabet Inc.’s own security. Unfazed, Mr. Heid pulled up a database of usernames and passwords that have been publicly shared after major security breaches. He found an old password of mine, but it would have failed because I use a unique password on my Nest account. (Other Nest owners haven’t been so careful.)
If he was really determined, he could have installed a keystroke-logging program on my laptop to capture my passwords over time.
What you can do: PASSWORDS ARE IMPORTANT. As soon as Mr. Heid showed me that old password of mine, I immediately strengthened the passwords of my most important accounts and made sure there were no repeats. Use a password manager to manage all your various passwords and turn on two-factor authentication where you can.
Also, you don’t need to have your own personal ethical hacker to see if your accounts have been breached. Go to haveibeenpwned.com and type in your email address.
The laptops I used for this experiment have been reset to factory settings, have web camera covers and up-to-date software. As for a baby monitor? I’m using one that doesn’t connect to the internet at all.
Updated: 11-18-2019
Hacker Offers $100K In BTC As Bounty For Hacking Halliburton
Anonymous hacker Phineas Fisher will pay up to $100,000 in crypto to hackers for leaking some damaging information about global high-profile firms. The bounty, called the “Hacktivist Bug Hunting Program” was published on Nov. 15 and targets big companies including Israeli spyware vendor NSO Group and American oil company Halliburton, as Vice reported on Nov. 17.
The idea of the new bounty is to pay other hackers who carry out politically motivated hacks against firms, which would lead to the disclosure of documents in the public interest, according to Vice. Other targets reportedly include mining and livestock companies in South America.
Phineas Fisher will pay hackers in Bitcoin or Monero
In a purported manifesto published on Friday, Phineas Fisher said that he will pay hackers in cryptocurrency such as Bitcoin (BTC) or privacy-oriented coin Monero (XMR).
Phineas Fisher, who has never been identified and may be an individual or a group of hackers, reportedly stated:
“Hacking to obtain and leak documents with public interest is one of the best ways for hackers to use their abilities to benefit society […] I’m not trying to make anyone rich. I’m just trying to provide enough funds so that hackers can make a decent living doing a good job.”
Anonymity Of Hacktivism Raises Major Concerns
As reported by Vice, Phineas Fisher’s identity has never been made public — even after an investigation into the famous Hacking Team hack. In 2015, Phineas Fisher took over the servers of the Hacking Team, an Italian firm providing hacking and surveillance software for police and corporations, in order to expose all the company’s secrets in a 400-gigabyte torrent file containing internal emails, files, and source code. After an extensive investigation, Italian authorities reportedly said that they had no idea who Phineas Fisher was.
As Phineas Fisher has remained anonymous since 2014 and recently announced the controversial bounty, the anonymity of hacktivism has raised major concerns among nations so far. Andrew Thompson, a manager at the cybersecurity firm FireEye, tweeted Nov. 17 that he has “zero percent trust in anything portrayed as hacktivism, which is anonymous.”
On Nov. 14, Cointelegraph reported on an anonymous organization called Unknown Fund, which plans to donate $75 million in Bitcoin to startups focused on anonymity and the protection of personal data.
What You Can Learn,What You Can Learn,What You Can Learn,What You Can Learn,What You Can Learn,What You Can Learn,What You Can Learn,What You Can Learn,What You Can Learn,What You Can Learn,What You Can Learn,What You Can Learn,What You Can Learn,What You Can Learn,What You Can Learn,What You Can Learn,What You Can Learn,What You Can Learn,What You Can Learn,What You Can Learn,What You Can Learn,What You Can Learn,What You Can Learn,What You Can Learn,
Related Articles:
Which Password Managers Have Been Hacked?
Google’s “Project Nightingale” Faces Government Inquiry Over Patient Privacy.
DNS Over HTTPS Increases User Privacy And Security By Preventing Eavesdropping And Manipulation
Russia Steps Up Efforts To Shield Its Hackers From Extradition To U.S.
Barr Revives Debate Over ‘Warrant-Proof’ Encryption (#GotBitcoin?)
Should Consumers Be Able To Sell Their Own Personal Data?
Doordash Says Security Breach Affected Millions Of People (#GotBitcoin?)
Fraudsters Used AI To Mimic CEO’s Voice In Unusual Cybercrime Case (#GotBitcoin?)
Pearson Hack Exposed Details on Thousands of U.S. Students (#GotBitcoin?)
Cyber Hack Got Access To Over 700,000 IRS Accounts (#GotBitcoin?)
Take A Road Trip With Hotel Hackers (#GotBitcoin?)
Hackers Target Loyalty Rewards Programs (#GotBitcoin?)
Taxpayer Money Finances IRS “Star Trek” Parody (#GotBitcoin?)
IRS Fails To Prevent $1.6 Billion In Tax Identity Theft (#GotBitcoin?)
IRS Workers Who Failed To Pay Taxes Got Bonuses (#GotBitcoin?)
Trump DOJ Declines To Charge Lois Lerner In IRS Scandal (#GotBitcoin?)
DMV Hacked! Your Personal Records Are Now Being Transmitted To Croatia (#GotBitcoin?)
Poor Cyber Practices Plague The Pentagon (#GotBitcoin?)
Tensions Flare As Hackers Root Out Flaws In Voting Machines (#GotBitcoin?)
Overseas Traders Face Charges For Hacking SEC’s Public Filings Site (#GotBitcoin?)
Group Hacks FBI Websites, Posts Personal Info On Agents. Trump Can’t Protect You! (#GotBitcoin?)
SEC Hack Proves Bitcoin Has Better Data Security (#GotBitcoin?)

Leave a Reply
You must be logged in to post a comment.